Patents
Literature
88 results about "Verification routine" patented technology
Efficacy Topic
Property
Owner
Technical Advancement
Application Domain
Technology Topic
Technology Field Word
Patent Country/Region
Patent Type
Patent Status
Application Year
Inventor
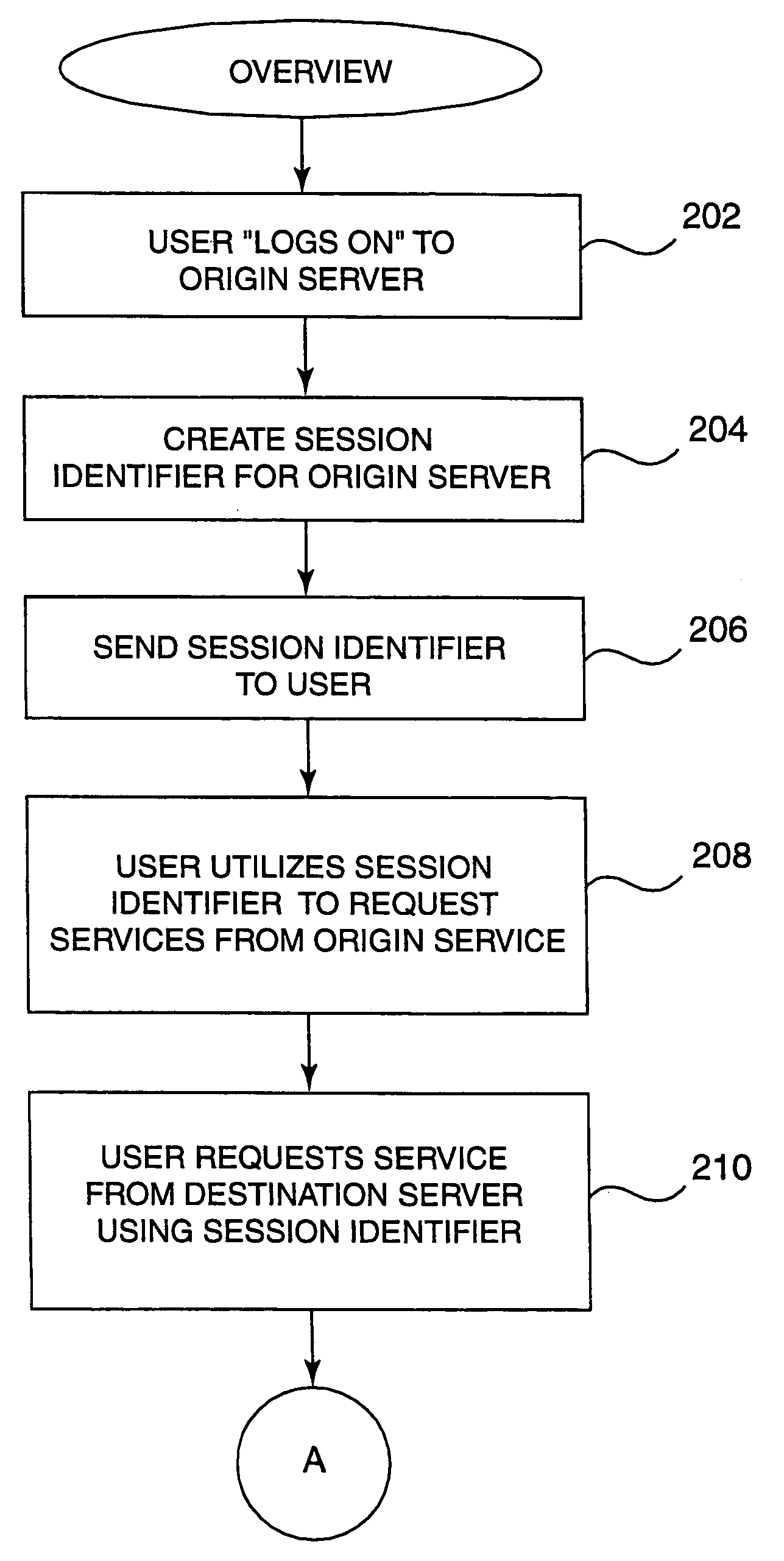
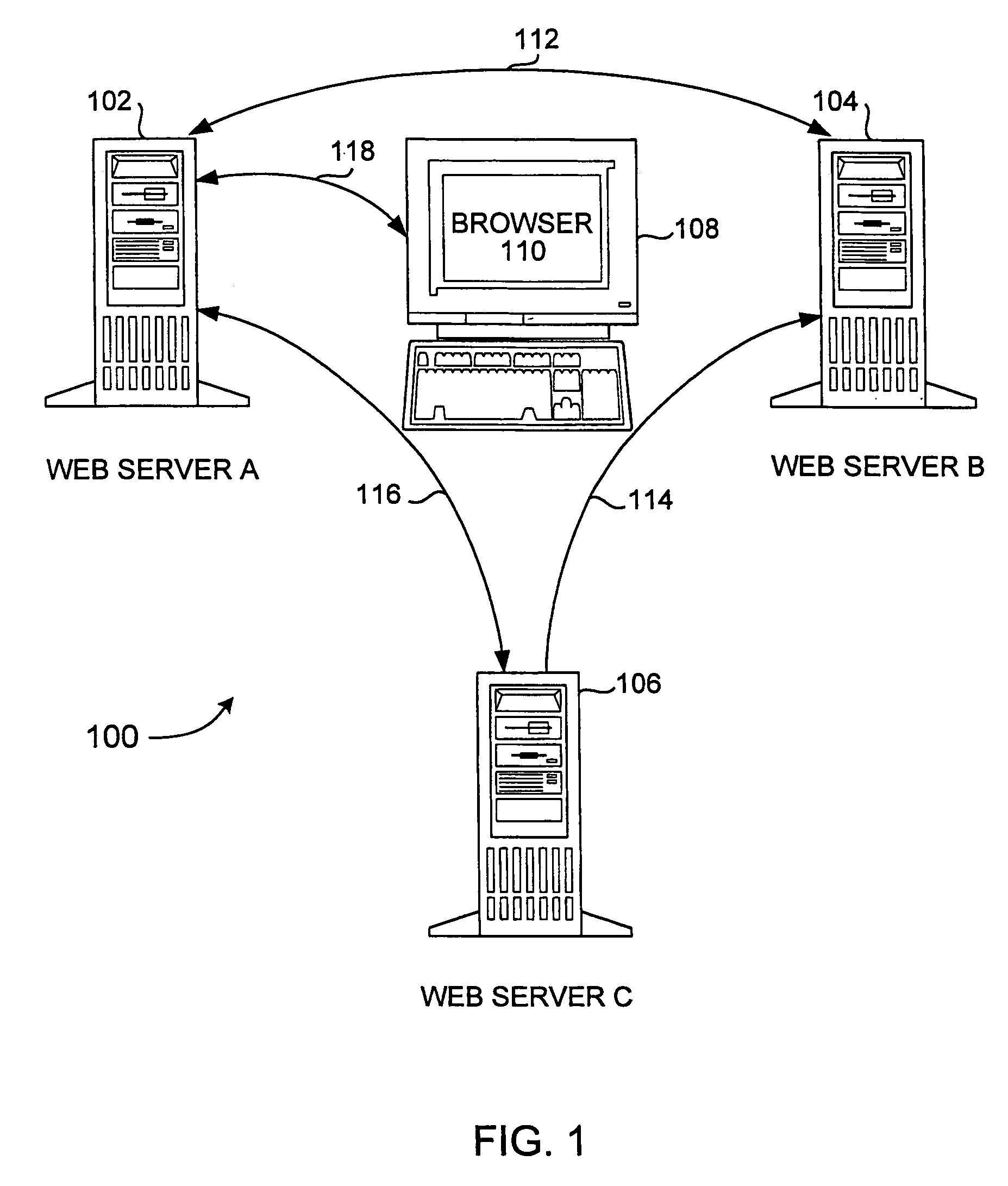
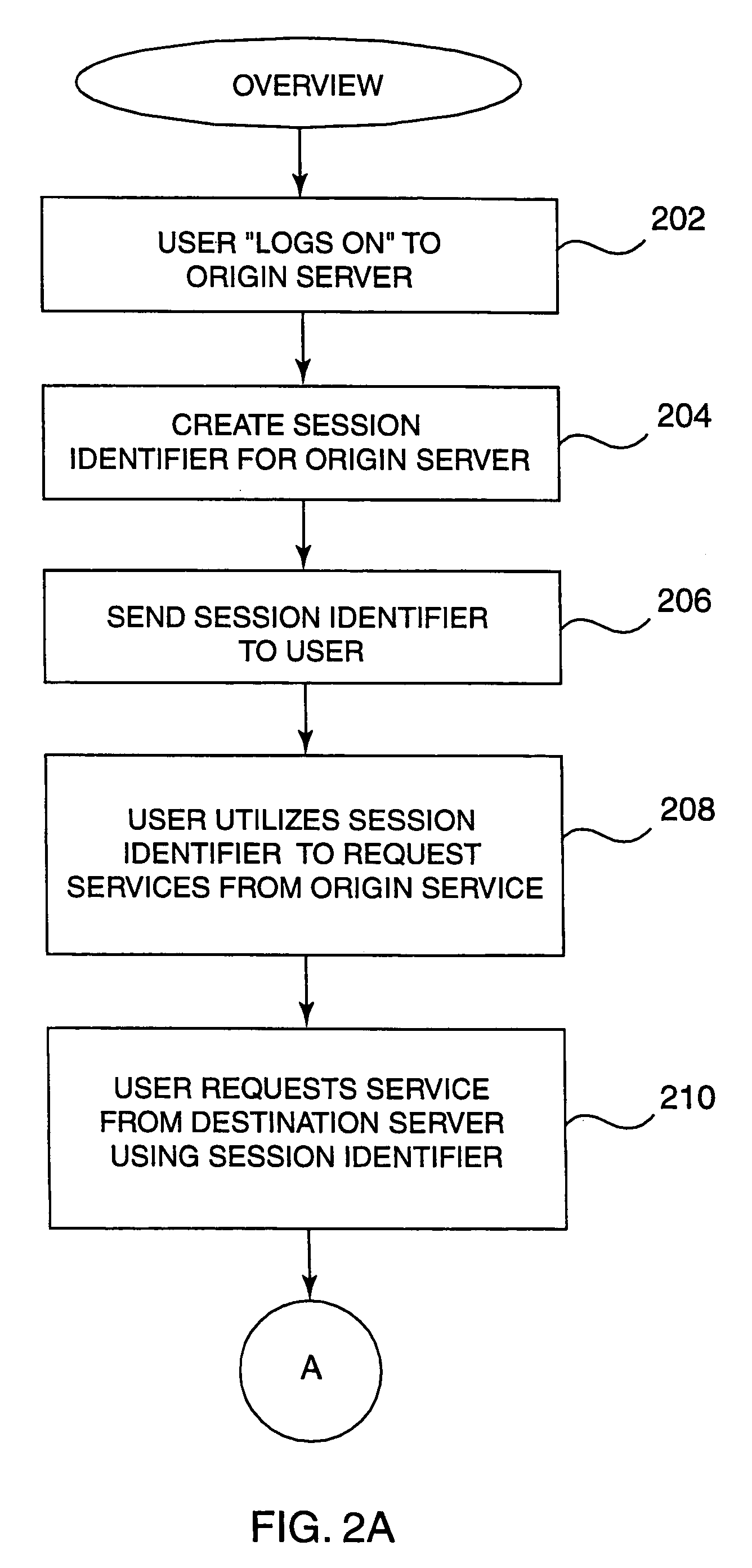
Universal session sharing
InactiveUS7188181B1Digital data processing detailsUser identity/authority verificationWeb siteA domain
Methods, systems, and computer program products are disclosed for sharing data related to a session created by a user within a domain of sites or services. A user logs on to a site, such as a Web site or other entity, and creates a session. The session created has an identifier which can be shared with other sites or entities in the same domain or logical group. In the course of utilizing services on the site, the user attempts access to services on another site. When this attempt is made, the user's session data is passed to the second site. The session data is analyzed on the second site by checking configuration data on the second site. If it is not found to be valid (e.g. it is created by a site outside the domain of the second site), the user is required to explicilty logon. If the configuration data indicates that it is valid, the session data is passed back to the first site using a verification routine (part of the configuration data) on the second site. If the first site authenticates the session data, the user is allowed to access services on the second site without having to explicitly logon.
Owner:ORACLE INT CORP
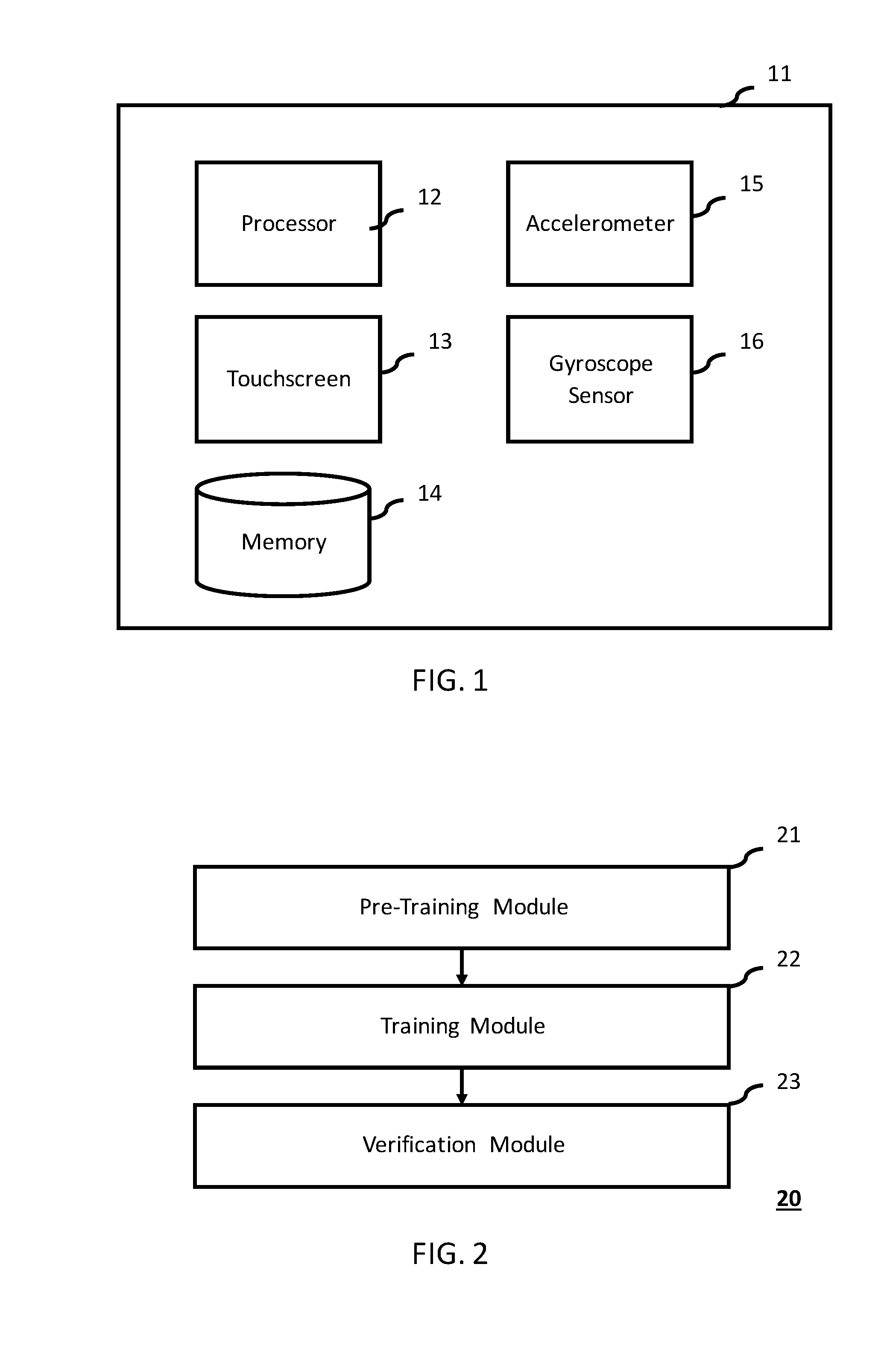
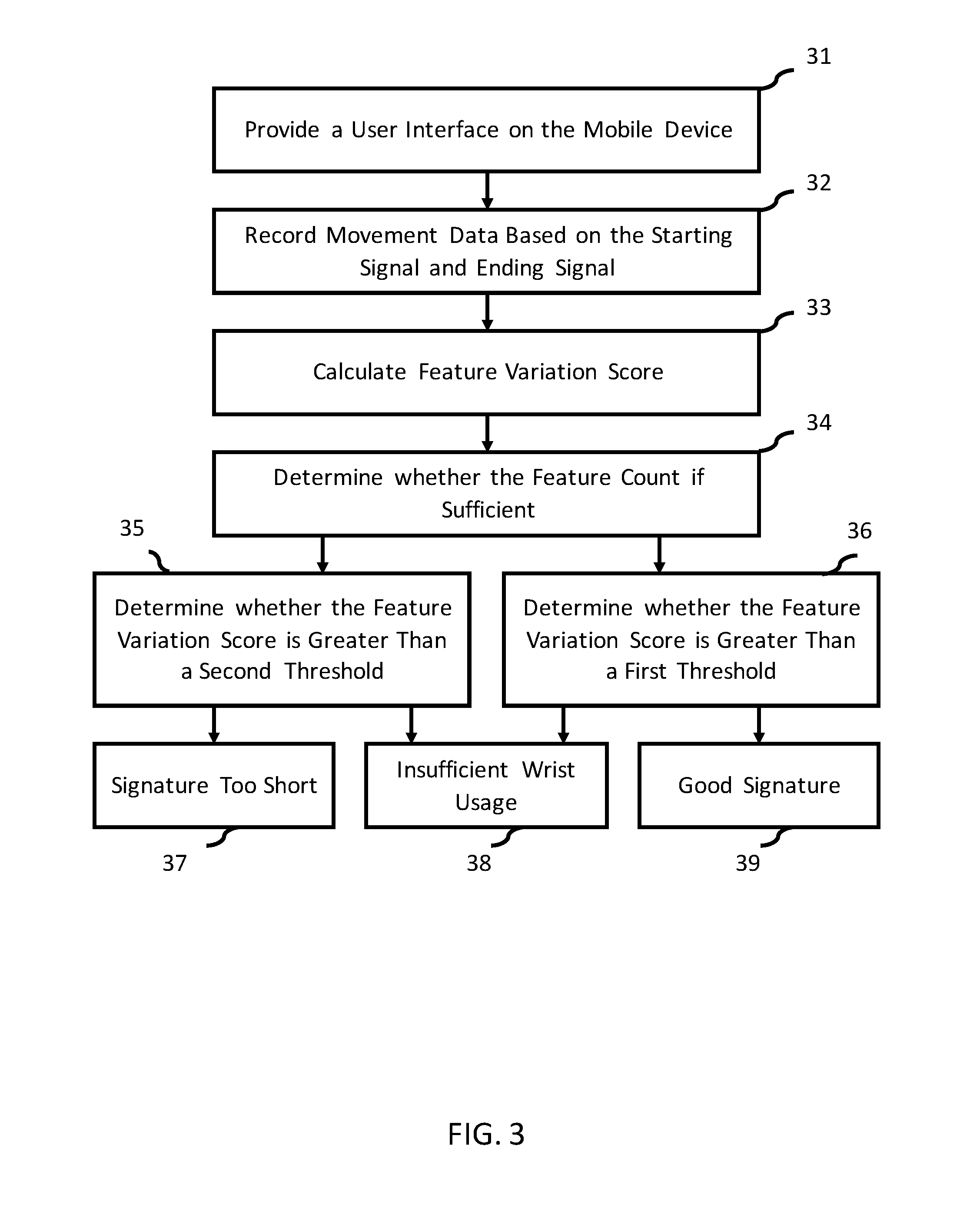
Motion based authentication systems and methods
InactiveUS20160226865A1Fast and secure and low-cost of authenticationCryptography processingDigital data authenticationUser inputTarget signature
A motion-based authentication method of authenticating a user with a mobile device is provided. A pre-training routine is conducted to detect an orientation characteristic and a duration characteristic associated with a user input. A training routine is conducted to capture a set of base signatures and to compute the consistency level associated with the signatures. A verification routine is conducted to compare the target signature with the set of base signatures. Authorization is granted if the target signature has reached the similarity threshold with respect to the base signatures.
Owner:CHEN PO KAI
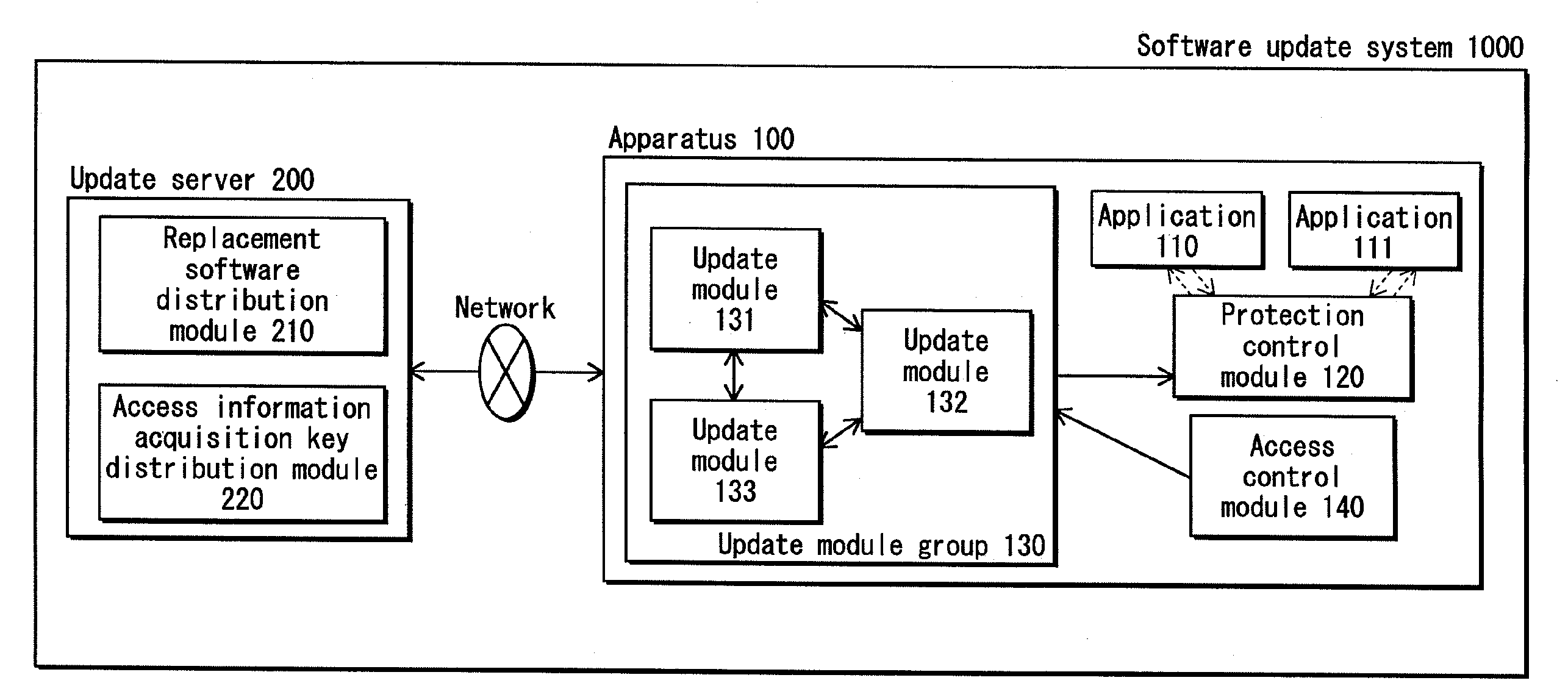
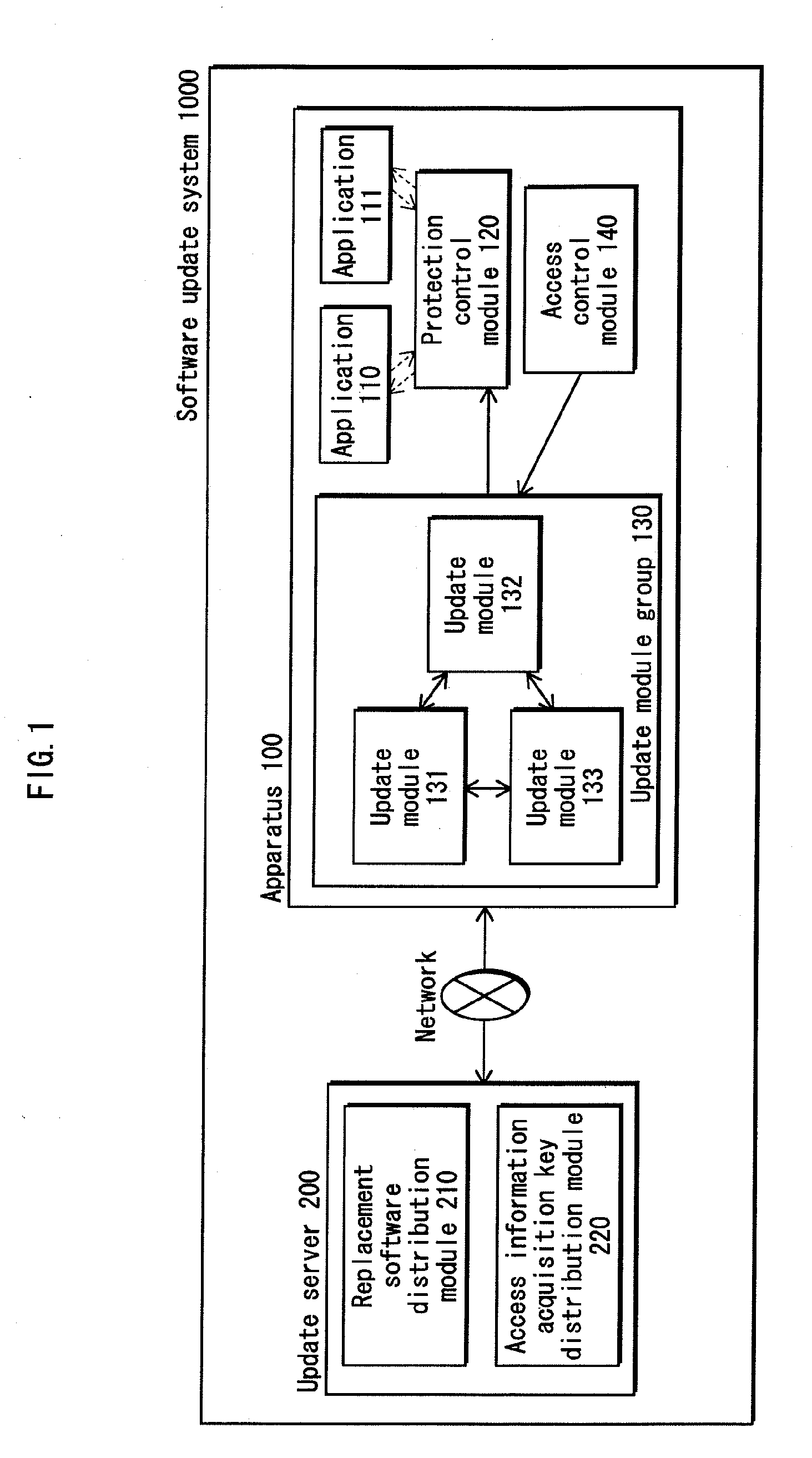
Software updating apparatus, software updating system, alteration verification method and alteration verification program
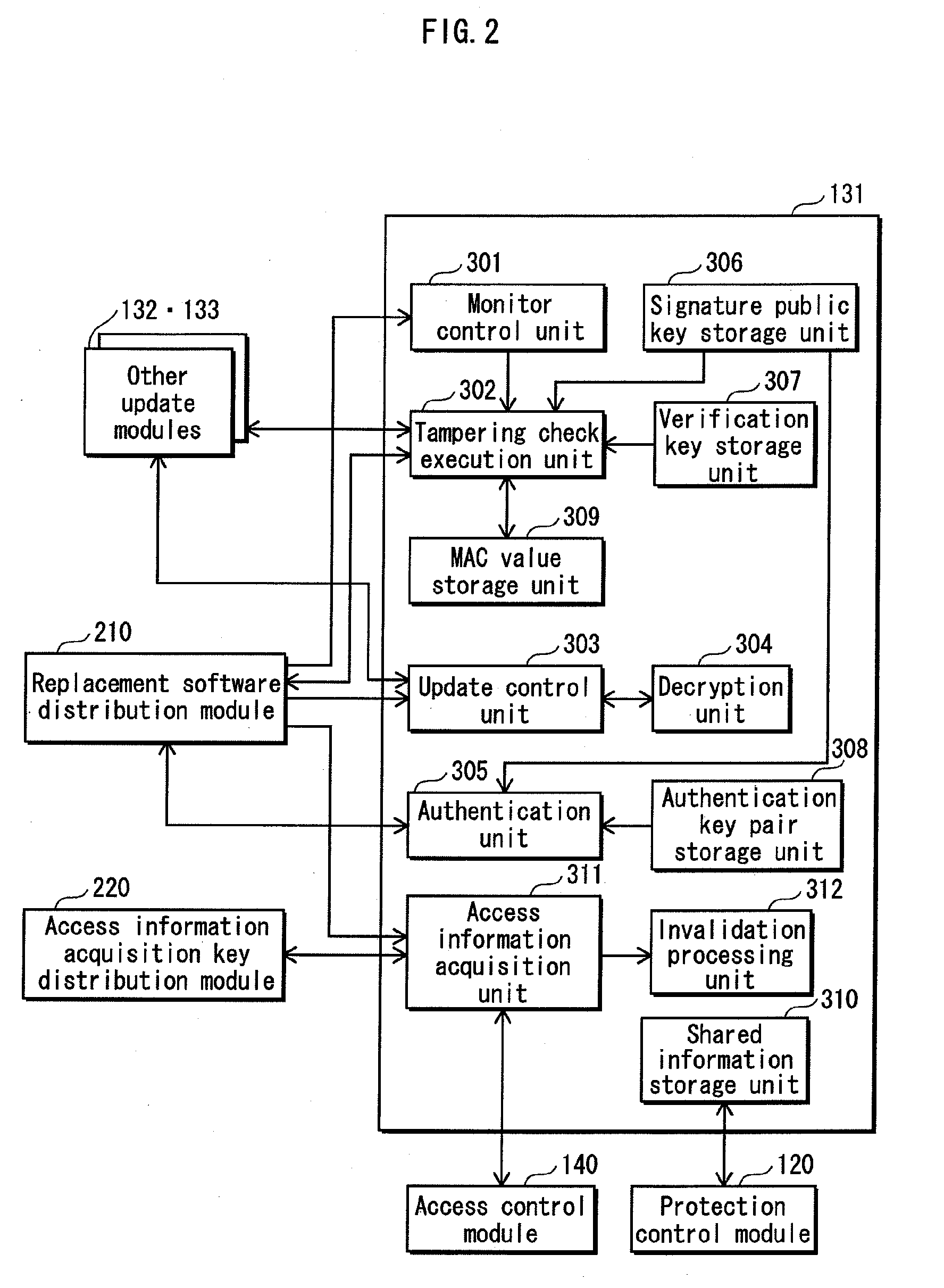
ActiveUS20100180343A1Increase probabilityPrevent protection controlKey distribution for secure communicationMemory loss protectionValidation methodsSoftware update
To aim provide a software update apparatus including an install module group (130) composed of a plurality of install modules. Each of the install modules has a function of receiving, from an external server (200), a replacement protection control module (121) to be used for updating a protection control module (120) having a function of verifying whether a predetermined application has been tampered with. Each of the install modules simultaneously running is verified by at least another one of the install modules simultaneously running, as to whether the install module has a possibility of performing malicious operations.
