Self-certified root implementation method based on open source DNS software
An implementation method and software technology, applied in the field of self-certification root implementation based on open source DNS software, can solve the problems of root zone glue records being tampered with and not providing a root zone glue record signature mechanism, etc., to achieve the effect of improving security
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
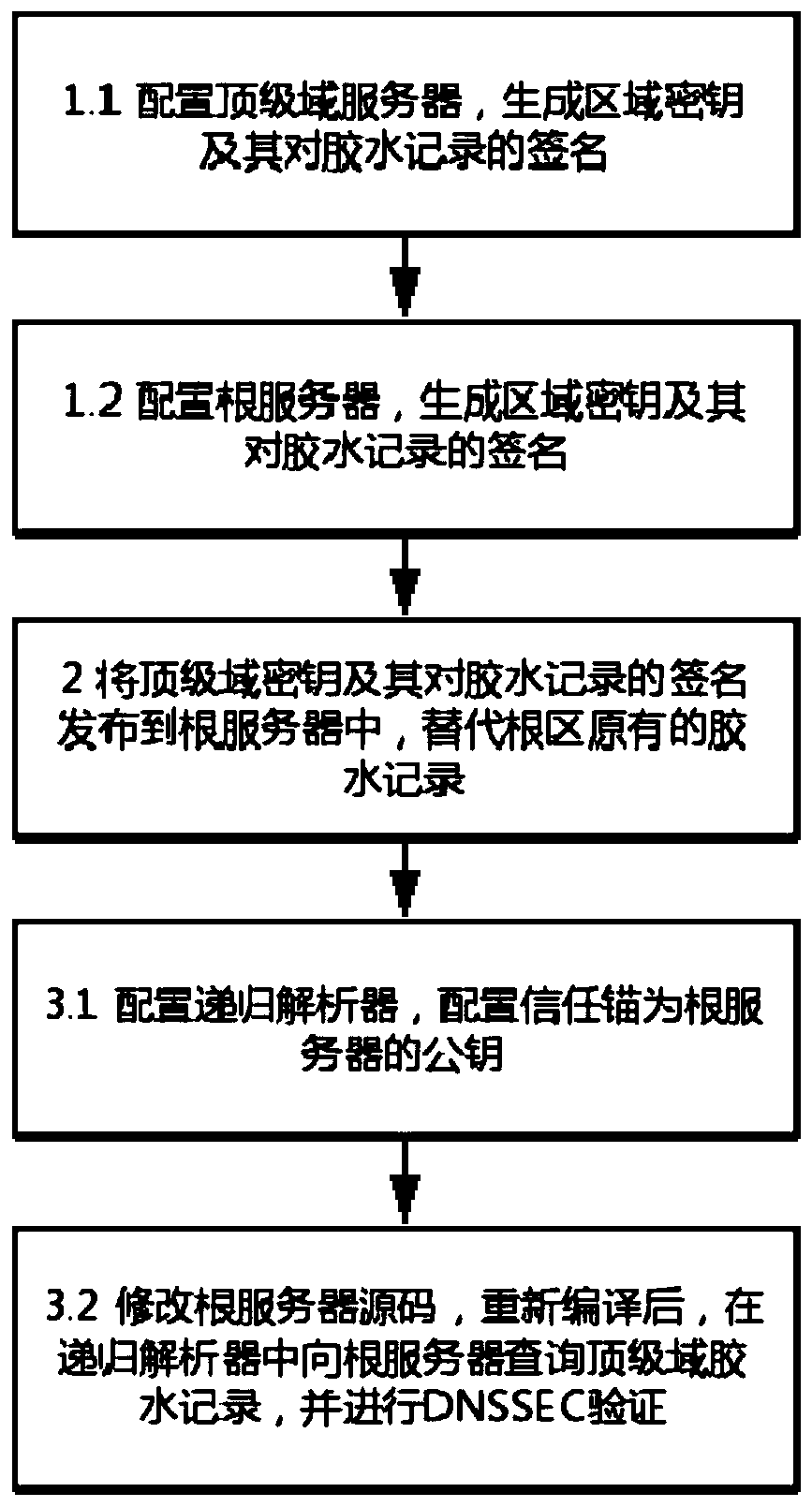
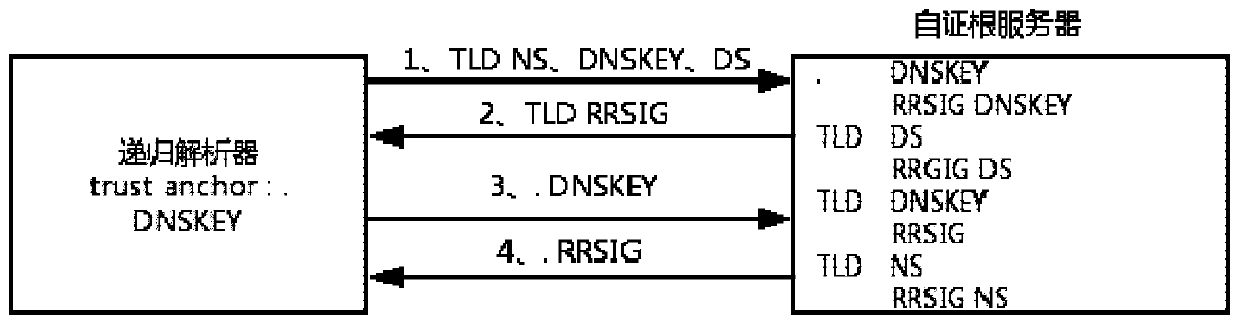
[0042] The self-certifying root scheme is a secure DNS encryption scheme in which the root zone data itself can self-certify the authenticity of the source. It is proposed to address the hidden danger of possible tampering of the root zone glue record in the existing DNSSEC scheme because it does not provide a signature mechanism. Self-certification root mainly contains three design goals:
[0043] 1. Glue signature: Add a digital signature from the top-level domain authority to the glue record, so that the source of the glue record in the root zone can be publicly verified.
