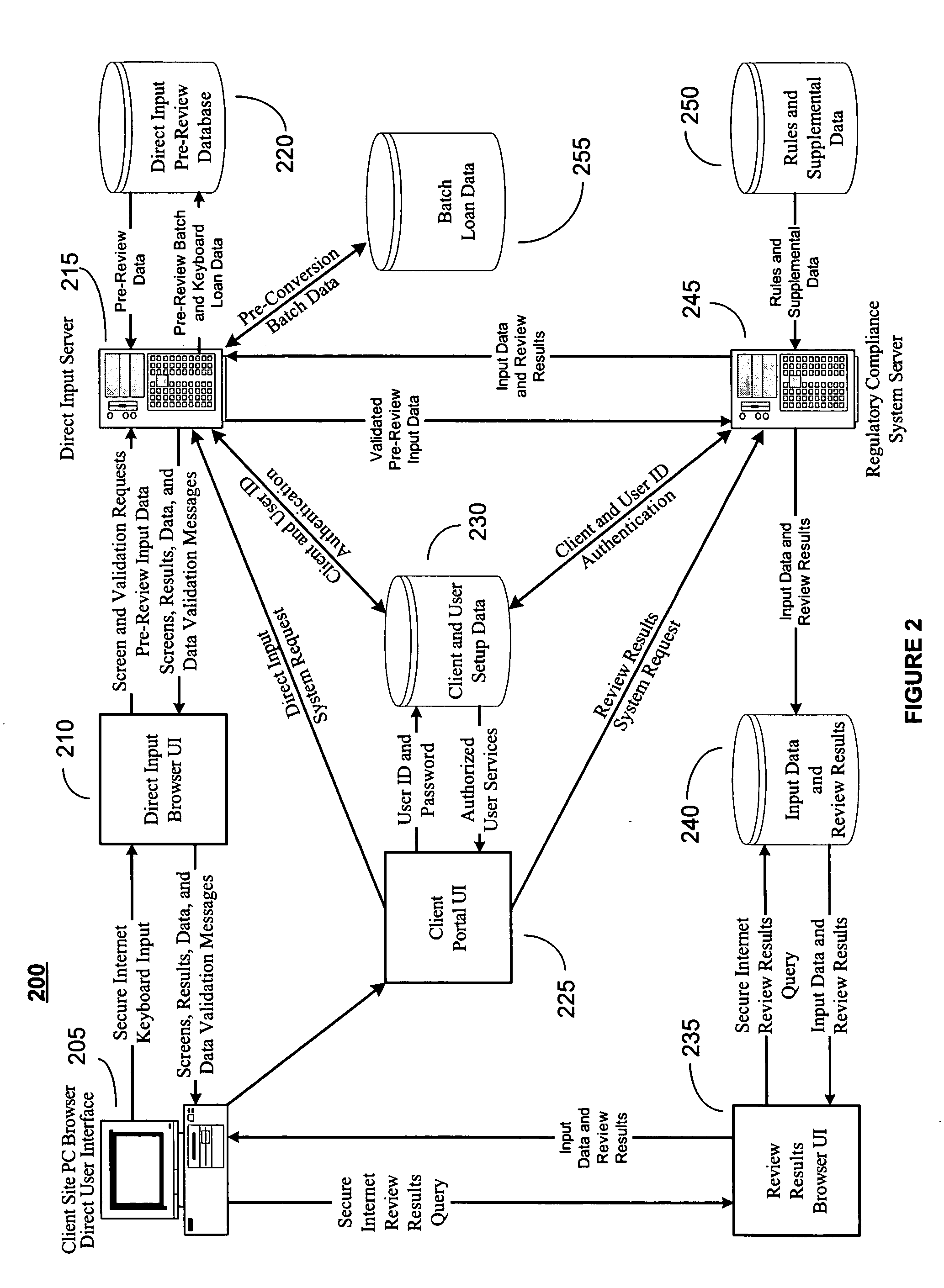
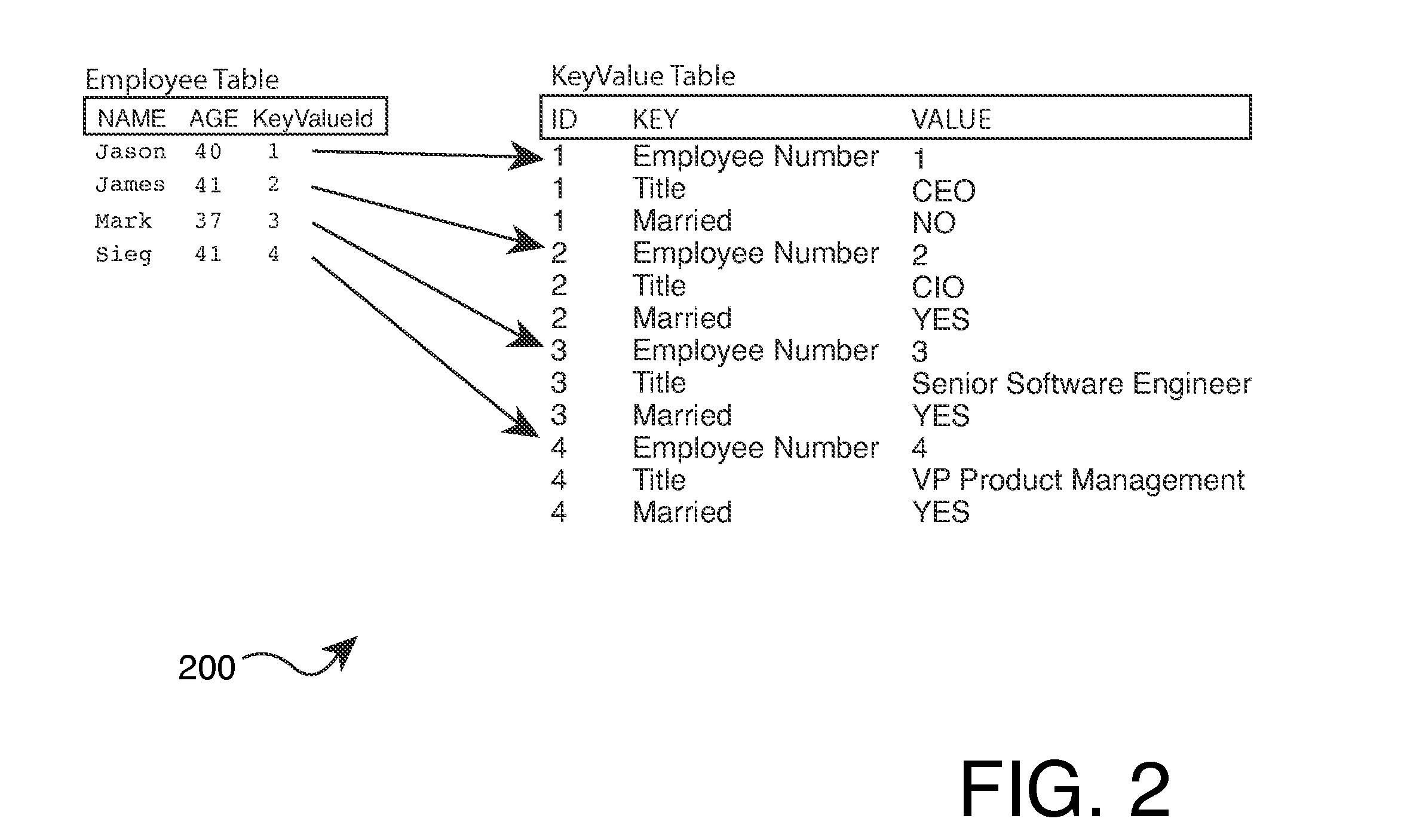
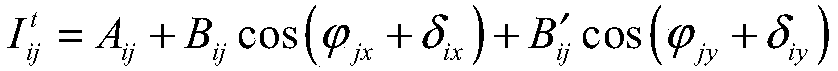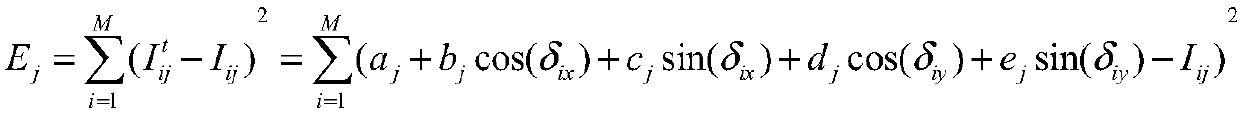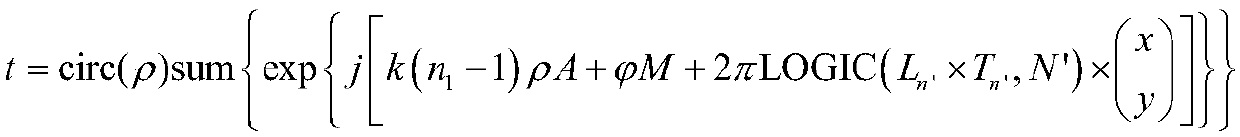Patents
Literature
61 results about "Computer number format" patented technology
Efficacy Topic
Property
Owner
Technical Advancement
Application Domain
Technology Topic
Technology Field Word
Patent Country/Region
Patent Type
Patent Status
Application Year
Inventor
A computer number format is the internal representation of numeric values in digital computer and calculator hardware and software. Normally, numeric values are stored as groupings of bits, named for the number of bits that compose them. The encoding between numerical values and bit patterns is chosen for convenience of the operation of the computer; the bit format used by the computer's instruction set generally requires conversion for external use such as printing and display. Different types of processors may have different internal representations of numerical values. Different conventions are used for integer and real numbers. Most calculations are carried out with number formats that fit into a processor register, but some software systems allow representation of arbitrarily large numbers using multiple words of memory.
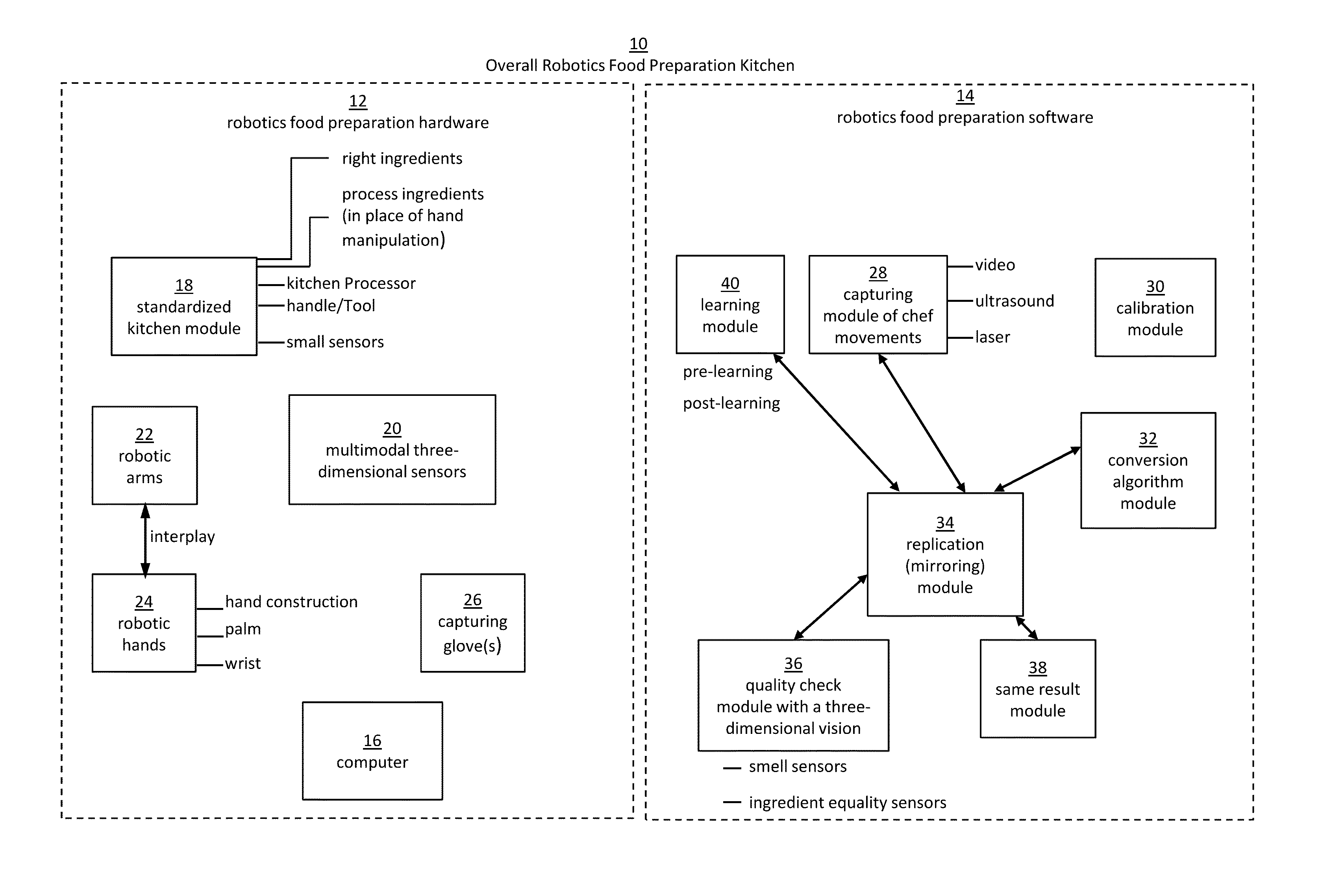
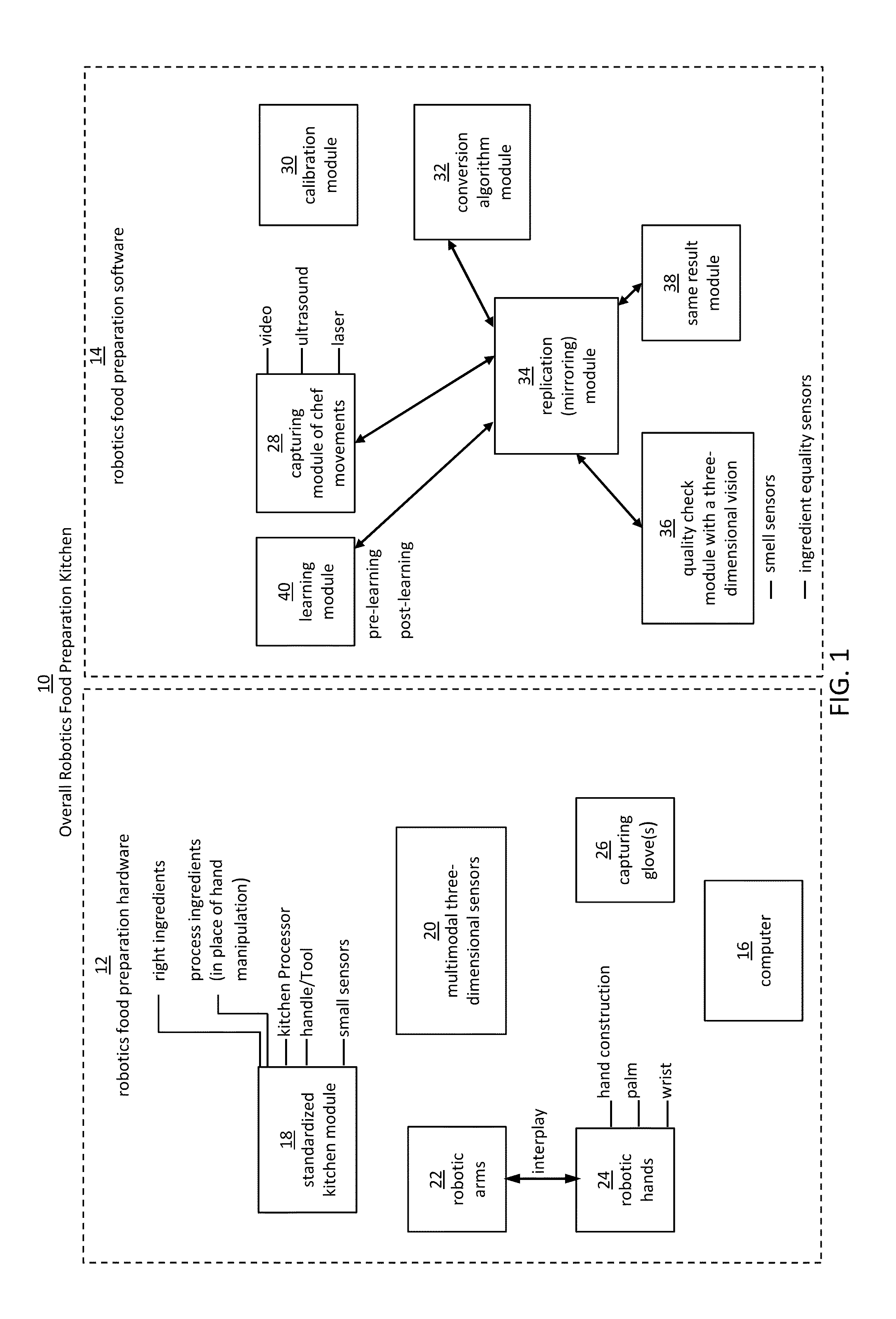
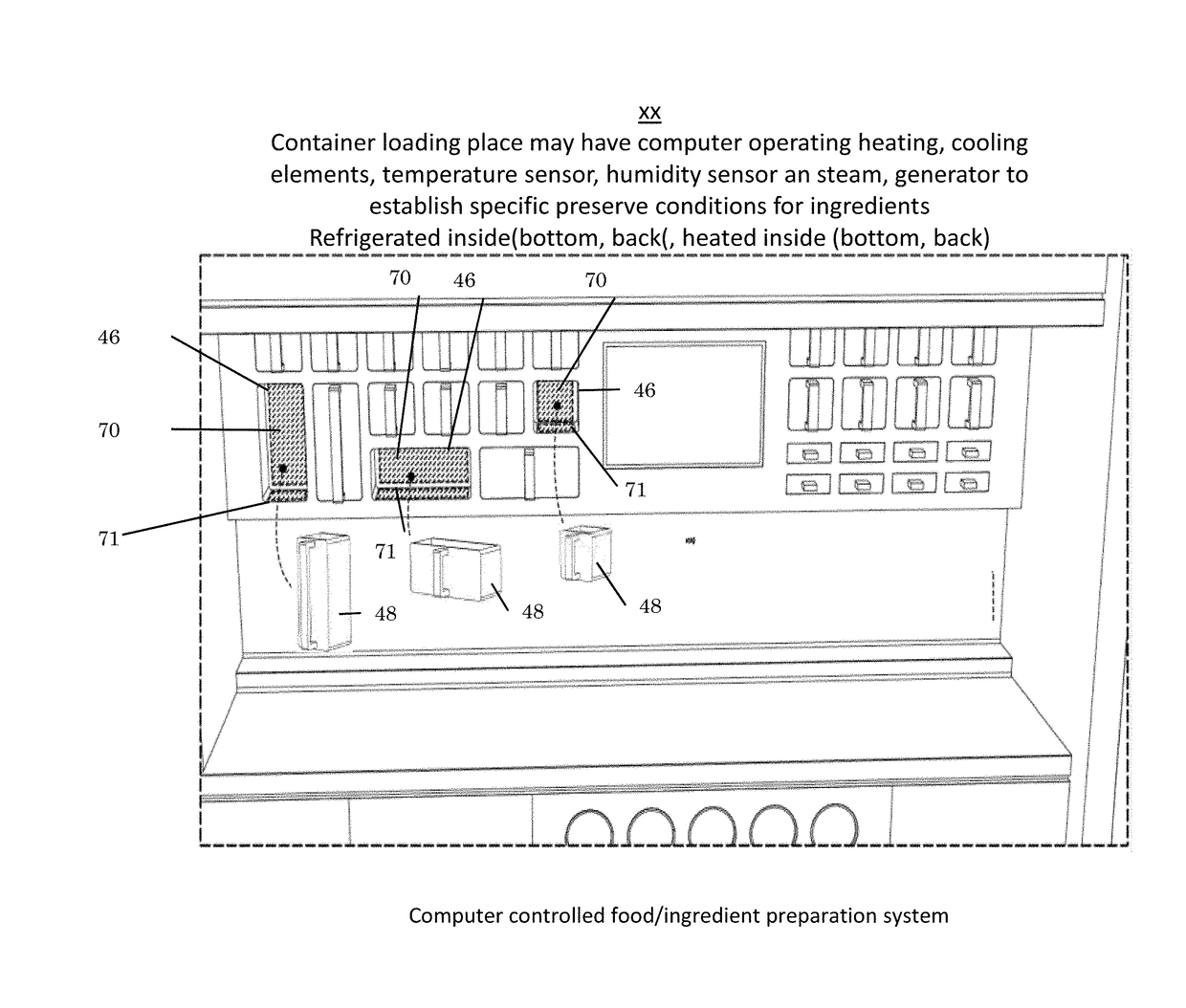
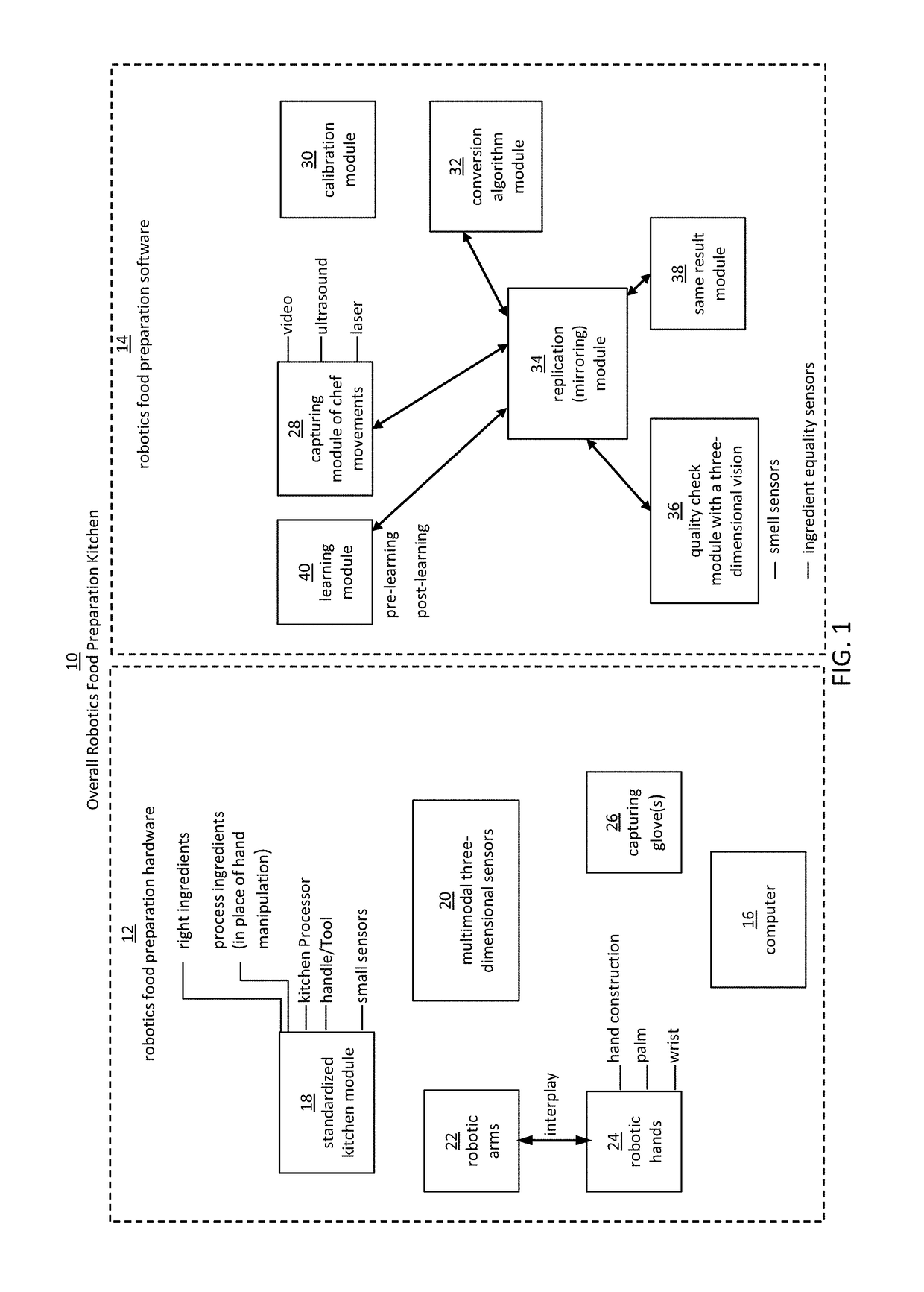
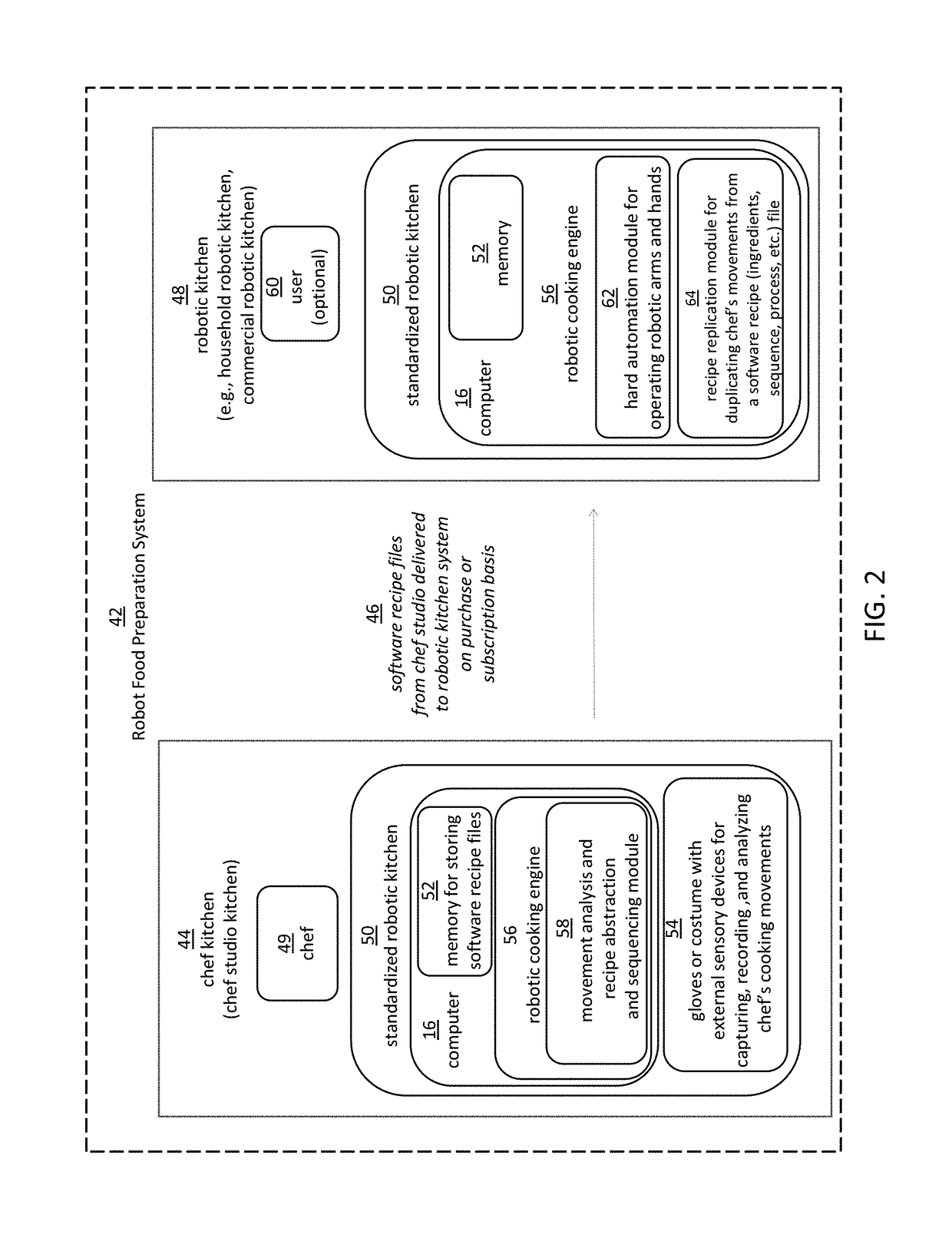
Robotic manipulation methods and systems for executing a domain-specific application in an instrumented environment with electronic minimanipulation libraries
ActiveUS20160059412A1Deal with variationProgramme-controlled manipulatorComputer controlHumanoid robot naoComputer number format
Embodiments of the present disclosure are directed to the technical features relating to the ability of being able to create complex robotic humanoid movements, actions, and interactions with tools and the instrumented environment by automatically building movements for the humanoid; actions and behaviors of the humanoid based on a set of computer-encoded robotic movement and action primitives. The primitives are defined by motions / actions of articulated degrees of freedom that range in complexity from simple to complex, and which can be combined in any form in serial / parallel fashion. These motion-primitives are termed to be minimanipulations and each has a clear time-indexed command input-structure and output behavior / performance profile that is intended to achieve a certain function. Minimanipulations comprise a new way of creating a general programmable-by-example platform for humanoid robots. One or more minimanipulation electronic libraries provide a large suite of higher-level sensing-and-execution sequences that are common building blocks for complex tasks, such as cooking, taking care of the infirm, or other tasks performed by the next generation of humanoid robots.