Owner:PANASONIC CORP
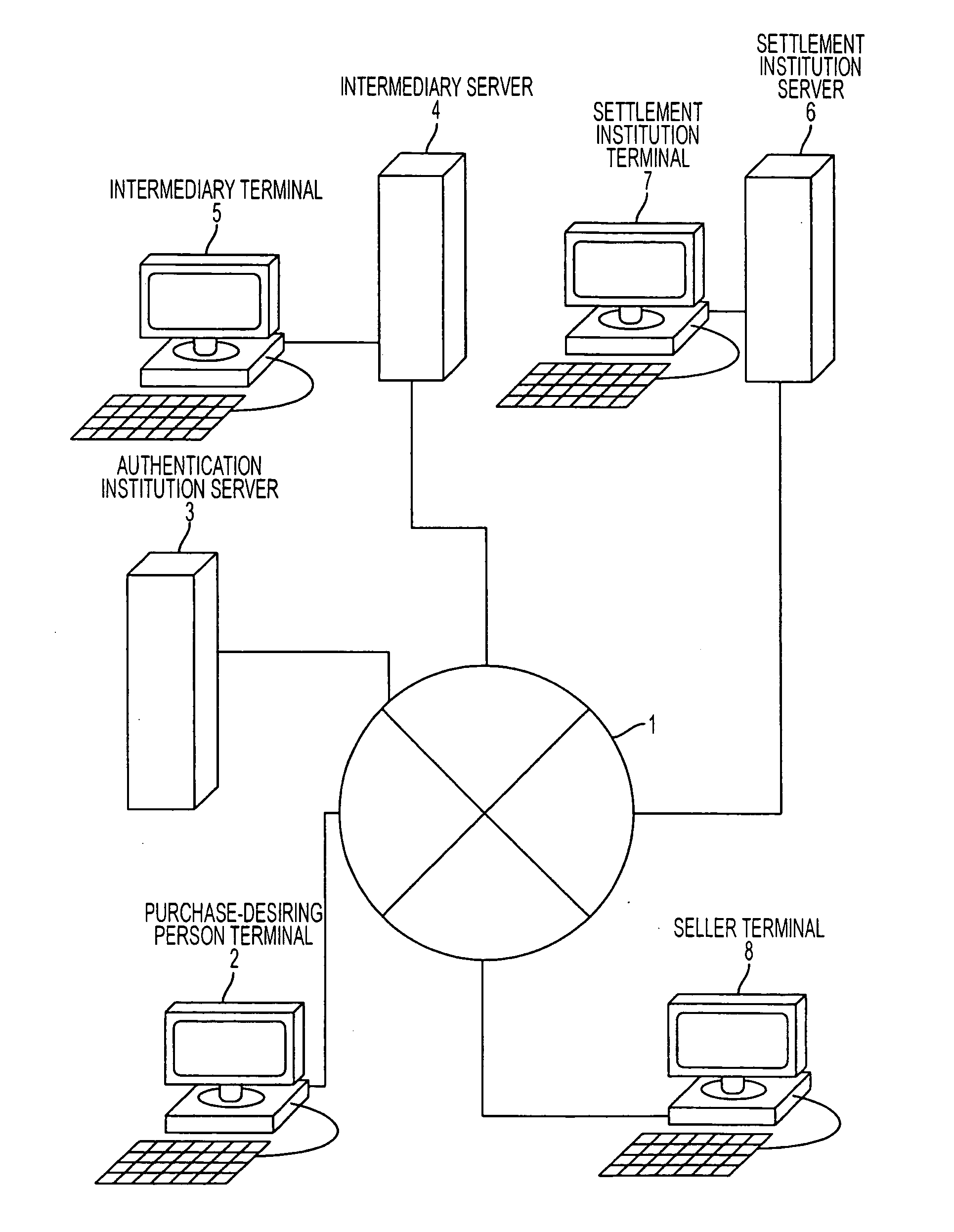
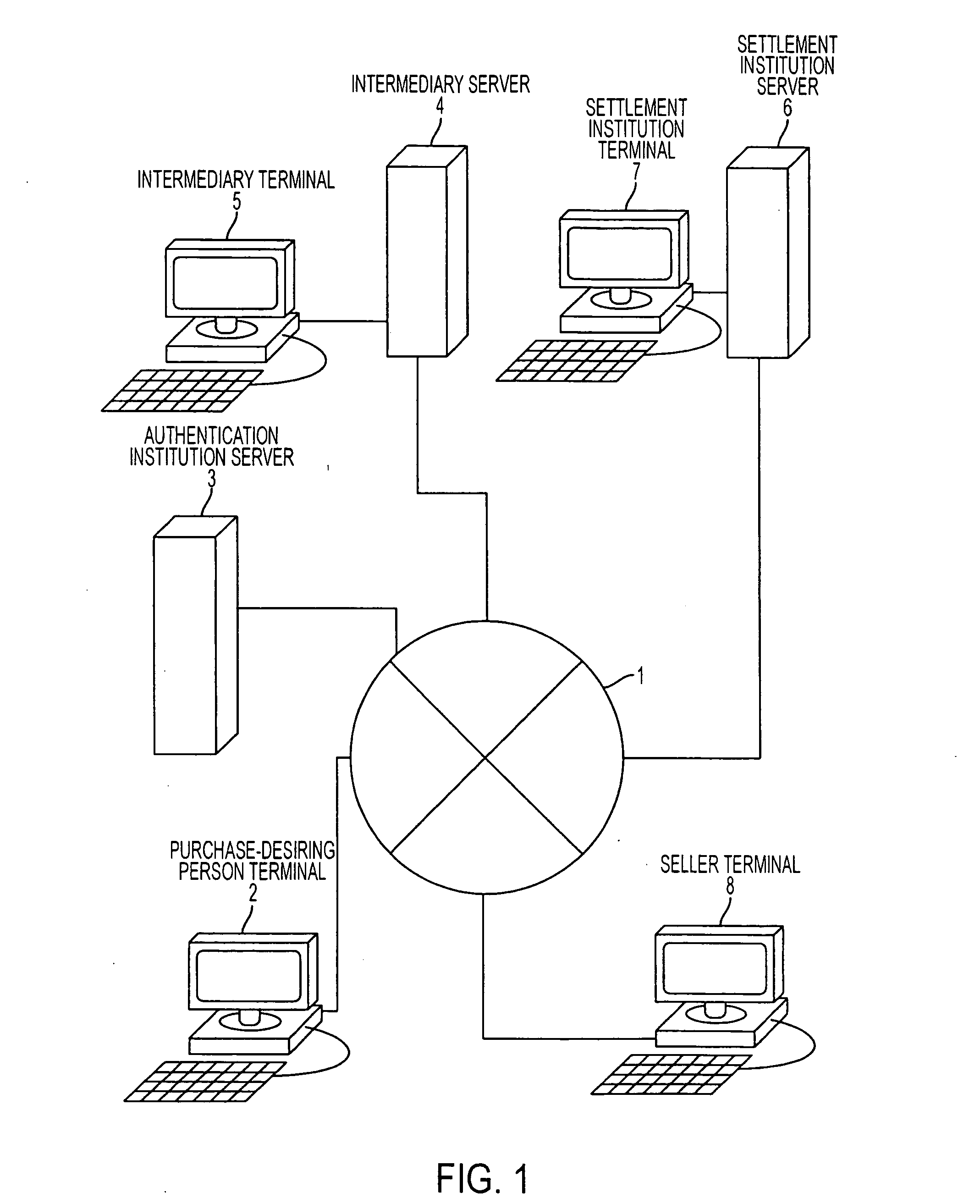
Personal information verification program, method and apparatus
InactiveUS20070145123A1User identity/authority verificationComputer security arrangementsPaymentComputer terminal
A personal information verification system using an intermediary server and a settlement institution server, where personal information with an electronic signature, showing a desired purchase and a first version of item hash information are received from a person terminal. Then, the intermediary server generates a second version of item hash information by hiding the purchase item and adding an electronic signature, and transmits the second version of the item hash information to the settlement institution server. The settlement institution server sends a payment bill to a seller, generates the third version of the item hash information, and transmits the third version of the item hash information together with the amended personal information. The intermediary server generates a fourth version of the item hash information and transmits the personal information and the first to fourth versions of the item hash information to the seller terminal.
Owner:FUJITSU LTD
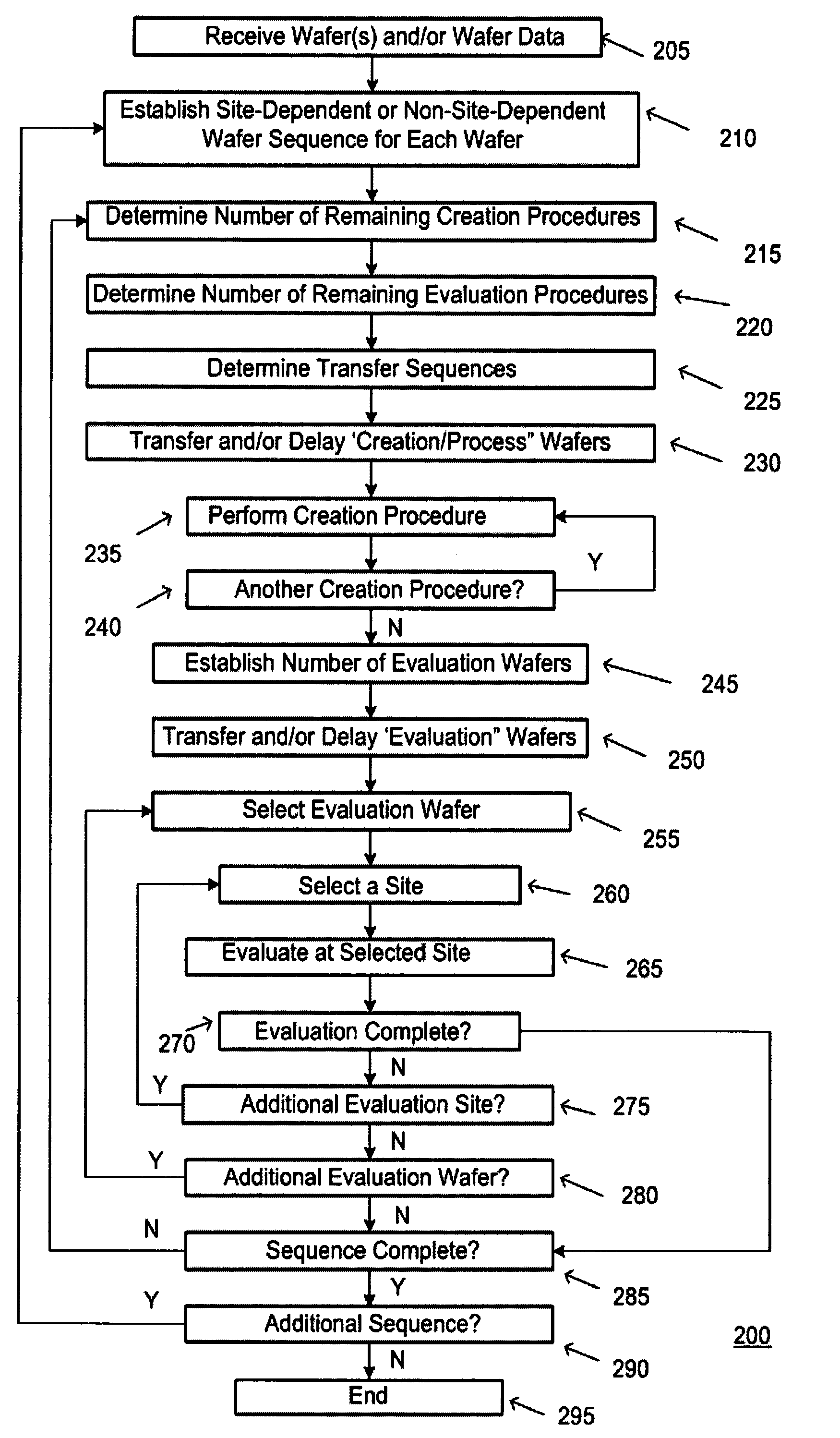
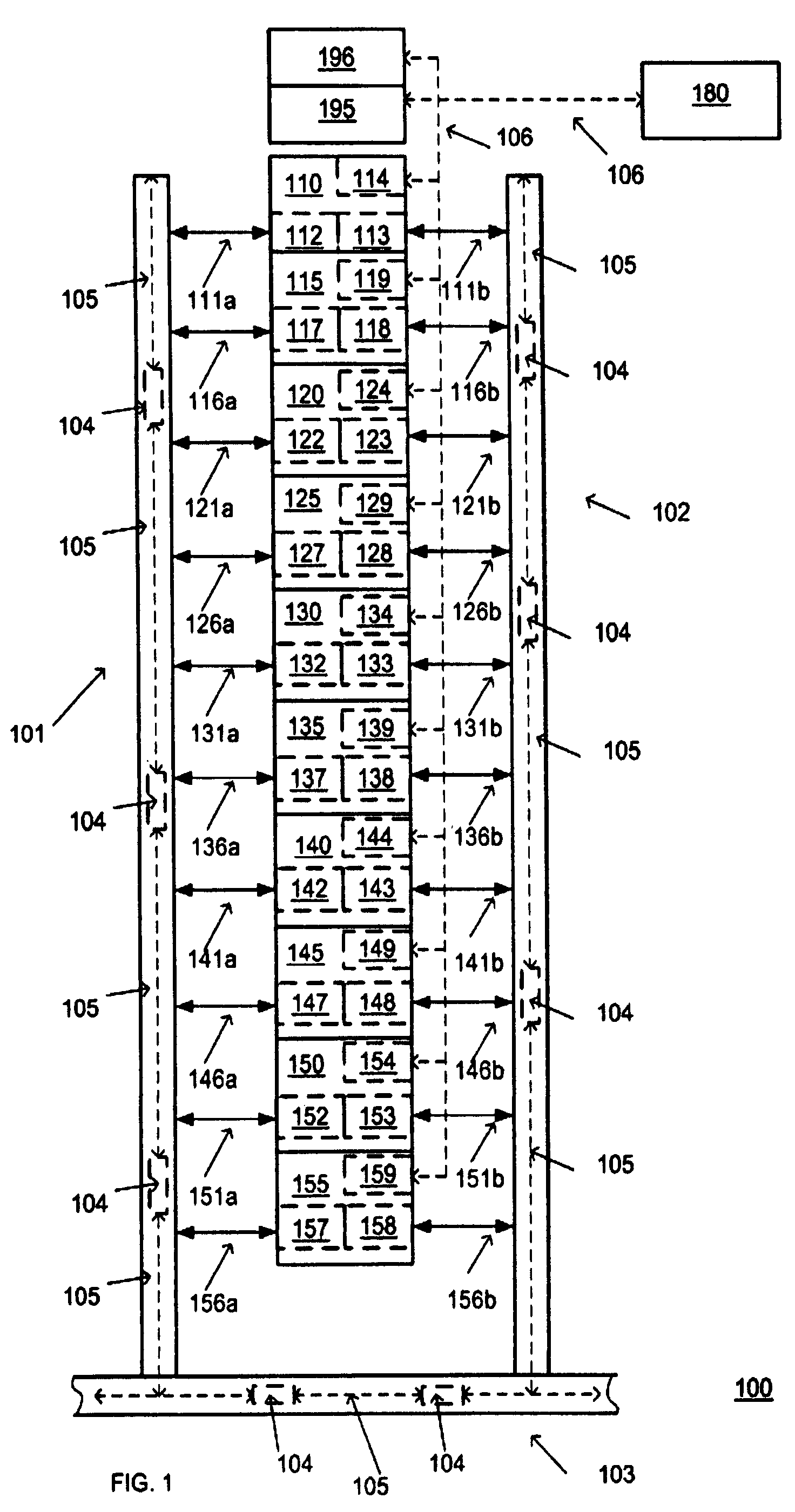
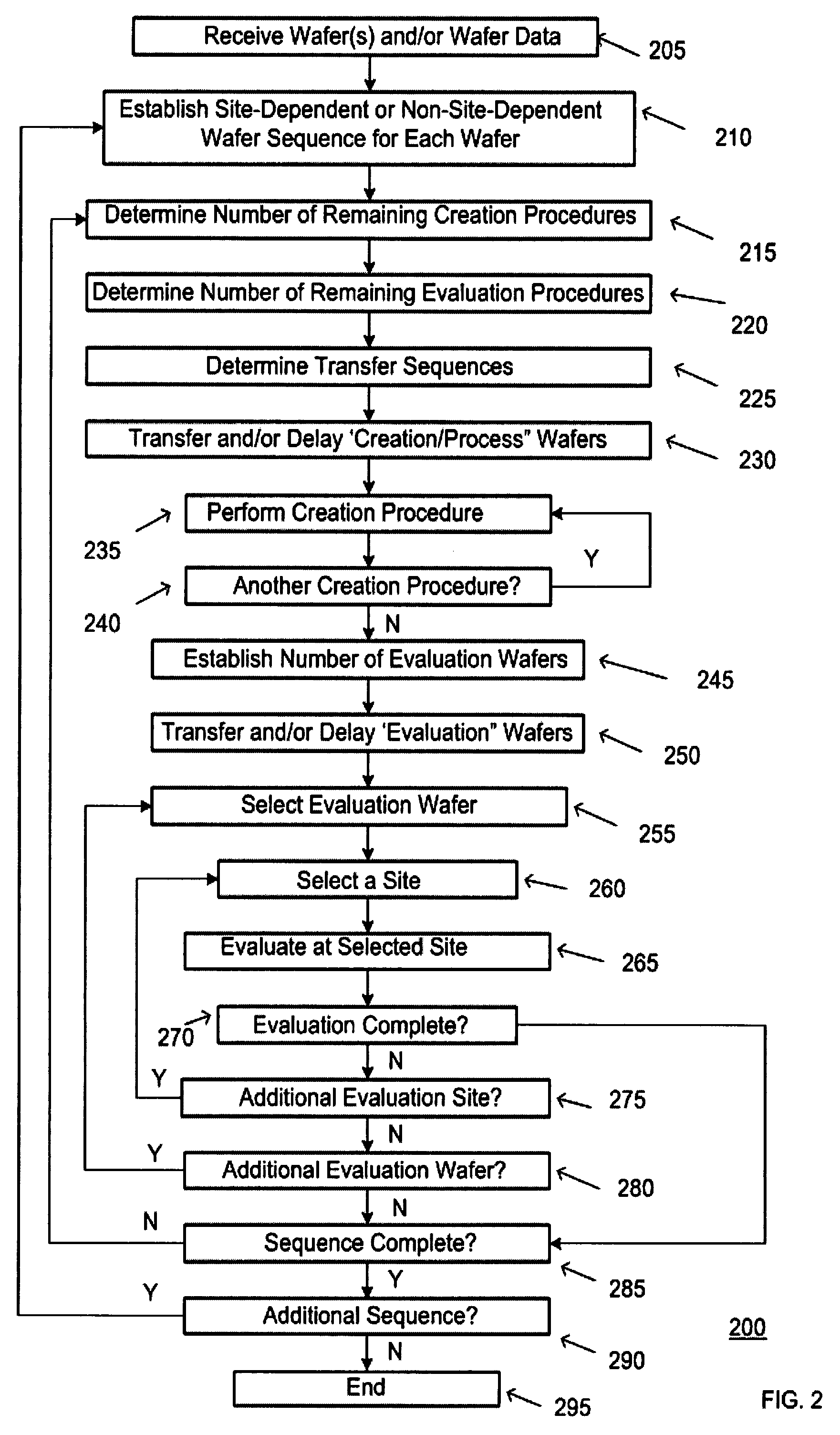
Method and apparatus for verifying a site-dependent procedure
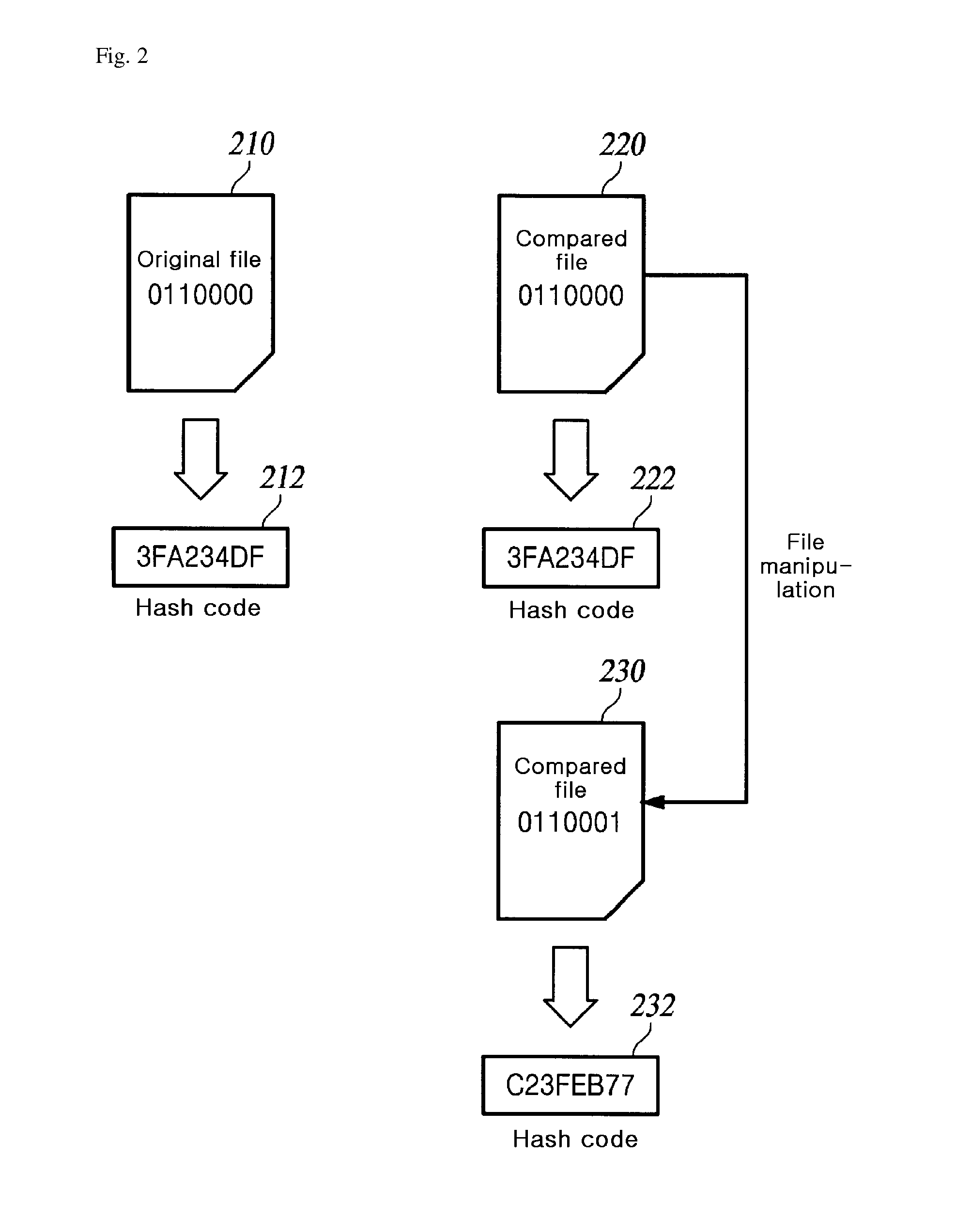
InactiveUS7596423B2Speed up the processReduce risk factorProgramme controlMaterial analysis by optical meansComputer architectureTransfer system
Owner:TOKYO ELECTRON LTD
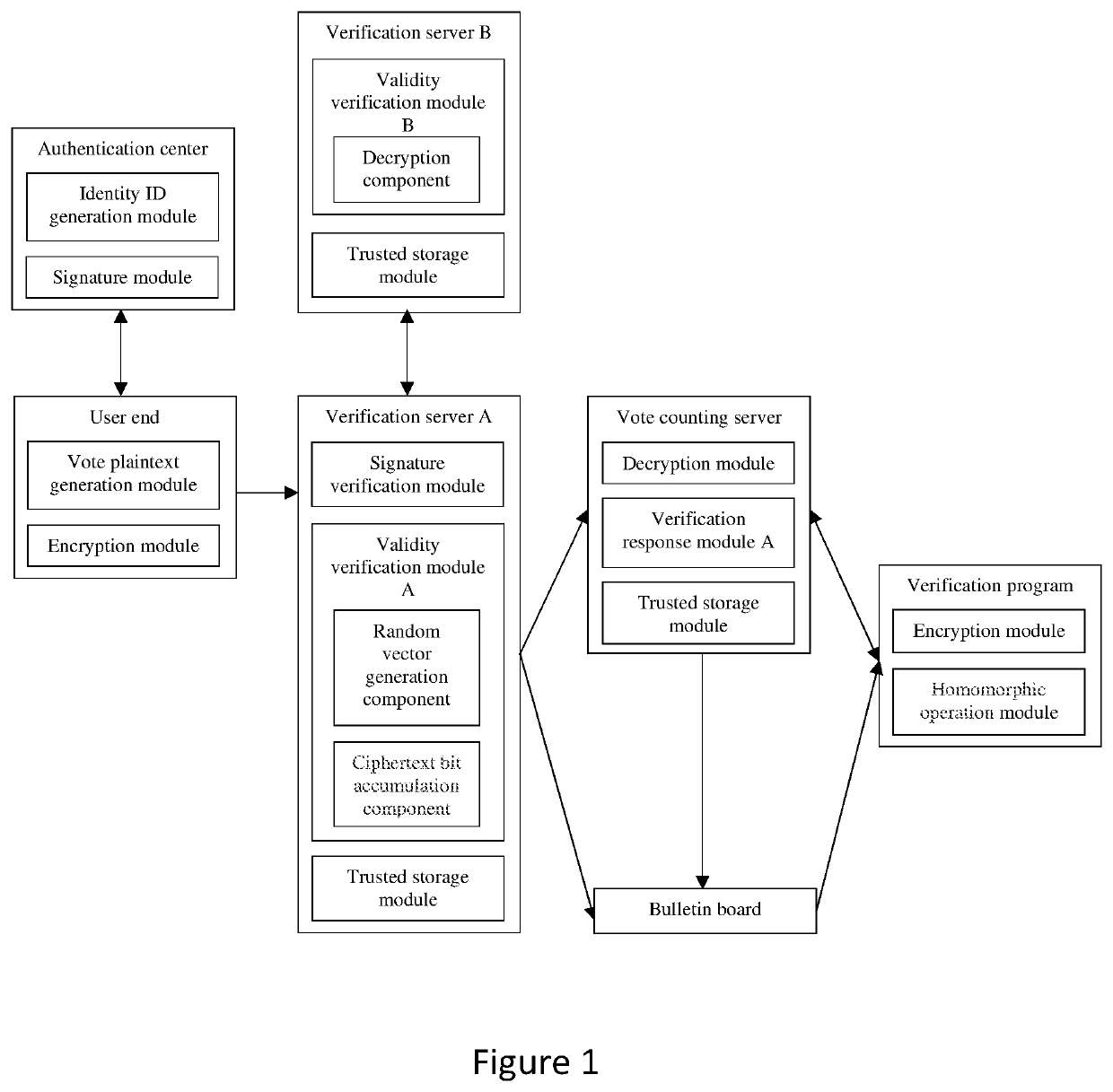
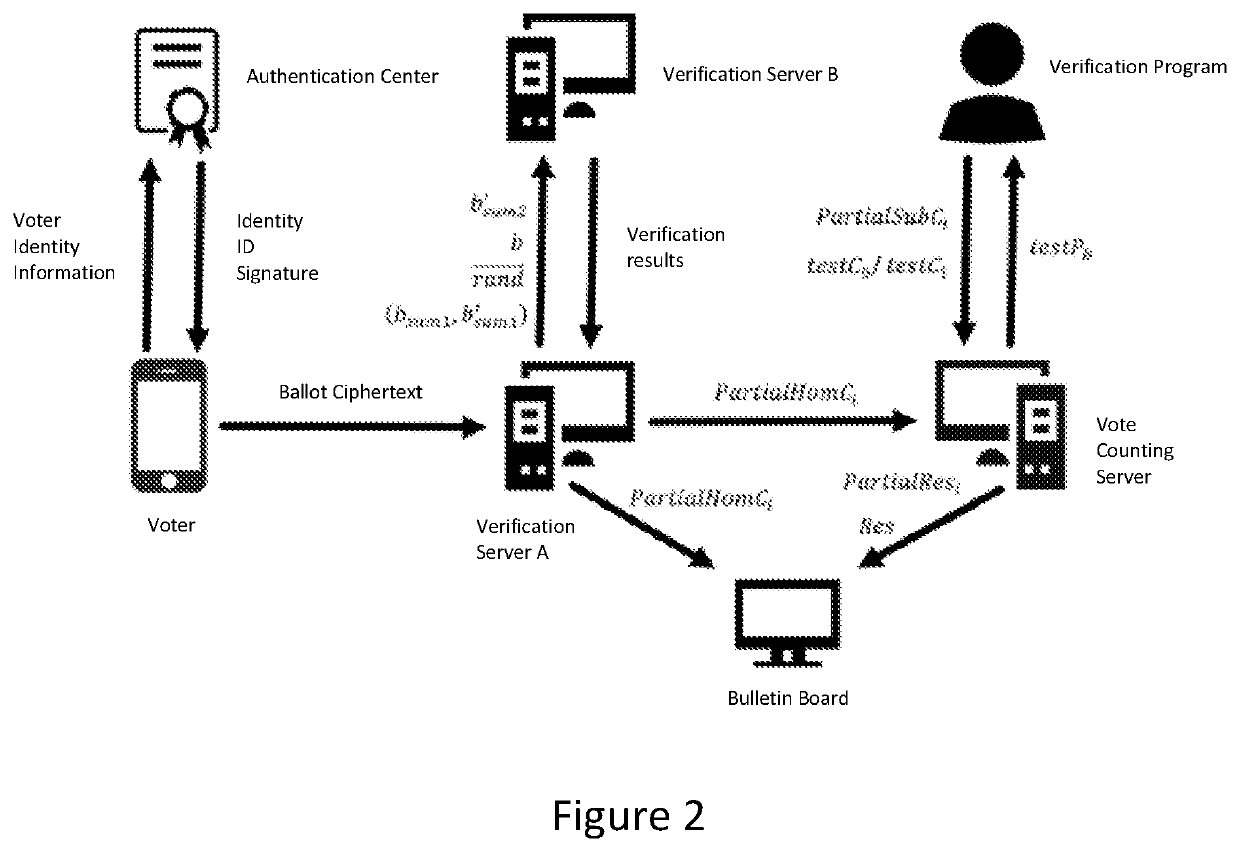
Verifiable post-quantum electronic voting system and implementation method therefor
PendingUS20200402073A1Improve computing efficiencyVoting arrangementVoting apparatusInternet privacyCiphertext
Owner:SOUTH CHINA UNIV OF TECH
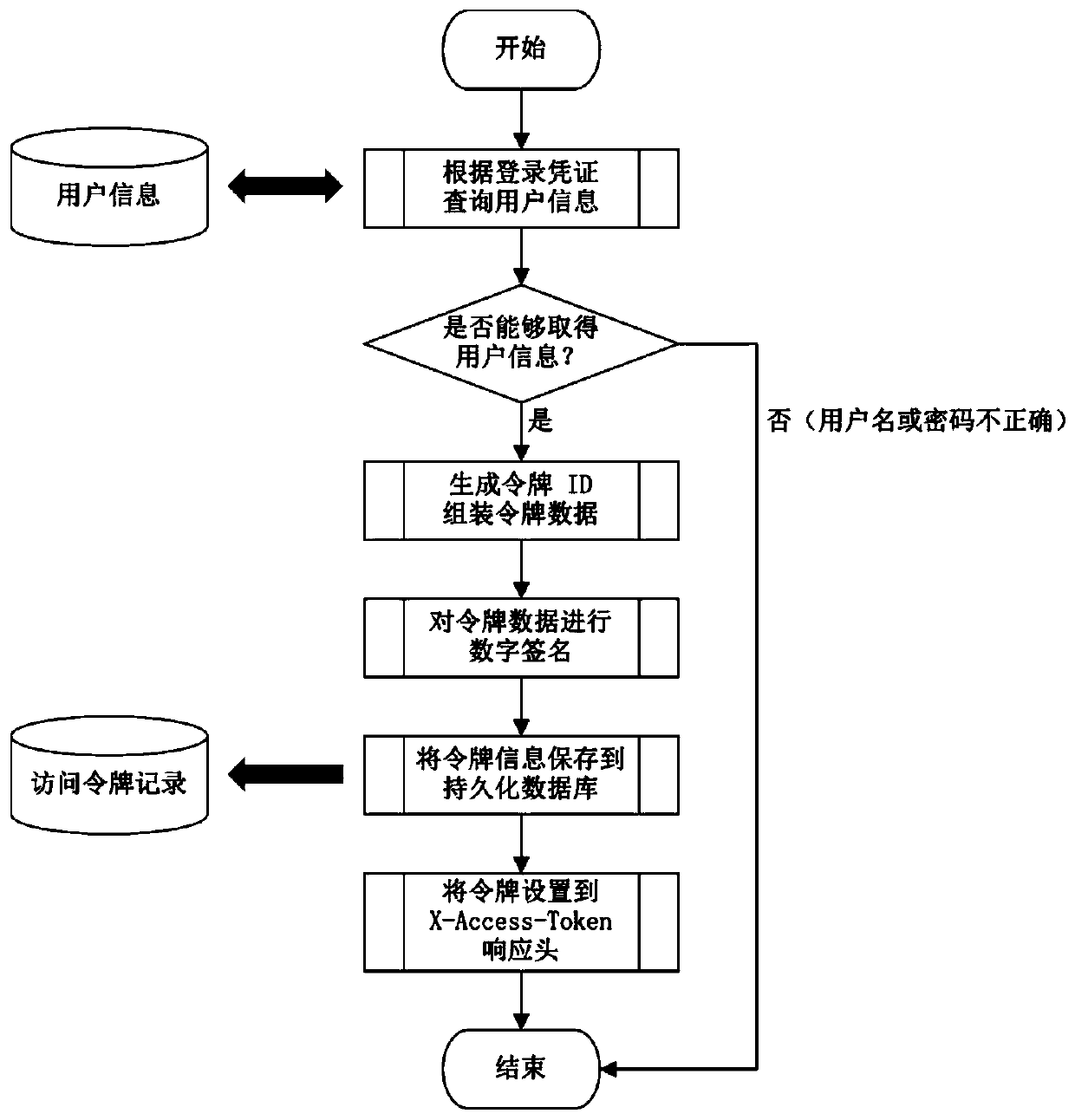
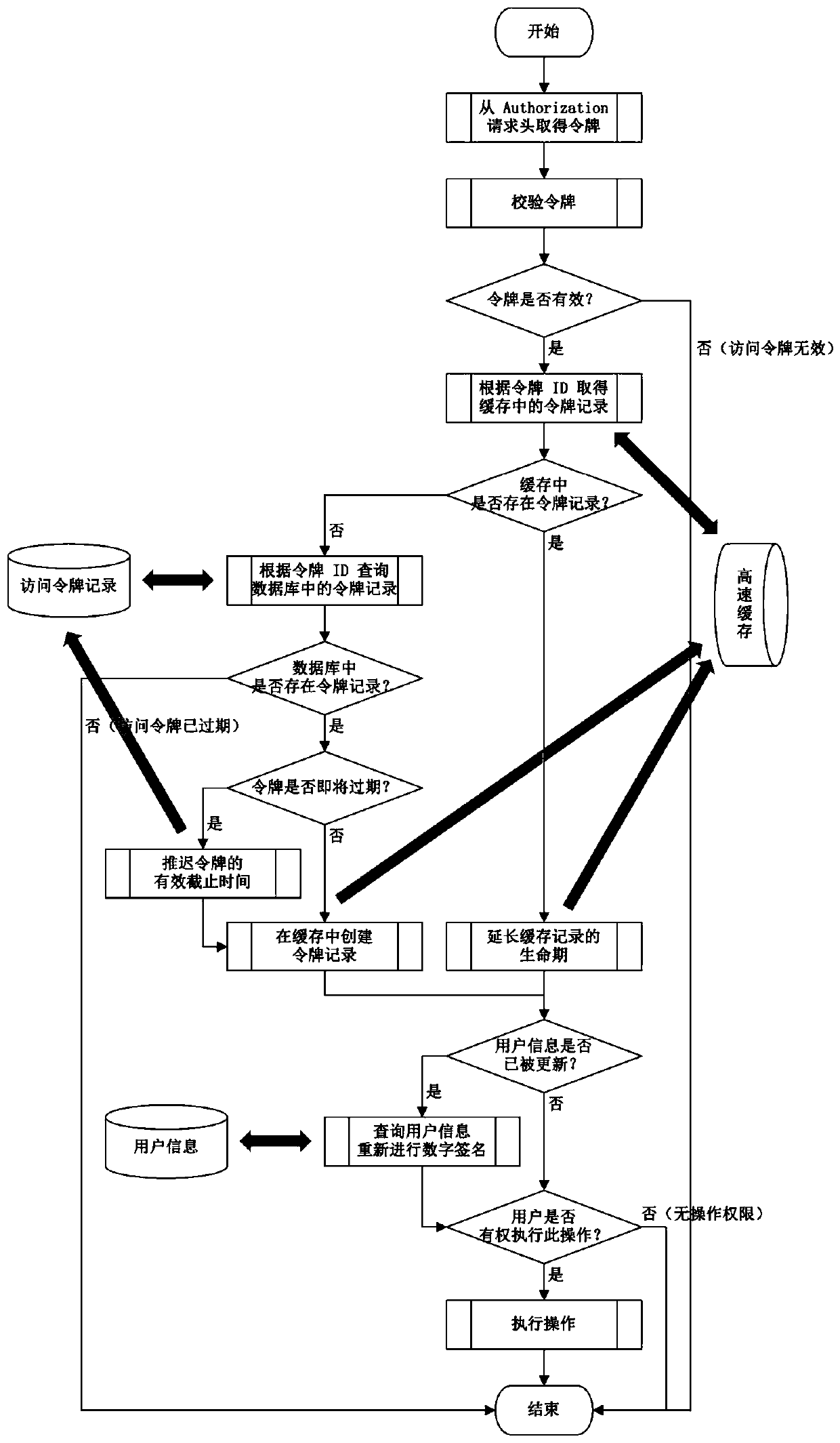
JWT-based authorization method capable of being manually revoked
InactiveCN110855672APrevent theftReduce consumptionKey distribution for secure communicationEncryption apparatus with shift registers/memoriesDigital signatureEngineering
The invention relates to application of a network authorization technology, in particular to a JWT-based authorization method capable of being manually revoked, which is an efficient, recyclable and instantly-updated authorization mechanism based on an access token. The method comprises a program used for providing login certificate verification and a server access token verification process; theprogram for providing the login certificate verification comprises the following steps: 1a, querying user information according to the login certificate; 2a, judging whether the user information can be obtained or not, and generating token ID assembly token data if the user information can be obtained; 3a, performing digital signature on the token data in the 2a; 4a, storing the token informationin a persistent database, and creating an access token record; 5a, setting the token to an X-Access-Token response header, and ending the authentication; 6a, judging whether the user information can be obtained or not in the 2a, and if the user information cannot be obtained, directly ending the authentication.
