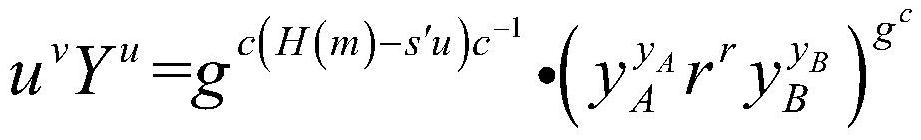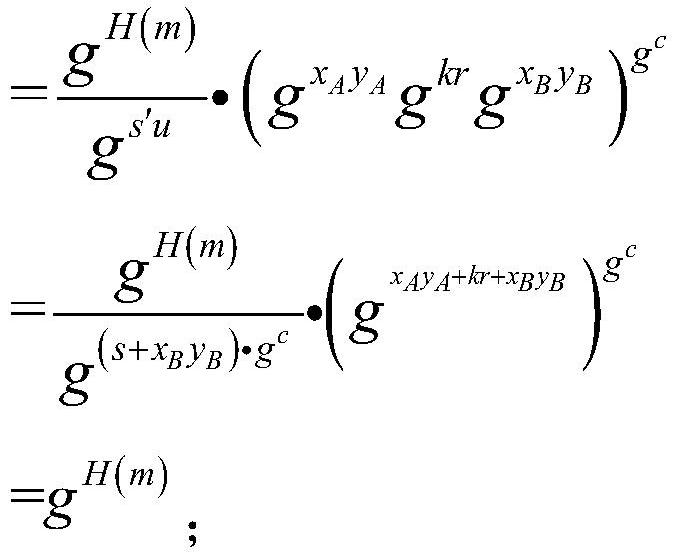Agent signature method based on Mamo
A proxy signature and formula technology, applied in the field of proxy signature based on Mambo, can solve the problems of violating the concept of proxy signature and infringing on the legitimate rights and interests of proxy signers, and achieve the effect of simple verification procedure and small amount of calculation.
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment
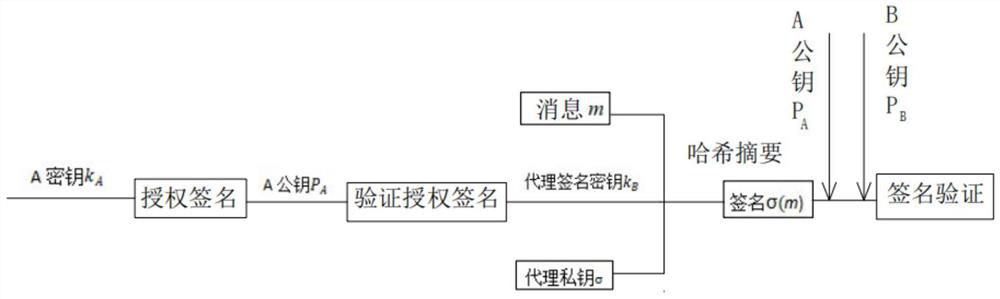
[0039] Example: see figure 1 , the present invention provides a technical solution: a Mambo-based proxy signature method, the specific method steps are as follows:
[0040] S1: Initialization: randomly select a large prime number p, q is a large prime factor of p-1, and g is generator; A is the original signer; B is the proxy signer; C is the signature verifier; A’s private key and public key pair are (x A ,y A ), B's private key and public key pair is (x B ,y B ),and m represents the message to be signed;
[0041] S2: The process of key generation: A randomly selects an integer k, calculates r and s through formulas (W1) and (W2), and then sends (r, s) as a proxy key to B through a secure channel; the specific formula as follows:
[0042] r=g k mod p (W1)
[0043] s=(x A the y A +kr) mod q (W2);
[0044] S3: The process of verifying the proxy key: After receiving (r, s), B first verifies the equation Whether it is established, if it is established, it can...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com