An attack message identification method, device and core equipment
A technology of attack message and identification method, which is applied in the field of attack message identification method, device and core equipment, can solve the problems of slow identity authentication and low efficiency of authentication request processing, so as to improve processing efficiency and avoid slow identity authentication or authentication The effect of failure
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment 1
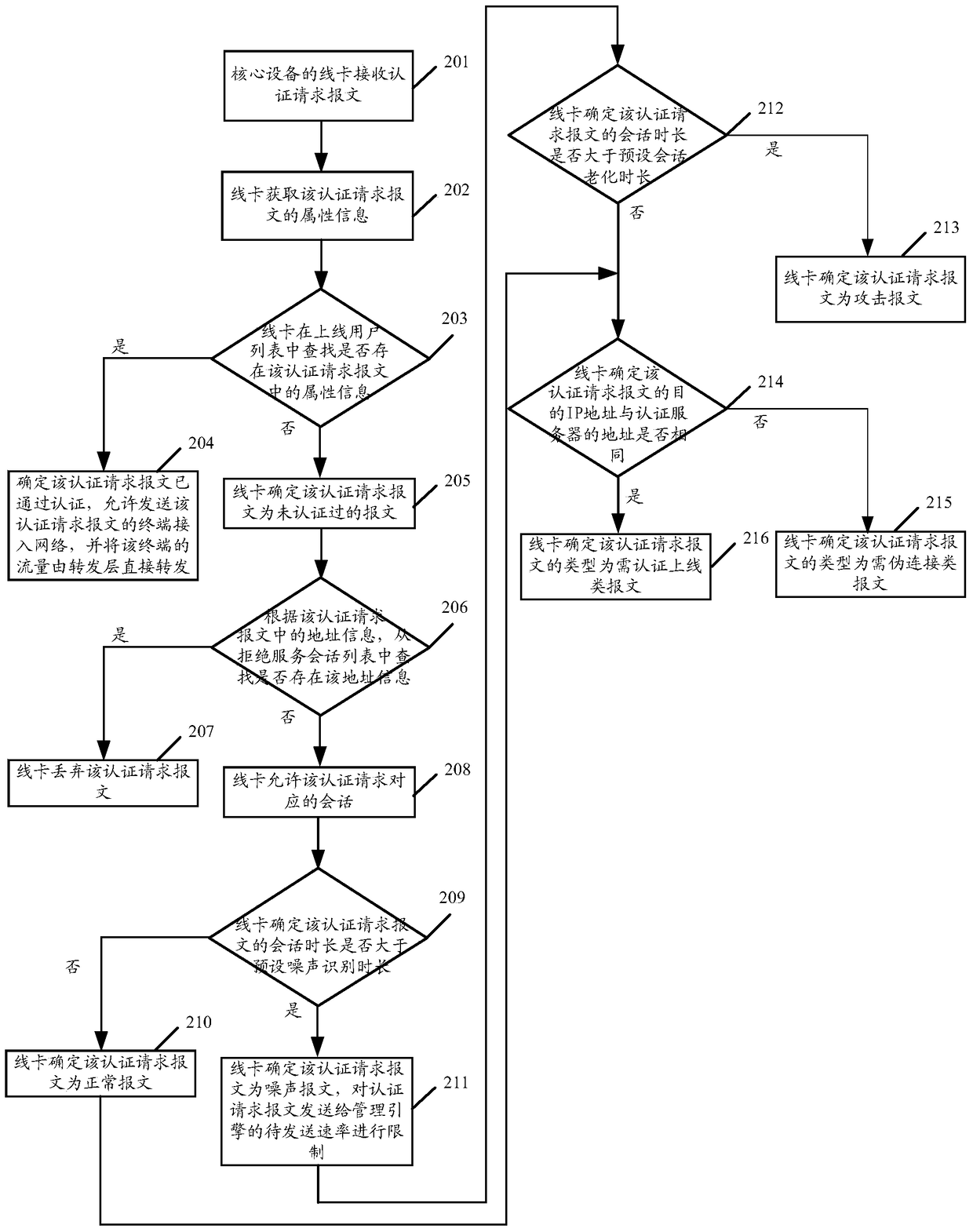
[0075] figure 2 The flow chart of the attack message identification method provided in Embodiment 1 of the present invention specifically includes the following processing steps:
[0076] Step 201, the line card of the core device receives the authentication request message.