Owner:无锡家校邦网络科技有限公司
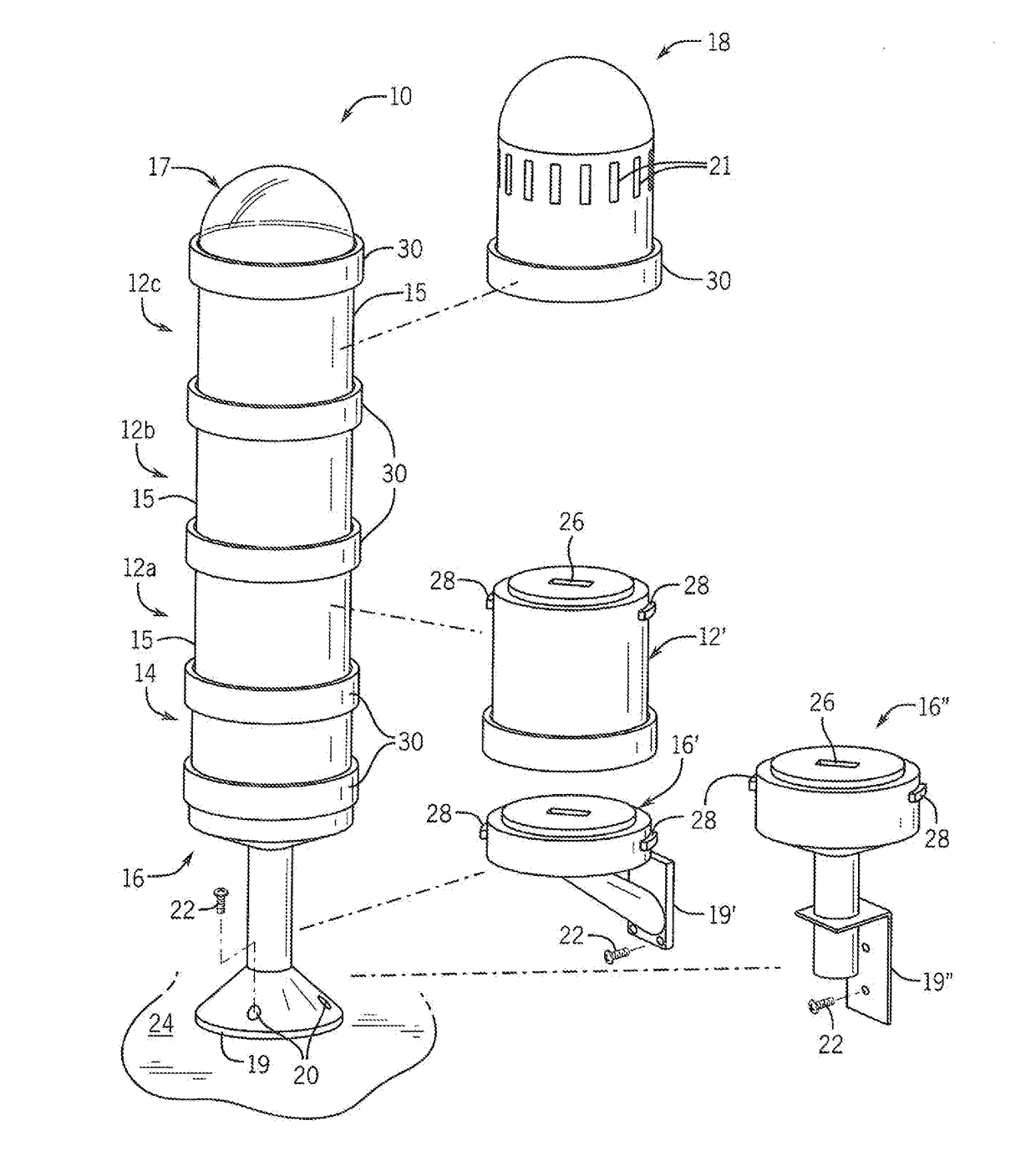
System and Method of Identifying a Module in a Stack Light
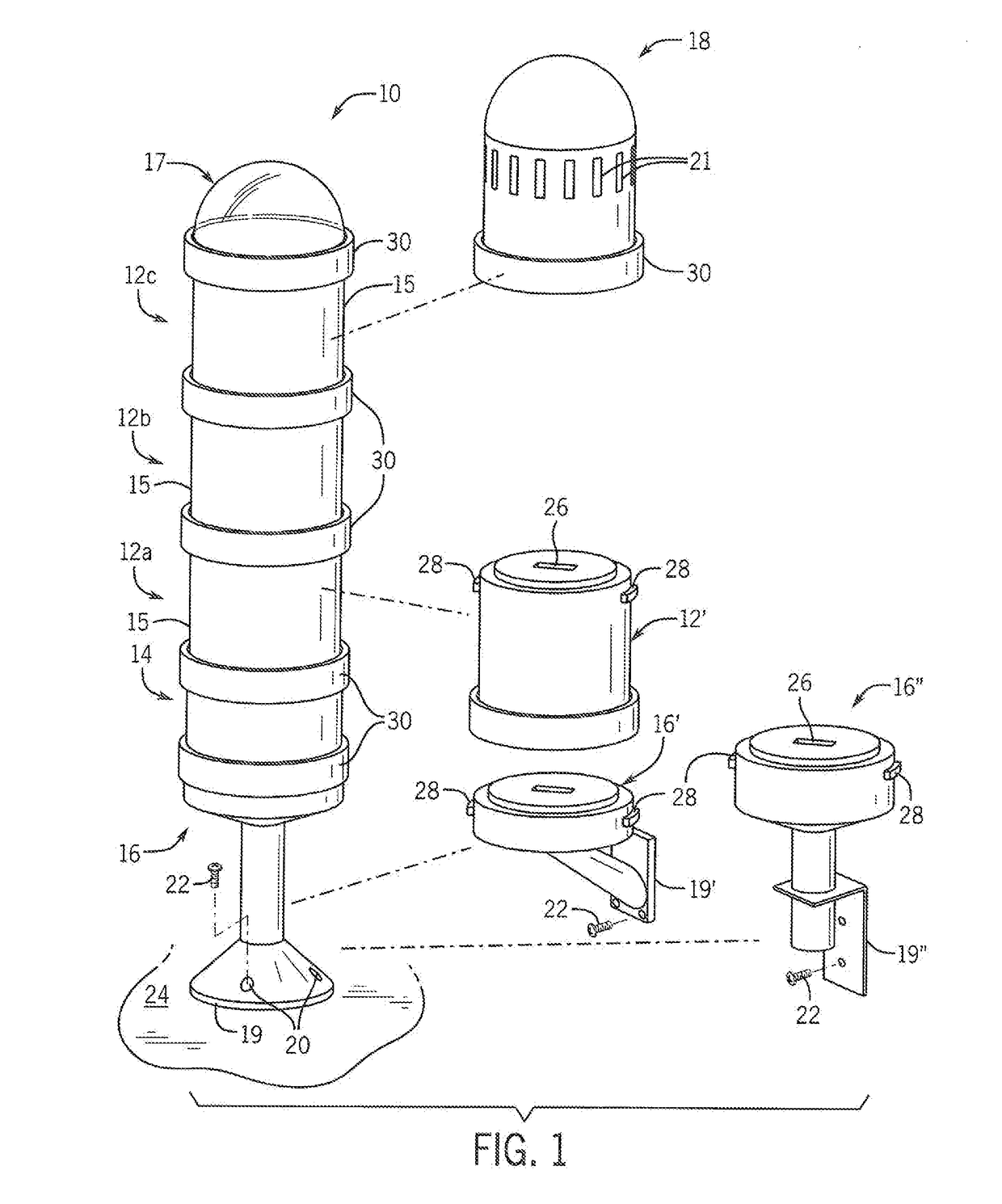
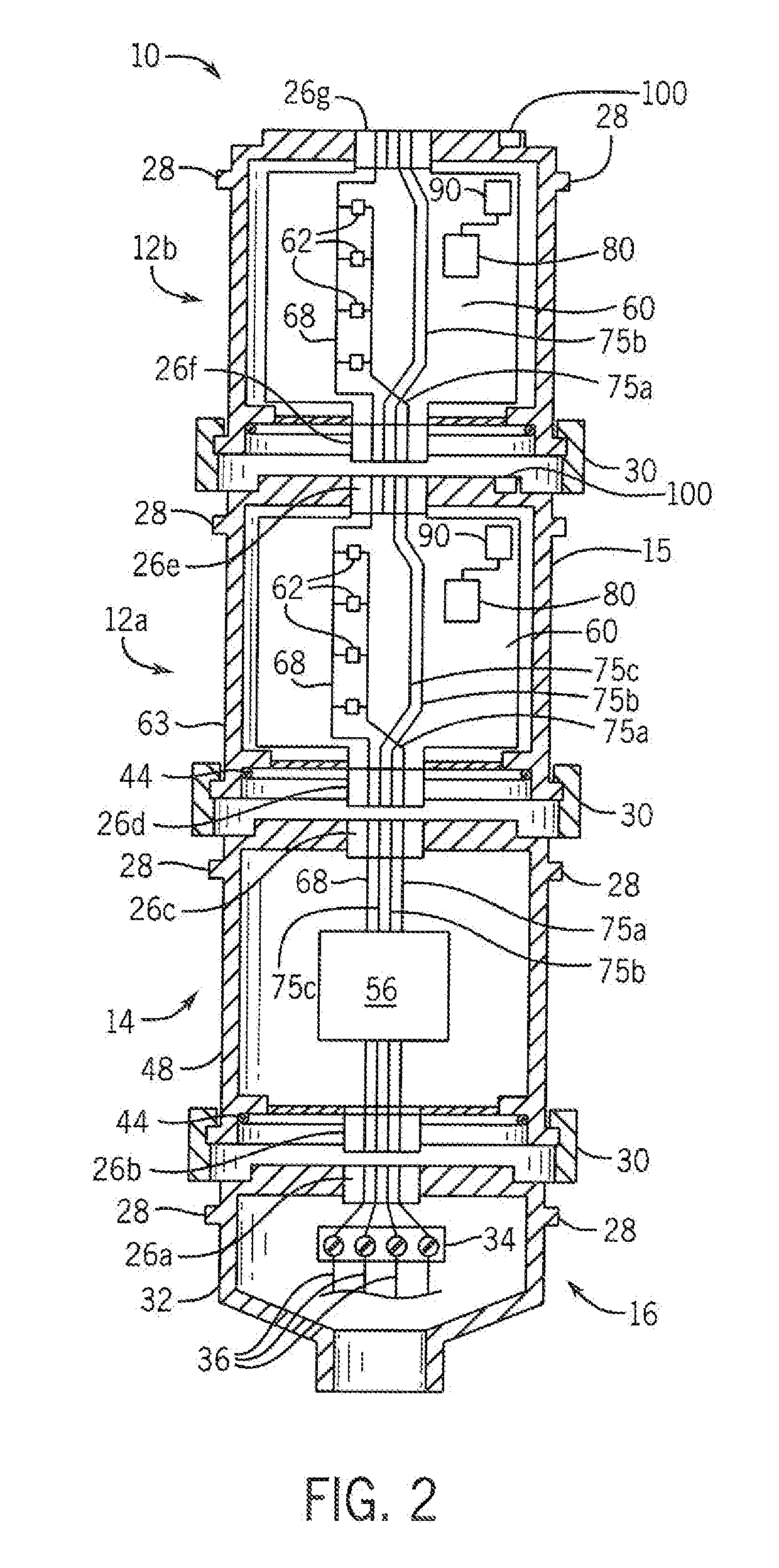
ActiveUS20180299370A1Side-by-side/stacked arrangementsPrinted circuit aspectsComputer moduleStack light
A system to verify the identity of modules within a stack light is disclosed. A sensor is mounted to a circuit board inserted within a housing of the module, and a target is mounted to or integrally formed in the housing. The sensor detects and generates a signal corresponding to the detected target. Different targets or locations for the target are provided for each housing. The module, a base for the stack light, or a remote controller in communication with the stack light identifies the housing in which the circuit board is mounted based on the feedback signal generated by detecting the target. At power-up, a routine may initiate a verification routine by which each module in the stack light determines the type of housing in which the circuit board for that module is located.
Owner:ROCKWELL AUTOMATION TECH
Hotspot sharing method based on artificial intelligence and feature analysis and big data cloud platform
ActiveCN112437439AEnsure safetyAvoid slowing downAssess restrictionSecurity arrangementEngineeringInformation security
The invention relates to a hotspot sharing method based on artificial intelligence and feature analysis and a big data cloud platform, and aims to identify an access intrusion detection result of a target terminal before the target terminal is accessed to a hotspot network corresponding to a current hotspot sharing terminal, thereby ensuring information security relative to the current hotspot sharing terminal. In this way, the target terminal can pass the access verification before using the hotspot network corresponding to the current hotspot sharing terminal. The access intrusion detectionresult is determined based on the information security evaluation characteristics, and the access intrusion detection result can be identified for different information communication networks where different hotspot sharing requests are located, so that access verification can be accurately and reliably realized. Moreover, the access verification is carried out on the big data cloud platform side,so that a corresponding verification program does not need to be deployed in the current hotspot sharing terminal, and the operation rate of the current hotspot sharing terminal can be prevented frombeing severely slowed down.
