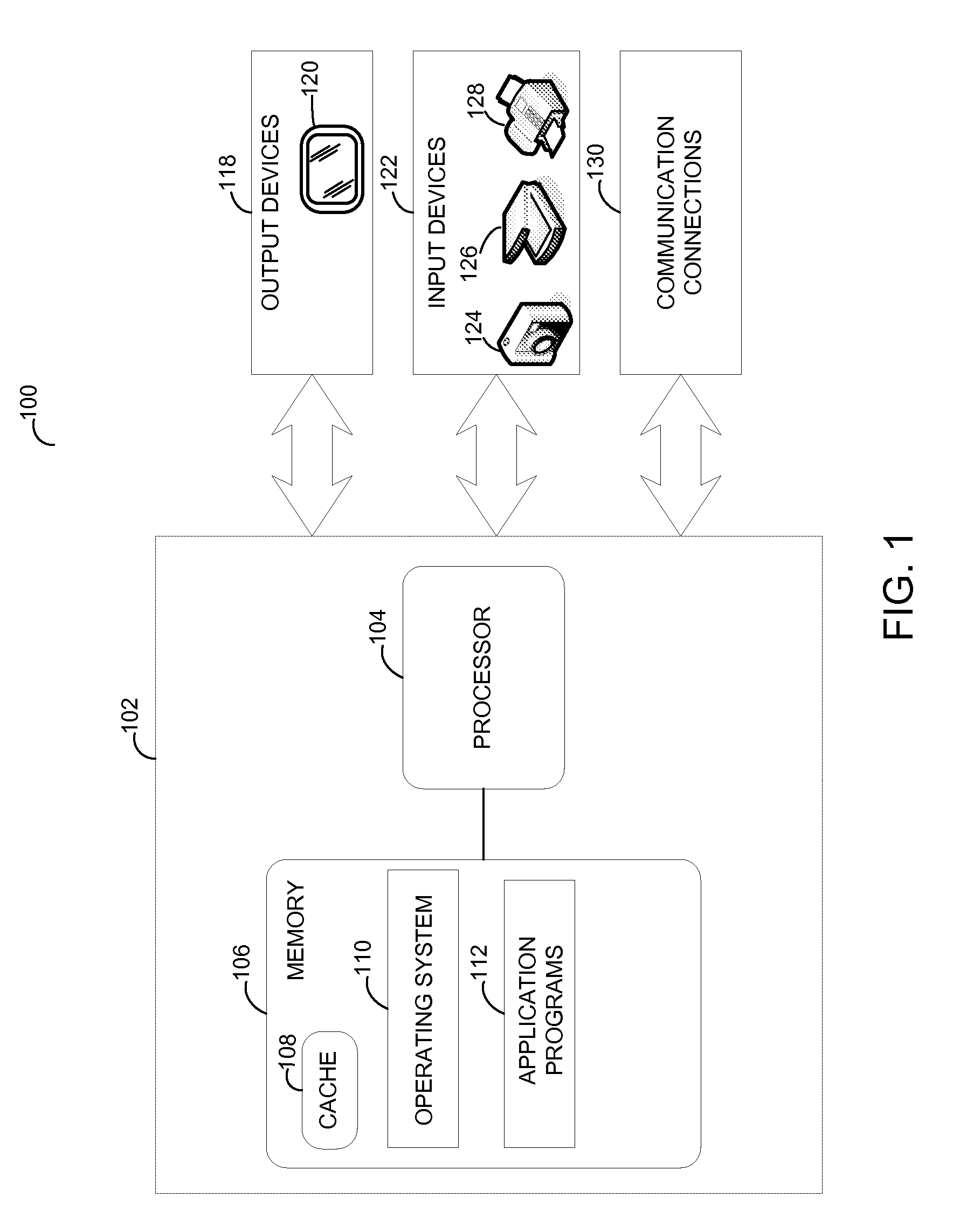
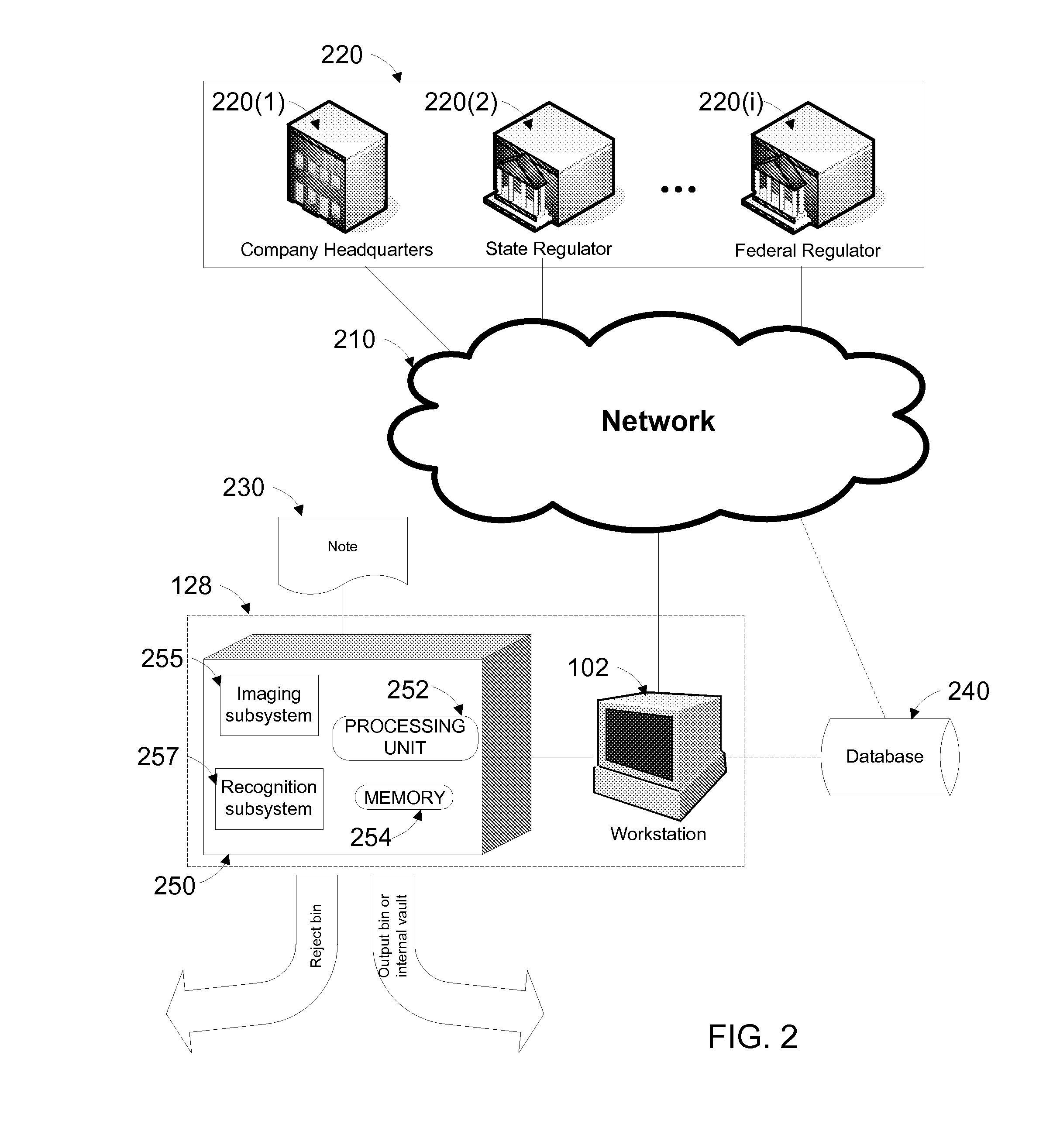
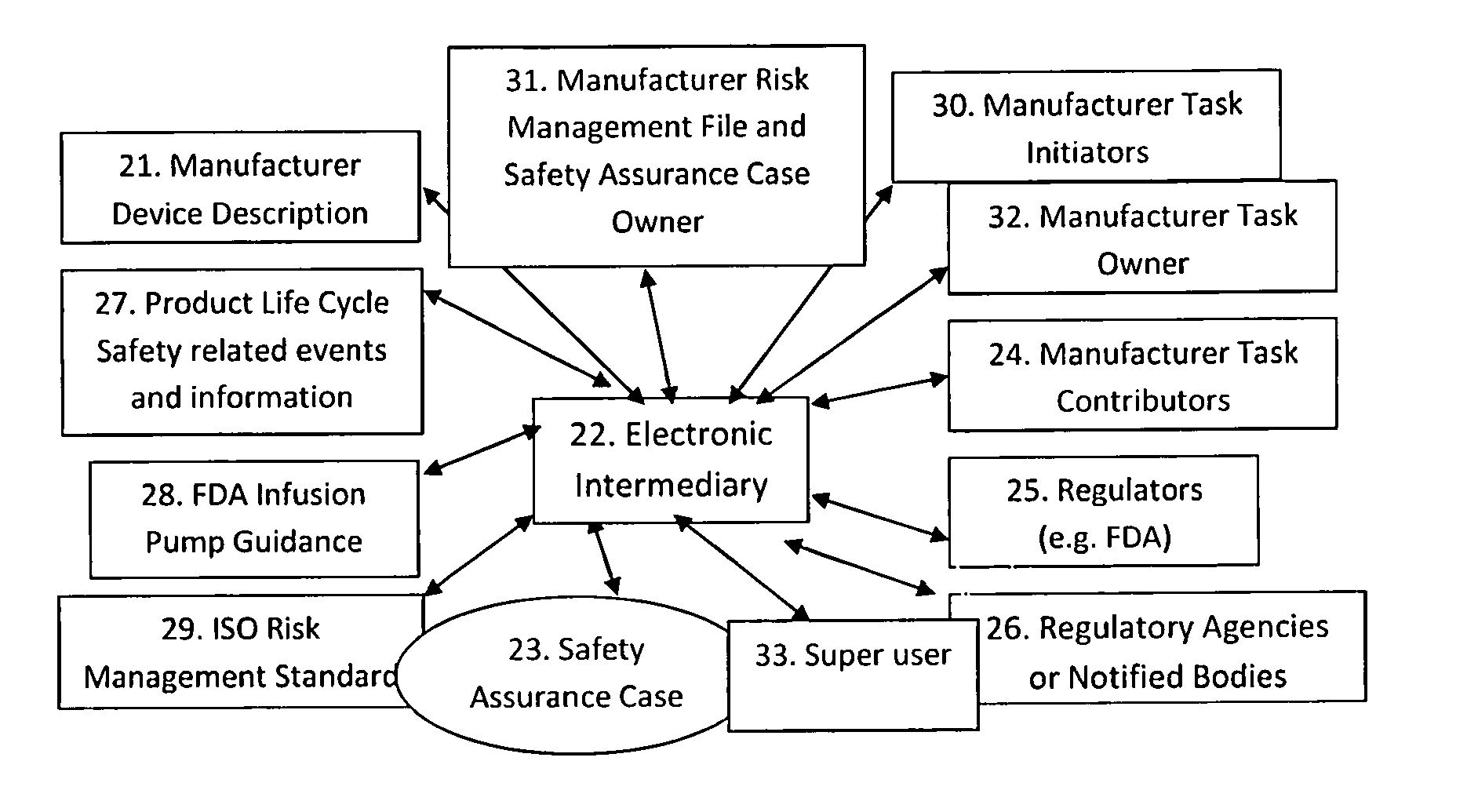
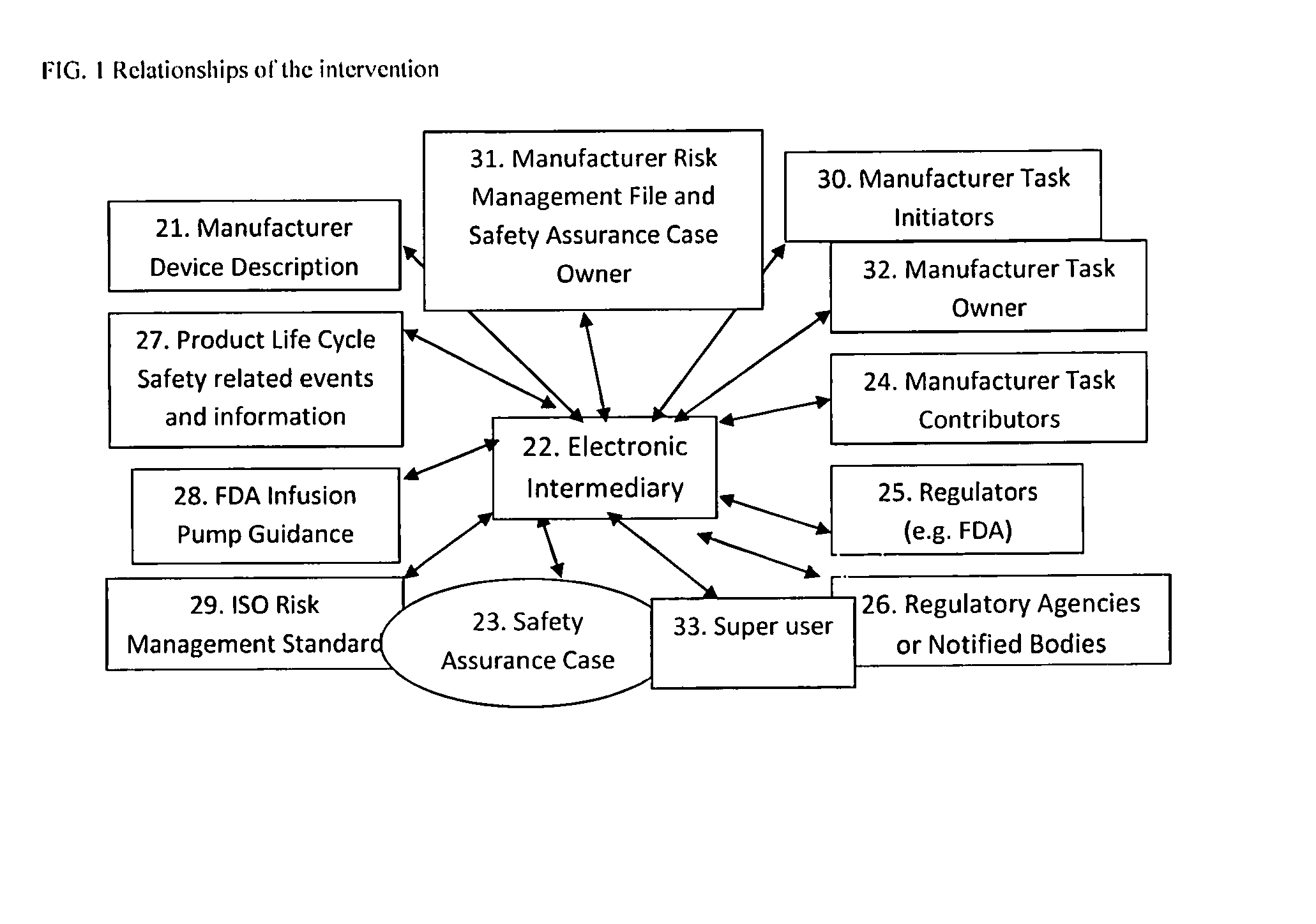
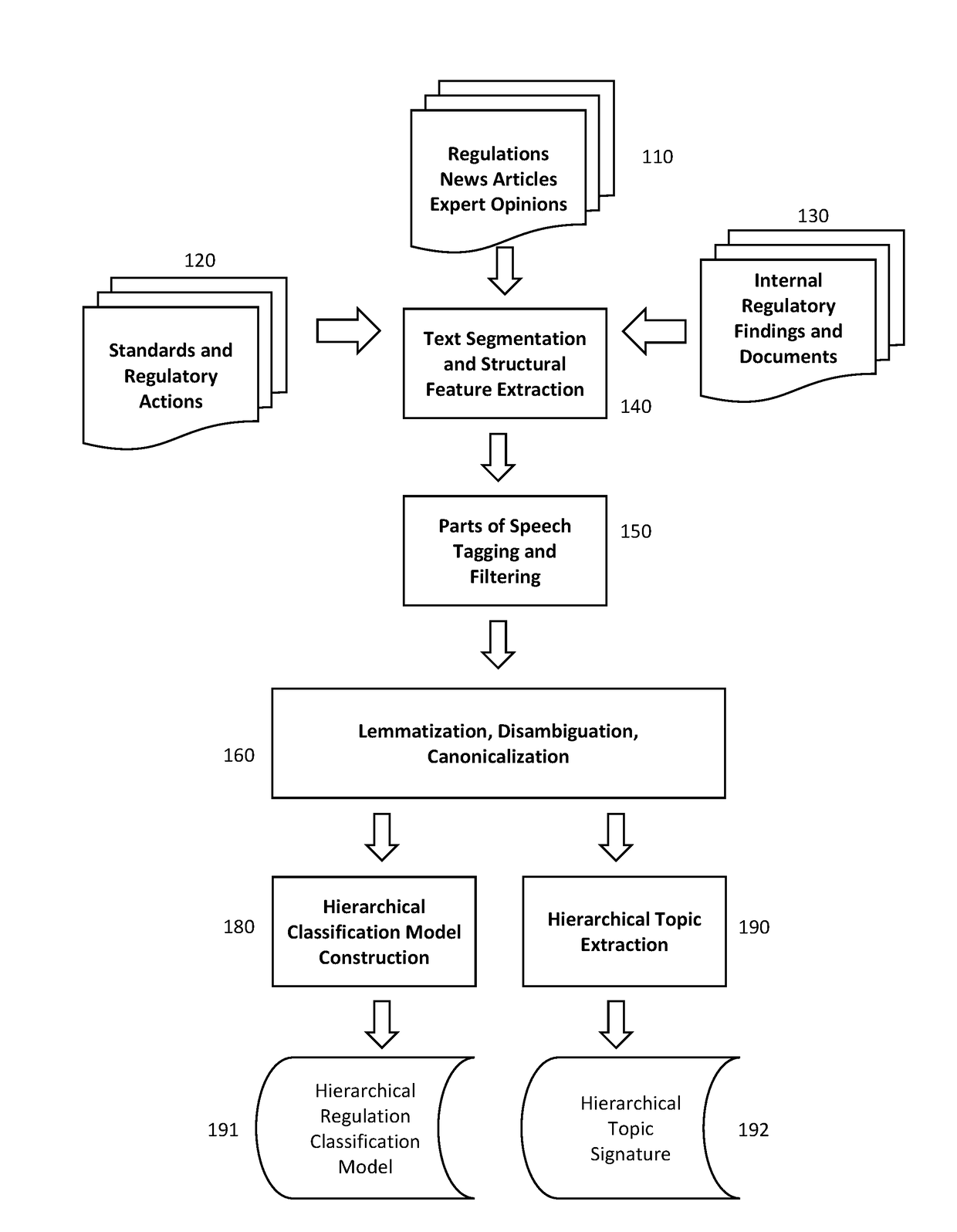
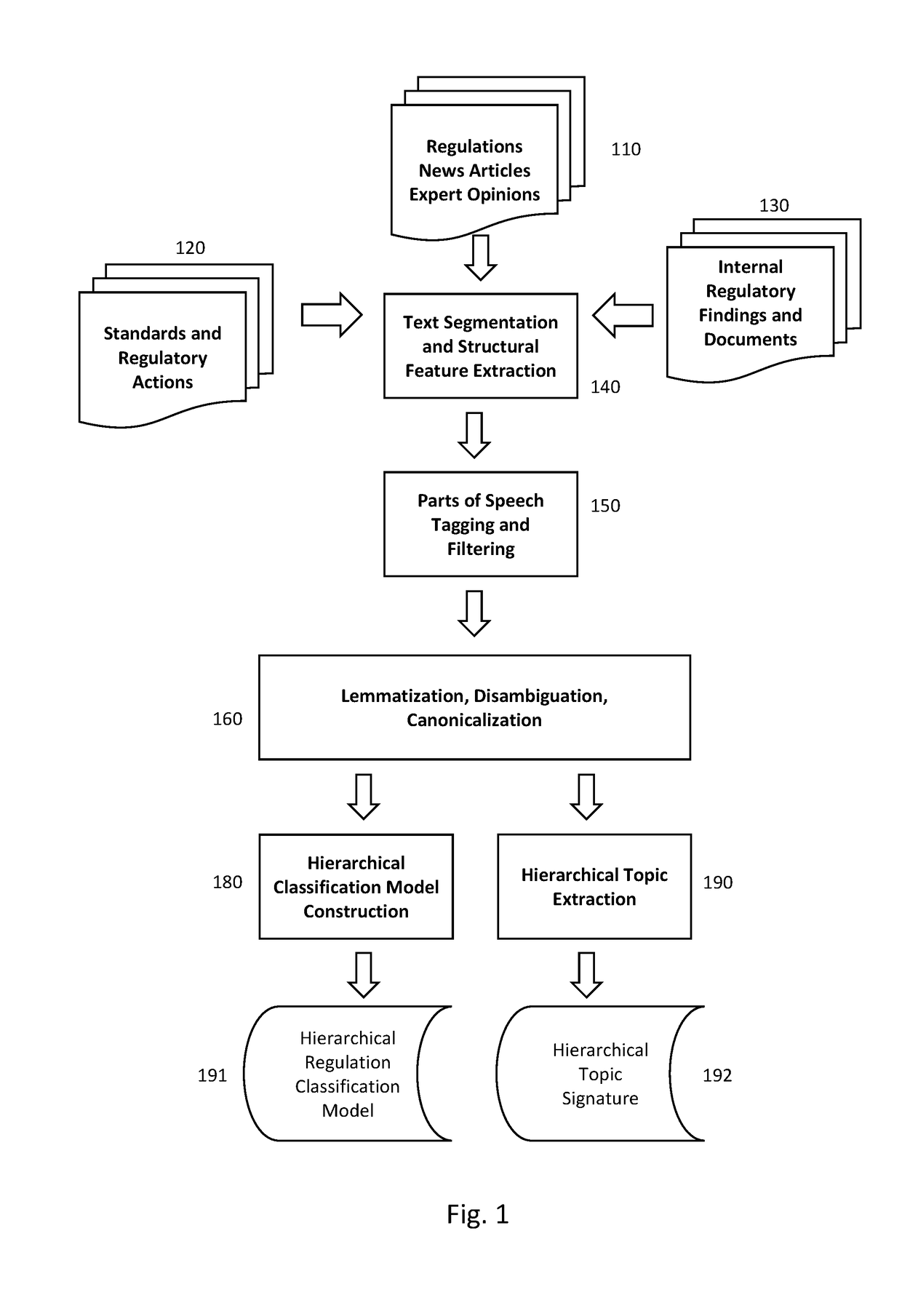
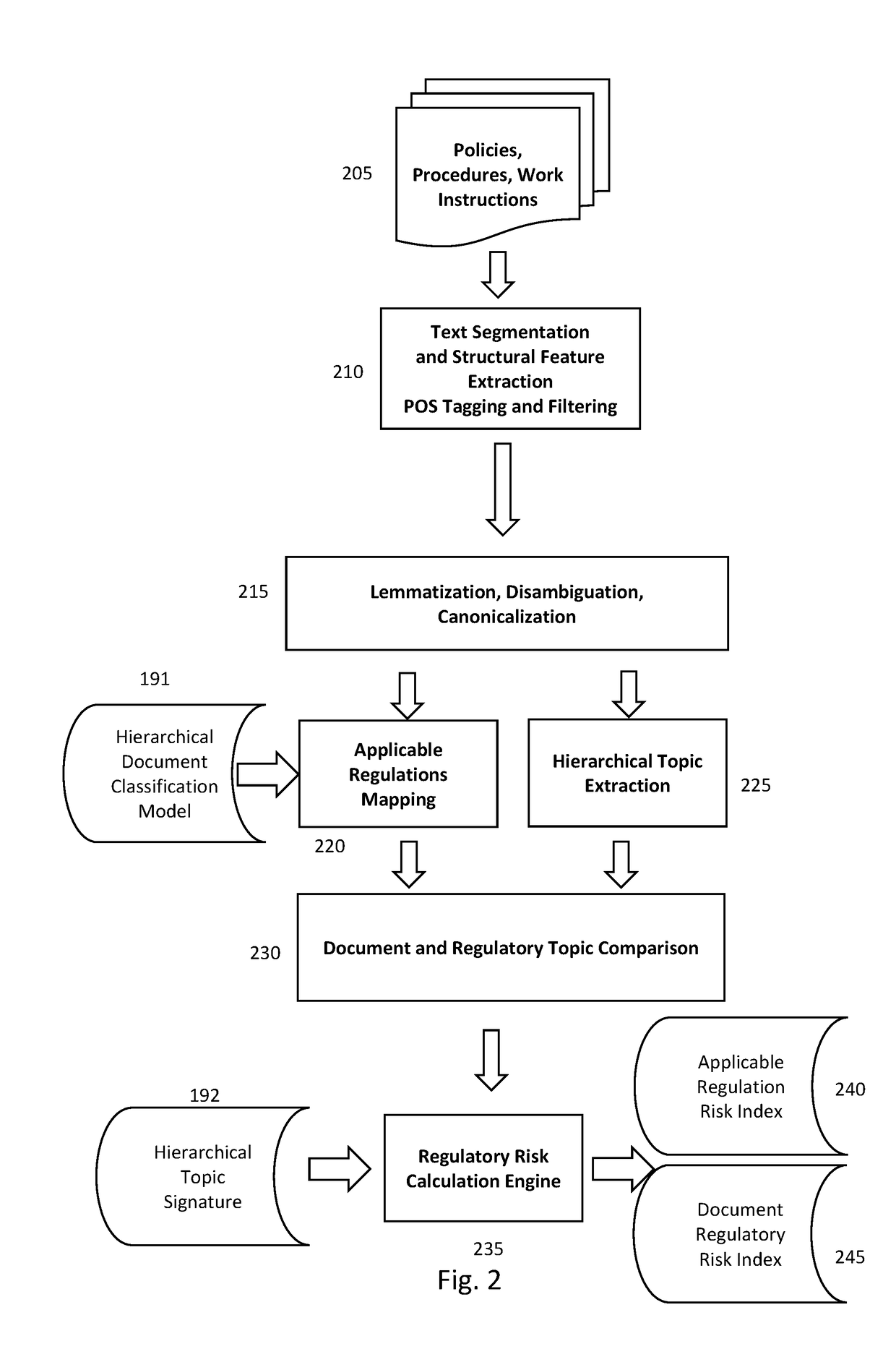
Patents
Literature
134 results about "Regulatory agency" patented technology
Efficacy Topic
Property
Owner
Technical Advancement
Application Domain
Technology Topic
Technology Field Word
Patent Country/Region
Patent Type
Patent Status
Application Year
Inventor
A regulatory agency (also regulatory authority, regulatory body or regulator) is a public authority or government agency responsible for exercising autonomous authority over some area of human activity in a regulatory or supervisory capacity. An independent regulatory agency is a regulatory agency...