[0077] As the gateway of all network users, the core device uploads the authentication of the entire network for centralized management, and the line card of the core device receives the authentication request message.
[0078] Step 202, the line card obtains the attribute information of the authentication request message.
[0079] In this step, the attribute information of the authentication request message includes the source network protocol (IP, Internet Protocol) address, media access control (MAC, Media Access Control) address, authentication port PORT, virtual local area network (VLAN) carried in the authentication request message. Identification (VID, Virtual Local Area Network ID).
[0080] ...
Embodiment 2
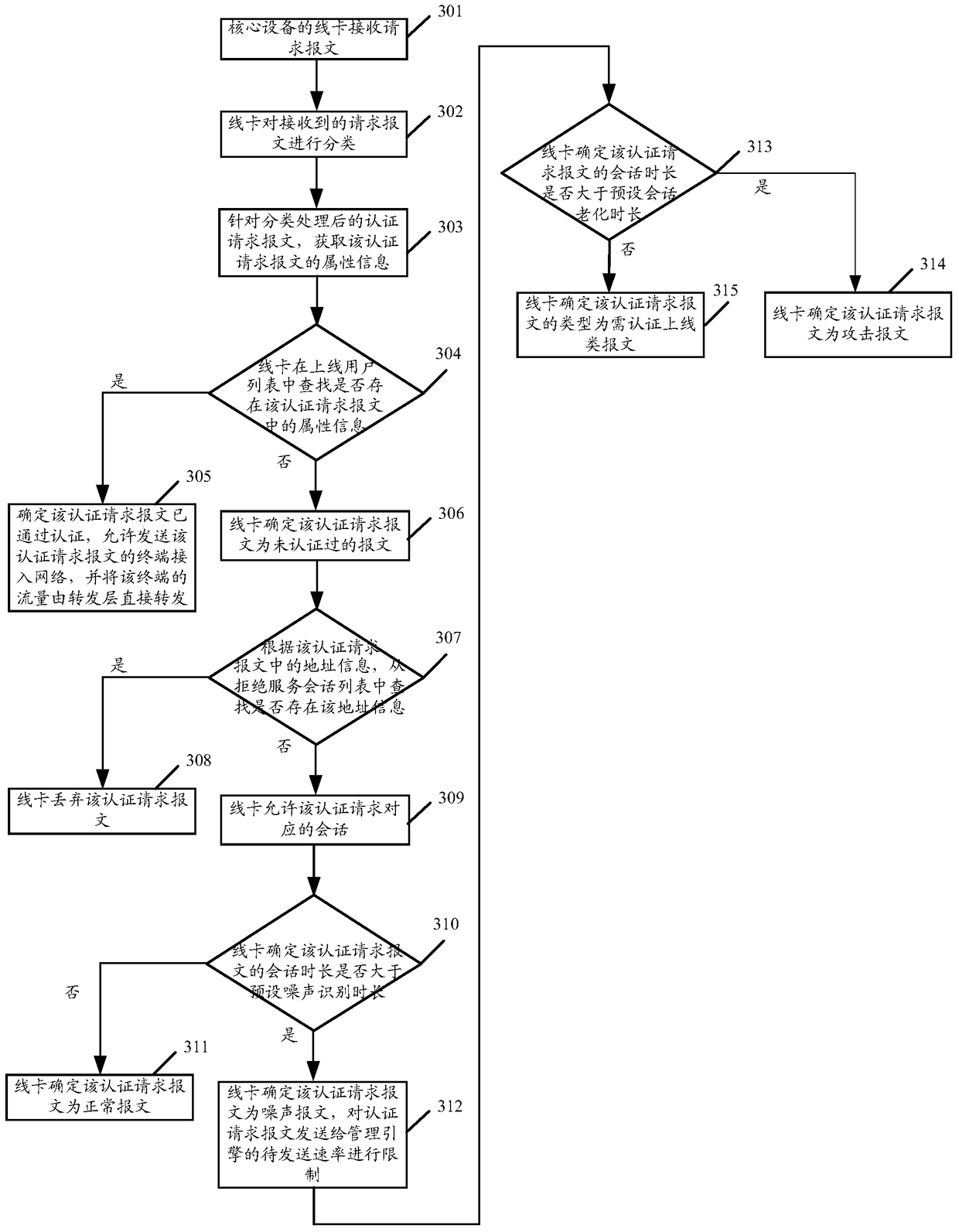
[0112] image 3 The flow chart of the attack message identification method provided by Embodiment 2 of the present invention specifically includes the following processing steps:
[0113] Step 301, the line card of the core device receives the request message.
