Cloud security authentication method and authentication device
An authentication device and security authentication technology, applied in the field of cloud security authentication, can solve the problems of non-existence of authentication process between the device and the cloud network, and the existence of security risks, so as to achieve low authentication costs, increase hardware costs, and improve security.
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
[0029] Below, the present invention will be further described in conjunction with the accompanying drawings and specific implementation methods. It should be noted that, under the premise of not conflicting, the various embodiments described below or the technical features can be combined arbitrarily to form new embodiments. .
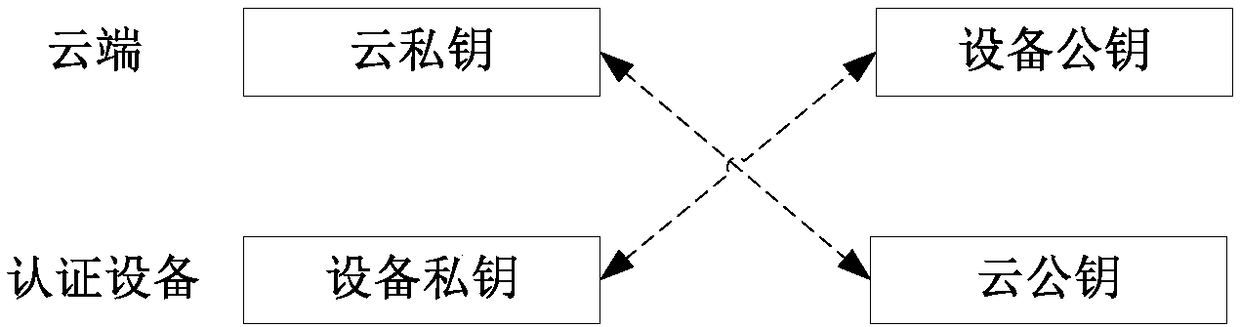
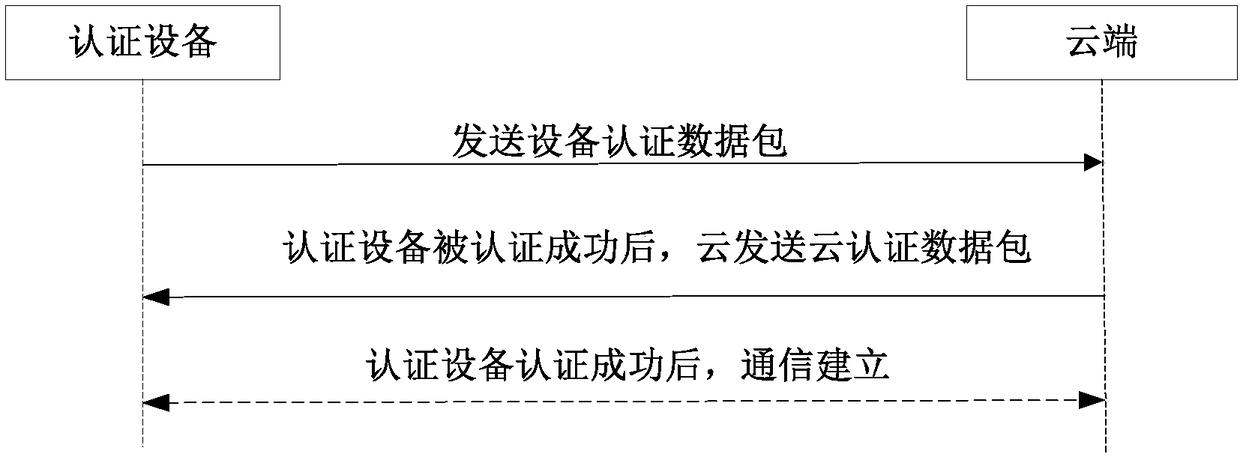
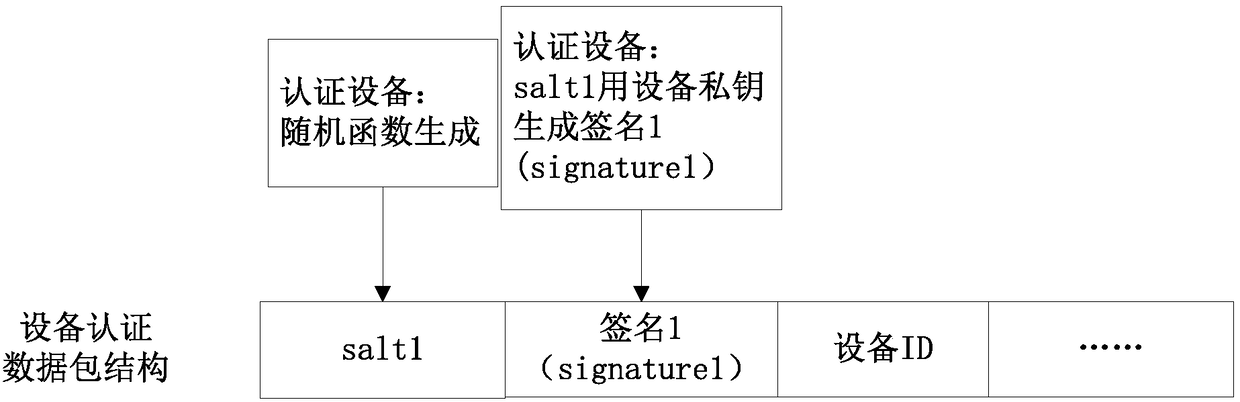
[0030] A cloud security authentication device such as figure 1 As shown, it includes an electronic device that stores a device private key and a cloud public key; wherein, the device private key is used to encrypt the device signature to obtain a device authentication data packet; the cloud public key is used to decrypt the cloud authentication data; it should be understood that, During device manufacturing, you can choose to burn the device private key and cloud public key into the device storage module, or you can use the data update method to rewrite when the device is updated. The cloud stores a cloud private key and a device public key, wherein t...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com