Identity recognition method, terminal and wearable device
A technology of identity recognition and wearable devices, applied in the security field, can solve problems such as inability to log in, forget passwords, etc., and achieve the effect of improving convenience and ensuring security
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment 1
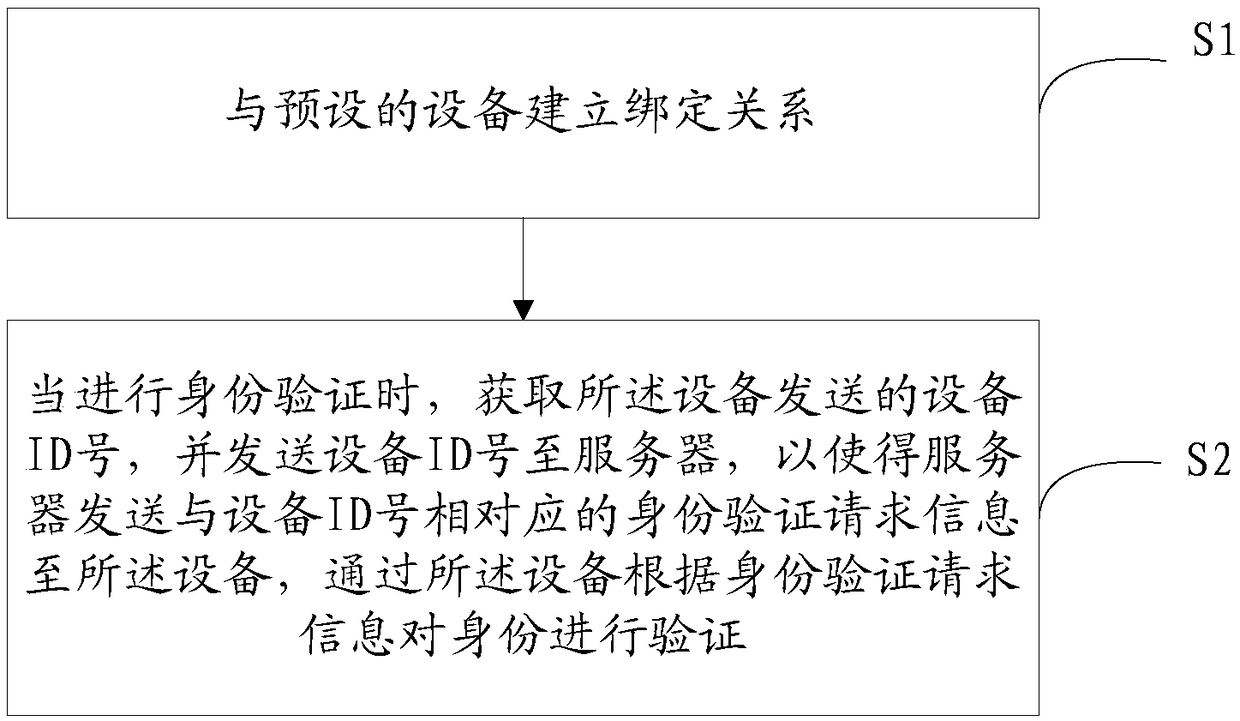
[0147] Please refer to figure 1 , Embodiment 1 of the present invention is:
[0148] The present invention provides a kind of identification method, comprises the following steps:
[0149] S1: Establish a binding relationship with a preset device;
[0150] Wherein, the S1 is specifically:
[0151] S11: Establish a communication connection with the device;
[0152] S12: Send a first request corresponding to obtaining device identity information to the device, so that the device randomly generates a first ID number and a second ID number respectively;
[0153] S13: Receive the identity information sent by the device, where the identity information includes a first ID number, a second ID number, and a device ID number;
[0154] S14: Send the identity information and the second request corresponding to establishing a binding relationship with the device to the server, so that the server can judge whether the device has completed the binding operation according to the device ID...