[0114] Step 302, the line card classifies the received request message.
[0115] Specifically, for each request message received at the entrance of the core device, determine whether the destination IP address in the request message is the same as the address of the authentication server, if not, determine that the request message is a message that requires a fake connection ; If they are the same, further determine whether the request message carries authentication information, that is, whether it is an authentication request message, if yes, determine that the request message is a message that requires authentication to go online, if not, determine that the request message is a redirect class message. The line car...
Embodiment 3
[0145] Based on the same inventive concept, according to the attack packet identification method provided in the above-mentioned embodiments of the present invention, correspondingly, Embodiment 3 of the present invention also provides an attack packet identification device, the structural diagram of which is as follows Figure 4 shown, including:
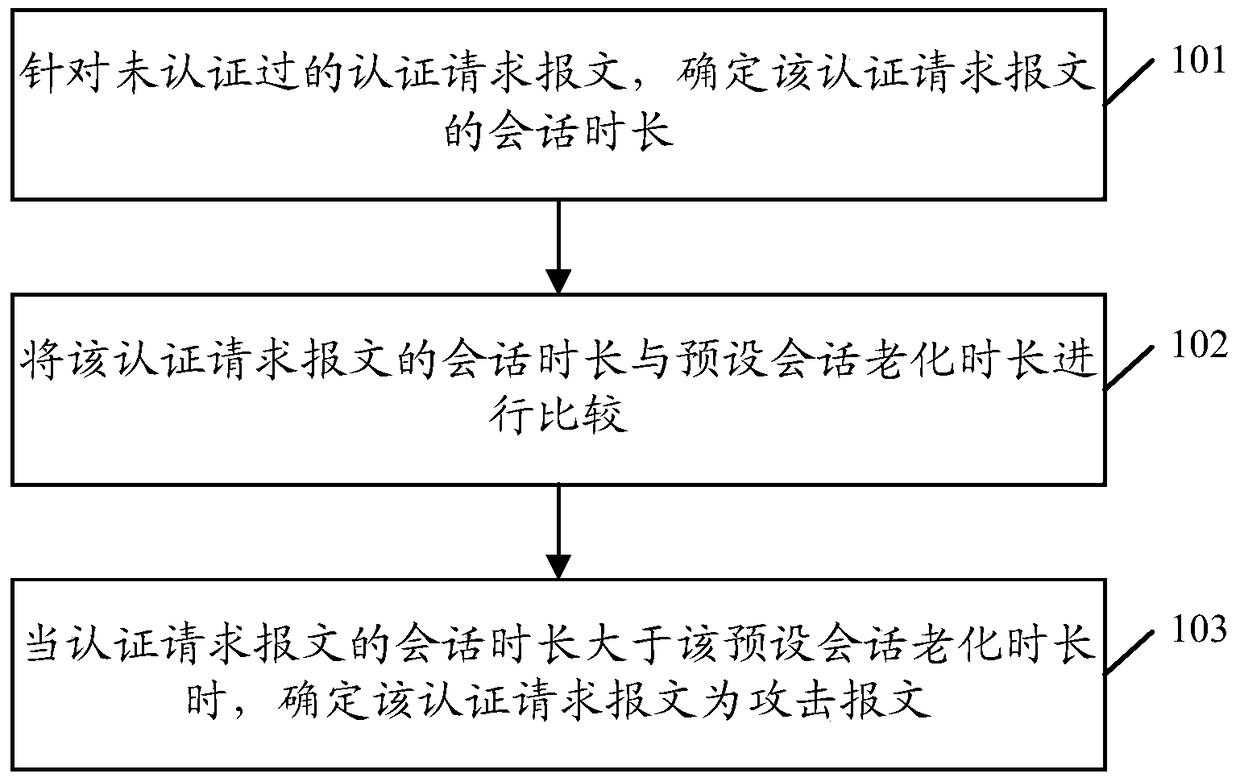
[0146] The first determining unit 401 is configured to determine the session duration of the authentication request message for the unauthenticated authentication request message;
[0147] The first comparison unit 402 is configured to compare the session duration of the authentication request message with a preset session aging duration;
[0148] The second determining unit 403 is configured to determine that the authentication request message is an attack message when the session duration of the authentication request message is greater than the preset session aging time.
[0149] Further, the first determining unit 401 is speci...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com