Identity verification method and device
An identity verification method and identity technology, which is applied in the field of computer networks, can solve problems such as low security, cracking, and poor anti-cracking ability of verification code pictures, and achieve the effect of high security, increased difficulty, and not easy to be cracked
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
no. 1 example
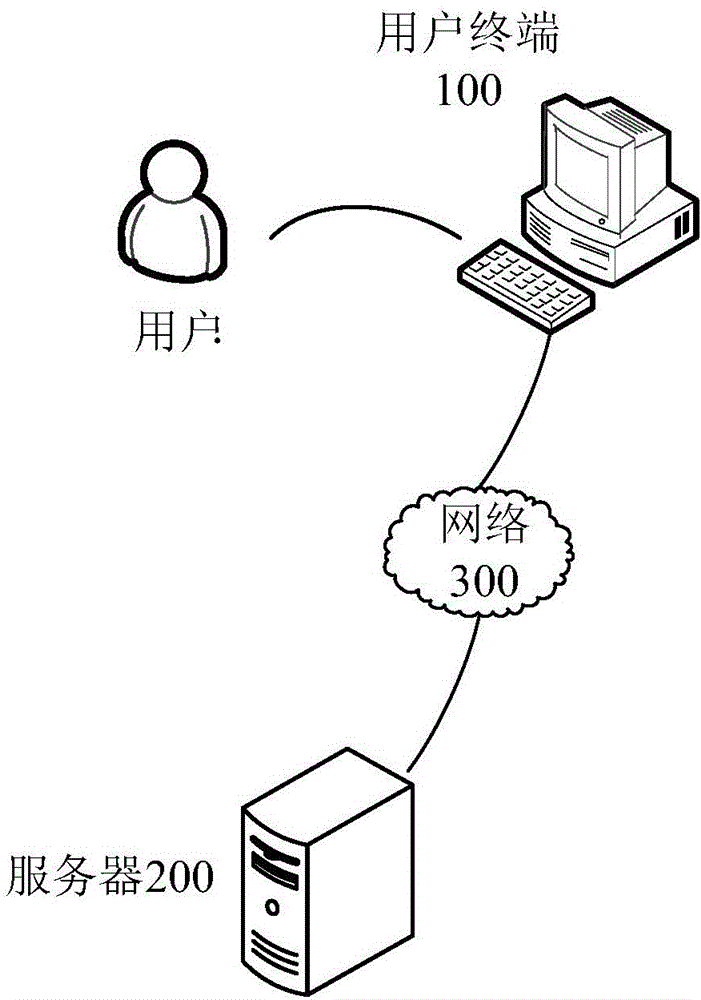
[0049] see Figure 5 , shows a flow chart of the identity verification method provided by the first embodiment of the present invention. to combine figure 2 , this embodiment describes the processing flow of the server, and the identity verification method provided by this embodiment includes the following steps:
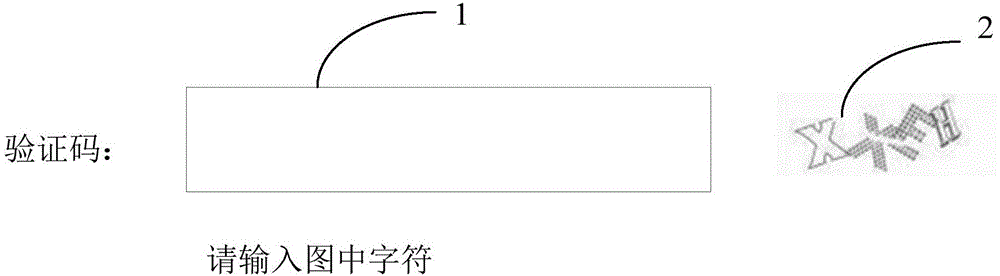
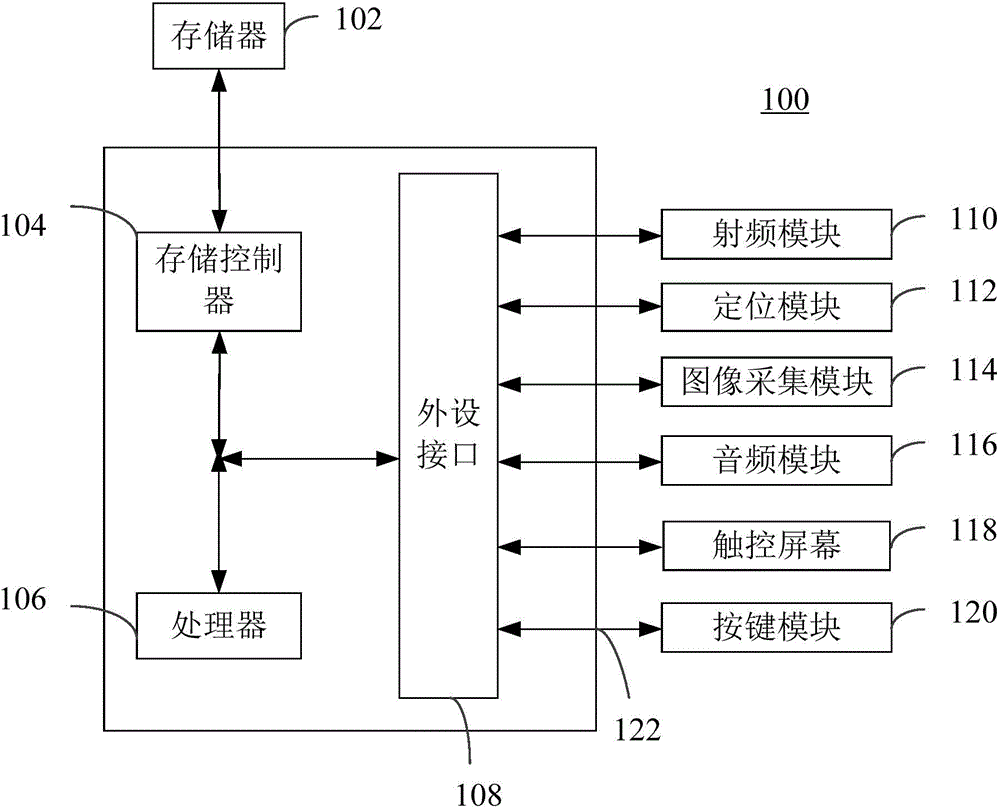
[0050] Step S11, the server receives a verification code pull request sent by a user terminal, and the verification code pull request carries account information of the user terminal.
[0051] When the user terminal detects that the user uses the terminal to initiate transactions and other sensitive operations that require identity verification, or logs in to an application too many times within a certain period of time, or logs in to an application in a different place, or enters an incorrect password for an application too many times, etc. When it happens, it can be determined that the identity verification request is triggered, and the user terminal can send a...
no. 2 example
[0072] see Figure 7 , shows a flow chart of the identity verification method provided by the second embodiment of the present invention. combine figure 2 , this embodiment describes the processing flow of the user terminal, and the identity verification method in this embodiment includes:
[0073] In step S21, the user terminal sends a verification code pull request to the server, and the verification code pull request carries account information of the user terminal.
[0074] Further, before step S21, the user terminal may also send a preset theme corresponding to the account information to the server for storage, wherein the preset theme is set by the user who created the user terminal account. The user terminal may also receive and display some of the pictures in the picture database that match the preset theme returned by the server, so that the user who sets the preset theme is familiar with these pictures. For a specific method, reference may be made to relevant con...
no. 3 example
[0081] see Figure 8 , shows a flow chart of the identity verification method provided by the third embodiment of the present invention. combine figure 2 , this embodiment describes the interaction processing flow between the user terminal and the server. The authentication methods in this embodiment may include:
[0082] In step S301, the user terminal receives account information input by the user.
[0083] Step S302, the user terminal reports the account information and the basic information of the user terminal to the server.
[0084] Step S303, the server stores the account information as the account information of the user terminal.
[0085] Step S304, the server returns multiple topics to the user terminal.
[0086] Step S305, the user terminal displays multiple themes to the user.
[0087] Step S306, the user terminal receives the theme selected by the user.
[0088] Step S307, the user terminal sends the theme selected by the user as a preset theme correspondi...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com