Owner:MBL LTD
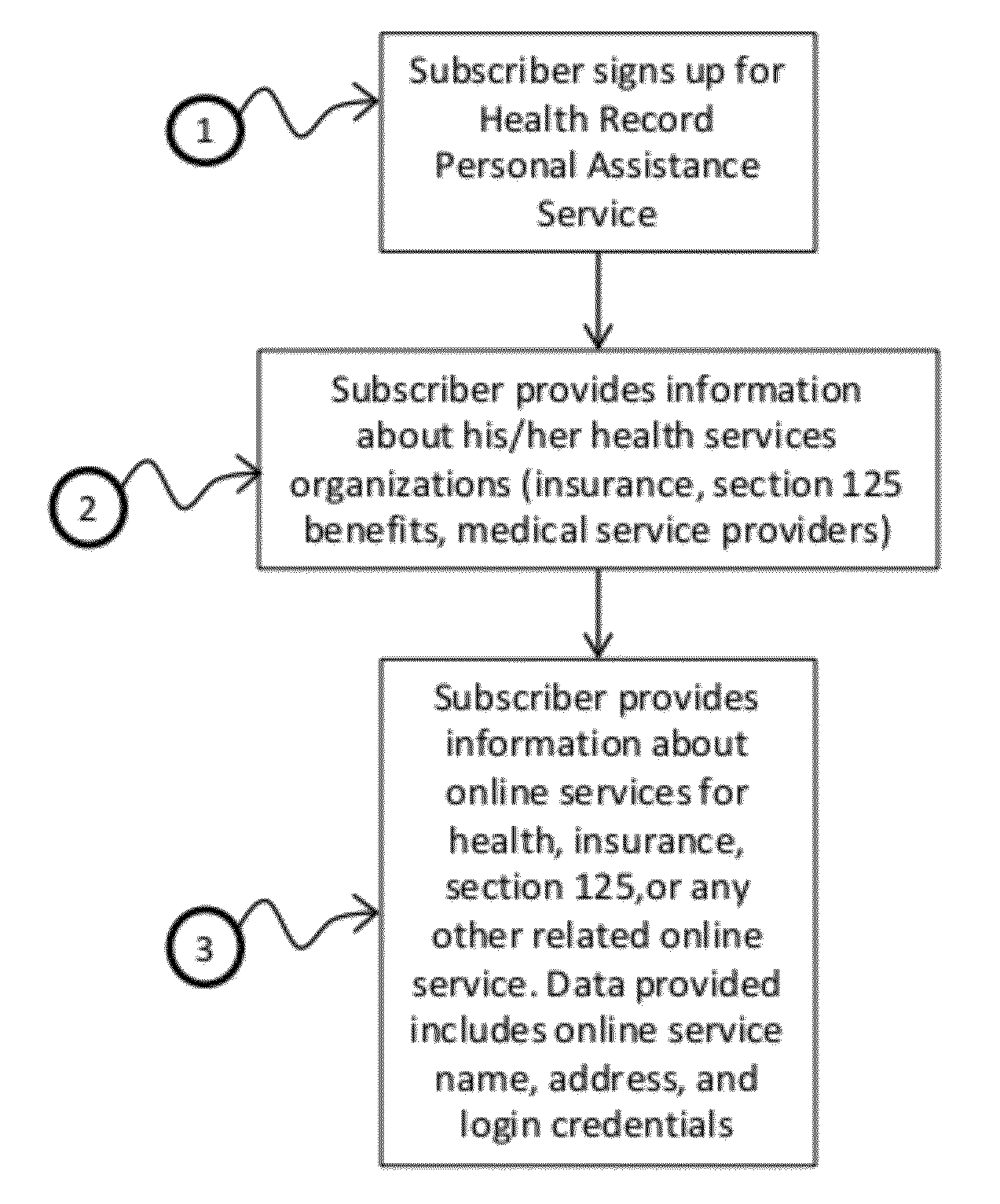
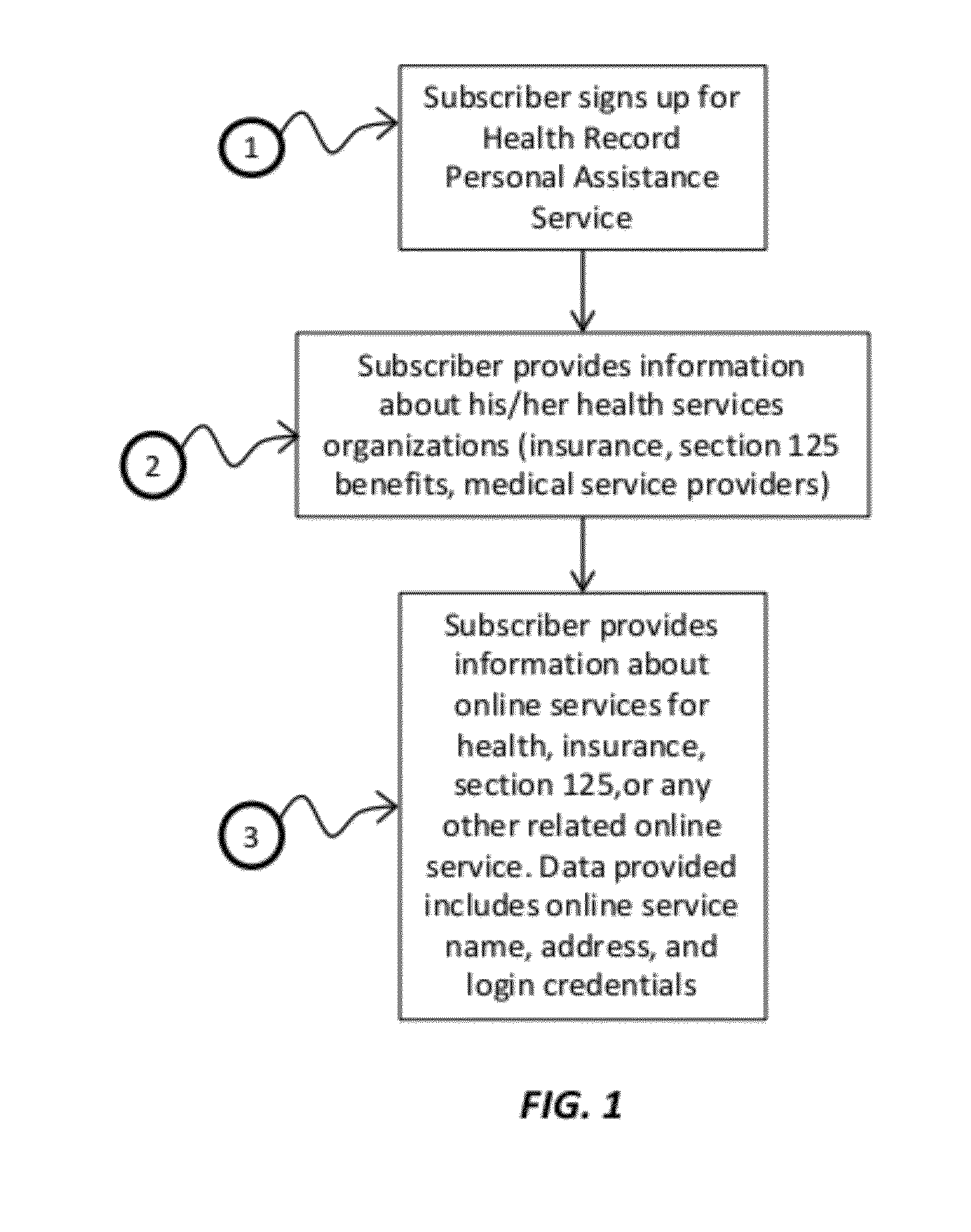
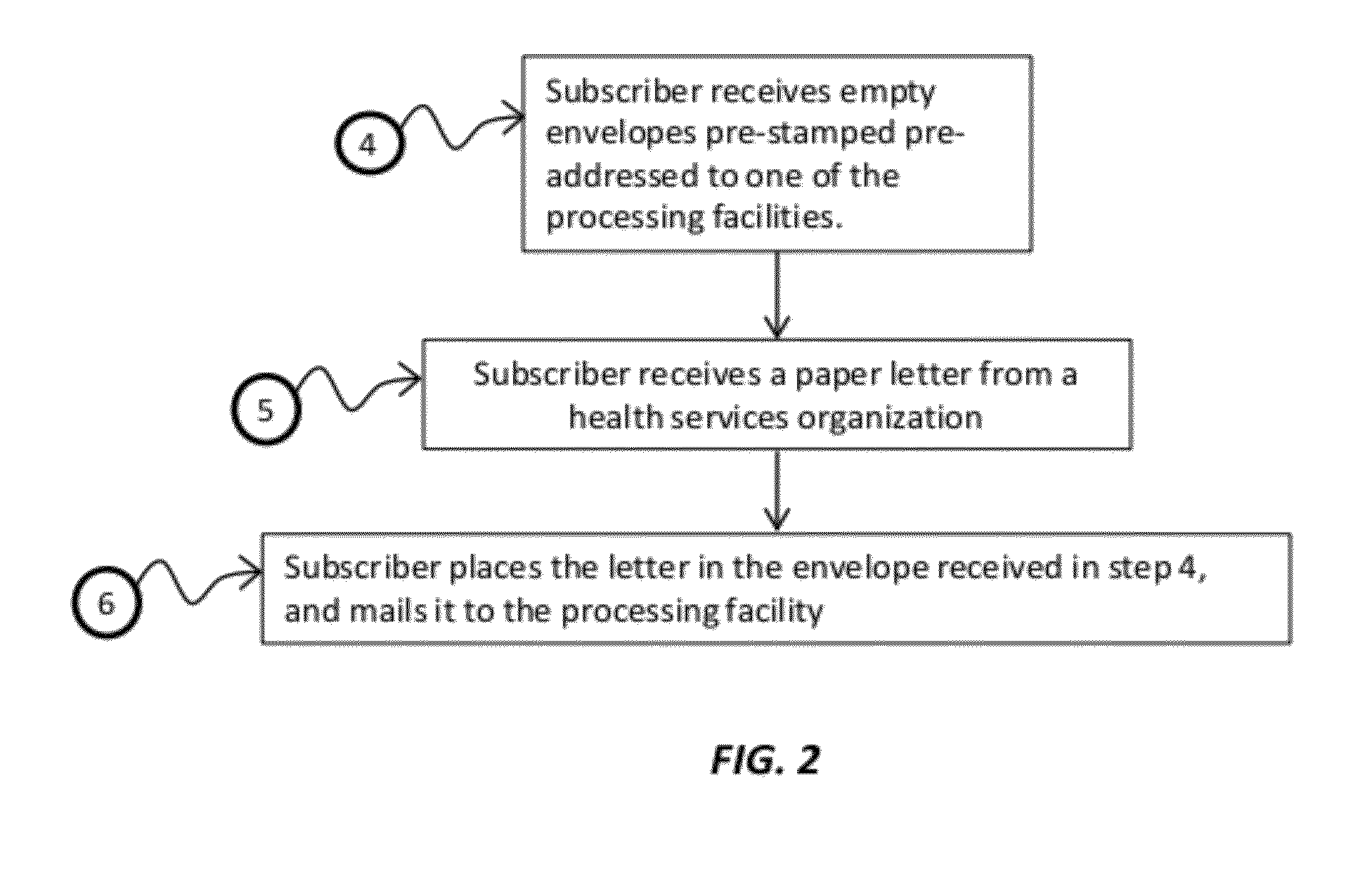
System and method of automated data analysis for implementing health records personal assistant with automated correlation of medical services to insurance and tax benefits for improved personal health cost management
InactiveUS20120185275A1Simplify comprehensionFraud can be detectedFinanceDigital computer detailsData fieldHealth benefits
Systems, methods, and computer-coded software instructions are provided for automated data analysis using graph topology techniques in a connections-mapping process to automatically identify interrelationships between various data fields in a system or body of data followed by statistical pattern analysis and machine learning techniques applied on the graphs (e.g., hidden networks) identified to improve analyses (e.g., automated analysis of medical bills and health insurance documents). Automated conversion of paper-based medical and insurance billing records to electronic data is provided, along with automatic correlation of medical services data to insurance plan policies and tax regulations for health benefits to detect errors or fraud, and to project health insurance plans for various subscribers.
Owner:LOGHMANI MASOUD
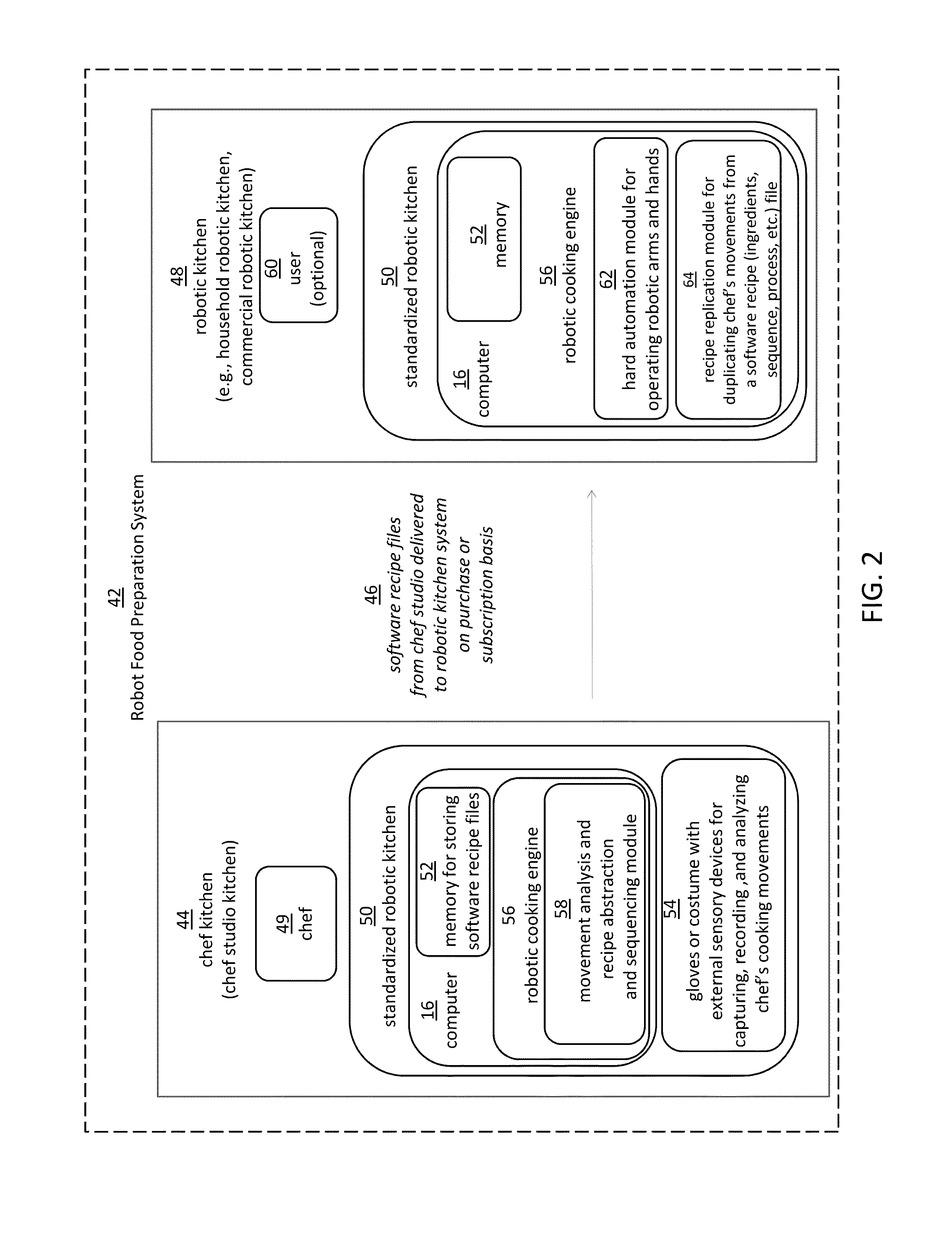
Robotic manipulation methods and systems for executing a domain-specific application in an instrumented environment with containers and electronic minimanipulation libraries
PendingUS20170348854A1Good orientationEasy to moveProgramme controlProgramme-controlled manipulatorComputer number formatDegrees of freedom
This disclosure discloses various technical features for creating robotic humanoid movements, actions, and interactions with tools and the instrumented environment by automatically building movements for the humanoid; actions and behaviors of the humanoid based on a set of computer-encoded robotic movement and action primitives. The primitives are defined by motions / actions of articulated degrees of freedom that range in complexity from simple to complex, and which can be combined in any form in serial / parallel fashion. These motion-primitives are termed to be minimanipulations and each has a clear time-indexed command input-structure and output behavior / performance profile that is intended to achieve a certain function. Minimanipulations comprise a new way of creating a programmable-by-example platform for robots. The minimanipulation electronic libraries provide a large suite of higher-level sensing-and-execution sequences that are common building blocks for complex tasks, such as cooking, taking care of the infirm, or other tasks performed by robots.