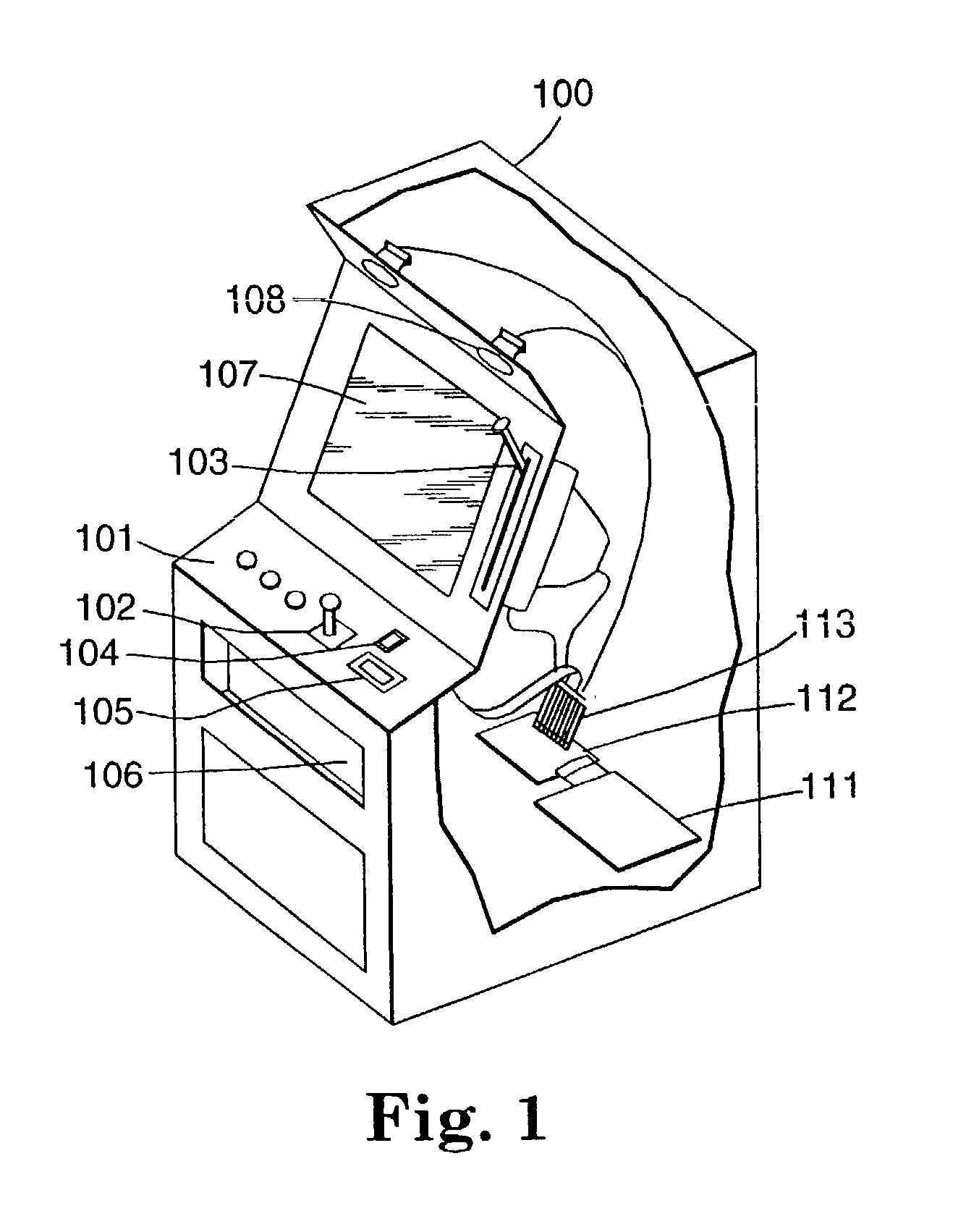
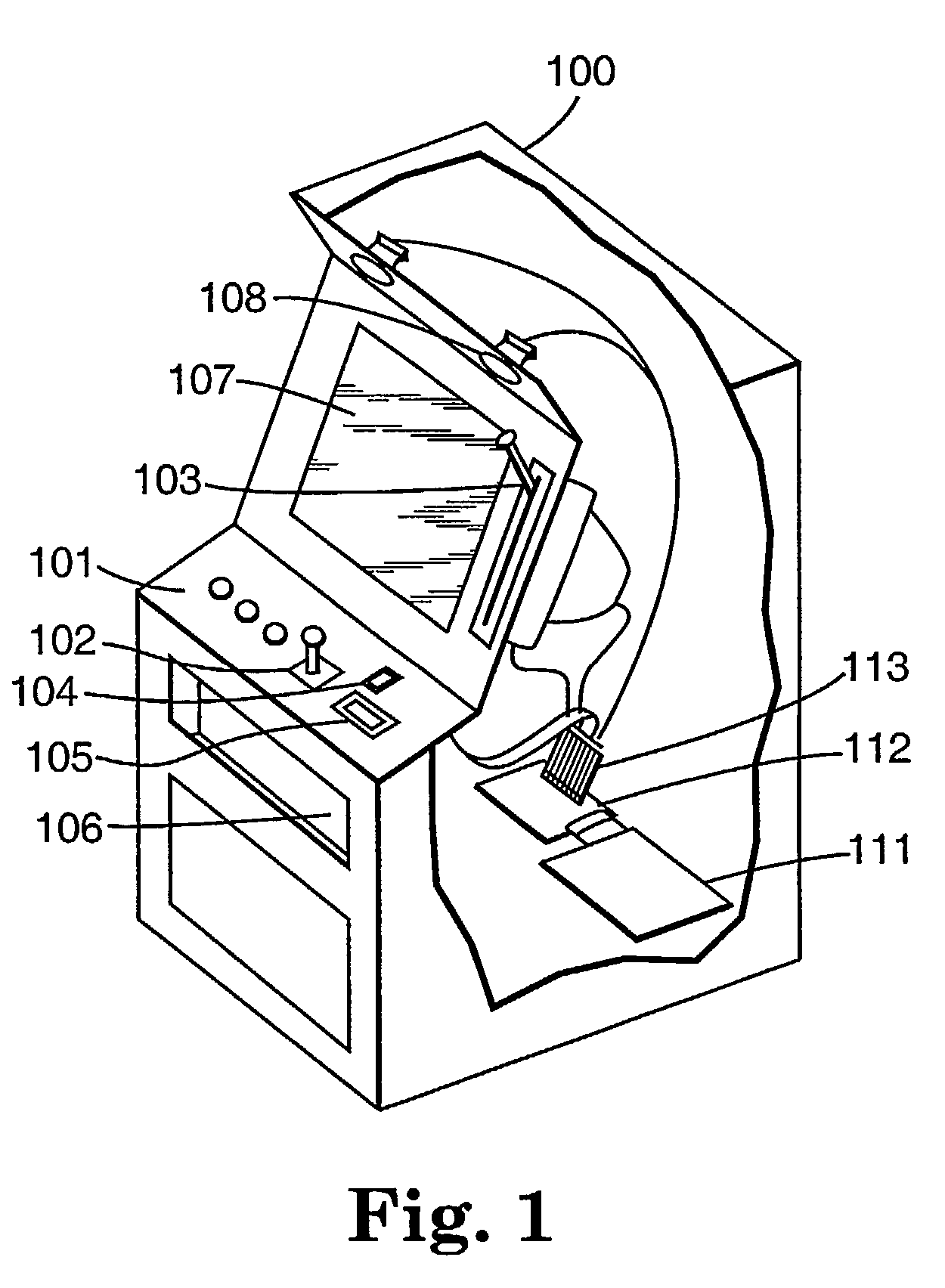
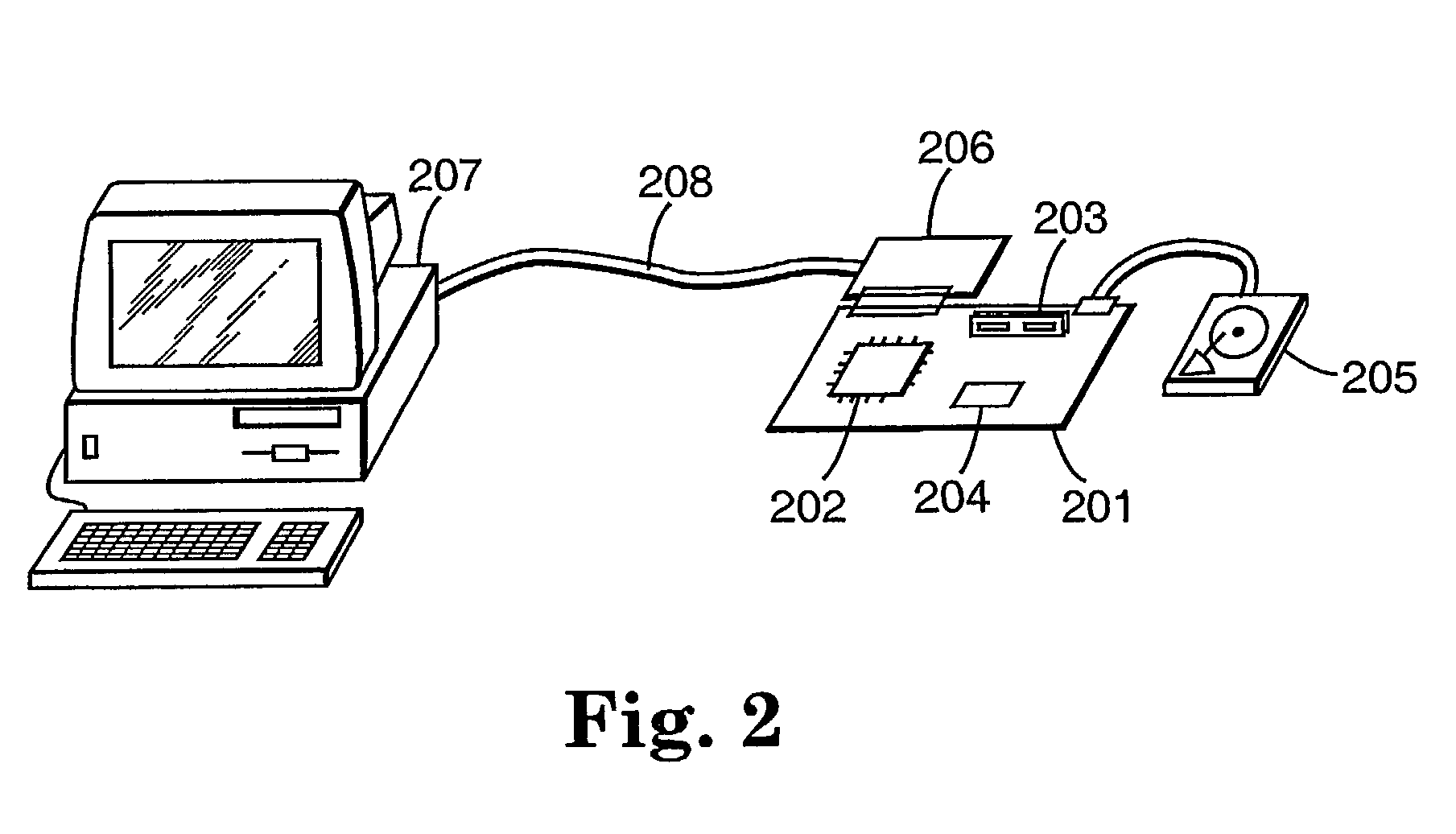
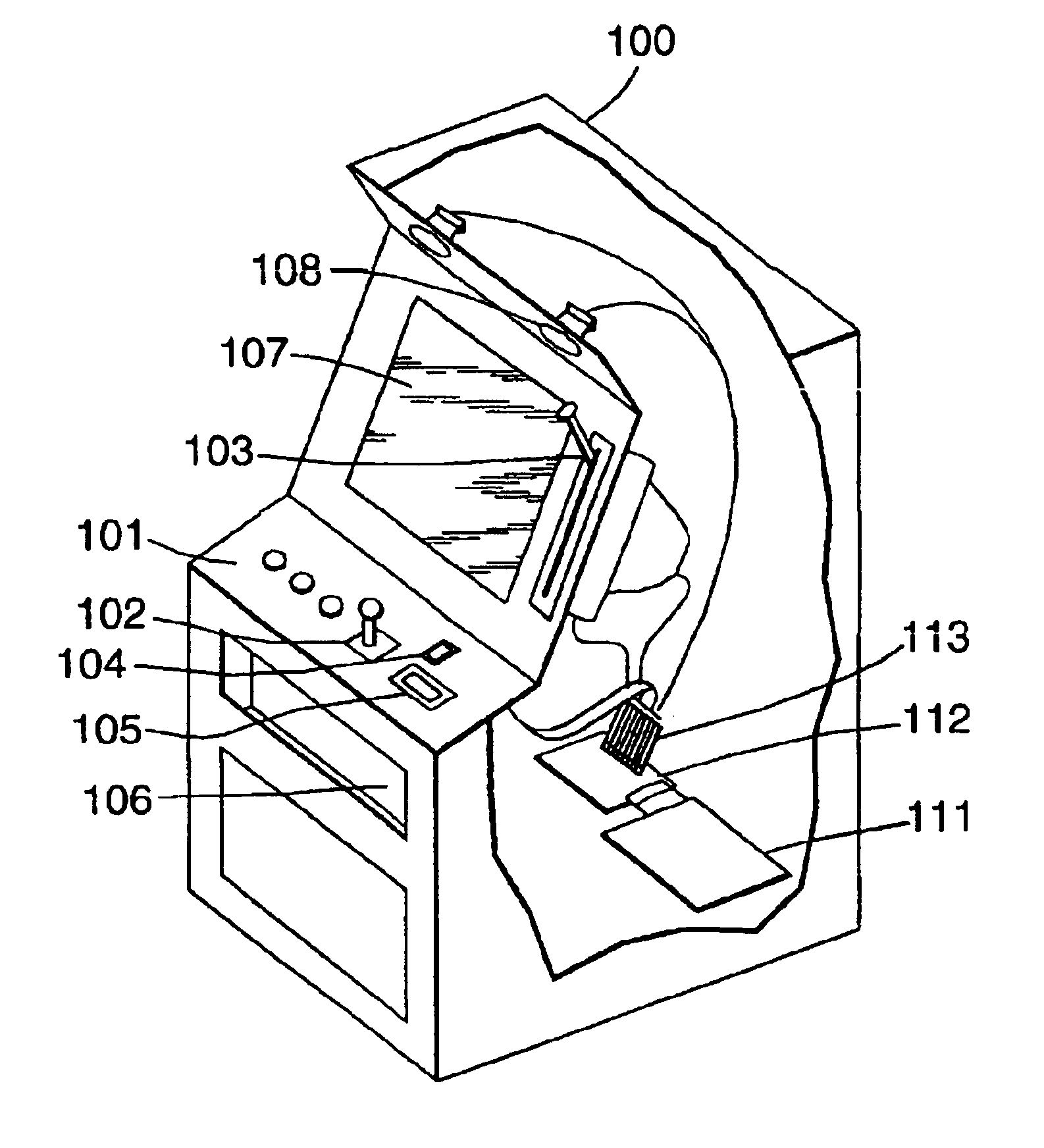
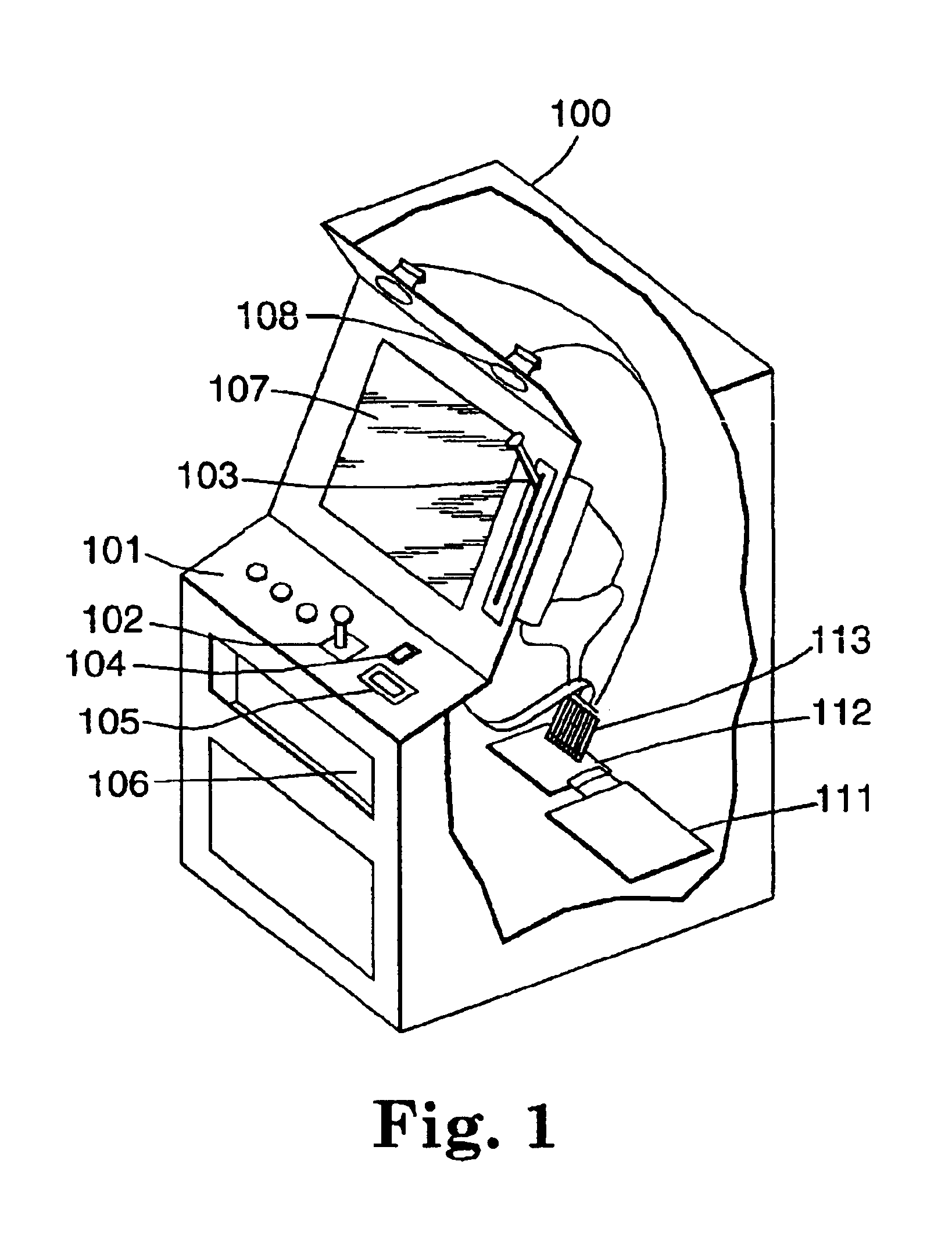
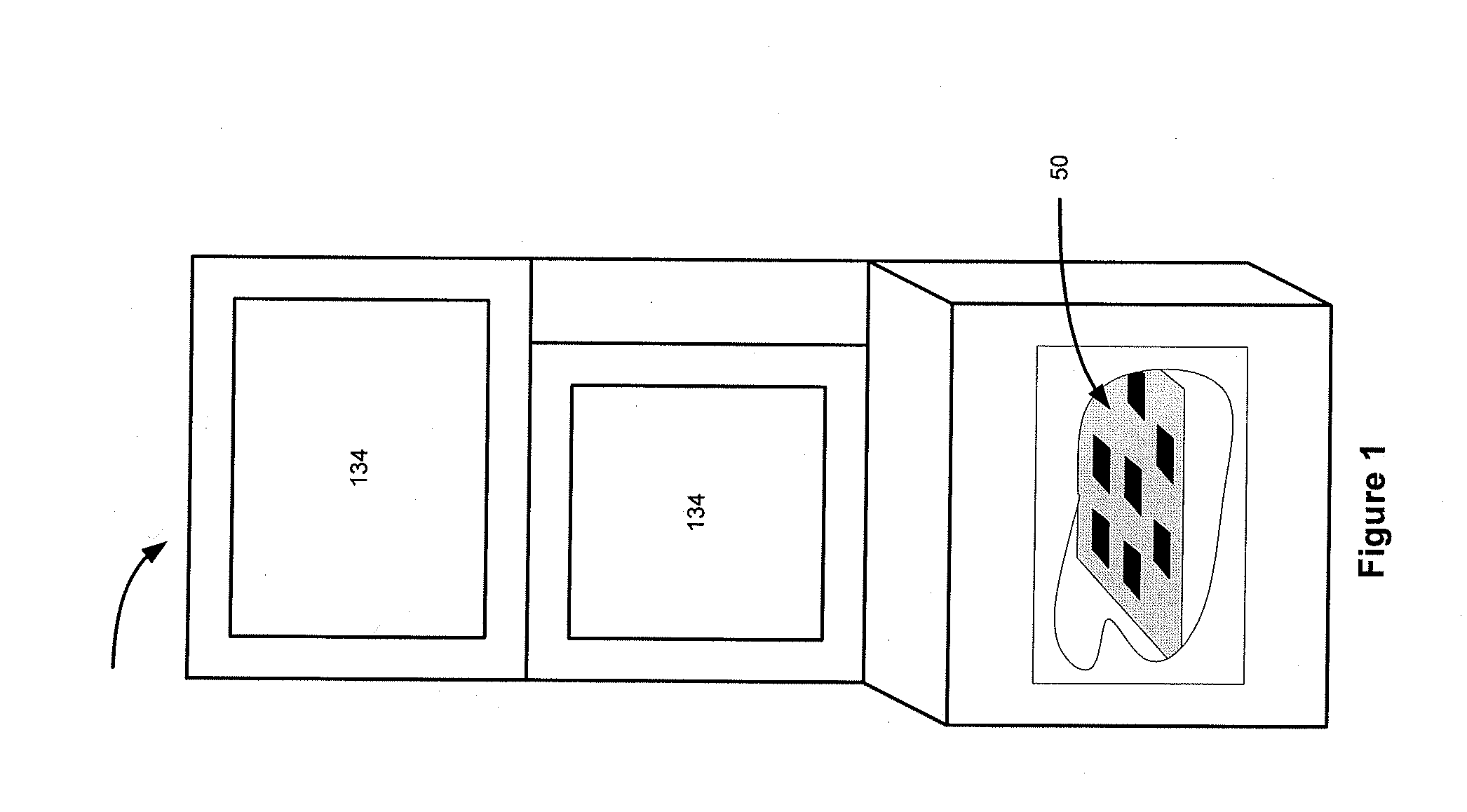
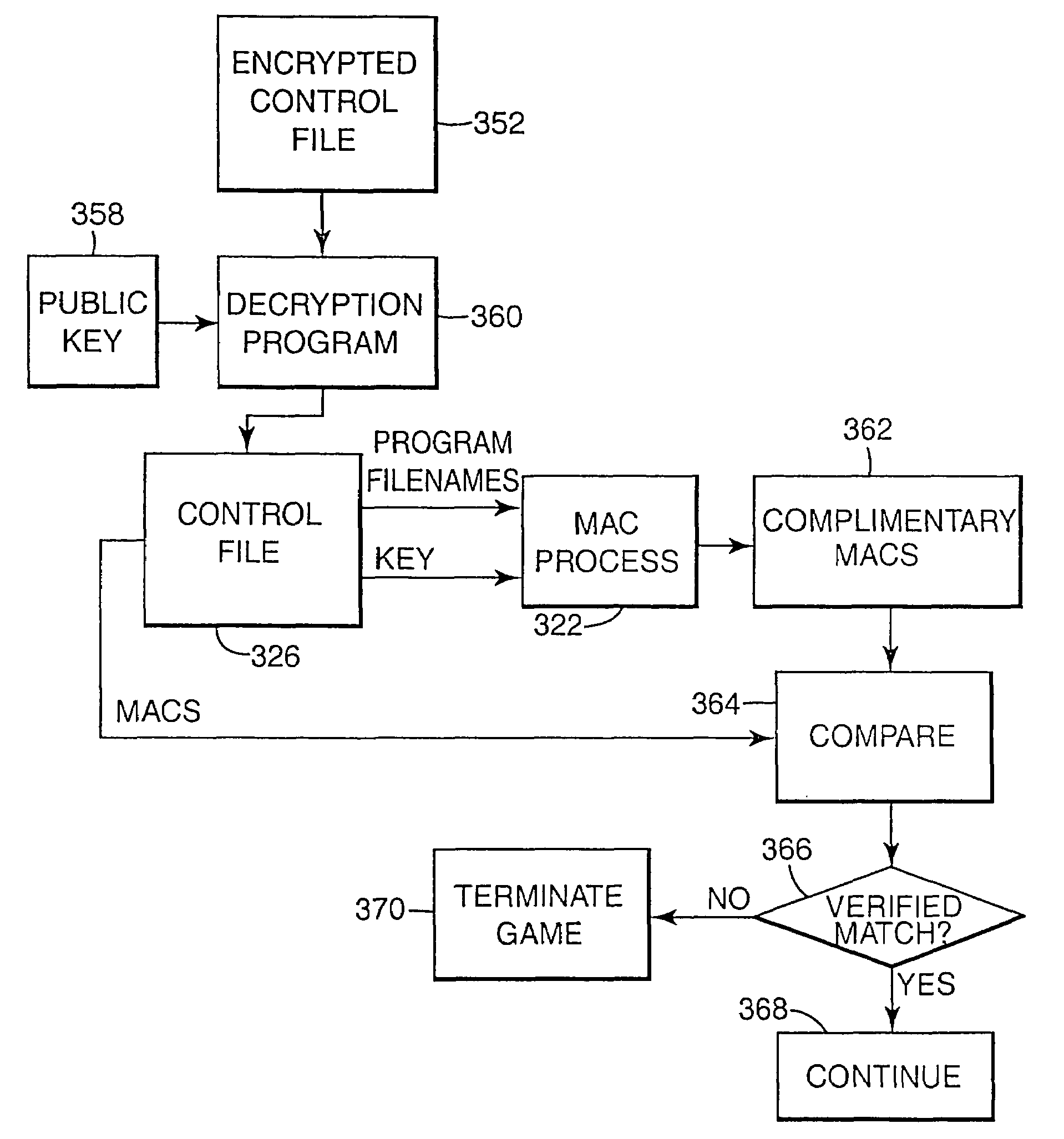
Encryption in a secure computerized gaming system
InactiveUS7043641B1Straightforward and easy to manageUser identity/authority verificationUnauthorized memory use protectionHash functionDigital signature
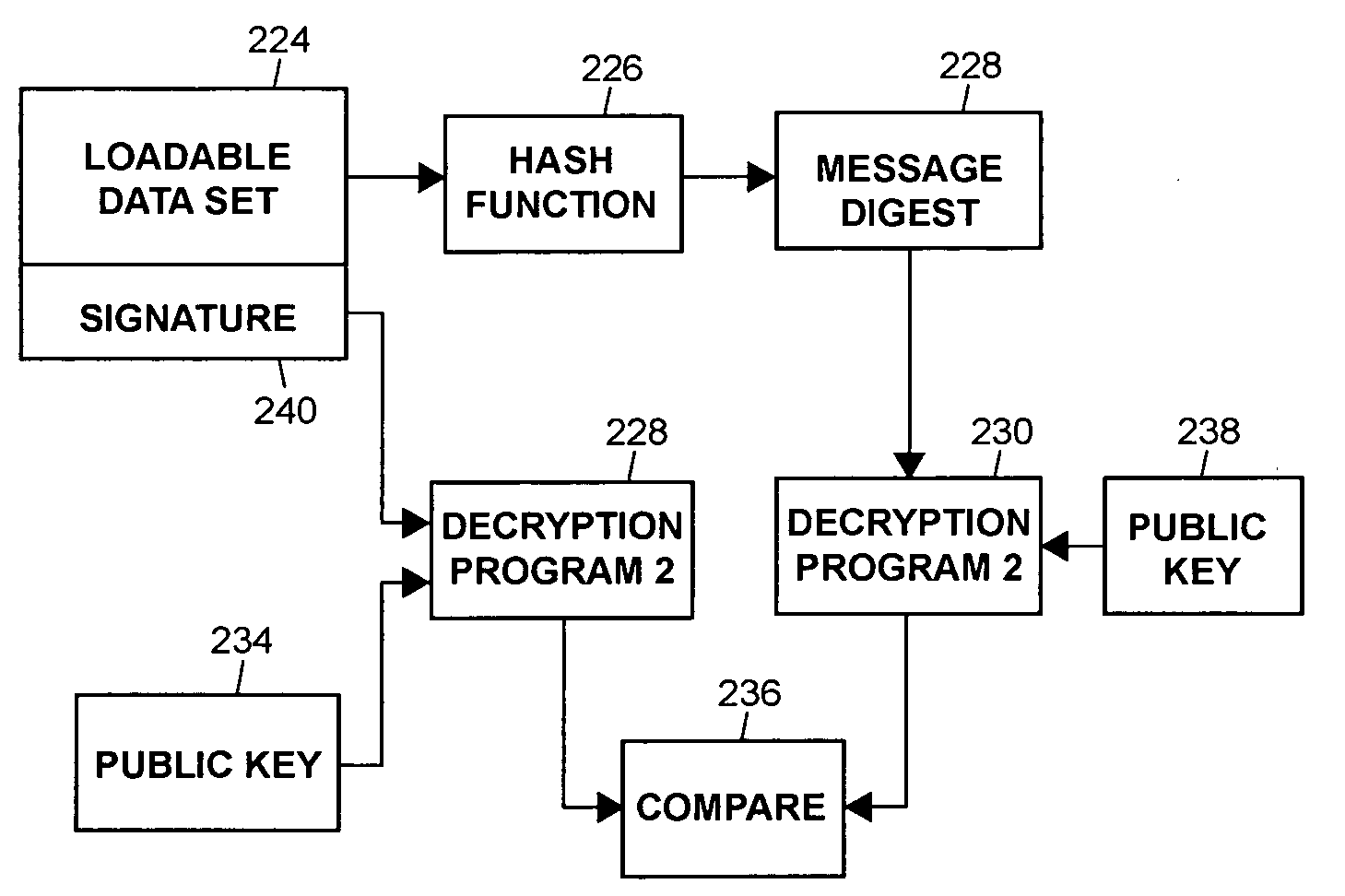
An architecture and method for a gaming-specific platform are disclosed that features secure storage and verification of game code and other data, provides the ability to securely exchange data with a computerized wagering gaming system, and does so in a manner that is straightforward and easy to manage. Some embodiments provide the ability to identify game program code as certified or approved, such as by the Nevada Gaming Regulations Commission or other regulatory agency. These and other functions make use of encryption, including digital signatures and hash functions as well as other encryption methods.
Owner:IGT
Authentication in a secure computerized gaming system
InactiveUS20030203756A1Data processing applicationsUser identity/authority verificationComputer hardwareData set
The present invention provides an architecture and method for a gaming-specific platform that features secure storage and verification of game code and other data, provides the ability to securely exchange data with a computerized wagering gaming system, and does so in a manner that is straightforward and easy to manage. Some embodiments of the invention provide the ability to identify game program code as certified or approved, such as by the Nevada Gaming Regulations Commission or other regulatory agency. The invention provides these and other functions by encrypting a random number, storing the encrypted random number, and hashing the random number and a casino game data set to provide a first bit string, and storing the first bit string.
Owner:IGT
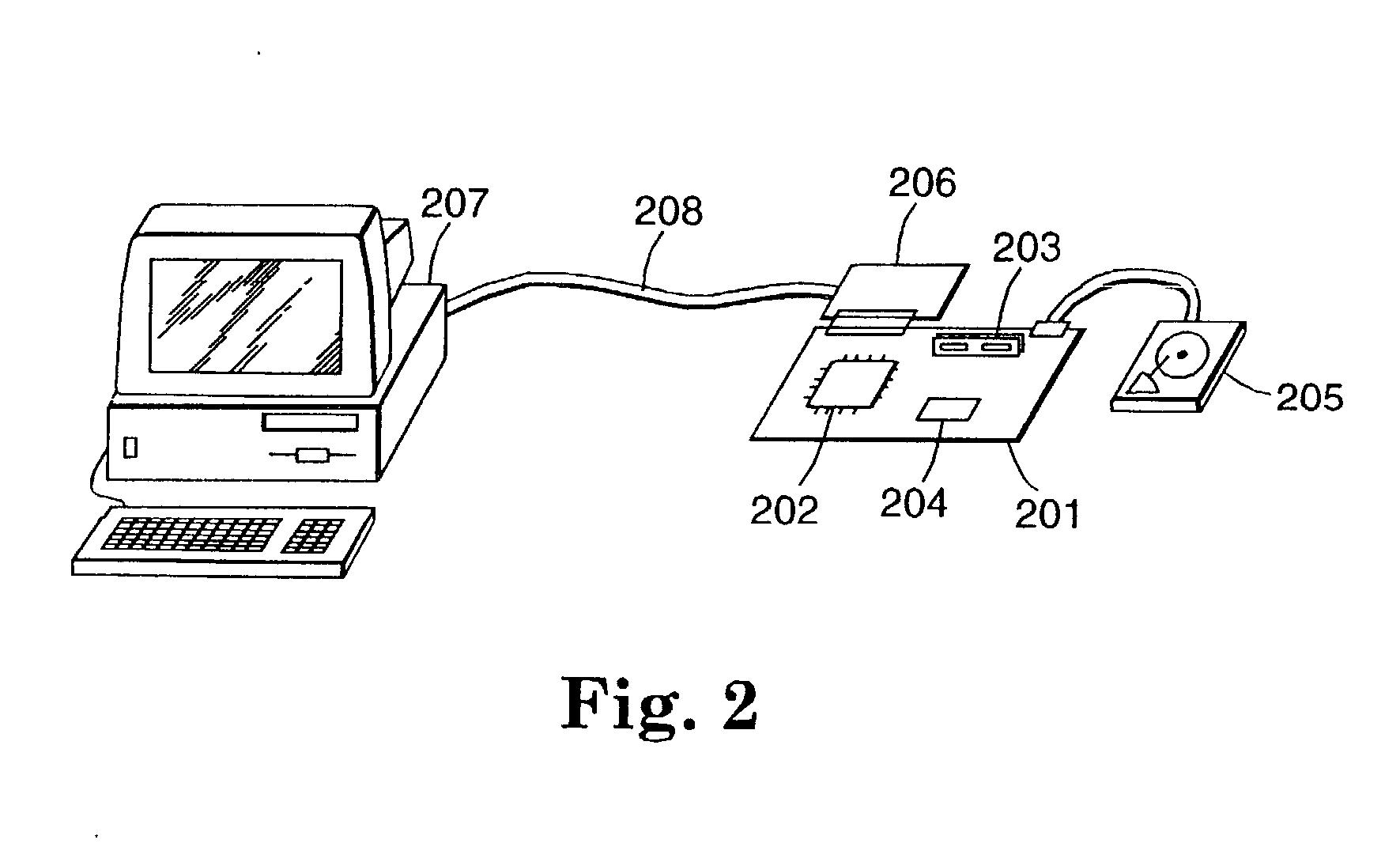
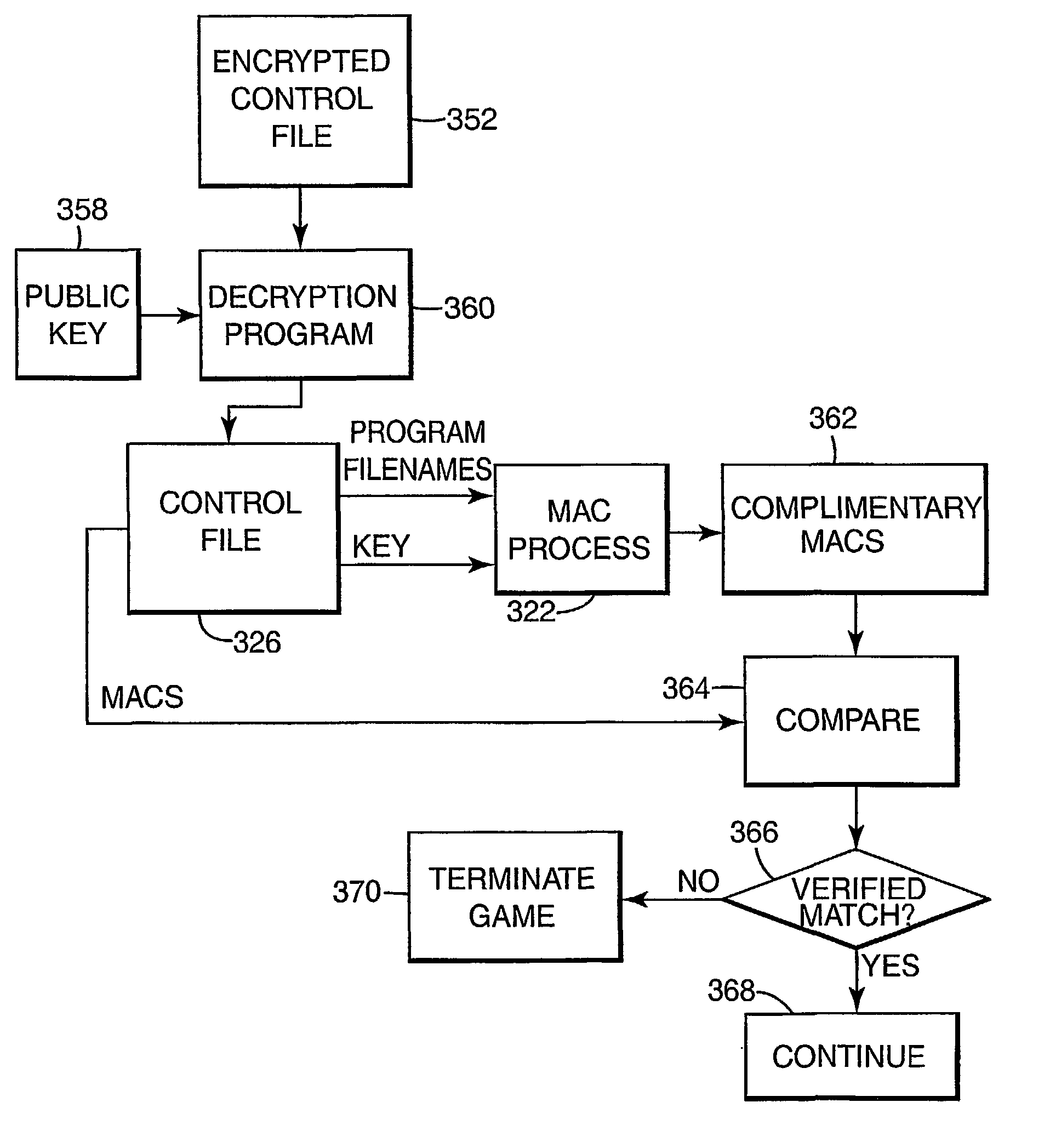
Encryption in a secure computerized gaming system
InactiveUS7203841B2Straightforward and easy to manageUser identity/authority verificationUnauthorized memory use protectionComputer hardwareHash function
The present invention provides an architecture and method for a gaming-specific platform that features secure storage (354) and verification (366) of game code and other data, provides the ability to securely exchange data with a computerized wagering gaming system, and does so in a manner that is straightforward and easy to manage. Some embodiments of the invention provide the ability to identify game program code as certified or approved, such as by the Nevada Gaming Regulations Commission or other regulatory agency. The invention provides these and other functions by use of encryption (216), including digital signatures (220) and hash functions (210) as well as other encryption methods.
Owner:IGT
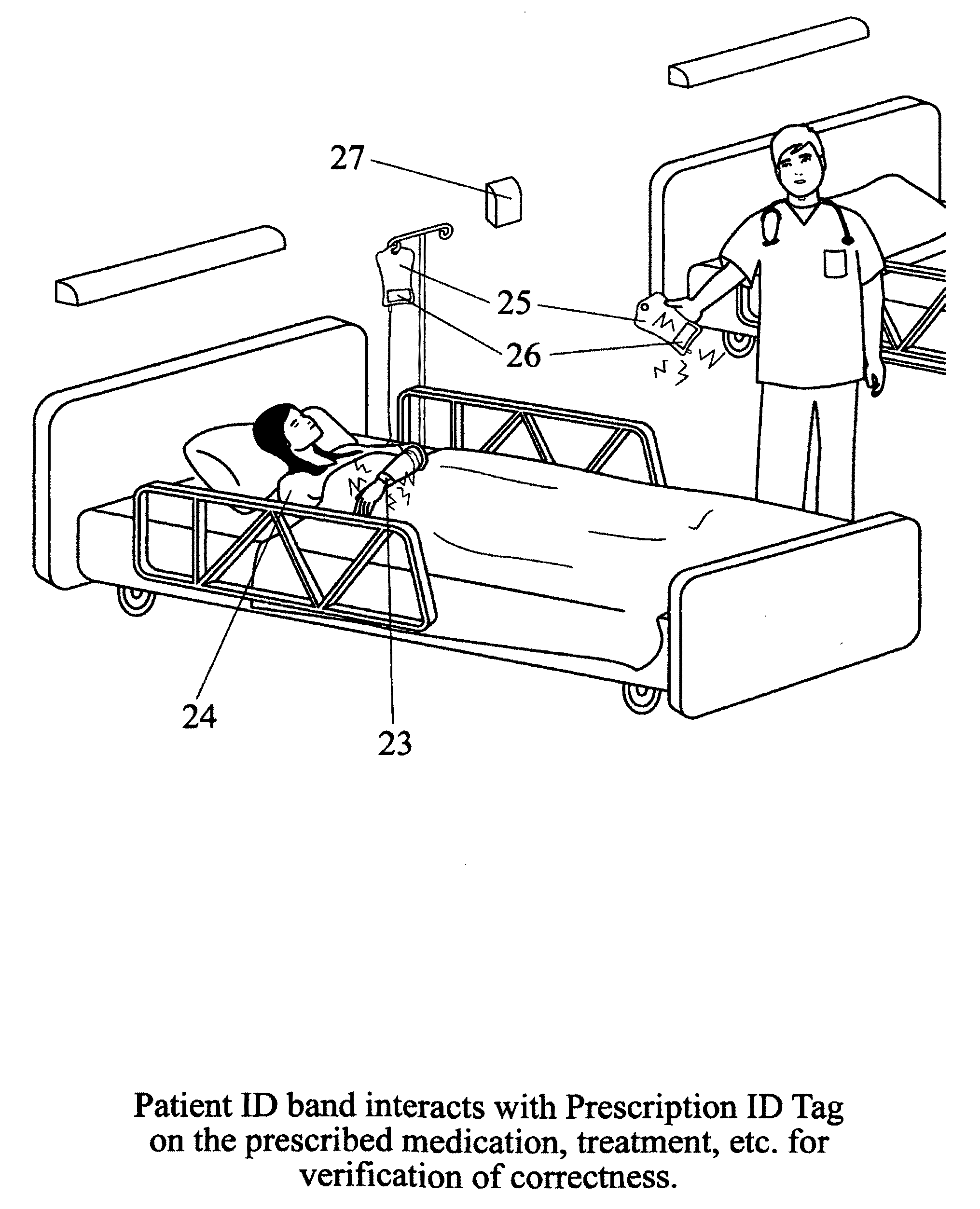
Monitoring system and method for patient care
A patient care monitoring system and method employ active RFID devices integrated with digital processing, memory and timing circuitry for patient identification, care giver identification and for identification of each prescribed treatment, procedure, medication and general and / or special care action. At the point-of-care, each care action identity device will match directly with the targeted patient identity device or issue an error warning to prevent mistakes. The patient identity device will also interact with an associated sensor network to proactively prompt care givers to provide general care actions, such as altering a patient's laying position, changing bed pan / clothing / bed sheet, etc. for invalid patients. Also the patient identity tag will furnish periodic records of every care action, mistakes, remedies, care givers' identities and time and date for a central processor of a healthcare facility to monitor the quality of patient care. Such record can also be potentially accessed via the Internet by the responsible regulatory agencies, accreditation associations, insurance firms and even patients' families to ensure patient care is meeting the standards as well as medical billing accuracy.
Owner:HUANG CHING CHING +4
Authentication in a secure computerized gaming system
InactiveUS6962530B2Straightforward and easy to manageData processing applicationsUser identity/authority verificationComputer hardwareData set
An architecture and method for a gaming-specific platform are disclosed that features secure storage and verification of game code and other data, provides the ability to securely exchange data with a computerized wagering gaming system, and do so in a manner that is straightforward and easy to manage. Some embodiments provide the ability to identify game program code as certified or approved, such as by the Nevada Gaming Regulations Commission or other regulatory agency. The disclosed embodiments provides these and other functions by encrypting a random number, storing the encrypted random number, and hashing the random number and a casino game data set to provide a first bit string, and storing the first bit string.
