Http (hypertext transfer protocol) access method, http server and http system
An access method and server technology, used in transmission systems, digital transmission systems, and key distribution, can solve problems such as illegal access, and achieve the effect of preventing data leakage and ensuring data security.
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment 1
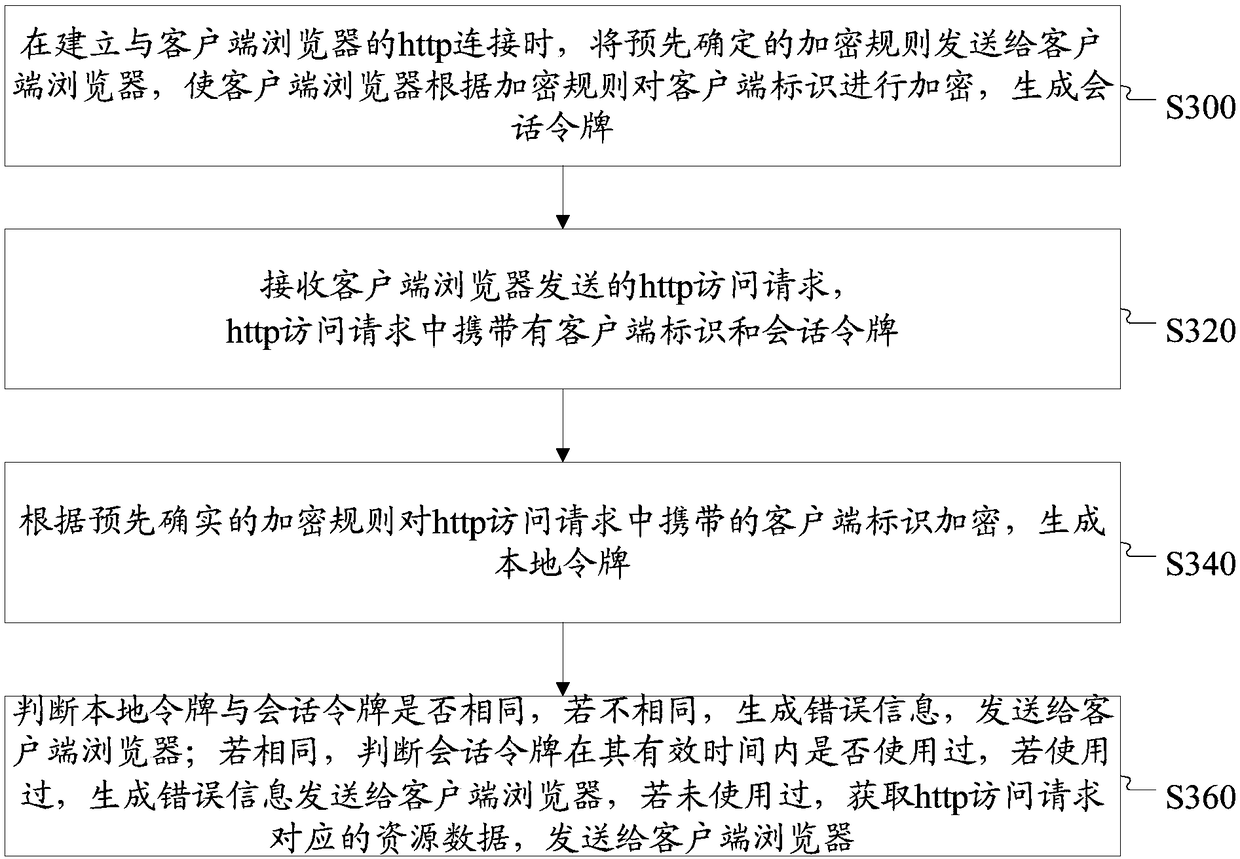
[0032] image 3 The flow chart of the http access method provided by the embodiment of the present invention, such as image 3 As shown, the method includes:
[0033] S300. When establishing an http connection with the client browser, send a predetermined encryption rule to the client browser, so that the client browser encrypts the client ID according to the encryption rule to generate a session token.