Owner:MBL LTD
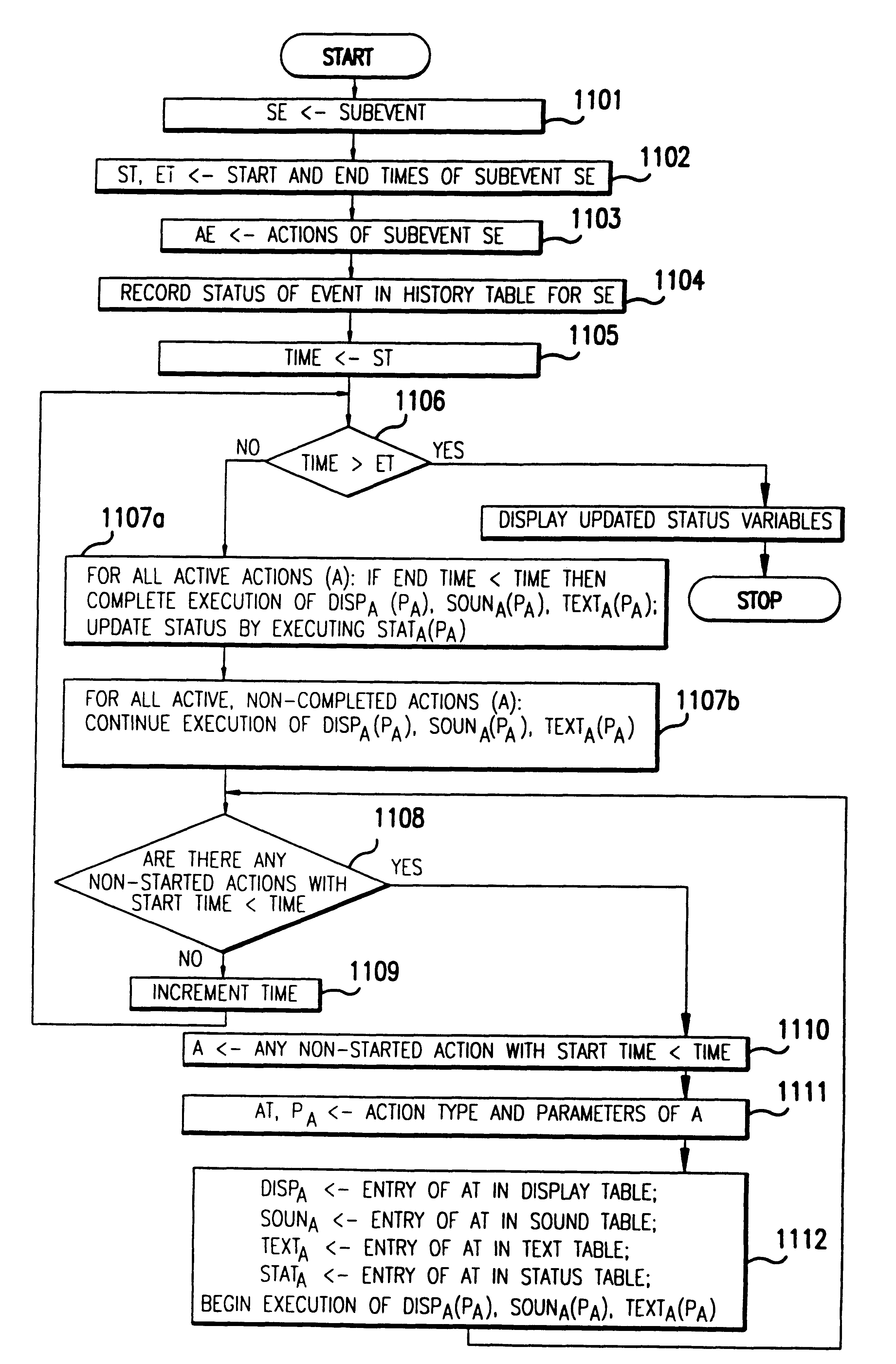
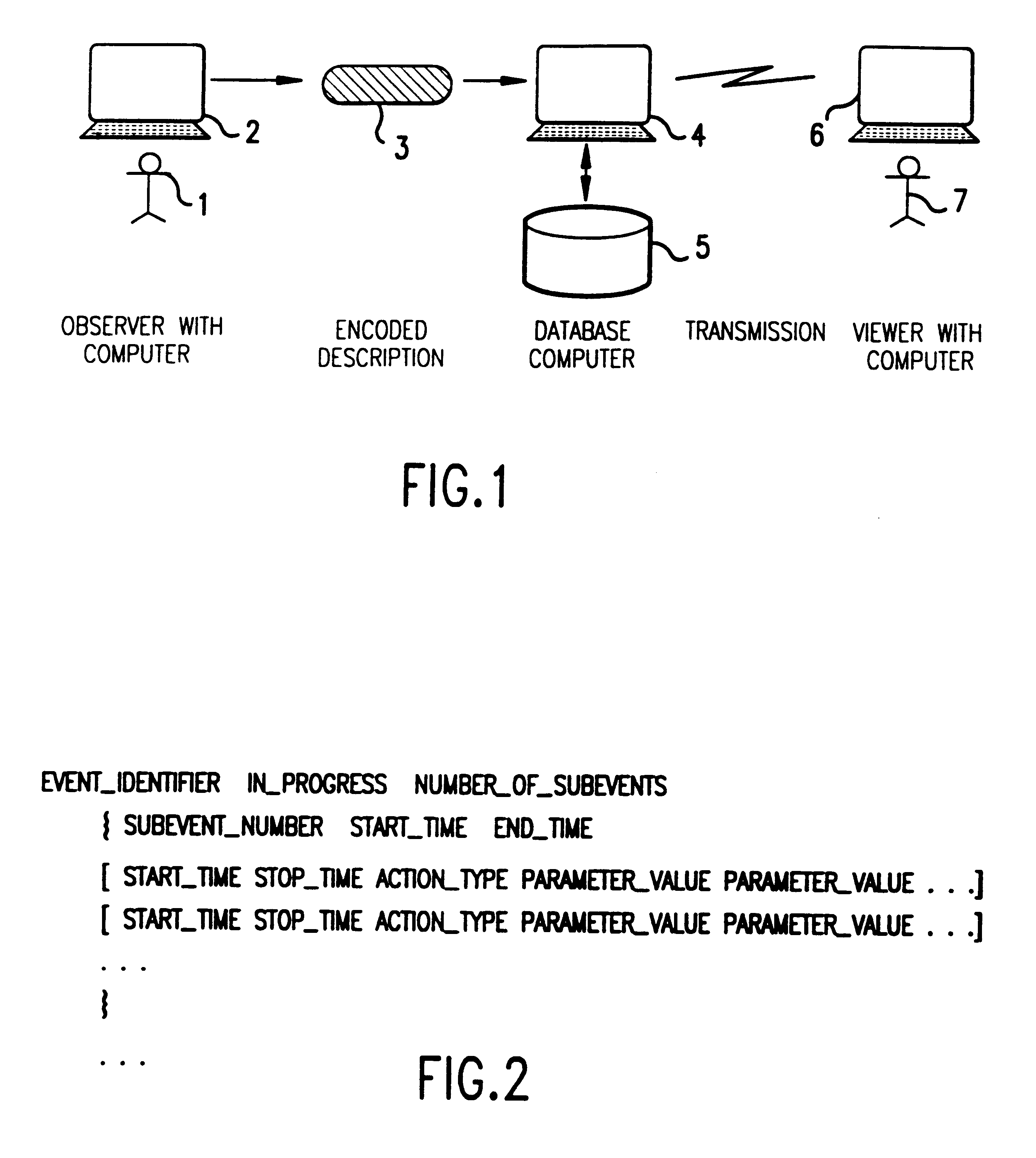
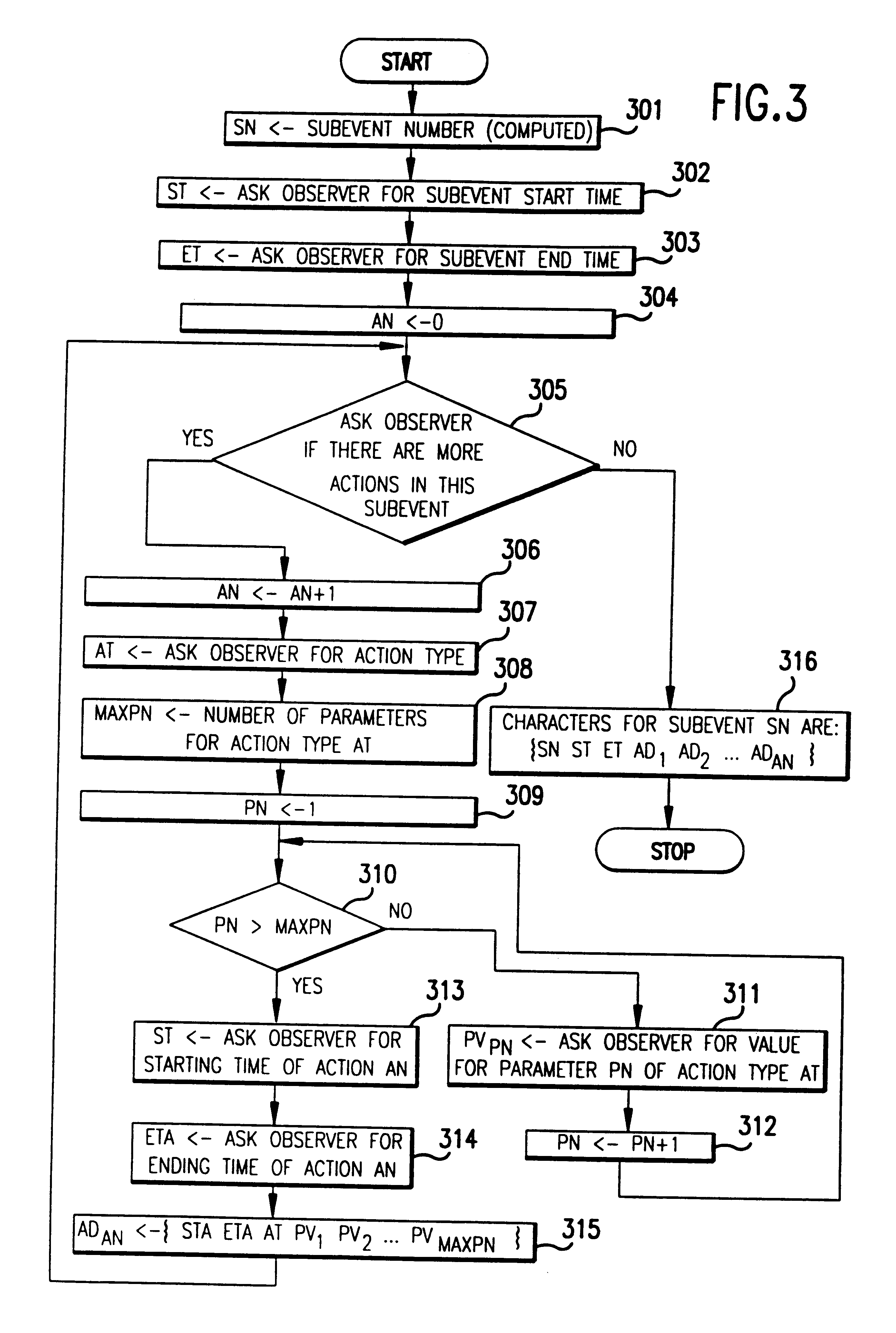
Method and apparatus for broadcasting live events to another location and producing a computer simulation of the events at that location
InactiveUS6204862B1Specific information broadcast systemsAnalogue secracy/subscription systemsComputer graphics (images)Computer number format
A live event may be broadcasted by producing a computer coded description of the sub-events that constitute the event. The coded description is stored in a centralized computer data base and the information thus stored is accessible by a viewer's computer. That viewer computer then produces a computer simulation of the live event using the coded description.
Owner:DDB TECH L L C
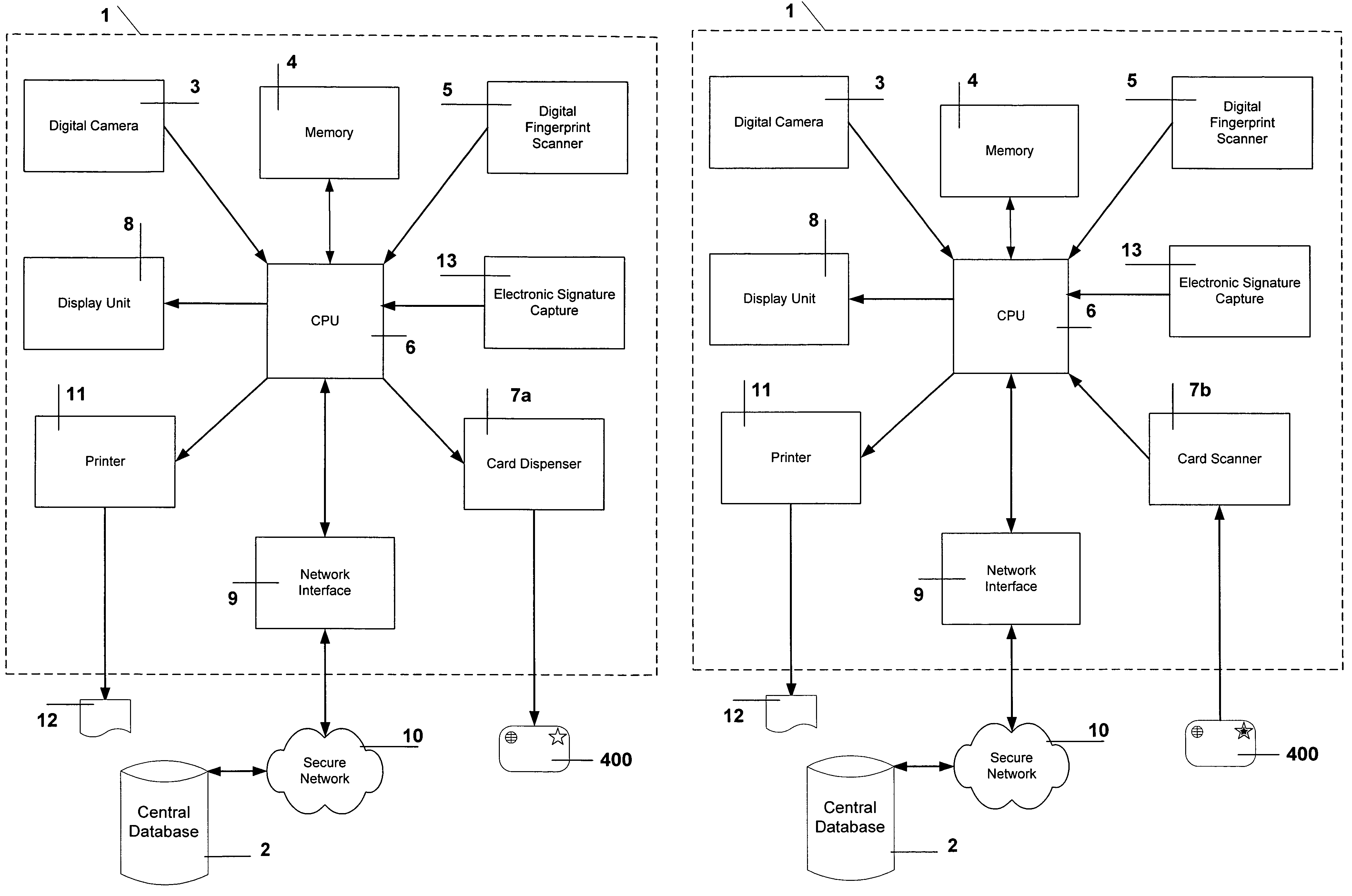
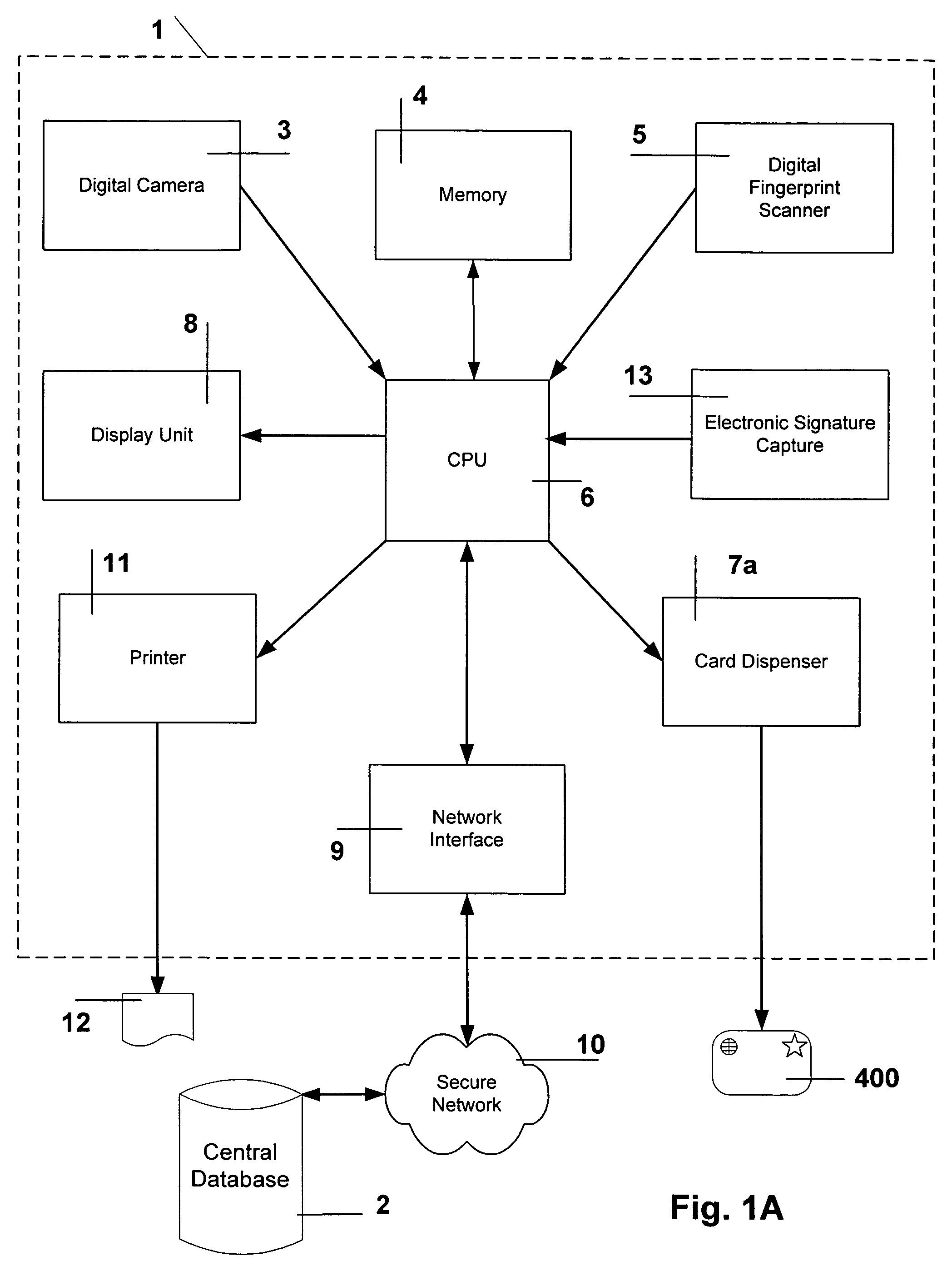
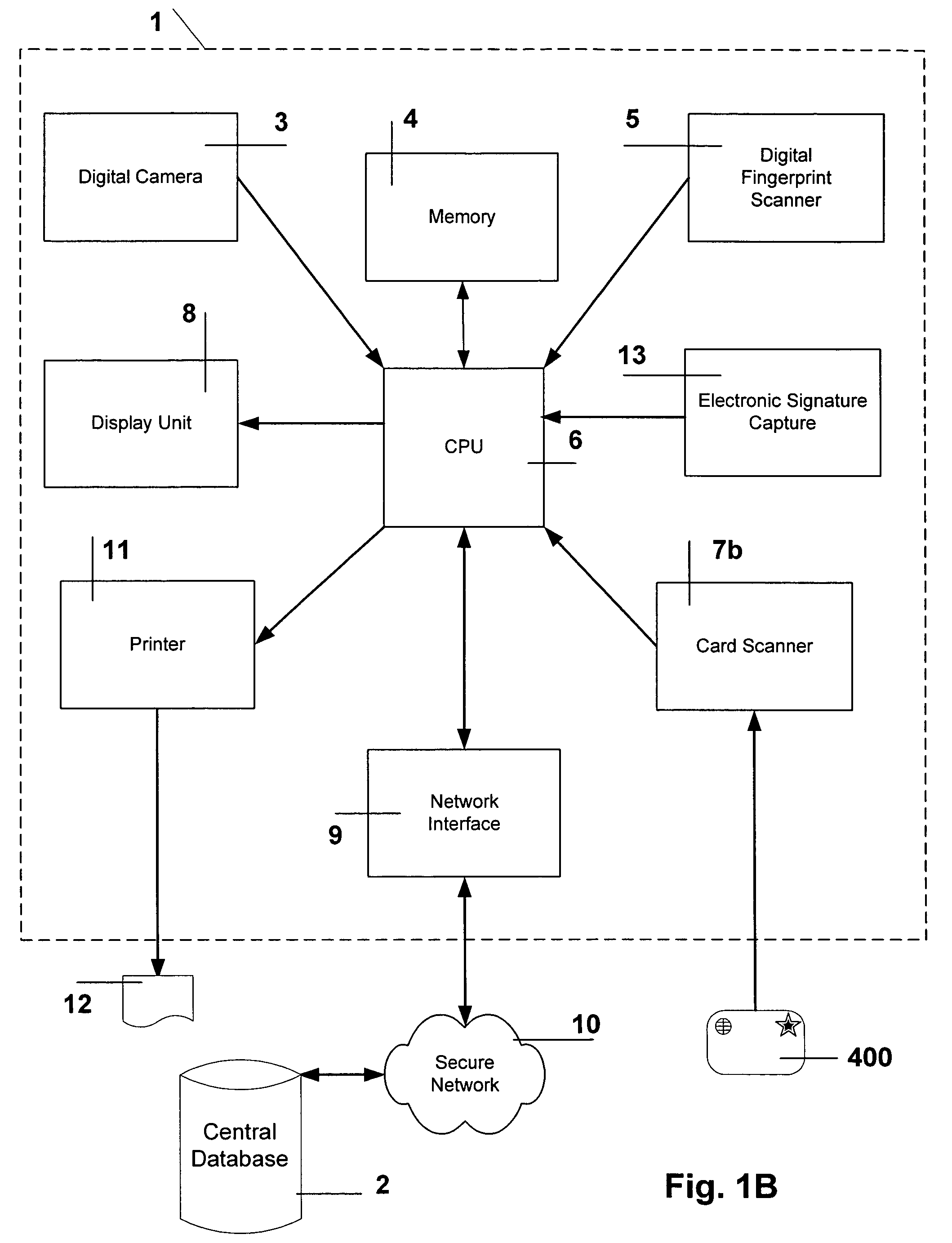
Method and system to issue an electronic visa of a foreign visitor at a country's foreign consular premises
InactiveUS7118027B2Reduce fraud and other misuse.Payment architectureSecret communicationComputer hardwareComputer number format
This invention integrates with a country's customs and immigration system to issue an electronic visitor's visa, and to validate periodically, electronically a visitor's visa within the country's borders. A computer-encoded visa card is created and issued to the visitor at the country's overseas consulate. Pertinent visa application information is embedded in the issued card. Cryptographic technology is used with the card to maintain privacy, as well as to reduce fraud and other misuse. The card is used as the visitor's official identification document whilst in the country. During the visitor's stay, at specified intervals, the visitor registers with self-service kiosks, which are placed at various locations within the country. The kiosks are securely integrated with the customs and immigration database.
Owner:SUSN LESTER
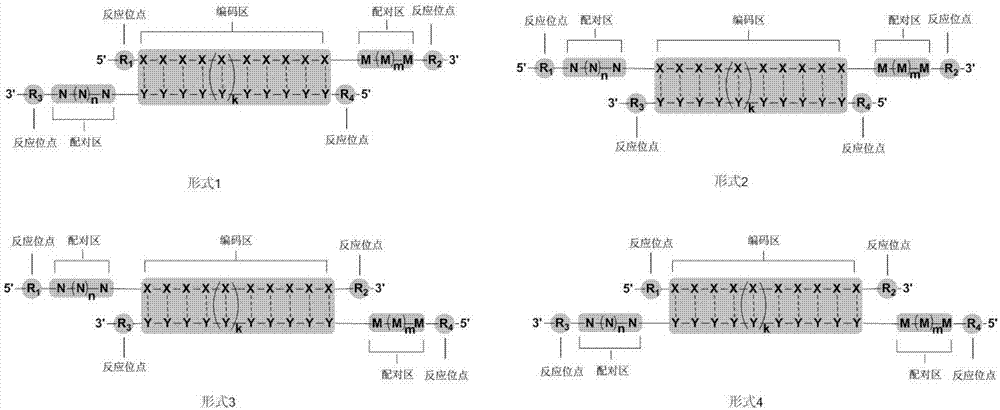
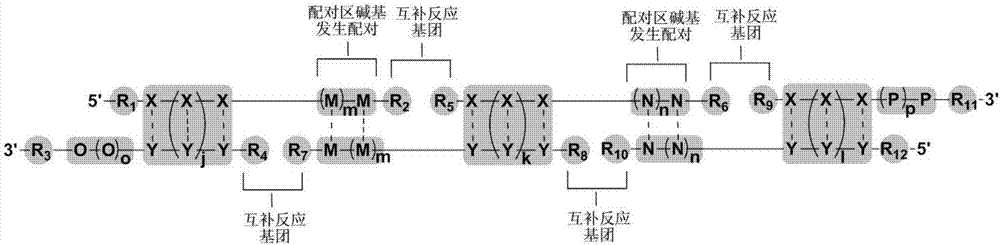
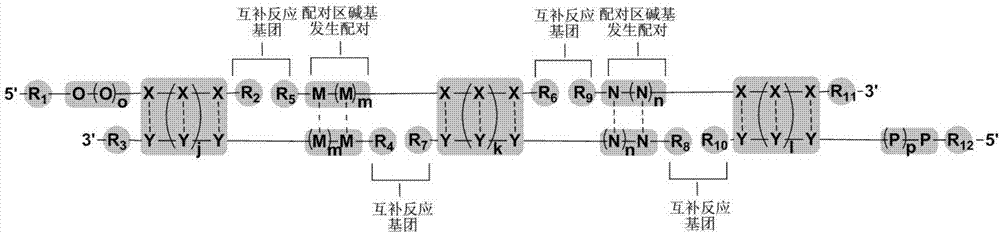
Computer coding method for double-stranded nucleotides of DNA coding compound library
ActiveCN107958139AEasy to operateSequence analysisSpecial data processing applicationsNucleotideScreening method
The invention relates to a computer coding method for double-stranded nucleotides of a DNA coding compound library and different combinations of nucleotide double-stranded sets obtained by the method.The computer coding method comprises the steps of performing computer coding on coding regions of the double-stranded nucleotides, performing computer coding on pairing regions of the double-strandednucleotides, combining the coding regions and the pairing regions of the double-stranded nucleotides to obtain double-stranded nucleotides having protrusions at the 5' or 3' ends, screening the combined nucleotide double-stranded sets, and modifying and linking both ends of n cycle of nucleotide double-stranded sets. The method is a computer coding method for constructing the DNA coding compoundlibrary, which is highly efficient, simple in operation and capable of rapidly obtaining a sufficient number of partial base sequence complementary pairings and having protrusion base sequences, and has a wide range of application prospects in constructing the DNA coding compound library.
