Information system user password generation method
A user password and information system technology, applied in the field of password generation in computer information system management, can solve problems such as password calculation, achieve flexible implementation methods, and save server and database resources
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment 1
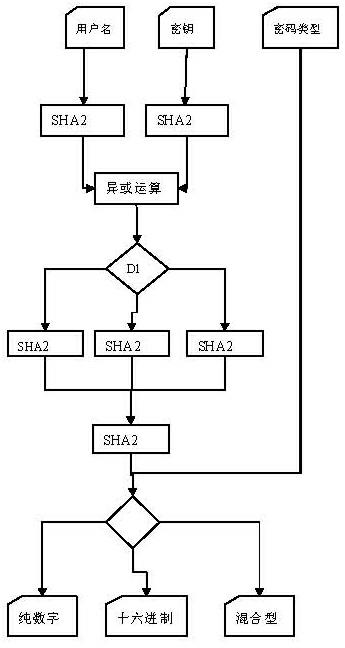
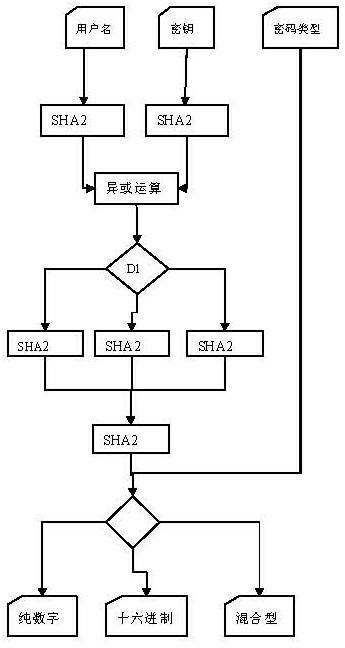
[0040] Example 1: Zhang Sang is a new employee of company A, and the information center of company A needs to assign Zhang Sang the user account and password of the two systems of office and finance. For the convenience of employees, all systems in the company can use a unified user name to log in for an employee, but the passwords of each system are different, and the initial password assigned to Zhang Sang is also different.
[0041] At present, the user name "zs" has been assigned to Zhang Sang, and the system needs to assign an initial password to Zhang San.
[0042] The distribution process is as follows: (1) First, the system uses the user name zs and the corresponding password 123 of the office system to generate two information digests DG1 and DG2 through the SHA224 algorithm, forming two 224bit (28 byte) byte arrays, the contents are as follows.
[0043] DG1
zs
737375AC94A60C0701B33555A48A9A7A7D15CBE88F7CD41AC770F8A6
DG2
123
26D6A8AD97C7...
Embodiment 2
[0060] Example 2: In addition to the office system, the financial system also needs to assign a password to Zhang Sang. The user name is still zs, but the system key corresponding to the financial system is 1234, which generates a five-digit pure digital password.
[0061] The results of each step are as follows: (1) First, the input calculation is performed, and the information digests DG1 and DG2 of "zs" and "1234" are calculated through the SHA384 algorithm, forming two 384bit (48 byte) byte arrays as listed in the following table.
[0062] DG1
[0063] (2) From the first unit of the array to the last unit of DG1 and DG2, XOR operations are performed on the bytes corresponding to DG1 and DG2 byte by byte, and a new byte array DG3 is formed as a result.
[0064] DG3
[0065] (3) Take the content DA of the first byte of DG3, convert it to 218 in decimal, and get the value of D1 as 2 after calculating the remainder with 3.
[0066] (4) The relationship betw...
Embodiment 3
[0072] Implementation example 3: Li Si, a new employee of company A, has been assigned a user name of ls, and needs to be assigned an unchangeable, alphanumeric, 7-digit password in the internal examination system, and the system password is abcd.
[0073] (1) First perform input calculations, calculate the information digests DG1 and DG2 of "ls" and "abcd" through the SHA512 algorithm, and form two 512bit (64 byte) byte arrays as listed in the following table.
[0074] DG1
BFA09D34CF95F35BC6BE51AFC67DD211C114EBD4F74AD27BE3B76B5C08EBCCF00A07B65C1FA93C65A0CB5120F1DE23D4127CFFB11A88E705CBAD7D1565582A8C
DG2
B09B6BA7452D6FD247F05658F3EDA1B372875D1FF8B6FACB1EBFB9D089CB336220852576E02608BE01AF0BA4353EE014374B74C7B480E9C0B96264605AF77FDB
[0075] (2) From the first unit of the array to the last unit of DG1 and DG2, XOR operations are performed on the bytes corresponding to DG1 and DG2 byte by byte, and a new byte array DG3 is formed as a result.
[0076...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com