Owner:中科星云物连科技(北京)有限公司
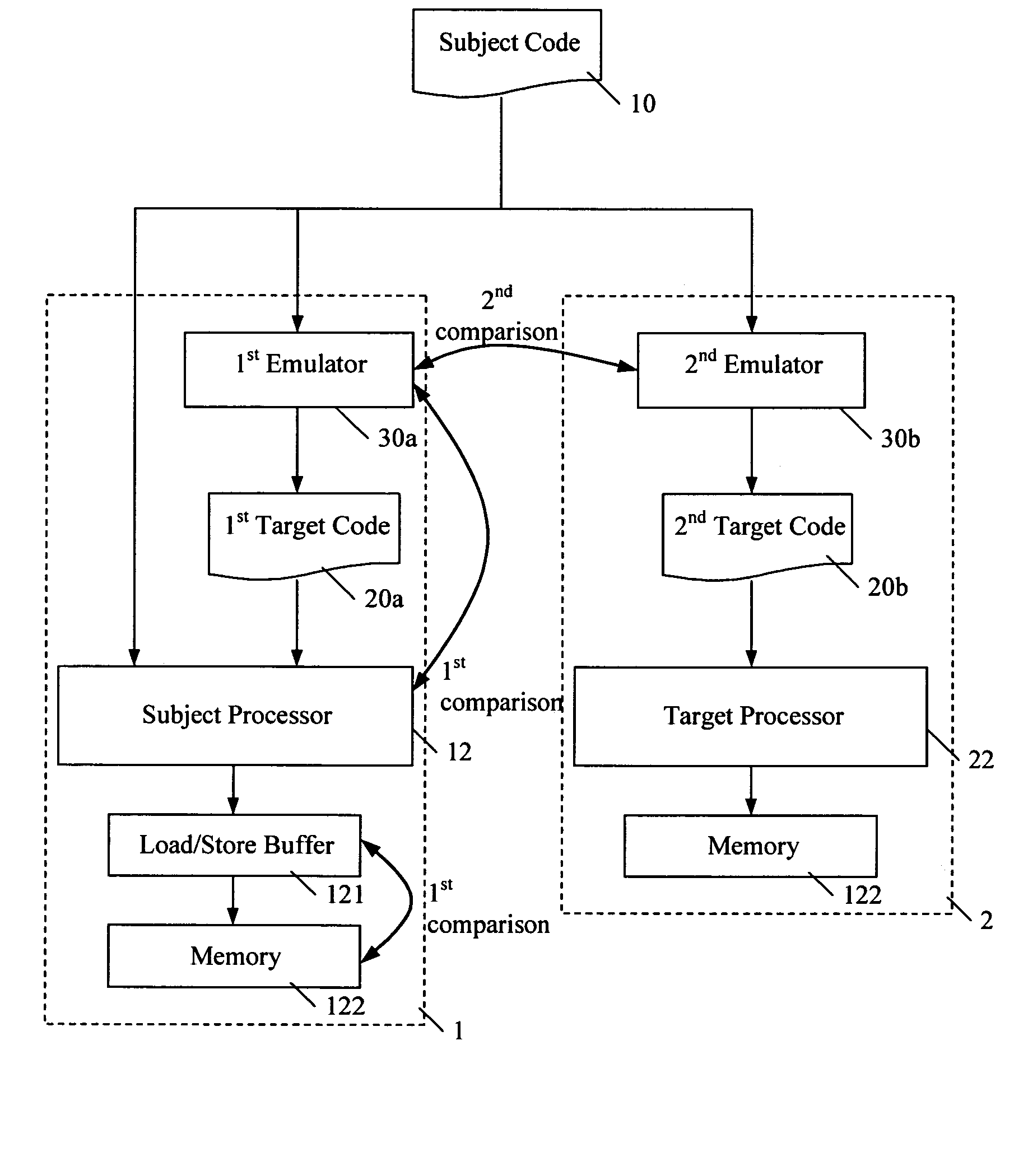
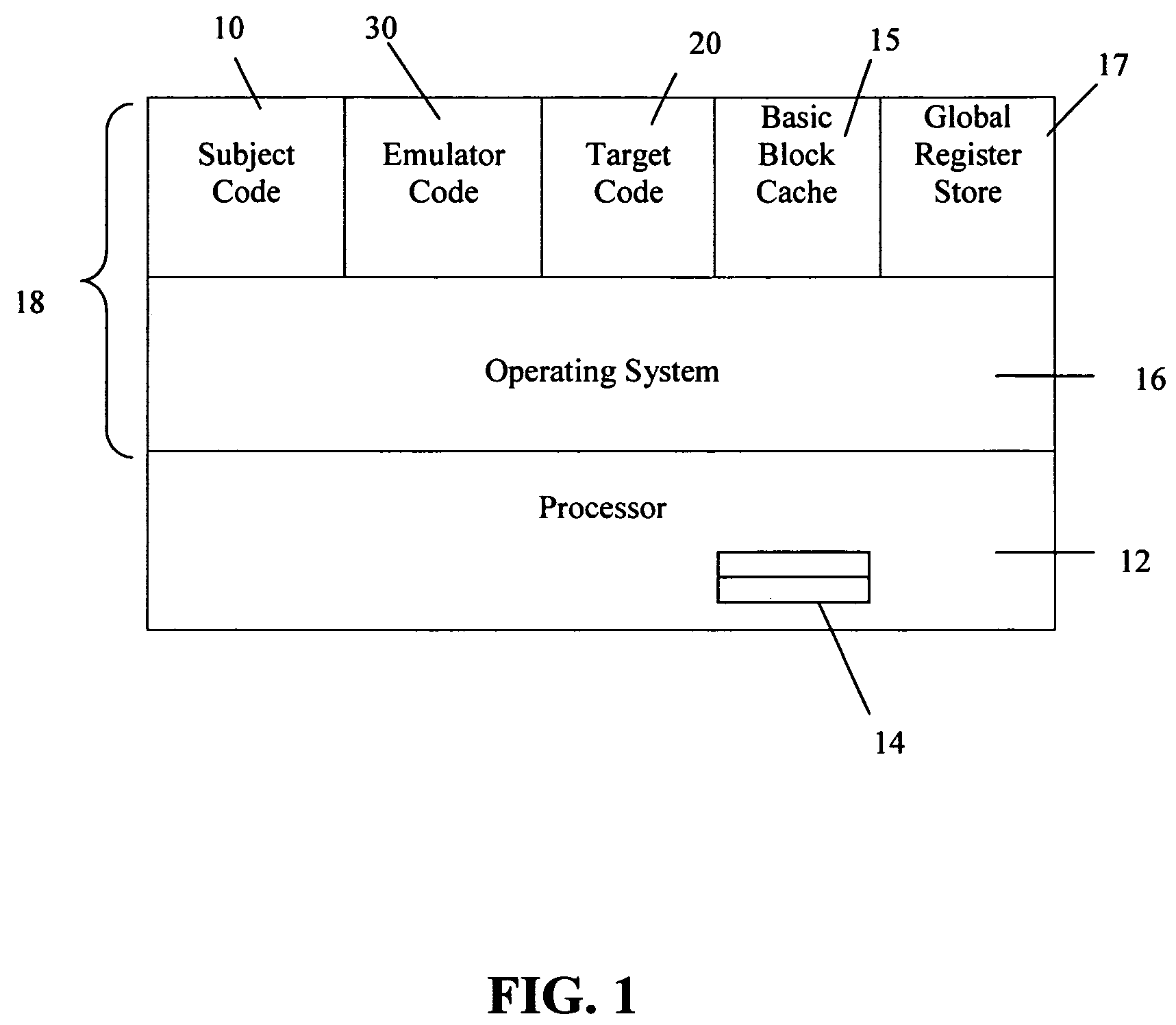
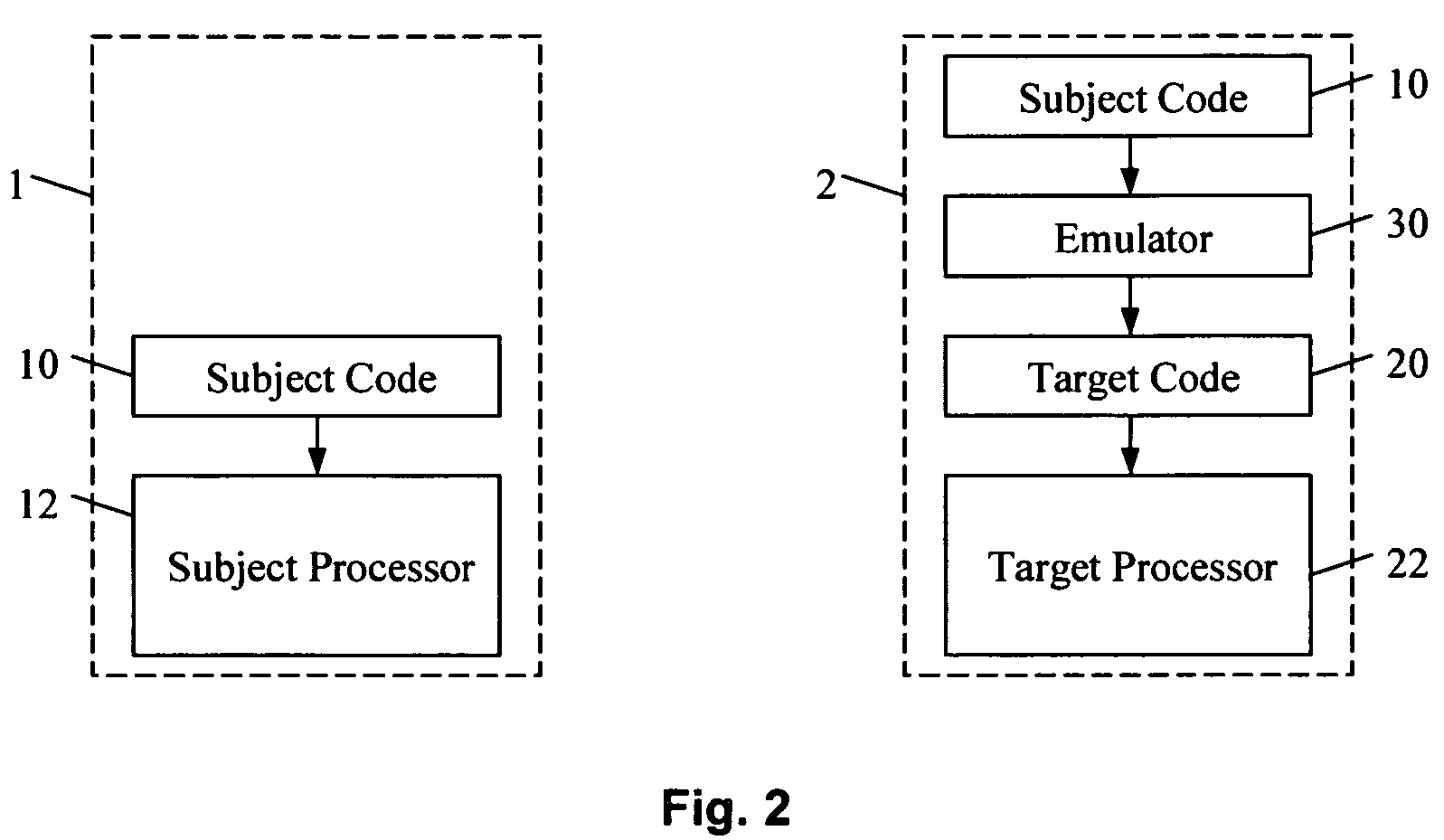
Method and apparatus for performing incremental validation of program code conversion
ActiveUS7793270B2Quick and efficientQuick and efficient and accurate and cost-effectiveSoftware testing/debuggingProgram loading/initiatingProgram codeProgramming language
A method and apparatus for verifying program code conversion performed by an emulator. A first emulator configured in a same-to-same (X-X) mode converts subject code into target code for execution by a subject processor. Execution of the subject code natively by the subject processor is compared against execution through the first emulator, to verify that program code conversion. Optionally, the first emulator is then used to incrementally validate program code conversion (i.e. optimisation and / or translation) performed by a second emulator, such as a this-to-that (X-Y) mode emulator running on a target processor.
Owner:IBM CORP
Trusted environment remote verification method, device, equipment, system and medium
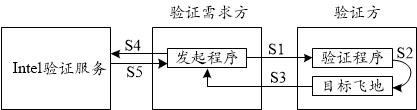
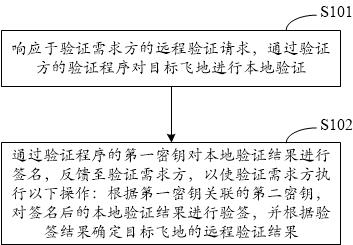
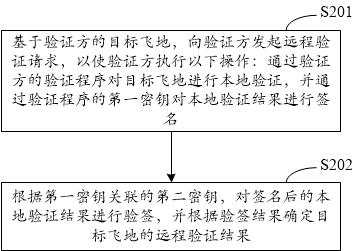
ActiveCN112231652AImprove remote authentication versatilityEasy to understandDigital data protectionInternal/peripheral component protectionCloud computingReliability engineering
The invention discloses a trusted environment remote verification method, device, equipment, system and medium, relates to the technical field of block chains, and can be used for cloud computing or cloud service. The method comprises steps: in response to a remote verification request of a verification demander, performing local verification on a target enclave through a verification program of averification party; signing a local verification result through a first secret key of a verification program, and feeding back to the verification demander, so that the verification demander executesthe following operations: verifying the signed local verification result according to a second secret key associated with the first secret key, and determining a remote verification result of the target enclave according to a signature verification result. The invention provides a novel trusted environment remote verification method, and the universality of remote verification is improved.
Owner:BAIDU ONLINE NETWORK TECH (BEIJIBG) CO LTD
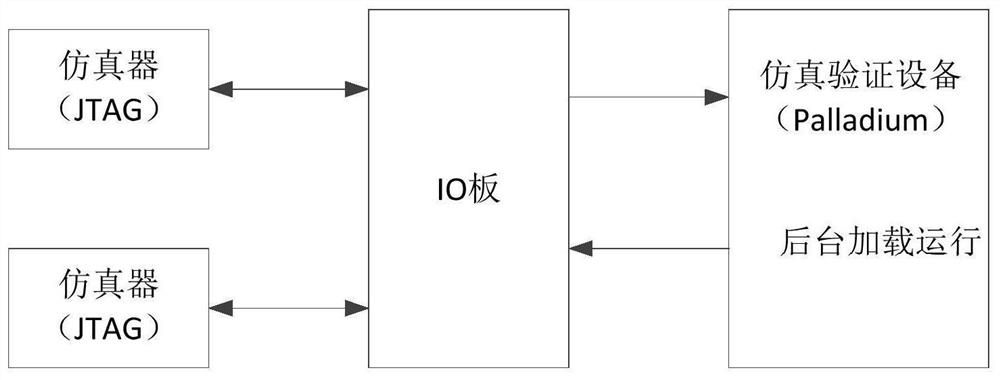
SOC (system on chip) simulation verification method and device, verification server and storage medium
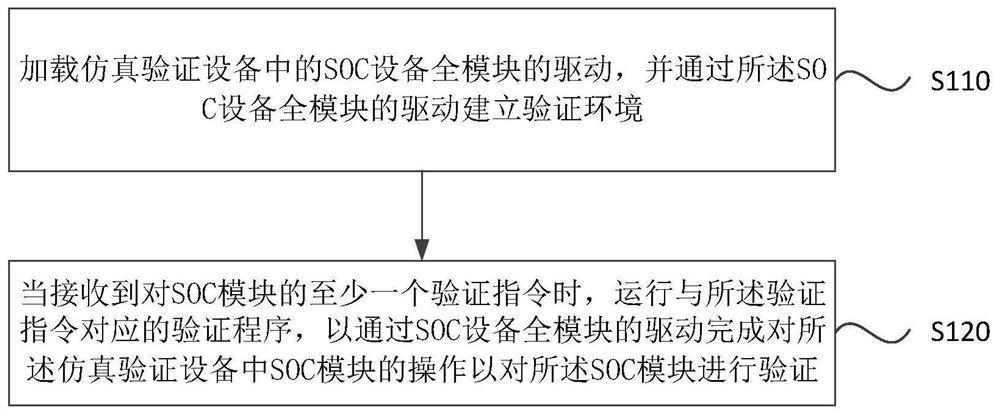
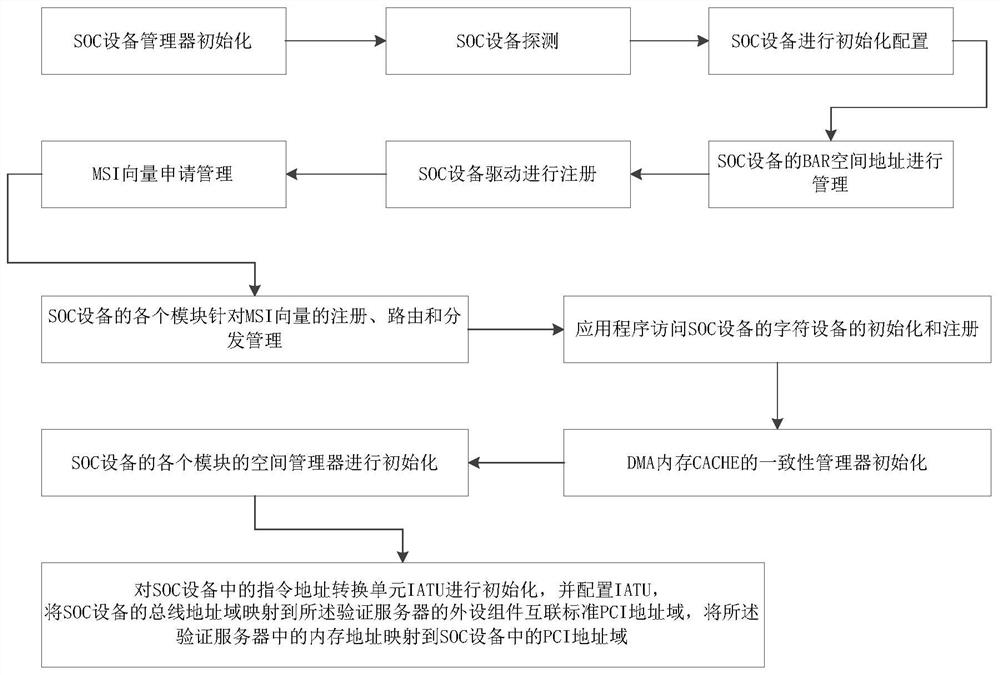
PendingCN113657069AReduce workloadReduce labor intensityCAD circuit designSpecial data processing applicationsVia deviceVerification
The embodiment of the invention provides a system-on-chip (SOC) simulation verification method and device, a verification server and a storage medium, the method is applied to the verification server, an operating system is installed in the verification server, and the method comprises the following steps: loading a driver of a whole module of SOC equipment in simulation verification equipment, establishing a verification environment through the driving of the whole module of the SOC equipment; and when at least one verification instruction for the SOC module is received, running a verification program corresponding to the verification instruction, so as to complete the operation of the SOC module in the simulation verification equipment through the driving of the whole module of the SOC equipment to verify the SOC module. According to the technical scheme provided by the embodiment of the invention, the verification efficiency can be improved, the verification program loading time can be shortened, multi-user parallel verification can be supported, and system-level combined verification can be supported.
Owner:KYLAND TECH CO LTD
Method of verifying integrity of program using hash
ActiveUS20160239364A1Minimize time gapImprove validityFault responseSoftware testing/debuggingProgramming languageAlgorithm
In a method for verifying the integrity of first to Nth binaries (N is a natural number greater than or equal to 2), the method may comprise: loading the first to Nth binaries into a main memory in order to execute the binaries; verifying a self hash to verify, by the Kth binary (K=1, . . . , N-1) which has been loaded into the main memory, the integrity thereof by using a hash; and verifying a link hash by setting any one of the first to Kth binaries as a verification binary and setting a (K+1)th binary to be loaded into the main memory as a binary to be verified so that the verification binary verifies the integrity of the binary to be verified by using a hash.
Owner:INKA ENTWORKS INC
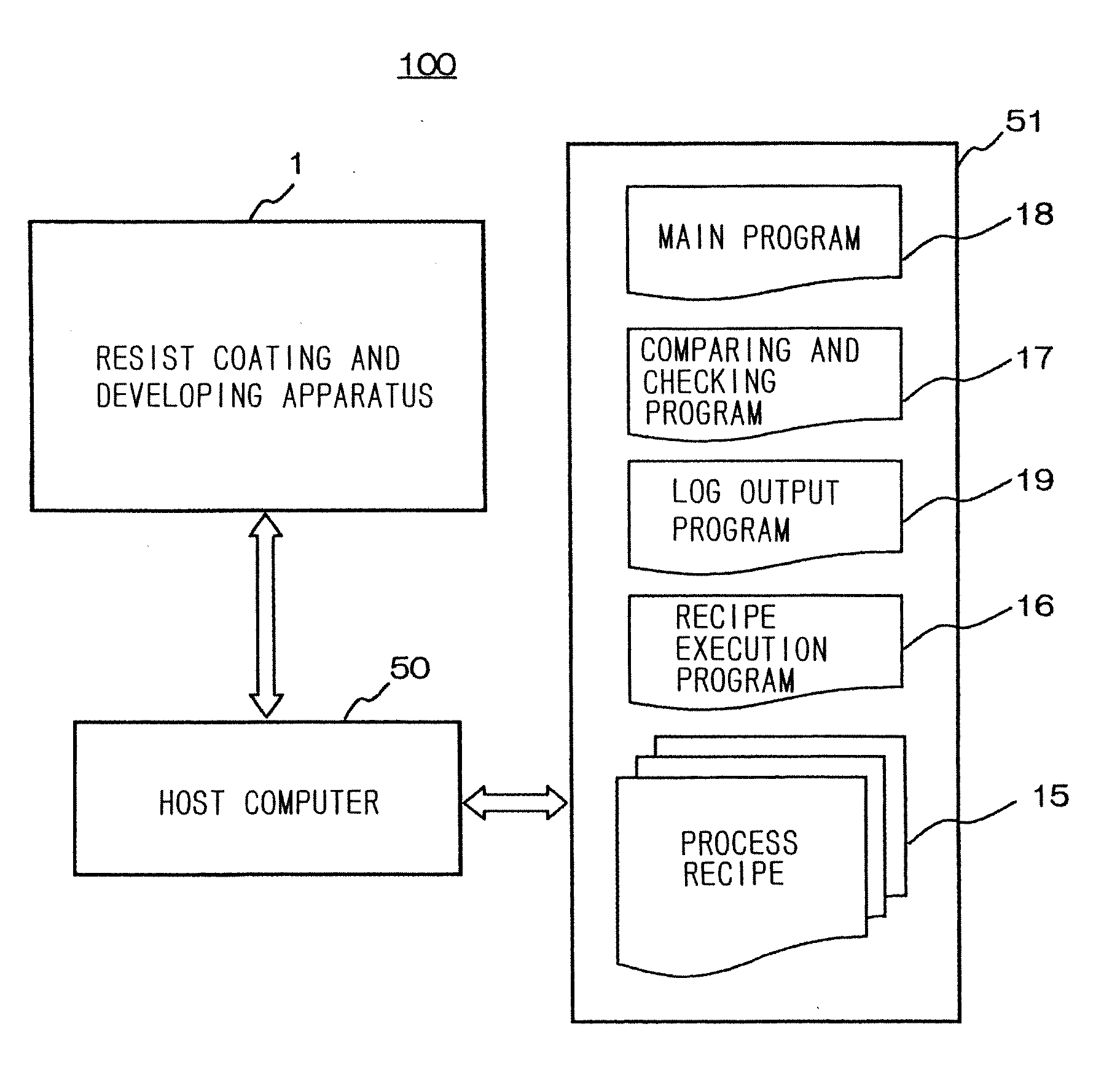
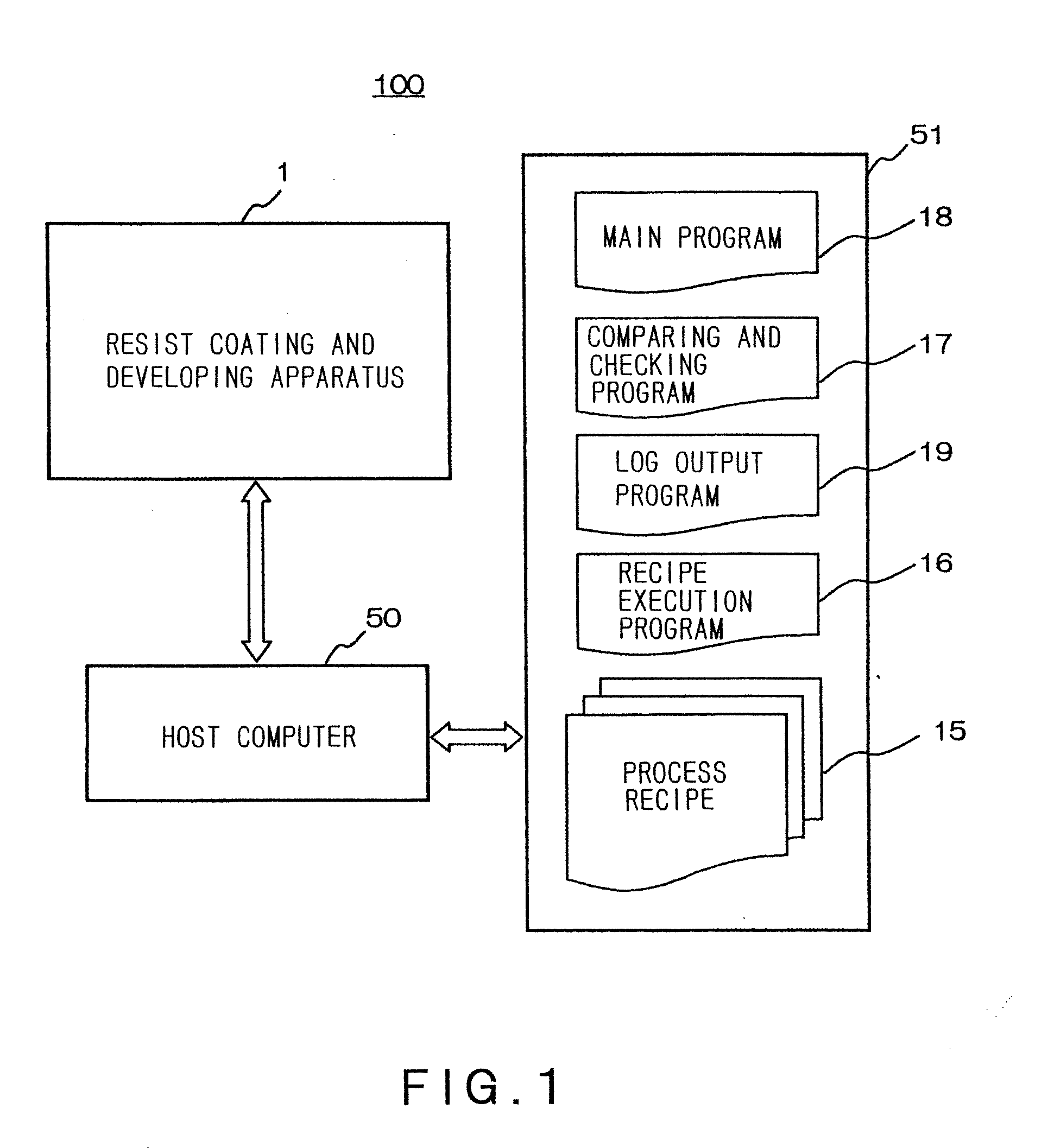
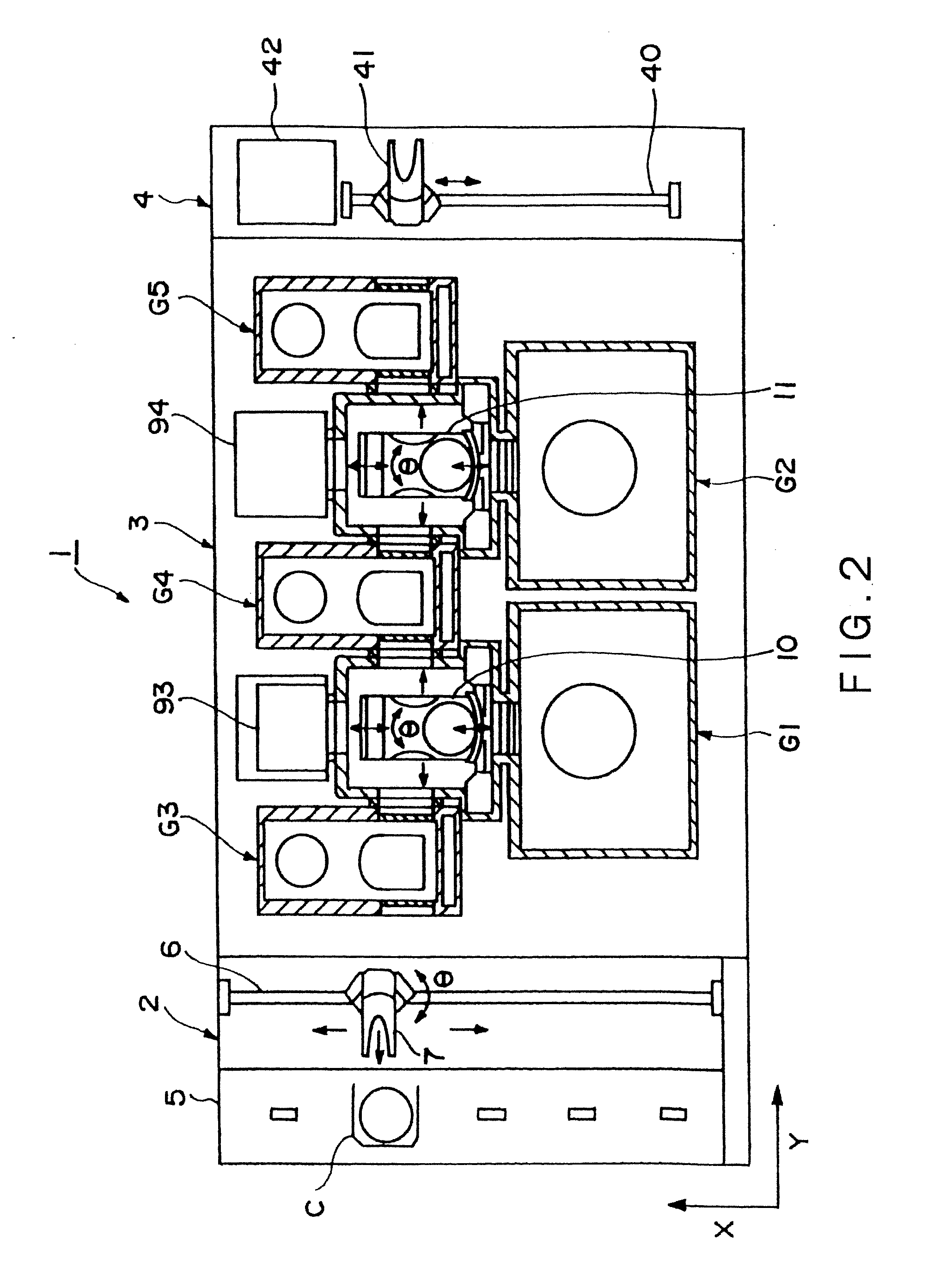
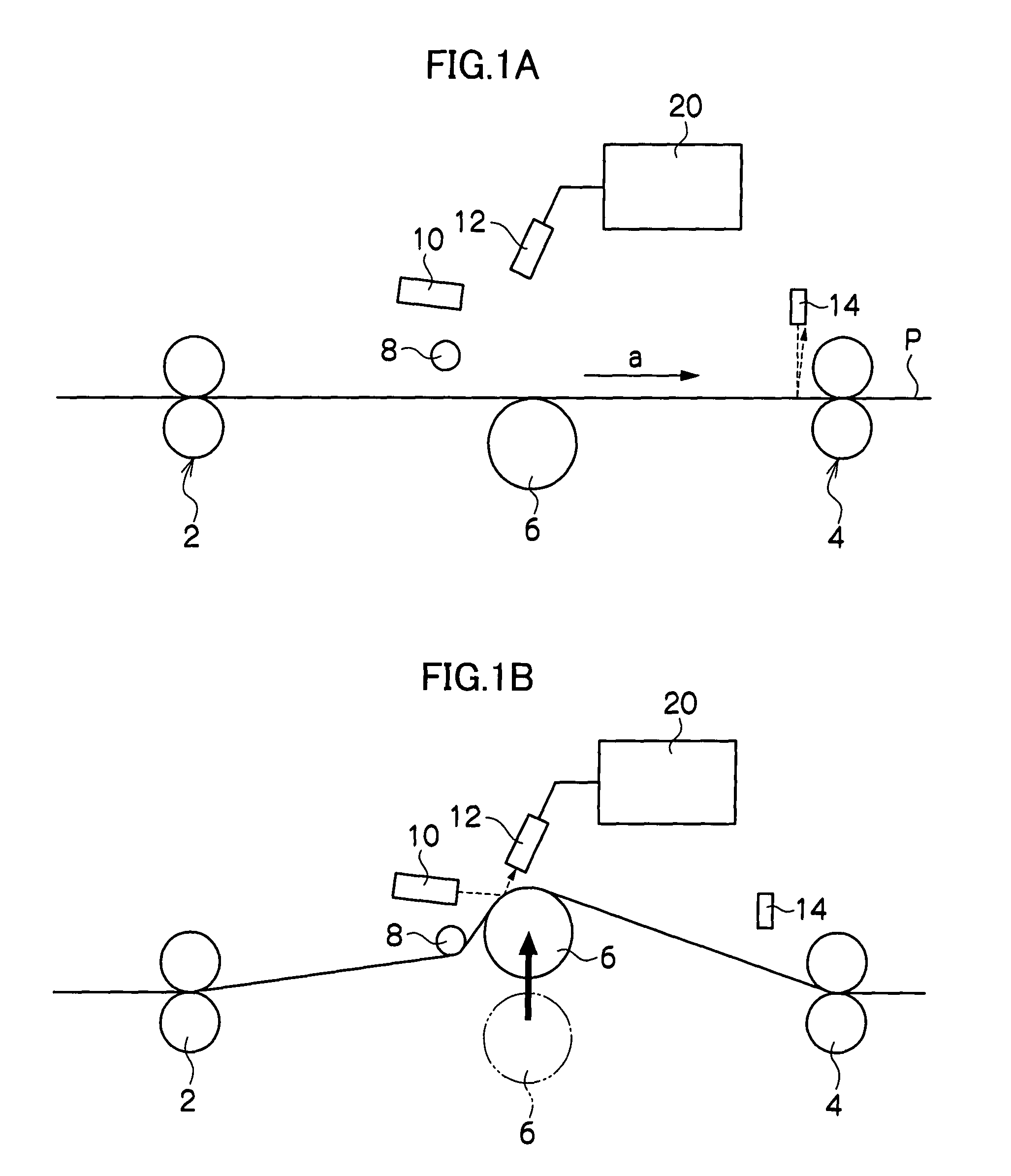
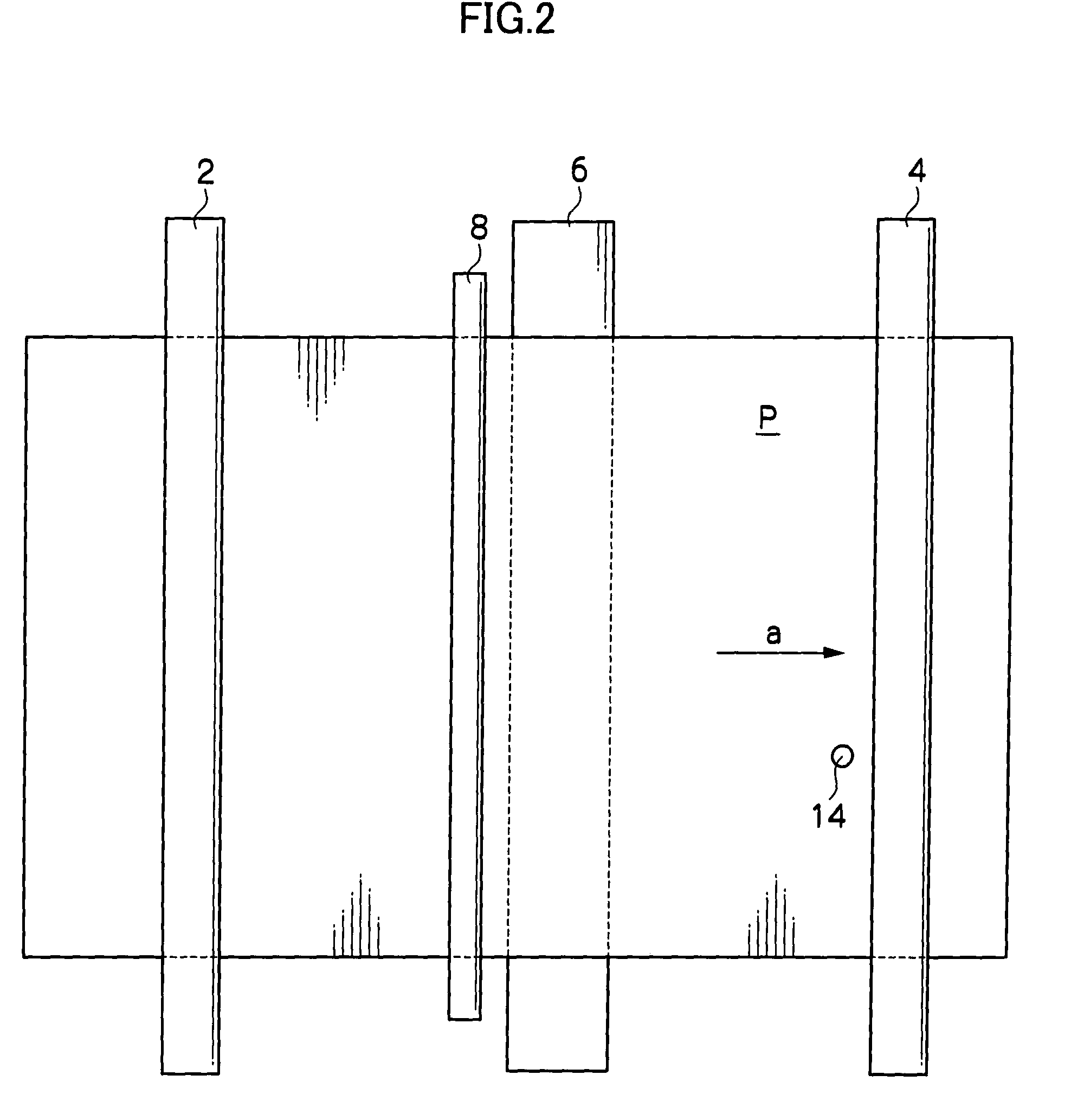
Substrate processing system, substrate processing method and computer-readable storage medium storing verification program
ActiveUS20070141730A1Completeness can be rapidlyImprove the quality of the finishProgramme controlPhotomechanical apparatusProgramming languageSoftware engineering
Disclosed is a method of verifying a recipe execution program. When a computer executes a recipe execution program, the computer sends instructions, which are issued based on a process recipe data defining specific operations to be performed by a substrate processing apparatus, to the substrate processing apparatus. When a computer executes a log output program, the computer outputs a log data indicating the instructions sent to the substrate processing apparatus. When a computer executes a comparing and checking program, the computer compares the log data which the process recipe data corresponding to the log data.