[0044] 2. Public key pinning: the resolver uses the public key whitelist or the method of first trust to obtain the top-level domain public key.
[0045] 3. Dual signature: When the top-level domain key is rolled over, the new top-level domain public key certificate requires two signatures from the root authority and the top-level domain authority (using the old key).
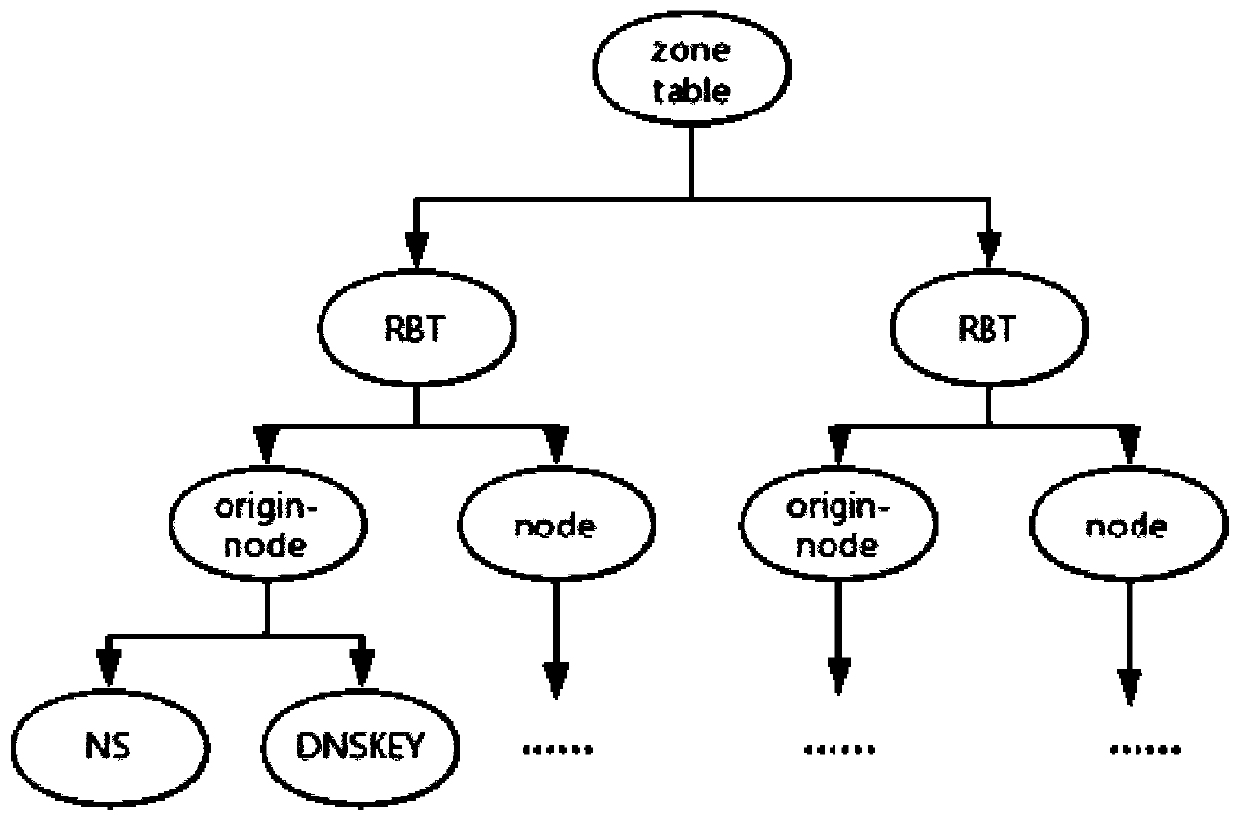
[0046] The schematic diagram of t...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com