Owner:IGT
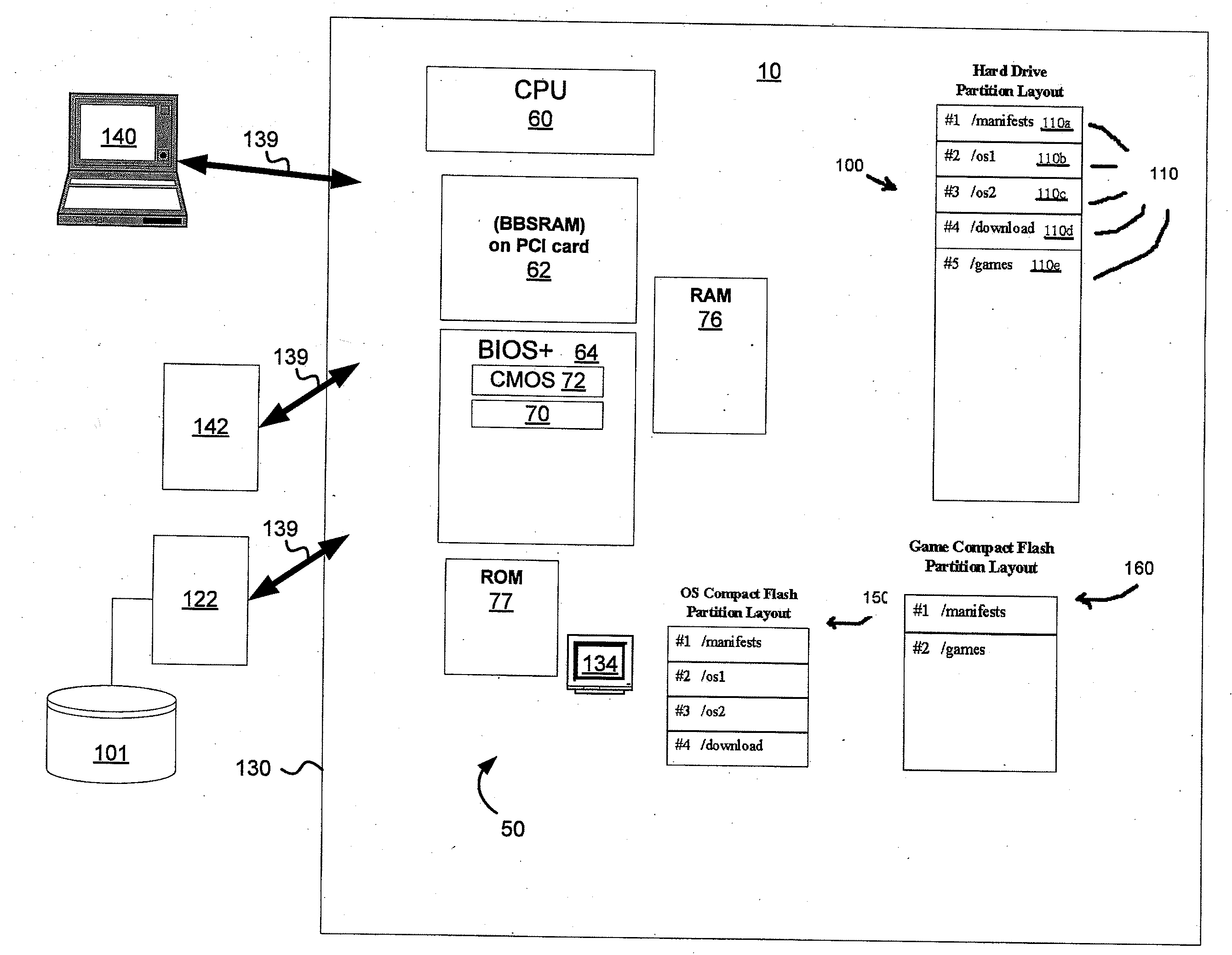
Data Integrity and Non-Repudiation
ActiveUS20080045342A1Reduce boot timeImprove loading timeUnauthorized memory use protectionHardware monitoringComputer hardwareData integrity
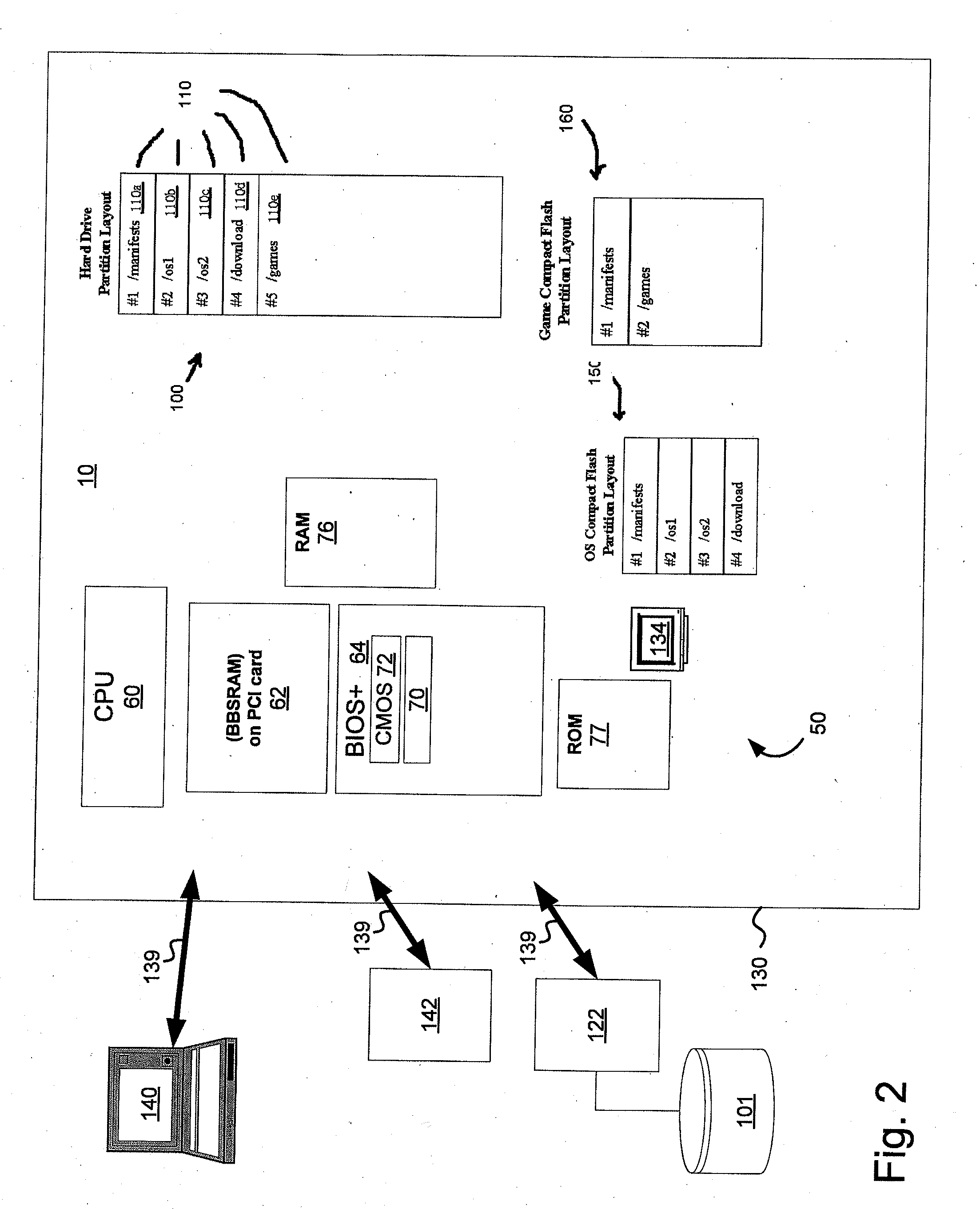
Disclosed is a system and method that uses digital signature technology to authenticate the contents of one or more manifests located on a storage device. Each manifest contains a list of file records, where each record contains the name of a file stored on the storage device, and a signature value derived from the contents of the file. At boot time, the gaming machine first authenticates the contents of the manifest and then authenticates the contents of the files using the signature value stored in the manifest. Files are verified using the signature, as they are needed, during the boot up of the operating system and throughout normal operation. This method reduces the boot time of the gaming machine and eliminates the need to check digital signatures for each individual file or over the entire contents of a non-secure media. Similarly, a method of adding authentication ability to legacy software components without necessarily altering the legacy software components is disclosed. Introduction of a stronger authentication algorithm, or when a private key has been compromised would normally require the software component to be re-built to support the new algorithm or private / public key pair; however, a method is disclosed where algorithms and key pairs may be changed and applied to legacy software without having to re-built, re-test, re-sign, or re-submit the component to regulatory agencies for approval. Also disclosed is a system and method of establishing a trusted environment containing a gaming operating system and associated authentication module, file system drivers, and / or network drivers that may be used to in the process of authenticating contents of one or more manifests located on a storage device.
Owner:LNW GAMING INC
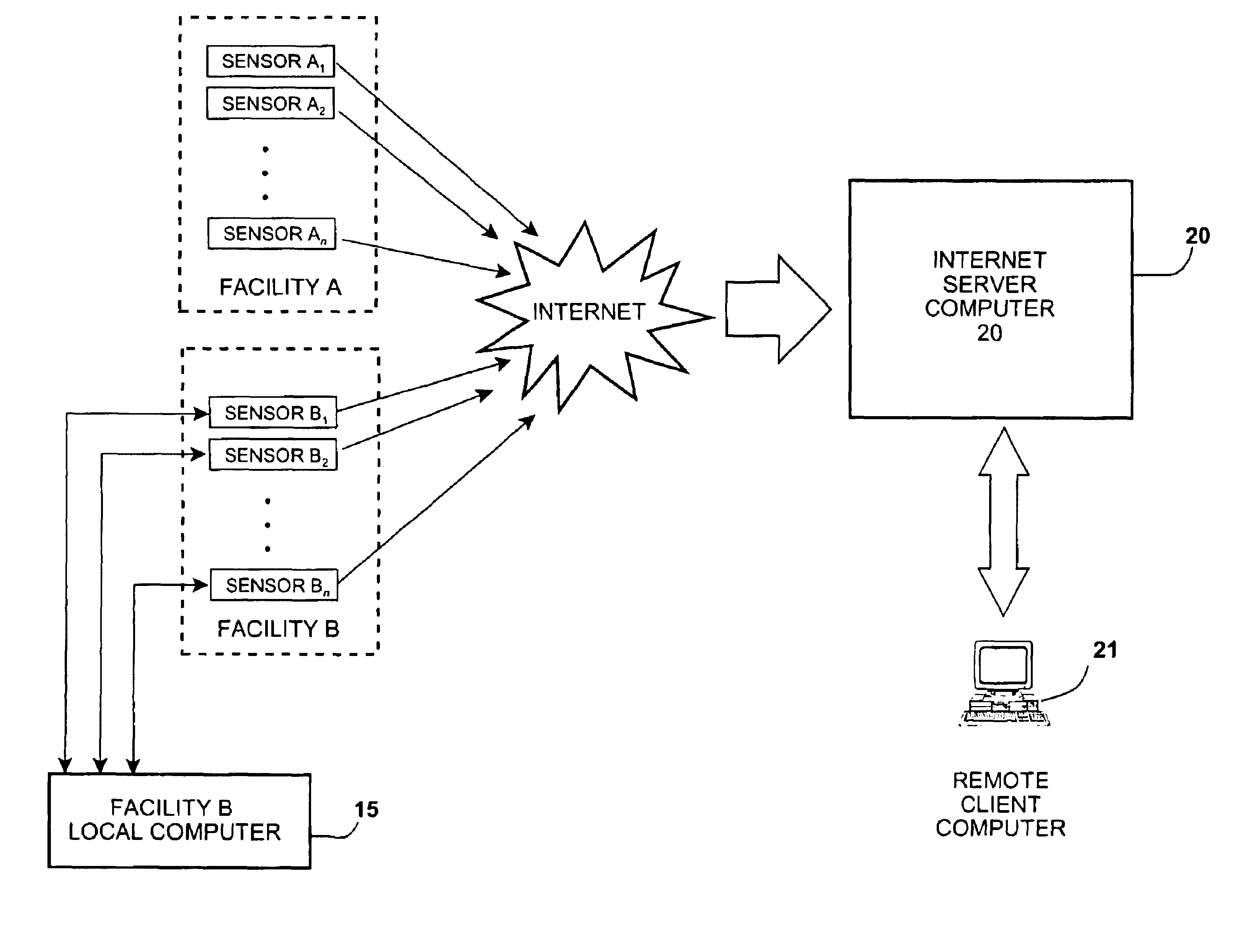
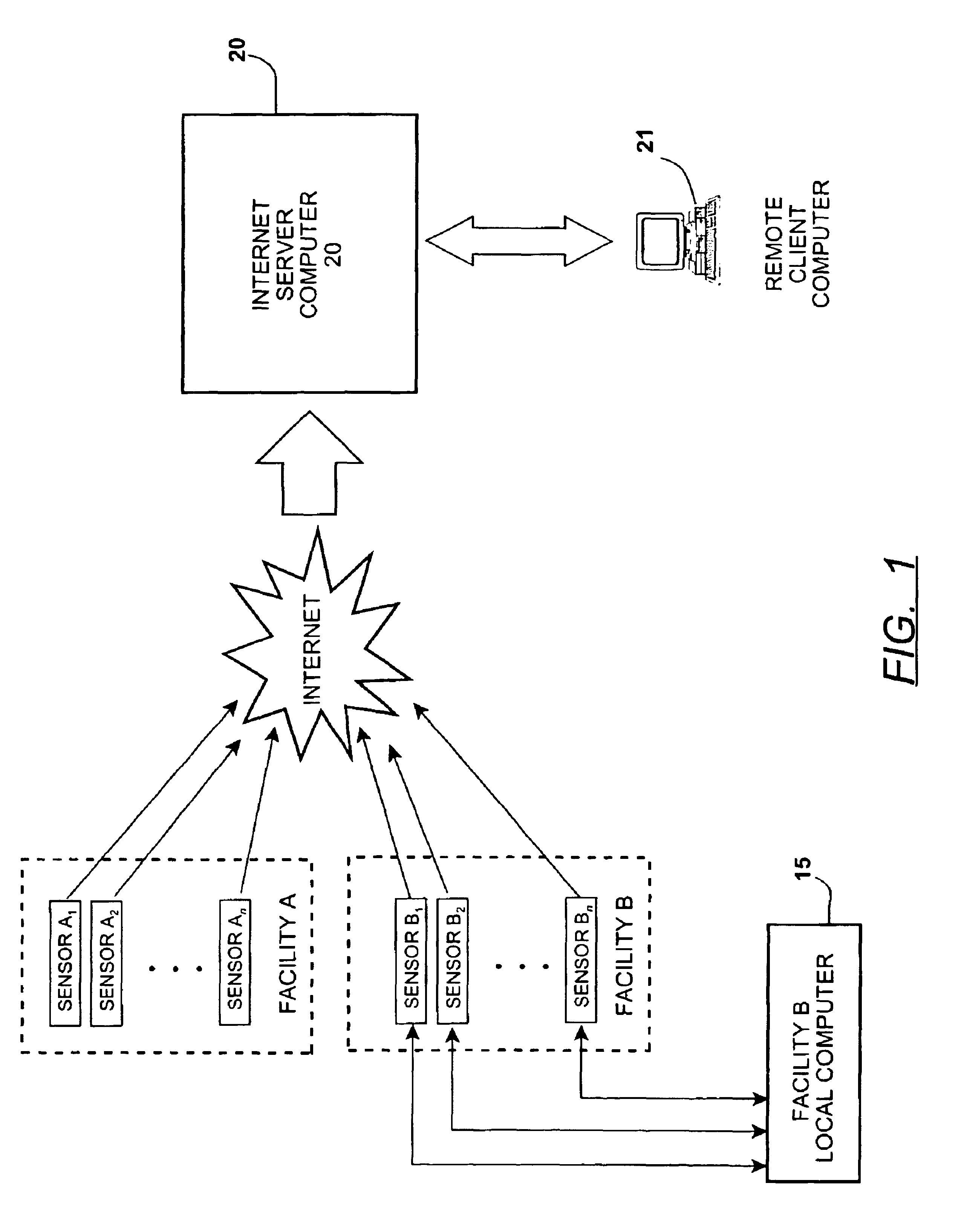
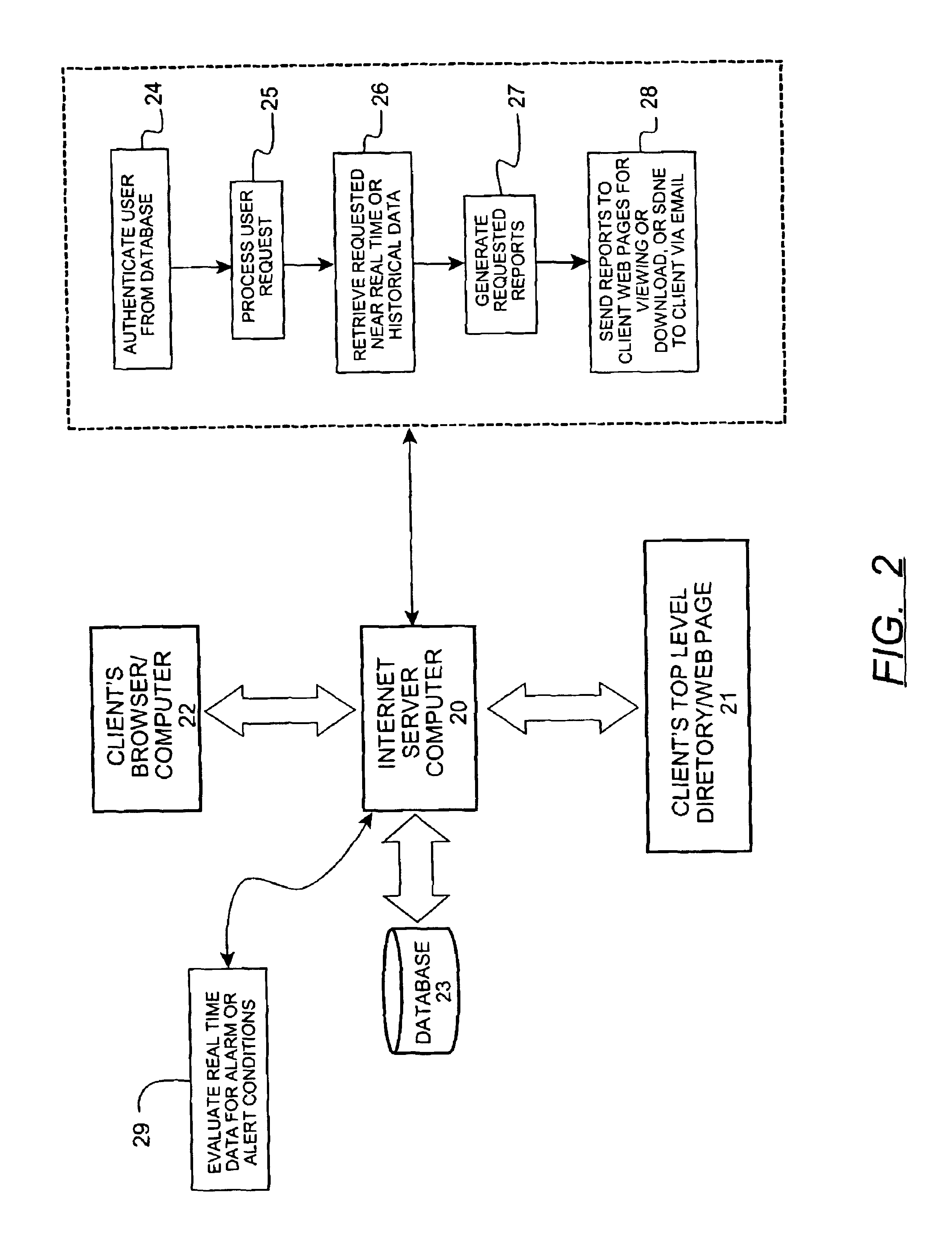
Method for remote monitoring of water treatment systems
InactiveUS6954701B2Rule out the possibilityNegating human error or tamperingUltrafiltrationSolid sorbent liquid separationWater treatment systemQuality assurance
A method of monitoring the daily operating performance parameters for water treatment processes through the collection of localized data. The data is manipulated to generate preconfigured performance, maintenance, and quality assurance reports and further provide automatic submission of data as required for regulatory review of certain water treatment systems such as potable water treatment. The data is collected from sensors located at an equipment site and transferred to a remote computer located by use of the Internet, further all data received and used for generation of reports is also accessible by Internet connection and be delivered directly to the regulatory agency without additional process.
Owner:WATEREYE +1
Encryption in a secure computerized gaming system
InactiveUS7116782B2Easy to managePublic key for secure communicationUser identity/authority verificationHash functionDigital signature
The present invention provides an architecture and method for a gaming-specific platform that features secure storage and verification of game code and other data, provides the ability to securely exchange data with a computerized wagering gaming system, and does so in a manner that is straightforward and easy to manage. Some embodiments of the invention provide the ability to identify game program code as certified or approved, such as by the Nevada Gaming Regulations Commission or other regulatory agency. The invention provides these and other functions by use of encryption, including digital signatures and hash functions as well as other encryption methods.
Owner:IGT
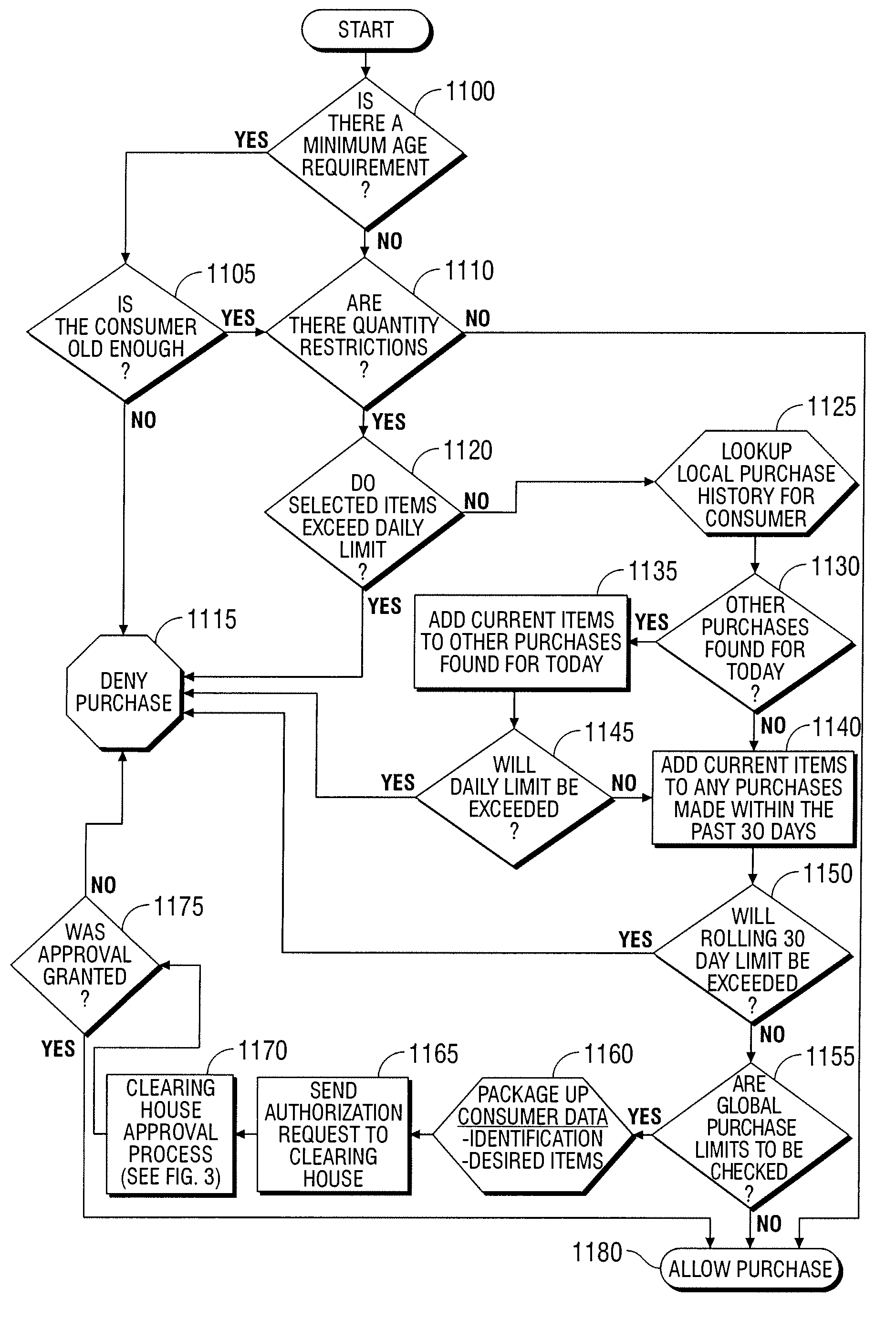
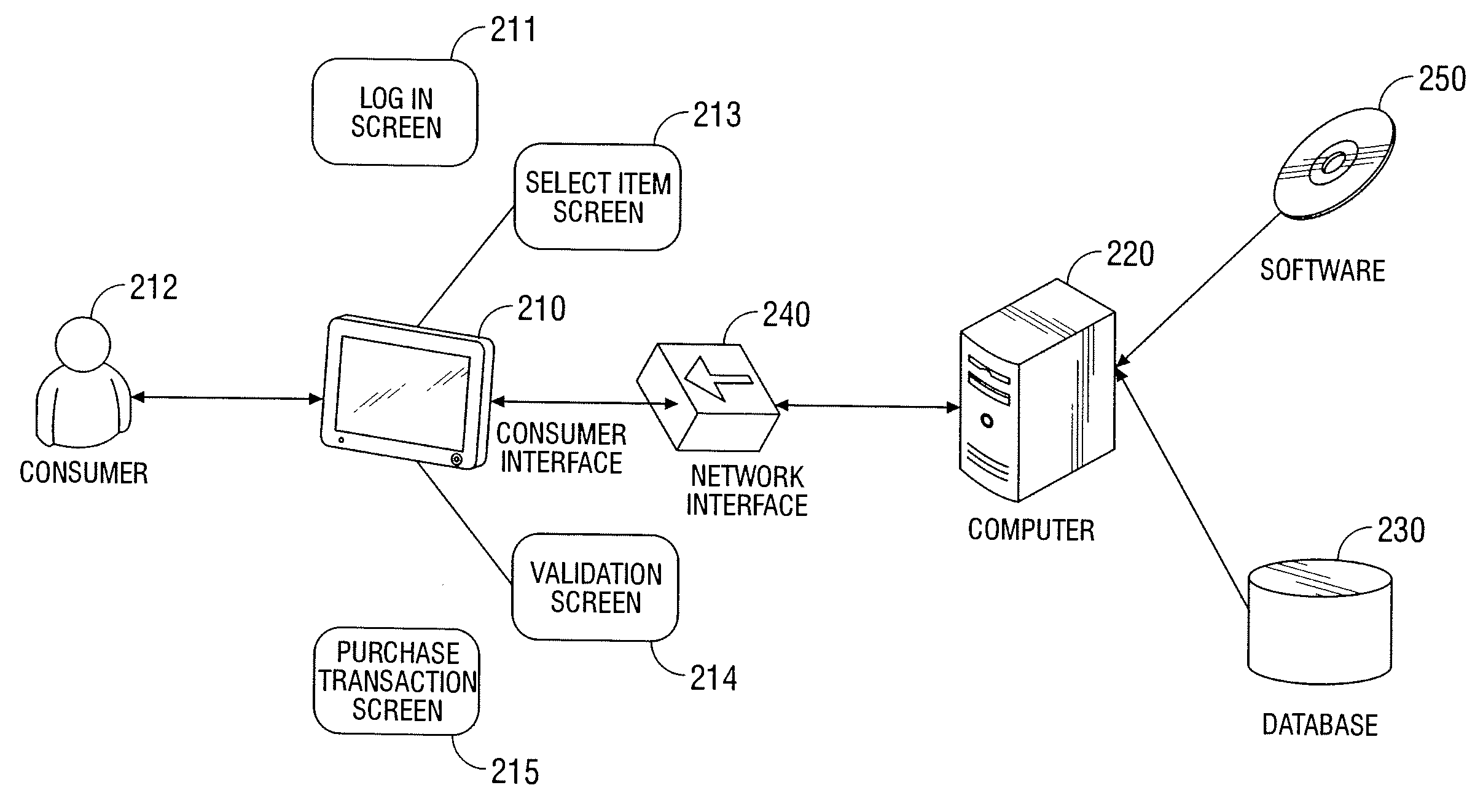
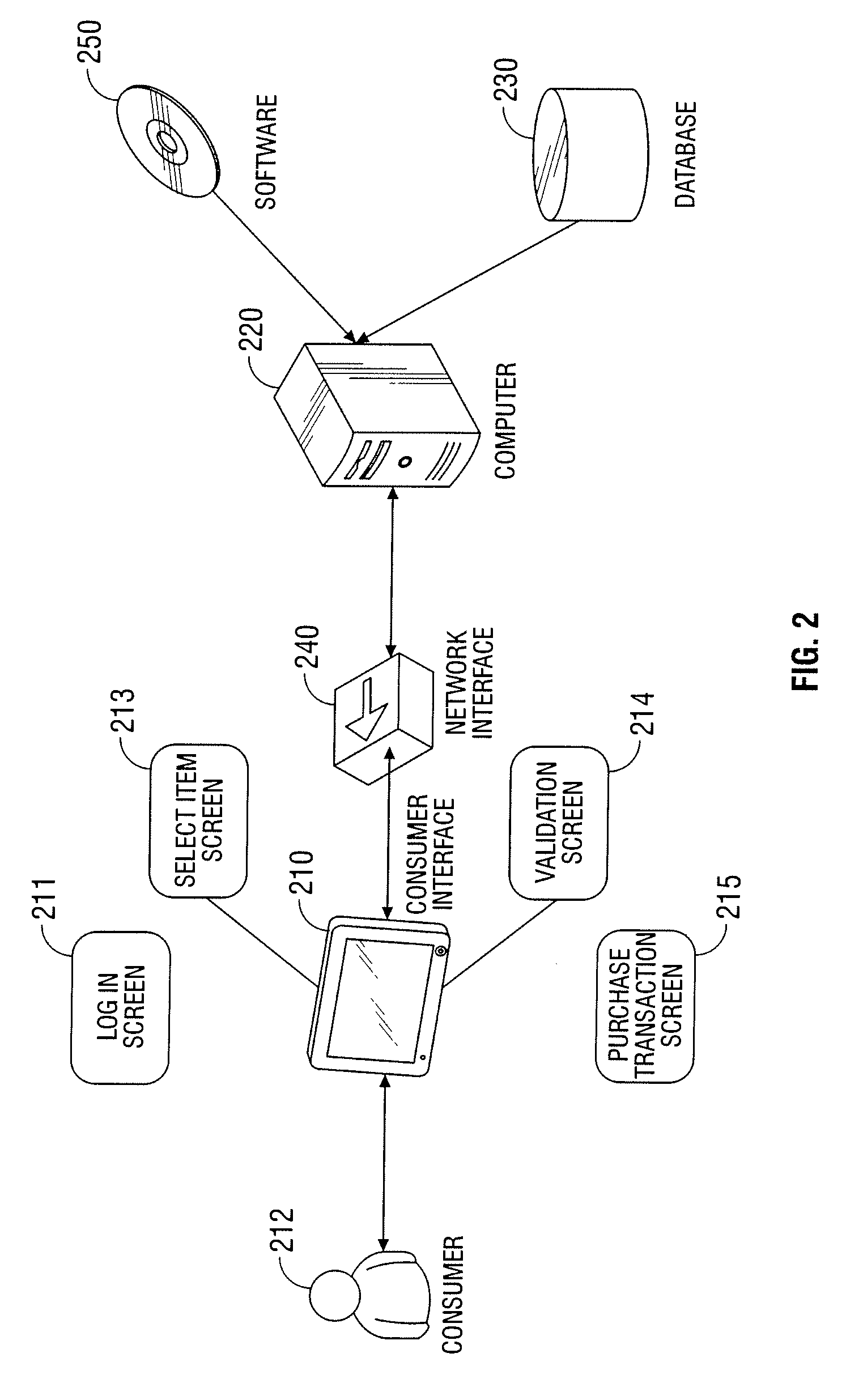
Automated vending of products containing controlled substances
ActiveUS7783379B2Efficient and widespread enforcementReduced resourceCoin-freed apparatus detailsCommercePseudoephedrineControl substances
The present invention provides for devices and methods for vending regulated products, particularly controlled substances, including those containing pseudoephedrine. The present invention allows for the identification of consumers through reliable log-in-procedures, allows the consumer to select items, validates whether the purchase request complies with regulations, to facilitate the delivery of the requested product to a consumer. Other embodiments include a vending machine that is placed into a retail environment in which software enforces validation of the purchasers' identities, limits the amount of pseudoephedrine for each purchaser within the regulations of local, state and federal agencies.This invention reduces the resources which must be expended in retail locations to comply with regulatory agencies, to implement effective counter measures against illegal purchases of regulated and controlled substances, and to ensure the effective limitation of these substances within reasonable limits required for normal consumption.
Owner:ASTERES
Predictive Key Risk Indicator Identification Process Using Quantitative Methods
Methods, computer-readable media, and apparatuses are disclosed for identifying predictive key risk indicators (KRIs) for organizations and / or firms through the application of specific statistical and quantitative methods that are well integrated with qualitative adjustment. An indicator is a variable with the purpose of measuring change in a phenomena or process. A risk indicator is an indicator that estimates the potential for some form of resource degradation using mathematical formulas or models. Organization / enterprise key risk indicators are an essential arsenal in the risk management framework of any firm or organization and may be required by regulatory agencies.