Owner:TOKYO ELECTRON LTD
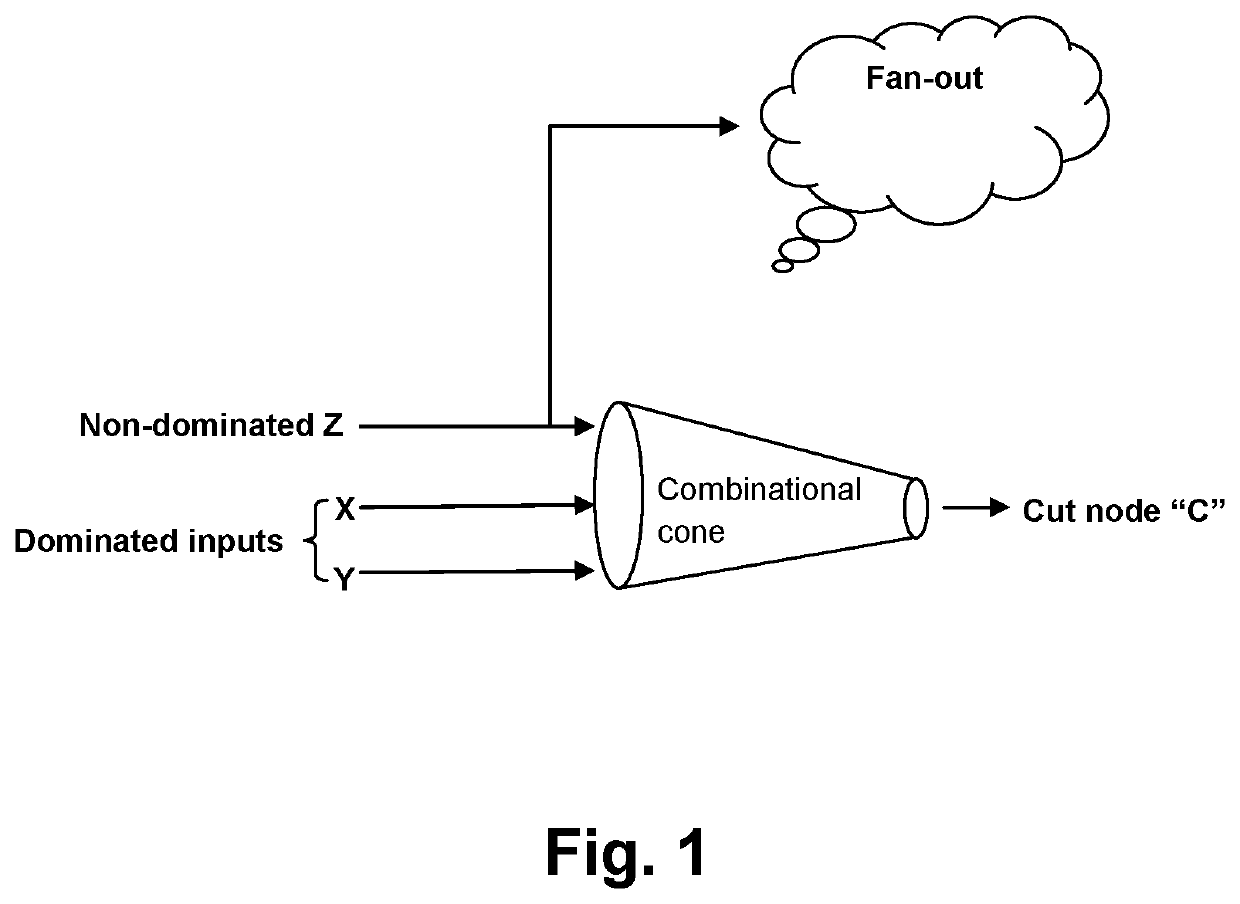
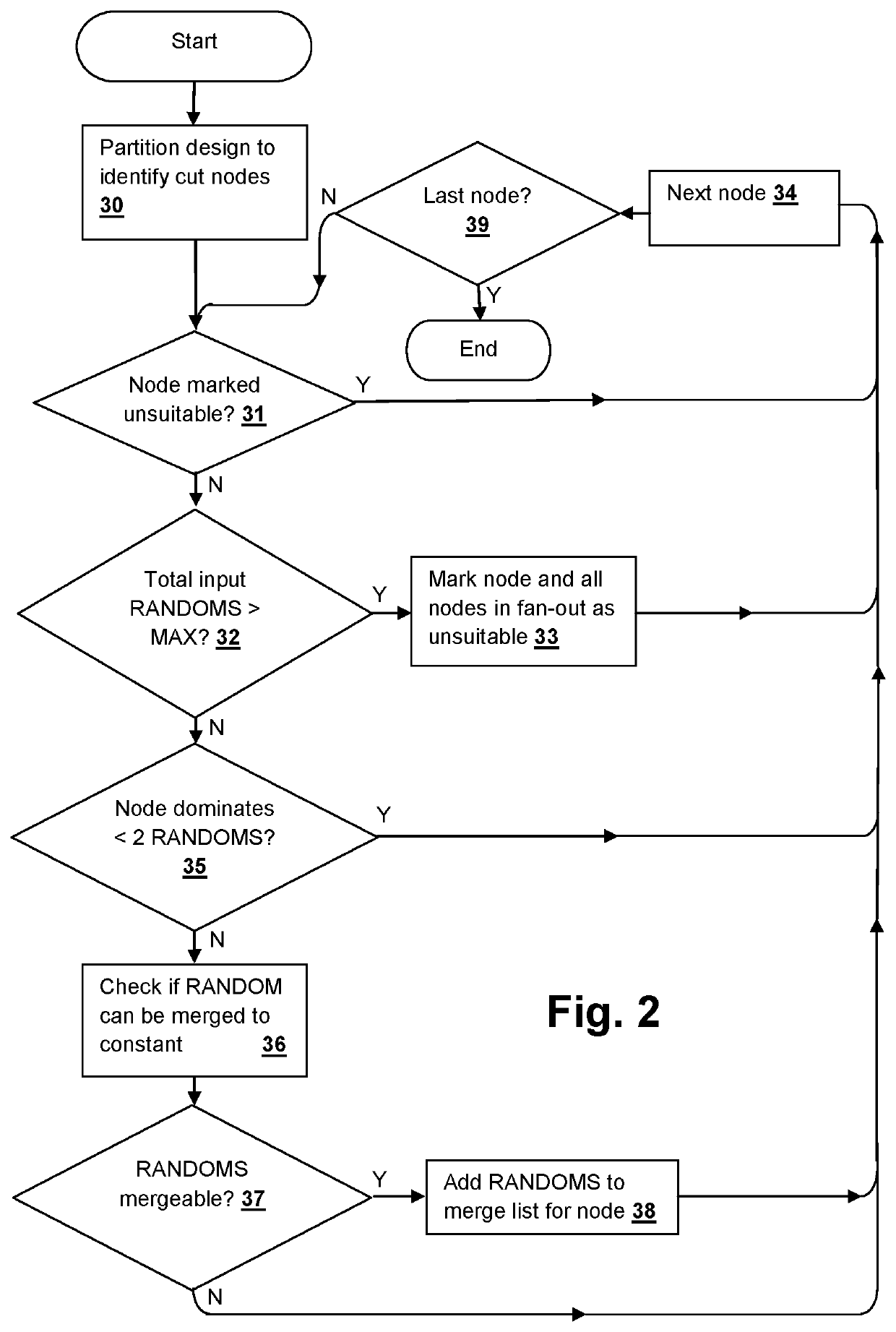
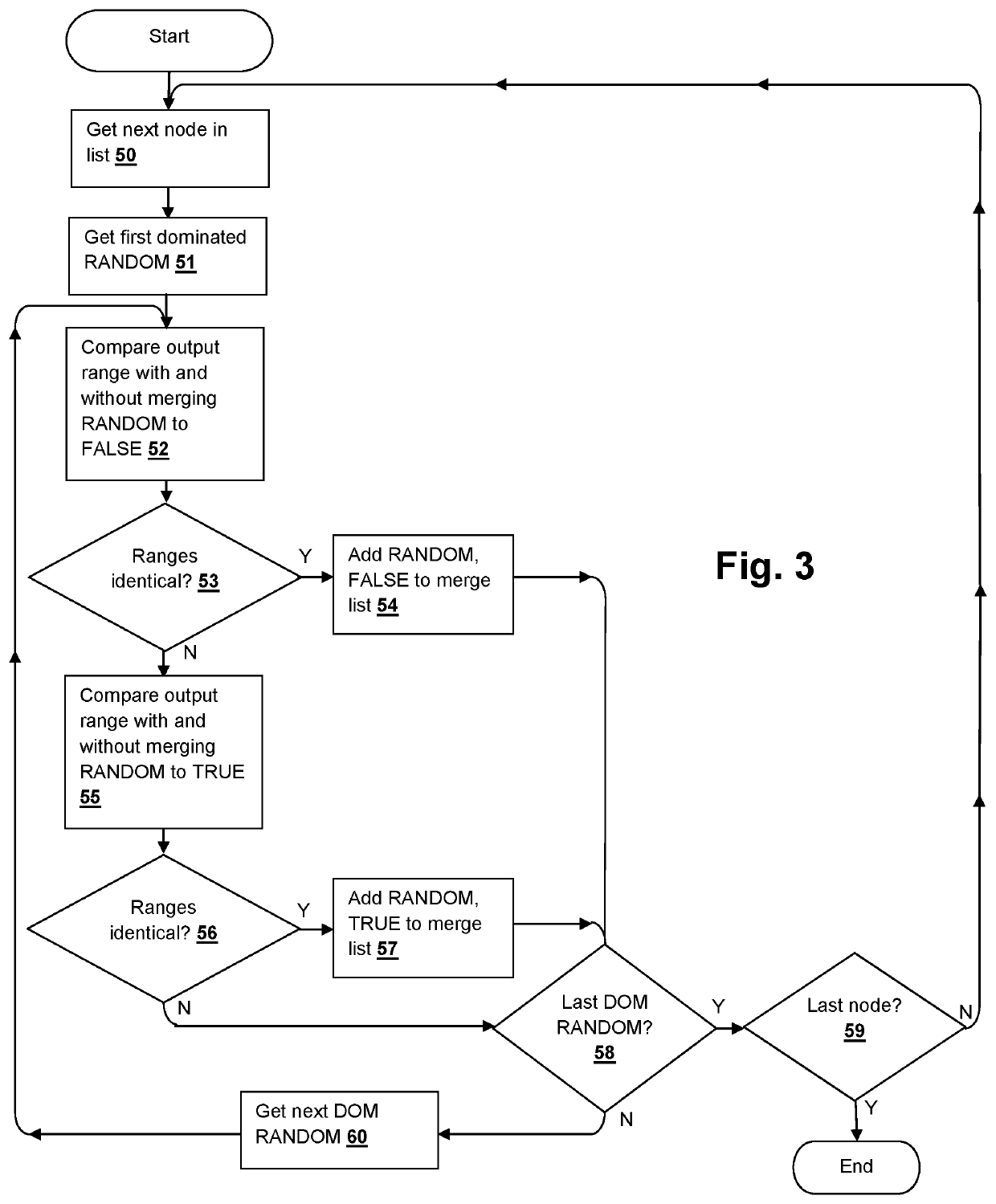
Verification complexity reduction via range-preserving input-to-constant conversion
A logic verification program, method and system provide an efficient behavior when verifying large logic designs. The logic is partitioned by cut-nodes that dominate two or more RANDOMS and a check is performed for a given cut-node to determine whether any of the dominated RANDOMS can be merged to a constant by performing satisfiability checks with each RANDOM merged to a constant, to determine whether a range of output values for the given cut-node has been reduced by merging the RANDOM. If the range is not reduced, the RANDOM can be added to the set of merge-able RANDOMS along with the corresponding constant value. If the range has been reduced, the opposite constant value is tried for a node and if the range is reduced for both constants, then the cut-node is abandoned for merging that dominated RANDOM and the next dominated RANDOM is tried.
Owner:IBM CORP
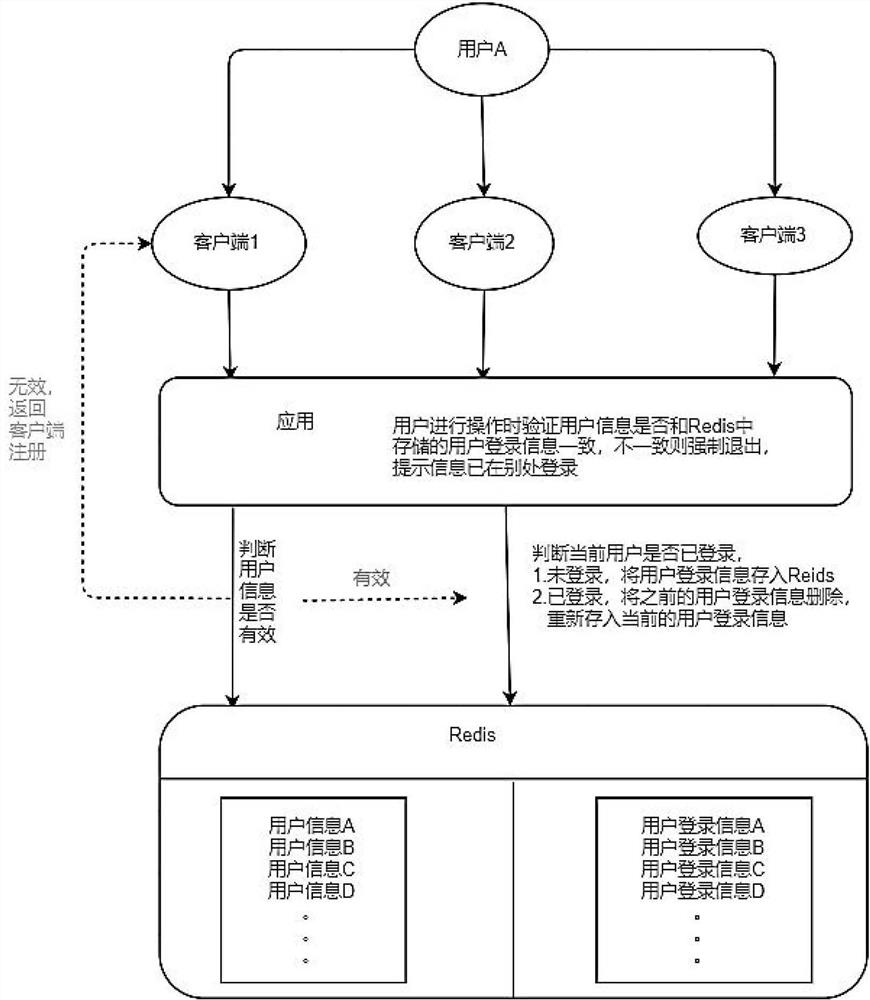
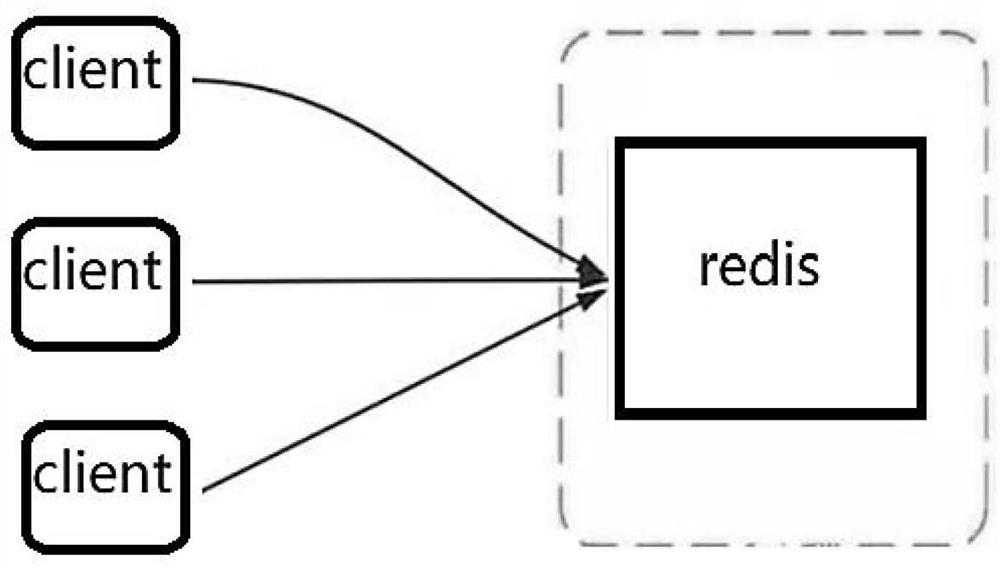
Method for preventing repeated login based on redis
InactiveCN112968862AAvoid repeated loginsAvoid insecurityDigital data authenticationTransmissionWeb siteEngineering
The invention relates to a method for preventing repeated login based on Redis cache, and the method comprises the following steps: taking a user ID of user information as a key of Redis, taking a token of user login information as a value, namely a key value after business processing, caching the token in the Redis, setting failure time, and only retaining the user login information of the last login when the same user logs in for multiple times; when a user accesses the same website on a plurality of devices or opens a plurality of windows on the same device to access different websites or the same website and runs a verification program, judging whether the user is in a legal login state or not by verifying whether current user login information is consistent with user login information in a cache or not; and preventing the repeated login.