Owner:上海药明康德新药开发有限公司
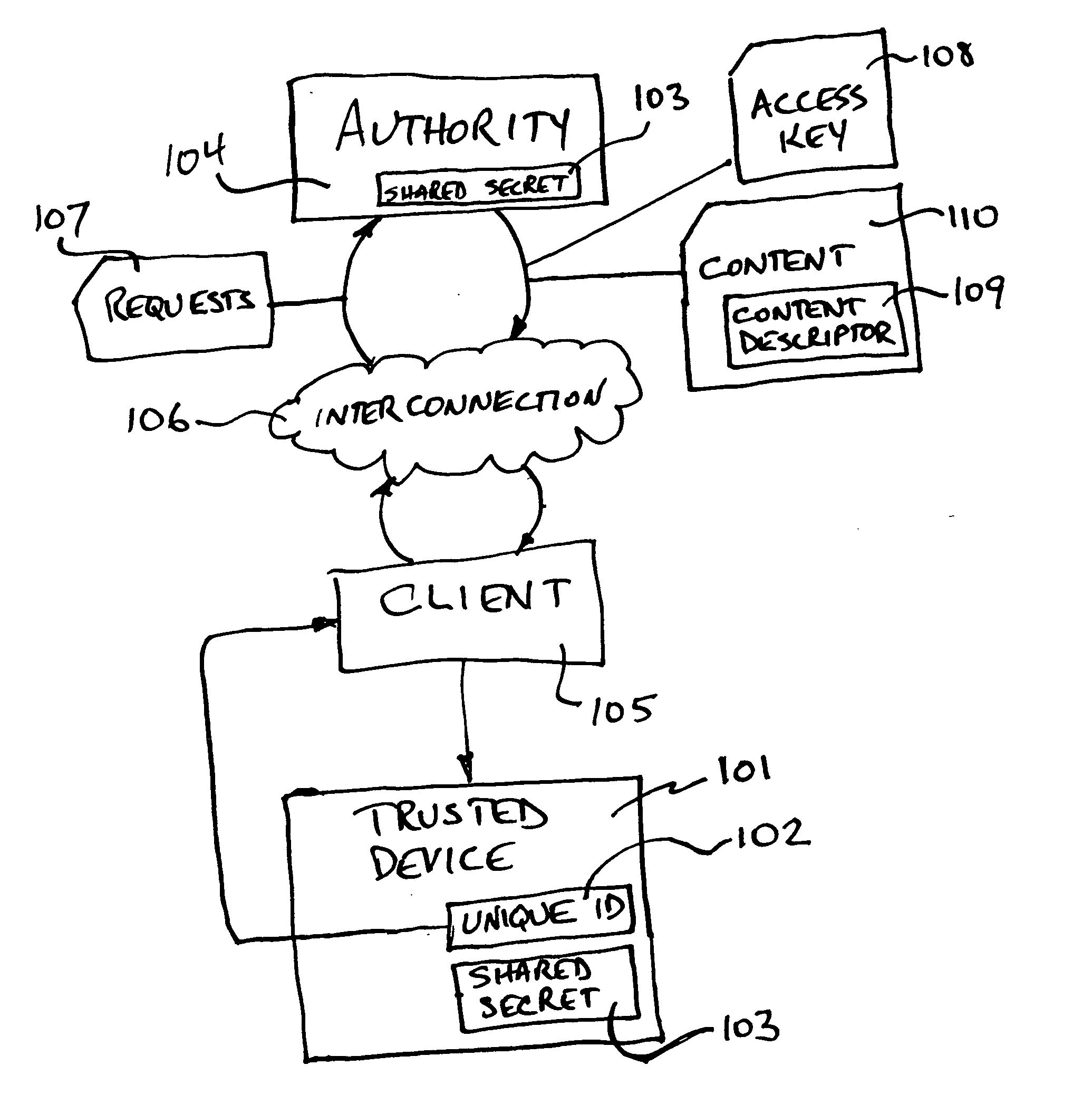
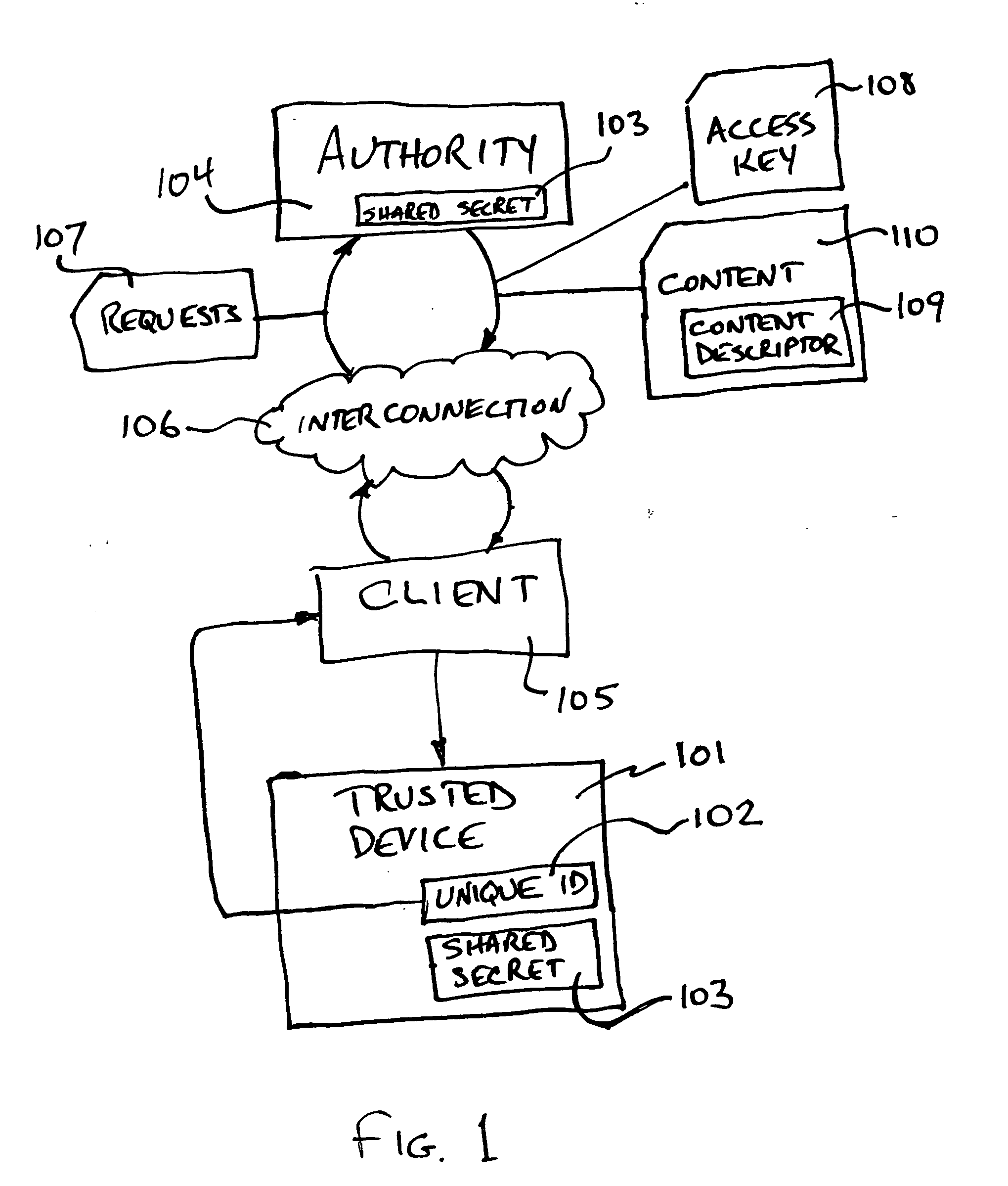
Method and apparatus for controlling access to downloadable content
InactiveUS20060064759A1Digital data processing detailsAnalogue secracy/subscription systemsComputer number formatClient-side
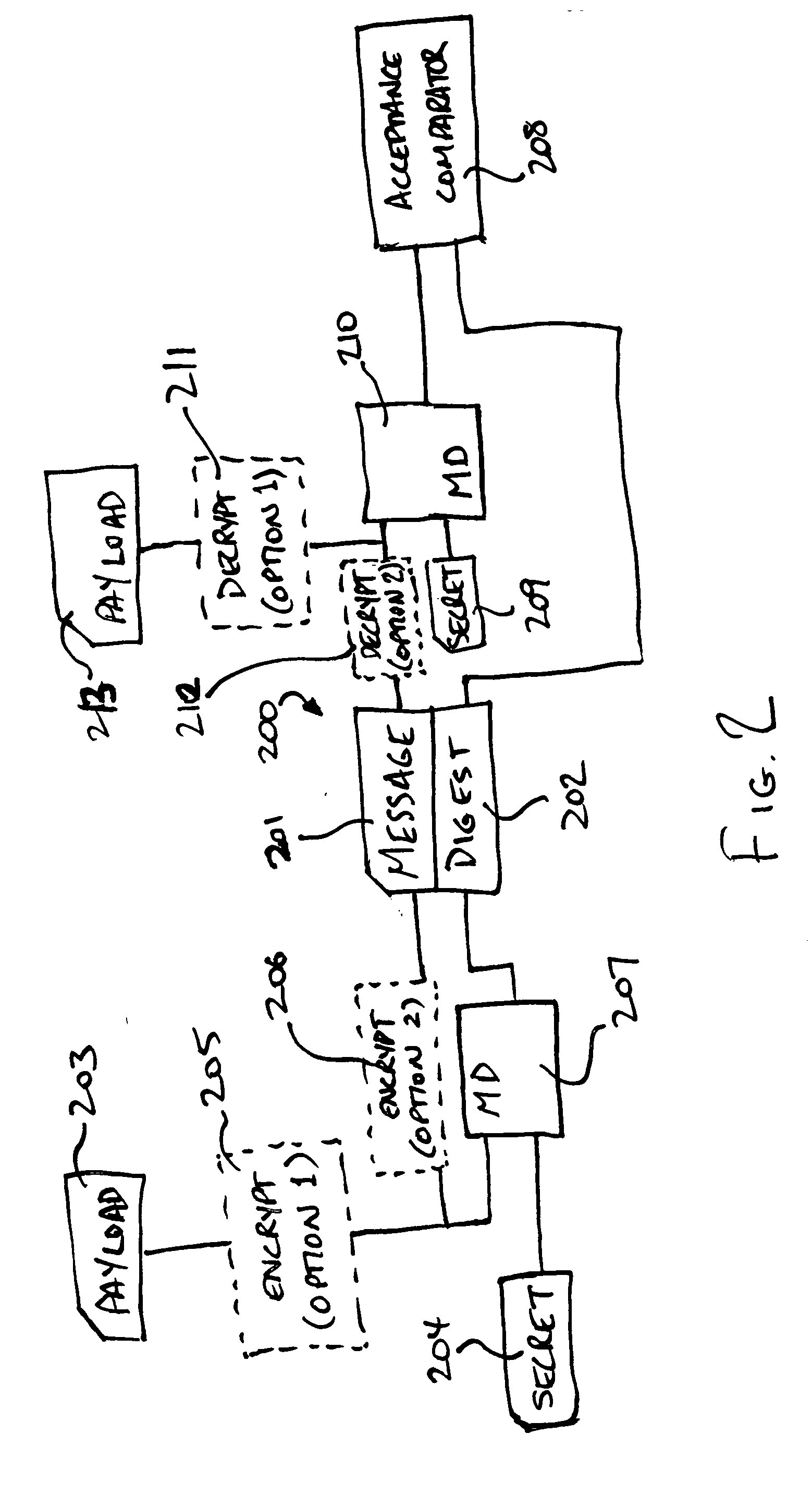
A method of access control in which an authority may limit the content a client may download to a trusted device comprises: the authority making content, and a content descriptor containing information about the content, available to a client; the authority providing an access key to a client; the client presenting the access key and a requested content descriptor to a trusted device for download; and the trusted device accepting or rejecting the requested download as determined by the access key and content descriptor presented. Numerous variations are possible. Apparatus for limiting distribution of content obtained together with an access key in which a shared secret is encoded from a computer executing a server process comprises: a trusted device including a verifier that verifies the encoded shared secret and a content acceptor that only accepts content when the shared secret is verified. The access key may include a message digest covering the shared secret in which case the trusted device may further comprise: a message digest encoded into which information including the shared secret is fed and which produces a message digest for comparison the access key.
Owner:WILDLIFE ACOUSTICS
Computer encoding method for reagent screening of DNA encoding compound library
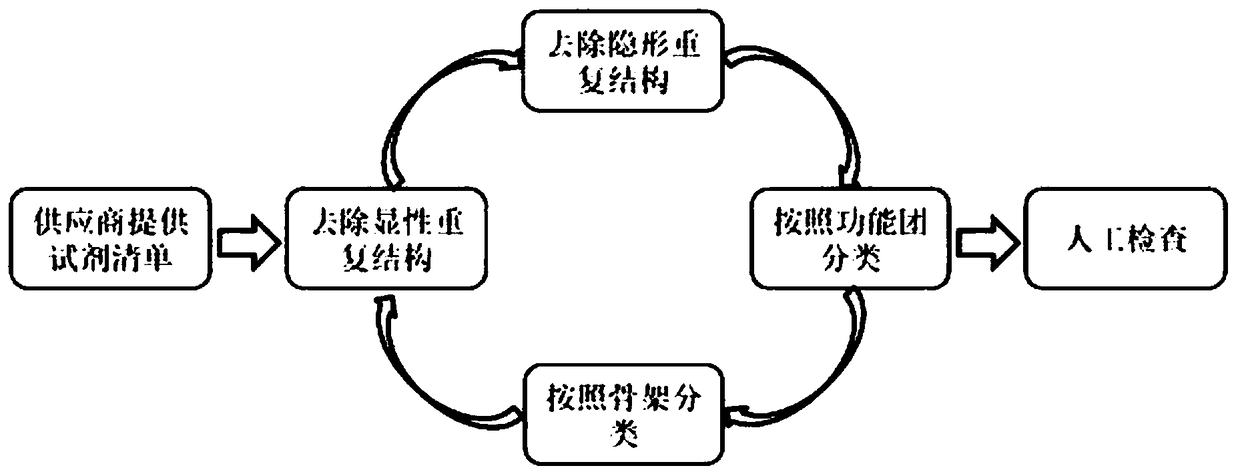
The invention relates to a computer encoding method for reagent screening of a DNA encoding compound library, which comprises the following steps: dominant duplicate checking of reagents, classification of the reagents according to functional groups or scaffolds, invisibility (after removal of a protecting group or a reaction group) duplicate checking of the reagents, screening of the classified reagents according to a certain screening rule, and removal of the reagents which do not meet the requirements. Tens of thousands of reagents can be subjected to duplicate checking and classification processing efficiently, easily and quickly through a computer program obtained in a computer encoding method, to obtain a reagent which is applicable to construction of the DNA encoding compound library and is provided with a certain type or several types of functional groups or scaffolds; and the computer encoding method for reagent screening of the DNA encoding compound library has broad application prospect in the construction of DNA encoding compound libraries.
Owner:上海药明康德新药开发有限公司
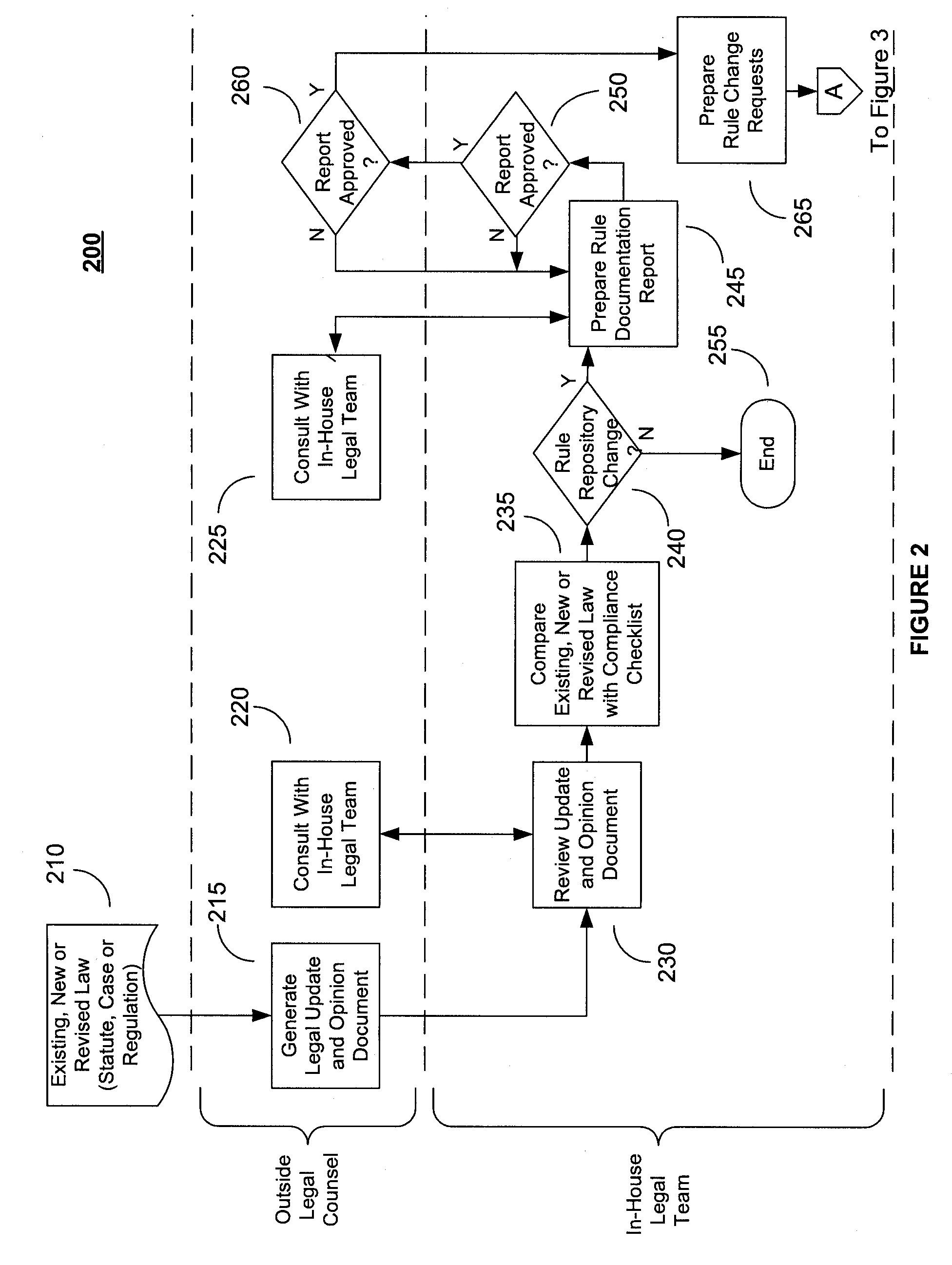
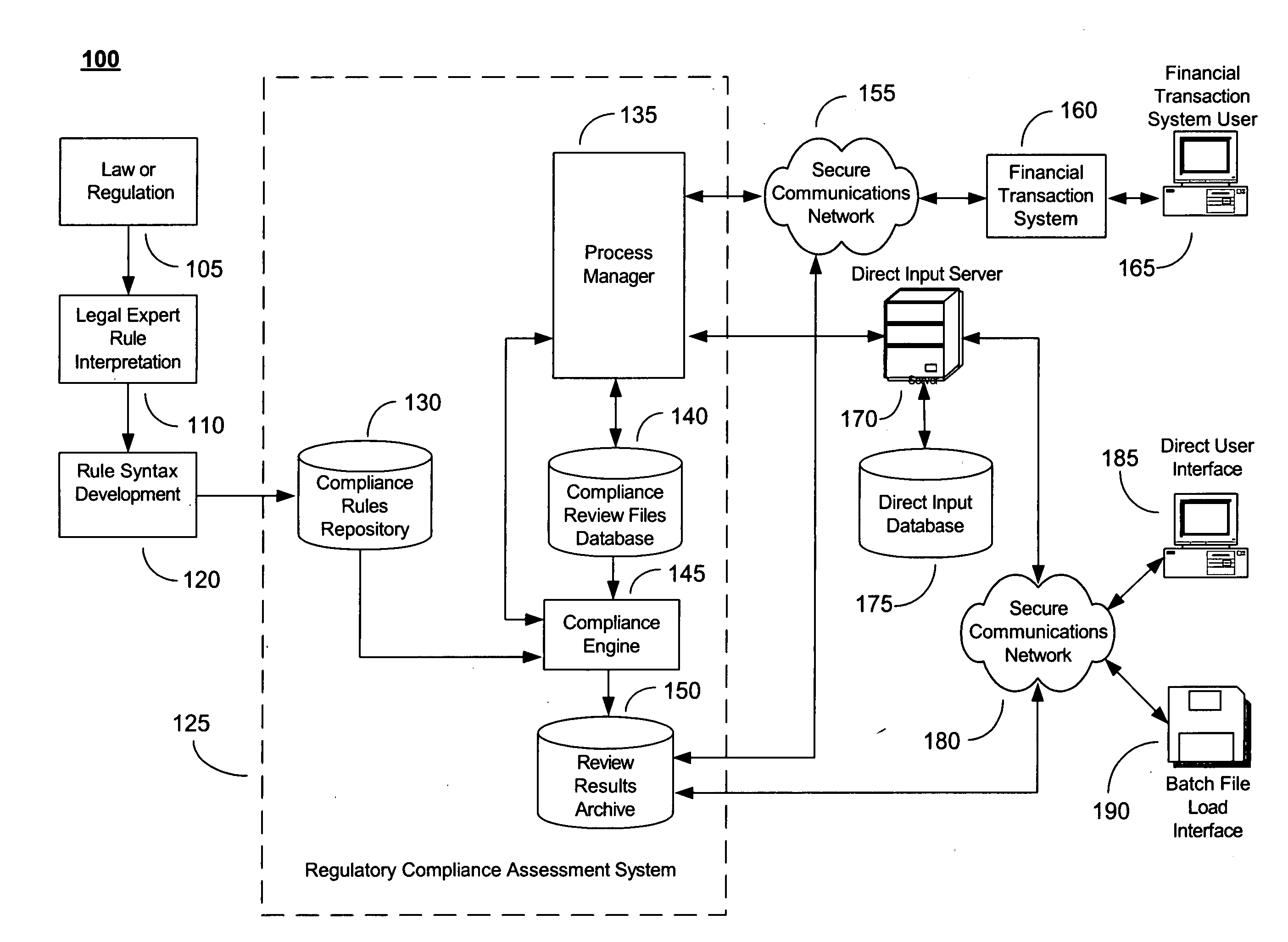
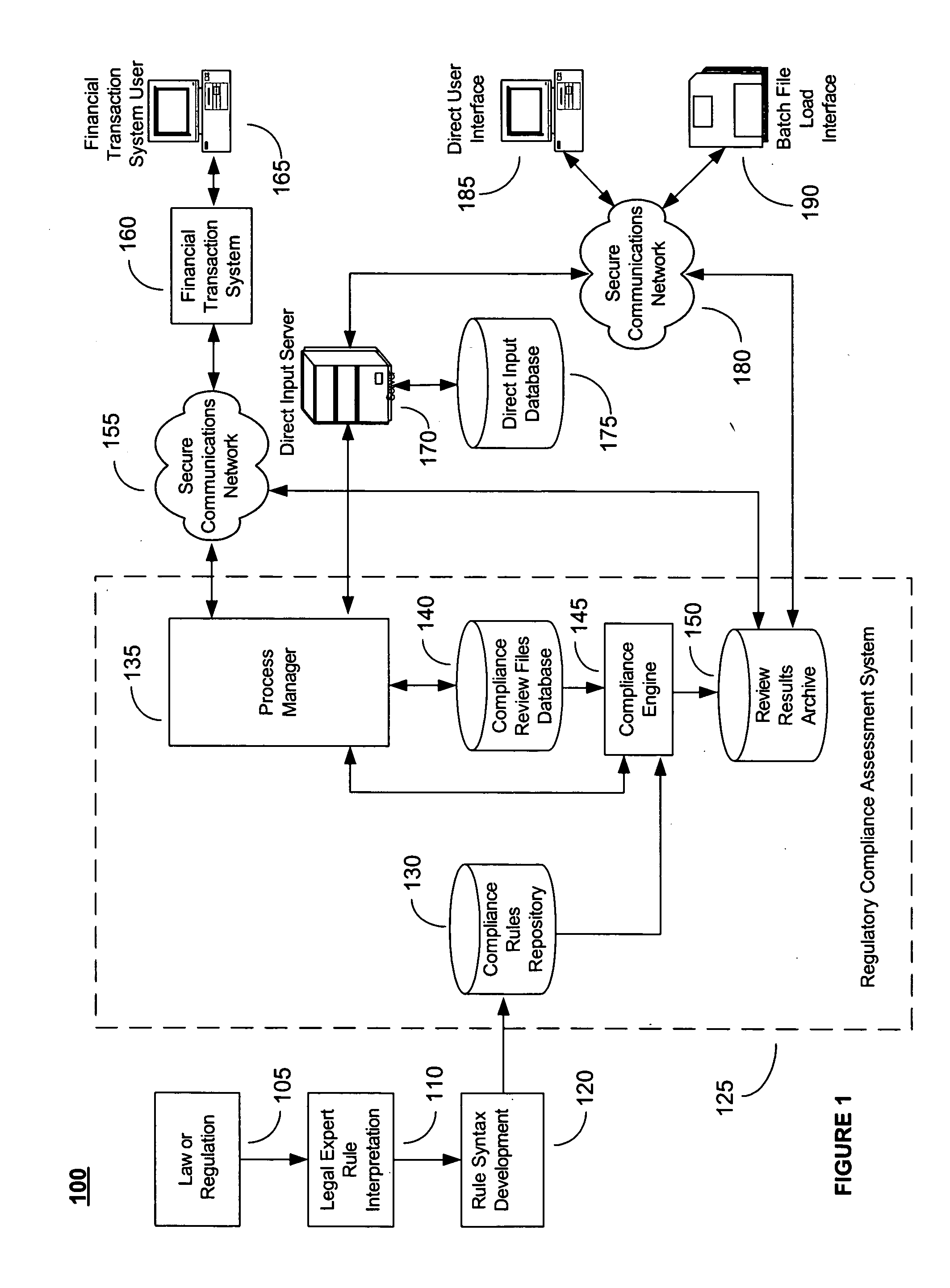
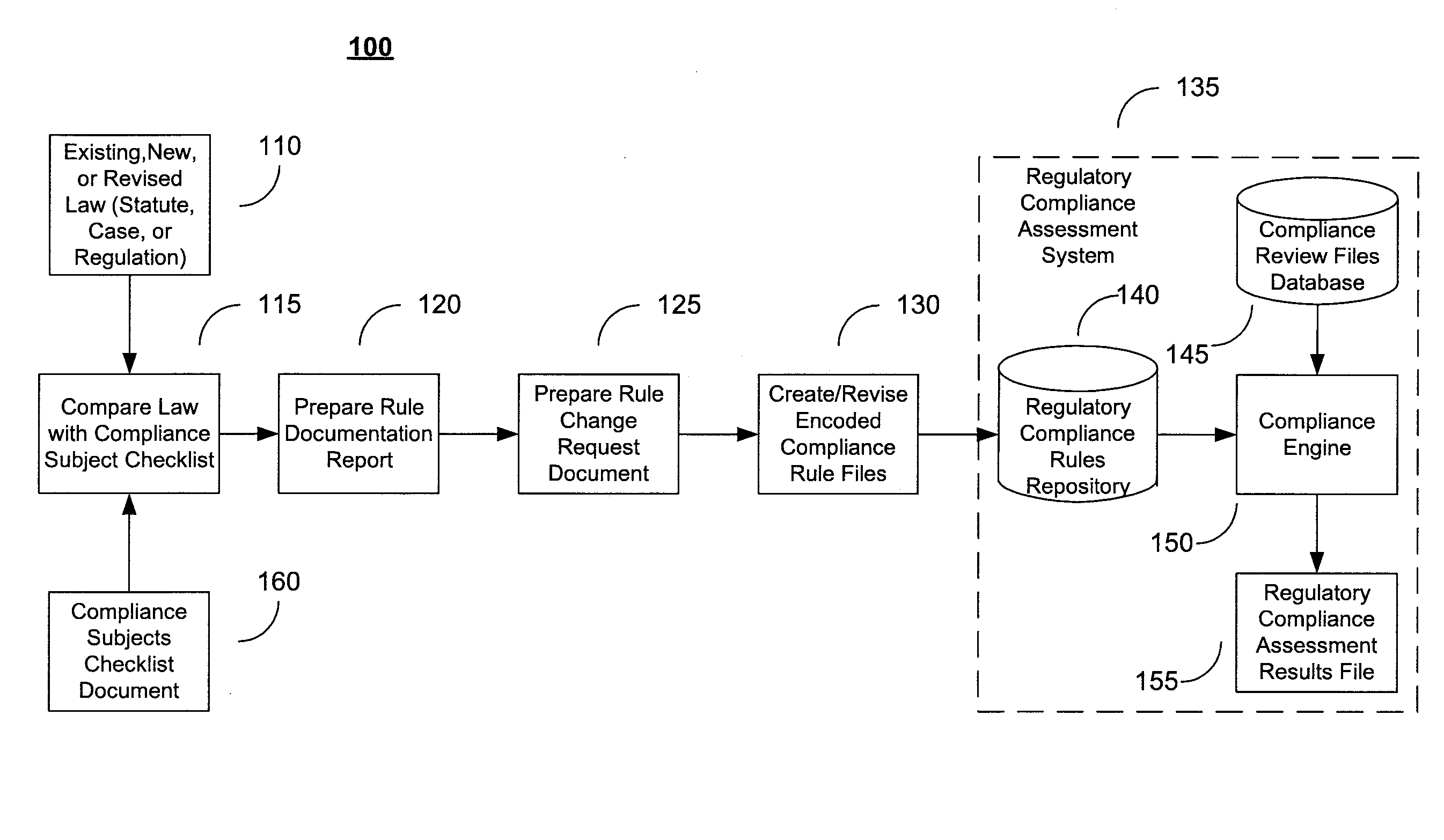
