Dynamic and static combined software security test method
A security testing, dynamic and static technology, applied in the field of dynamic and static software security testing, can solve problems such as path space explosion, achieve the effect of changing blindness, improving vulnerability mining methods, and solving path state space explosion
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment 1
[0027] Embodiment one: see Figure 4 , the software safety testing method of dynamic and static combination of the present invention, specifically comprises the following steps:
[0028] 1) Disassembling the executable program (software) under test to obtain assembly code;
[0029] 2) Convert the assembly code into a unified intermediate assembly language form, so as to shield the differences in the underlying specific languages;
[0030] 3) Generate the function call graph (CG) and control flow graph (CFG) of the file according to the intermediate assembly language form;
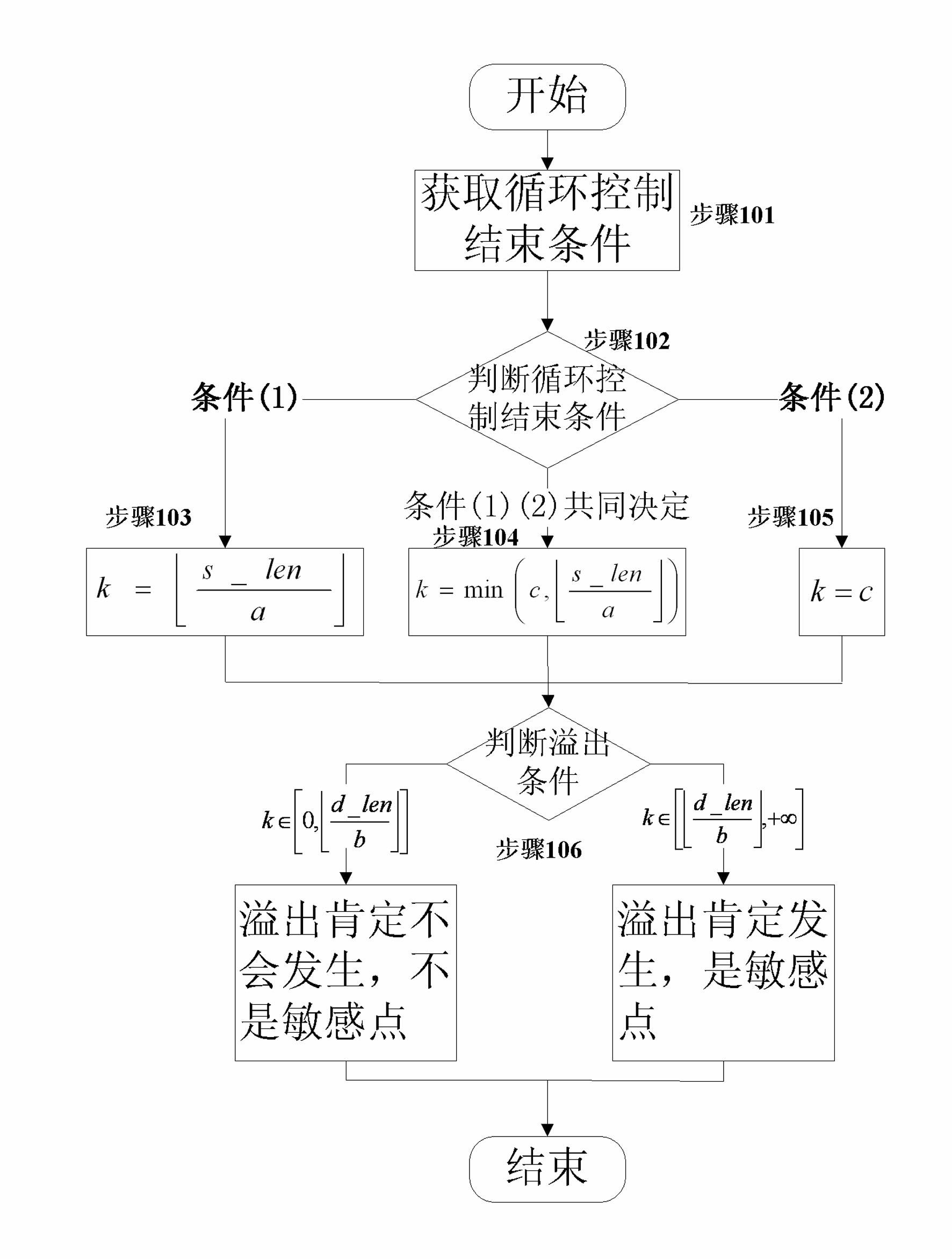
[0031] 4) Define the function characteristics of sensitive points, and find out the functions of system vulnerable points (ie, sensitive points) through static analysis of the function call graph (CG);
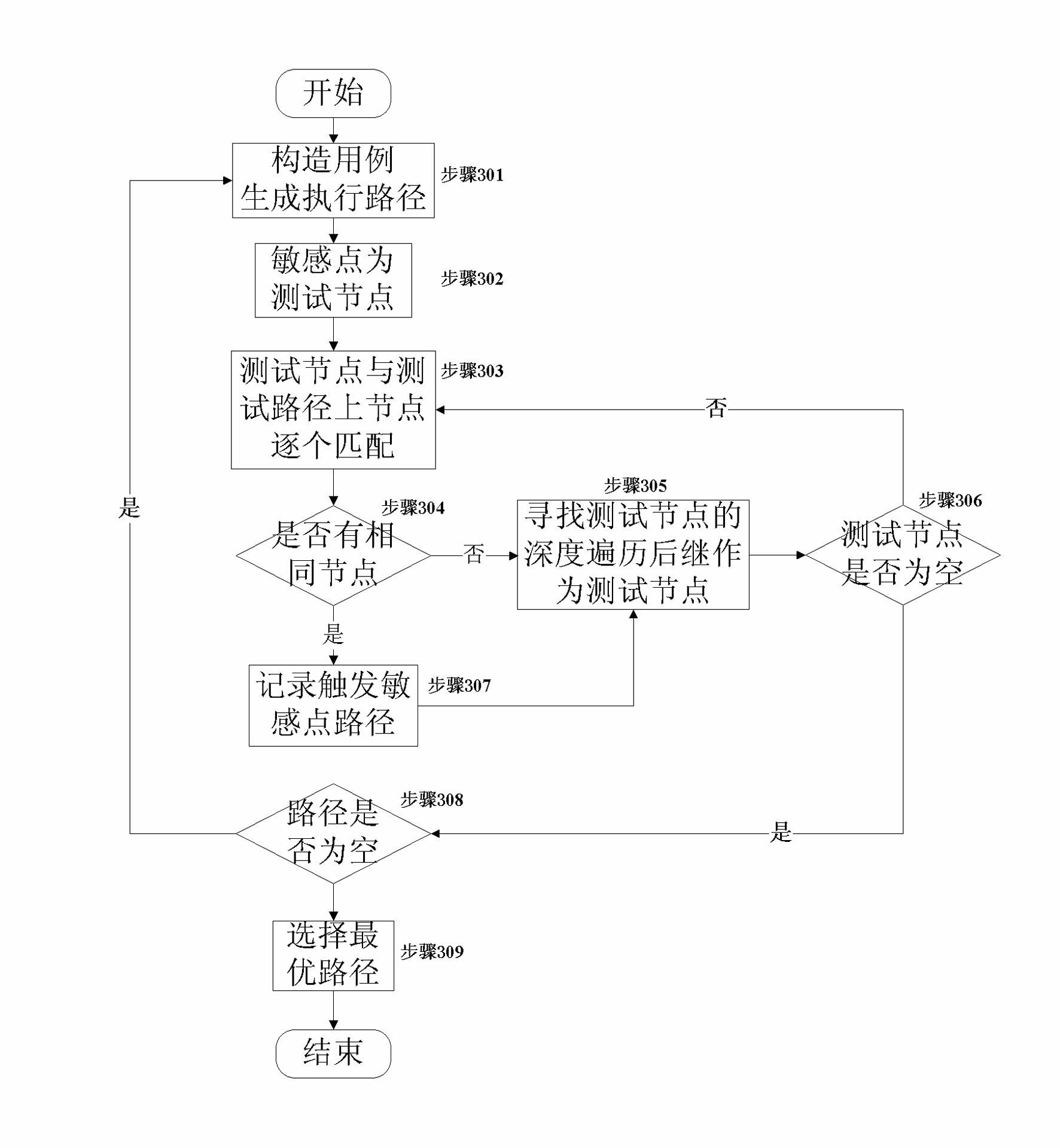
[0032] 5) Use dynamic analysis method to construct appropriate test cases, run the executable program under test, generate and record the execution path;
[0033] 6) According to the function call graph ...