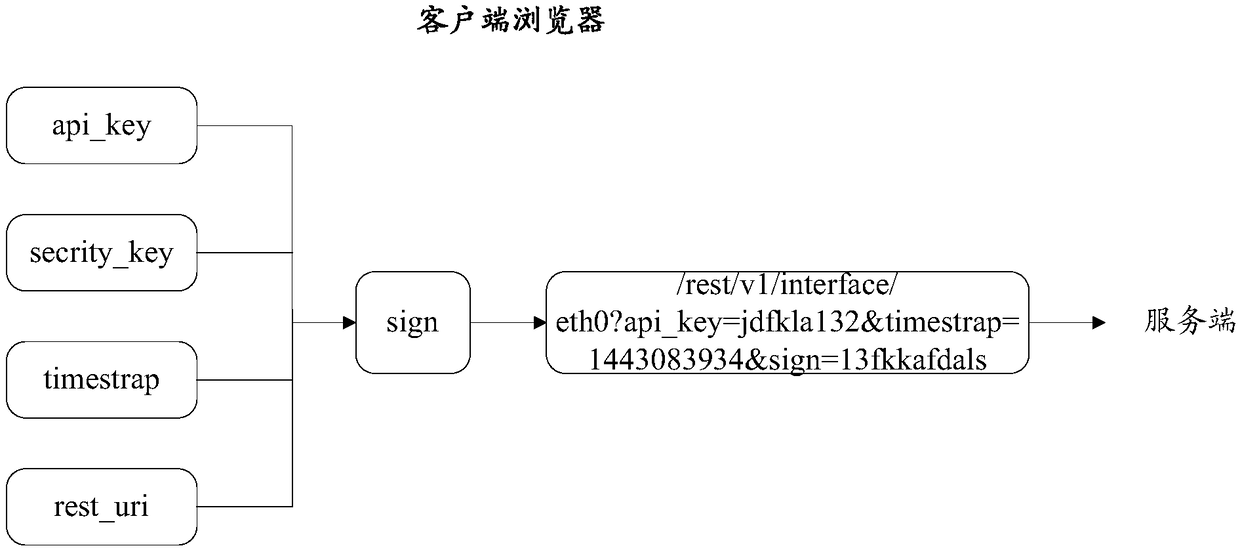
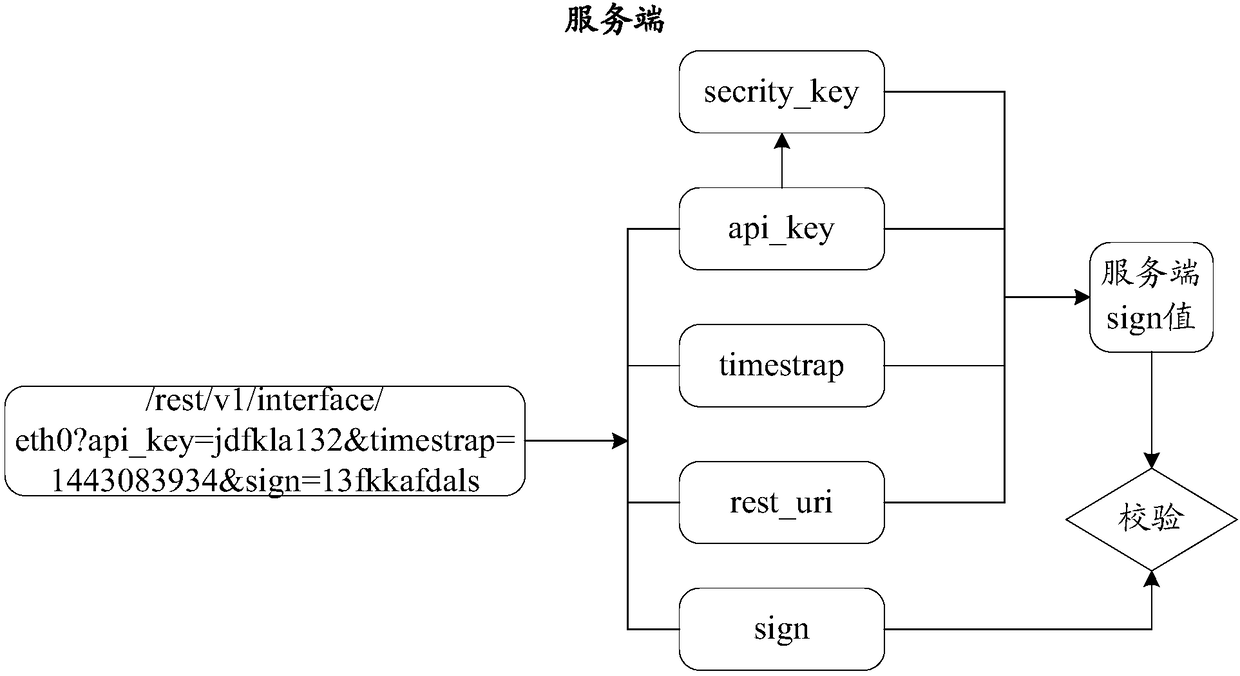
[0034] The predetermined encryption rule in this embodiment is to use the method name method of each application programming interface (Application Programming Interface, API) on the server side to encrypt the client ID, replacing the commonly used ulr of the application programming interface to encrypt the client ID. encryption.
[0035] Since the method name method of each API is different, and is developed and designed by the developer, the design rules of the method name method of the API are relatively free and flexible, difficult for illegal users to obtain, and have ...
Embodiment 2
[0052] Based on the same technical idea as the embodiment, this embodiment provides an http server.
[0053] Figure 4 The structural block diagram of the http server provided for the embodiment of the present invention, such as Figure 4 As shown, the http server includes: a sending unit 41, a receiving unit 42, an encryption unit 43, and a judging unit 44;
[0054] The sending unit 41 is used to send the predetermined encryption rules to the client browser when establishing an http connection with the client browser, so that the client browser encrypts the client identification according to the encryption rules to generate a session token Card;
[0055] The receiving unit 42 is configured to receive the http access request sent by the client browser, where the http access request carries the client identification and the session token;
[0056] An encryption unit 43, configured to encrypt the client ID carried in the http access request according to pre-determined encrypt...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com