Owner:BANK OF AMERICA CORP
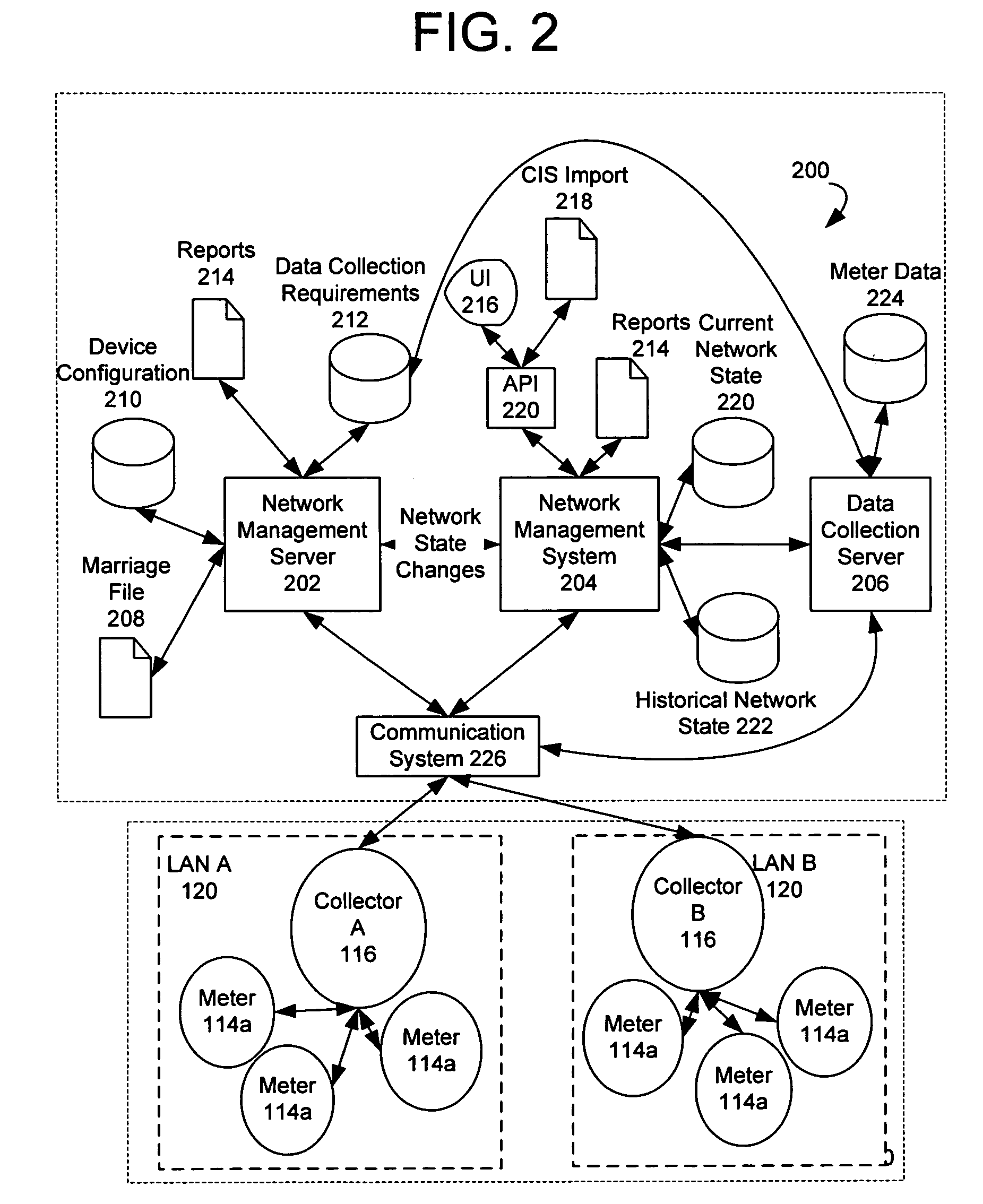
System and method for creating multiple operating territories within a meter reading system
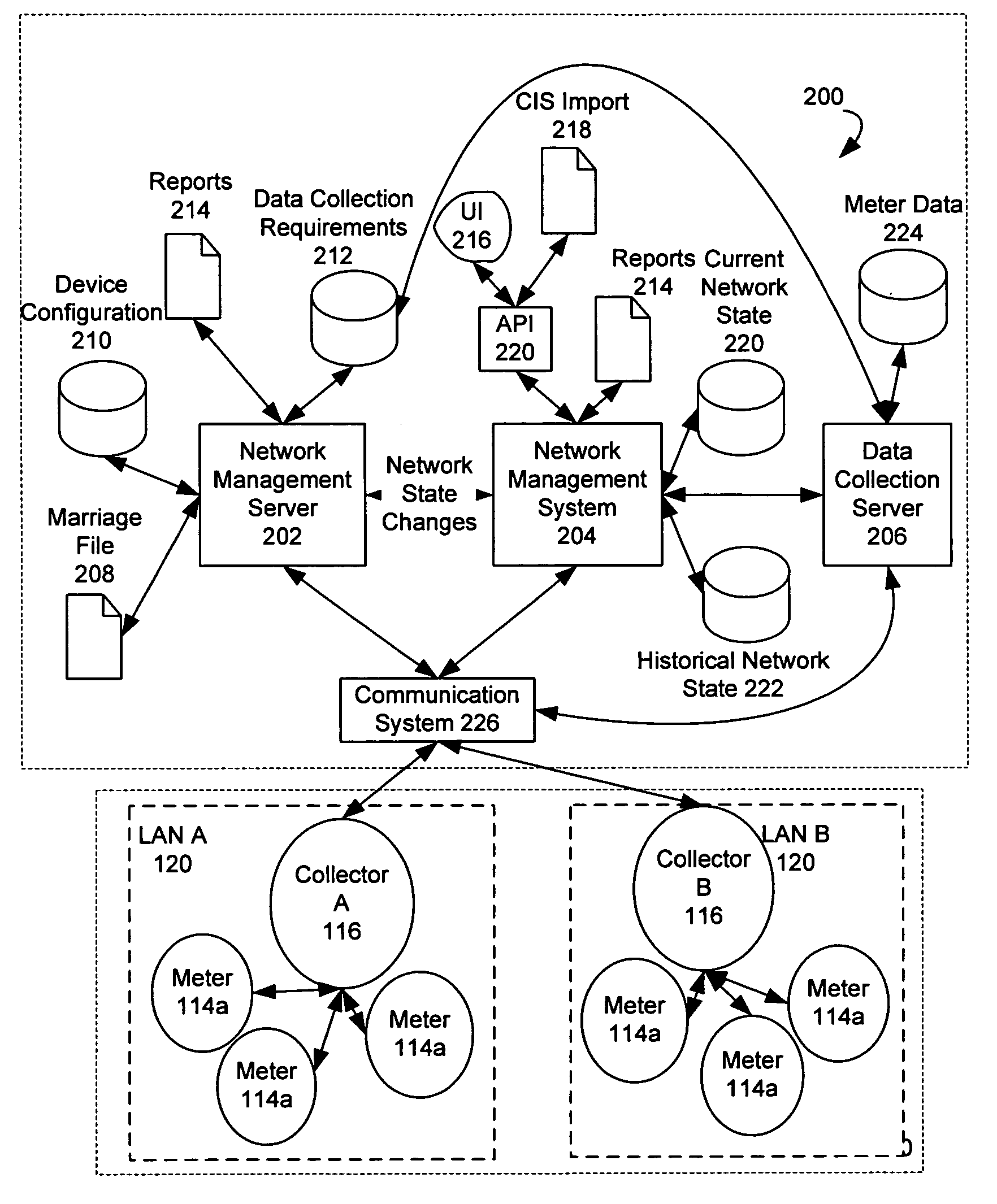
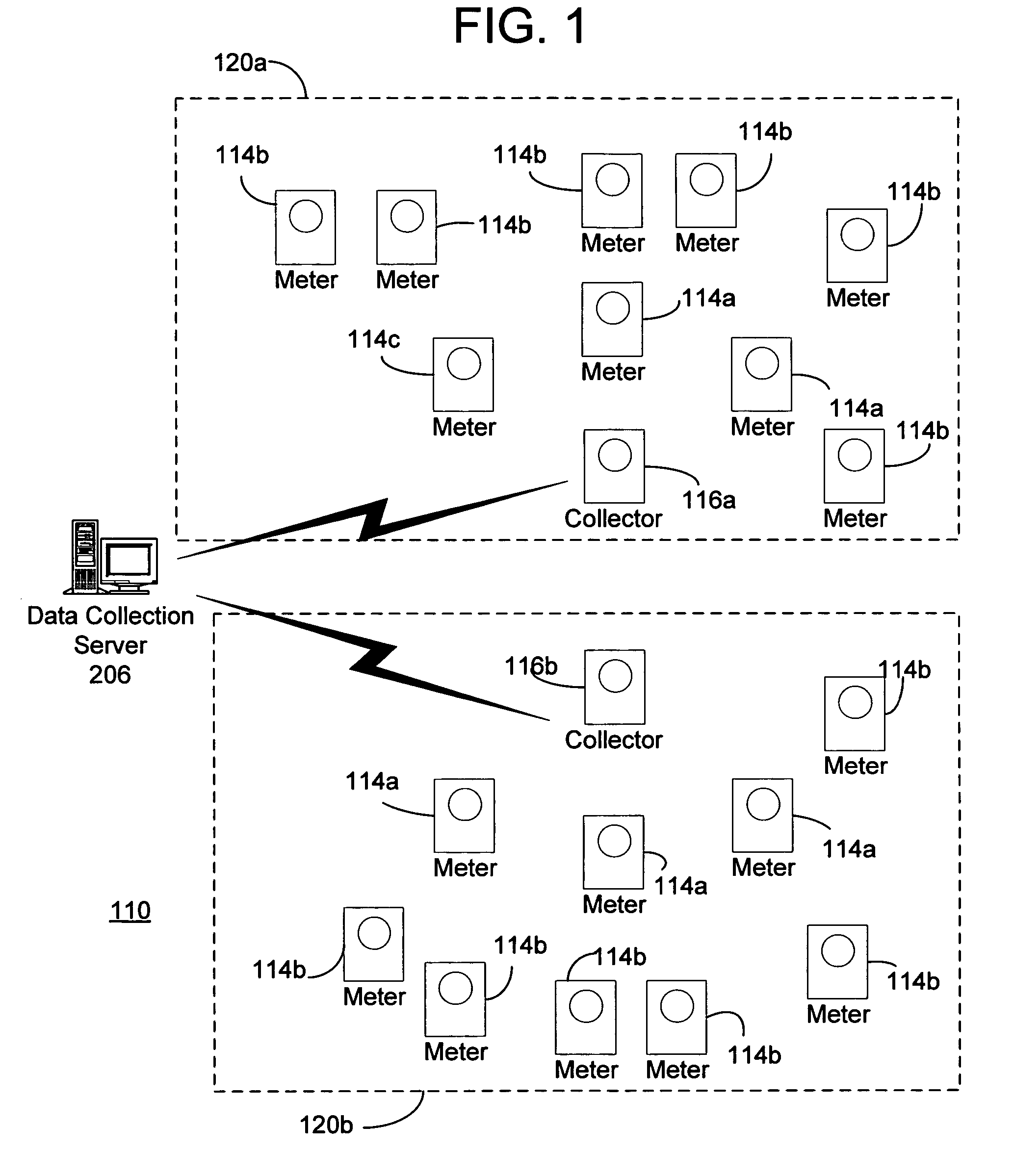
InactiveUS7170425B2Close proximityAvoid registrationElectric signal transmission systemsMobile data collection deviceTime of useComputer science
Owner:ELSTER ELECTRICTY LLC
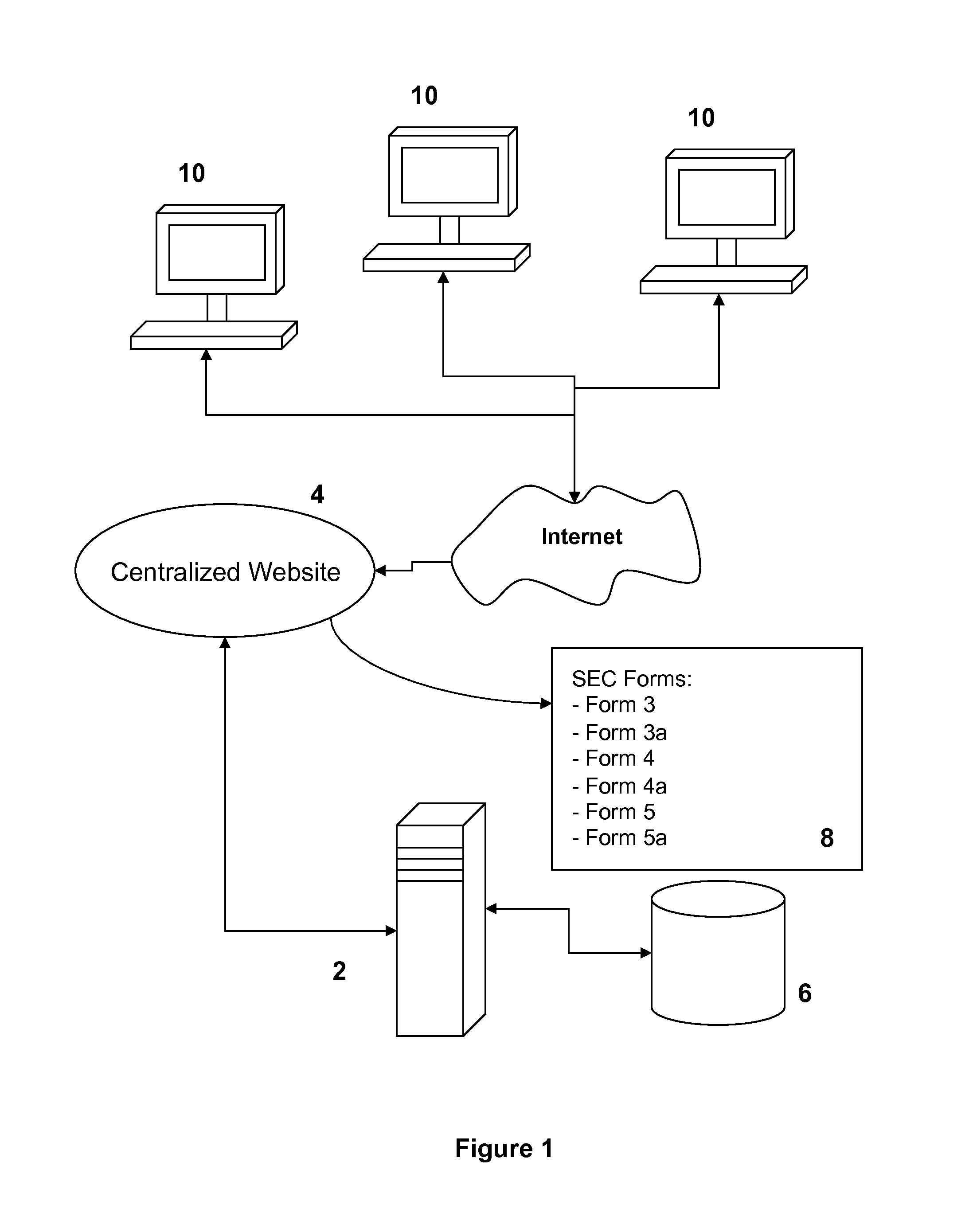
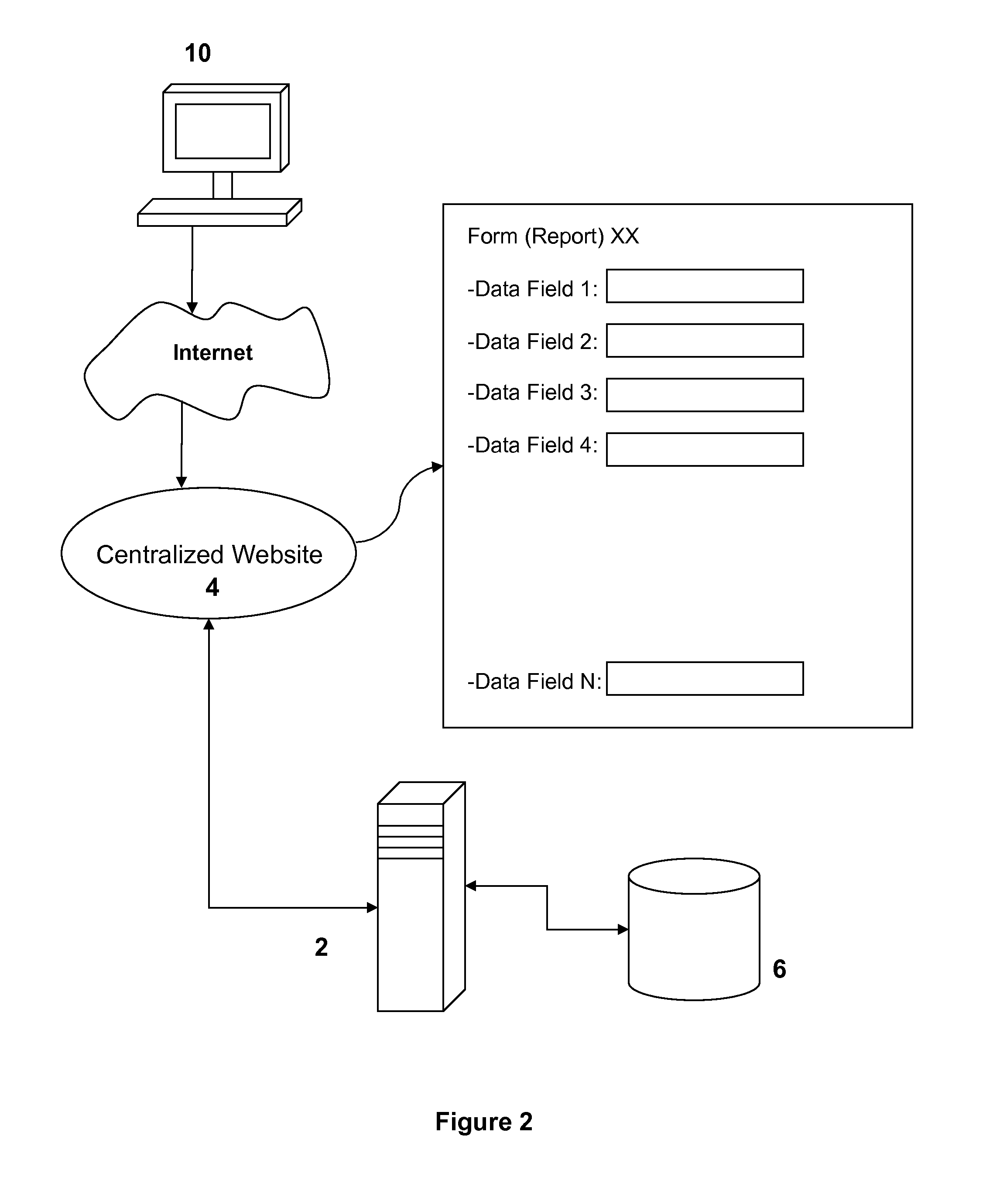
Systems and methods for preparing and submitting documents to comply with securities regulations
InactiveUS8813178B1Facilitate and expedite and minimize amount of errorFast preparationDigital data processing detailsMultiple digital computer combinationsGraphicsGraphical user interface
Owner:MARKETFORMS
Automated Vending of Products Containing Controlled Substances
ActiveUS20080269947A1Efficient and widespread enforcementReduced resourceAcutation objectsCoin-freed apparatus detailsPseudoephedrineControl substances
The present invention provides for devices and methods for vending regulated products, particularly controlled substances, including those containing pseudoephedrine. The present invention allows for the identification of consumers through reliable log-in-procedures, allows the consumer to select items, validates whether the purchase request complies with regulations, to facilitate the delivery of the requested product to a consumer. Other embodiments include a vending machine that is placed into a retail environment in which software enforces validation of the purchasers' identities, limits the amount of pseudoephedrine for each purchaser within the regulations of local, state and federal agencies.This invention reduces the resources which must be expended in retail locations to comply with regulatory agencies, to implement effective counter measures against illegal purchases of regulated and controlled substances, and to ensure the effective limitation of these substances within reasonable limits required for normal consumption.
Owner:ASTERES
Enhanced Note Processing
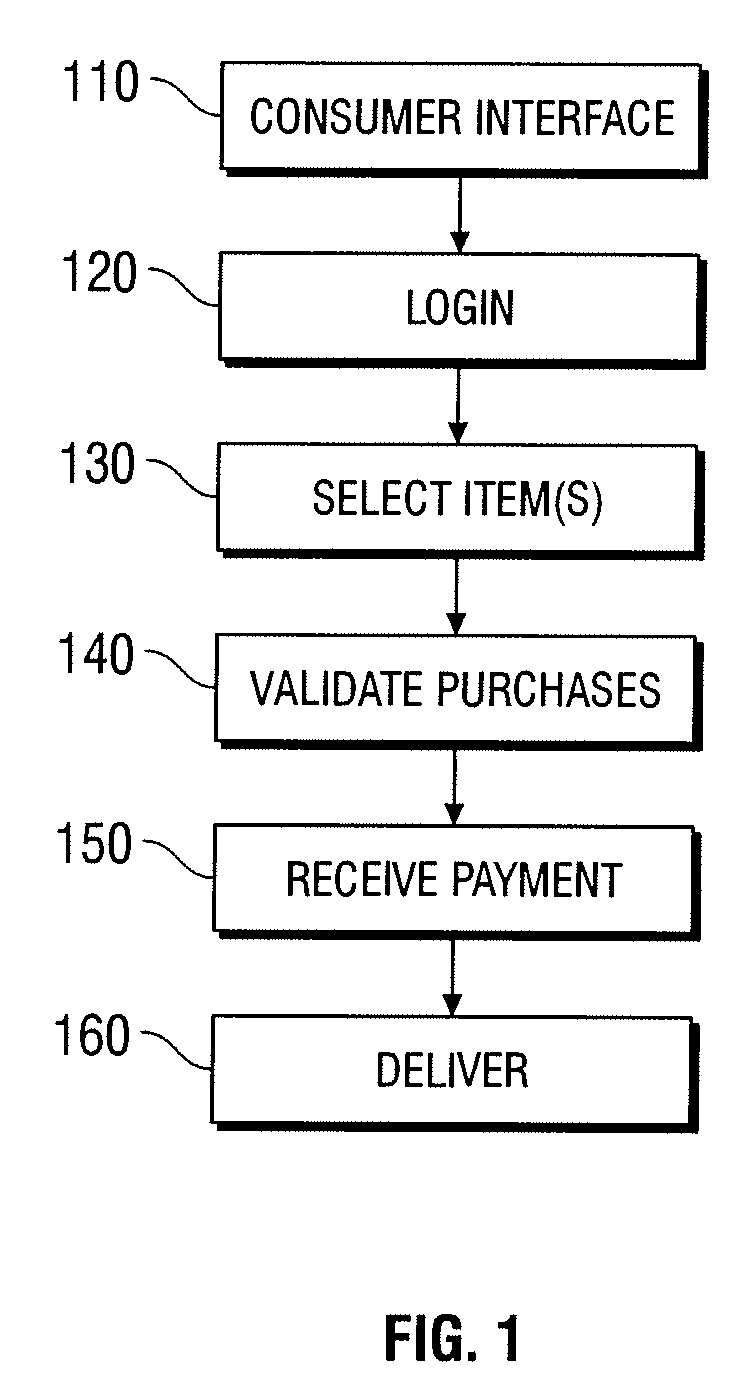
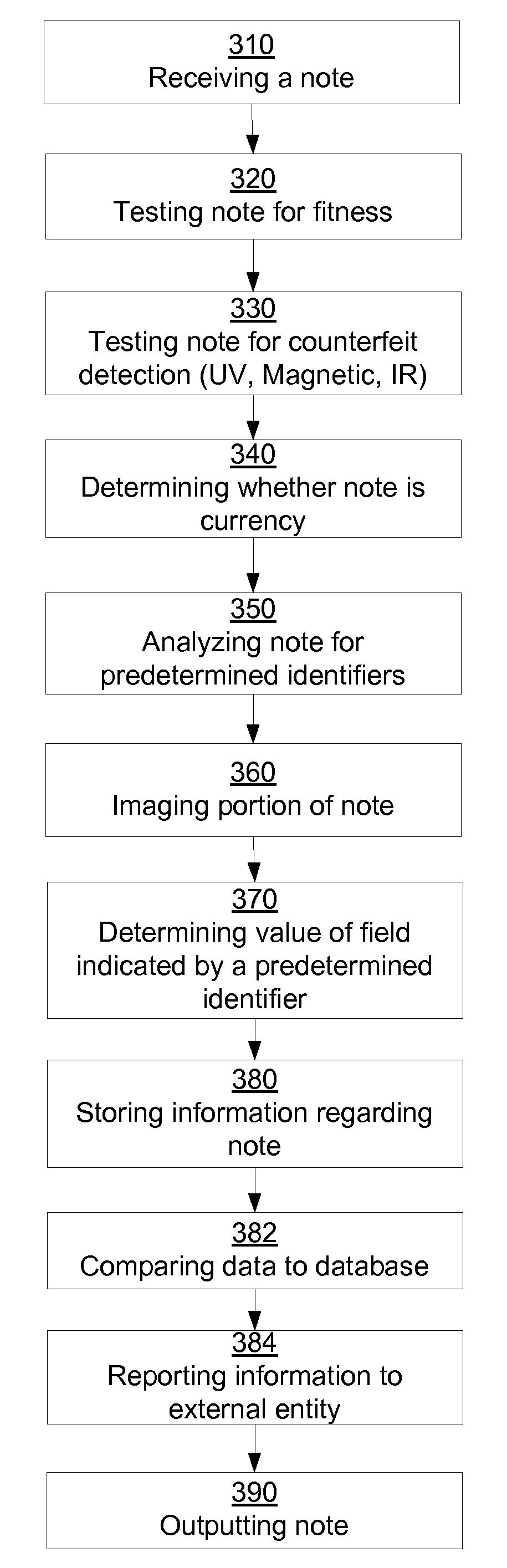
Techniques and systems are disclosed to perform, in some examples, the steps of receiving a note or an image of a note, imaging at least a portion of the note, determining a value of at least one field indicated by a predetermined identifier of the note through character and mark recognition, and storing information regarding the note in a memory. The information regarding the note that may be stored in a memory may be forwarded to a regulatory agency or an external entity for reporting or record-keeping.
Owner:BANK OF AMERICA CORP
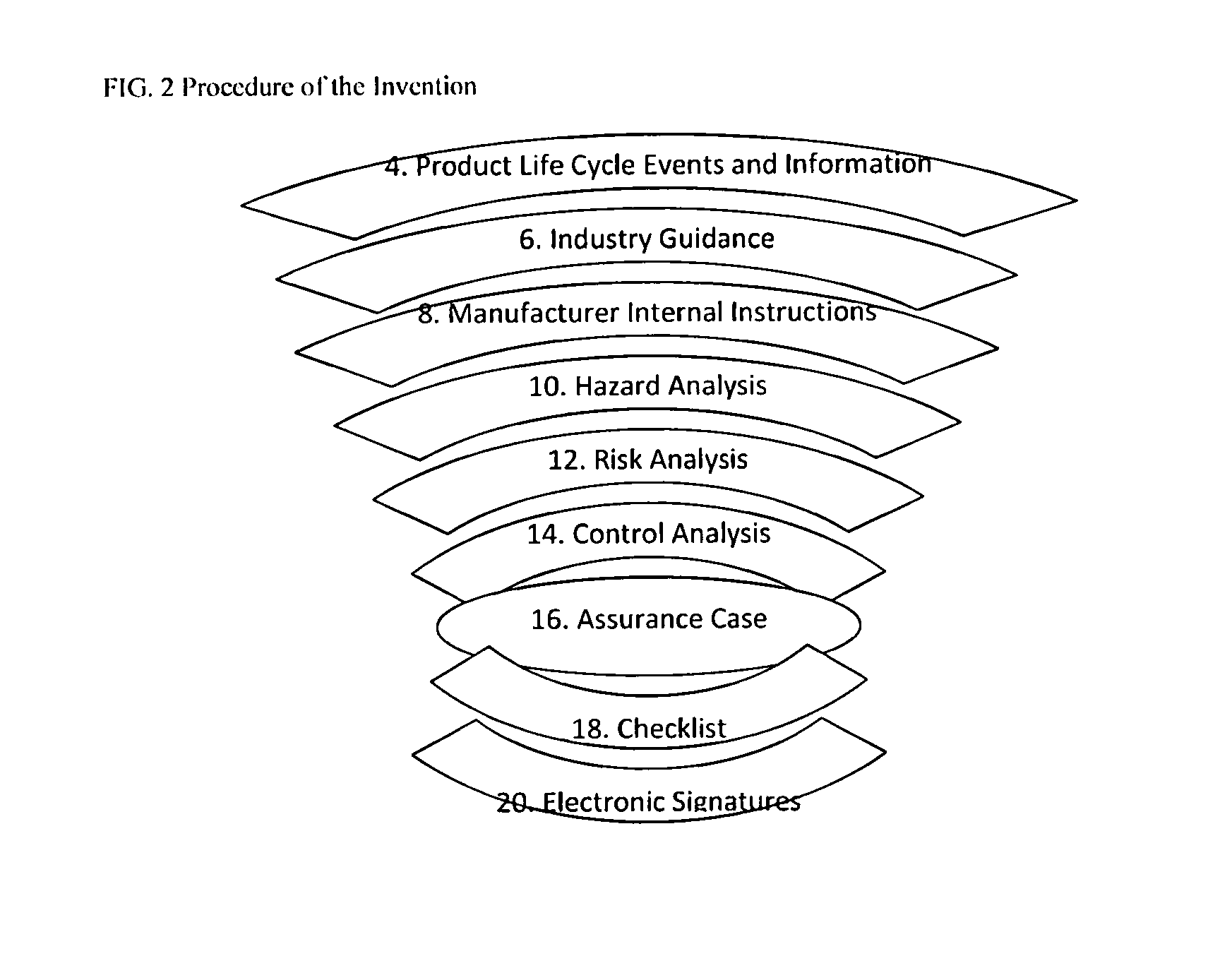
System for collecting and managing risk management file and safety assurance case data
Owner:WU FUBIN
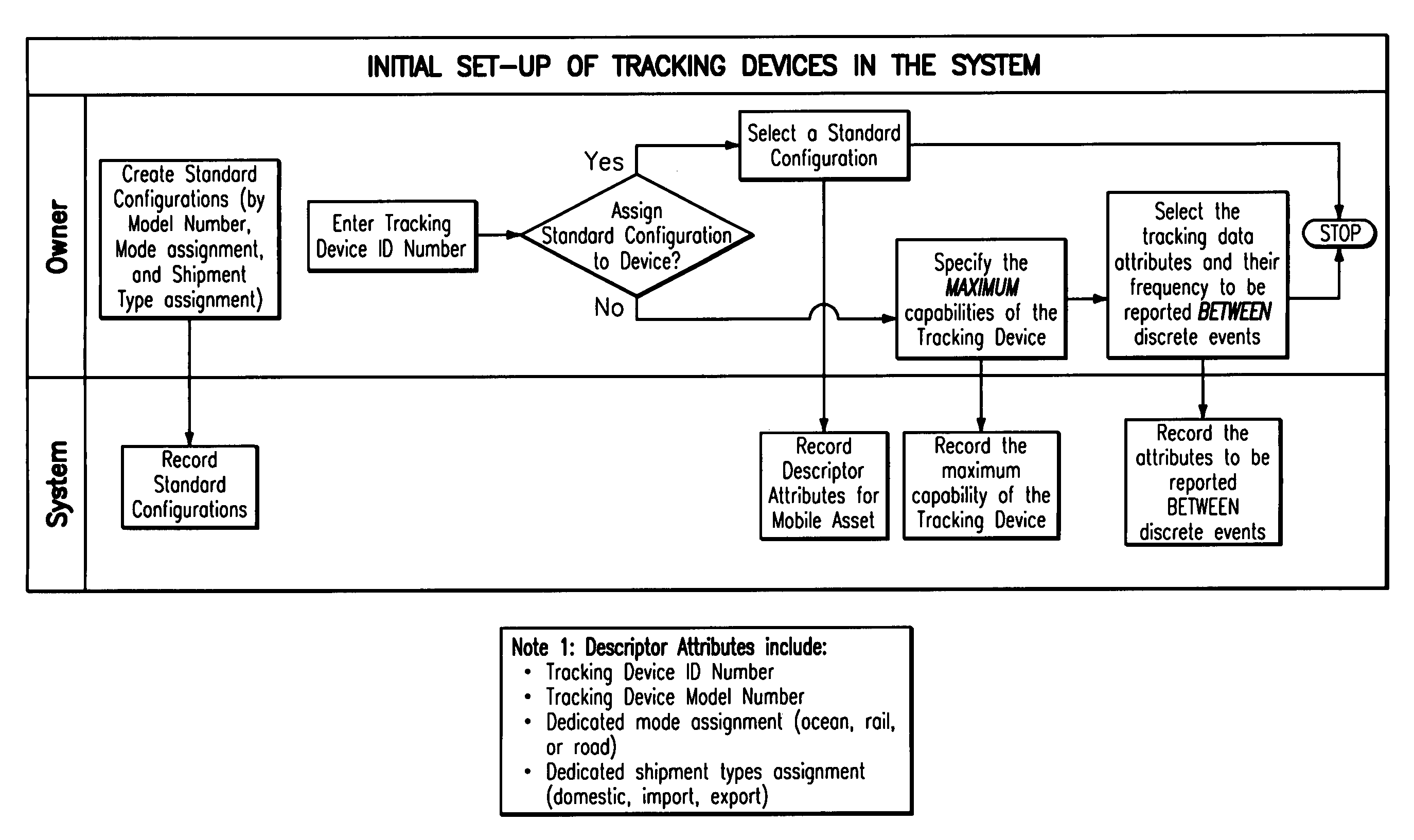
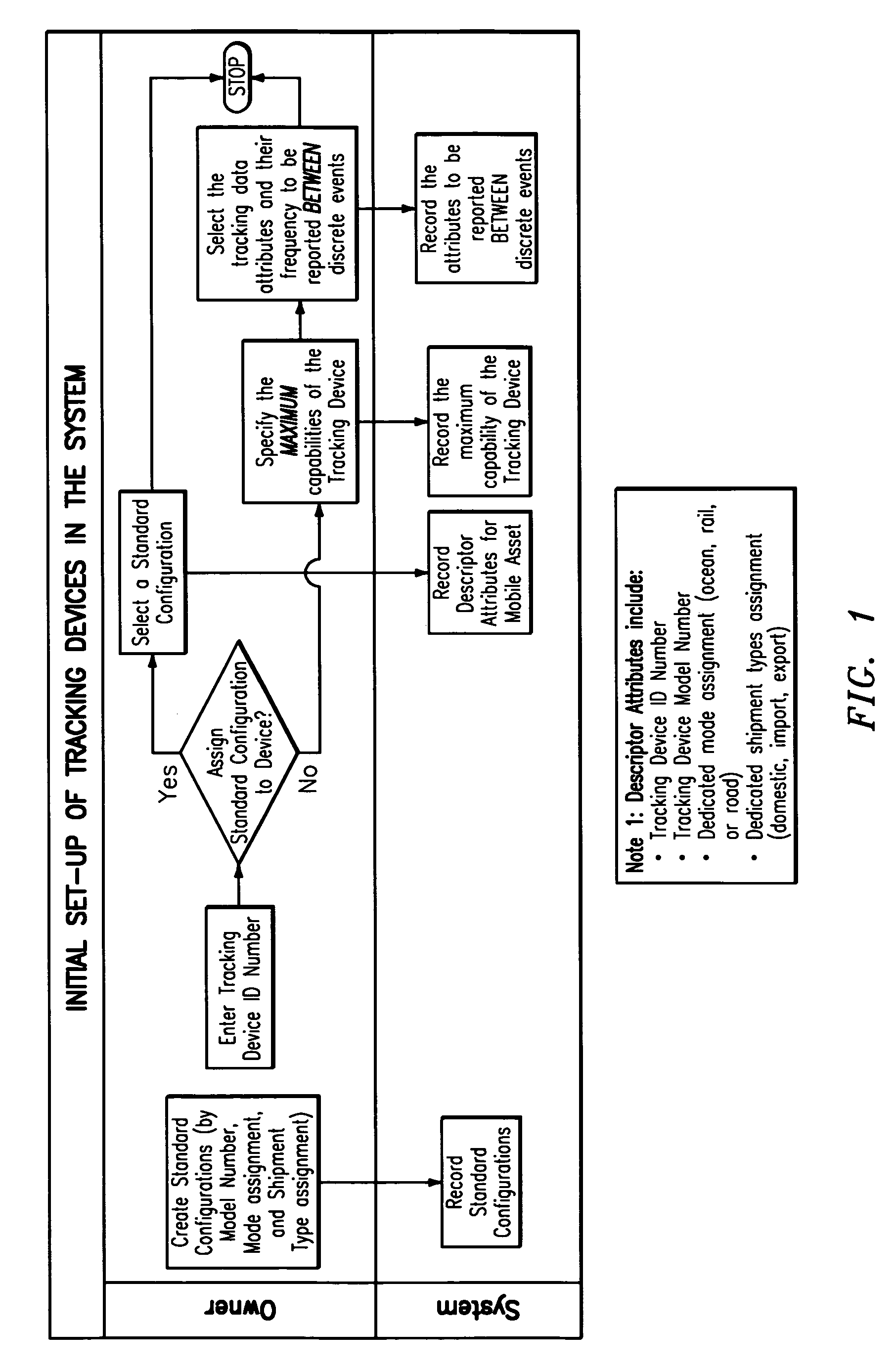
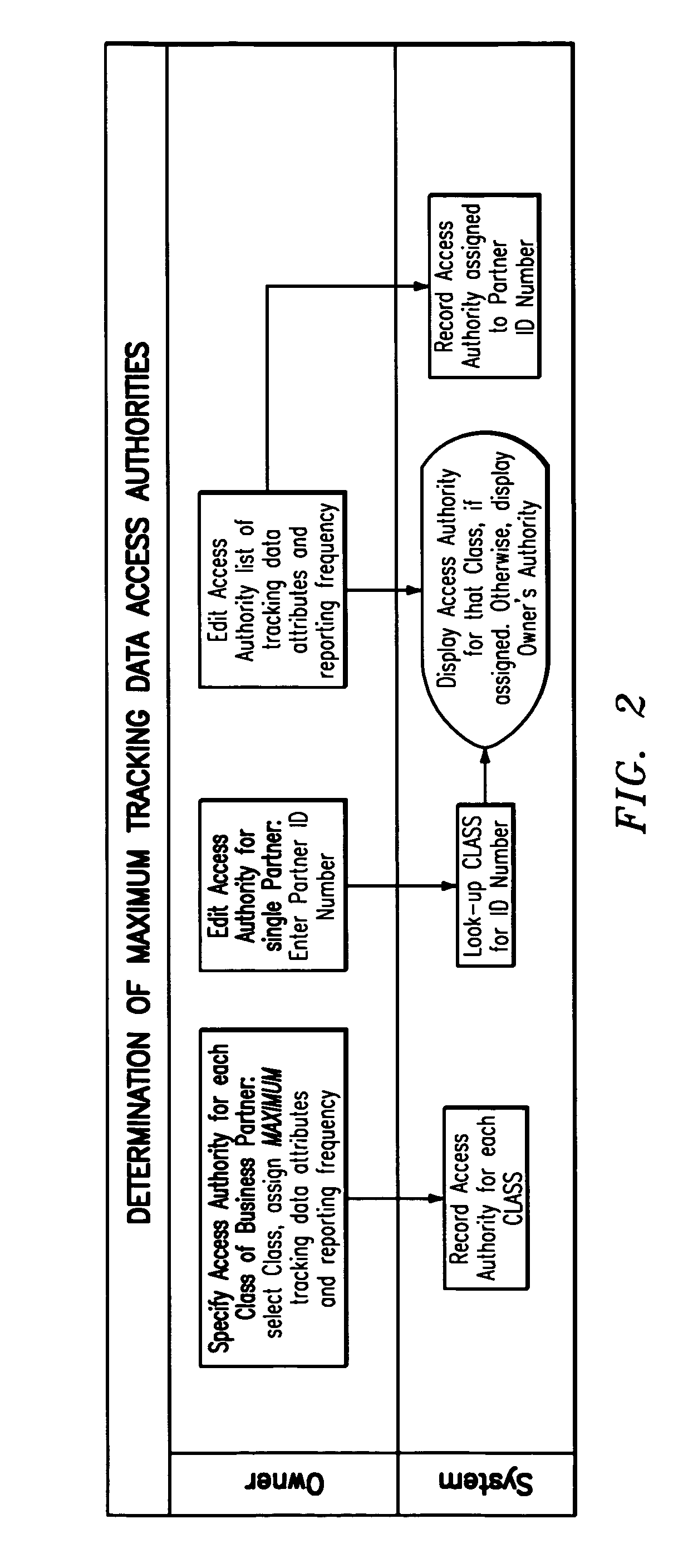
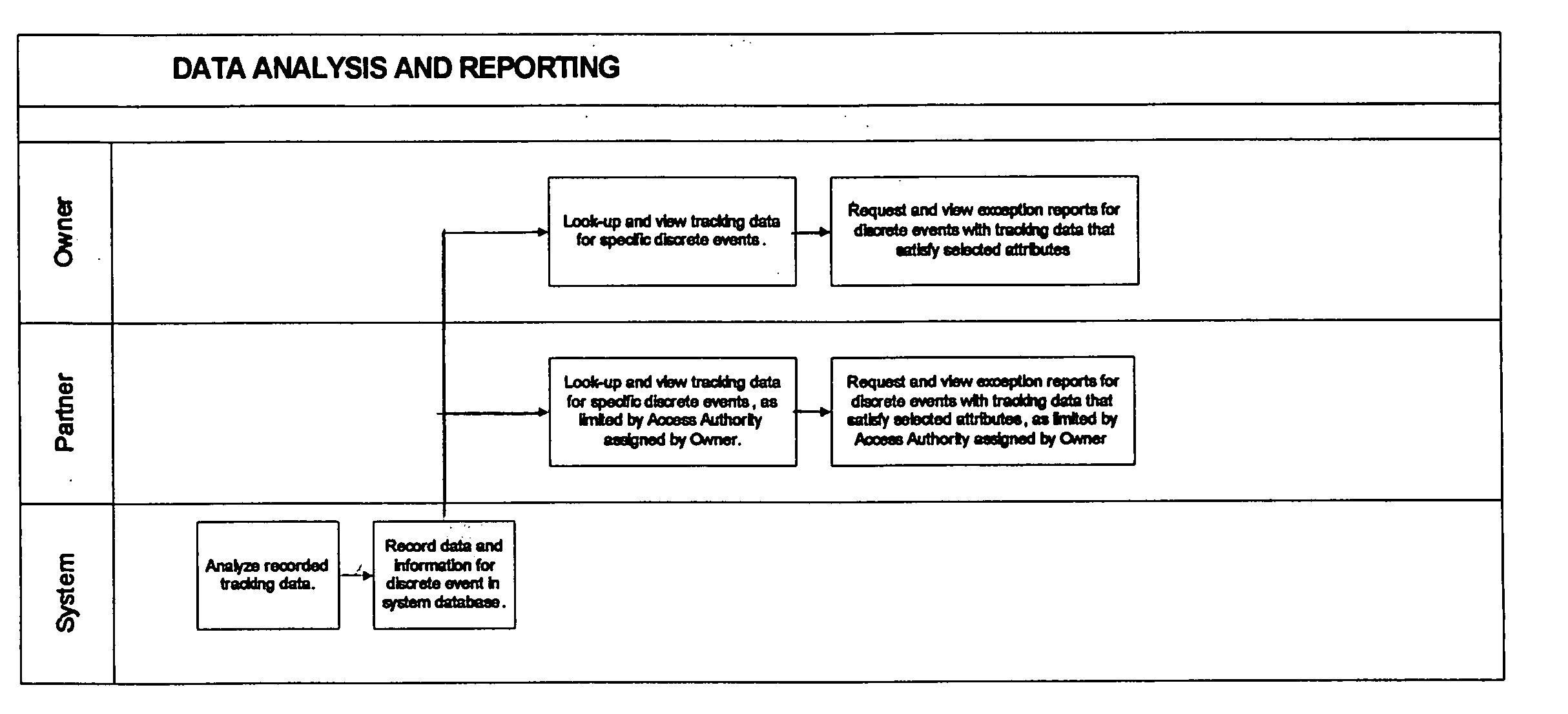
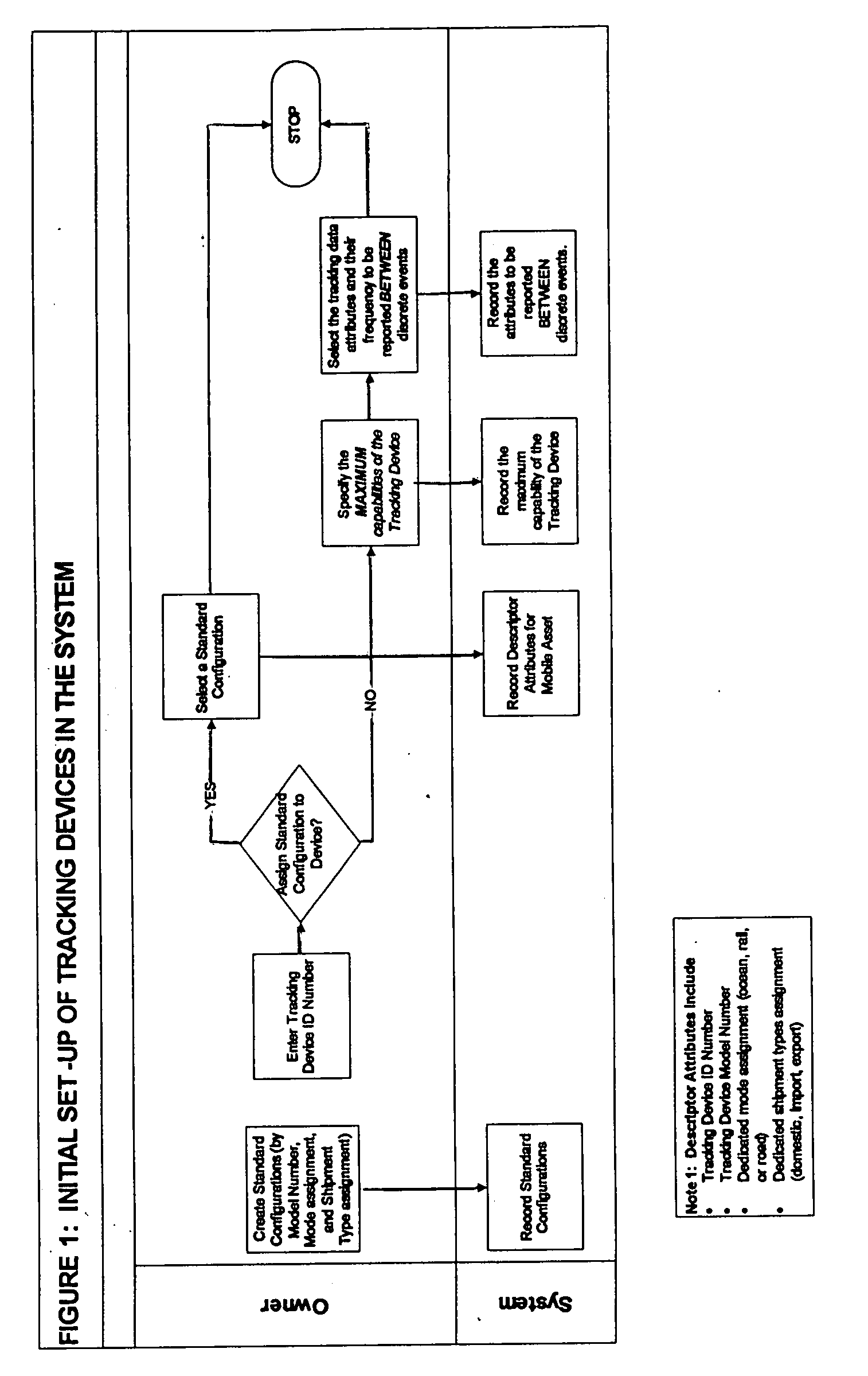
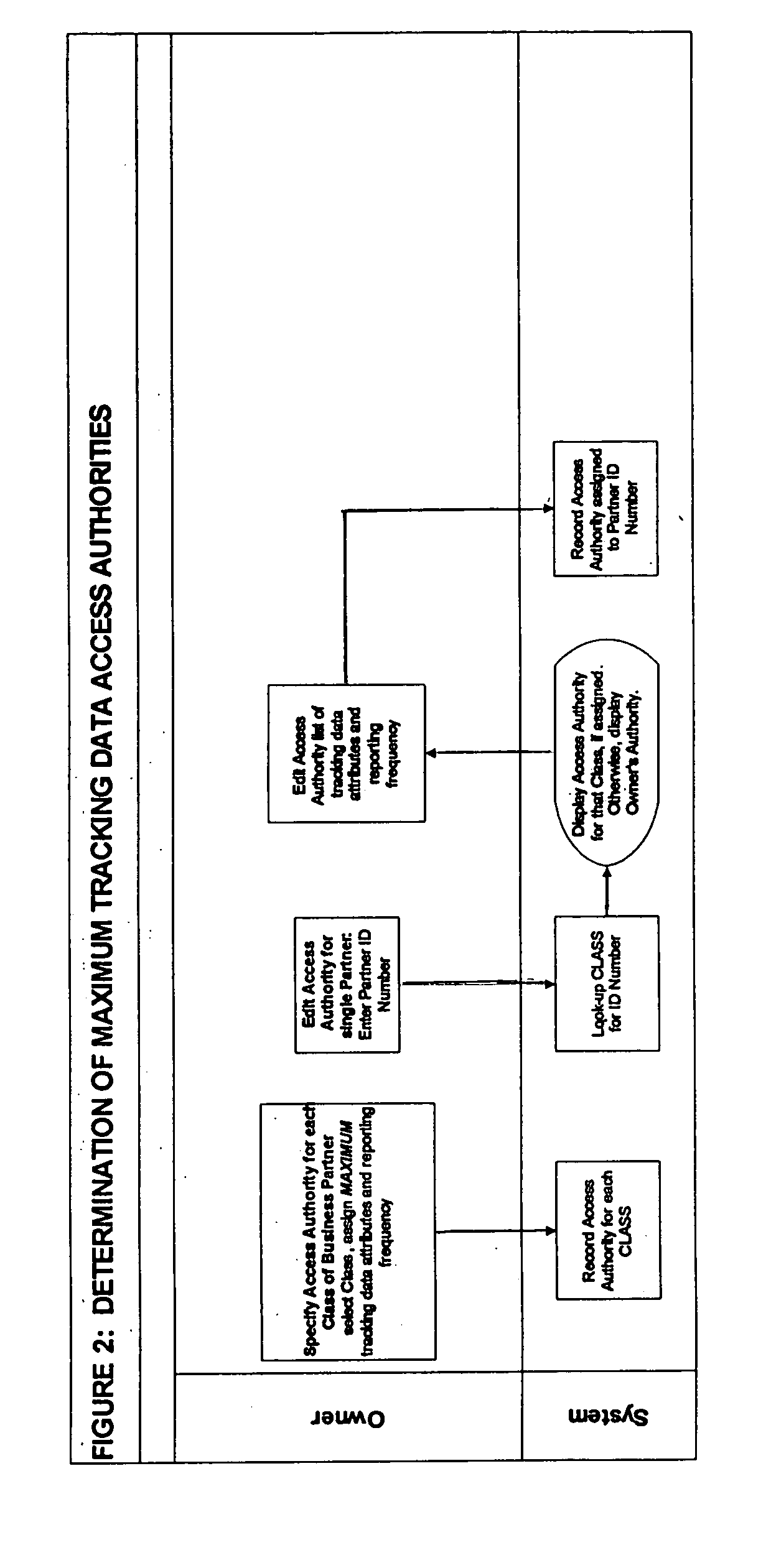
System and method for effectuating the acquisition and distribution of tracking data on mobile assets, including shipment containers used in freight transportation
ActiveUS7385500B2Electric signal transmission systemsFrequency-division multiplex detailsLogistics managementInternet based
