A security authentication system and corresponding method utilizing operator network
An operator network, security authentication technology, applied in the field of mobile communication, can solve the problems of easy theft, the stability and security of the authentication process cannot be guaranteed, and achieve the effect of improving security, saving authentication costs, and eliminating the need for roaming fees.
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
[0039] Embodiments of the present invention are described below with reference to the drawings. Elements and features described in one drawing or one embodiment of the present invention may be combined with elements and features shown in one or more other drawings or embodiments. It should be noted that representation and description of components or processes that are not relevant to the present invention and known to those of ordinary skill in the art are omitted from the drawings and descriptions for the purpose of clarity.
[0040] The present invention will be further described below in conjunction with the accompanying drawings.
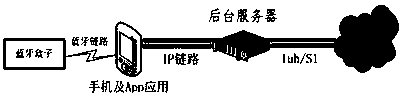
[0041] figure 1 It shows the implementation of security authentication system using operator network in this embodiment, including SIM card interface device ( figure 1 displayed as a Bluetooth box), mobile terminal ( figure 1 displayed as mobile phones and App applications), and the background server connected to the core network (CN) of the...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com