Owner:南京联创数字科技有限公司
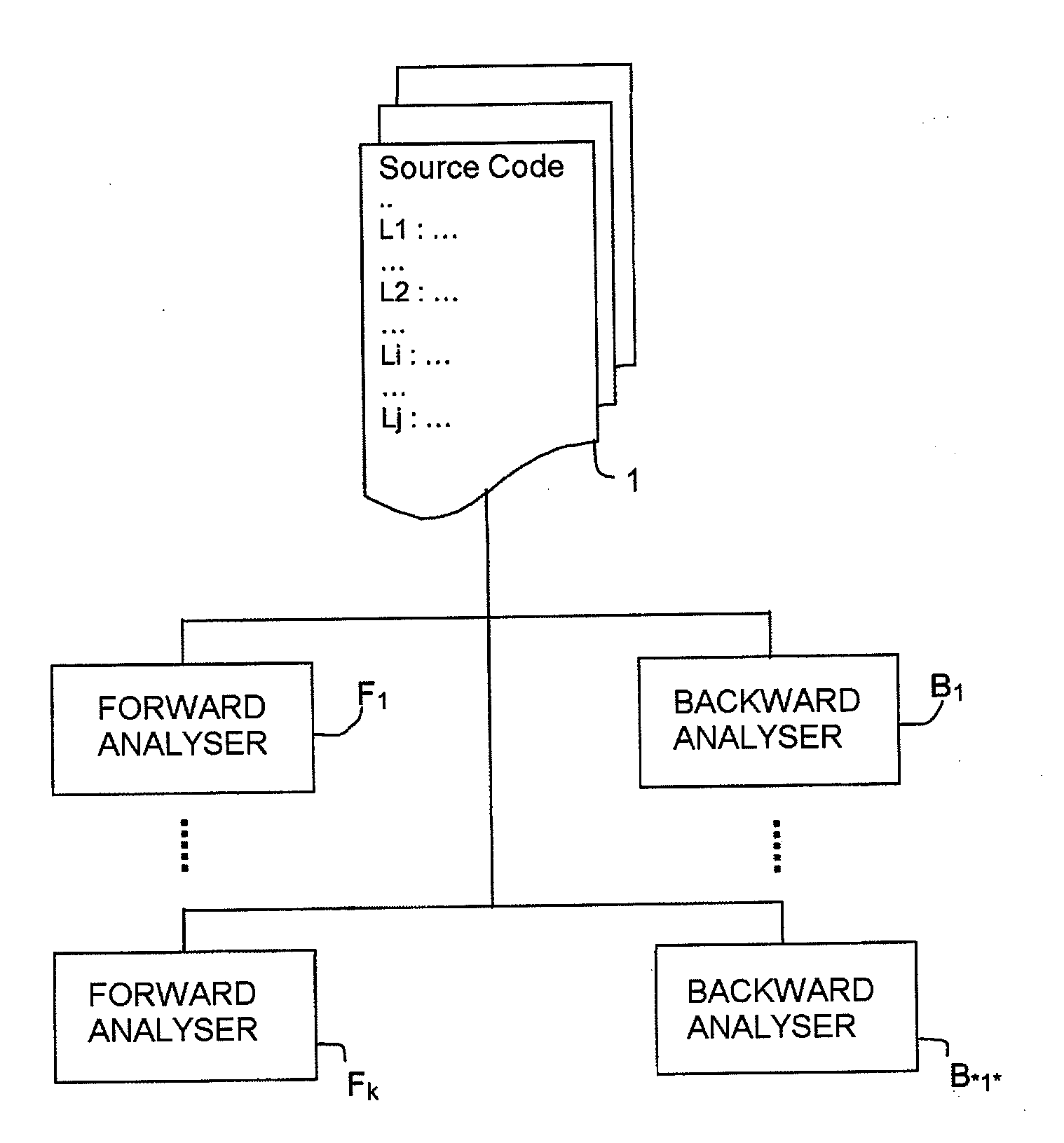
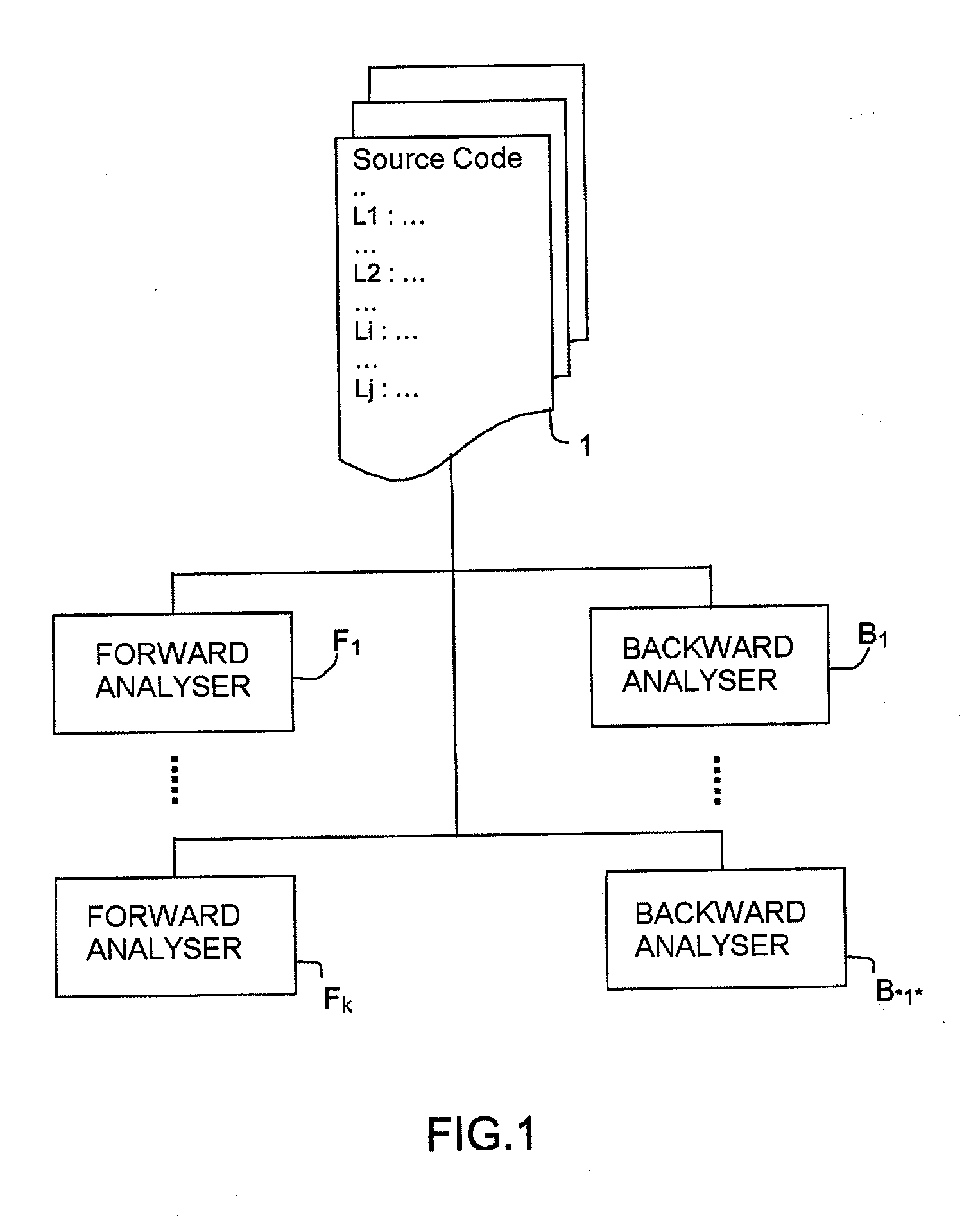
Method and System for Verifying Properties of a Computer Program
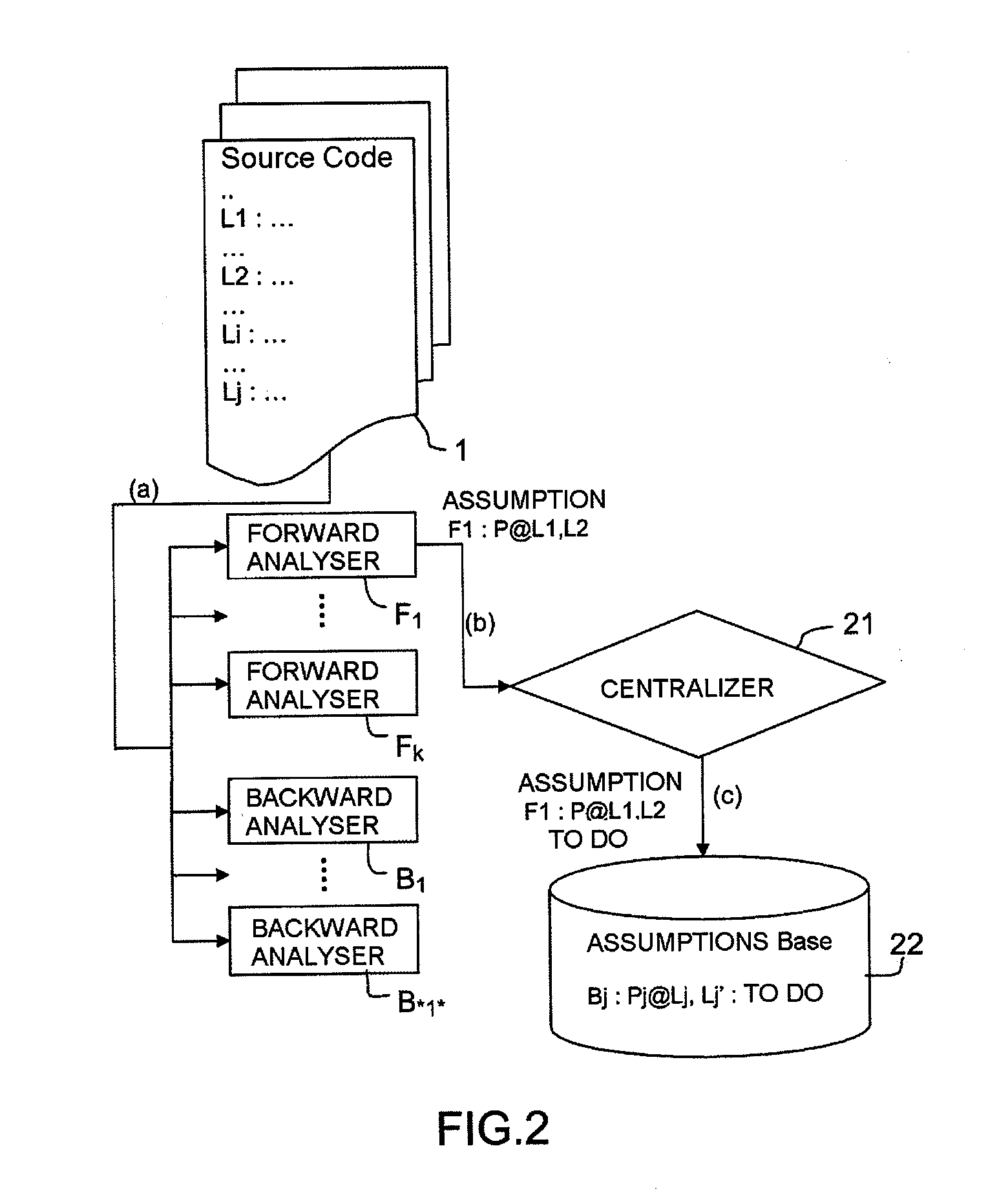
ActiveUS20100115493A1Error detection/correctionSpecific program execution arrangementsAnalyserTheoretical computer science
A method and a system for verifying properties of a computer program is provided, pertaining to the validity of properties at program points by means of at least one forward analyser and one backward analyser. For each property, in an issuing phase an analyser issues to a centralizer module an assumption on the validity of the property at a point of the program, the centralizer module storing the assumption in a database with an attribute indicating the original analyser and a status indicating that the assumption needs to be verified; in a phase of verifying the assumption, stored in the database, a test analyser is selected to analyse the assumption in cooperation with the other analysers, the centralizer module determining analysers able to cooperate. The verification phase is iterated until all assumptions stored in the base have been analysed by at least one test analyser, a verified assumption being marked as valid.
Owner:COMMISSARIAT A LENERGIE ATOMIQUE ET AUX ENERGIES ALTERNATIVES
Credit card verification enhancement system
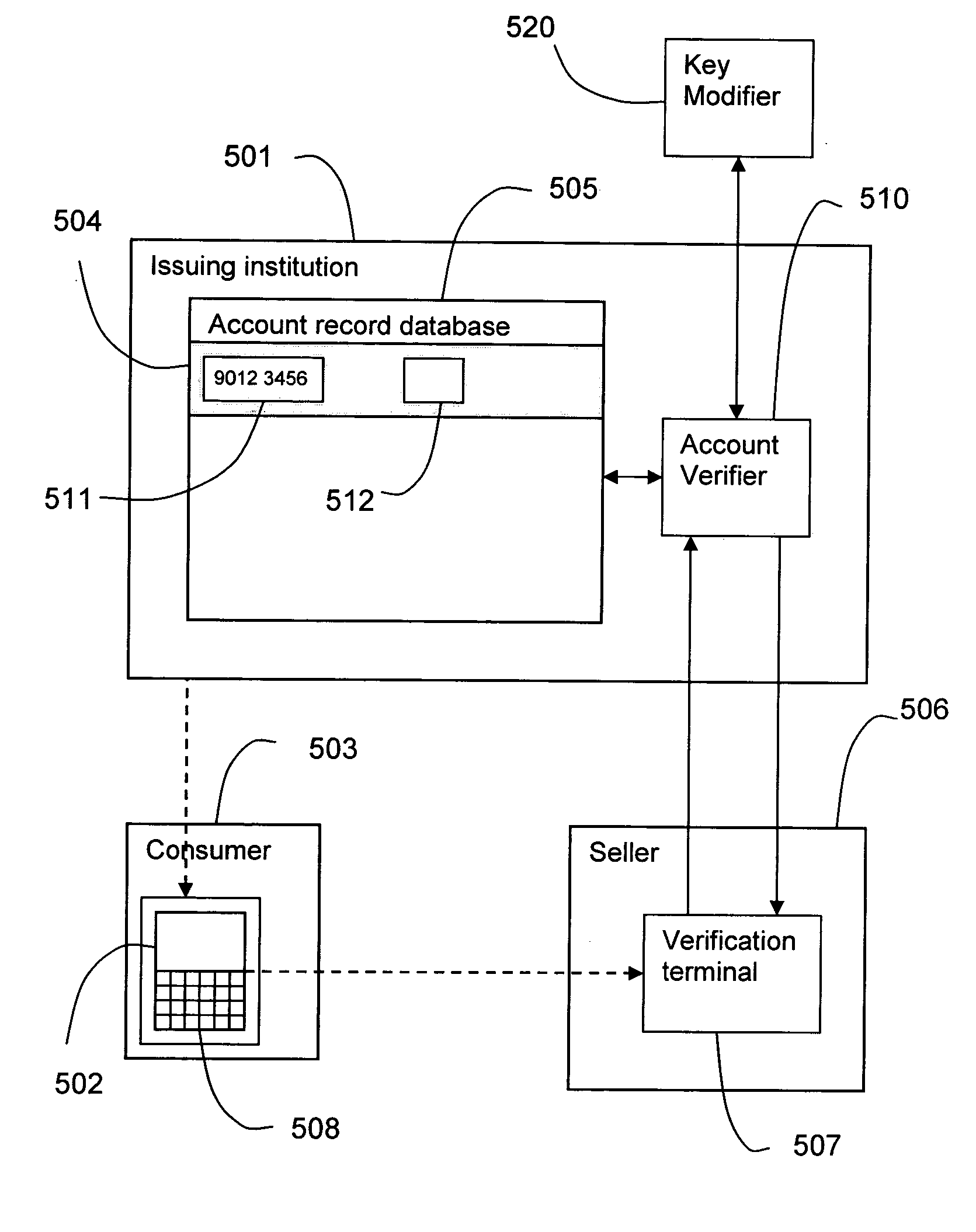
InactiveUS20070017972A1Enhance security and robustnessPrevent illegal useComplete banking machinesFinanceData validationPayment transaction
A method and system verifies the validity of a credit card payment transaction with a set of requester account data by searching an account record database for a matched record containing a record account number that matches the requester account number and an expected verification key that matches the requester verification key, said expected verification key changes after each successful payment transaction validation, according to a pre-determined list of values to enhance the security and robustness of account transactions. Also, the present invention provides a method and system that is cost-effective to implement and highly compatible with the current account verification procedure.
Owner:CHEN HAN PING
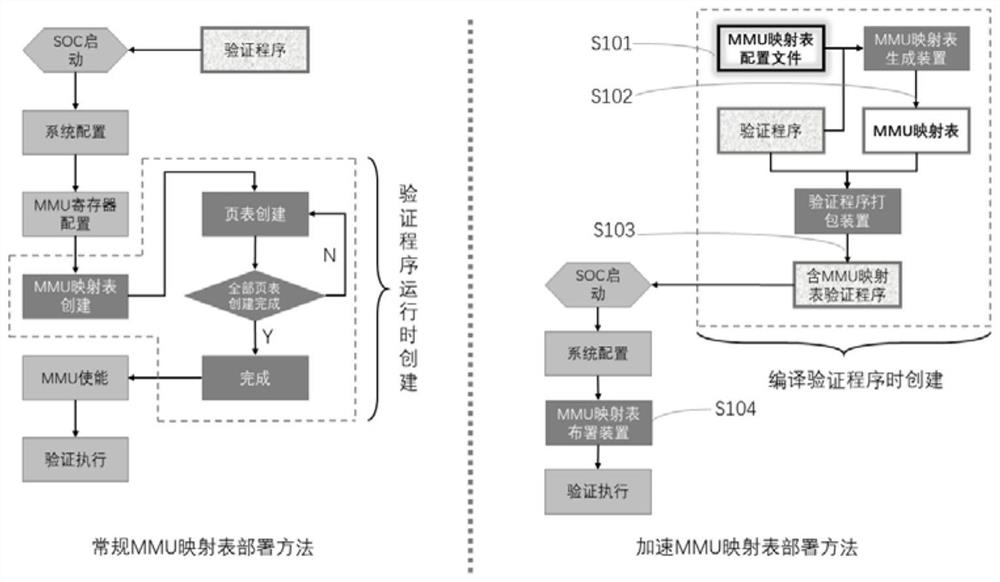
System and method for accelerating MMU mapping table deployment
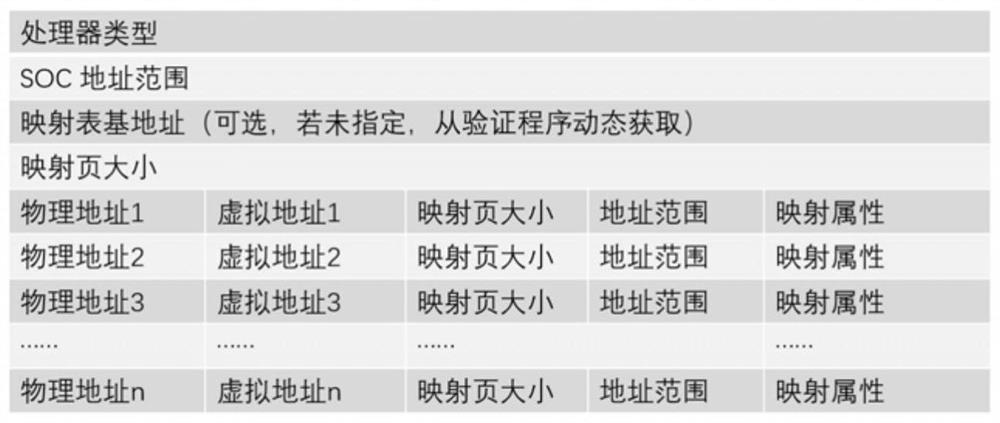
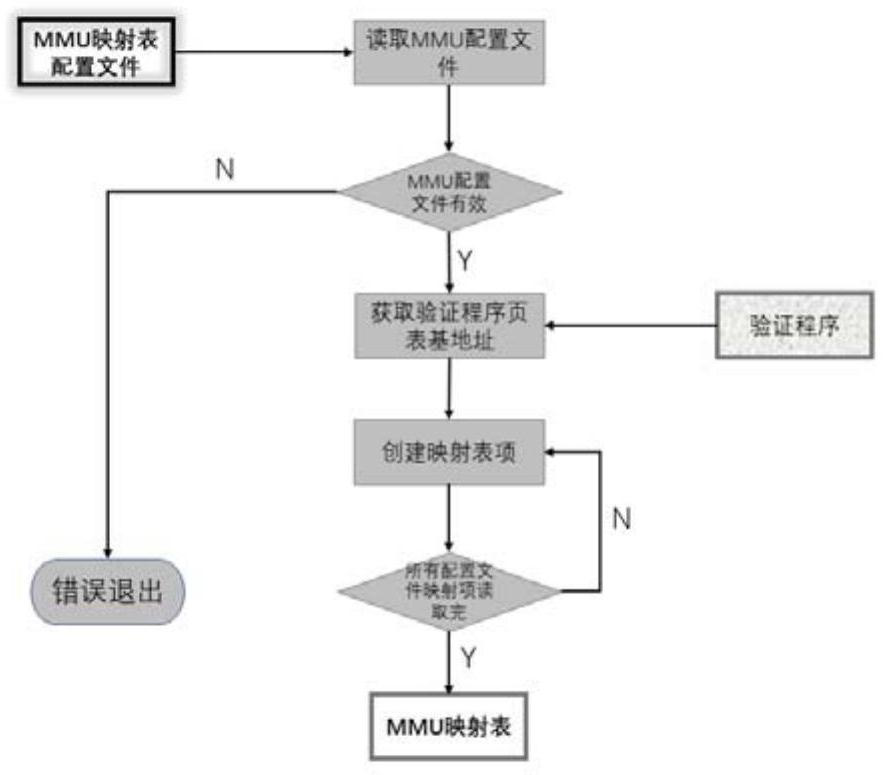
PendingCN114239448AReduce creation timeReduce the chance of misconfigurationCAD circuit designSpecial data processing applicationsProgramming languageParallel computing
The invention provides a system and a method for accelerating MMU mapping table deployment. The system comprises an MMU mapping table generation device and a verification program packaging device which run on a verification program compiling server, and an MMU mapping table deployment device which runs on a target SOC; the MMU mapping table generation device is used for reading, analyzing and legality checking an MMU mapping table configuration file, and generating an MMU mapping table adaptive to the target SOC according to the MMU mapping table configuration file; the verification program packaging device analyzes an original verification program generated by compiling, obtains an MMU mapping table address specified by the verification program and maximum size information of an MMU mapping table, checks validity of the size of the MMU mapping table adapted to a target SOC, and combines and packages the generated MMU mapping table adapted to the SOC and the verification program into a new verification program containing the MMU mapping table; and the MMU mapping table deployment device analyzes the MMU mapping table adapted to the target SOC, and completes deployment of the MMU mapping table on the target SOC.
Owner:SHANGHAI LINKCHIP SEMICON TECH CO LTD
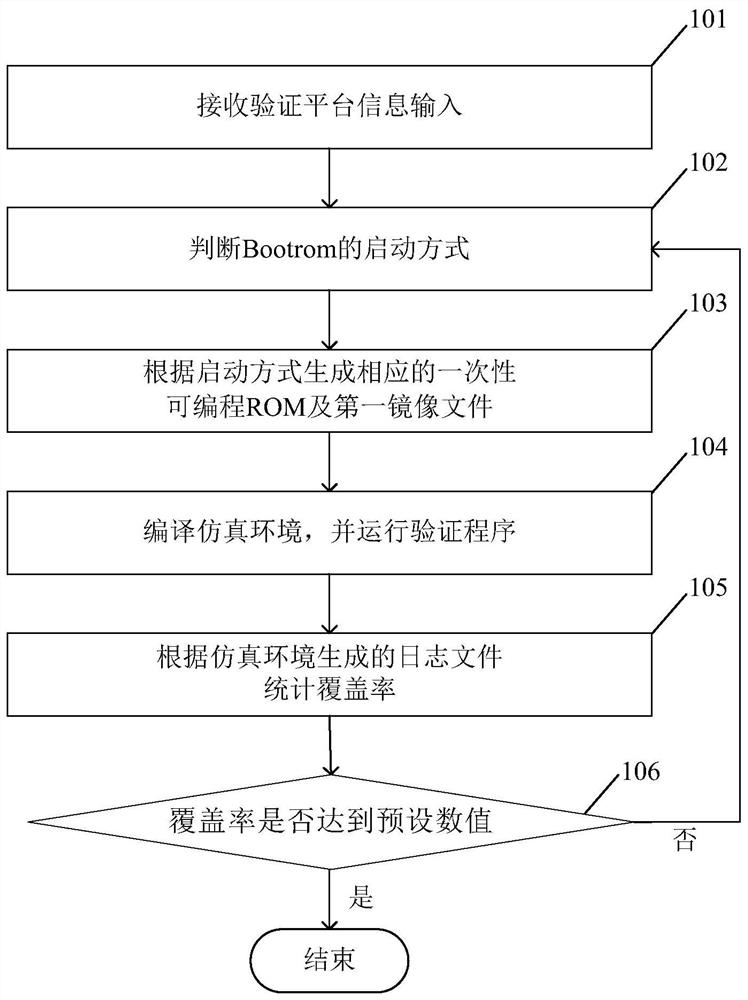
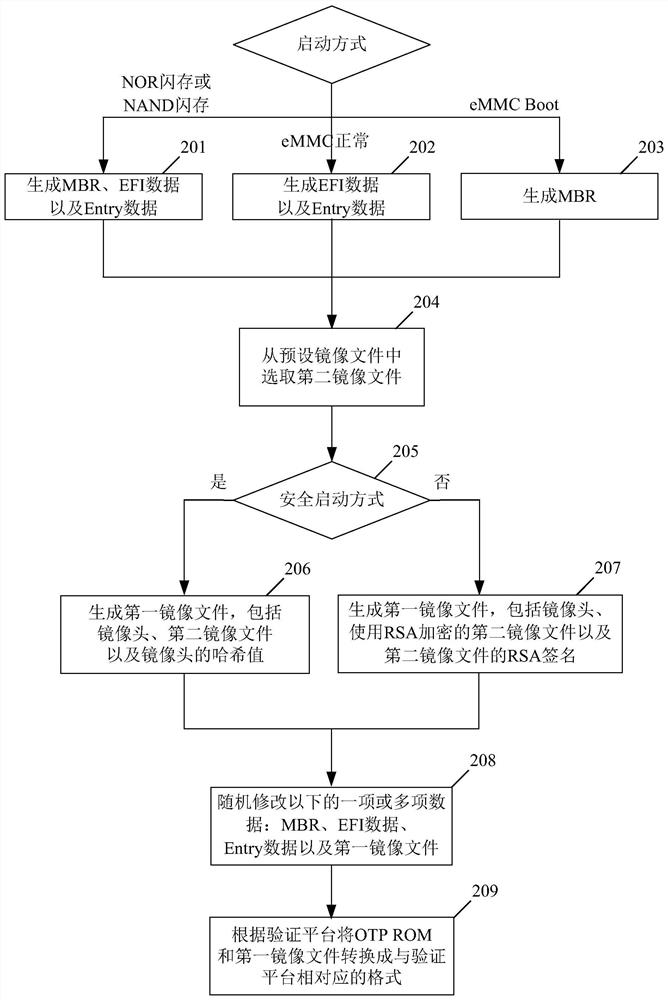
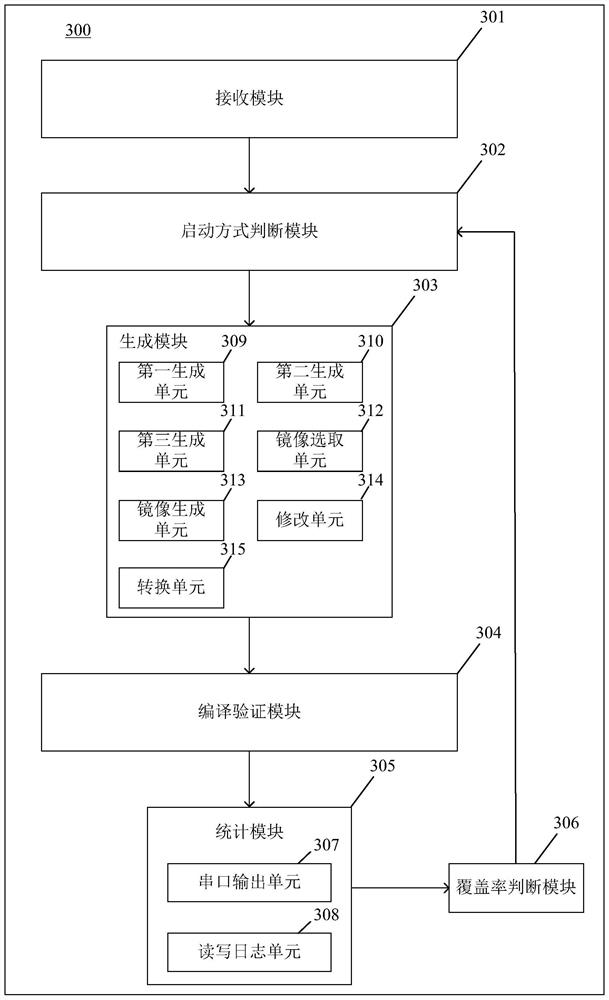
Multi-platform Bootrom verification method, device and system and computer readable medium
PendingCN111767231ASimplify the verification processImprove verification efficiencySoftware testing/debuggingComputer hardwareSoftware engineering
The invention provides a multi-platform Bootrom verification method, device, system and a computer readable medium. The method comprises the following steps of 1, receiving verification platform information input, 2, judging a starting mode of the Bootrom, 3, generating a corresponding one-time programmable ROM and a first mirror image file according to the starting mode, 4, compiling a simulationenvironment, and running a verification program, 5, generating a log file or counting the coverage rate according to the simulation environment, and 6, judging whether the coverage rate reaches a preset numerical value or not, if so, ending, and if not, returning to the step 2. According to the method, the corresponding verification files are automatically generated and verified according to different verification platforms and different starting modes, so that the multi-platform Bootrom automatic verification is realized, the multi-platform Bootrom verification process is simplified, and themulti-platform Bootrom verification efficiency is greatly improved.