A method and system for effectuating the optimum configuration of a duplex tracking device used to track the location and attributes of a mobile asset during a discrete event and the distribution of the data reported by the device so that the owner of the mobile asset and one or more of the owner's business partners can contemporaneously access the tracking data that they require. Each party first specifies a minimum configuration for all events with which they are associated, and then optionally specifies more extensive configurations for classes of discrete events. The owner may also constrain the data that partners can request by specifying access authorities for each class of business partners. The configuration parameters for a discrete event are systematically determined to minimize the data to be reported by the device while still meeting the requirements of all the parties, as constrained by the access authorities. Each party may then view and edit, as desired, the configuration until it is frozen prior to satellite transmission to the tracking device. The apparatus includes an internet-based program tool by which any participant can contemporaneously participate in the specification of the configuration parameters for the tracking device for a discrete event, and also access the data for events with which they are associated and generate exception reports. In a preferred embodiment, the mobile asset is a shipment container used to transport freight by ocean, rail, or road, the tracking device reports via satellite communications, the discrete event is a single shipment of goods from a origin location to a destination location, and the parties include the owner of the mobile asset (carrier), the owner of the contents (shipper), the receiver (consignee), and relevant logistics providers and regulatory agencies.
Owner:IGIT ENTERPRISES
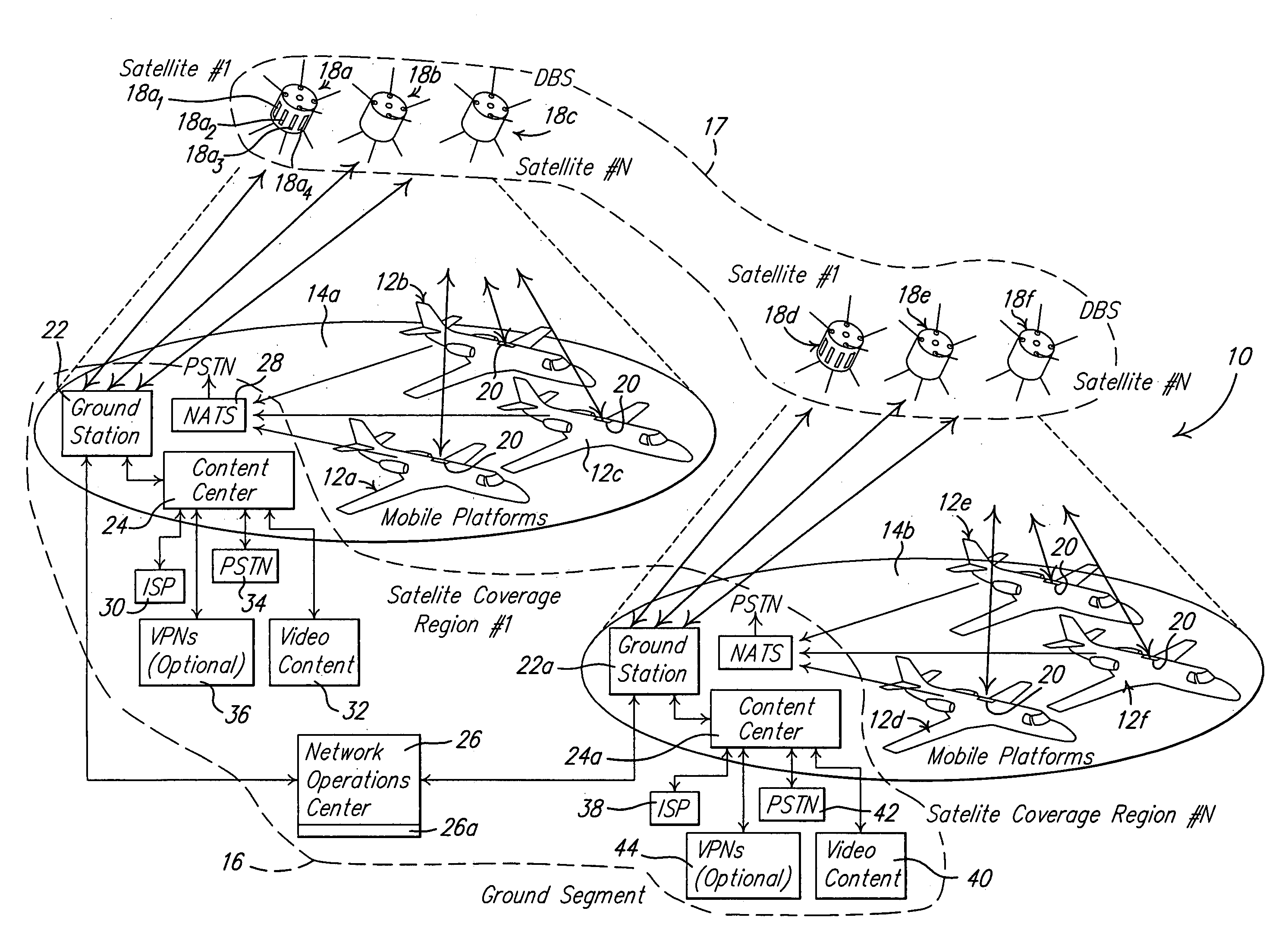
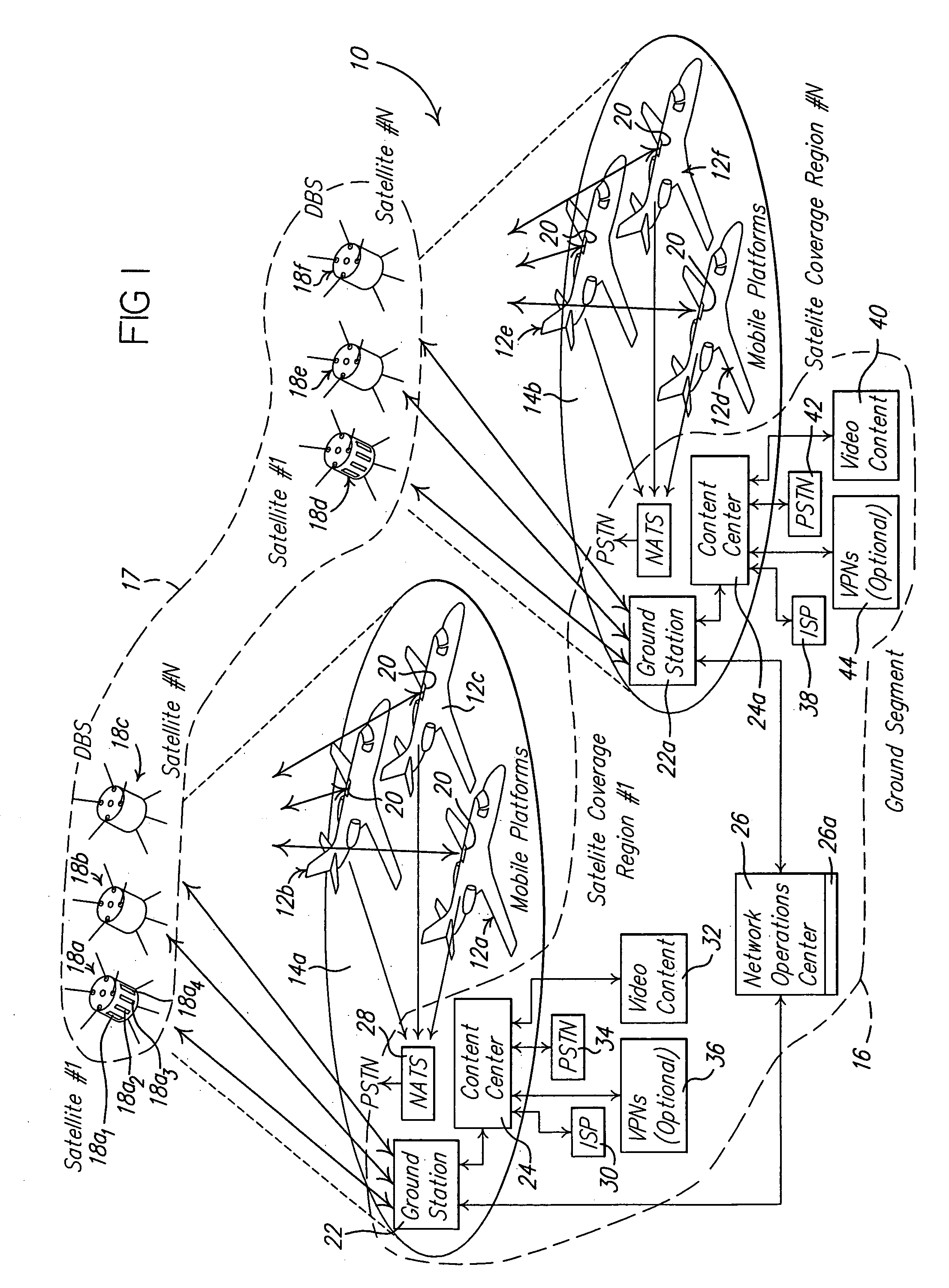
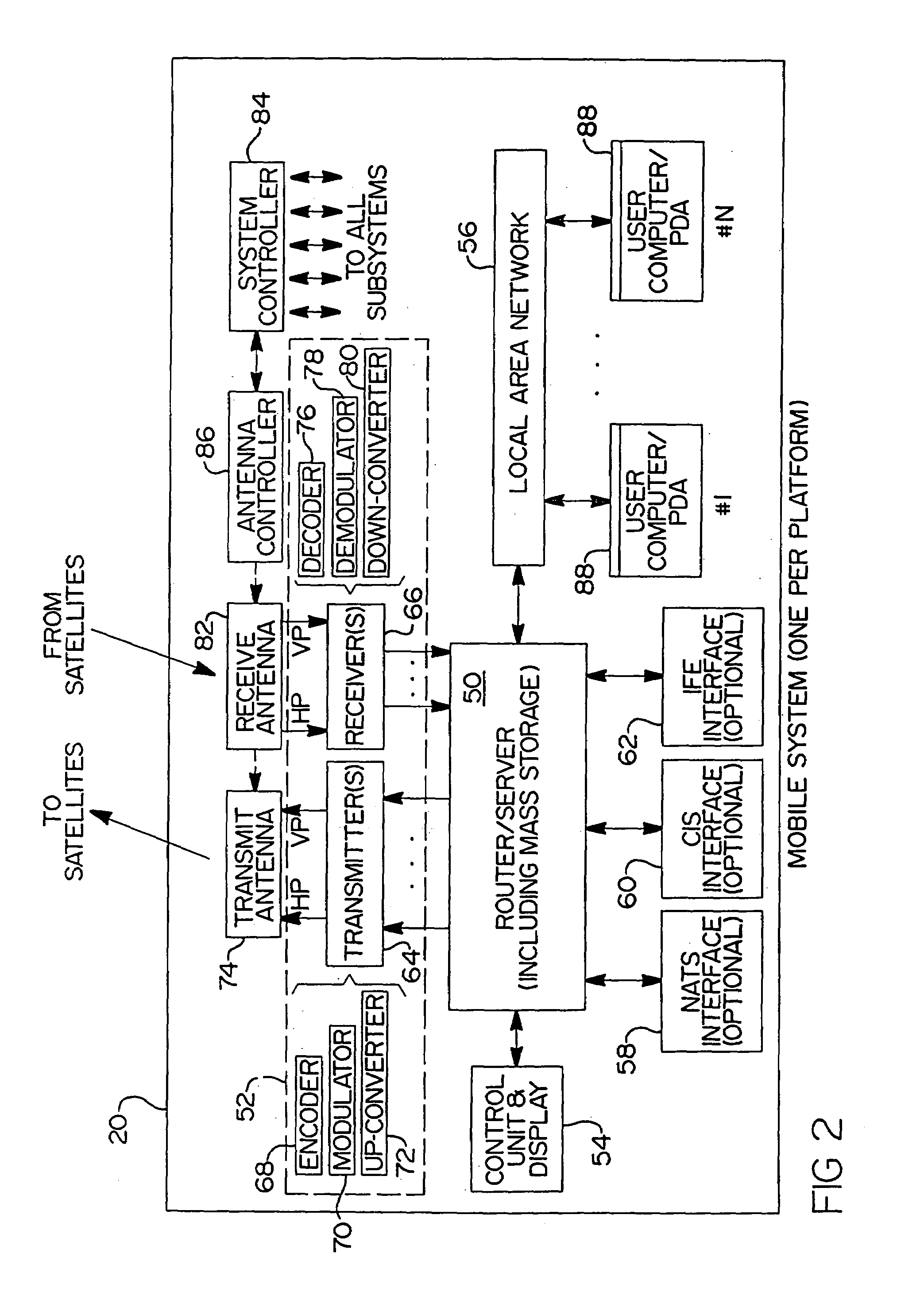
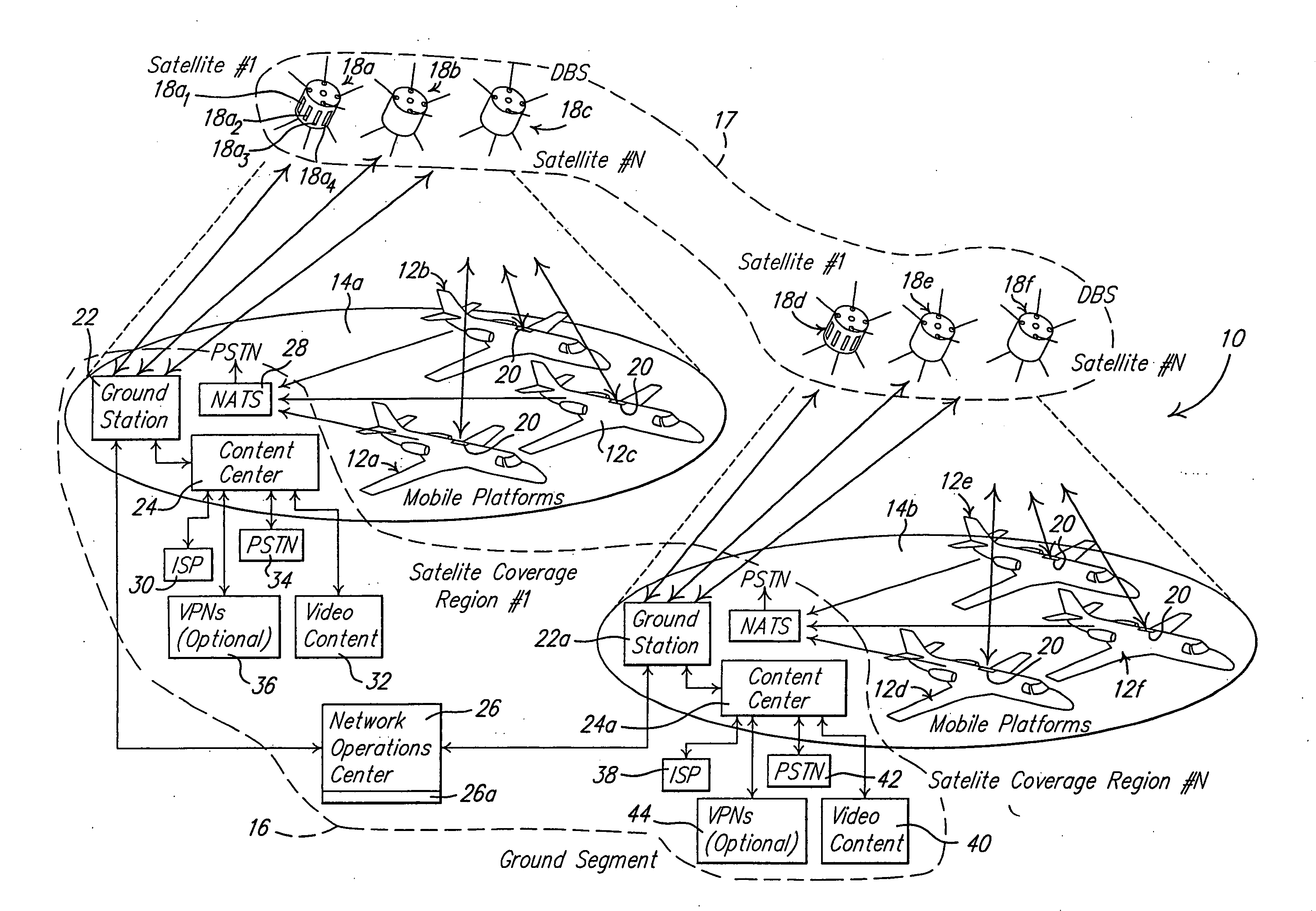
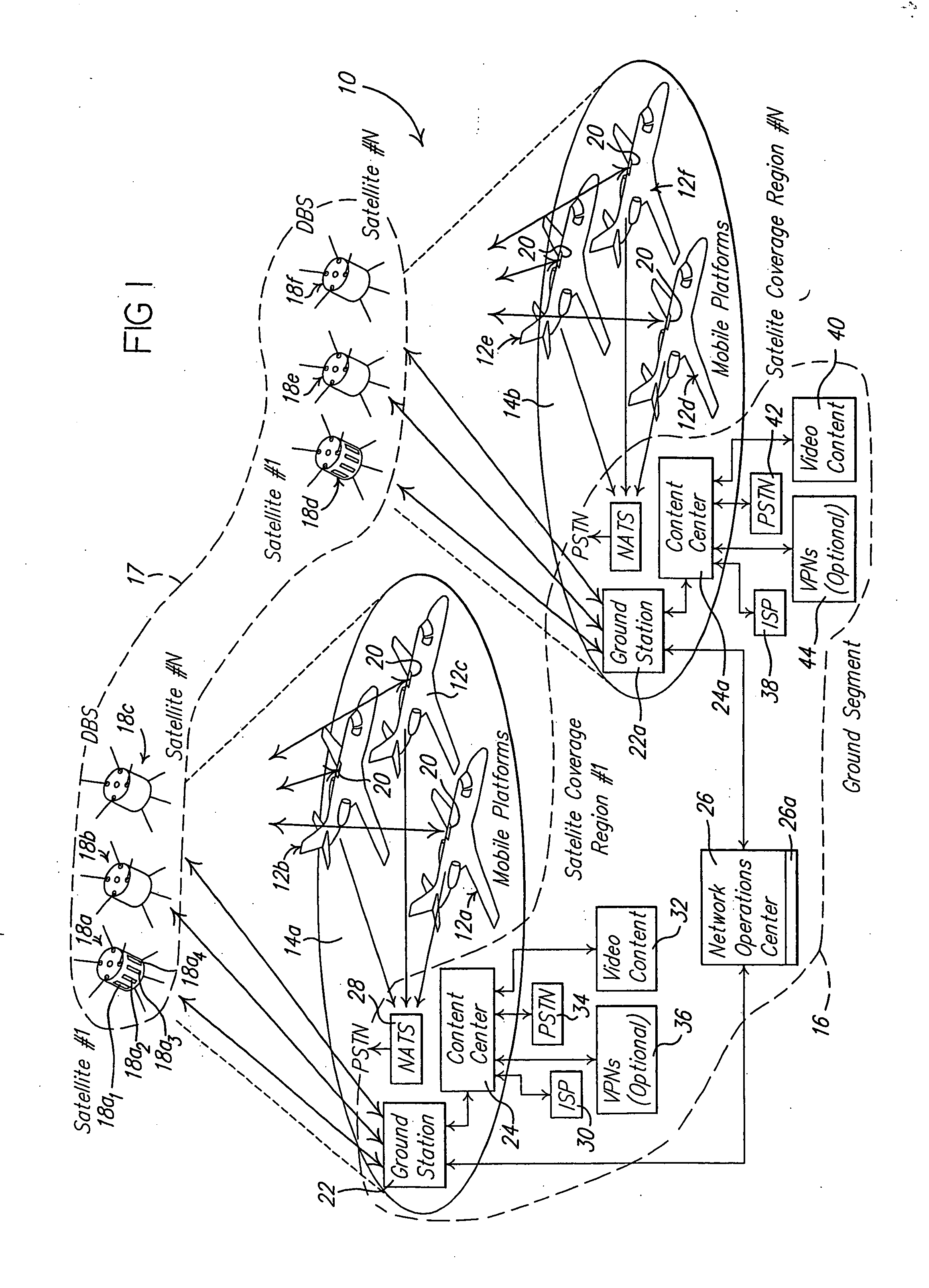
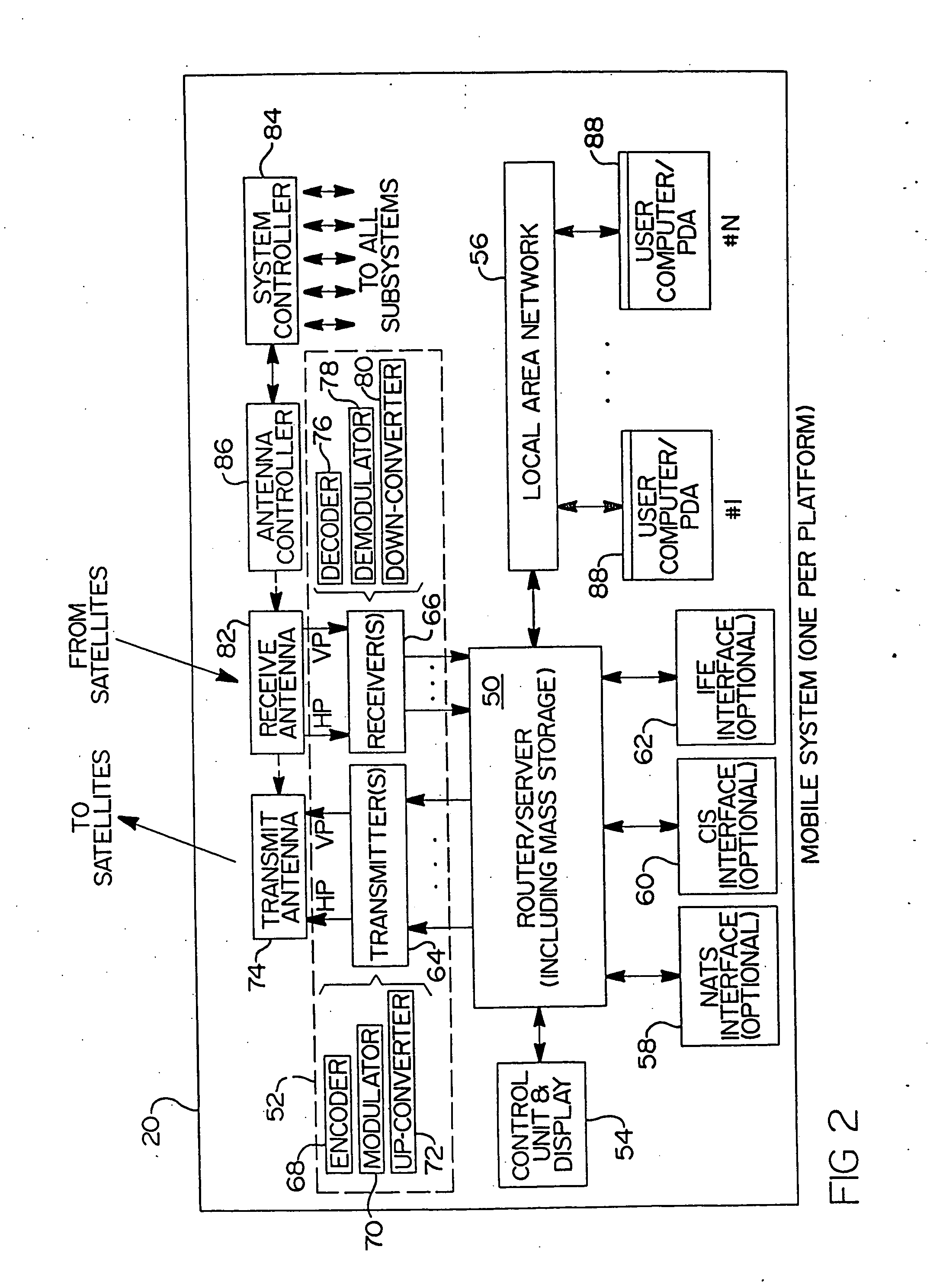
Return link design for PSD limited mobile satellite communication systems
InactiveUS7054593B2Maximize system efficiencyReduce system operating costsPower managementActive radio relay systemsTransmitted powerEngineering
A system and method for managing access to a satellite-based transponder by a plurality of aircraft each having a mobile radio frequency (RF) system. The system employs a ground-based, central control system for managing access to the satellite-based transponder so that the aggregate power spectral density (PSD) of the RF signals of all the mobile systems does not exceed, at any time, limits established by regulatory agencies to prevent interference between satellite systems. This is accomplished by a dual control loop arrangement for monitoring the signal-to-noise ratio (Eb / No) of the RF signal transmitted by the satellite-based transponder. A ground-based control loop is used whereby a ground-based central controller monitors the Eb / No and transmits commands to the aircraft (via the satellite transponder) to maintain the Eb / No of the transmitted signal within a predetermined range. A fast scan angle compensation is used by the mobile system of the aircraft to implement another control loop to further adjust the transmit power. This control loop maintains the Eb / No of the signal transmitted to the satellite-based transponder at the commanded level inbetween updates from the ground-based central controller.
