Malicious code detection method and system
A malicious code detection and malicious code technology, applied in the direction of instruments, electrical digital data processing, platform integrity maintenance, etc., can solve the problems of poor detection effect and achieve the effect of reliable analysis and recognition ability
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
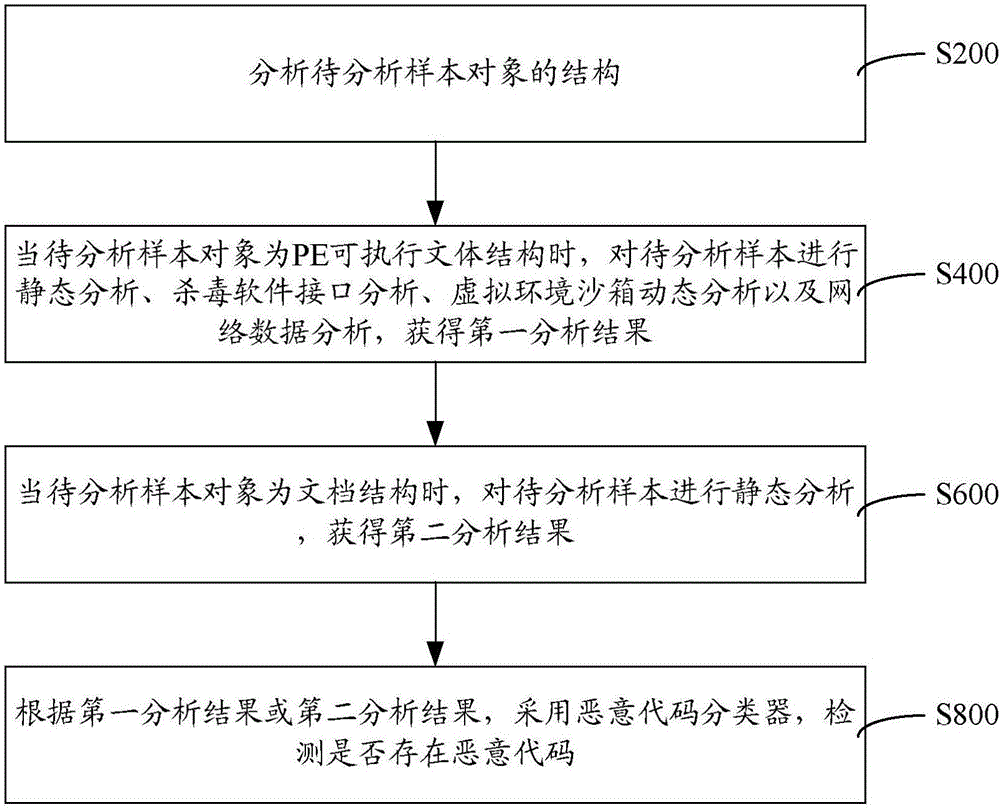
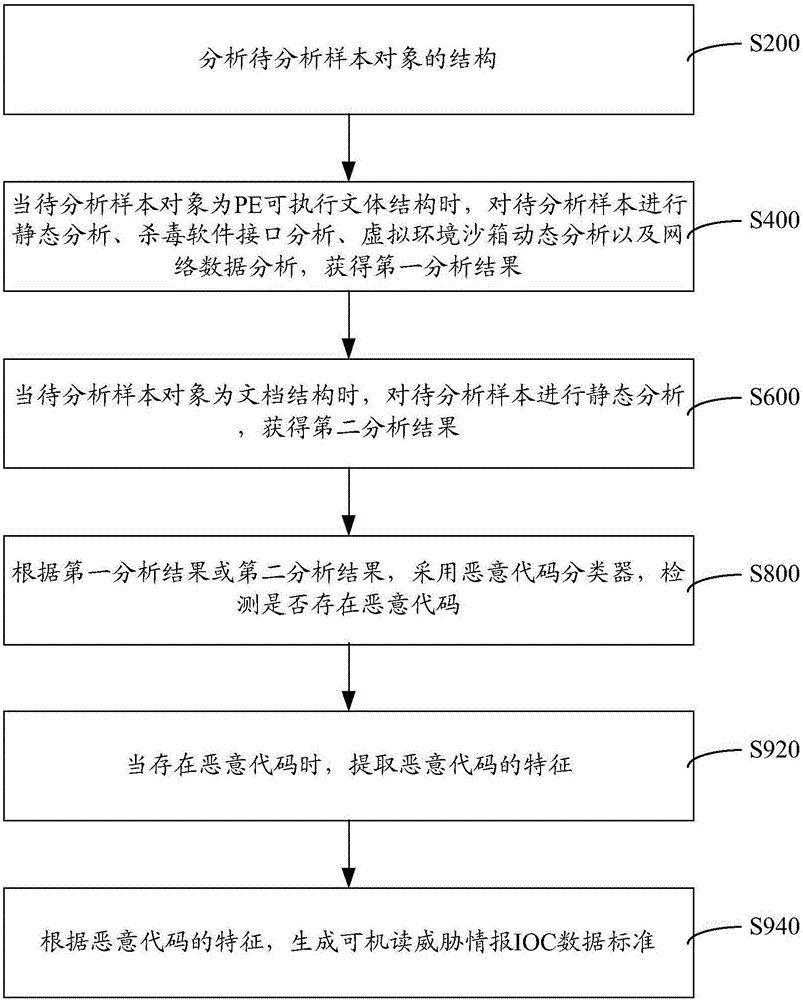
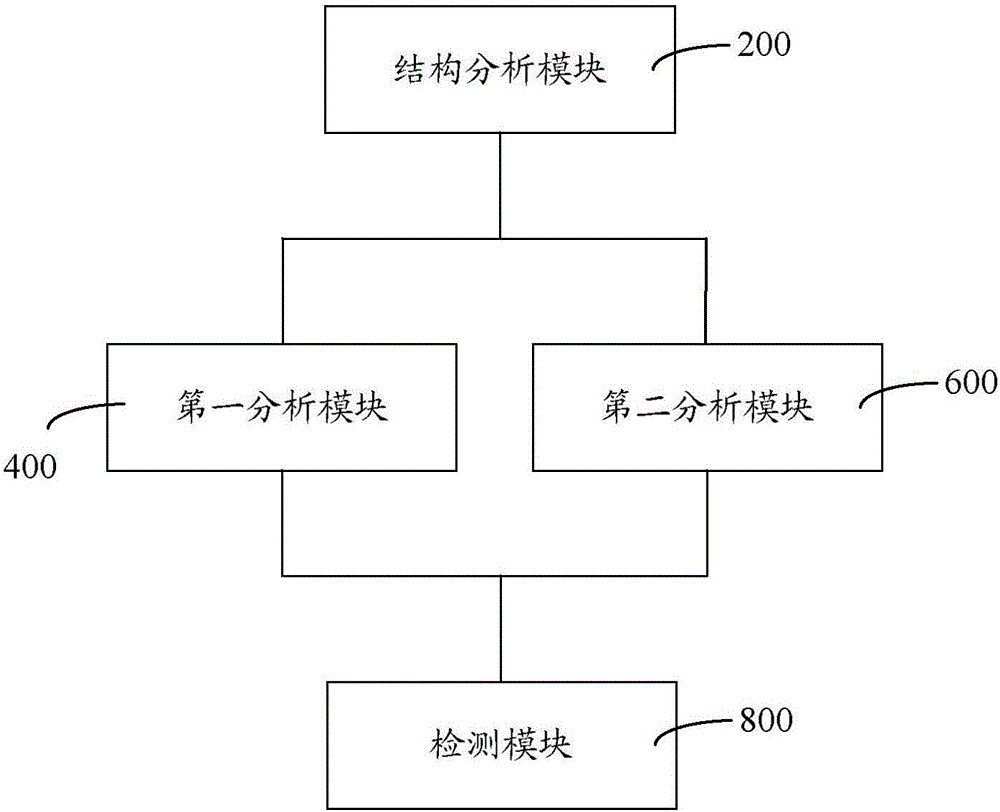
[0021] like figure 1 As shown, a malicious code detection method includes steps:
[0022] S200: Analyze the structure of the sample object to be analyzed, the structure includes a PE executable text structure and a document structure.
[0023] Obtain the sample to be analyzed, identify the sample object to be analyzed, and further analyze the structure of the sample object to be analyzed, wherein the structure of the sample object to be analyzed includes a PE (Windows Preinstallation Environment, Windows Preinstallation Environment) executable text structure and document structure. PE is the pre-installed data of Windows, a computer system. For the structure of different sample objects to be analyzed, different detection and analysis methods are required for further processing.
[0024] S400: When the sample object to be analyzed is a PE executable style structure, perform static analysis, antivirus software interface analysis, virtual environment sandbox dynamic analysis, a...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com