Embodiment 2
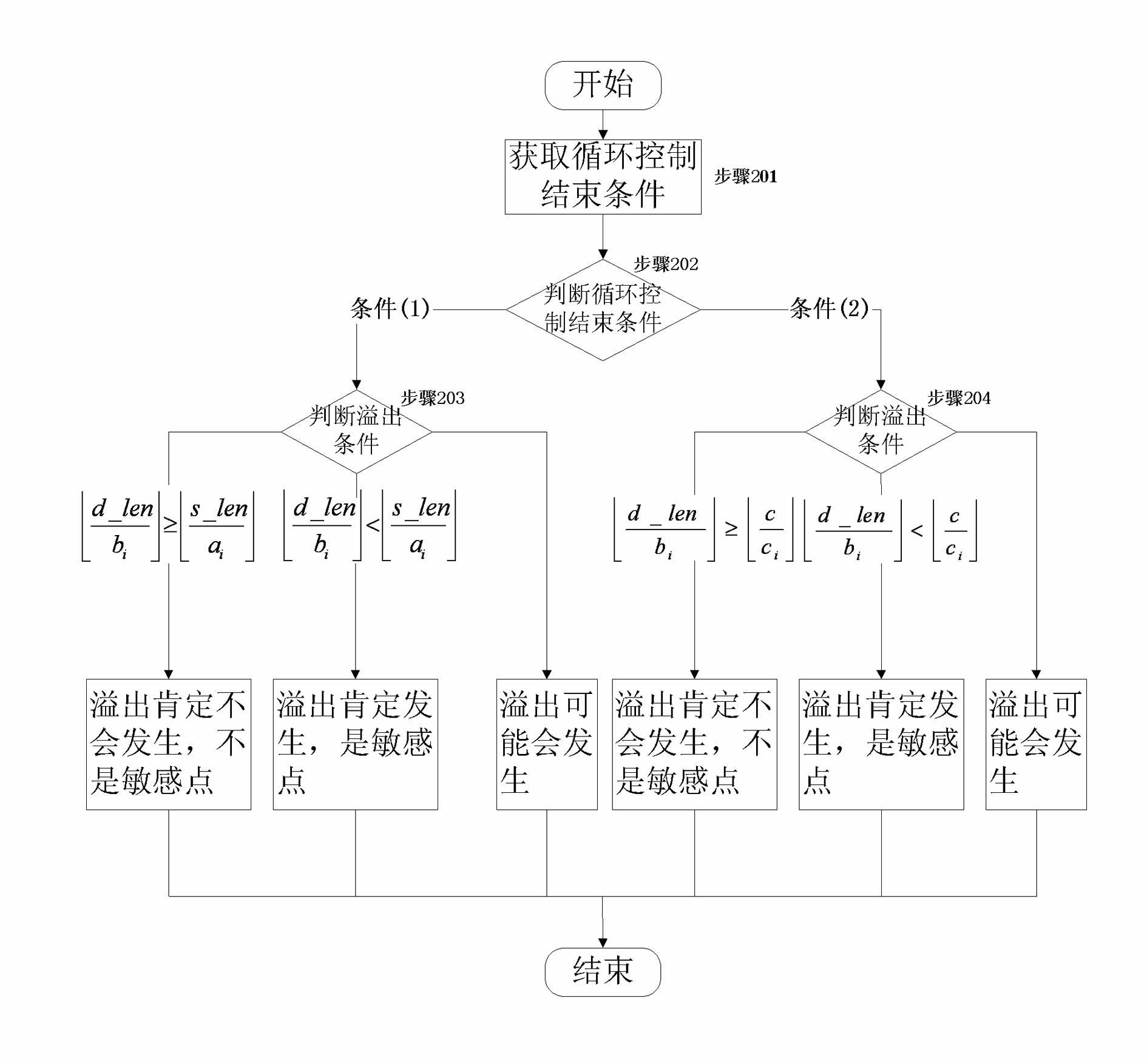
[0036] Embodiment two: the software safety testing method of the dynamic and static combination of the present embodiment is different from embodiment one, in step 3), by writing IDA plug-in, realizes the program control flow graph (CFGs) and function call of the tested program Graph (CG) generation. The specific generation of the control flow graph is specific, because there are multiple CFGs, so the plural form CFGs). In step 4), two types of sensitive points are defined, namely: calling an unsafe function and looping memory write errors.
Embodiment 3
[0037] Embodiment three: the software security testing method of the dynamic and static combination of the present embodiment is different from embodiment two in that in step 5), a test case is randomly constructed to cover as many code tree branches as possible for Generate execution paths. In step 6), according to the principle of depth-first traversal, find the path from the sensitive point to a certain node of the generated path.
[0038] The software safety testing method of dynamic and static combination of the present invention only uses 12 intermediate assembly language statements, replaces more than 300 instructions (in step 2) of the CISC (Complex Instruction Set Computer) instruction set of X86), effectively improves the traditional Vulnerability mining method improves the efficiency of software security testing.
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com