Owner:THE BOEING CO
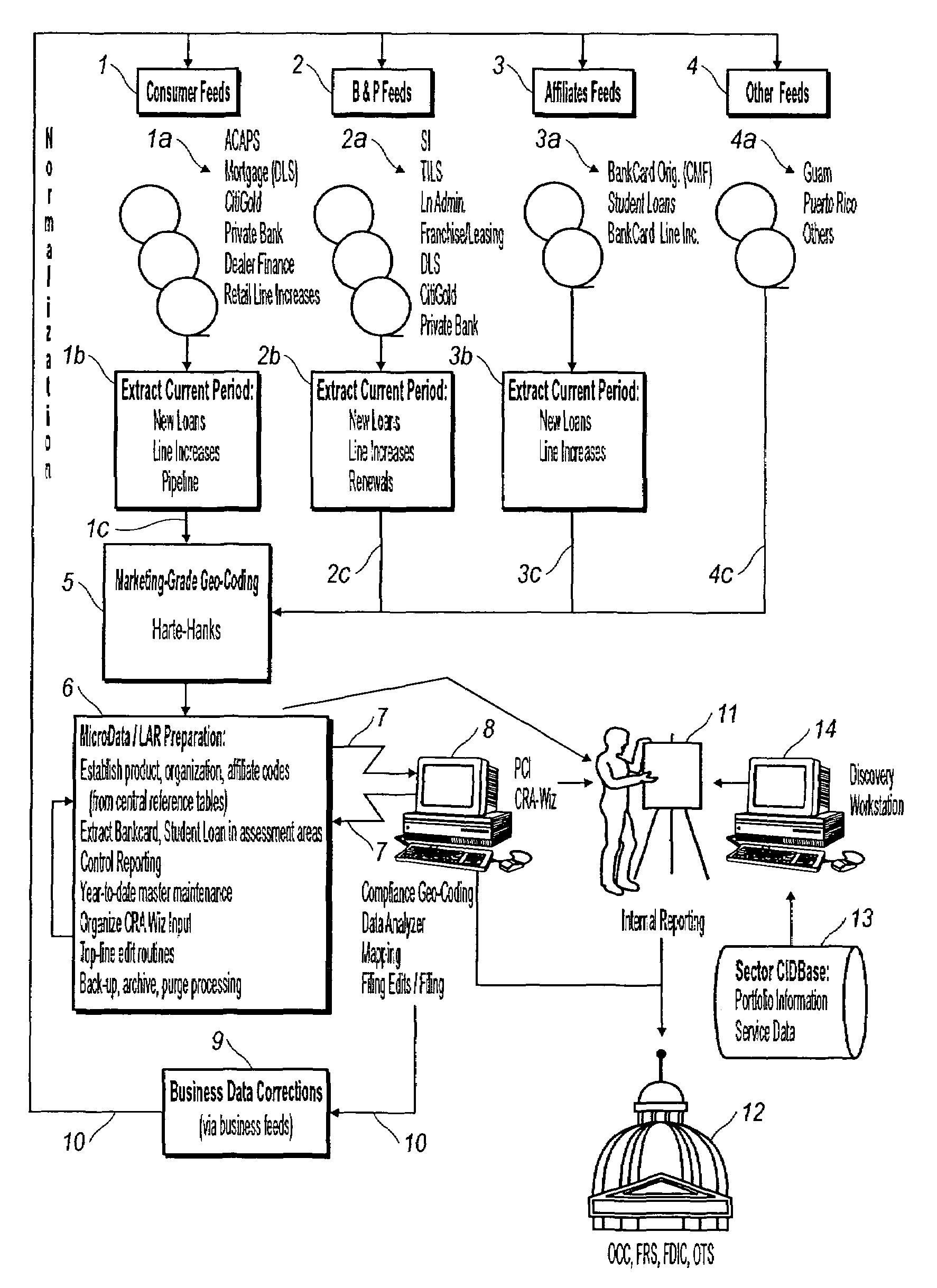
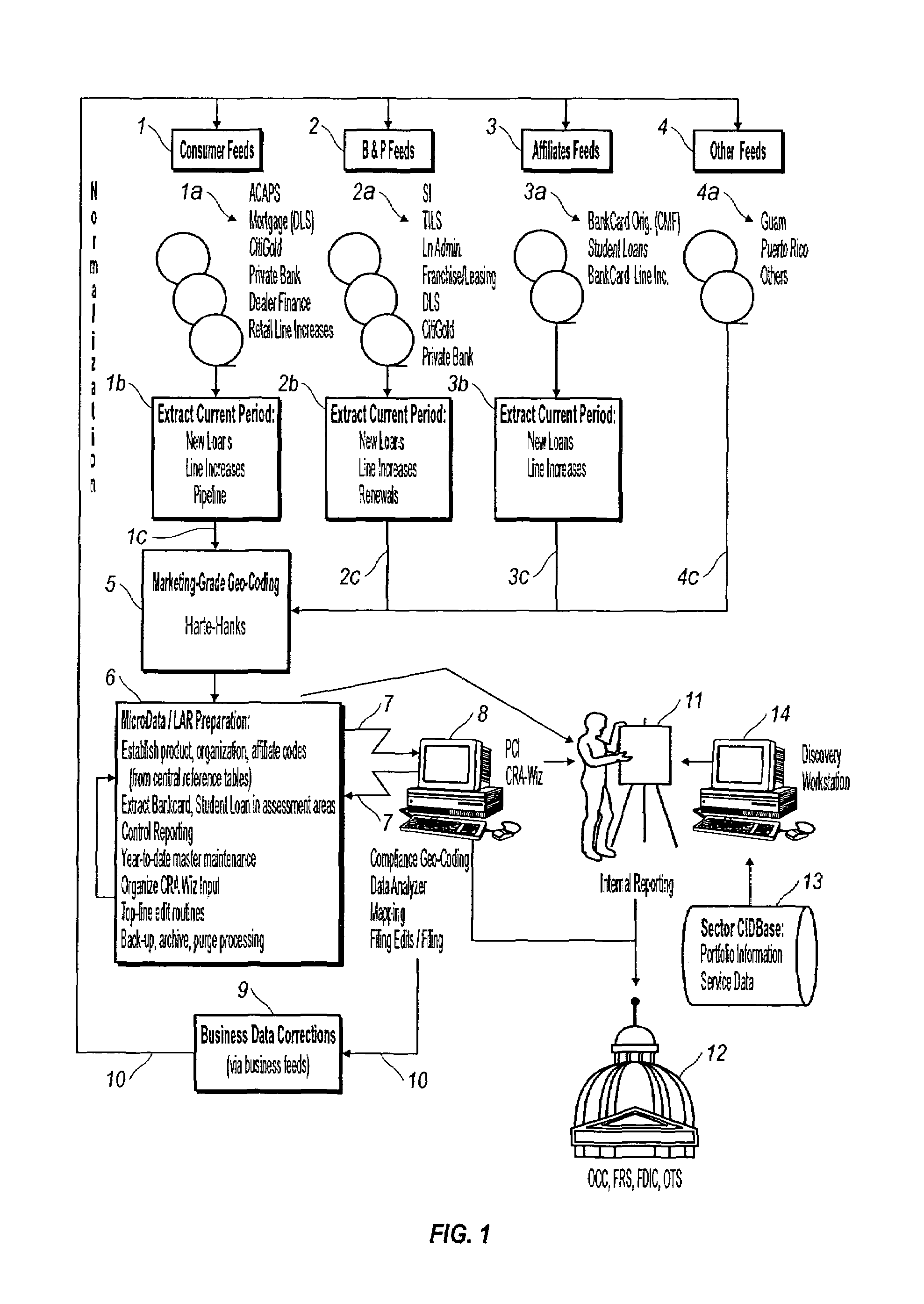
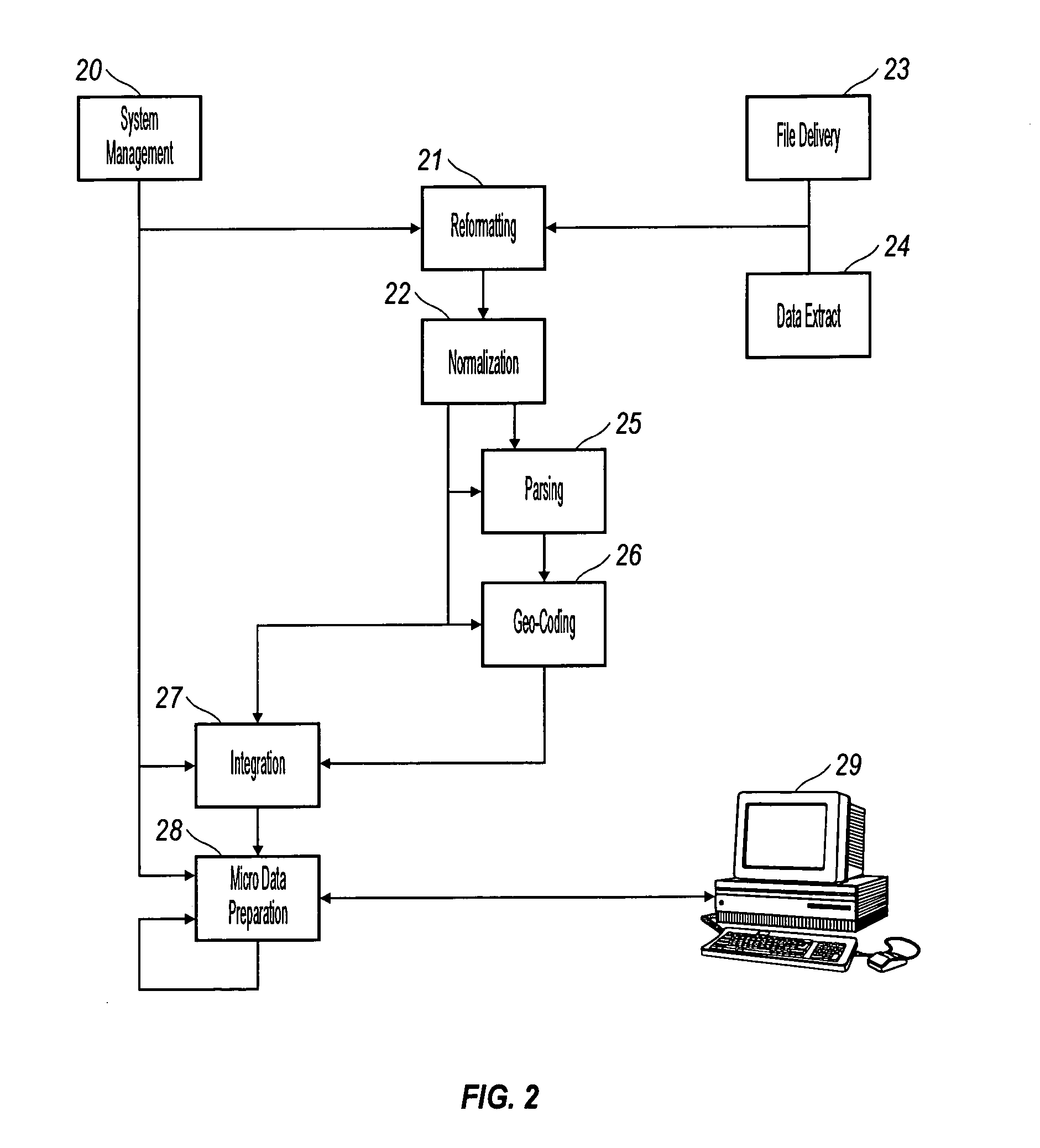
Method and system for performing CRA, HMDA, and fair lending analysis and reporting for a financial institution
InactiveUS6993505B1Solve the real problemAvoid restrictionsFinanceSpecial data processing applicationsNot for profitCredit card
The present invention discloses a method and system for collecting, standardizing, and analyzing lending data from all the offices of a financial institution, including information on small business, home equity, motor vehicle, credit card, mortgage, other secured and unsecured consumer products for commercial, community development, not-for-profit, and consortium customers. The invention enables data collection and analysis in a timely fashion such that interim reports may be prepared so that changes in lending practices can be implemented to assist with assuring compliance with the fair lending acts. A central repository is linked to all of the offices of the financial institution, and data mapping features are used to provide standardized reporting so that all data will be reported in a standardized form. The system processes, collects and standardizes information on new loans, renewals, credit line increases and application decisions for all of the business units within a financial institution. The present invention permits internal management reporting for review of performances against the CRA and HMDA plans. It also permits preparation of the reports for filing with the federal regulatory agencies, such as OCC, FRS and OTS. Furthermore, the present invention permits rapid response to federal regulatory agency audits of reported CRA and HMDA information.
Owner:CITIBANK
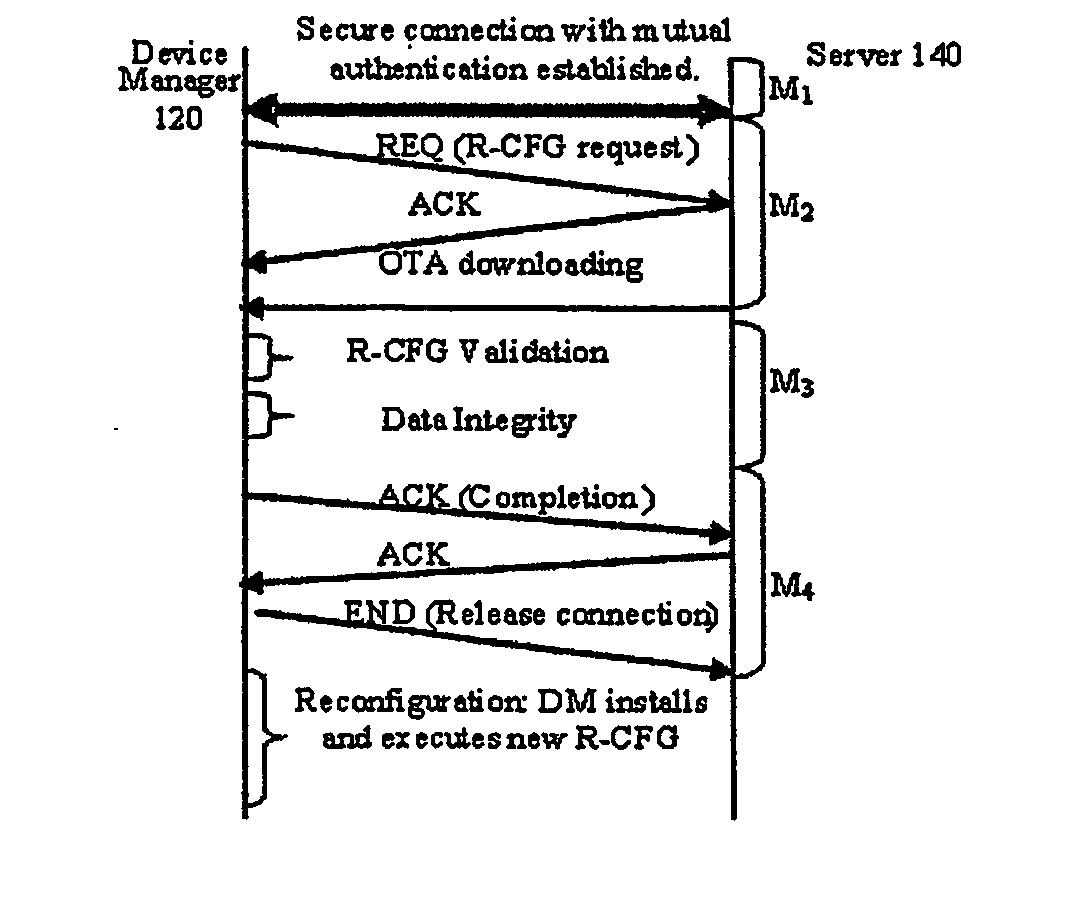
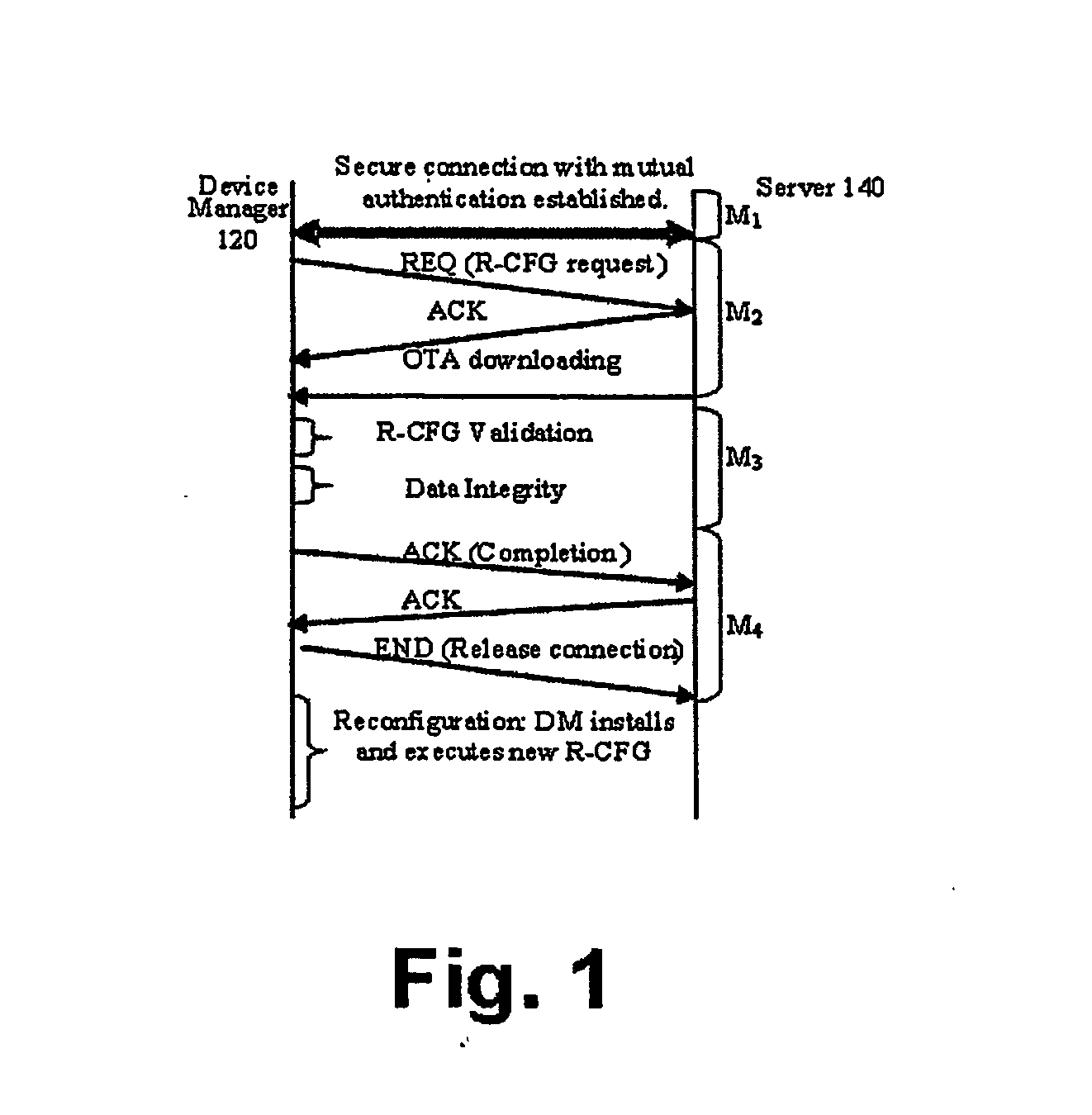
Software defined radio download
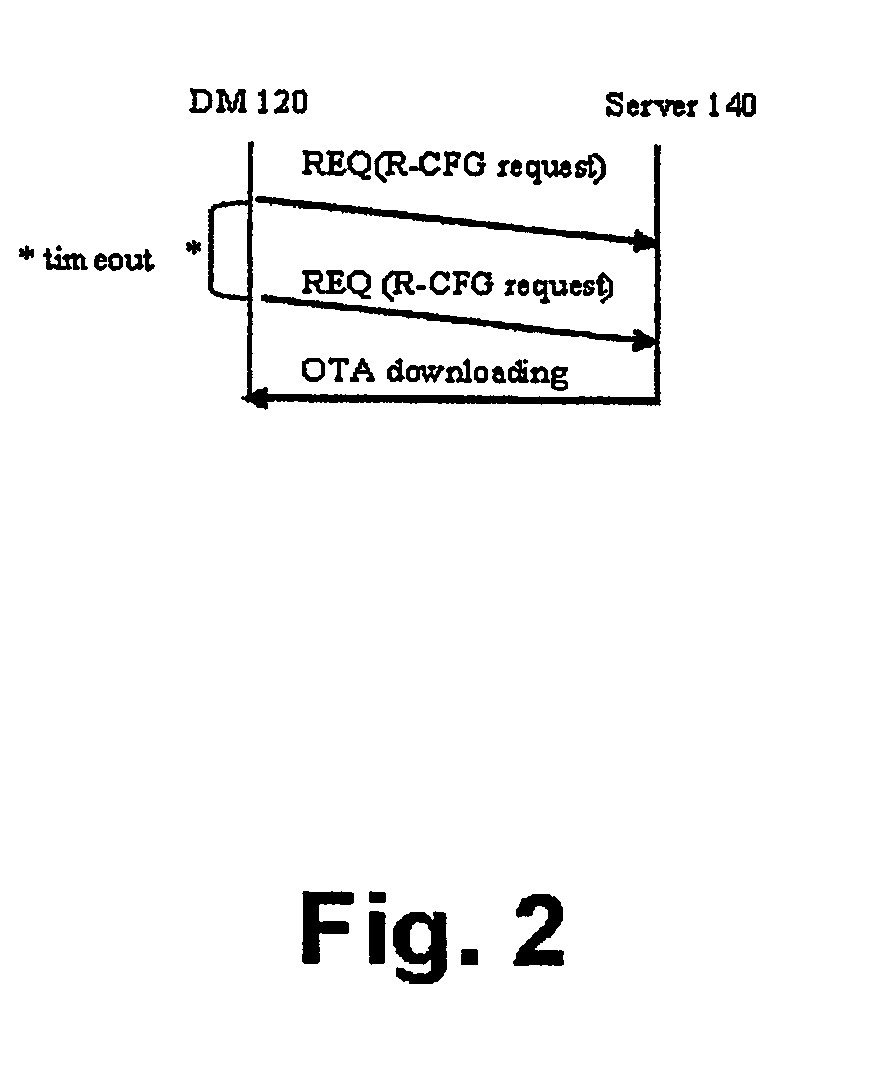
InactiveUS20060282497A1Avoid downloadingOvercome disadvantagesNetwork traffic/resource managementMultiple digital computer combinationsComputer hardwareSoftware define radio
A method for securely connecting a software defined radio (SDR) (110) to a server (140) through a network is presented. A request to download a radio configuration (R-CFG) file is sent from the SDR device to the server. A determination is made that the R-CFG file is configured to control a plurality of radio frequency parameters for the SDR device solely within levels permitted by a regulatory agency. The R-CFG is then downloaded to the SDR device.
Owner:SOVEREIGN PEAK VENTURES LLC
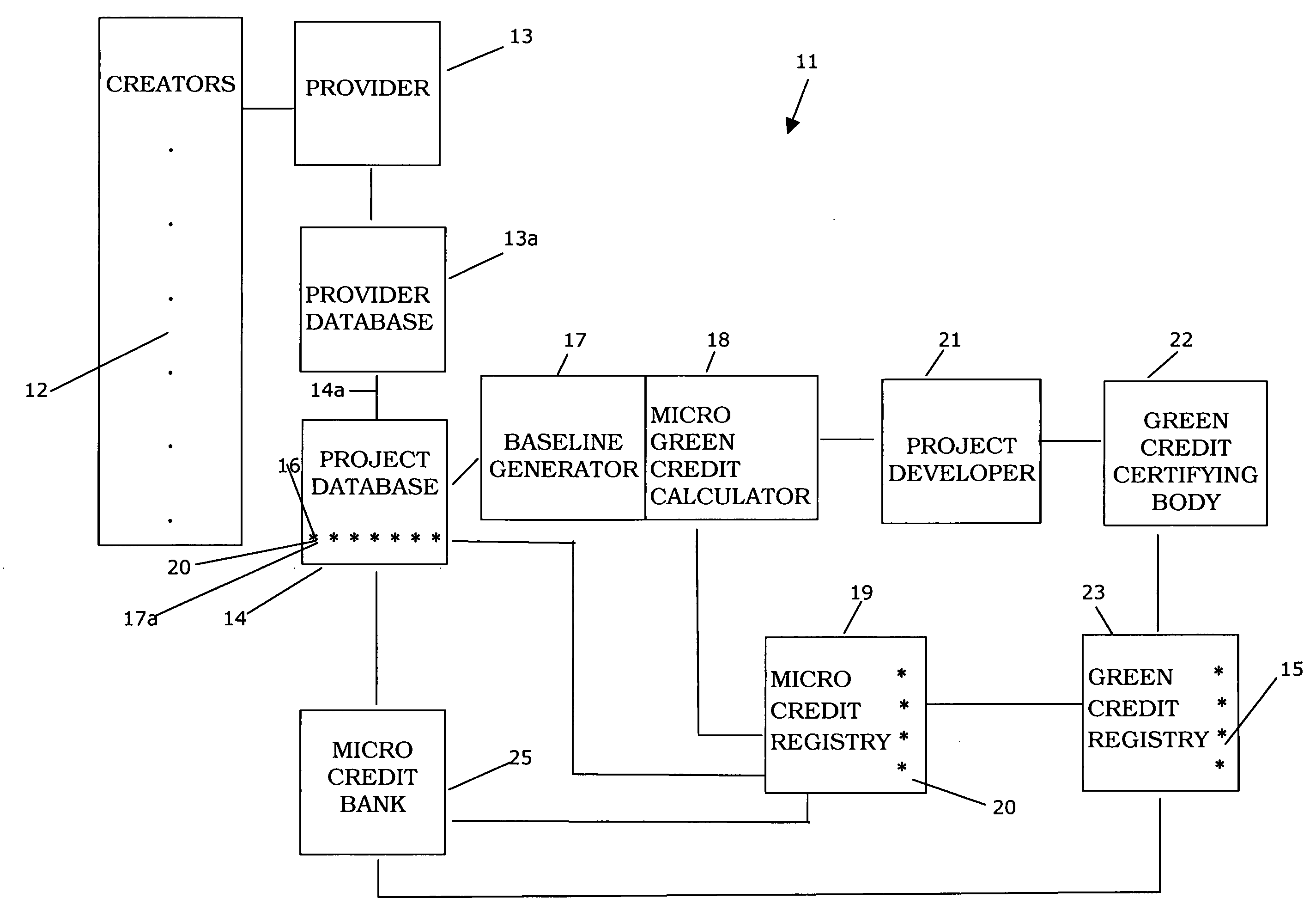
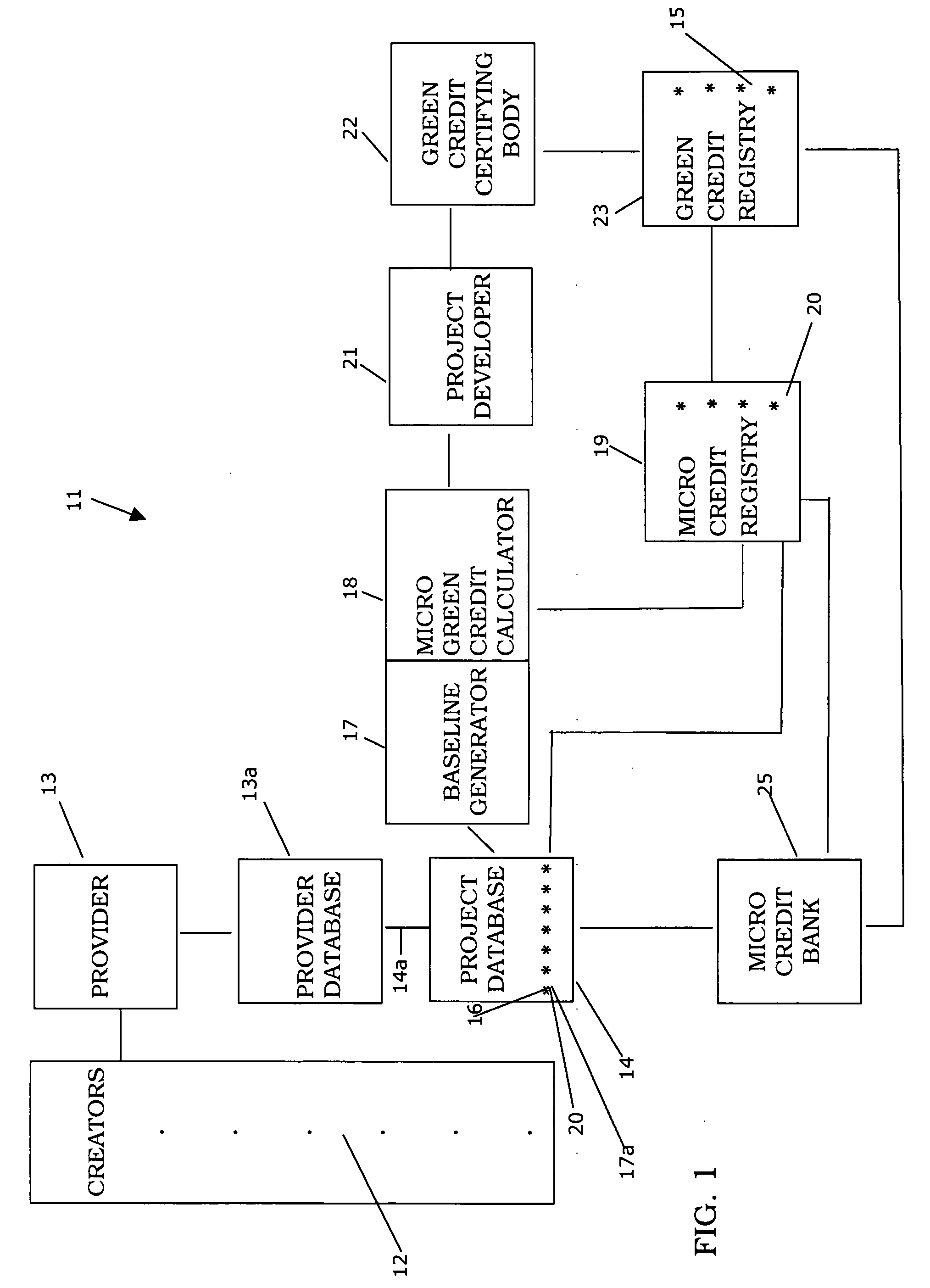
Methods and apparatus for creating and managing green micro credits
Owner:CARBON FLOW
System and method for effectuating the acquisition and distribution of tracking data on mobile assets, including shipment containers used in freight transportation
ActiveUS20060192673A1Minimize dataMinimize informationElectric signal transmission systemsFrequency-division multiplex detailsLogistics managementComputer science
A method and system for effectuating the optimum configuration of a duplex tracking device used to track the location and attributes of a mobile asset during a discrete event and the distribution of the data reported by the device so that the owner of the mobile asset and one or more of the owner's business partners can contemporaneously access the tracking data that they require. Each party first specifies a minimum configuration for all events with which they are associated, and then optionally specifies more extensive configurations for classes of discrete events. The owner may also constrain the data that partners can request by specifying access authorities for each class of business partners. The configuration parameters for a discrete event are systematically determined to minimize the data to be reported by the device while still meeting the requirements of all the parties, as constrained by the access authorities. Each party may then view and edit, as desired, the configuration until it is frozen prior to satellite transmission to the tracking device. The apparatus includes an internet-based program tool by which any participant can contemporaneously participate in the specification of the configuration parameters for the tracking device for a discrete event, and also access the data for events with which they are associated and generate exception reports. In a preferred embodiment, the mobile asset is a shipment container used to transport freight by ocean, rail, or road, the tracking device reports via satellite communications, the discrete event is a single shipment of goods from a origin location to a destination location, and the parties include the owner of the mobile asset (carrier), the owner of the contents (shipper), the receiver (consignee), and relevant logistics providers and regulatory agencies.