Embodiment 2
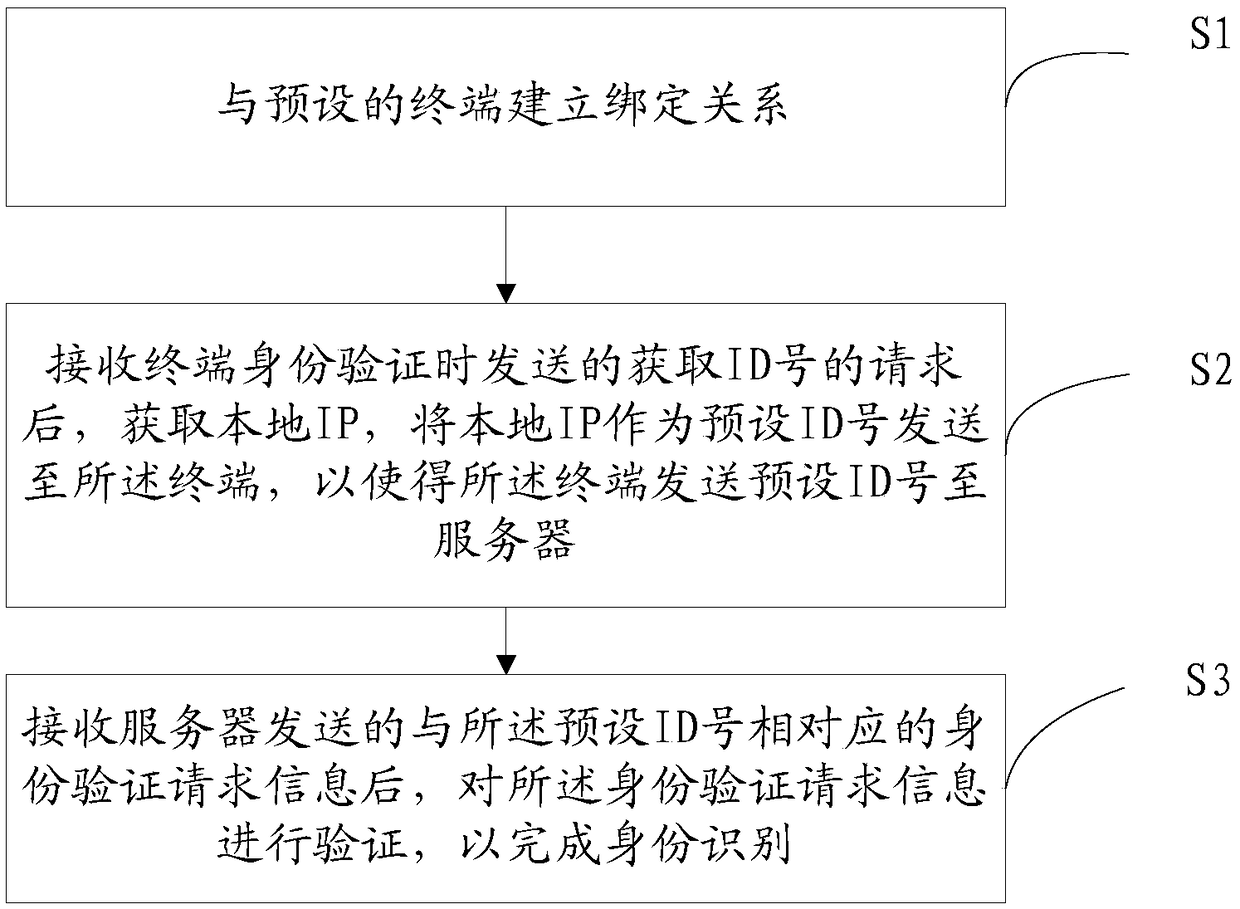
[0166] Please refer to figure 2 , the second embodiment of the present invention is:
[0167] The present invention provides a kind of identification method, comprises the following steps:
[0168] S1: Establish a binding relationship with a preset terminal;
[0169] Wherein, the S1 is specifically:
[0170] S11: Establish a communication connection with the terminal;
[0171] S12: After receiving the first request corresponding to the acquisition of device identity information sent by the terminal, randomly generate a first ID number and a second ID number respectively;
[0172] S13: Obtain a local IP as a preset ID number; generate identity information according to the first ID number, the second ID number, and the preset ID number;
[0173] S14: Send the identity information to the terminal, so that the terminal sends the identity information and the second request corresponding to the binding operation to the server, so that the server can judge the preset ID number a...
Embodiment 3
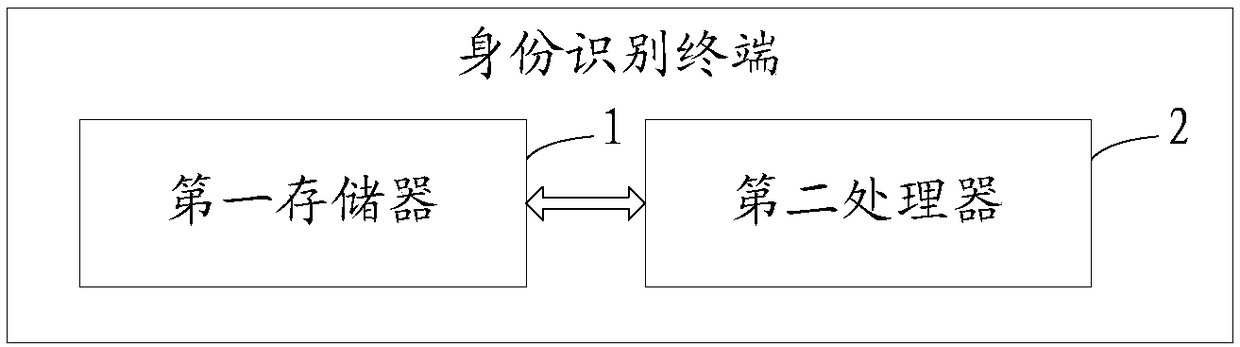
[0193] Please refer to image 3 , Embodiment three of the present invention is:
[0194] The present invention provides an identification terminal, comprising a first memory 1, a first processor 2 and a computer program stored on the first memory 1 and operable on the first processor 2, the first processor 2 The following steps are implemented when the computer program is executed:
[0195] S1: Establish a binding relationship with a preset device;
[0196] Wherein, the S1 is specifically:
[0197] S11: Establish a communication connection with the device;
[0198]S12: Send a first request corresponding to obtaining device identity information to the device, so that the device randomly generates a first ID number and a second ID number respectively;
[0199] S13: Receive the identity information sent by the device, where the identity information includes a first ID number, a second ID number, and a device ID number;
[0200] S14: Send the identity information and the seco...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com