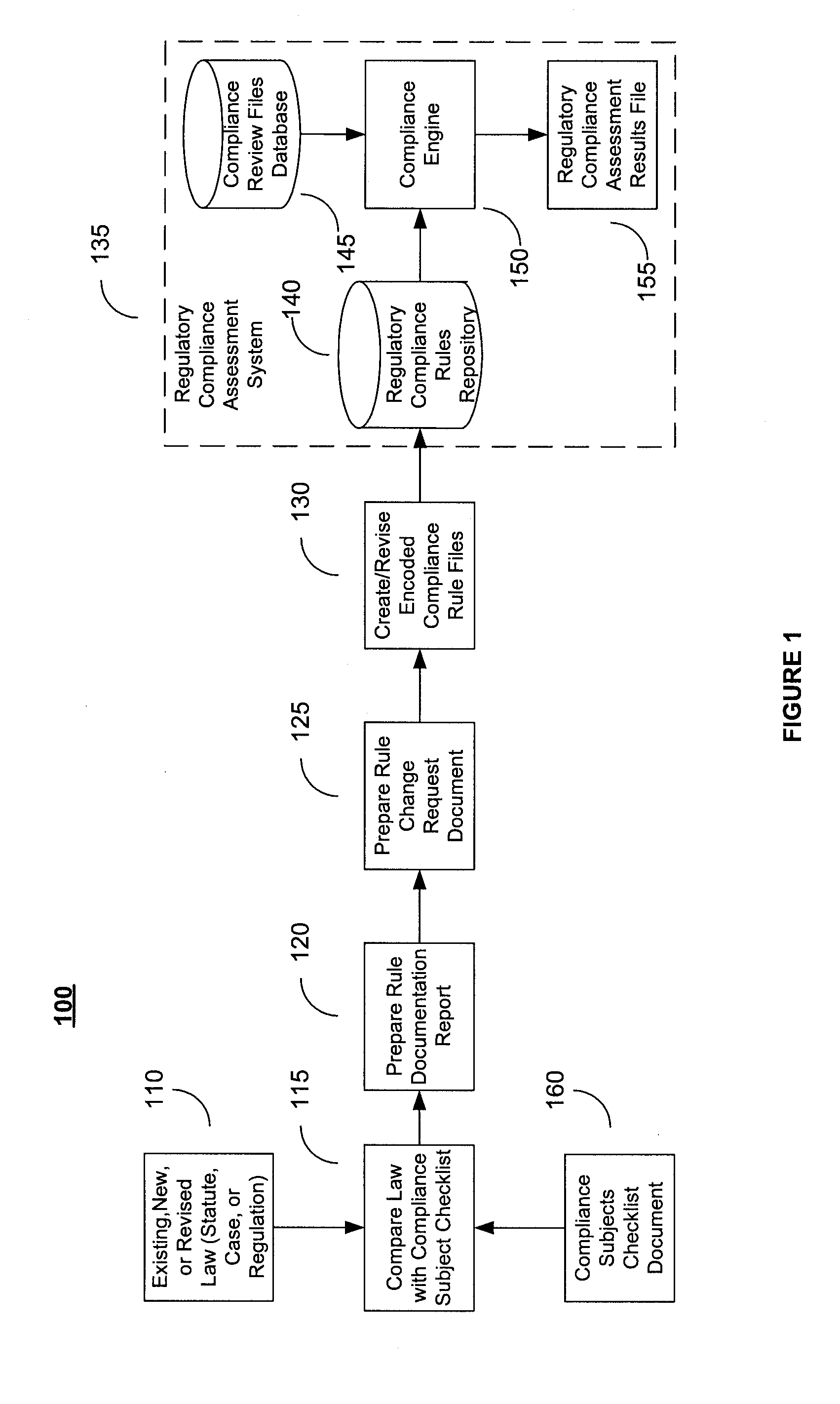
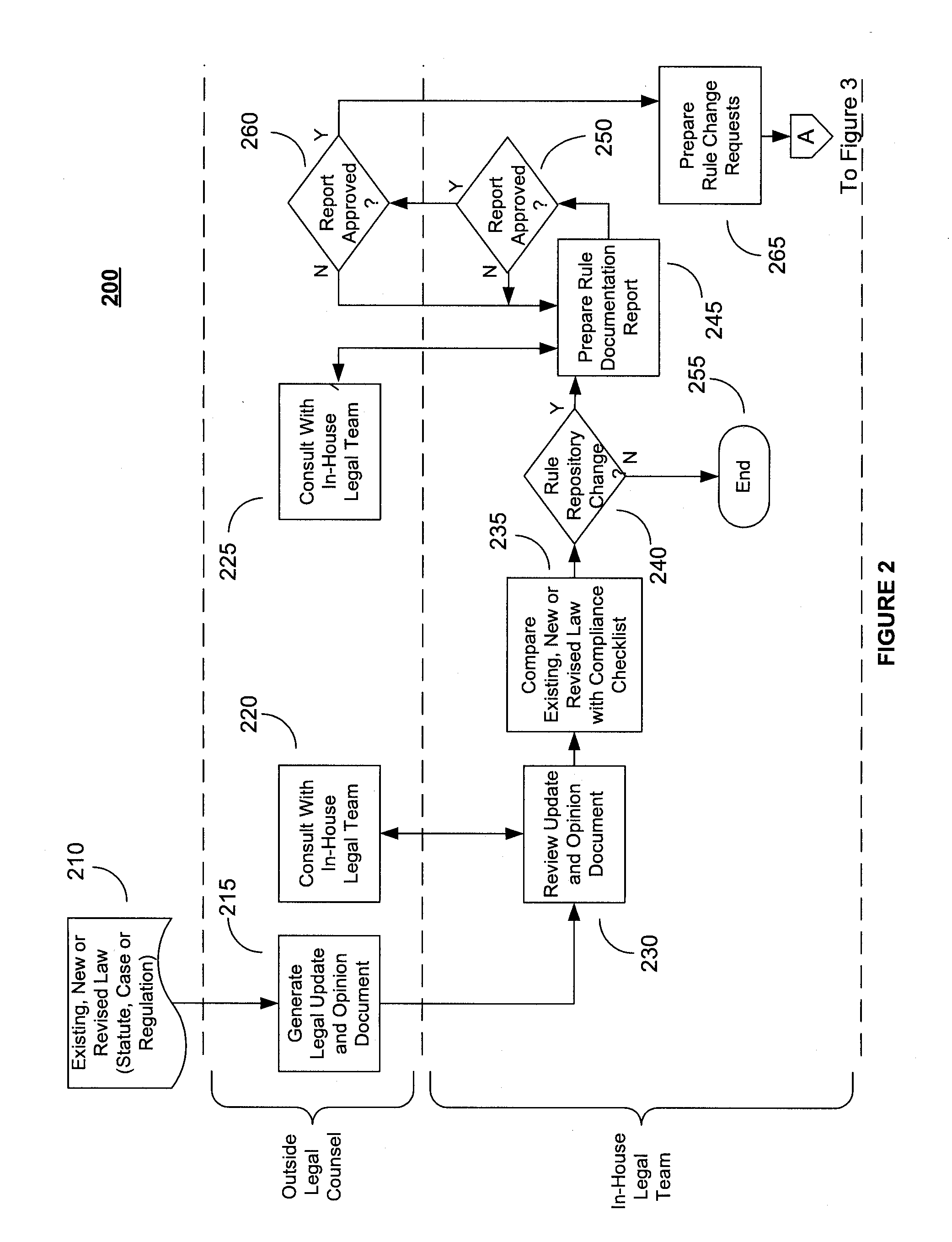
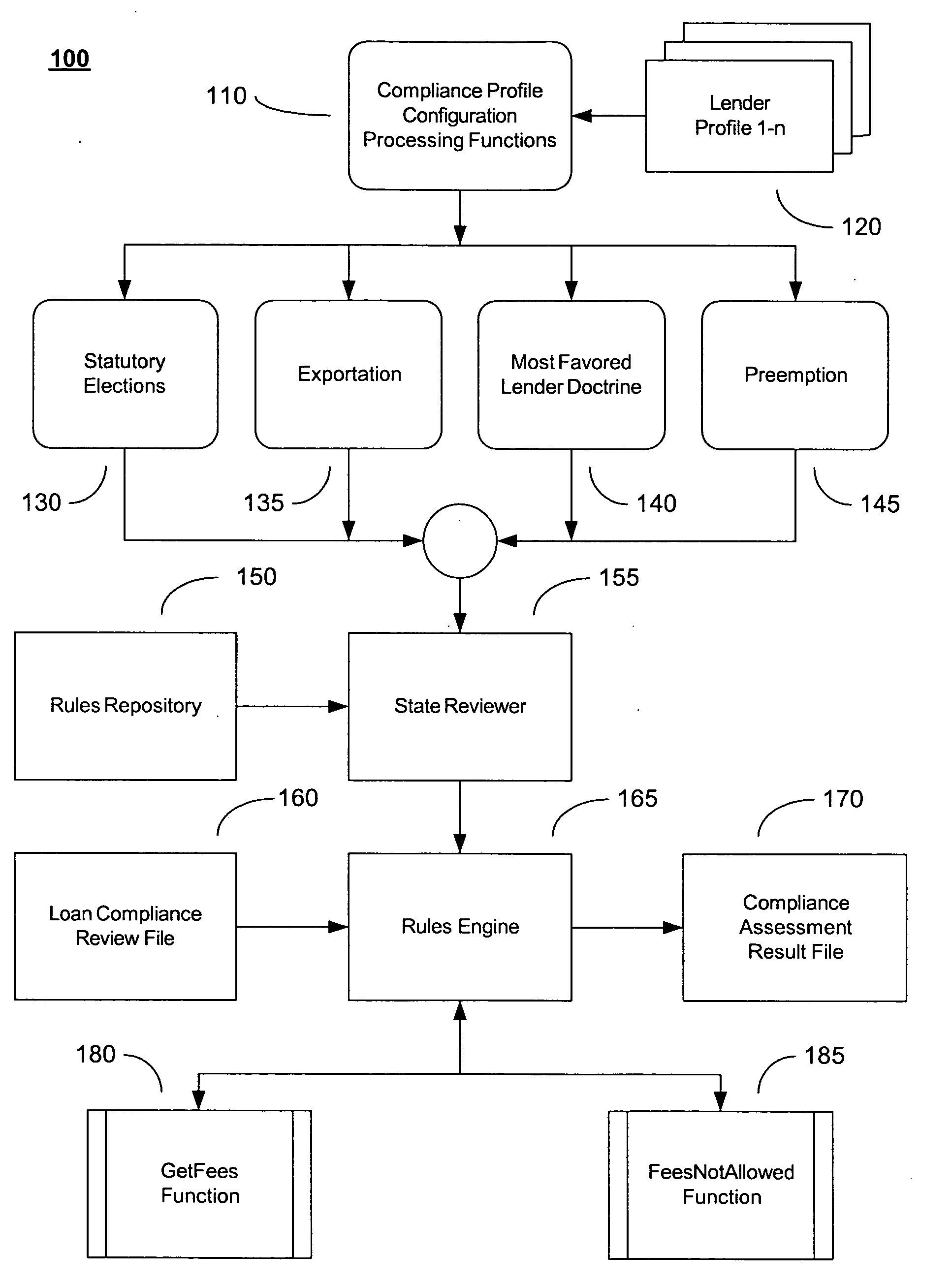
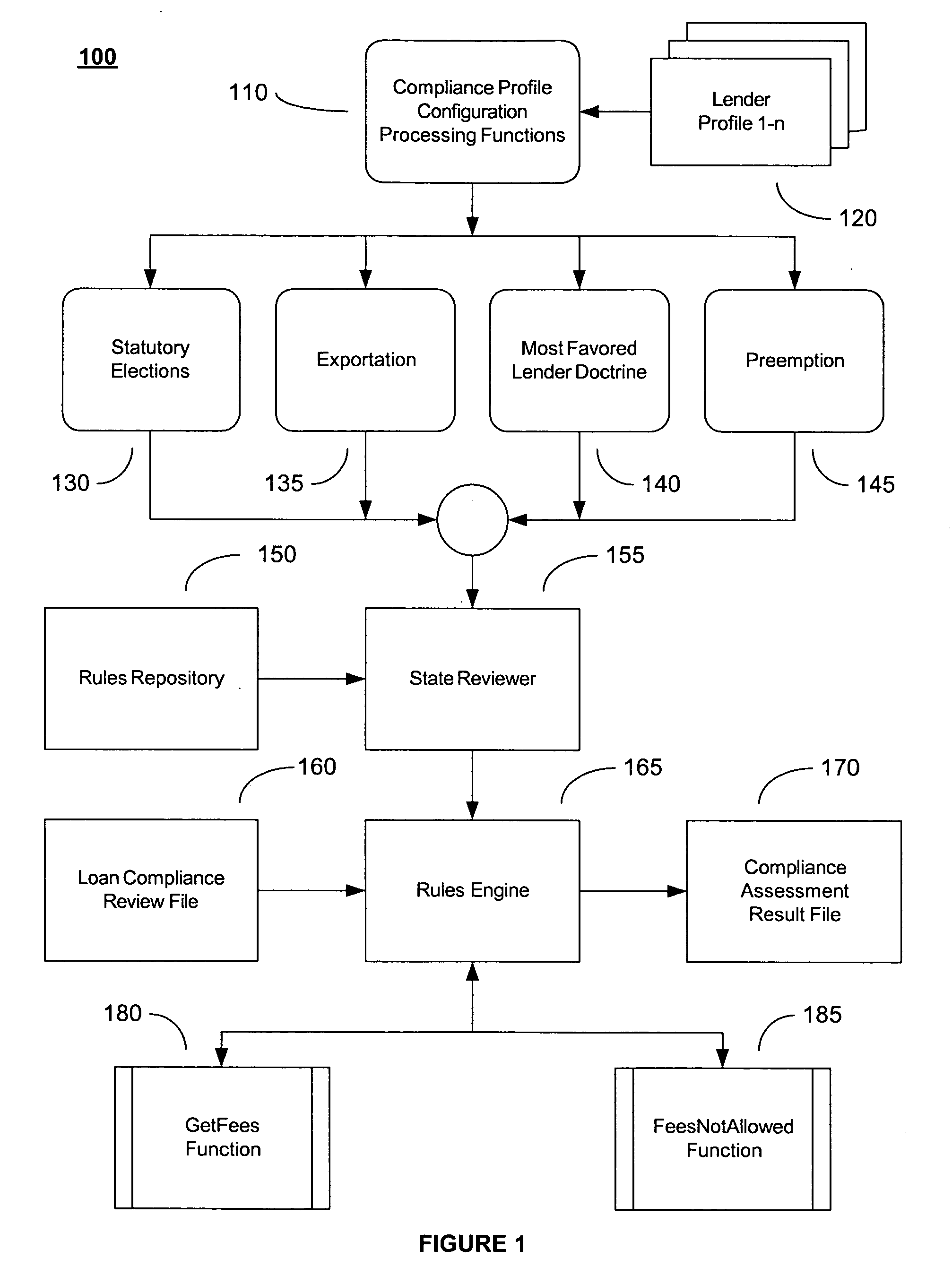
System and Method for Regulatory Rules Repository Generation and Maintenance
InactiveUS20060101027A1Data processing applicationsSpecial data processing applicationsDocumentation procedureData file
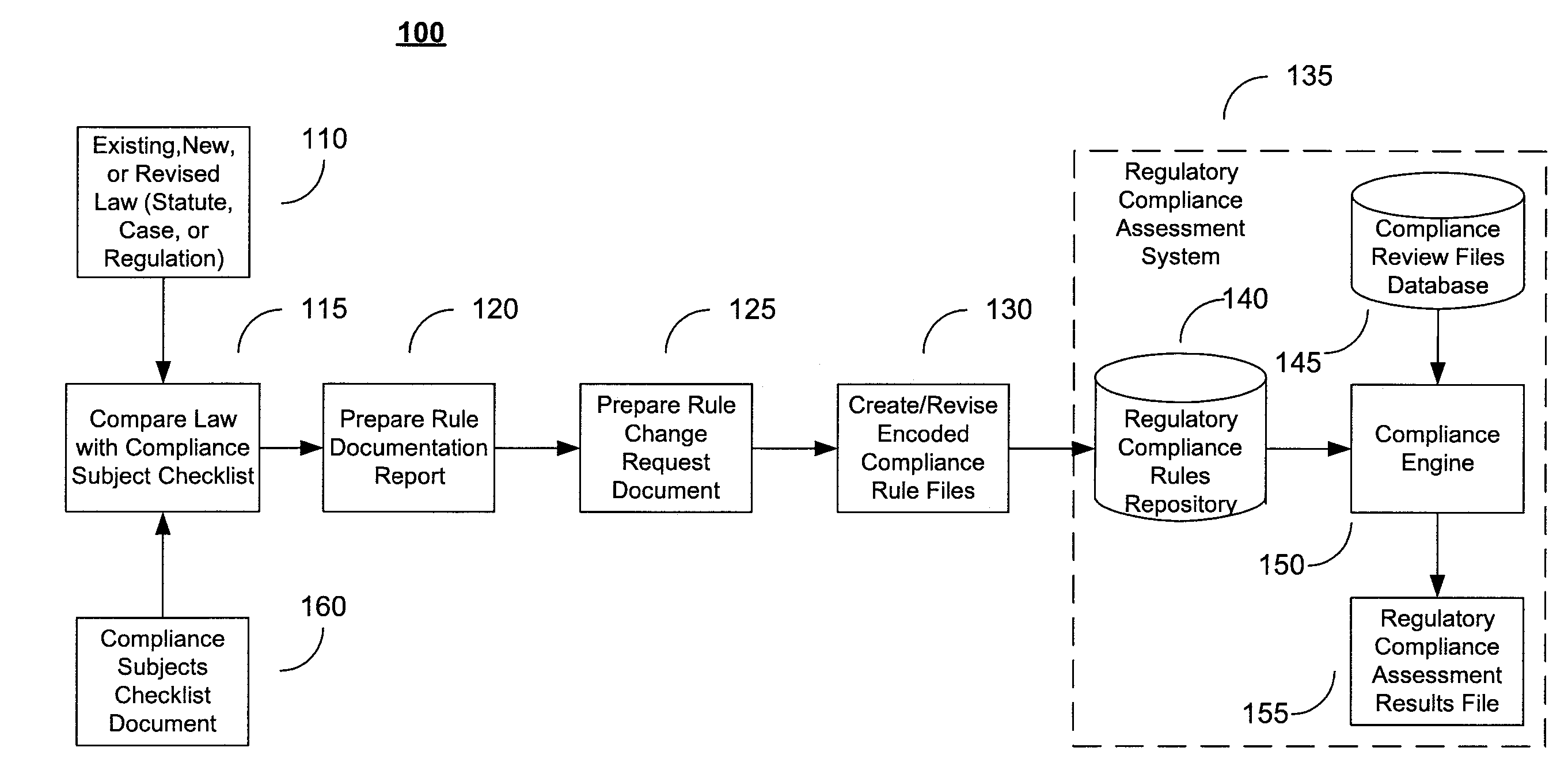
A system and method for deriving compliance requirements from statutes, regulations, case law, official interpretations, attorney general opinions, determination and other interpretive letters, administrative agency regulations, and sources prescribing and interpreting compliance requirements for a jurisdiction, preparing compliance rules documentation that reflect these regulatory requirements, creating computer-encoded compliance rules from the compliance rules documentation, and storing these computer-encoded compliance rules in a compliance rules repository within a regulatory compliance computer system. The jurisdiction may be Federal, state or local authority. The regulatory compliance computer system makes use of the computer-encoded compliance rules by extracting compliance review data from a institution's data system and archiving the institution's data file in a compliance review file database, comparing the compliance review file against the applicable computer-encoded compliance rules in the rules repository, and preparing a regulatory compliance results file that captures noncompliant data in the institution's data system.
Owner:MAVENT HLDG
Method of generating information embedded halftone screen code
InactiveCN1882026AKeep natural shapeHigh densityImage data processing detailsPictoral communicationPrint mediaComputer graphics (images)
The present invention provides a method of generating information embedded halftone screen code. According to this method, massive digital information can be stored through printing on at least one type of print media, such as images, texts, symbols, background, and so on. And the information embedded can be read and recognized simply and reliably. Particularly, the quality of the images will not be reduced after information embedded. The information printed on the media comprises a predetermined array of halftone dots with different morphology including physical and geometrical characteristics, which forms the computer codes to embed information into printed content. The advantages of this invention are: the maximum similarity value can be reduced to under the threshold value according to this method; the recognition performance of the halftone screen code can be improved; and robustness can still be maintained at a high level even though the paper is defected or polluted. Besides, the quality of the image will not be lowered and the image can keep its original condition after information embedded.
