Multisource-to-multi-target approaching testing method performed based on parallel symbols
A technology of approximation testing and symbolic execution, which is applied in the field of multi-source and multi-target approaching testing based on parallel symbolic execution, can solve the problems of low test efficiency, achieve high-efficiency software security parallel scheduling tests, improve efficiency, and solve the effects of blindness
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment 1
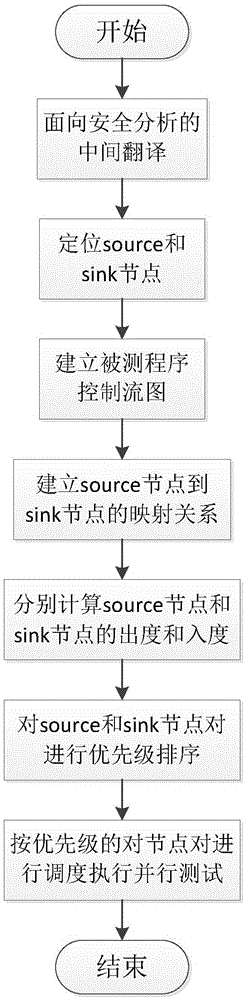
[0044] Embodiment one, see figure 1 As shown in , a multi-source and multi-target approach testing method based on parallel symbolic execution includes the following steps:
[0045] Step 1. Translate and transform the program under test by using an intermediate language oriented to safety analysis, and locate the source node of the input function and the sink node of the dangerous function;
[0046] Step 2. Utilize the IDA plug-in to generate the control flow graph and function call graph of the program under test, analyze the set of call paths from the source node to the sink node, and establish a multi-source to multi-target mapping relationship between the source node and the sink node;
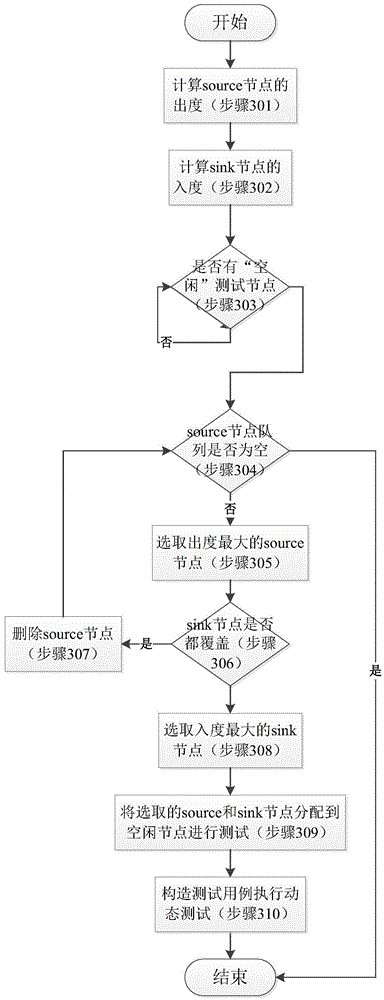
[0047] Step 3. Calculate the out-degree of the source node and the in-degree of the sink node, and calculate the test priority of the source and sink node pair, sort the test priority, select the source node with a larger out-degree as the test starting point, and compare the selected sour...
Embodiment 2
[0049] Embodiment two, see Figure 1~3 As shown in , a multi-source and multi-target approach testing method based on parallel symbolic execution includes the following steps:
[0050] Step 1. Translate and transform the program under test by using an intermediate language oriented to safety analysis, and locate the source node of the input function and the sink node of the dangerous function;
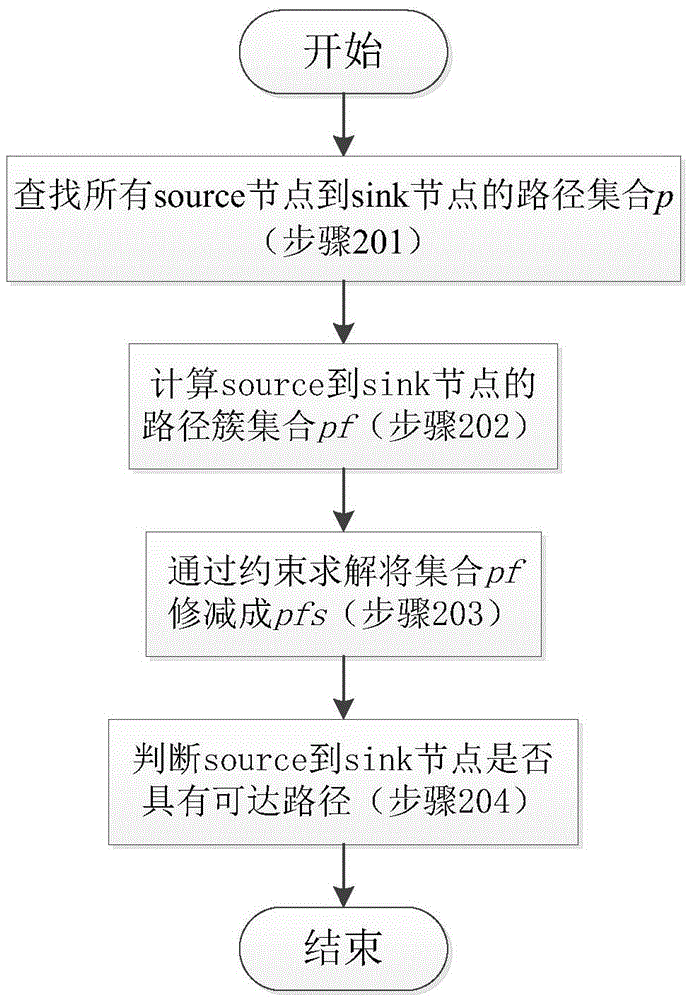
[0051] Step 2. Use the IDA plug-in to generate the control flow graph and function call graph of the program under test, analyze the call path set from the source node to the sink node, and establish a multi-source to multi-target mapping relationship between the source node and the sink node, specifically including As follows:
[0052] Step 2.1, find the path set p from all source nodes to sink nodes on the control flow graph and function call graph;
[0053] Step 2.2, generate a program dependency graph, reduce the path set p, and calculate the path cluster set pf from the source t...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com