Methods and devices for key distribution, dynamic password generation and authentication
A dynamic password and key generation technology, applied in the field of information security, can solve the problems of high authentication cost, leakage of seed key, easy interception of seed key by malicious programs, etc.
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment 1
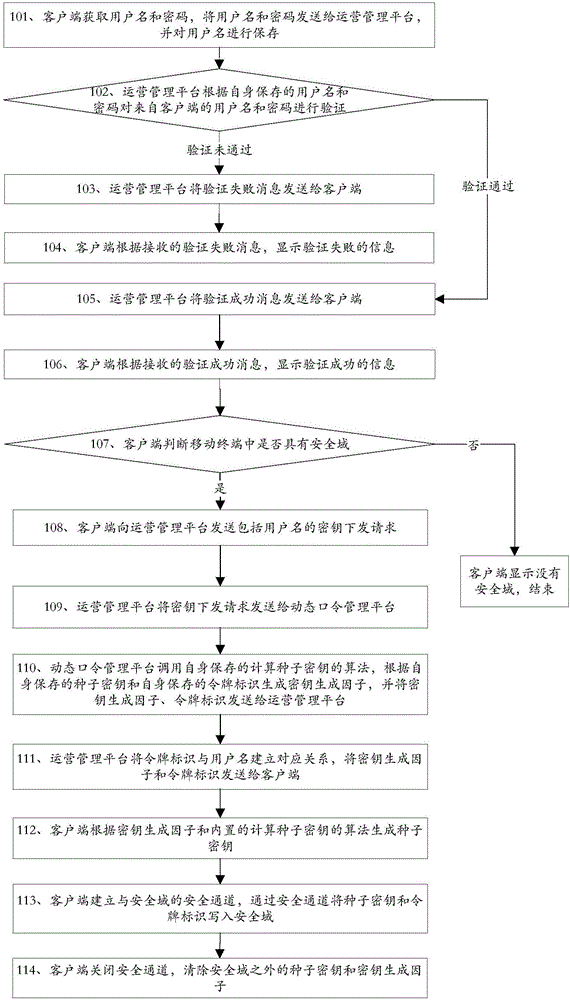
[0111] This embodiment provides a method for issuing keys, such as figure 1 shown, including:
[0112] Step 101: the client obtains the user name and password, sends the user name and password to the operation management platform, and saves the user name.
[0113] Specifically, the client obtains the user name and password input by the user, and sends the user name and password to the operation management platform.
[0114] For example, when the client user opens the client in the mobile terminal, the client displays the user name and password input window, when the user enters the user name and password in the corresponding input window, and clicks the login or confirm button, the client obtains the user name and password , and send the user name and password to the operation management platform.
[0115] Before step 101 is executed, it also includes installing a client on the mobile terminal. Specifically, the mobile terminal installs the client after downloading the clie...
Embodiment 2
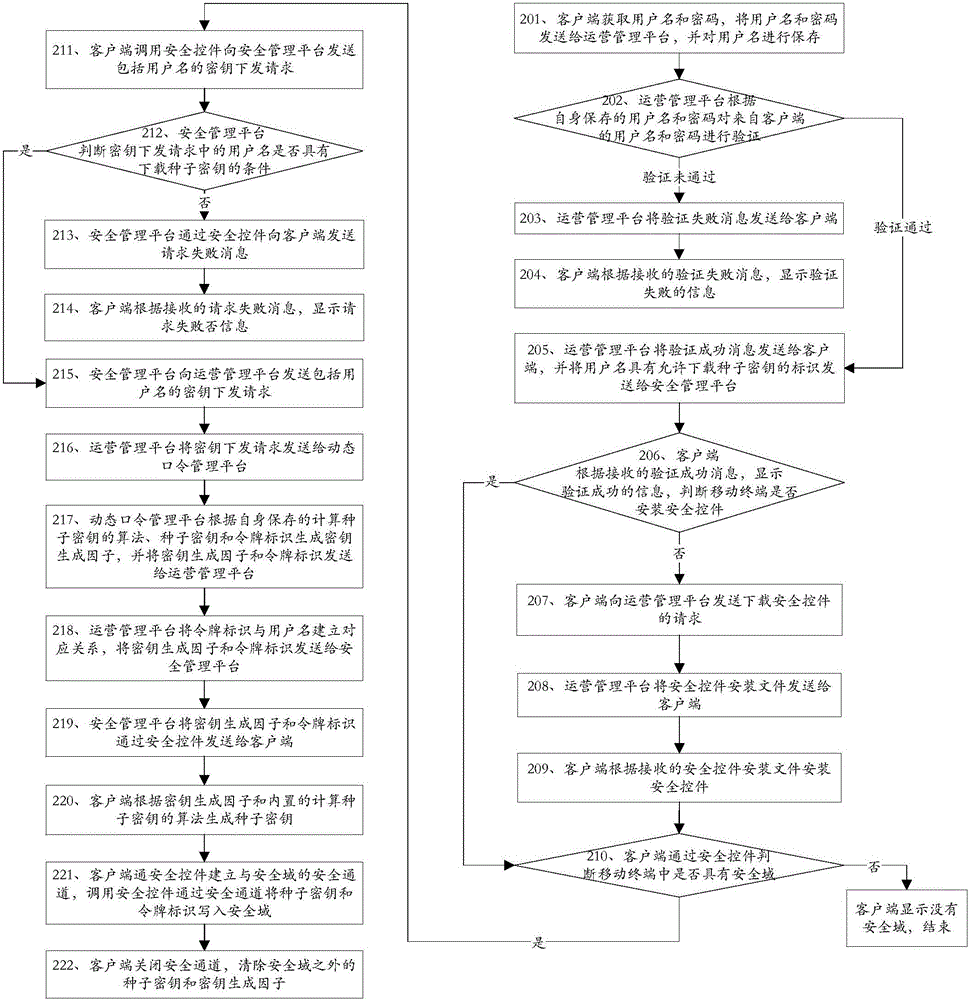
[0159] This embodiment provides a key delivery method, which is applied to a system composed of a mobile terminal, an operation management platform, a security management platform, and a dynamic password management platform, wherein the mobile terminal includes a client and a security domain, such as figure 2 shown, including:
[0160] Step 201: the client obtains the user name and password, and sends the user name and password to the operation management platform.
[0161] Specifically, the client obtains the user name and password input by the user, and sends the user name and password to the operation management platform.
[0162] For example, when the user opens the client in the mobile terminal, the mobile terminal displays the user name and password input window, when the user enters the user name and password in the corresponding input window and clicks the login or confirmation button, the client obtains the user name and password, and The user name and password are ...
Embodiment 3
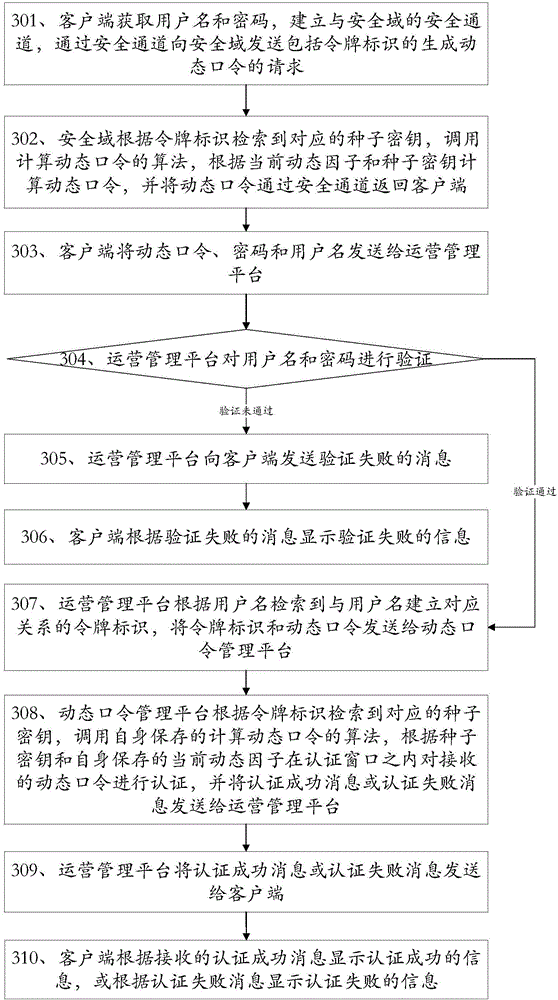
[0237] The invention provides a method for generating and authenticating a dynamic password, such as image 3 As shown in , it is a flow chart of generating a dynamic password when the client logs in and authenticating the generated dynamic password, including the following steps:
[0238] Step 301: The client obtains the user name and password, establishes a secure channel with the security domain, and sends a request for generating a dynamic password including a token identifier to the security domain through the secure channel.
[0239] Specifically, step 301 specifically includes:
[0240] Step 3011: The user opens the client terminal in the mobile terminal, and the client application interface is displayed on the mobile terminal, and an input window for user name and password is displayed on the client application interface.
[0241] Step 3012: The user enters the user name and password respectively through the user name input window and the password input window, clicks...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com