Lock management method capable of realizing long-distance control
A remote control and management method technology, applied in the field of lock management, can solve the problems of low concealment, embezzlement, easy to forget to carry, etc., and achieve the effect of convenient concealment and easy use
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
no. 1 example
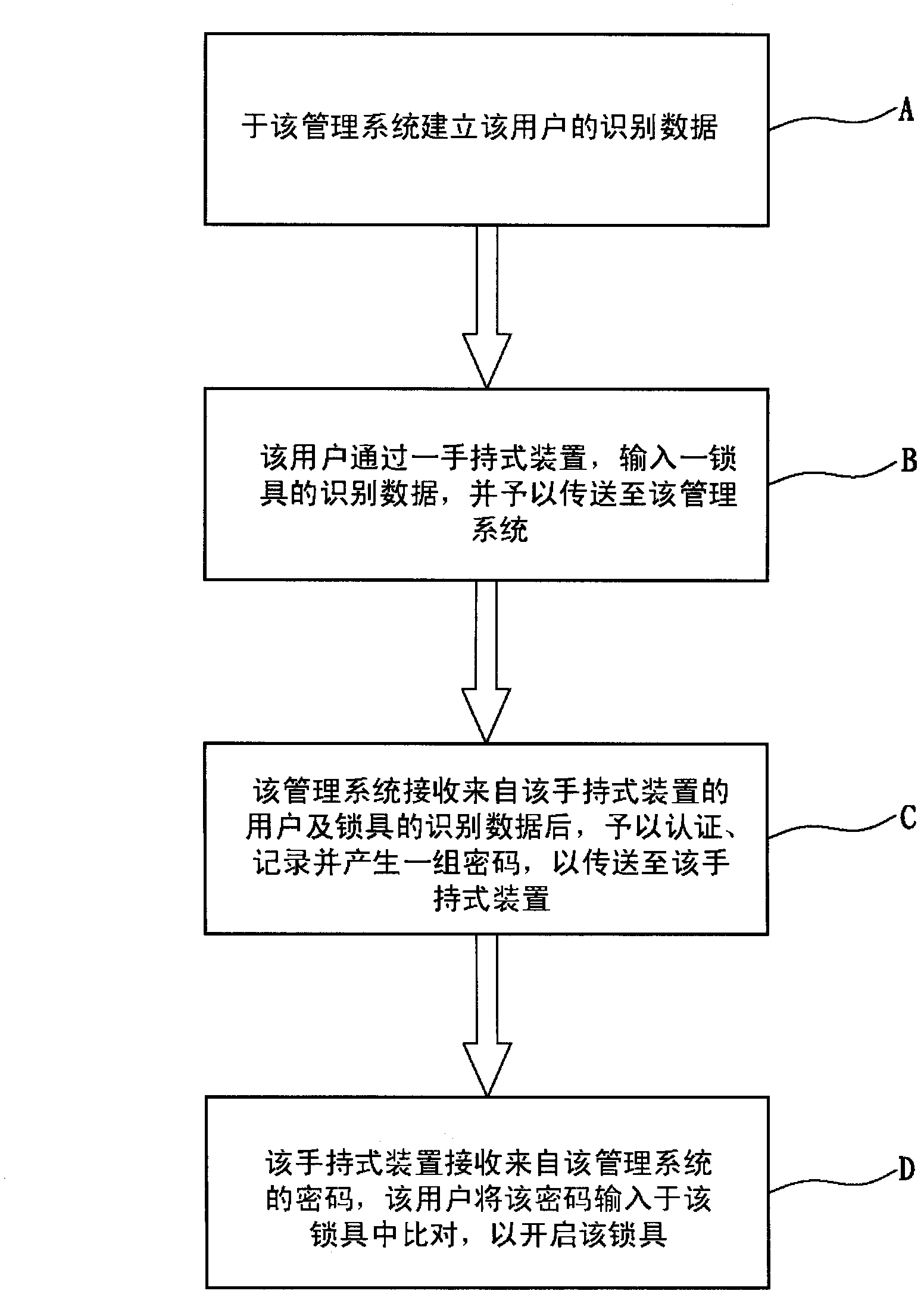
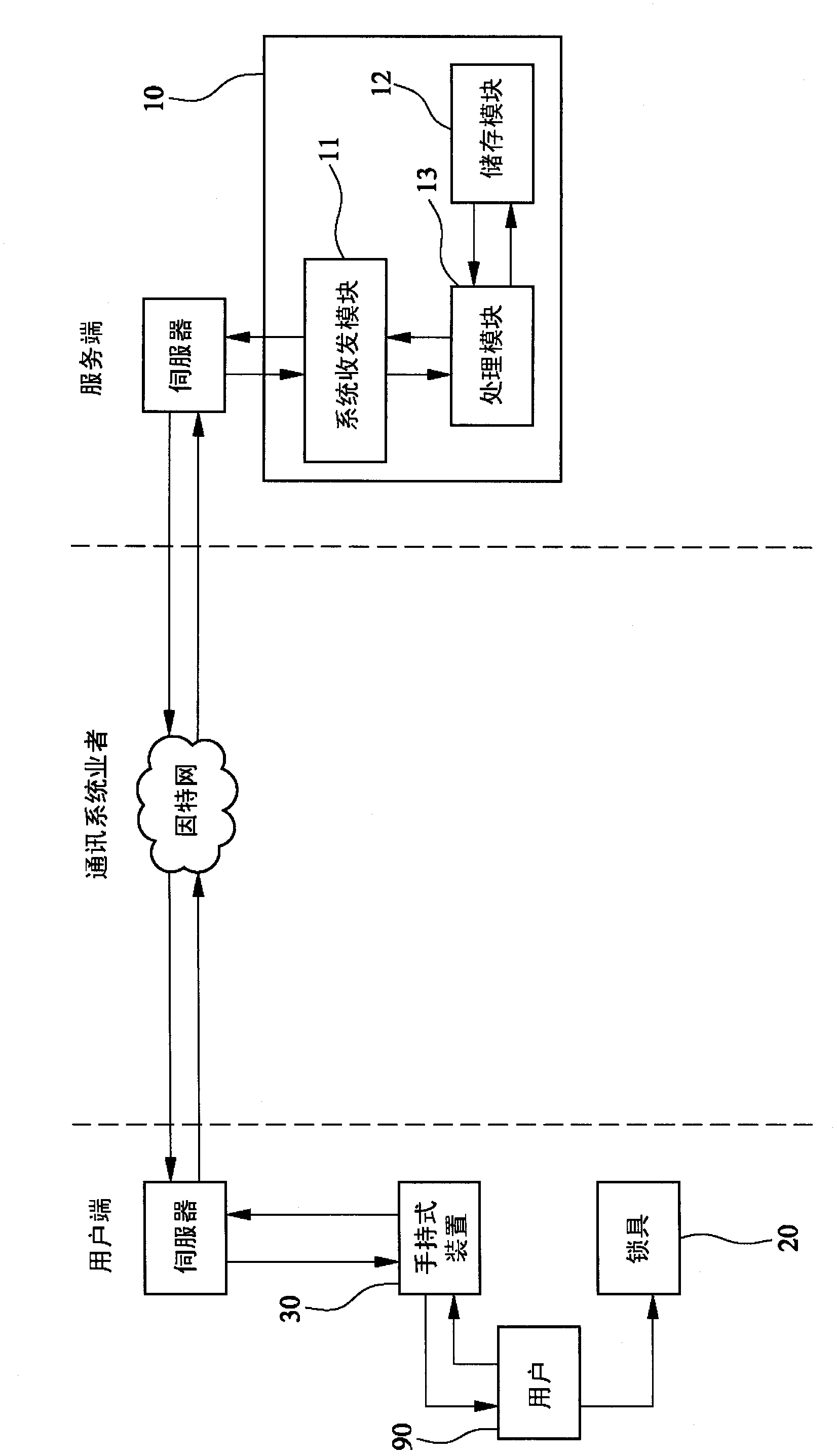
[0037] see Figure 1 to Figure 4 As shown, the present invention is a remote-controllable lock management method. A management system 10 is used to remotely control a lock 20 to assist a user 90 in trusteeship. The method includes:
[0038] (A) establishing the identification data of the user 90 in the management system 10;
[0039] (B) The user 90 inputs the identification data of a lock 20 through a handheld device 30 and transmits it to the management system 10;
[0040] (C) After the management system 10 receives the identification data of the user 90 and the lock 20 from the handheld device 30, it authenticates, records and generates a set of passwords to be sent to the handheld device 30;
[0041] (D) The handheld device 30 receives the password from the management system 10 , and the user 90 inputs the password into the lock 20 for comparison to open the lock 20 .