Owner:顾泽苍
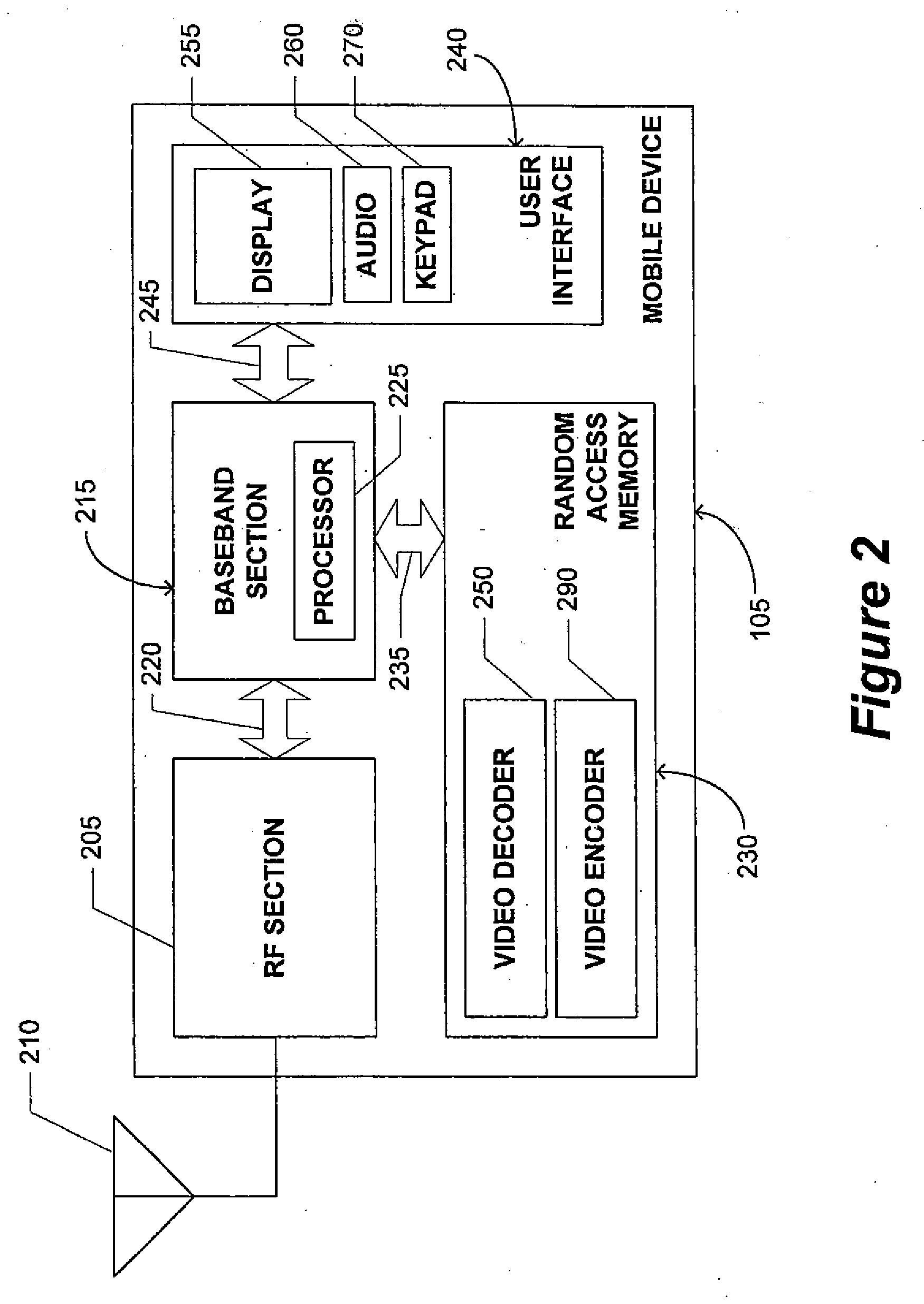
Mobile Device Management System
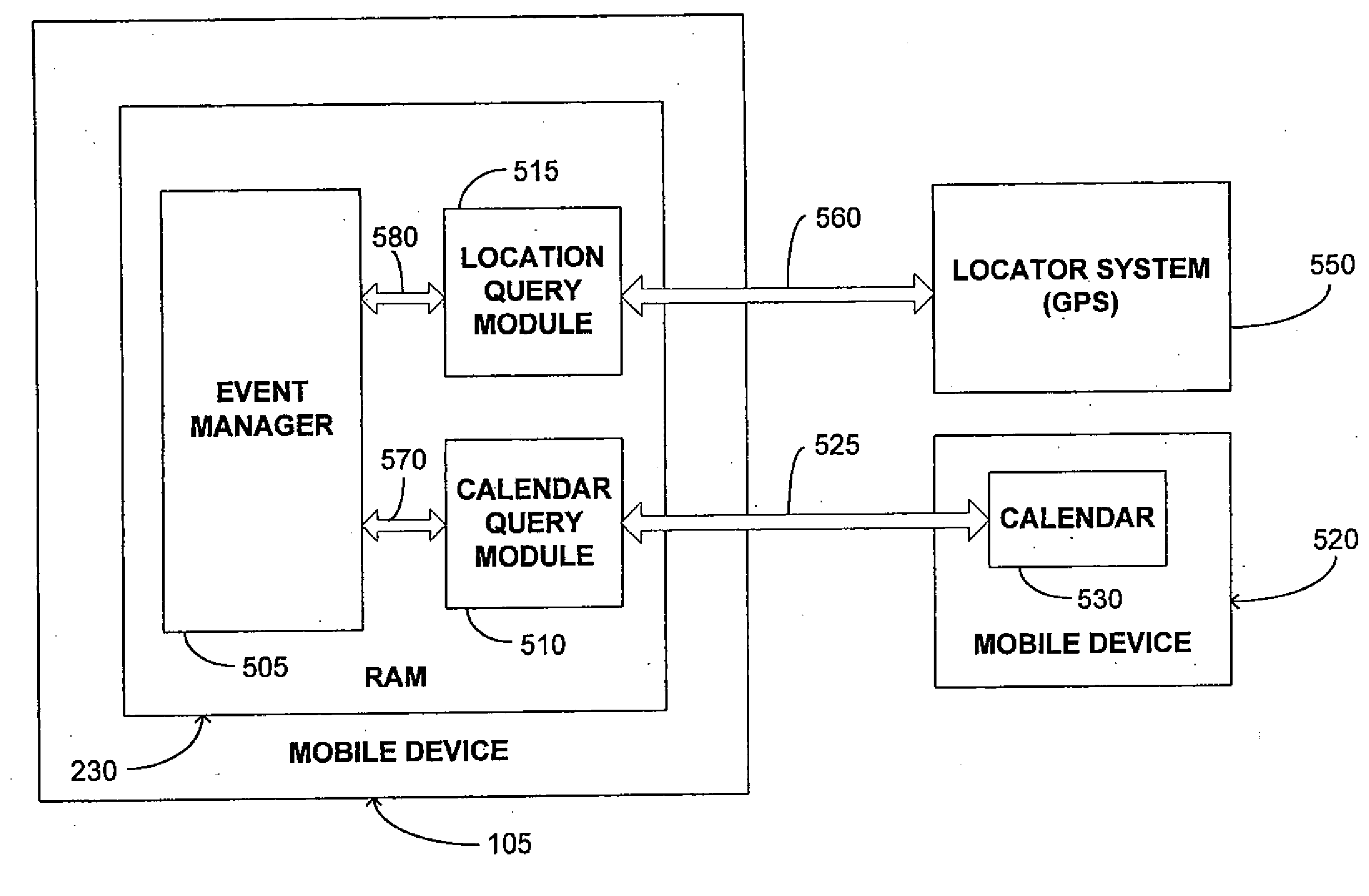
InactiveUS20100274614A1Television system detailsPicture reproducers using cathode ray tubesComputer number formatGlobal Positioning System
A mobile device management system including a method for monitoring a remote video camera and event scheduling, synchronization and modification using location information. Video from a remote camera is encoded by a computer and streamed in real time over a network to a mobile device for decoding and display. The computer encoder and mobile device decoder are software-based. Event calendar and schedule information is incorporated, shared and automatically updated among multiple mobile devices. Location information, such as from a locator network or a satellite-based global positioning system, is used to provide real time updates to a mobile device calendar or event schedule. A map or other indicia of the location of other mobile devices may be provided.
Owner:PLUTO TECH
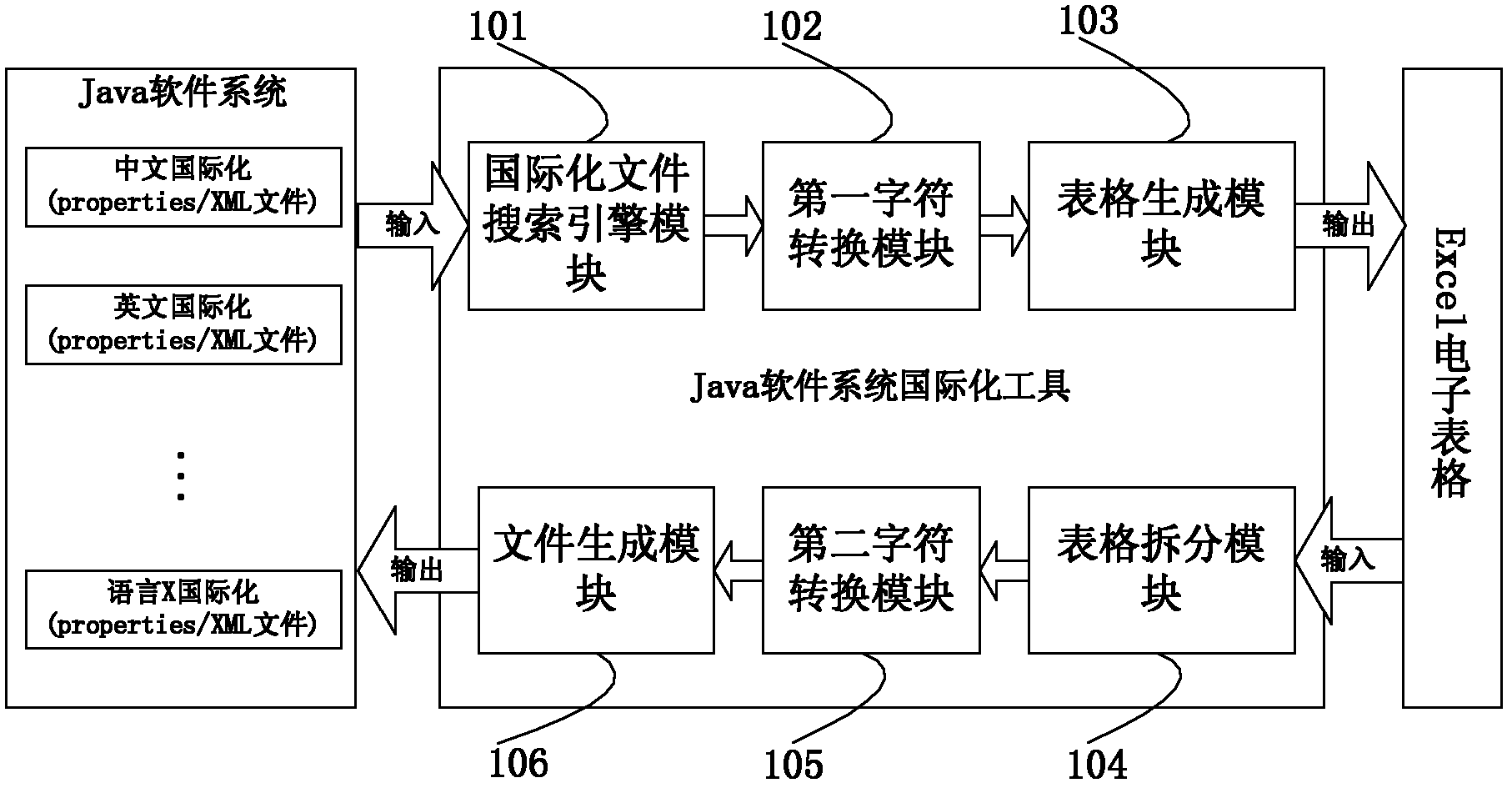
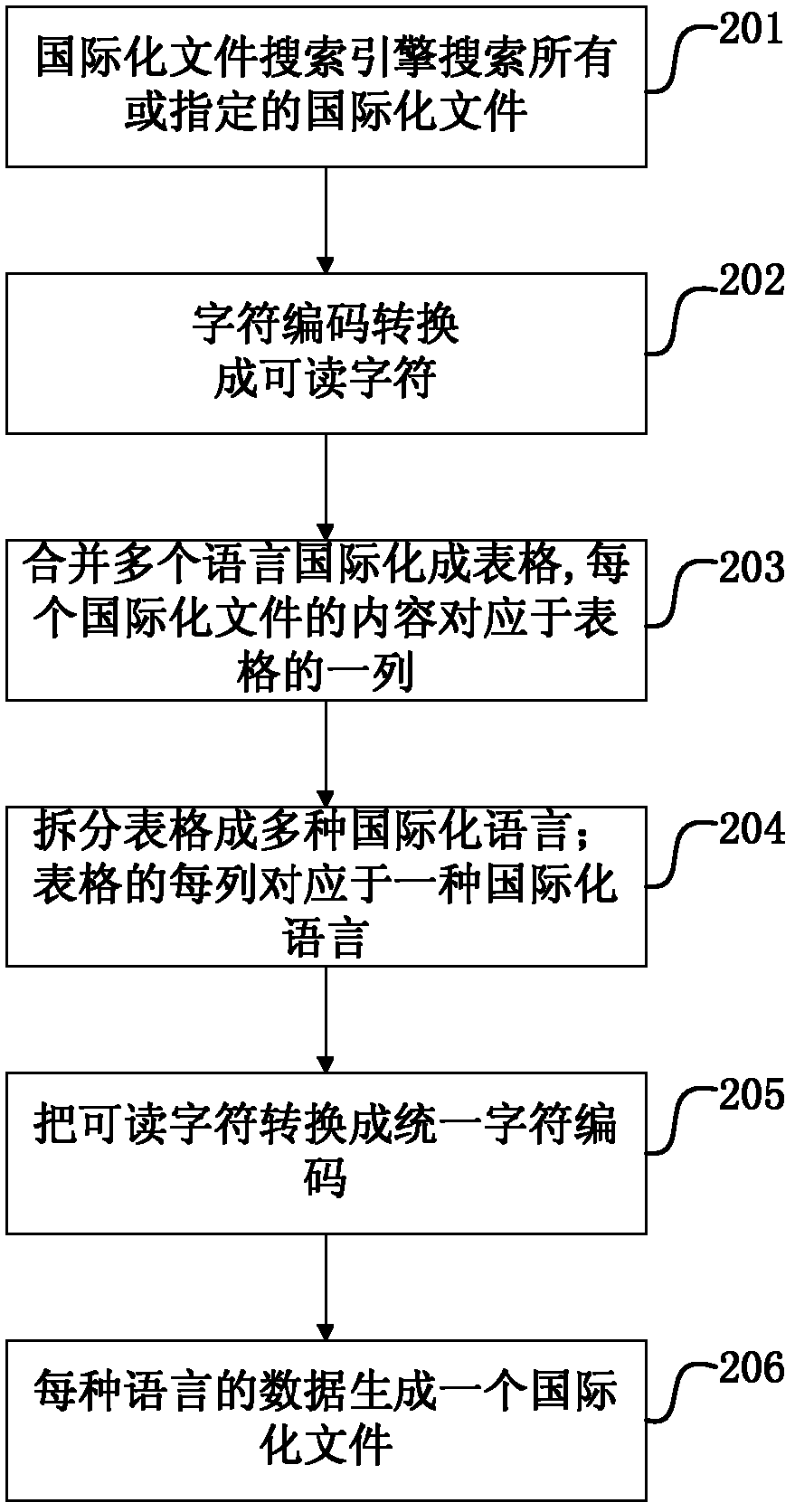
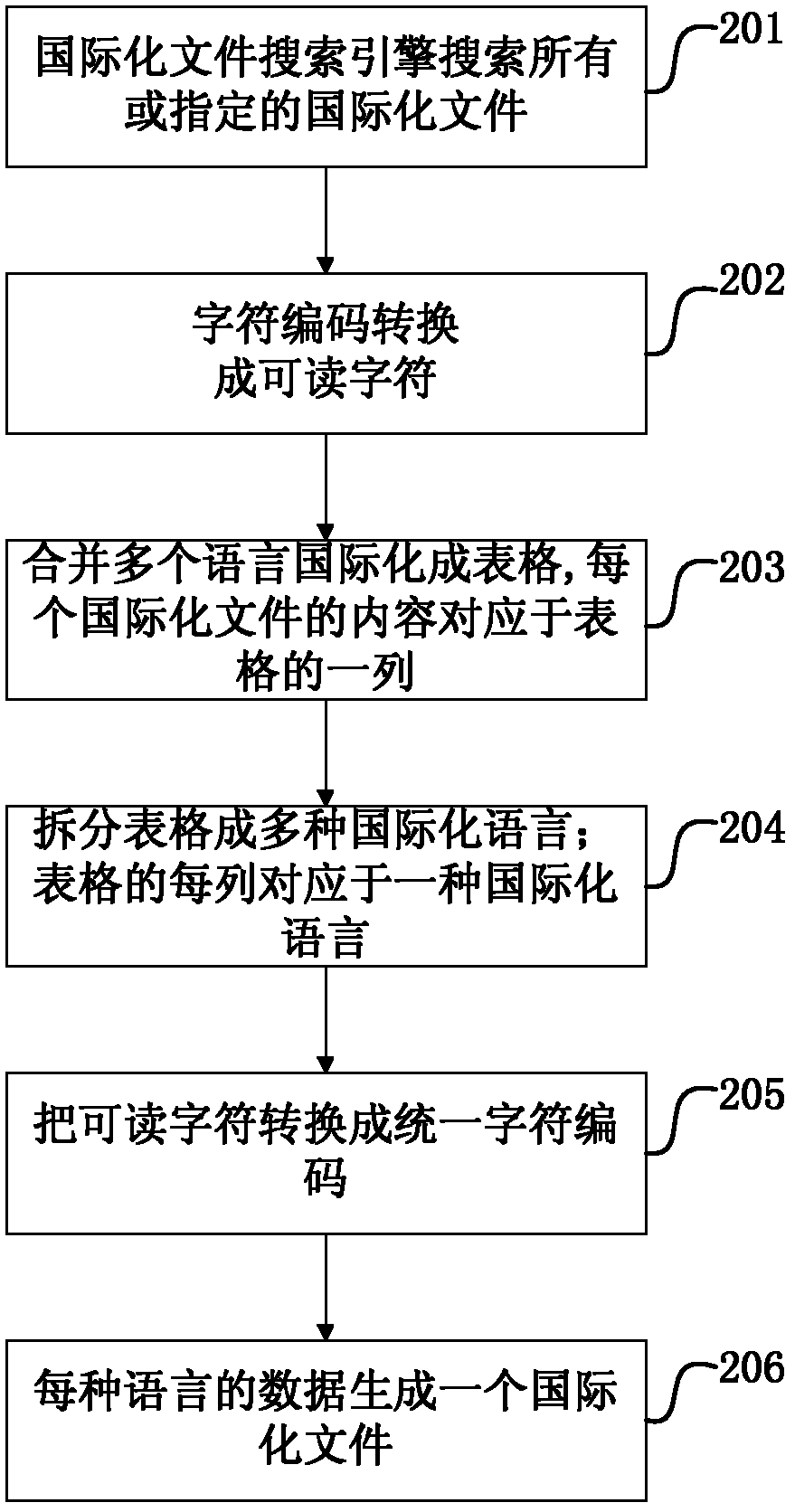
Software system internationalization method and device
ActiveCN102279847ASimplify internationalization operationsInternationalization GuaranteeSpecial data processing applicationsComputer hardwareSoftware system
The invention provides a method for internationalizing a software system. The method comprises the steps of: loading one or more computer-coded internationalizing files of languages, converting a coding format into a readable character, converting the one or more internationalizing files into editable files, wherein the editable files comprise internationalizing key value fields and one or more translation fields corresponding to the internationalizing key value fields, the internationalizing key value fields comprise a plurality of internationalizing key value items, each internationalizing key value item records an internationalizing key value, each translation field comprises a plurality of translation items, each translation item is used for recording the translation of one language of the internationalizing key value in the corresponding internationalizing key value item; and outputting the editable files. The invention also provides a device for internationalizing the software system. According to the invention, entry, edition and check operations of internationalizing data of the internationalizing translators can be simplified.
Owner:RAISECOM TECH
System and method for two-pass regulatory compliance
An automated system and method for ensuring that information in the form of data files provided by highly regulated businesses, such as financial institutions, comply with the most currently applicable Federal, state and local laws and regulations. This may be accomplished by applying a set of computer-encoded compliance rules to the transaction data files from these businesses in a two-pass regulatory compliance review methodology. In a first pass, a limited set of input data elements from one or more input transaction data files is used that results in an extremum or worst-case condition for compliance assessment by using one or more compliance rule sets. The transaction data files that are found to be not in compliance when using this limited set of data elements may or may not be in compliance when using a more complete and detailed set of data elements in a second pass.
Owner:MAVENT HLDG
User Interface Defined Document
PendingUS20150134707A1Digital data information retrievalDigital data processing detailsTablet computerDocumentation procedure
The preferred embodiment of the invention encompasses a method used to (a) create computer applications, or (b) create database-backed forms / documents for a customizable user interface within an existing computer program, that (c) can then be stored, queried and analyzed using map-reduce techniques; using nothing but the front-end user-interface design performed on the device and without the use of any computer coding or database management or setup of any kind.The preferred embodiment invention permits both simple documents (also known as forms), documents-within-documents, and business processes that link documents together, to be defined and converted into a working application on a smart phone, tablet or computer system by end users without the use of code or database management by the end user.
Owner:FIELD SQUARED INC
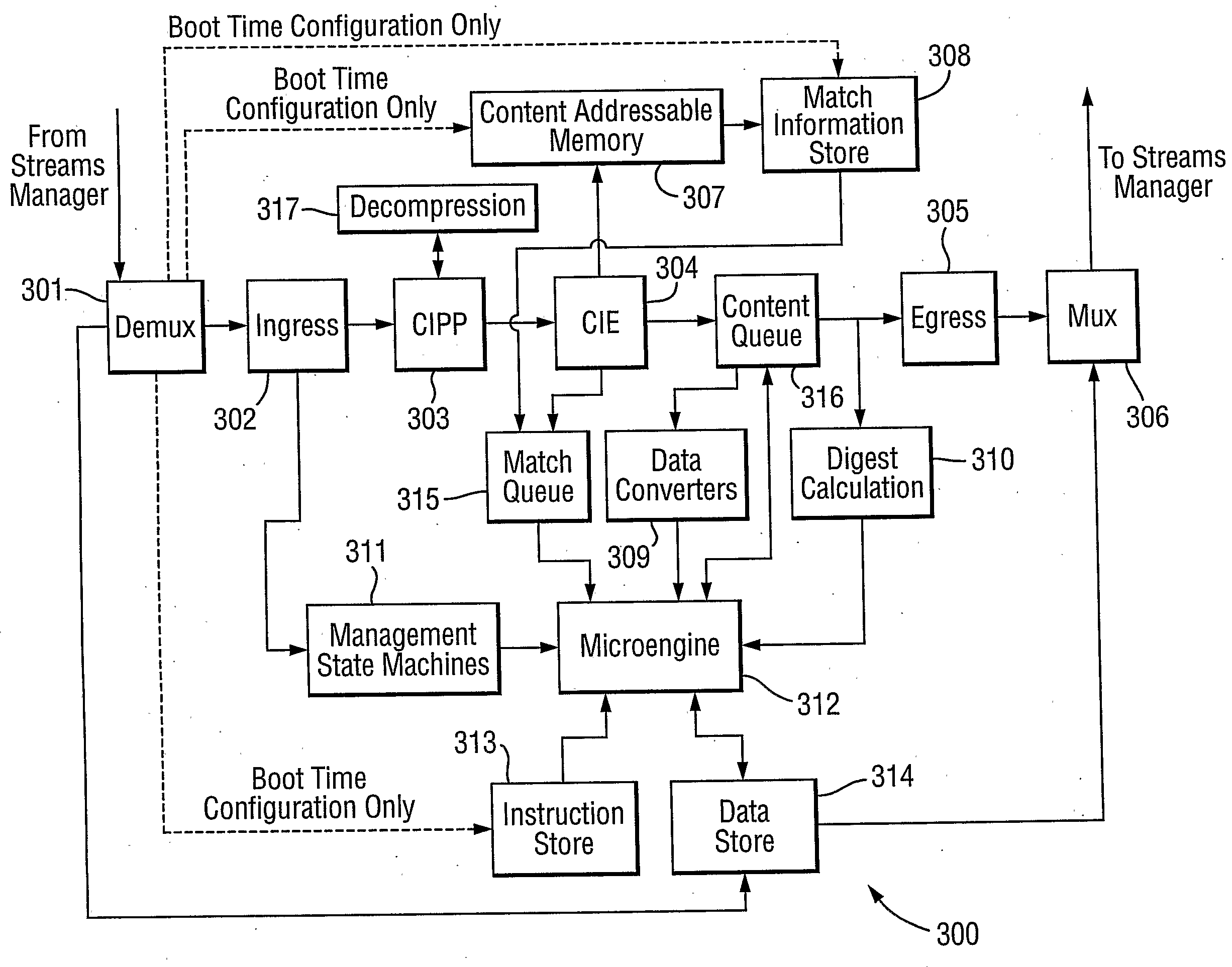
Network implemented content processing system
InactiveUS20090119774A1Adjustable parametersMemory loss protectionError detection/correctionPattern matchingComputer number format
In the present invention, a data processing device for processing streams of network borne data includes content inspection logic configurable to perform pattern matching functions on a received content stream and output match data, and a microengine for executing computer coded instructions, the microengine being coupled to the content inspection logic for configuring the pattern matching function of the content inspection unit in respect of a particular processing job for the received content stream and for processing the content stream independence on the match data. The microengine is adapted to reconfigure dynamically the content inspection logic in dependence on the match data thereby to modify the pattern matching function performed by the content inspection logic on the content stream during the course of a processing job. The present invention provides a novel architecture and method for processing content as it flows through a network. The processing of content includes parsing, analysing, modifying and controlling the delivery of a content stream using a number of pattern matching techniques. Importantly, the present invention makes it possible to adjust the parameters of the pattern matching search as the search progresses through the content stream.
Owner:BAE SYSTEMS PLC
Anti-counterfeit packaging method and apparatus
InactiveCN1866320AOvercome being easily imitatedTo overcome the shortage of large material consumptionStampsPackagingComputer number formatComputer engineering
Owner:SICHUAN YIBIN WULIANGYE GROUP
System and Method for Regulatory Rules Repository Generation and Maintenance
InactiveUS20090177664A9Data processing applicationsSpecial data processing applicationsDocumentation procedureData file
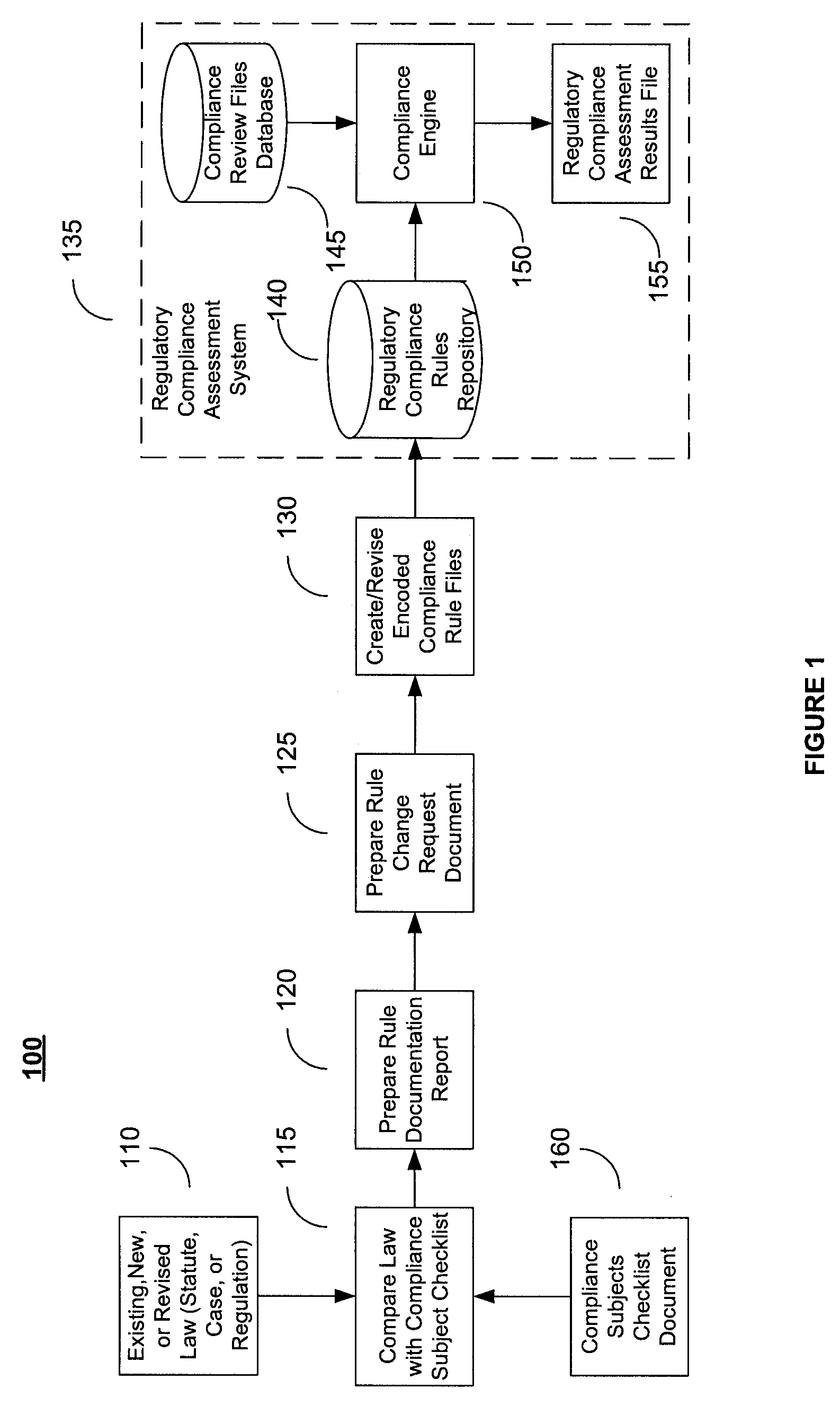
A system and method for deriving compliance requirements from statutes, regulations, case law, official interpretations, attorney general opinions, determination and other interpretive letters, administrative agency regulations, and sources prescribing and interpreting compliance requirements for a jurisdiction, preparing compliance rules documentation that reflect these regulatory requirements, creating computer-encoded compliance rules from the compliance rules documentation, and storing these computer-encoded compliance rules in a compliance rules repository within a regulatory compliance computer system. The jurisdiction may be Federal, state or local authority. The regulatory compliance computer system makes use of the computer-encoded compliance rules by extracting compliance review data from a institution's data system and archiving the institution's data file in a compliance review file database, comparing the compliance review file against the applicable computer-encoded compliance rules in the rules repository, and preparing a regulatory compliance results file that captures noncompliant data in the institution's data system.