Owner:IGIT ENTERPRISES
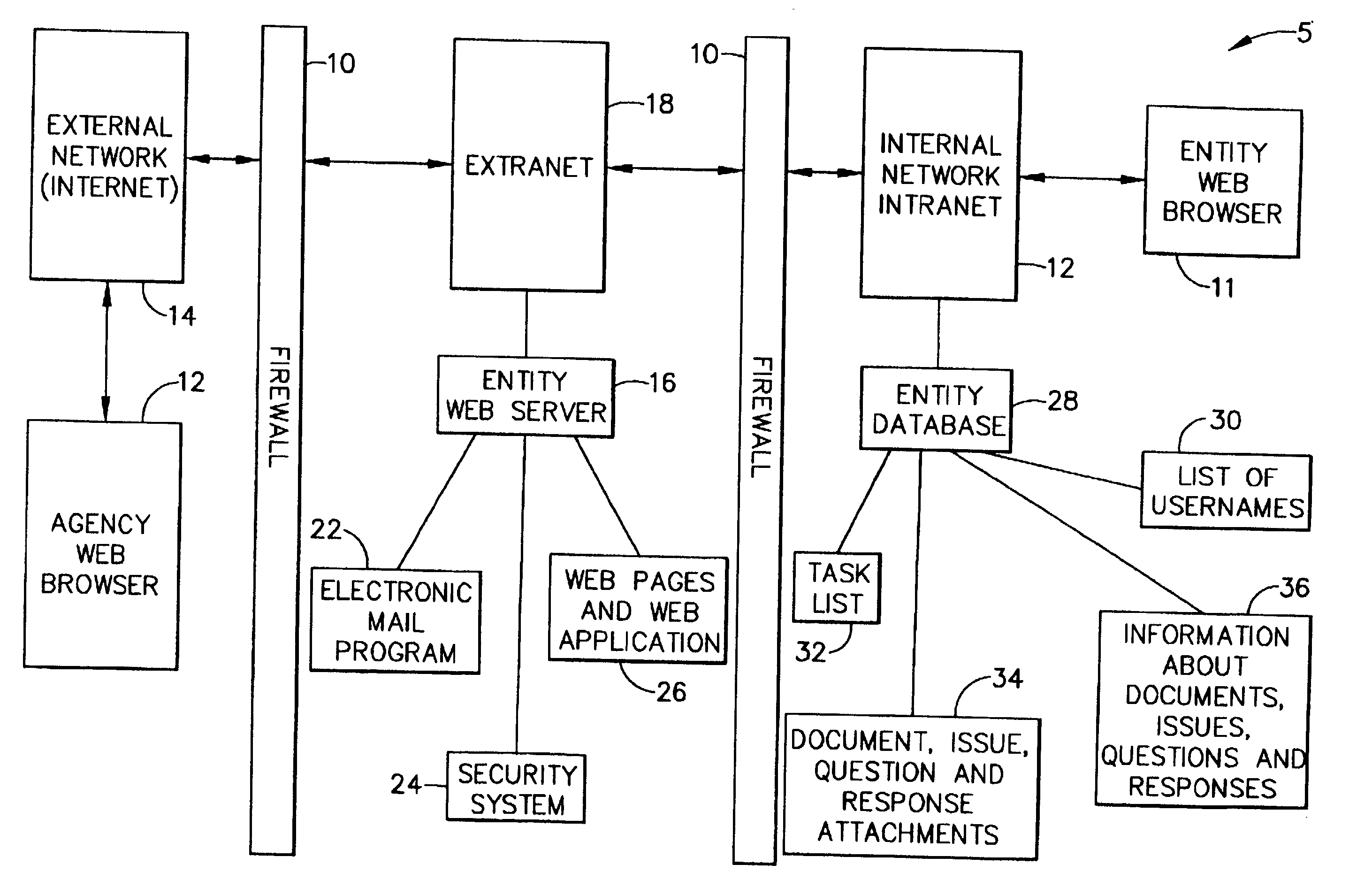
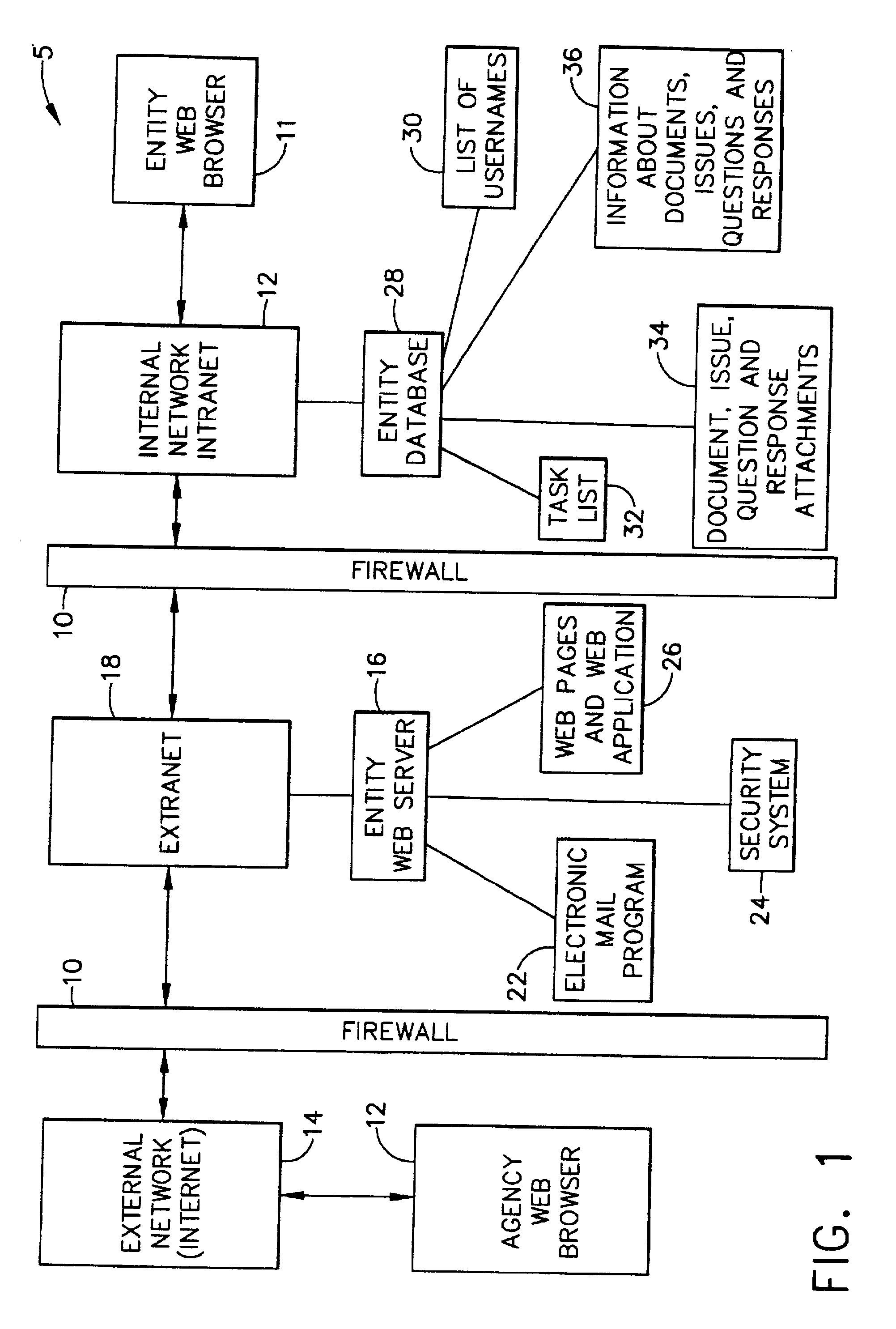
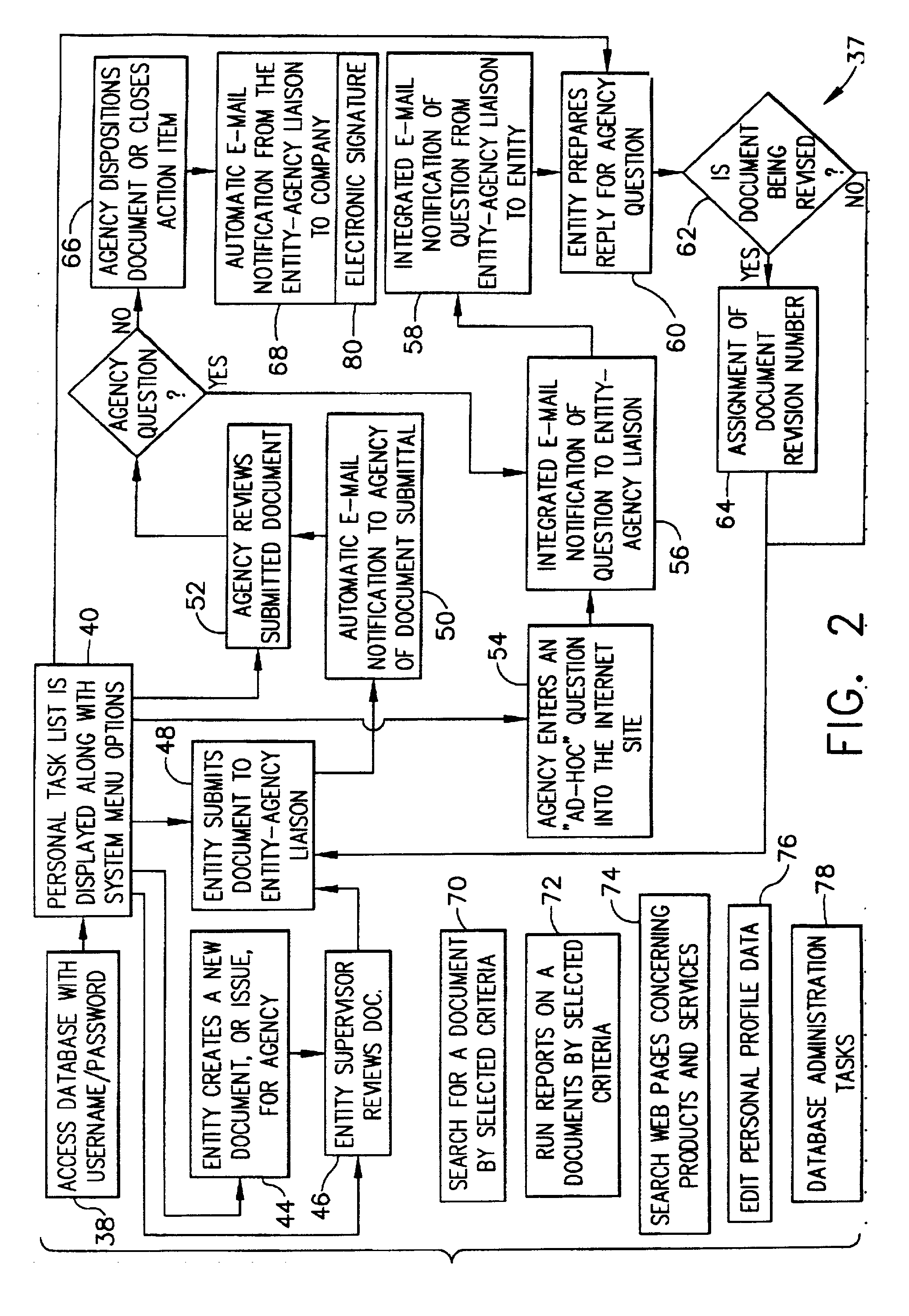
System and method for collaboration between regulatory agency and regulated entity
InactiveUS20020116620A1Simplify the encryption processComputer security arrangementsPayment architectureInternet privacySecure transmission
A computer-implemented system and method of secure transmission and collaboration of information between the employees of an entity and a regulator agency for the purpose of obtaining disposition by the regulatory agency. The system consists of a connected web sever and a database, both of which are protected behind at least one firewall. The web server and the multifunctional database are hosted and maintained by the entity for use by the regulatory agency and connects the employees of an agency and employees of the regulatory agency. The web server utilizes a security system to allow access to various functions of the system according to identity of the user.
Owner:GENERAL ELECTRIC CO
Method of data collection for fisheries management
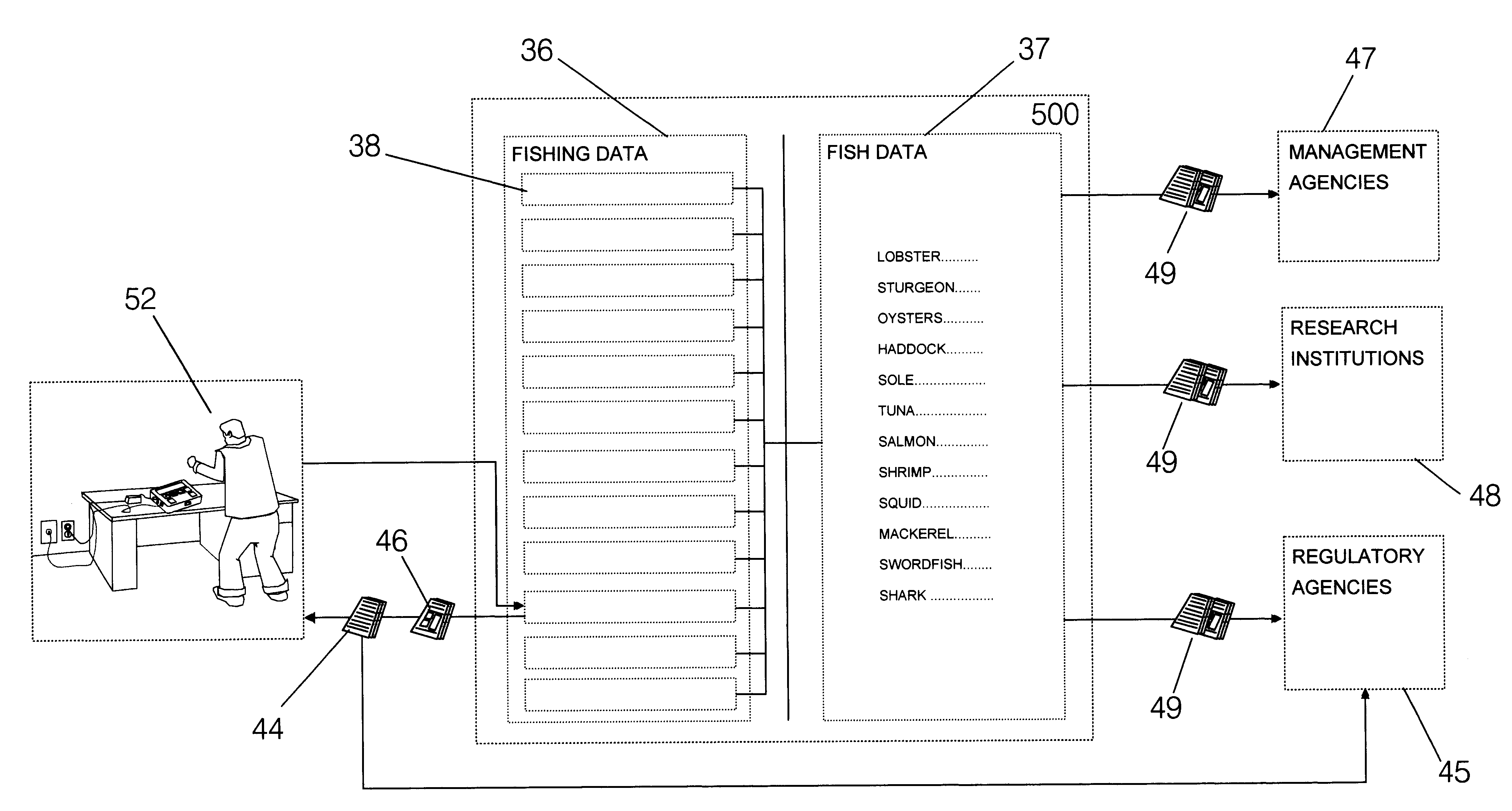
InactiveUS6567792B1Facilitate entryClimate change adaptationComputer security arrangementsFish stockingSynthetic data
A method of gathering, analyzing, and reporting data about commercial fish stocks and fisheries. Under this method, individual commercial fishermen use a device specific to the type of fishing being done to record the number of fish brought aboard, the number kept or released, the reason for release, the date, time, and location of the catch, and the fishery conditions, such as water temperature, depth, and salinity at the time that fish are brought aboard the fishing vessel. The individual fishermen transfer the data, typically via telephone link, to a central data repository, or to a receiving station when the data is transferred to the central data repository at a later time. The data is encrypted during transfer and placed in fisherman files, each fisherman having his own, restricted-access file. Data from all individual fishermen, as well as from other sources, are placed in a composite data pool to be used as source data for a general fishery database on fishstocks and fisheries. This data can be stripped of data that would identify a particular fisherman as the source, to preserve fishing secrets. Confidential reports can be generated from a fisherman file and delivered to the individual fisherman who is the source of that data. Reports for regulatory agencies can also be generated from the data in the fisherman file. The fishery database provides a unit for regulatory agencies, fisheries managers, and fish research institutions to analyze, monitor, and report on the development of fishstocks and fisheries.
Owner:THISTLE MARINE
System and method for automated discovery and ranking of regulatory compliance risks
InactiveUS20180053128A1Reduce in quantitySimplify the comparison processResourcesInternational standardRanking
Owner:COSTAS GUNTHER
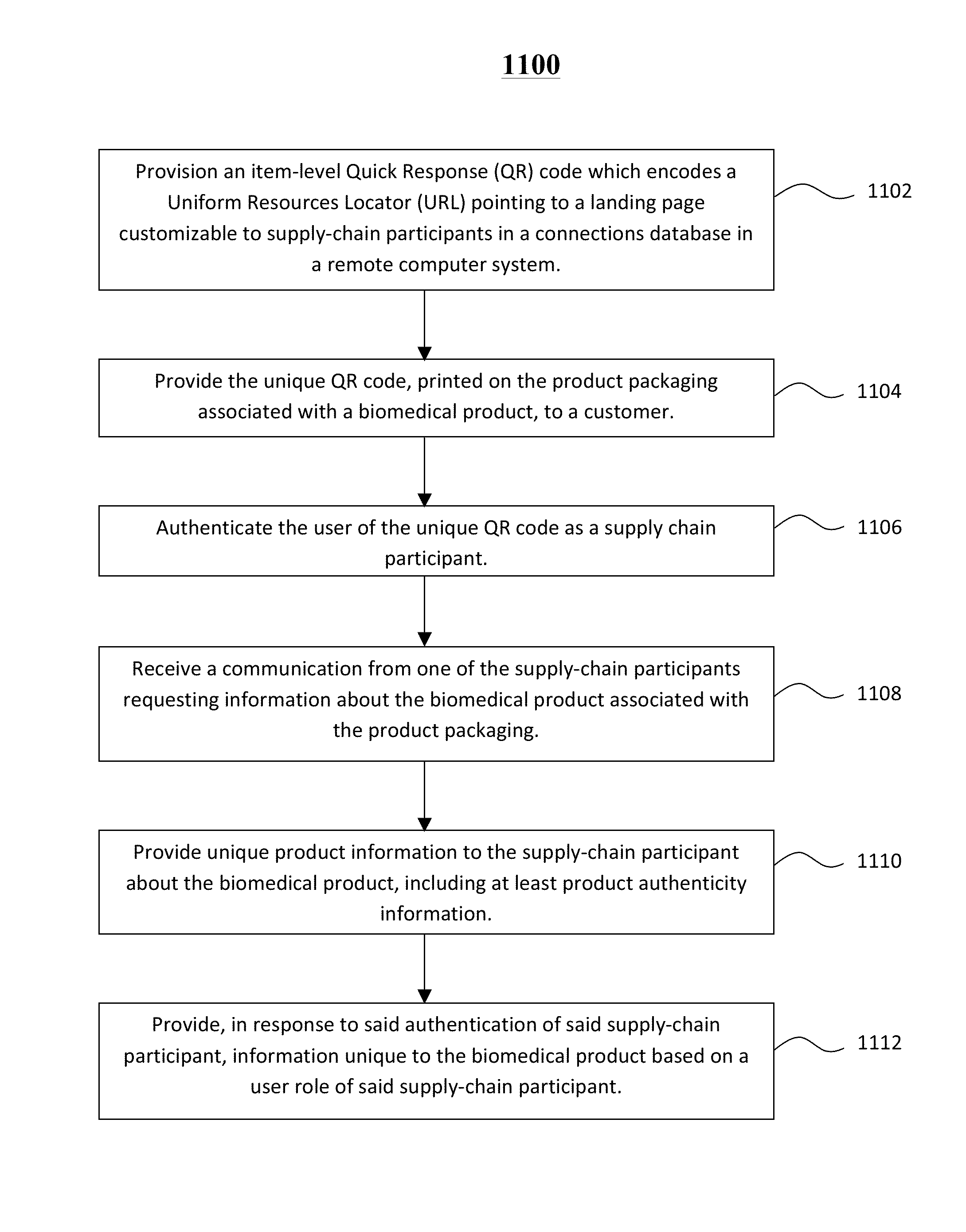
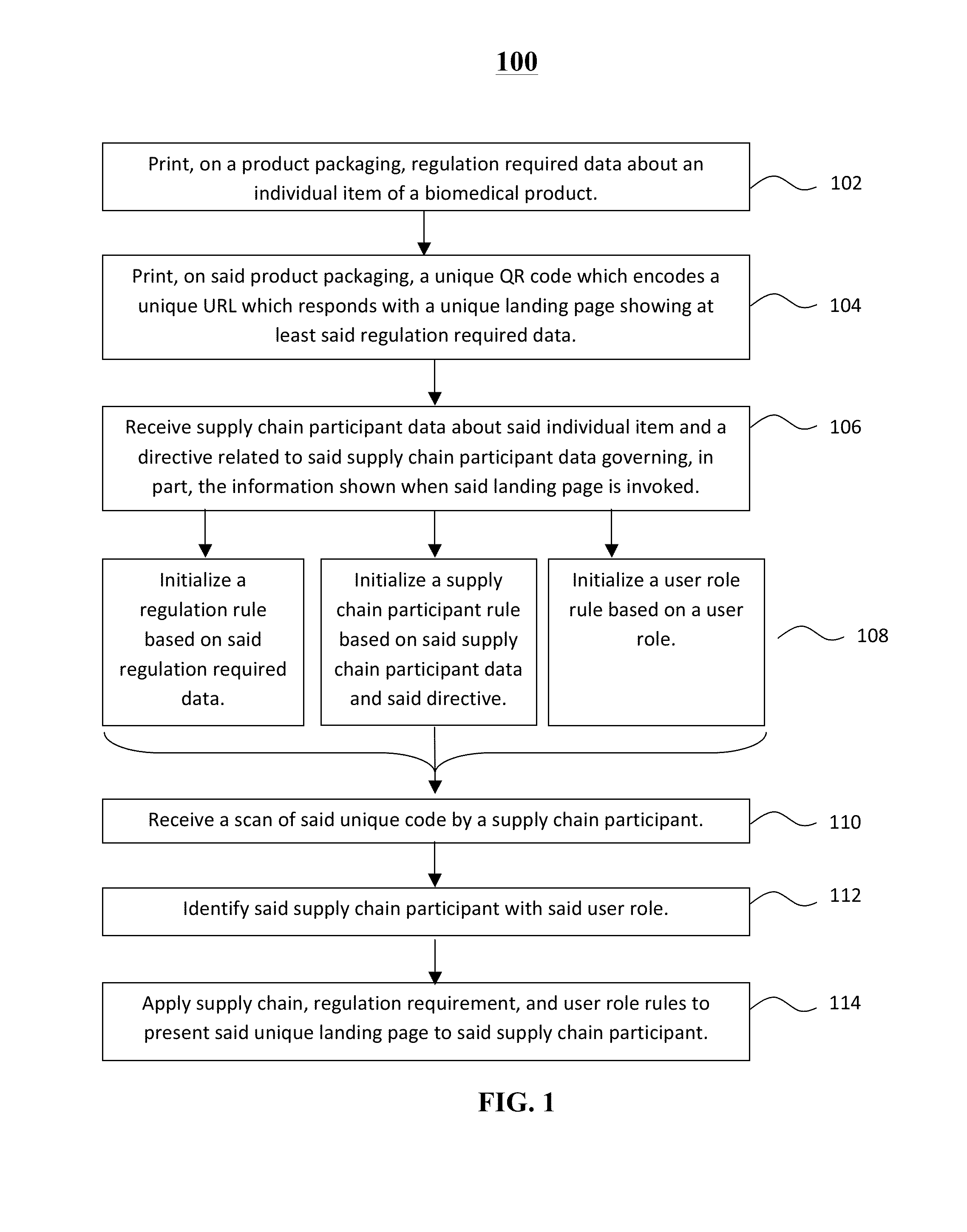
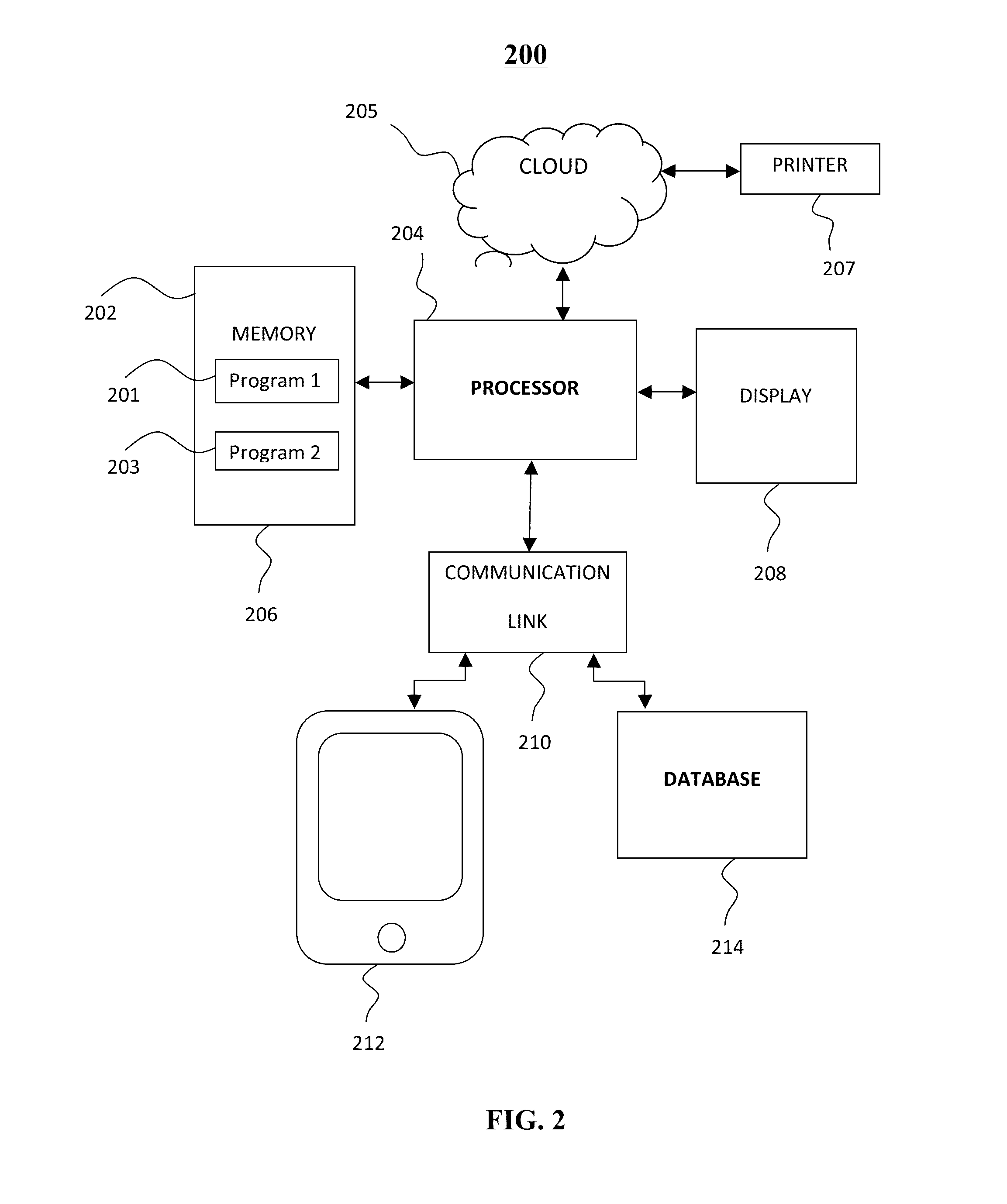
Systems and methods for tracking and tracing products through a supply chain utilizing unique URLs
Embodiments of the present invention may be used in various regulation-heavy industries, such as pharmaceutical, biomedical, construction, energy, heavy industry, and similar industries with large regulatory and / or safety considerations. The present invention describes a track-and-trace solution based on unique item-level QR codes printed on product packaging and encoding unique URLs to enable granular, item-level product management. In some embodiments of the invention, the information presented to users who access these unique URLs is tailored based on product usability information provided from authorized supply chain participants, the role of the user in the supply chain, and / or regulation required data comprising product safety data as required by regulations from a regulatory agency. Embodiments of the invention may be used for the purposes of item authentication, anti-counterfeiting measures, product recall management, and the efficient distribution of supplementary product information.
Owner:AGILEQR
Return link design for PSD limited mobile satellite communication systems
InactiveUS20060040614A1Quick fixAccurate power levelPower managementActive radio relay systemsTransmitted powerEngineering
A system and method for managing access to a satellite-based transponder by a plurality of aircraft each having a mobile radio frequency (RF) system. The system employs a ground-based, central control system for managing access to the satellite-based transponder so that the aggregate power spectral density (PSD) of the RF signals of all the mobile systems does not exceed, at any time, limits established by regulatory agencies to prevent interference between satellite systems. This is accomplished by a dual control loop arrangement for monitoring the signal-to-noise ratio (Eb / No) of the RF signal transmitted by the satellite-based transponder. A ground-based control loop is used whereby a ground-based central controller monitors the Eb / No and transmits commands to the aircraft (via the satellite transponder) to maintain the Eb / No of the transmitted signal within a predetermined range. A fast scan angle compensation is used by the mobile system of the aircraft to implement another control loop to further adjust the transmit power. This control loop maintains the Eb / No of the signal transmitted to the satellite-based transponder at the commanded level inbetween updates from the ground-based central controller.
Owner:THE BOEING CO
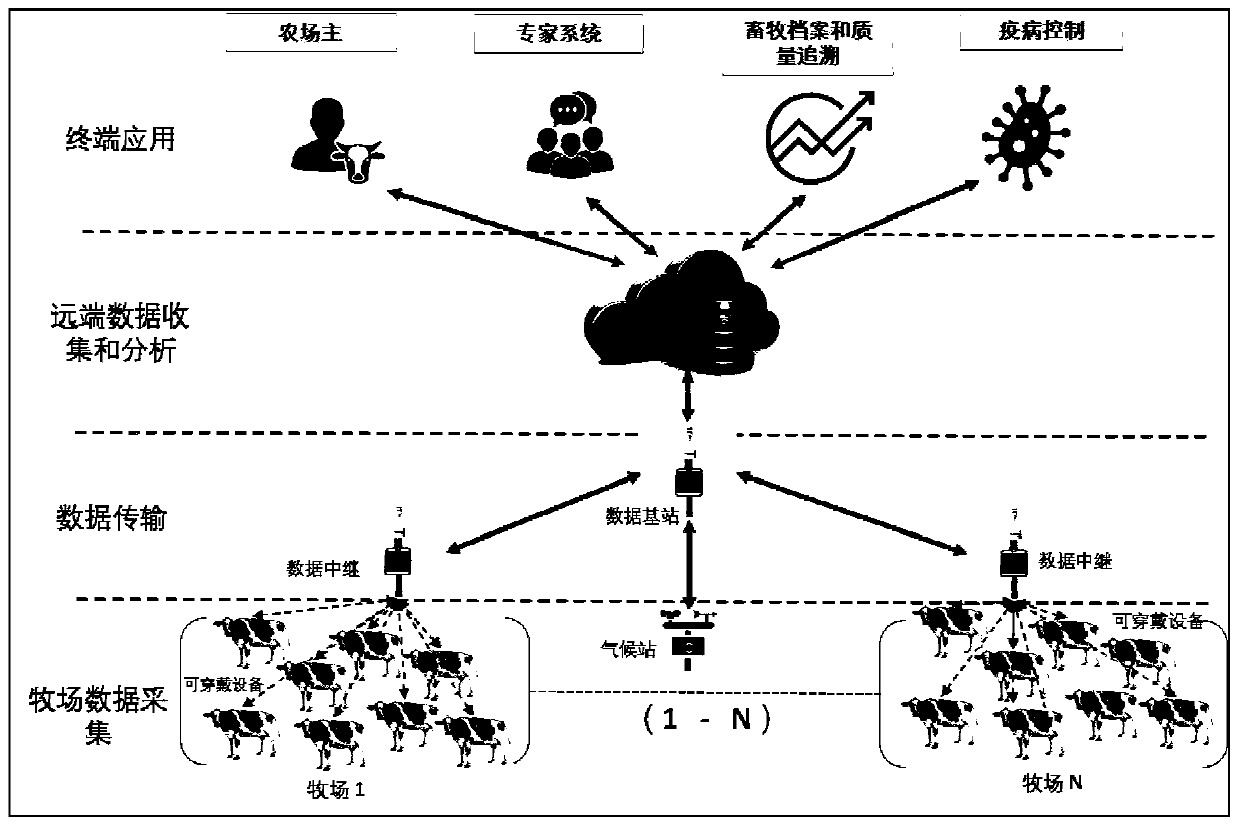
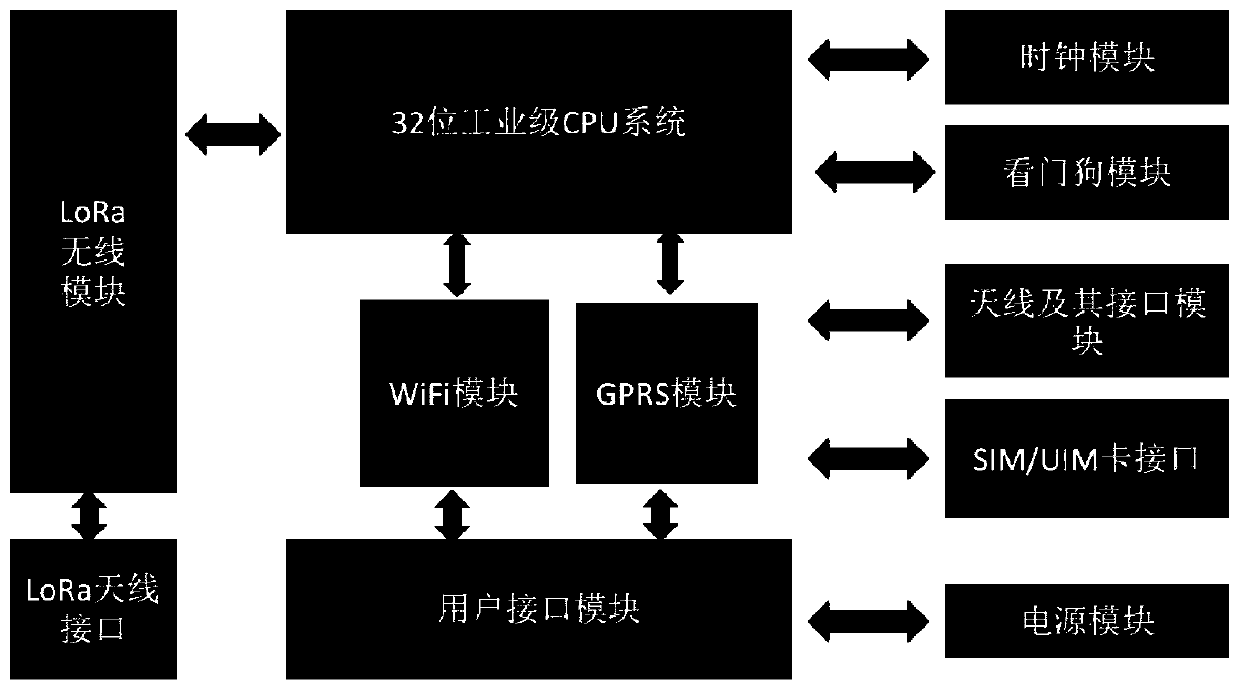
Intelligent livestock system based on Internet of Things
InactiveCN110221588AImprove corrosion resistanceRealize linkageData processing applicationsClimate change adaptationPastoralismSoftware system
The invention provides an intelligent livestock system based on the Internet of Things, relates to the field of application sensors, LoRa networks, and artificial intelligence livestock, realizes theautomatic collection of livestock and pasture statuses, stores and analyzes data, and gives an intelligent solution for integrating the Internet of Things technology into the livestock industry. The intelligent livestock system comprises an intelligent livestock software system, a special soil moisture information collection climatological station for a pasture, a livestock wearable device, a visual individual identification module and a livestock wireless network based on an LoRa broadband technology. The livestock personnel, scientific research institutions and regulatory agencies can masterthe conditions of the pasture and livestock in real time for daily management; the linkage between ranchers, experts and supervision departments is realized to provide solutions and rapid support foremergency events; complete livestock bookbuilding is achieved, and a foundation is built for further integrating pastures, slaughter houses and retailer information and realizing whole-course qualitytracing; and a large-range epidemic disease outbreak is predicted and effectively controlled by combining a think tank and a big data analysis technology.