[0042] To allow the user 90 to use the lock 20 to lock his articles (such as bicycles, automobiles, etc...
no. 2 example
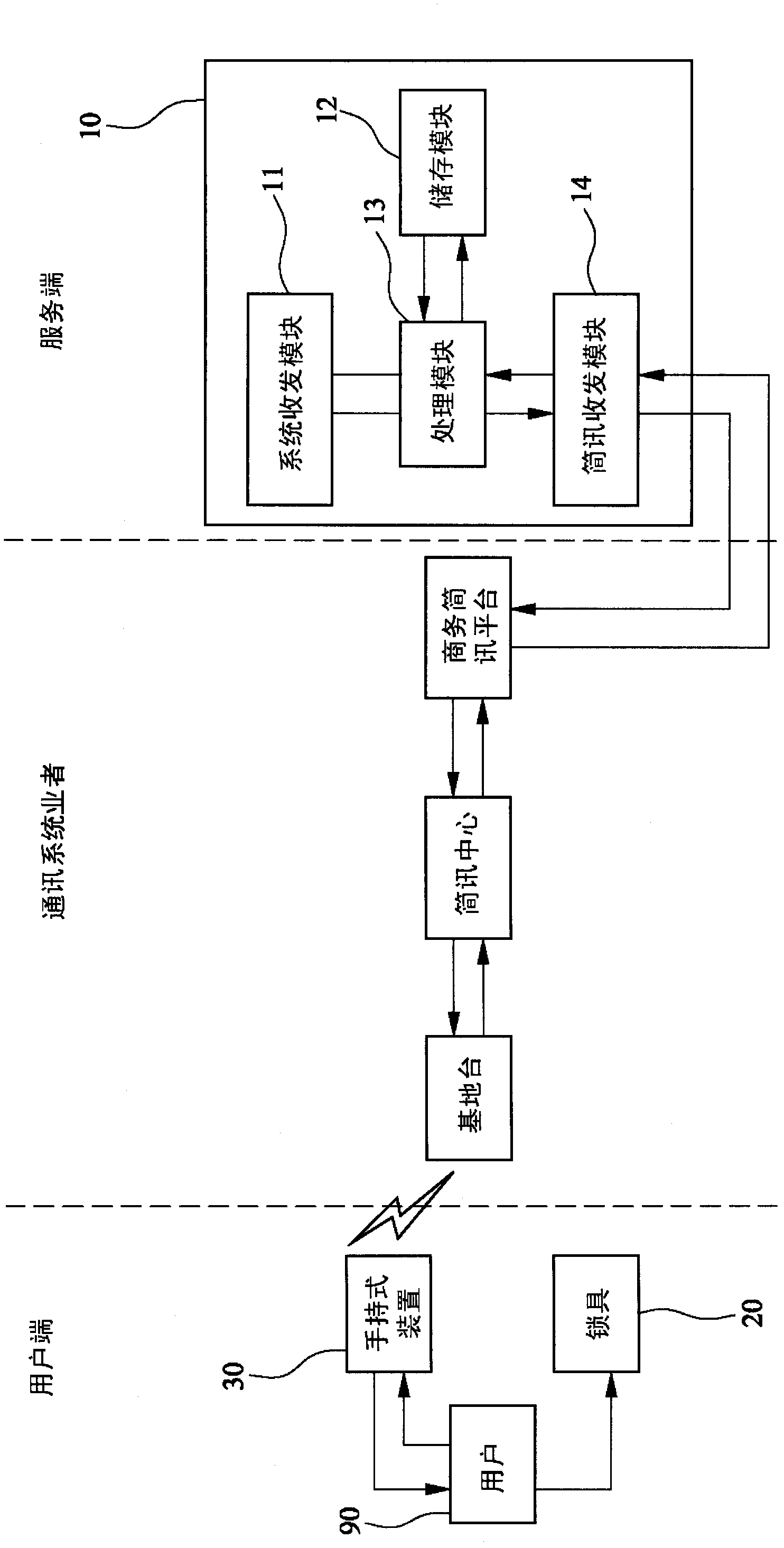
[0068] see Figure 5 , Figure 5A and Image 6 As shown, the second embodiment of the present invention is different from the above-mentioned first embodiment in that the lock 20 is further combined with a receiving module 23 on the side wall of the body 21, and the lock 20 is preset with an array password , and the management system 10 is also provided with the same array password as the password of the lock 20, and after the management system 10 is authenticated, it will choose a password from these passwords and send it to the lock 20 , the lock 20 receives and records the set of passwords, and compares them with the passwords input by the user 90 .
[0069] Also take bicycle storage as an example, please refer to Image 6 Shown, its (B) to (D) detailed step flow process, and the difference of above-mentioned first embodiment place following detailed steps:
[0070] The step of (C-2), that is, when the processing module 13 of the management system 10 cooperates with the...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com