Owner:JLQ TECH CO LTD
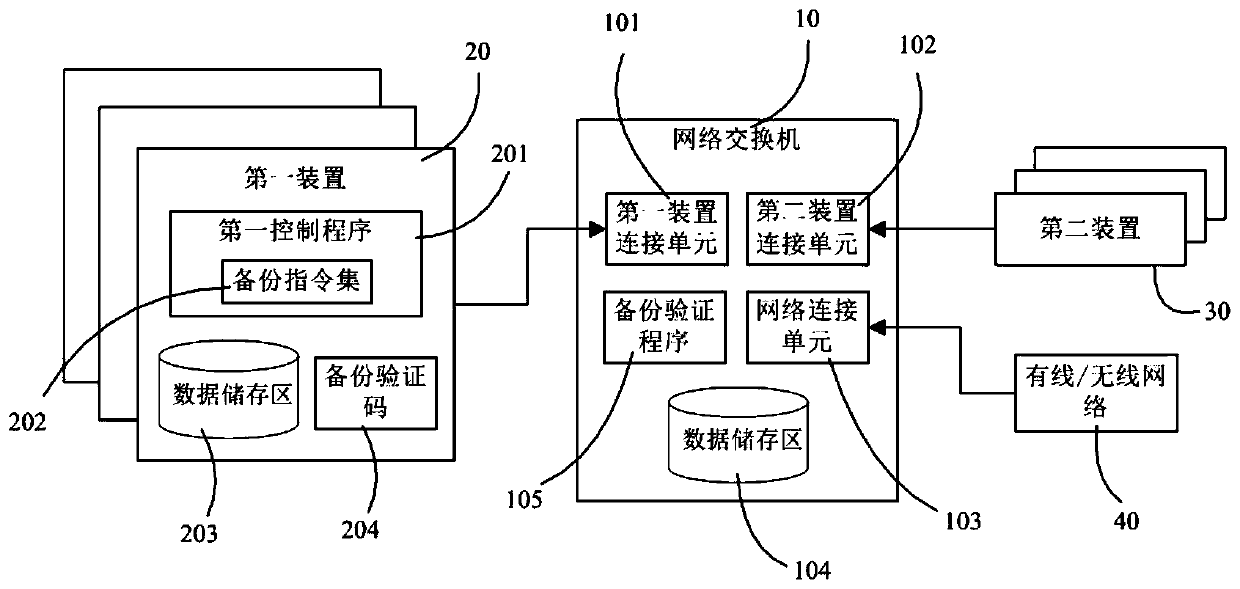
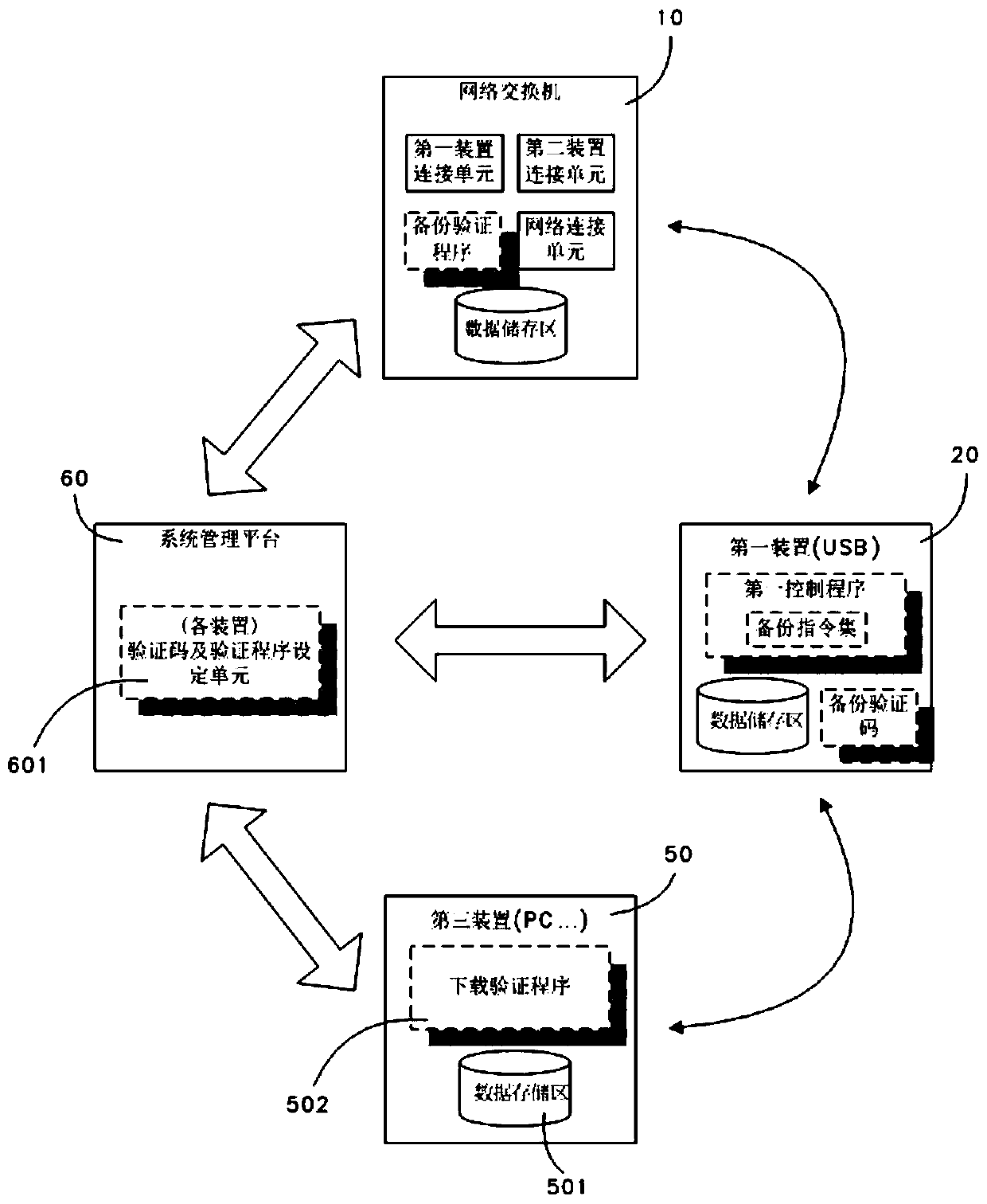
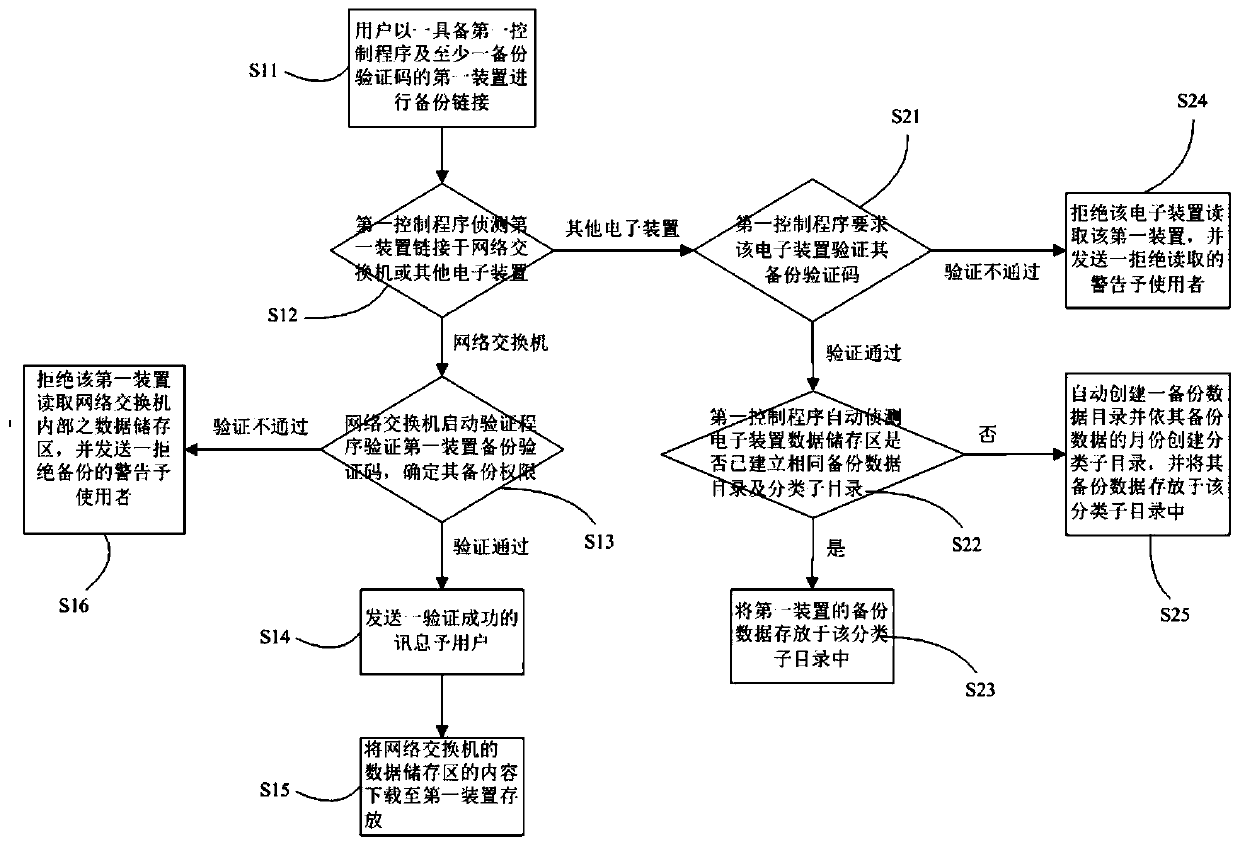
System and method for network switch to perform automatic backup of data
The invention provides a system and method for a network switch to execute automatic data backup. The system comprises a network switch which is at least provided with a plurality of first device connecting units, a plurality of second device connecting units and a plurality of network connecting units, wherein each unit is electrically connected to a main board so as to be respectively connectedwith a corresponding first device and a corresponding second device. The network switch is provided with at least one data storage area and a verification program, and when the first device or the second device reads the data storage area, the verification program verifies the backup permission of the device; and a plurality of first devices, storage medium, at least one data storage area is arranged; a first control program and a backup verification code are installed in the first control module. When the first device is connected with the first device connection unit of the network switch, the first control program drives the backup instruction set to automatically search the data storage area in the network switch, and downloads the content of the data storage area to the first device for storage through the authority of the backup verification code.
Owner:陈立新
Program running process conformance verification method
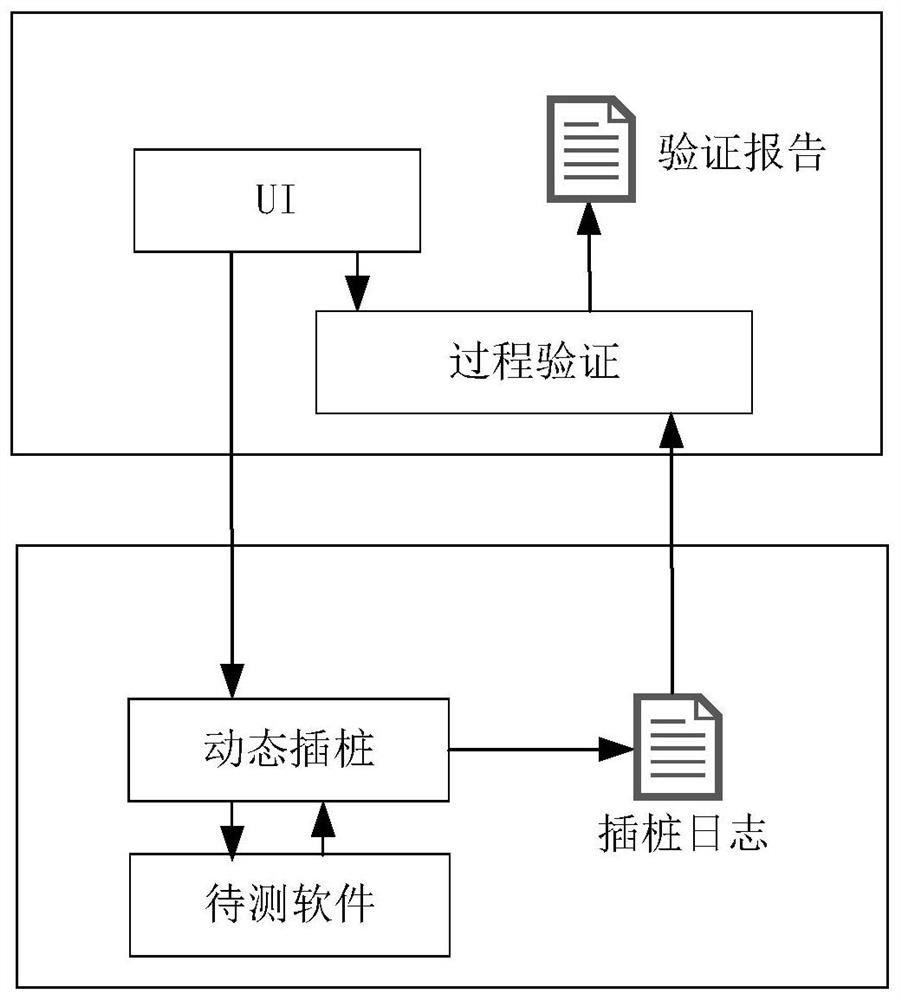
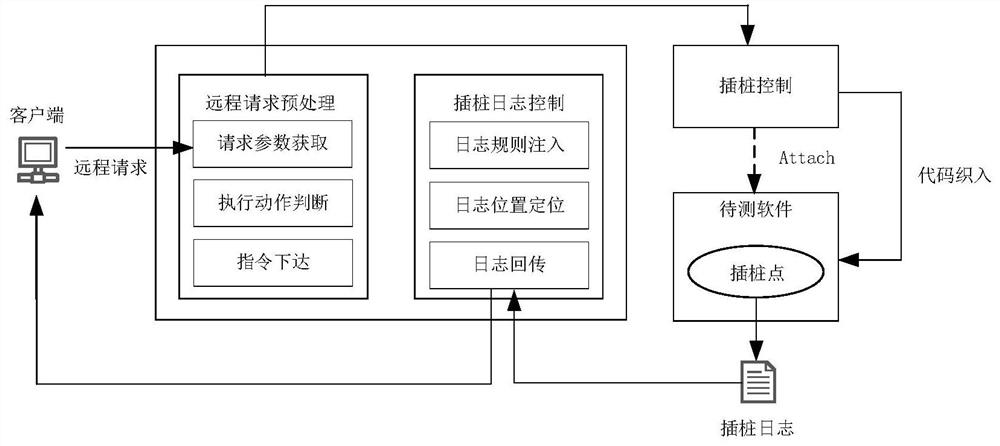
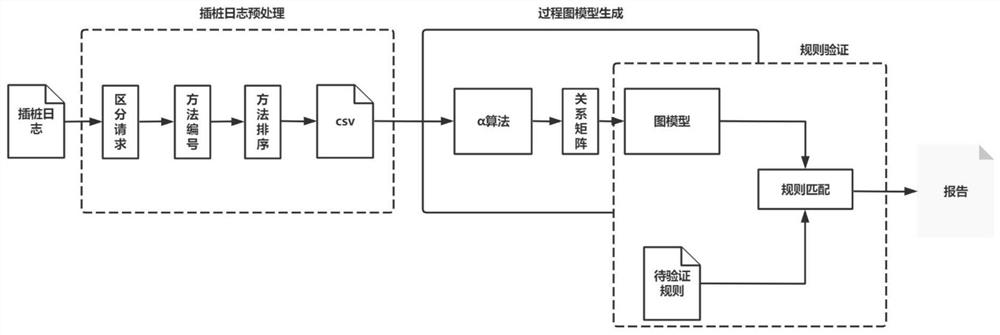
ActiveCN112579437AFilling the Gaps in Compliance VerificationSoftware testing/debuggingData modelingValidation methods
The invention provides a program running process conformance verification method, which comprises two links of dynamic instrumentation and process verification. The method comprises the steps of receiving and analyzing an instruction input by a user, executing an instrumentation start-stop process and returning a process data log during dynamic instrumentation work; receiving the process data logduring the process verification, extracting the relationship between methods in the log to establish a process diagram model, and sequentially matching the process diagram model with the standard rule, thereby verifying the standard conformity of the program running process. According to the program running process verification method, the internal execution process information during program running is visually and quantitatively displayed through methods such as instrumentation point burying and data modeling, the program running process verification method is provided, and the blank of software running process conformity verification is filled up.
Owner:中国科学院电子学研究所苏州研究院 +1
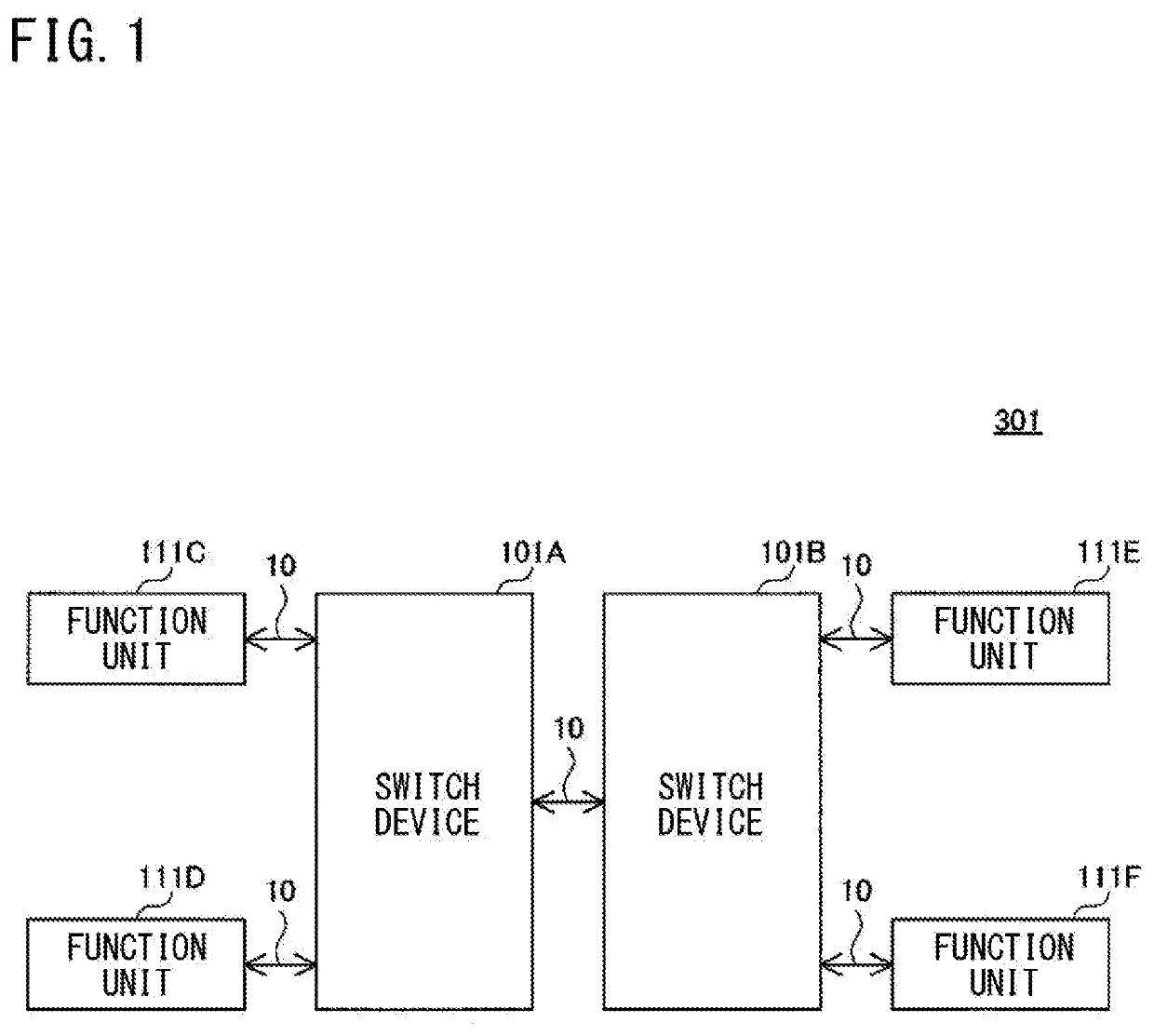
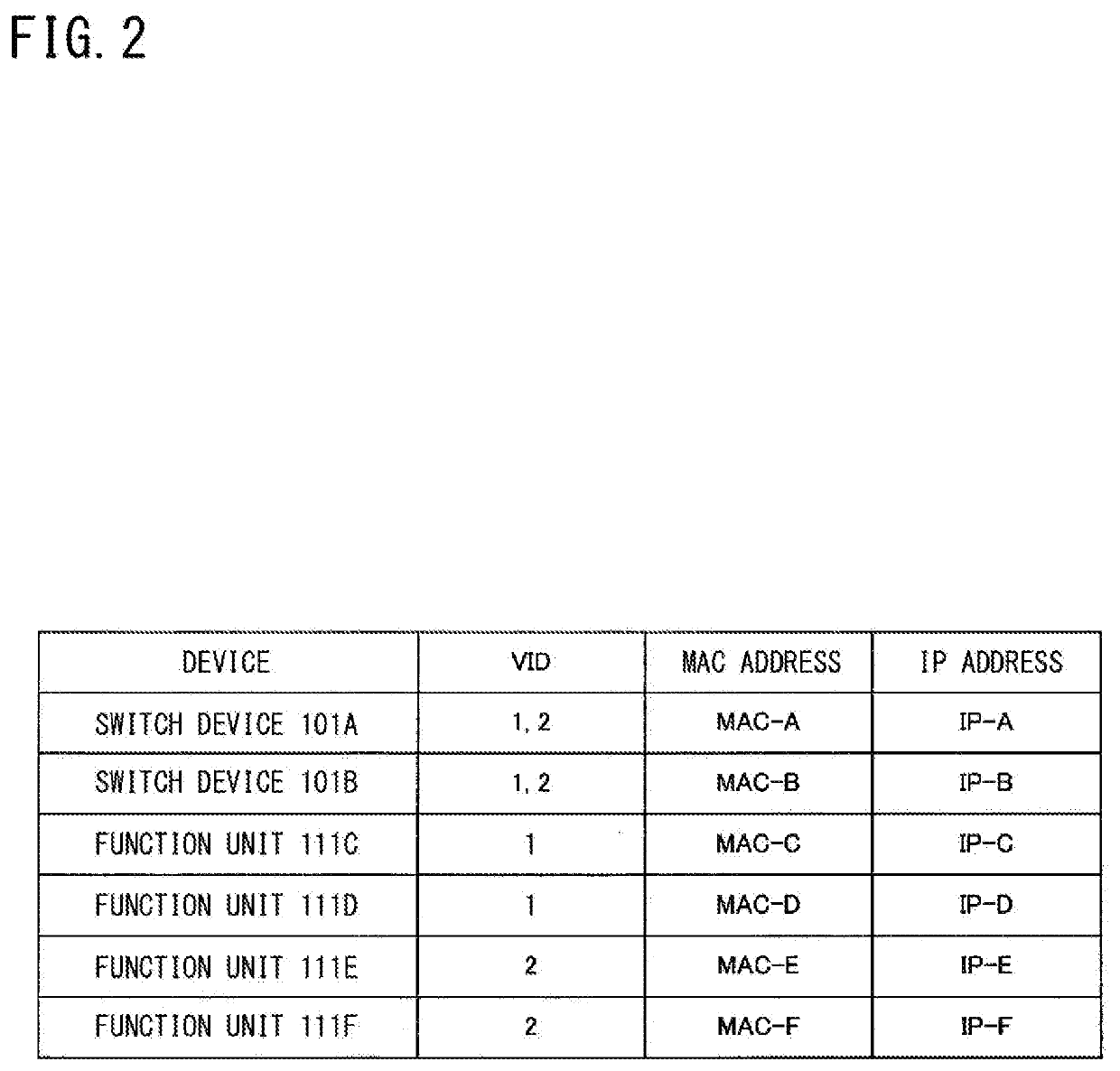
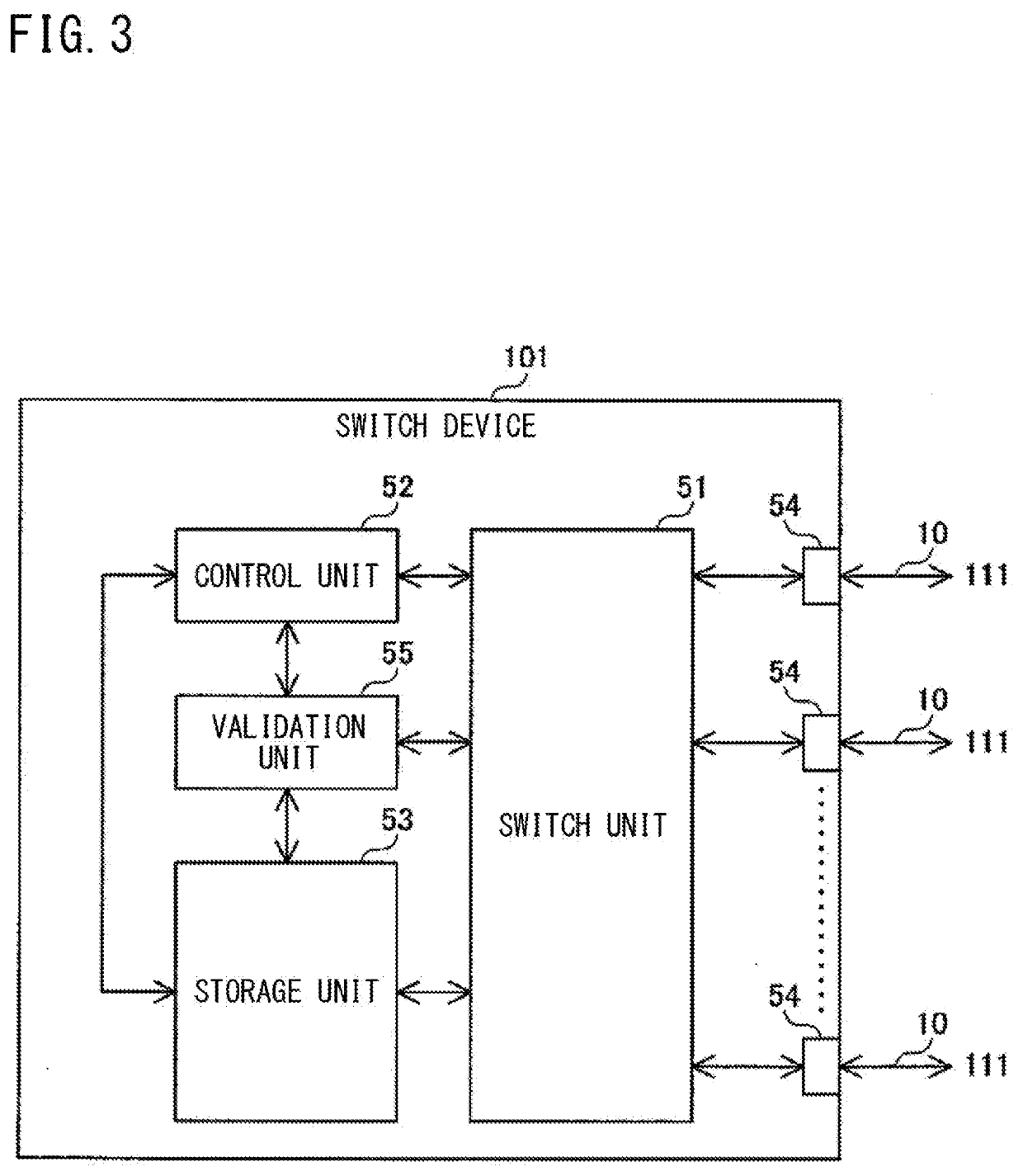
On-board communication system, switching device, verification method, and verification program
An on-vehicle communication system includes: a plurality of function units; and one or a plurality of switch devices, each switch device being configured to perform a relay process of relaying communication data between the function units. When unauthorized communication by a function unit has been detected, the switch device performs a validation process of validating a function unit other than an unauthorized-communication function unit that is the function unit for which the unauthorized communication has been detected.
Owner:AUTONETWORKS TECH LTD +2
Surface-reading apparatus, subject verification apparatus and storage medium storing subject verification program
ActiveUS8422743B2Non-fibrous pulp additionNatural cellulose pulp/paperSurface conditionsComputer science
The present invention provides a surface-reading apparatus that includes a subject-flexing mechanism and a surface-reading component. The subject-flexing mechanism causes a subject to flex in one of a convex form and a concave form. The surface-reading component reads a characteristic of a surface condition of the subject that has been flexed by the subject-flexing mechanism. The surface-reading component can includes an optical reading component that optically reads the characteristic of the surface condition of the subject. The optical reading component may be a reflected light-reading component that reads the characteristic of the surface condition of the subject with reflected light or may be a transmitted light-reading component that reads the characteristic of the surface condition of the subject with transmitted light.
Owner:FUJIFILM BUSINESS INNOVATION CORP
Access control method and system of Internet of Things, and user equipment
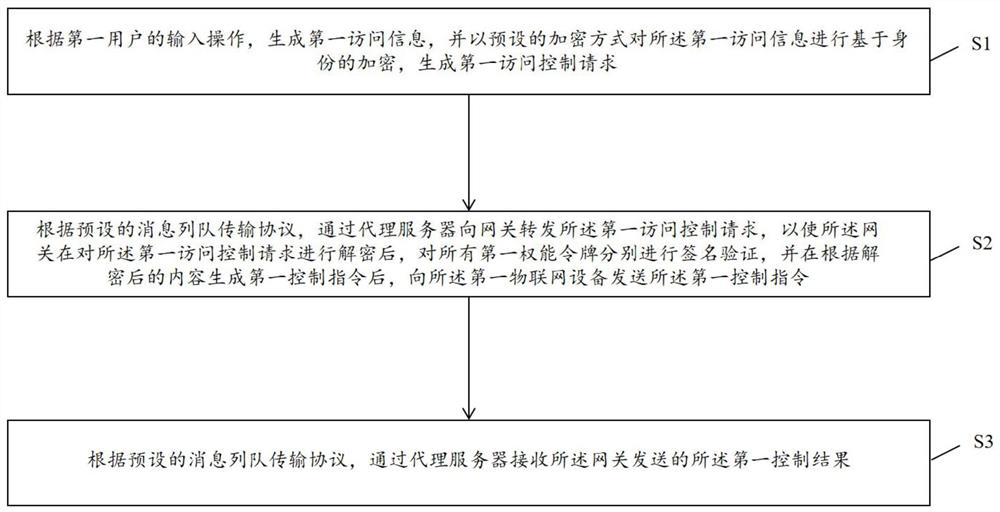
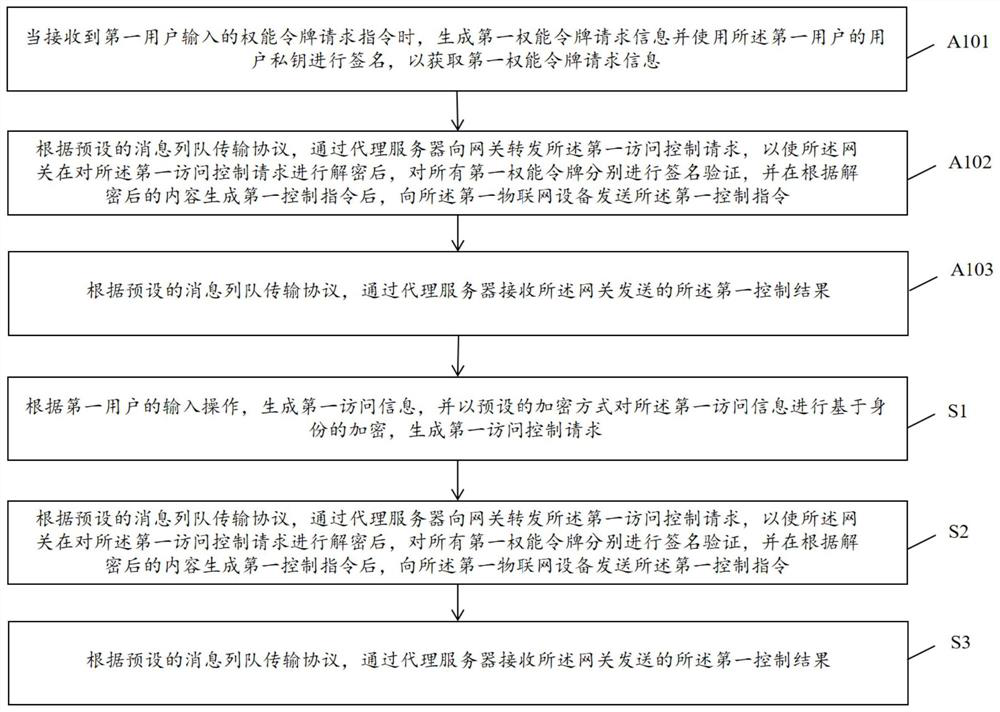
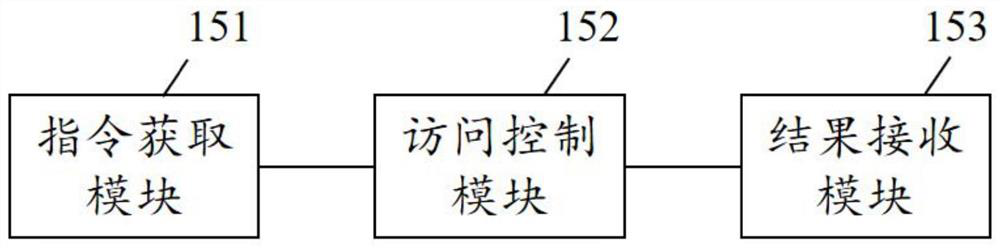
ActiveCN113329003AQuick responseAvoid it happening againUser identity/authority verificationServer agentID-based encryption
The invention discloses an access control method and systemof Internet of Things, and user equipment. The user equipment comprises an instruction acquisition module, an access control module and a result receiving module. The system comprises a central server, a proxy server, a gateway, Internet of Things equipment and user equipment. Through cooperation of an identity-based encryption technology and the proxy server based on a message queue transmission protocol, a digital certificate of a first user is verified in advance when a first permission token chain is generated, and after verification is passed, the digital certificate is placed in the first permission token chain and signed. The method, the user equipment and the system not only avoid the generation of a large number of keys and the subsequent key management burden, but also enable a verification program for the digital certificate of a visitor and a signature verification program of the first permission token chain to be carried out together, thereby accelerating the response speed of access control on the premise of ensuring the legality of the access control.