Owner:MAVENT HLDG
Digital anti-fake printing method
InactiveCN101105837AEasy to identifyThe method of change is intuitive and easy to understandVisual representation by matrix printersVisual representatino by photographic printingComputer number formatSecurity printing
Owner:俞熹
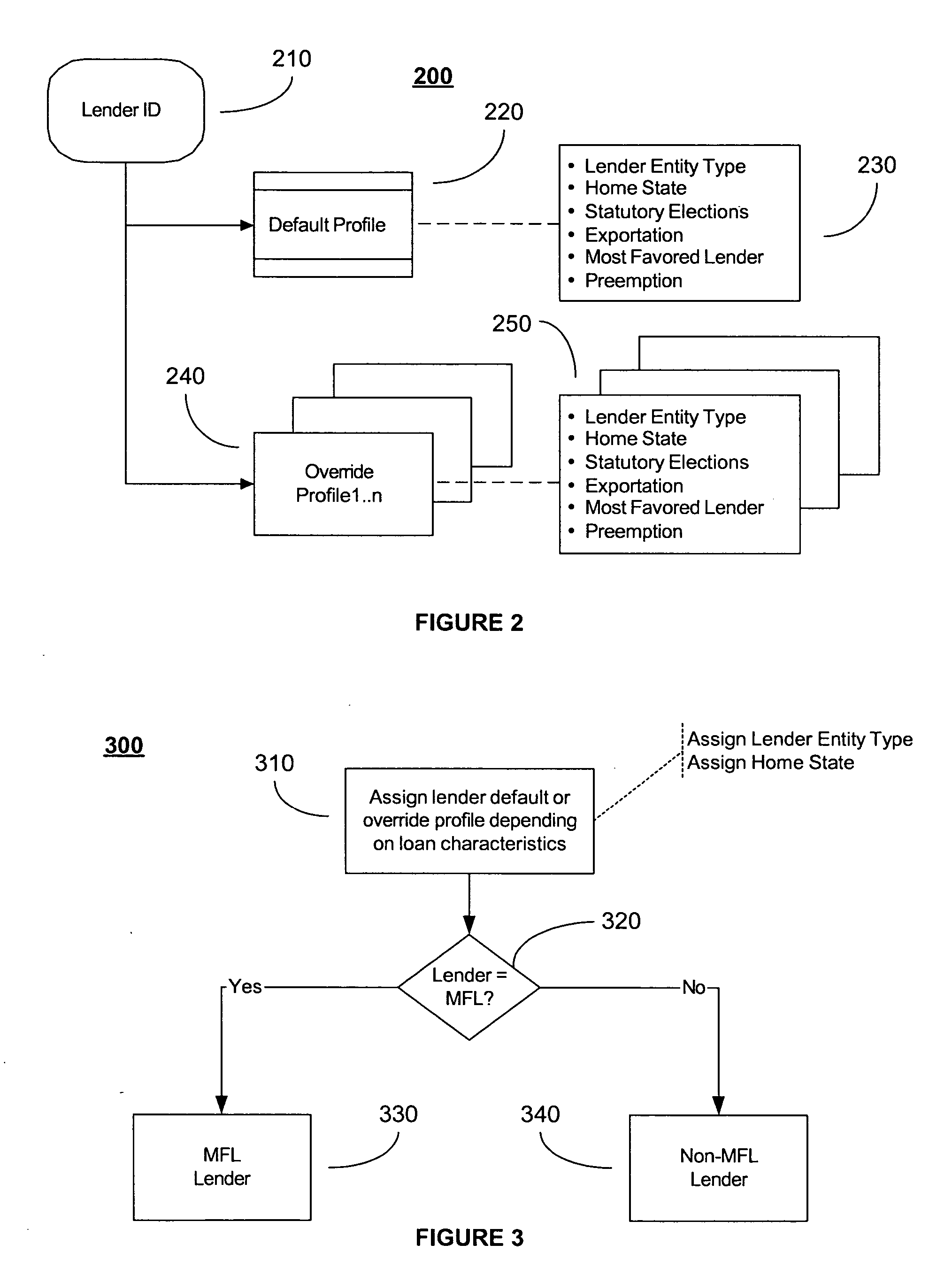
System and method for compliance profile configuration and application
A system and method for specifying elections in one or more designated lender compliance profiles that include statutory election, exportation election, most favored lender election, preemption election and non-electable regulatory requirements. A set of computer-encoded compliance rules applicable to a particular financial institution is derived from a lender compliance profile. This designated set of computer-encoded and computer-executed compliance rules derived from a compliance profile may be used to determine regulatory compliance assessment of lender compliance review computer data files. The requirements of the computer-encoded compliance rules are traceable to one or more state jurisdictions, including home state, property state, and target state. The computer-encoded compliance rules are derived from statutes, regulations, case law, official interpretations, attorney general opinions, determination and other interpretive letters, administrative agency regulations, and any other sources prescribing or interpreting compliance requirements for a jurisdiction.
Owner:MAVENT HLDG
Collaborative structured analysis system and method
InactiveUS8966569B2Digital data processing detailsComputer security arrangementsComputer number formatStructured analysis
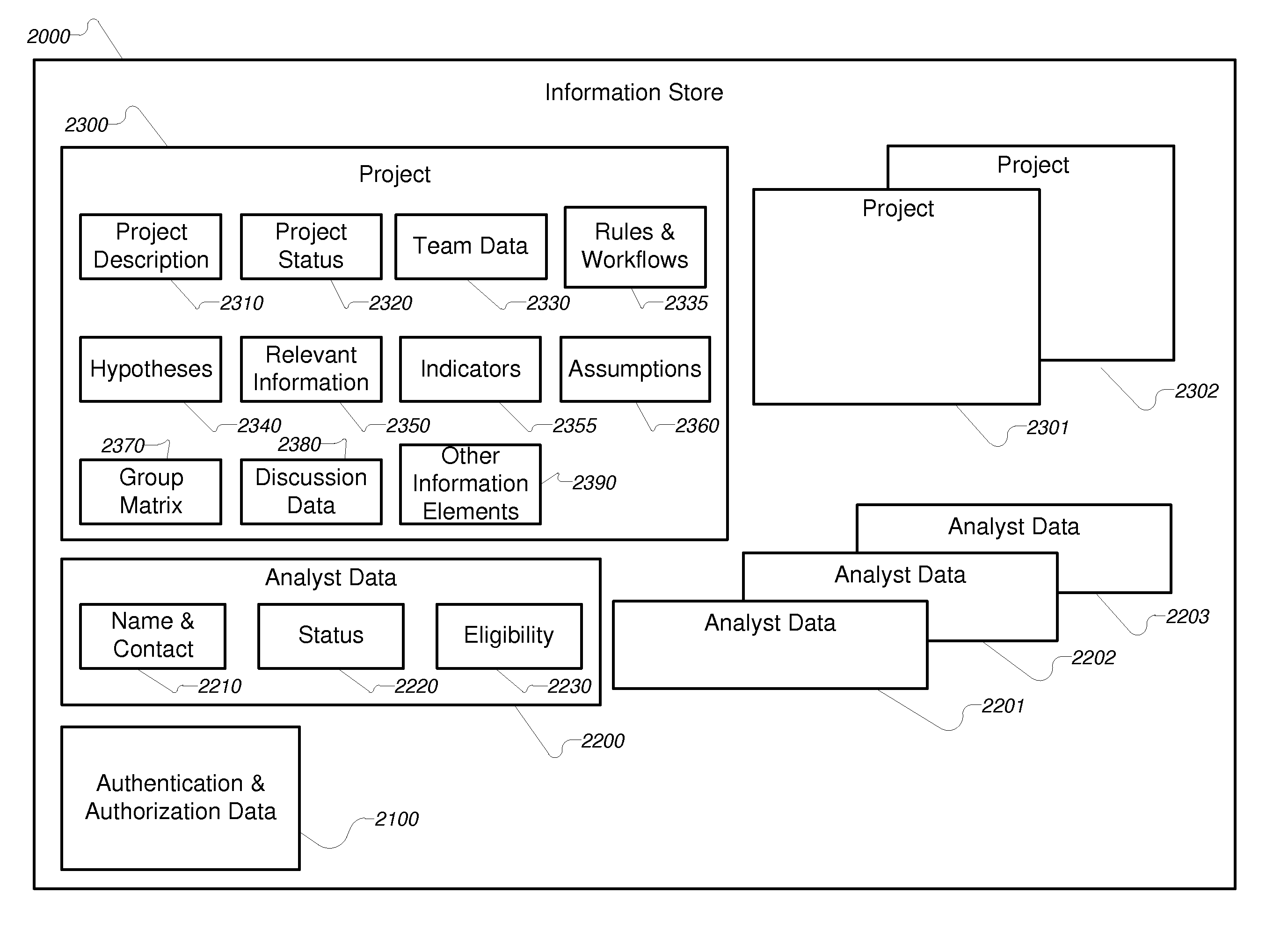
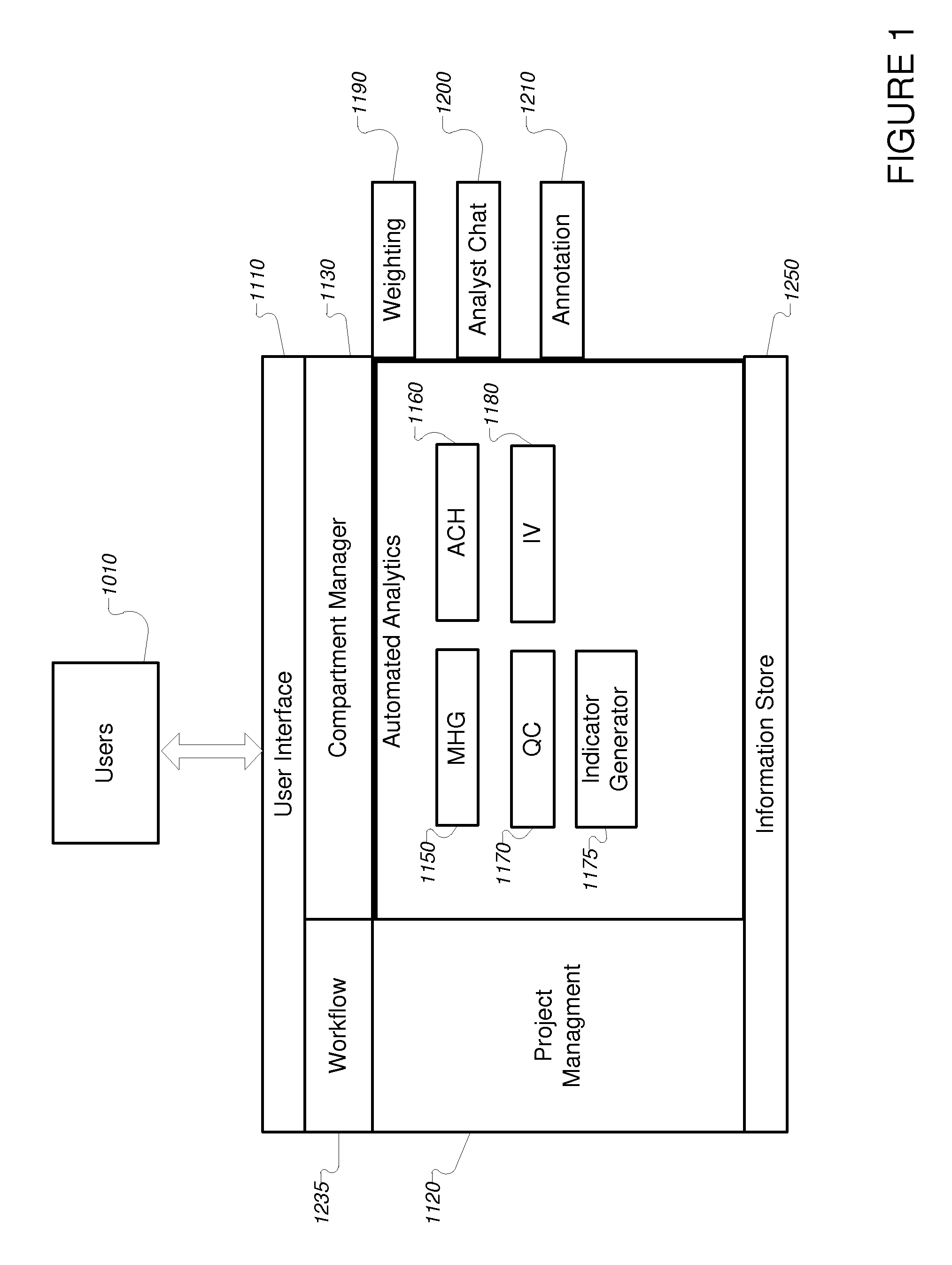
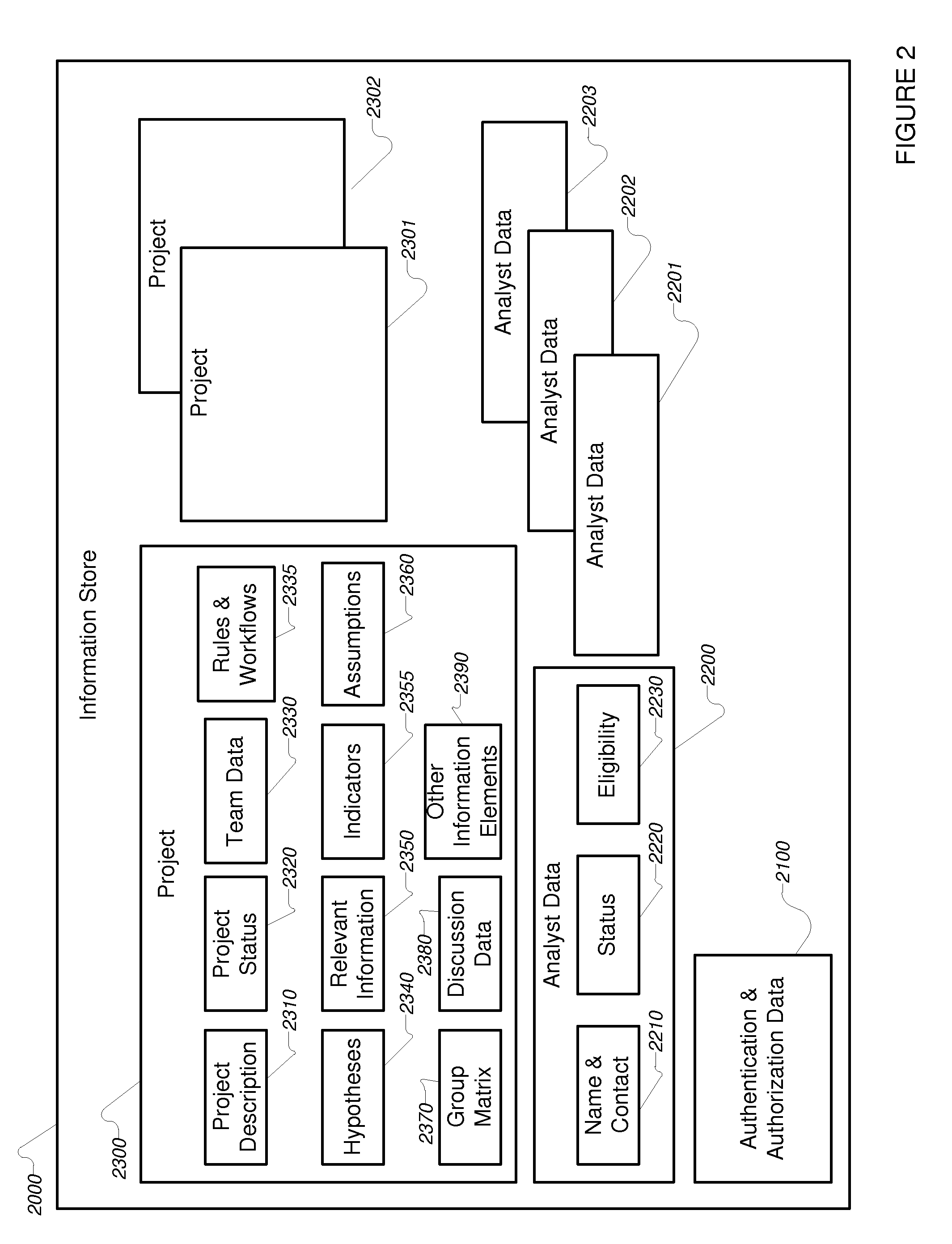
Methods, systems, and apparatus for providing compartmented, collaborative, integrated, automated analytics to analysts are provided. In a first aspect, the present invention provides a computer-implemented method for providing compartmented, collaborative, integrated, automated analytics to analysts including: selecting a computer-encoded project-specific workflow; determining a computer-encoded compartment manager, said computer-encoded compartment manager including computer-encoded information about the context of said project-specific workflow; retrieving said computer-encoded information about the context; selecting a computer-implemented automated analytic using said computer-encoded project-specific workflow; providing under control of said computer-encoded compartment manager said information about the context to said automated analytic; processing said computer-encoded information using said computer-implemented automated analytic, to generate thereby analytical information representing an outcome to said analysts; and processing said analytical information in accordance with said computer-encoded compartment manager and said computer-encoded project-specific workflow.
Owner:GLOBALYTICA
Predicting method of RNA two-grade structure
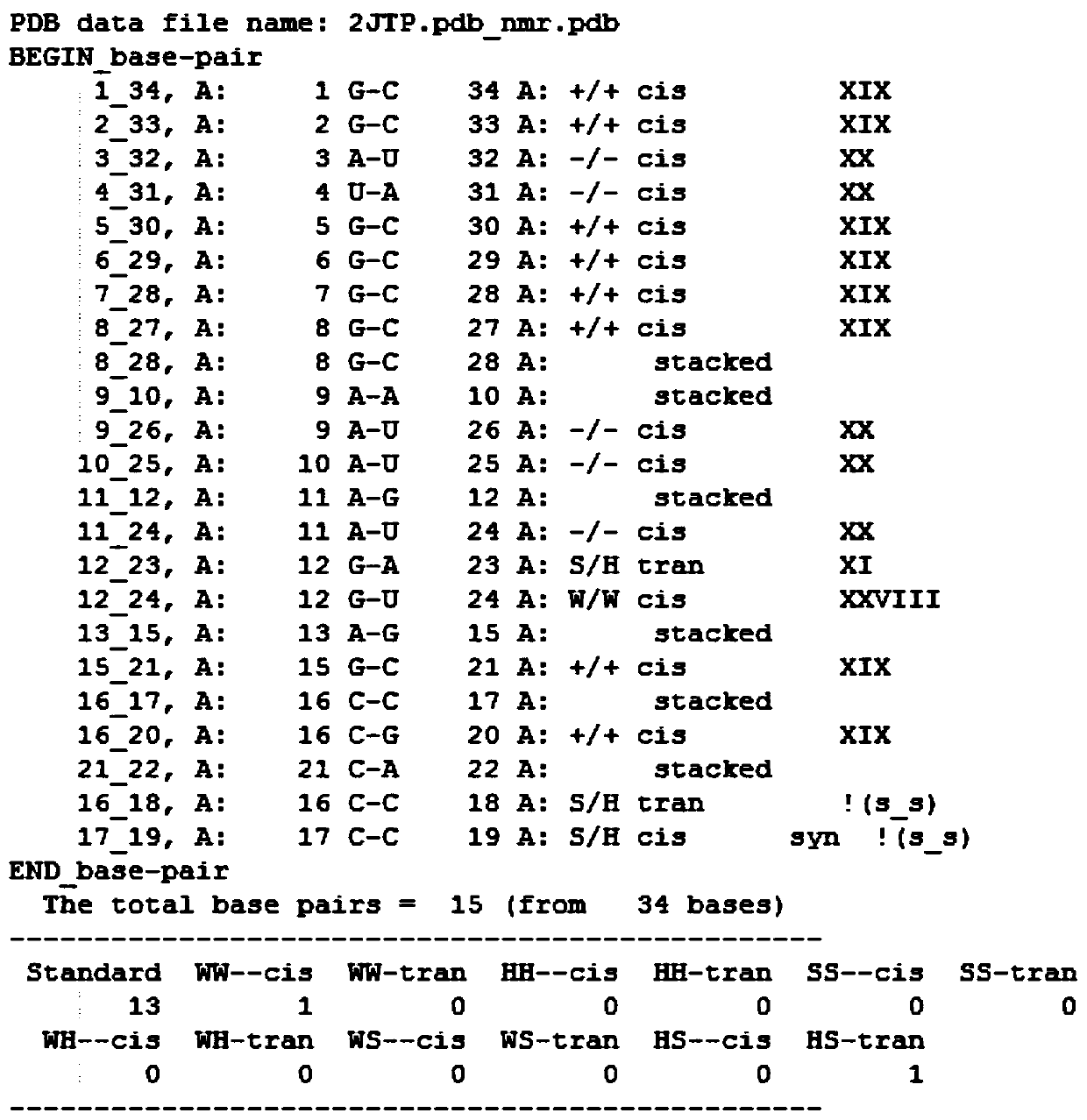
PendingCN110010194AImprove forecasting efficiencyPrediction is accurateBiostatisticsCharacter and pattern recognitionData setAlgorithm
The invention discloses a predicting method of an RNA two-grade structure. The method comprises the steps of performing data preprocessing on a PDB data set, dividing the PDB data set into an RNA first-grade sequence data set and an RNA second-grade structure data set; performing computer coding processing on the RNA first-grade sequence in the RNA first-grade sequence data set, and inputting thecoded RNA first-grade sequence as a characteristic into a machine learning model which is established based on a supervising learning algorithm, obtaining a target function, and using the RNA second-grade structure data set as an output label of the machine learning model, and training and testing the machine learning model; and finally performing RNA two-grade structure predicting by means of thetrained and tested machine learning model. According to the predicting method, a supervising learning algorithm is used and an artificial intelligence method is used for predicting the RNA two-gradestructure, thereby greatly improving predicting efficiency and realizing relatively high predicting result accuracy.
Owner:ZHEJIANG UNIVERSITY OF SCIENCE AND TECHNOLOGY
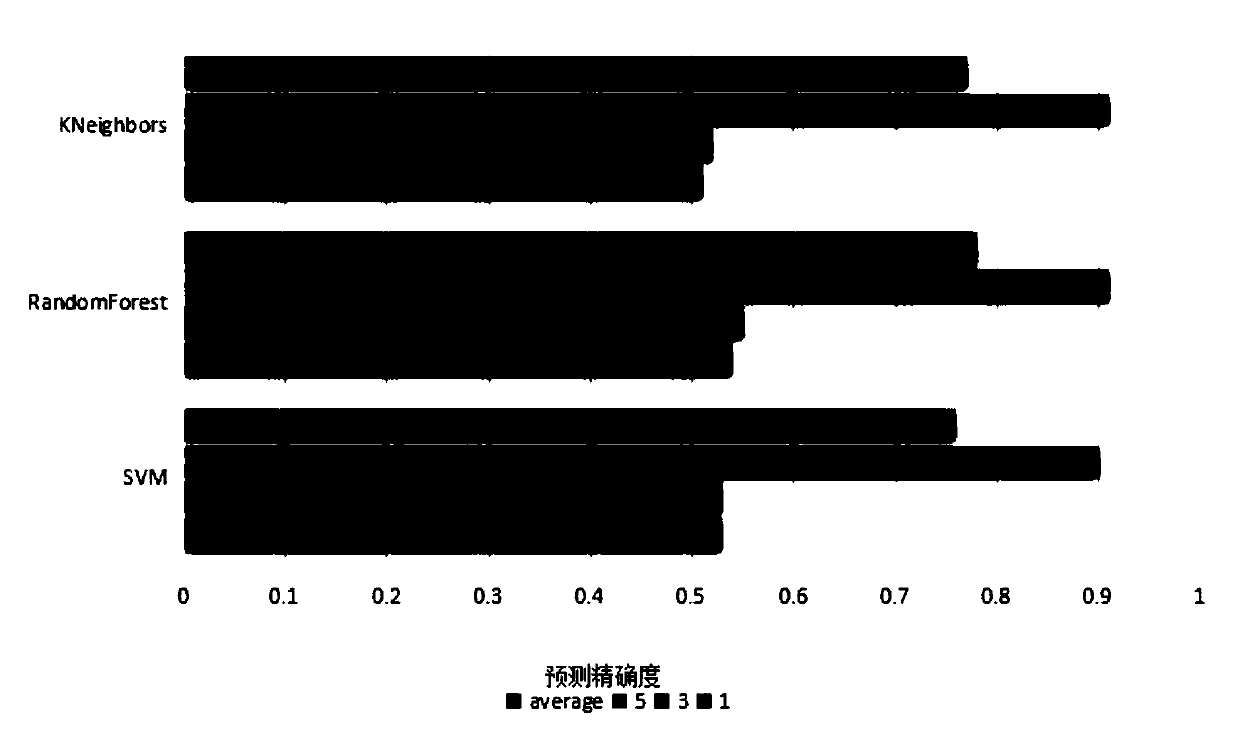
Method for integrally automatically generating pipeline designs
InactiveCN104318026AImprove design efficiencyImprove design qualitySpecial data processing applicationsGraphicsComputer number format
The invention provides a method for integrally automatically generating pipeline designs. The method includes steps of coding all commonly used pipeline elements by the aid of computers, forming foundation elements corresponding to codes and storing the foundation elements in databases; determining positions of starting points and ending points of pipelines and initial connected equipment and final connected equipment of the pipelines; collecting all elements connected with the pipelines and determining connection logical relations among the elements; determining the codes of the pipeline elements, retrieving the foundation elements of the corresponding elements from the databases according to the codes of the elements; retrieving data of the foundation elements of the first elements to form three-dimensional graphs and positioning the three-dimensional graphs at the starting points of the pipelines; computing coordinates of the positions of outlets of the first elements according to coordinates of the positions of the starting points of the pipelines and information of the data of the foundation elements of the first elements, utilizing the coordinates of the outlets as starting points of the second elements and connecting the second elements with the first elements according to set logical relations; sequentially retrieving all the elements in the pipelines from the databases, connecting the elements with one another according to coordinate positioning modes and the logical relations and forming three-dimensional models of the pipelines. The method has the advantages that the design efficiency can be greatly improved, an error rate can be reduced, and the design quality can be enhanced.