Owner:HARBIN UNIV OF COMMERCE
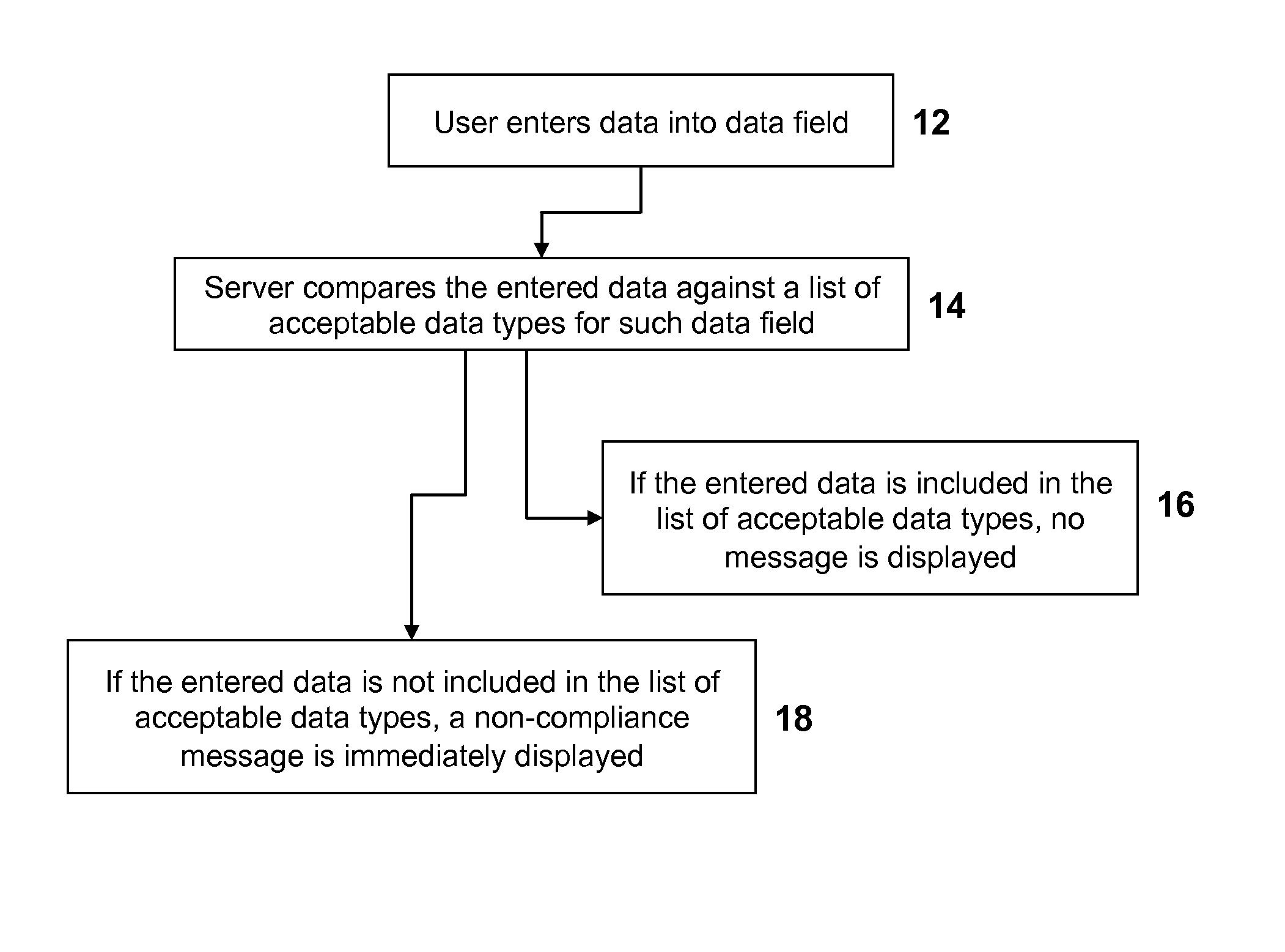
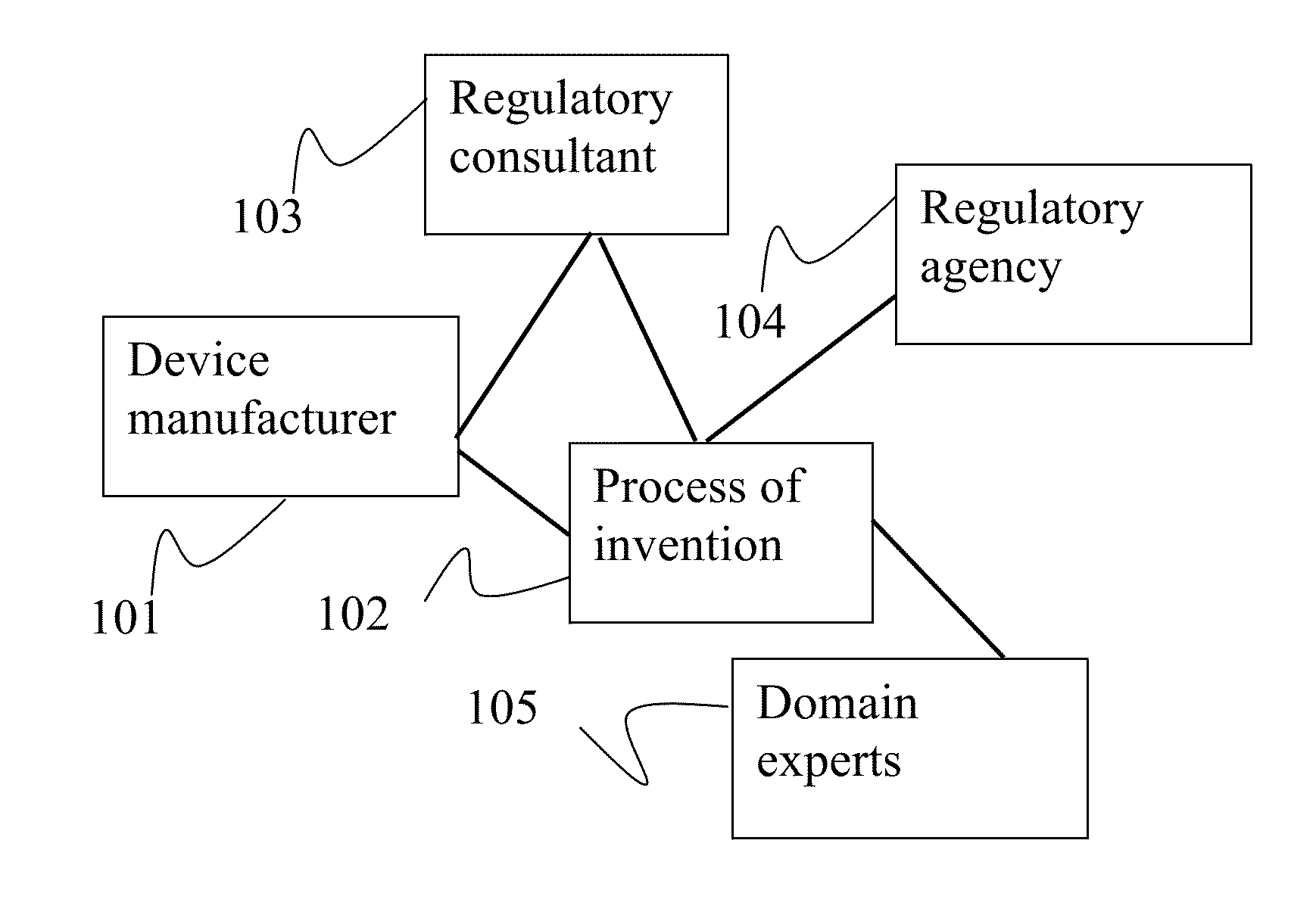
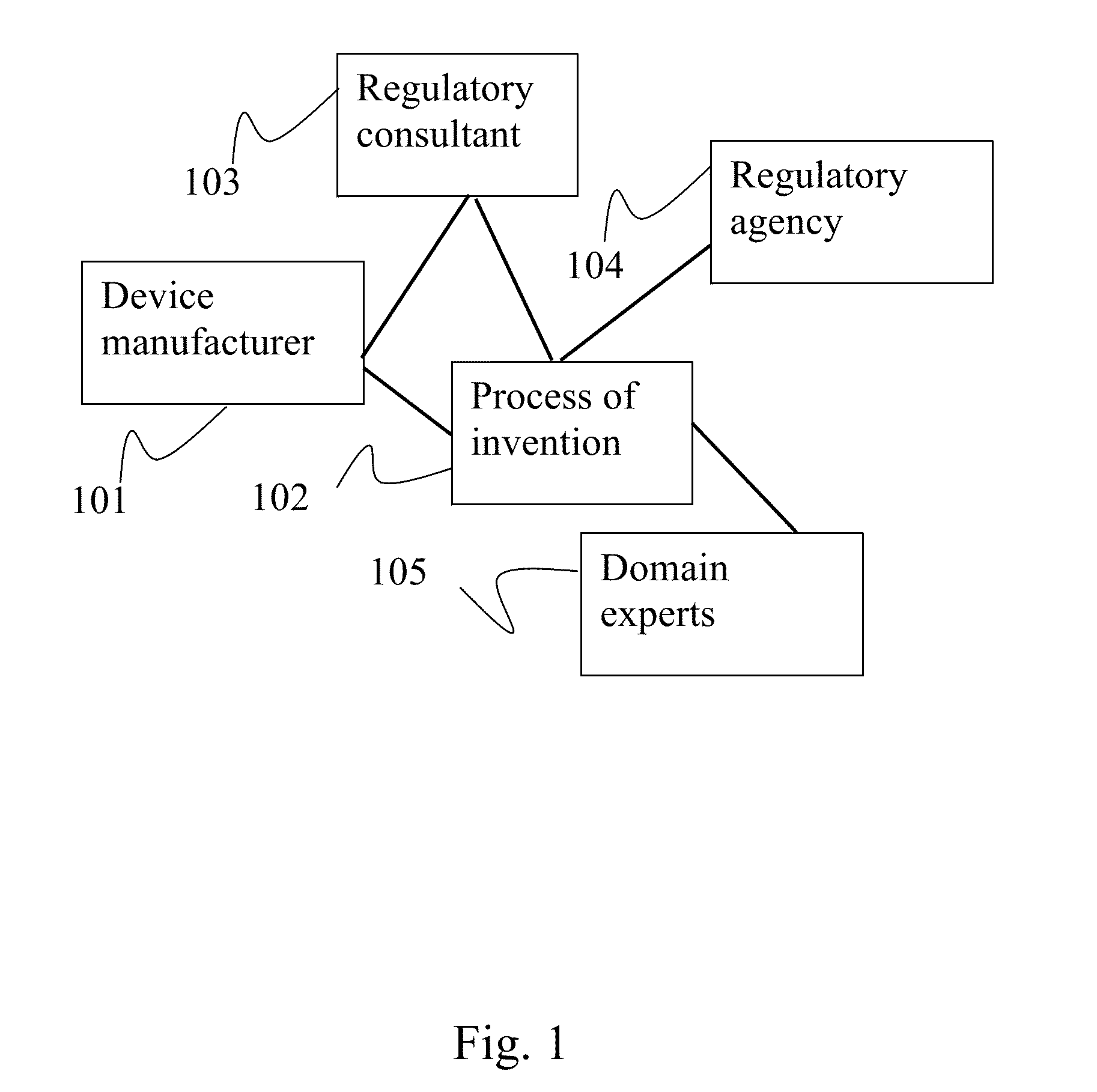
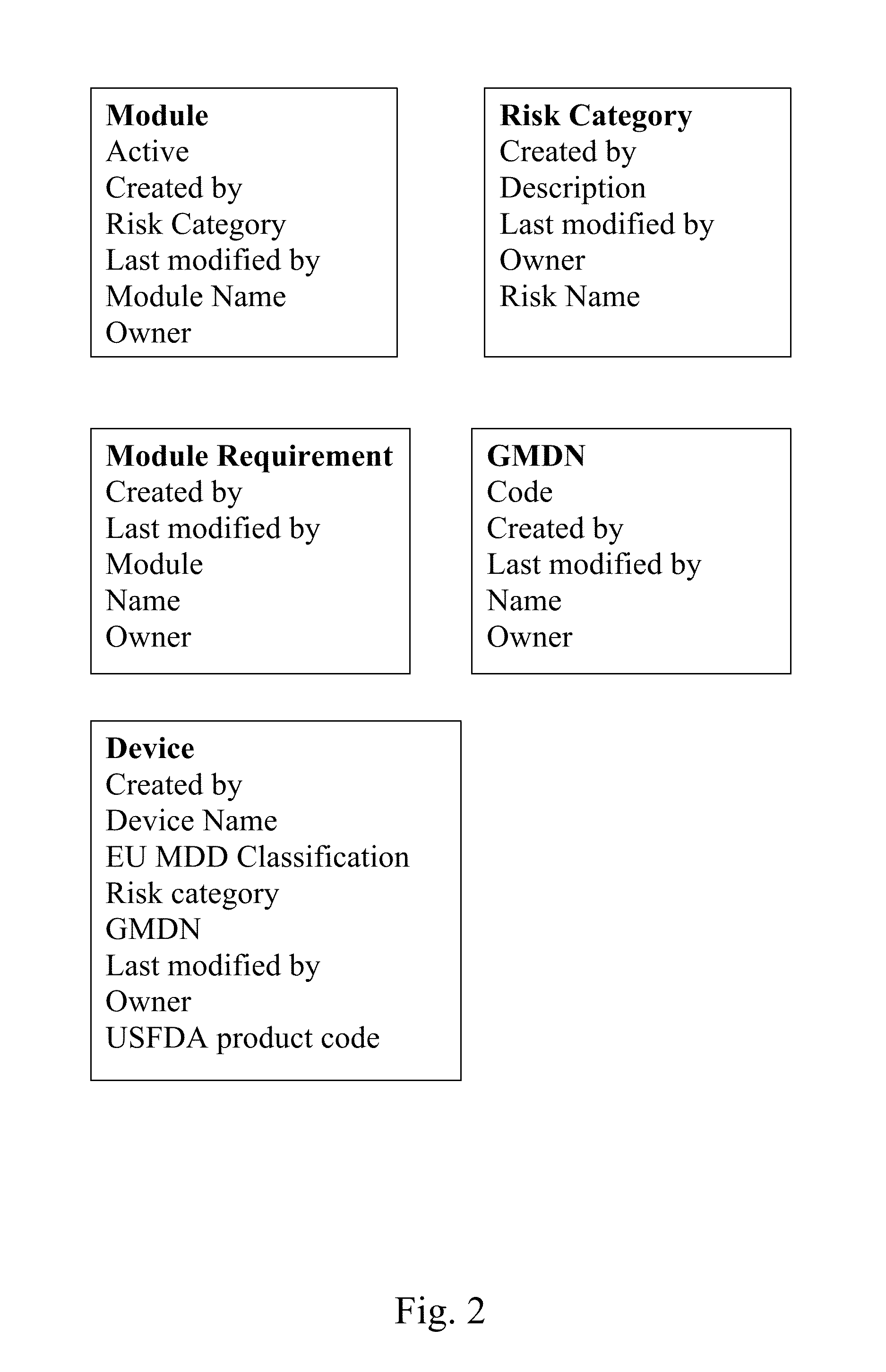
System and method for regulation compliance
The system and method herein disclosed is an online tool for reaching regulatory compliance. It uses a database of requirements by device, country, and agency necessary for licensing and marketing. Further databases include the compliance documents themselves, provided by given users concerning given devices. Still further databases include lists of domain experts, who may be called upon to review and edit these compliance documents. Expert systems running on a server associated with the system and method herein disclosed guide the user along the route to reaching compliance by means of aiding classification, prompting for missing documents, suggesting workarounds, submitting documents and payments automatically, and the like. Regulatory agencies may be given access to parts of the databases of the system and method herein disclosed to allow them to peruse and evaluate the compliance documents.
Owner:ARAZY BENNY
Virtual technology transfer office
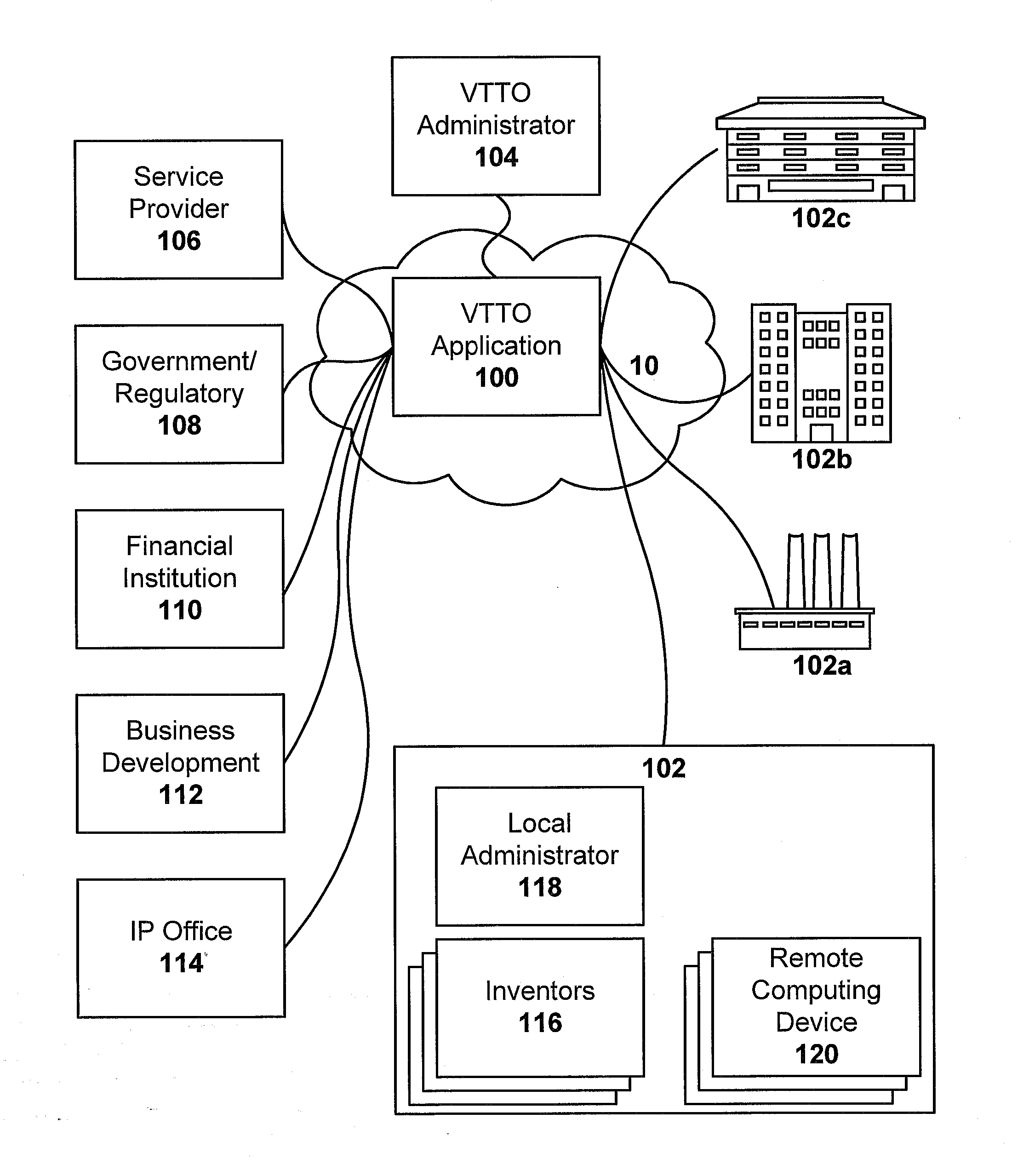
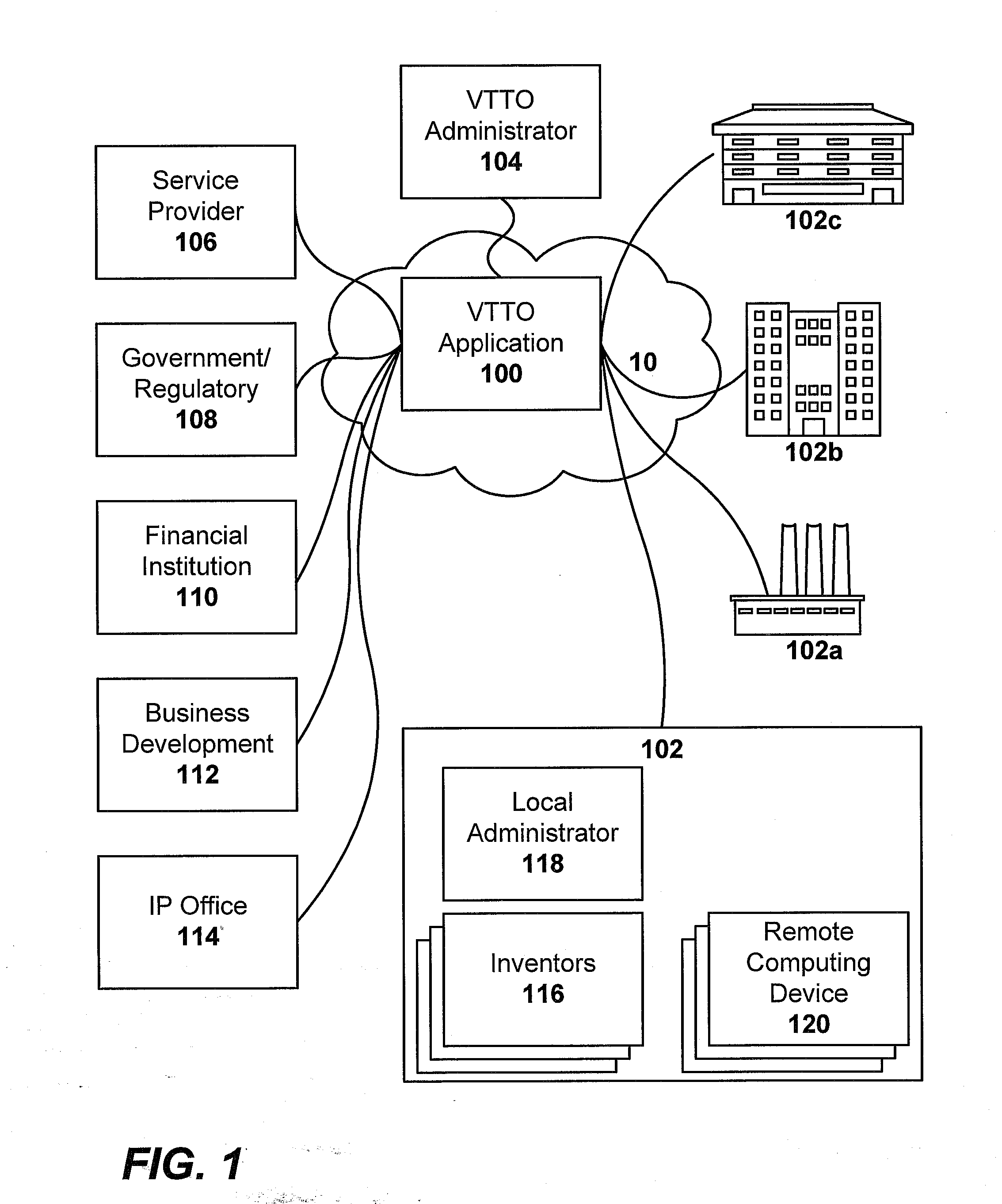
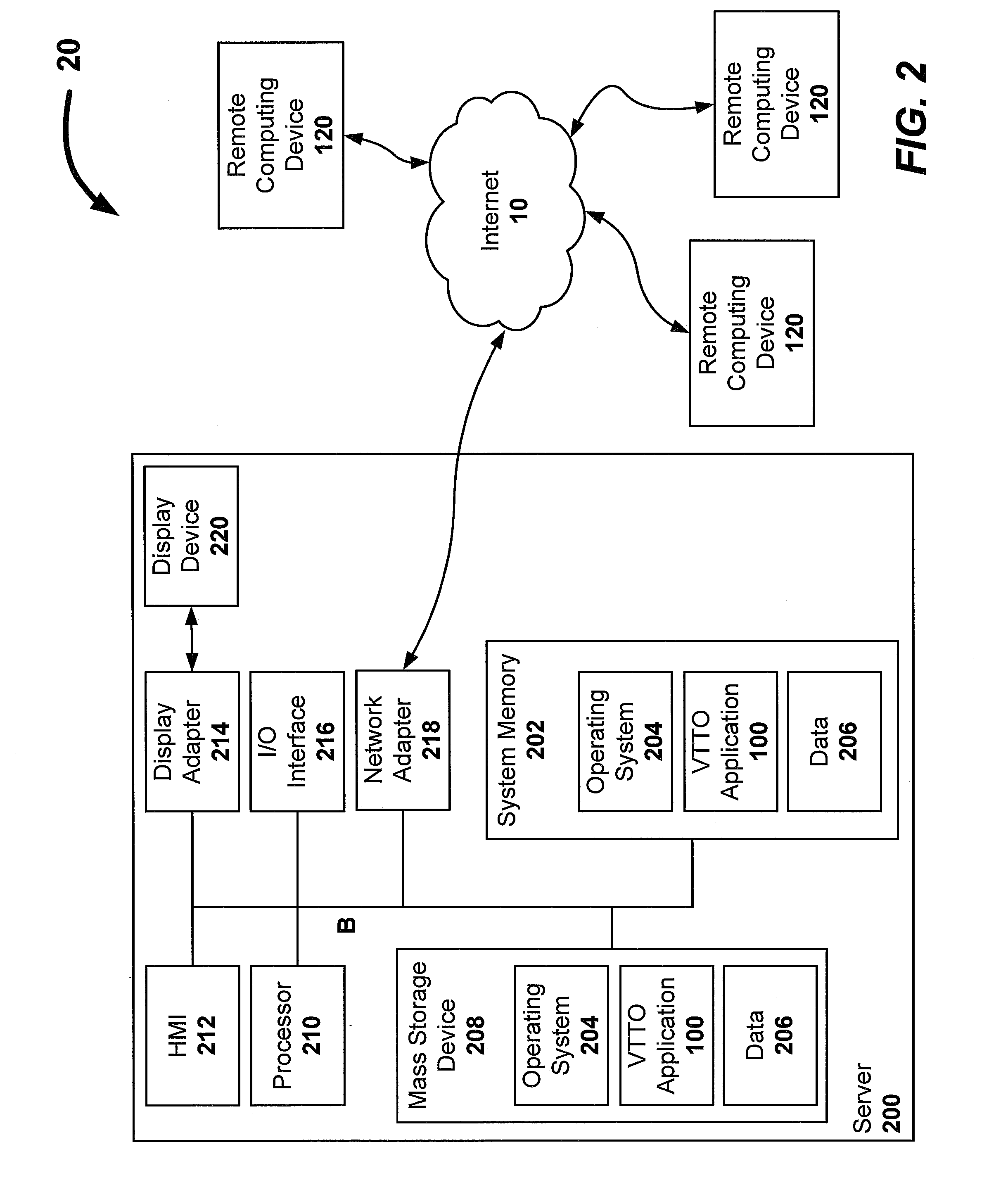
ActiveUS20070203737A1Easy to optimizeFacilitate actionOffice automationCommerceService provisionTechnology transfer
An online, and therefore virtual, technology transfer office accessible by multiple inventive entities is provided. The systems and methods of the invention provide a comprehensive interface to a remote application that collects information related to inventions, ranks the inventions, solicits approval for pursuing intellectual property protection, funding, financing, commercializing or otherwise exploiting the invention, solicits bids from a stable of service providers, manages the award of contracts to provide services, facilitates collaboration between users internal and external to the inventive entities and between different entities, implements security protocols, and reports government funded inventions to the appropriate regulatory agencies, and manages intellectual property portfolios. Each inventive entity may specify the level of control to be retained to utilize the virtual technology office application as a supplement for or as a substitute for full time technology transfer personnel.
Owner:FLORIDA A&M UNIVERSITY
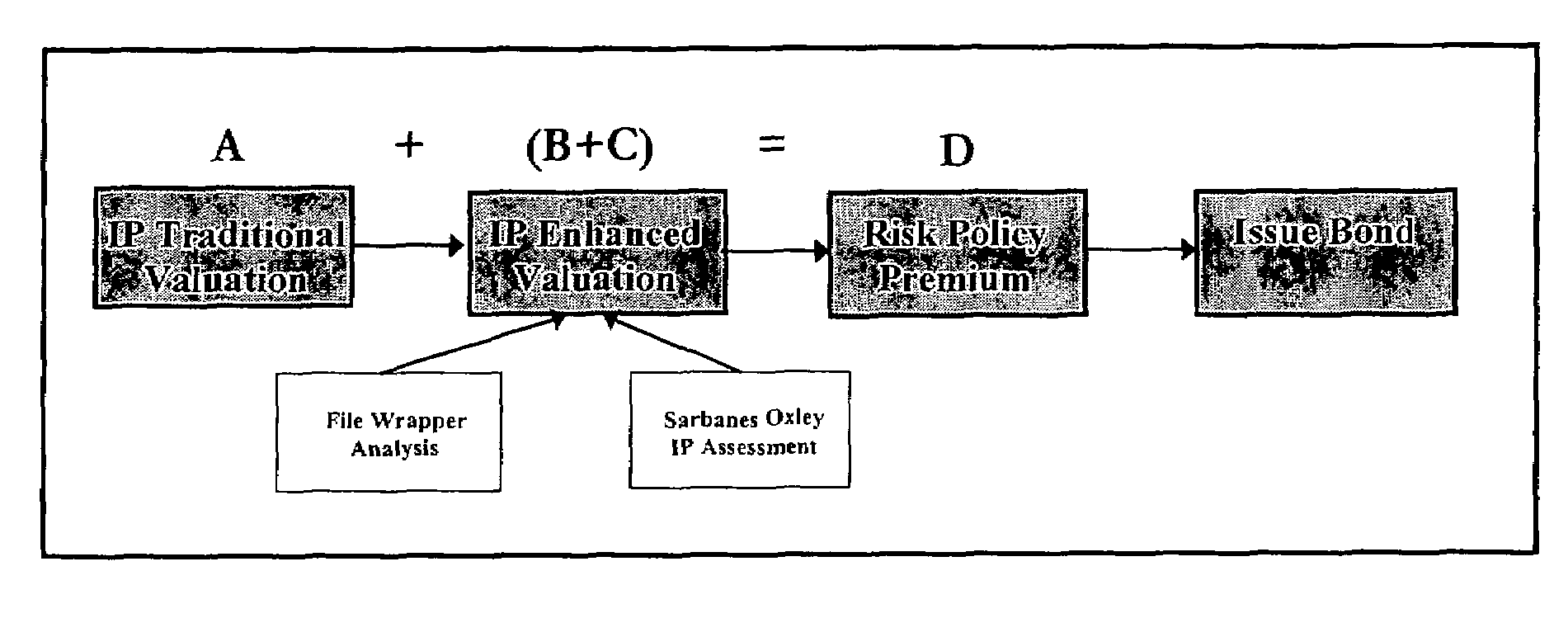
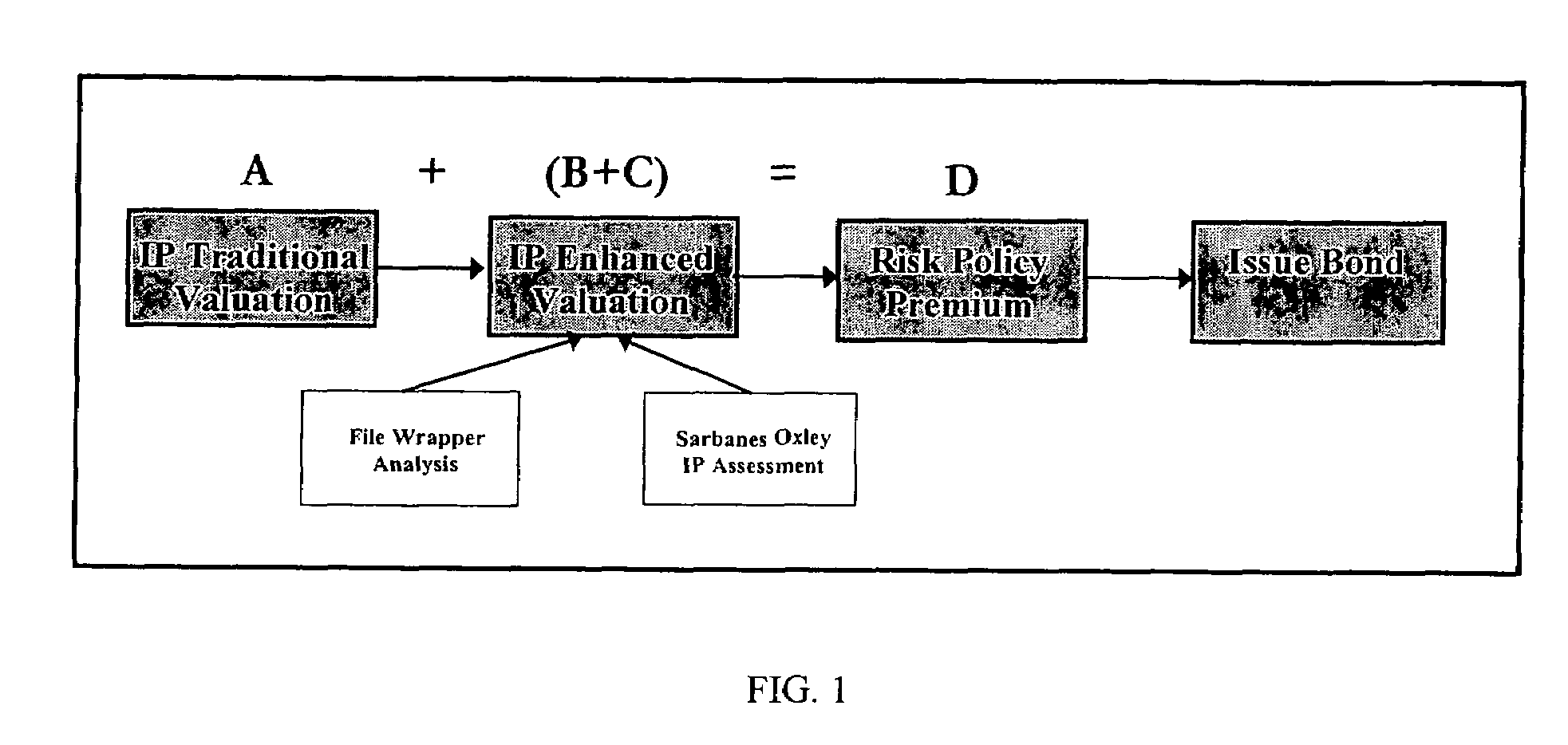
Method of appraising and insuring intellectual property
ActiveUS7536312B2Reduce financial riskExclude in valueMarket predictionsFinanceIntellectual propertyComputer science
Methods are disclosed for using computers, computer programs, algorithms and computer networks and communications hardware and protocols to appraise the value of assets as well as protecting asset owners from the risk that other entities will value those assets differently. The methods disclosed include:Supplementing traditional valuation methods with other considerations that may affect the value of intellectual property assets.Using insurance type financial instruments to maintain compliance with regulatory requirements such as those imposed by the Sarbanes Oxley Act, the SEC, or the IRS.Using insurance type financial instruments to protect intellectual property asset owners from the risk that tribunals, regulatory agencies, or other entities will appraise intellectual property assets at a different value.
Owner:OCEAN TOMO
Features
- R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
Why Patsnap Eureka
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Social media
Patsnap Eureka Blog
Learn More Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com