Owner:GUANGZHOU UNIVERSITY
Vulnerability detection method and device, electronic equipment and computer readable storage medium
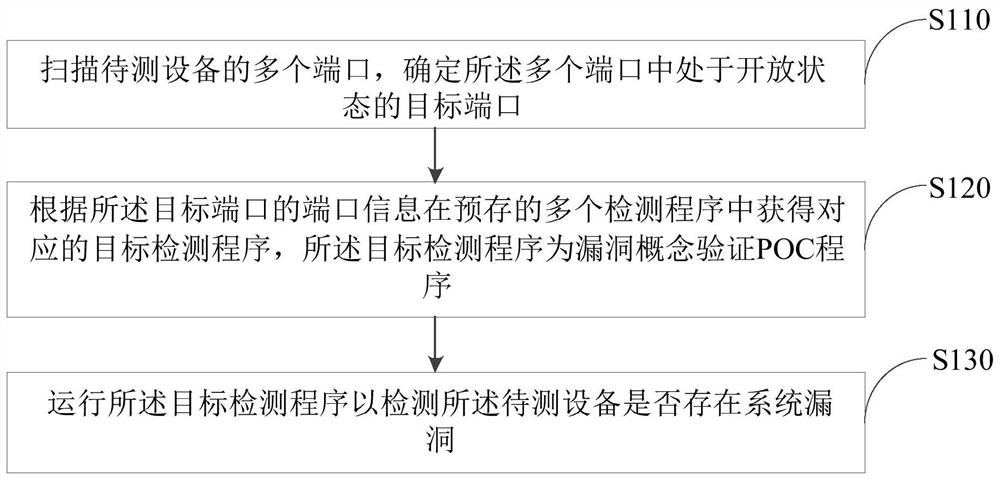
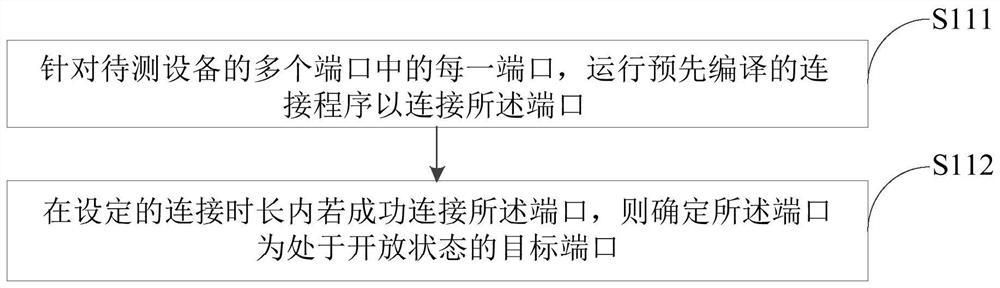
The invention provides a vulnerability detection method and device, electronic equipment and a computer readable storage medium, and the method comprises the steps: determining a target port in an open state by scanning a plurality of ports of to-be-detected equipment; obtaining a corresponding target detection program from a plurality of pre-stored detection programs according to the port information of the target port, wherein the target detection program is a vulnerability concept verification POC program; and finally, running the target detection program to detect whether the to-be-detected equipment has system vulnerabilities or not. In the scheme, whether the equipment has the system vulnerability or not is detected by scanning the port and running the corresponding vulnerability concept verification program, so that the vulnerability condition on the system level can be successfully detected, and the phenomenon that the equipment is subsequently attacked due to the vulnerabilityon the system level is avoided.
Owner:北京知道未来信息技术有限公司
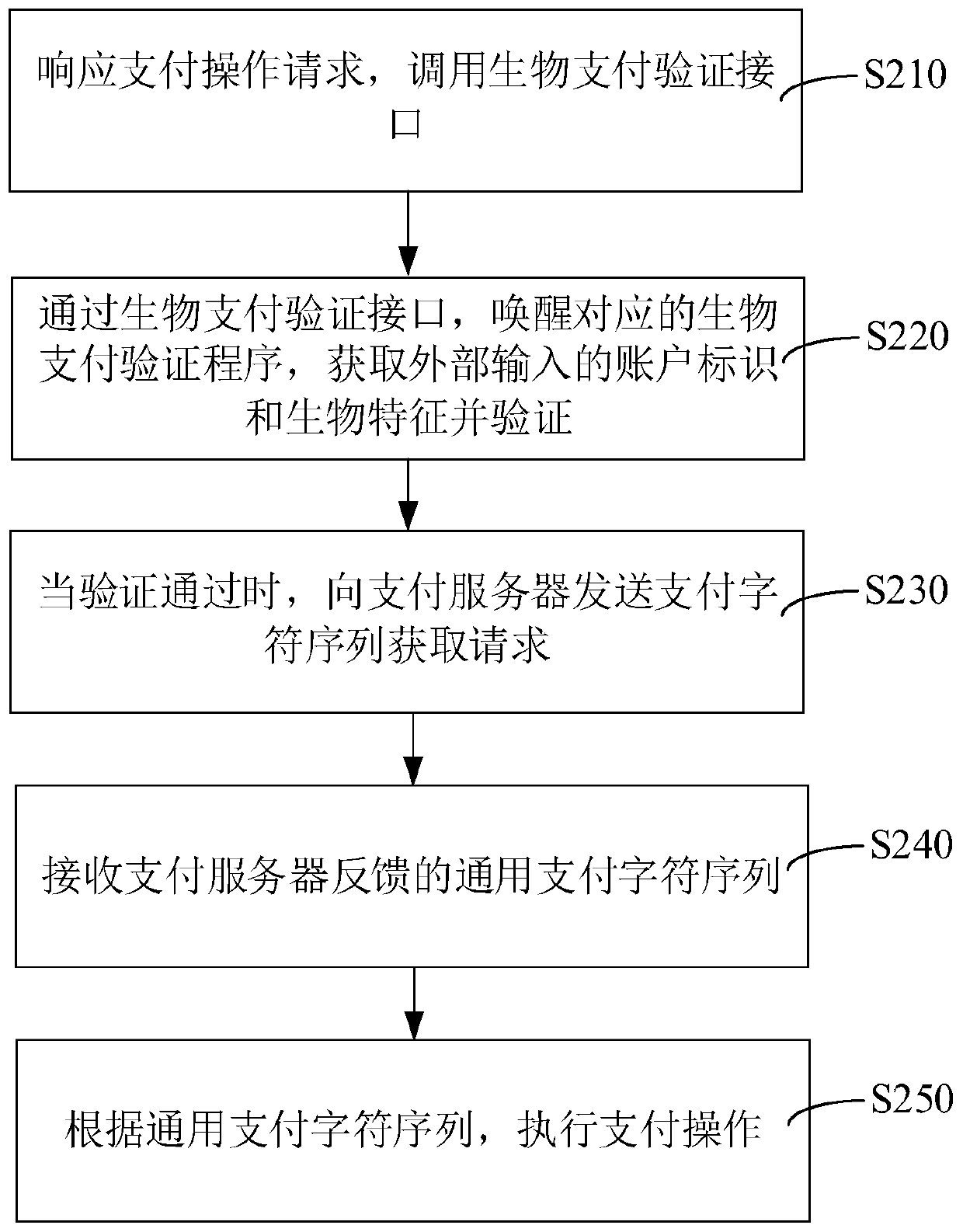
Payment method and device, computer readable storage medium and computer equipment
The invention relates to a payment method and device, a computer readable storage medium and computer equipment, and the method comprises the steps: responding to a payment operation request, and calling a biological payment verification interface; awakening a corresponding biological payment verification program through the biological payment verification interface, and obtaining and verifying anexternally input account identifier and biological characteristics; when the verification is passed, sending a payment character sequence acquisition request to a payment server; receiving a generalpayment character sequence fed back by the payment server, wherein the general payment character sequence does not set a payment value; and executing payment operation according to the universal payment character sequence. Through the above method, the terminal can obtain the universal payment character sequence for payment from the payment server only when passing the biological verification, theprocess does not depend on the network condition of a merchant and the processing time of ordering, and the payment time can be reduced.
Owner:TENCENT TECH (SHENZHEN) CO LTD
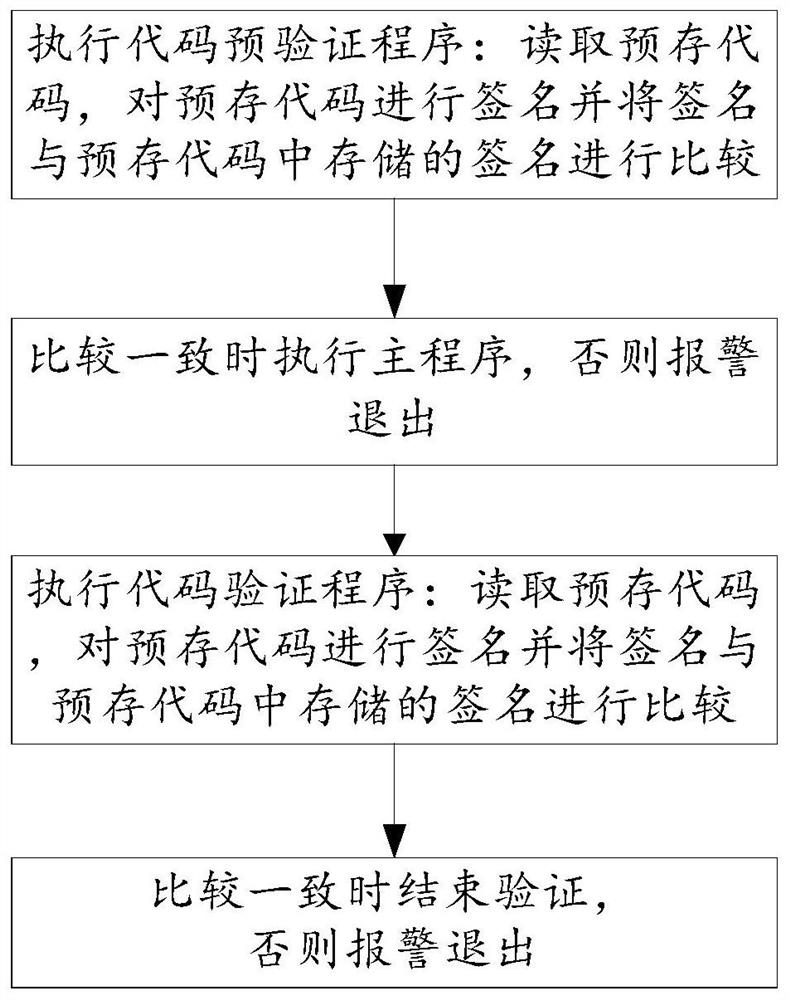
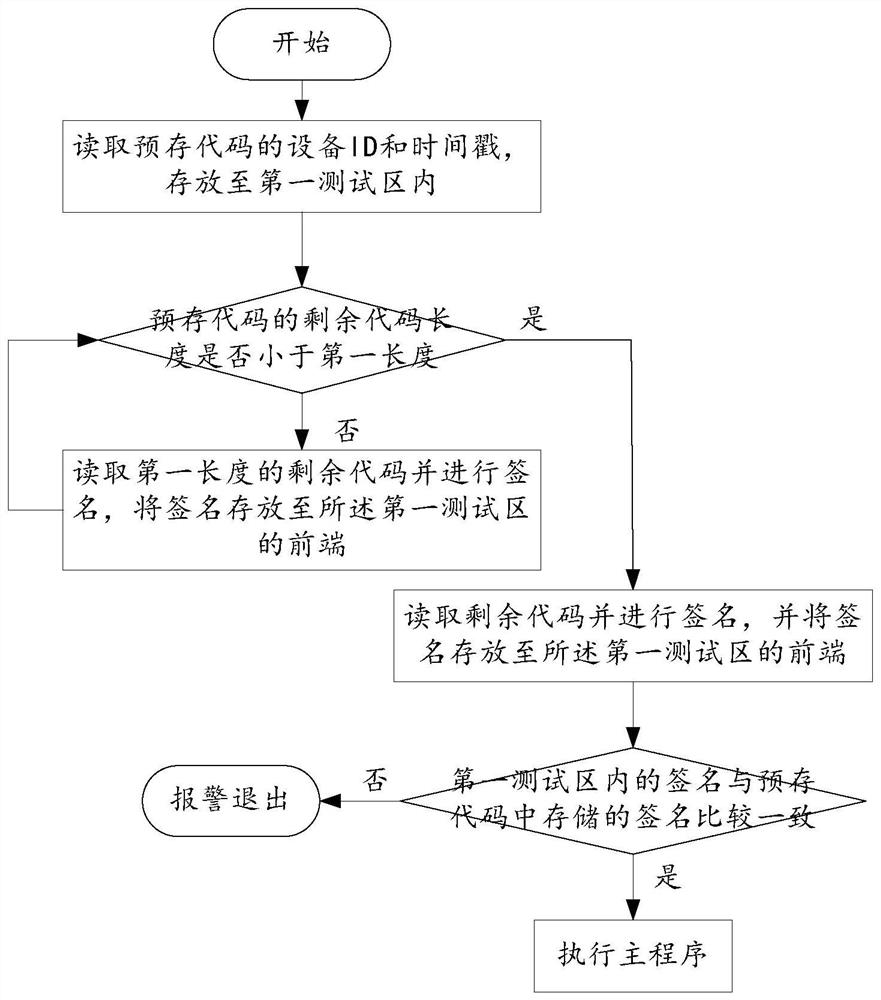
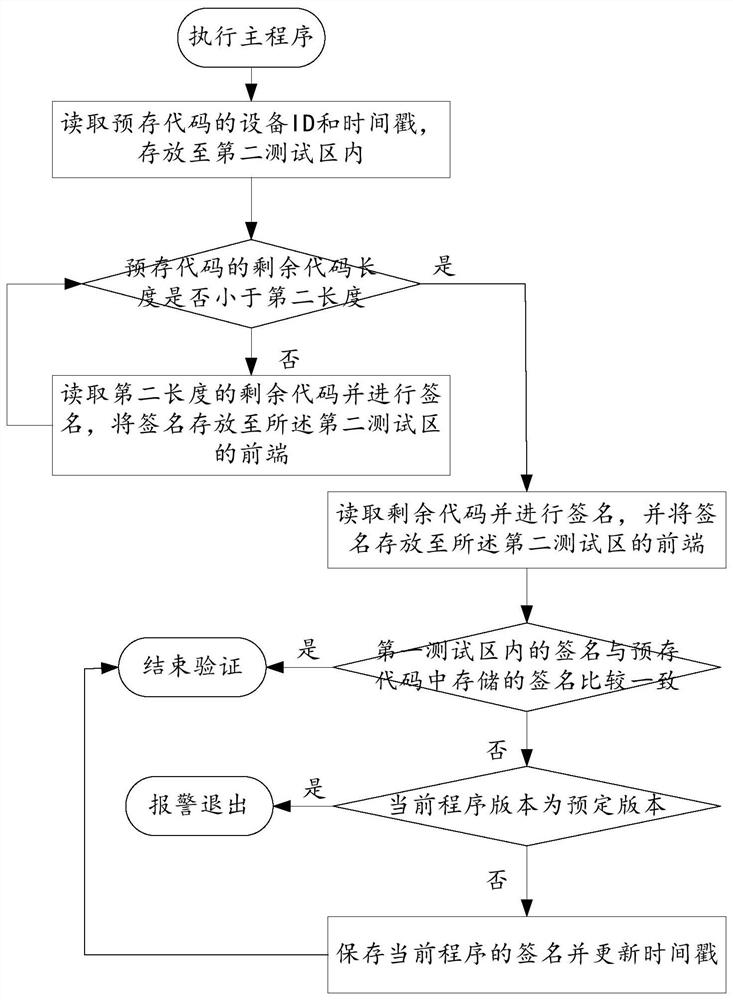
Code verification method, networking terminal equipment and readable storage medium
PendingCN113642007AIncreased complexityDigital data protectionPlatform integrity maintainanceProgramming languagePre validation
The invention discloses a code verification method, networking terminal equipment and a readable storage medium. The code verification method comprises the steps of executing a code pre-verification program, specifically, reading a pre-stored code, signing the pre-stored code and comparing a signature with a signature stored in the pre-stored code; if the signature is consistent with the signature stored in the pre-stored code, executing a main program, otherwise, alarming and exiting; executing a code verification program; and if the signature is consistent with the signature stored in the pre-stored code, ending the verification, and otherwise, alarming and exiting. According to the technical scheme provided by the embodiment of the invention, the code is pre-verified before the main program is executed, the security of the code is firstly determined, meanwhile, the main program is started under the condition that pre-verification has no problem, and the verification program for the code is synchronously started in the running process of the main program, so that verification guard is performed in the running process of the program, codes are verified and protected through two-section type starting, the signature in the code verification process changes along with the change of time at the same time, and the cracking complexity is increased.
Owner:BOE TECH GRP CO LTD
Dispatching identity information from secure hardware appliance
ActiveUS10789386B2Key distribution for secure communicationUser identity/authority verificationComputer hardwareEmbedded system
A technique for promoting network security employs a user-centric approach in which a hardware appliance serves as a local security hub for storing and dispatching user identity information (UII). The hardware appliance is configured to release UII in response to access requests by applying a variable verification procedure. The variable verification procedure tests multiple verification factors associated with an access request, assigns a verification strength to each factor, and selectively releases the requested UII in response to a combined verification strength exceeding a threshold.
Owner:REAVIRE INC
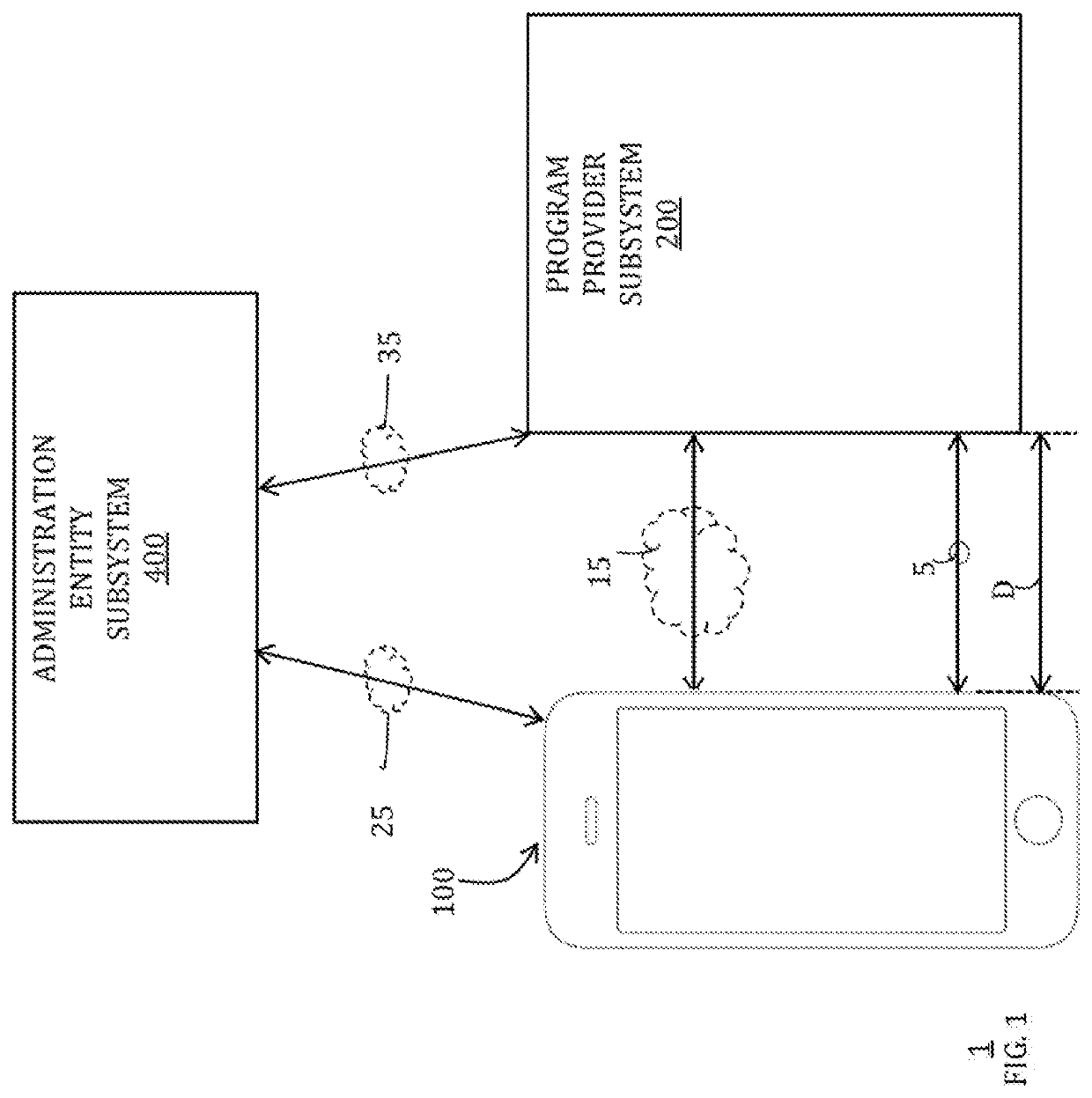
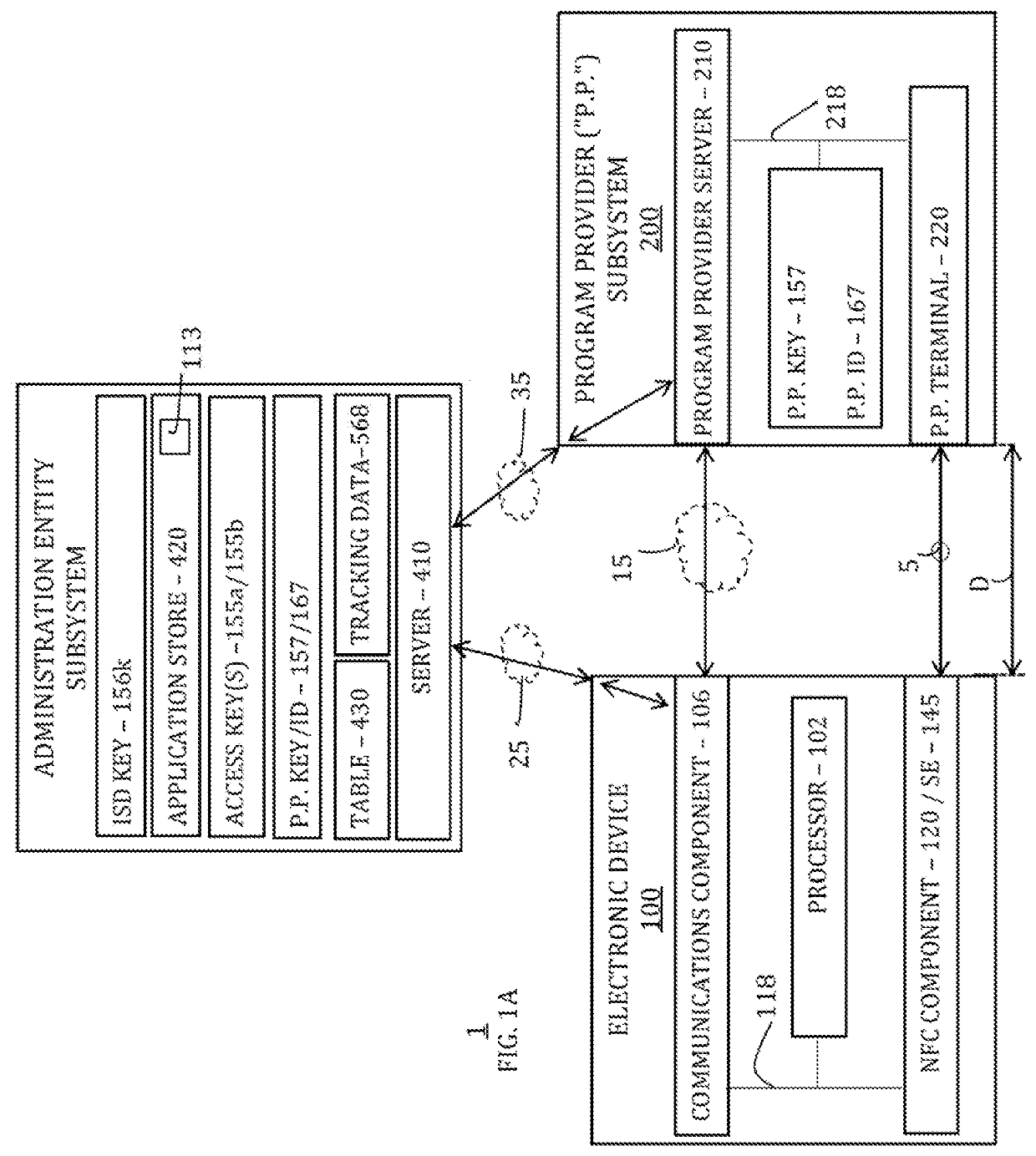
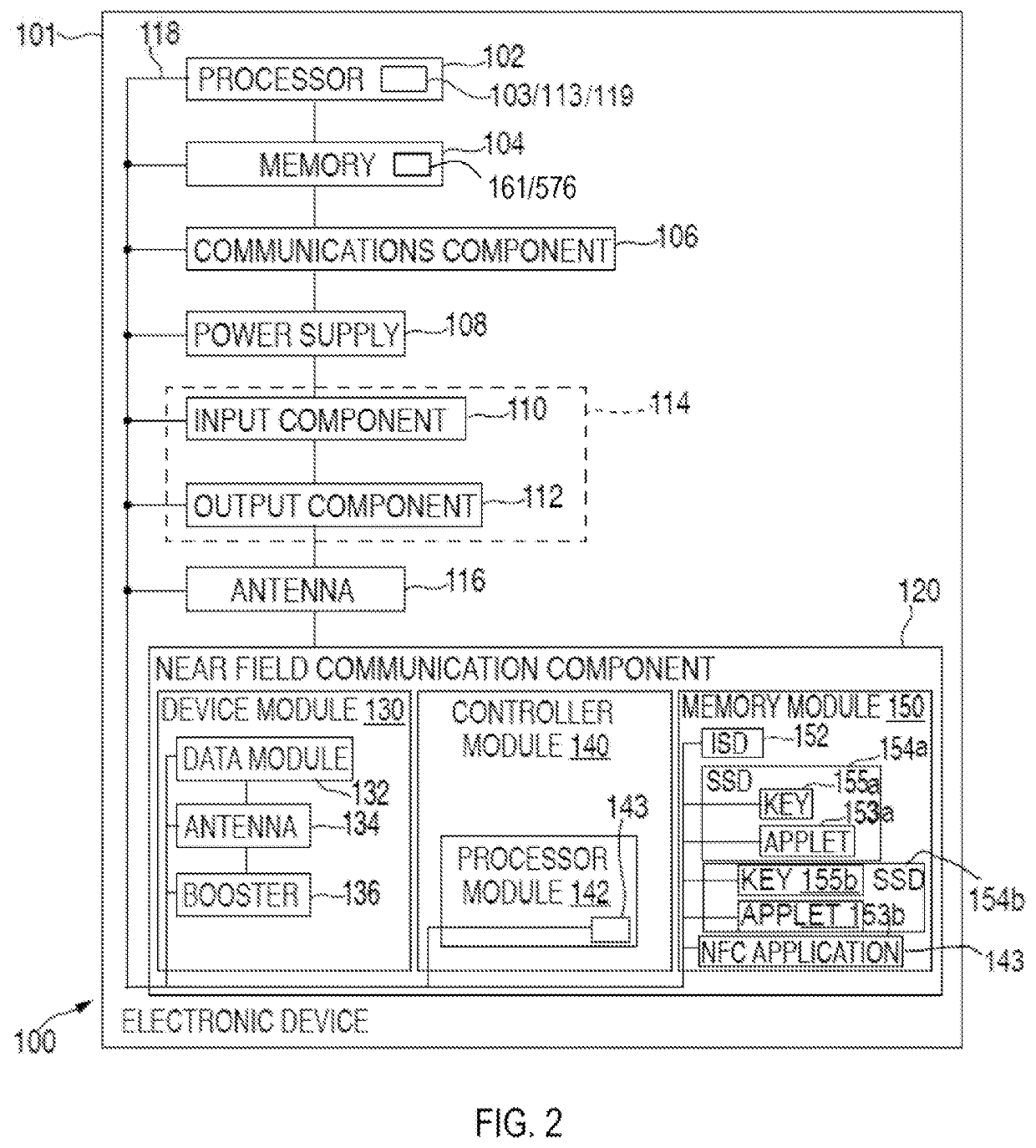
Managing program credentials on electronic devices
Systems, methods, and computer-readable media for personalizing program credentials are provided. For example, a program credential (e.g., loyalty pass) associated with a program provider (e.g., an issuer) subsystem may be customized using personal data. The personal data can be collected from an electronic device before provisioning the customized program credential on the electronic device for use in a suitable transaction. However, such personal data may not be collected unless an administration entity subsystem is first able to validate the program provider subsystem. The administration entity subsystem can generate tracking data that may be used during the validation and / or provisioning in order to track when program credentials are personalized.
Owner:APPLE INC
Features
- R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
Why Patsnap Eureka
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Social media
Patsnap Eureka Blog
Learn More Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com