Owner:青岛鸿瑞电力工程咨询有限公司
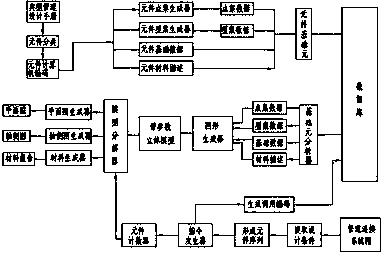
Civil air defense emergency alert information message compression encoding method based on Beidou communication functions
InactiveCN104066117ASend lessShorten sending timeNetwork traffic/resource managementNetwork topologiesComputer number formatCommon word
The invention provides a civil air defense emergency alert information message compression encoding method based on Beidou communication functions. The method comprises: a civil air defense common word code library is built; words included in the code library are expressed with corresponding codes and the codes are encapsulated into subframes; characters not included in the code library are expressed with corresponding computer codes; the computer codes and the subframes are connected according to the order of the original message to form a message text, and a message header and a message tail are added to the message text to form a to-be-sent message; it is determined if the length of the to-be-sent message is greater than the maximum length, L bytes, permitted by the Beidou system, and if so, the to-be-sent message is segmented into a plurality of sub-messages, the length of which is no greater than L bytes, for sending, each sub-message having a message header and a message tail; otherwise, the to-be-sent message is sent directly. The method can reduce the length of the message and the sending times of a long message. The alert information notifying time is shortened, and the flow is saved. The method is simple and easy to implement with good reliability.
Owner:ELECTRONICS ENG COLLEGE PLA
Information system user password generation method
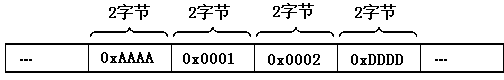
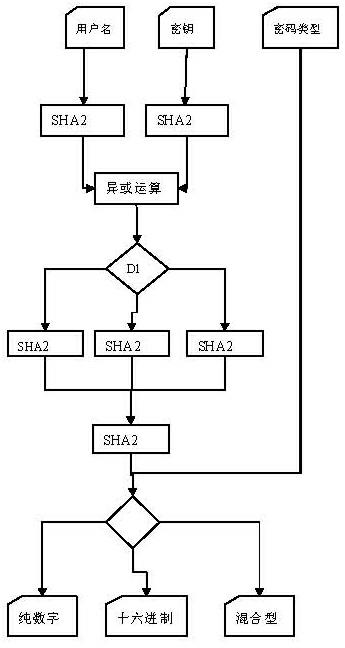
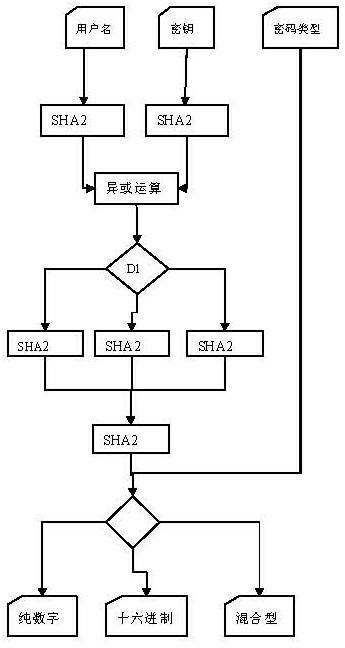
InactiveCN102222188AEnough securitySave resourcesPlatform integrity maintainancePasswordComputer number format
The invention relates to an information system user password generation method, which belongs to the technical field of computer coding, and particularly relates to a password generation method applied in the information system management of a computer. The method comprises the step of carrying out several-time hashing to input information to obtain a corresponding password. The method has the advantages that the safety of algorithm is sufficient, and the password does not need to be stored in a database, so that the resources of a server and a database can be saved, and the implementation mode is flexible and simple.
Owner:KUNMING ENG & RES INST OF NONFERROUS METALLURGY
Method of detecting surface shape of reflection element based on dual-frequency orthogonal grating projection
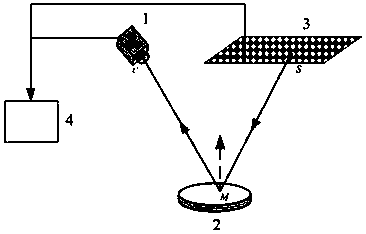
InactiveCN108426539ASolve the vertical direction separatelySolve the problem of fringe projection in the horizontal directionUsing optical meansDual frequencyPhase shifted
The invention provides a method of detecting the surface shape of a reflection element based on dual-frequency orthogonal grating projection. When the method is used to detect the reflection optical surface shape, basic devices comprise a CCD sensor, a to-be-detected element, an LCD display and a computer. The LCD display sequentially displays phase-shifting fringe patterns generated by computer coding, and the CCD receives and obtains the deformed fringe patterns reflected through the surface of the to-be-detected element. If a physical grating and a mechanical device are used for phase shifting in a measuring system, switching in a vertical grating and a horizontal grating needs to be carried out, and a corresponding phase shifting amount is further completed. In order to avoid grating switching in the two directions and realize the accurate phase shifting amount, a dual-frequency orthogonal grating phase shifting method based on least squares iteration is proposed, the dual-frequency orthogonal grating is applied to phase deflectometry, no grating needs to be replaced in a measuring process, an accurate phase shifting amount is not needed either, and phase distribution in two directions can be acquired at the same time. The method has the beneficial effects of being high in measuring result accuracy and applicable to high-accuracy three-dimensional surface shape measurement.
Owner:SICHUAN UNIV
Programmable conversion hardware
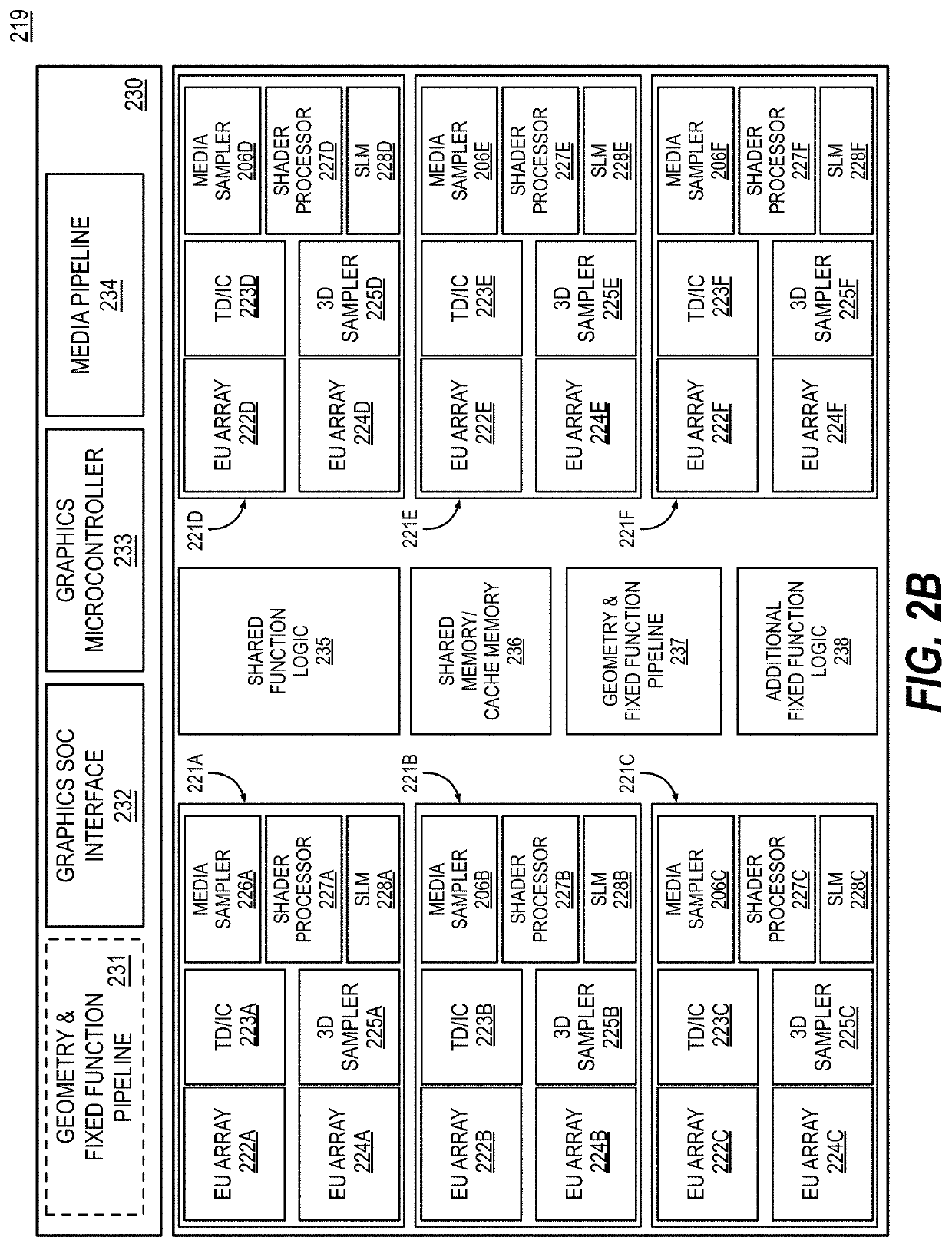
ActiveUS20210072955A1Operational speed enhancementDigital data processing detailsComputer number formatData format
An apparatus to facilitate a computer number format conversion is disclosed. The apparatus comprises a control unit to receive to receive data format information indicating a first precision data format that input data is to be received and converter hardware to receive the input data and convert the first precision data format to a second precision data format based on the data format information.
Owner:INTEL CORP
Coding scheduling control method and scheduling controller
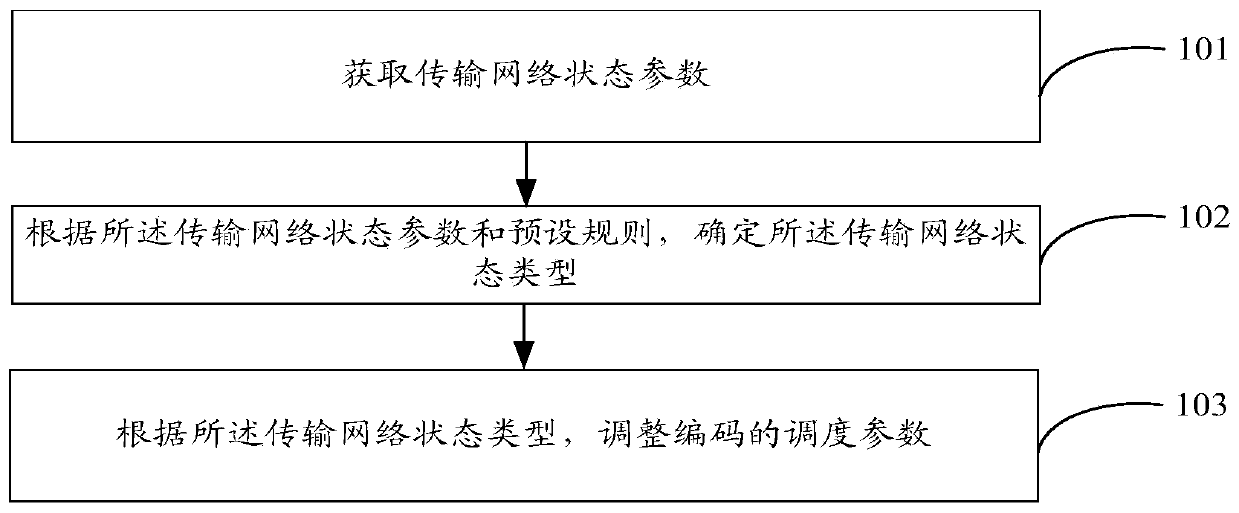
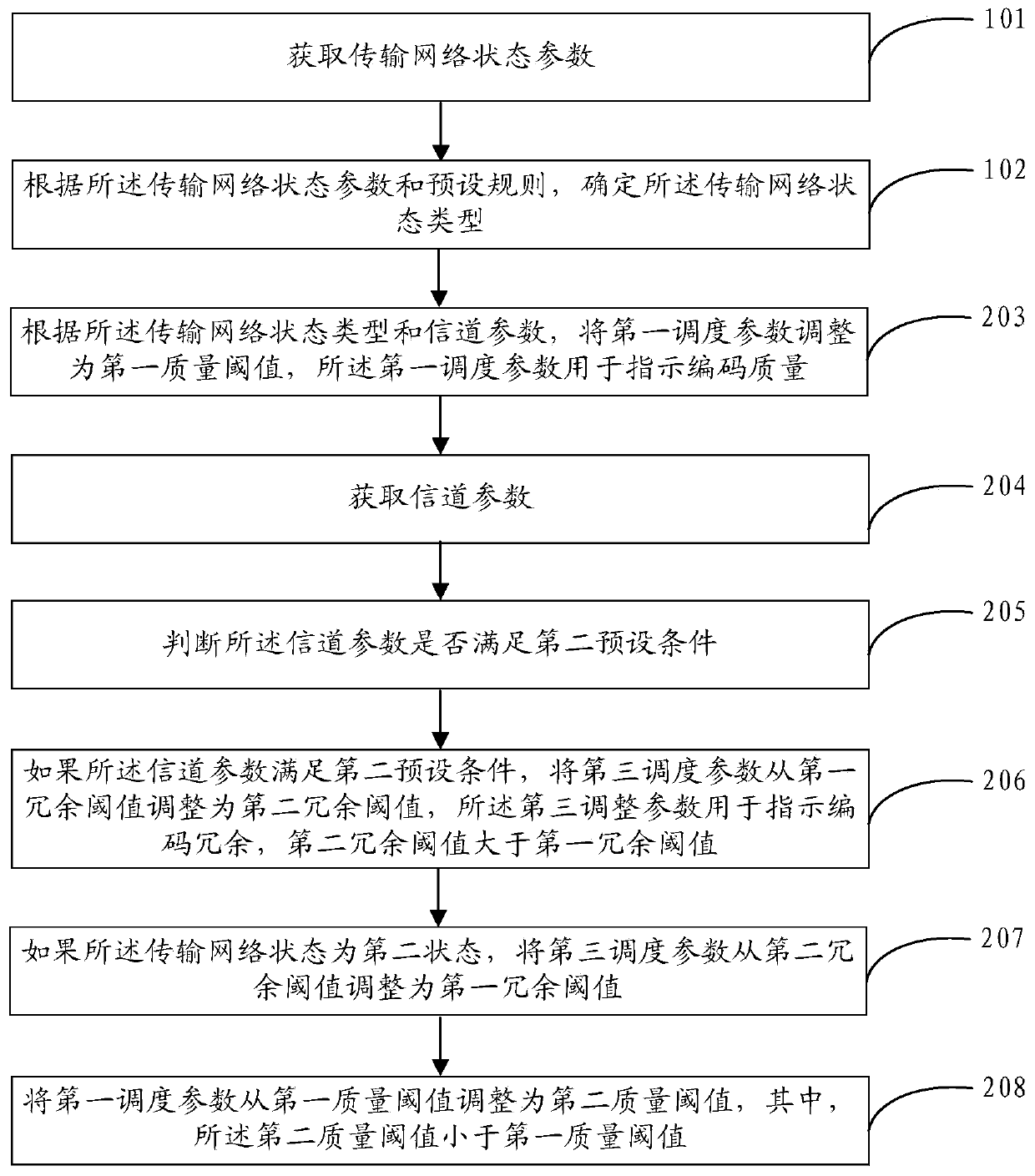
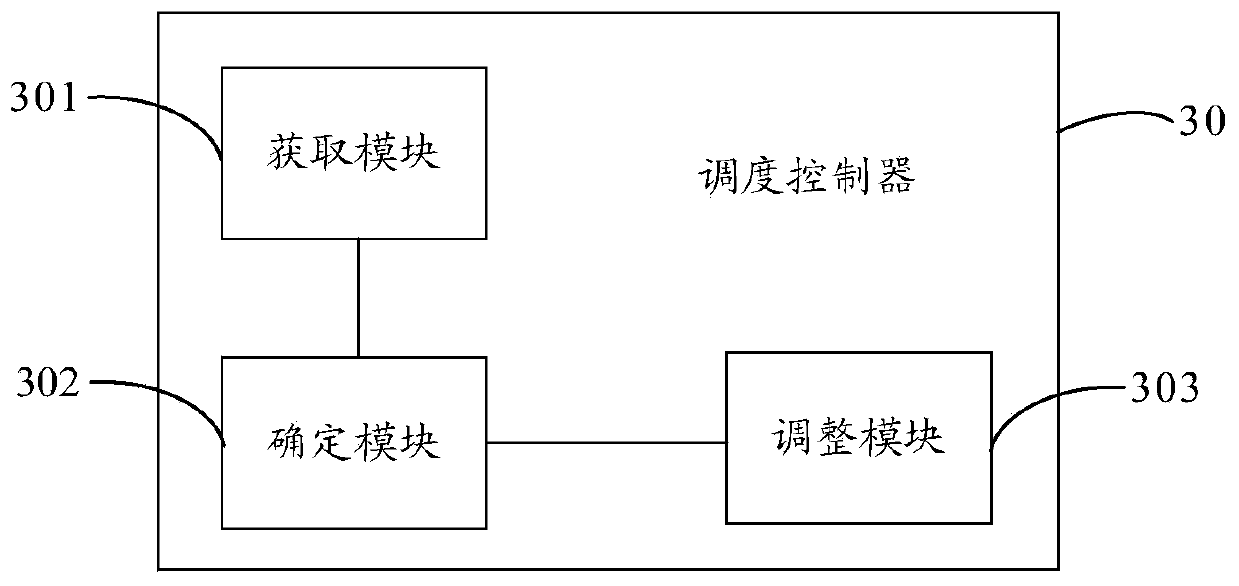
InactiveCN111246262ADigital video signal modificationSelective content distributionComputer number formatDistributed computing
The invention provides a coding scheduling control method and device, and relates to the technical field of computer coding. The method comprises the steps: obtaining a transmission network state parameter; determining the transmission network state type according to the transmission network state parameter and a preset rule; and adjusting a scheduling parameter of the code according to the transmission network state type. According to the embodiment of the invention, the display frame can be dynamically adjusted at a far end.
Owner:XIAN WANXIANG ELECTRONICS TECH CO LTD
Method for designing structurally controllable tight arrangement perfect vortex array mask
Owner:HENAN UNIV OF SCI & TECH
A 3D code and a method for recognizing the 3D code
InactiveCN109447208ALarge encoding capacityEasy to makeRecord carriers used with machinesSensing by electromagnetic radiationComputer graphics (images)Computer number format
The present invention provides a 3D code and a method for recognizing the 3D code. The 3D code of the present invention comprises a 3D code surface, wherein the 3D code surface comprises an identification unit having three dimensions, and at least two colors are provided in the identification unit. The 3D code can be printed by 3D printing technology or laser engraving technology, or machining technology, to identify convex and concave features on two-dimensional codes by using double cameras, and to encode 3D codes by computer, so that 3D codes can be recognized by 3D codes, and the encodingcapacity of 3D codes is larger than that of two-dimensional codes and three-dimensional codes. Moreover, the 3D code of the invention is simple to manufacture, and greatly increases the capacity of storing the information in a carrier similar to the 3D code in the future world.
Owner:北京目瞳科技有限公司
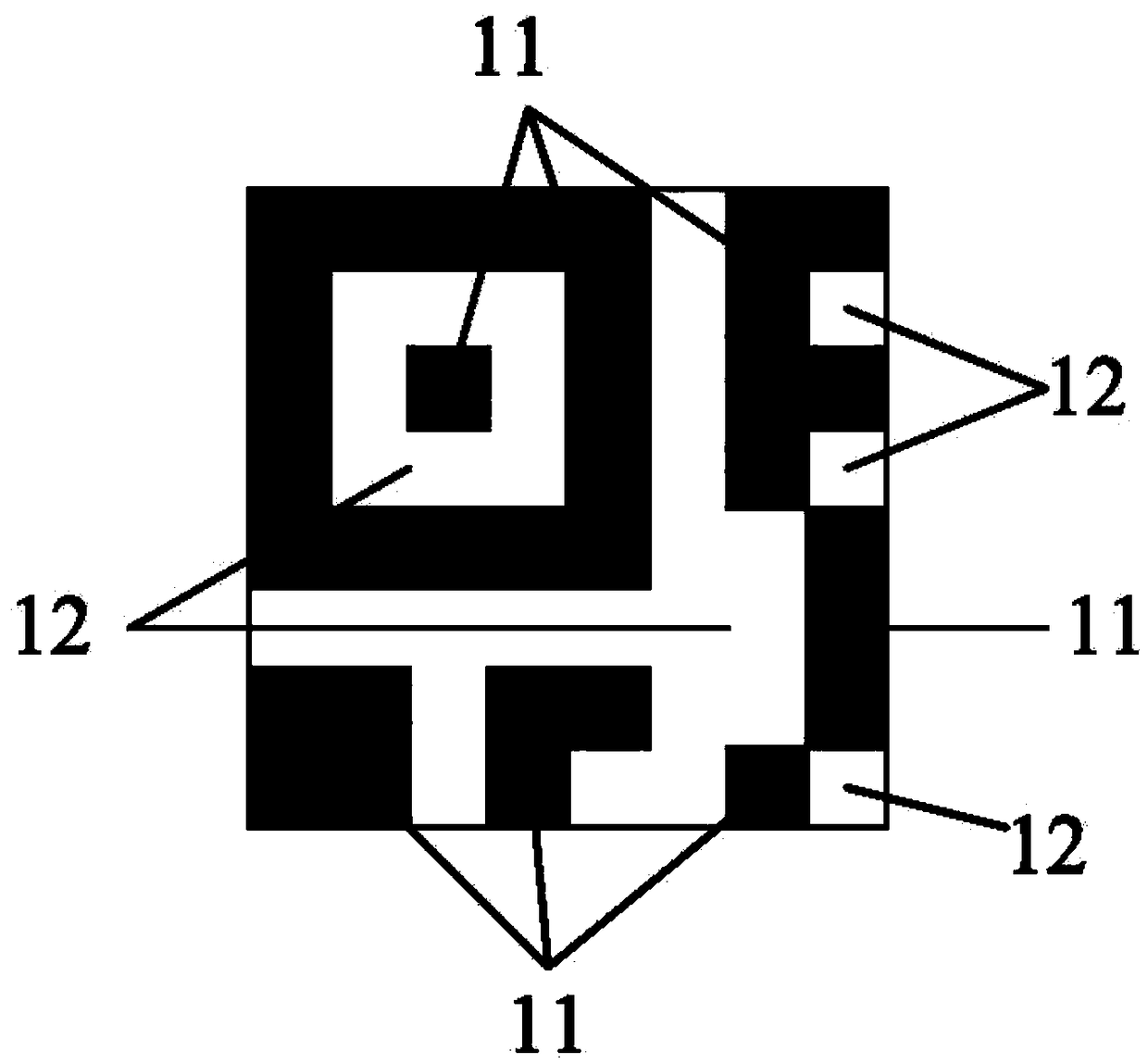
Approximate evaluation and monitoring system of trademarks based on stroke order algorithm and method
InactiveCN108897722AAvoid violationsHigh similarityData processing applicationsNatural language data processingInformation processingTrademark
The invention relates to the field of trademark information processing and discloses an approximate evaluation and monitoring system of trademarks based on a stroke order algorithm and a method. According to the invention, the strokes of Chinese characters can be converted into computer codes to form a set of stroke coded data with a certain combination order, and the approximate words of variouswords can be found through a retrieval contrast algorithm, and the trademark text can be split into single words, and an approximate value can be calculated. The method can be applied to the review evaluation and tort monitoring of the character trademark part.
Owner:重庆智荟数创科技有限公司
Features
- R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
Why Patsnap Eureka
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Social media
Patsnap Eureka Blog
Learn More Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com