JWT-based authorization method capable of being manually revoked
A technology of tokens and user information, applied in the application field of network authorization technology, can solve the problems of misappropriation of client permissions, consumption of server memory space, difficulty in dealing with high concurrent requests, etc., to achieve the effect of supporting high concurrent access and reducing consumption
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
[0034] The present invention will be further described below in conjunction with the accompanying drawings. The following examples are only used to illustrate the technical solution of the present invention more clearly, but not to limit the protection scope of the present invention.
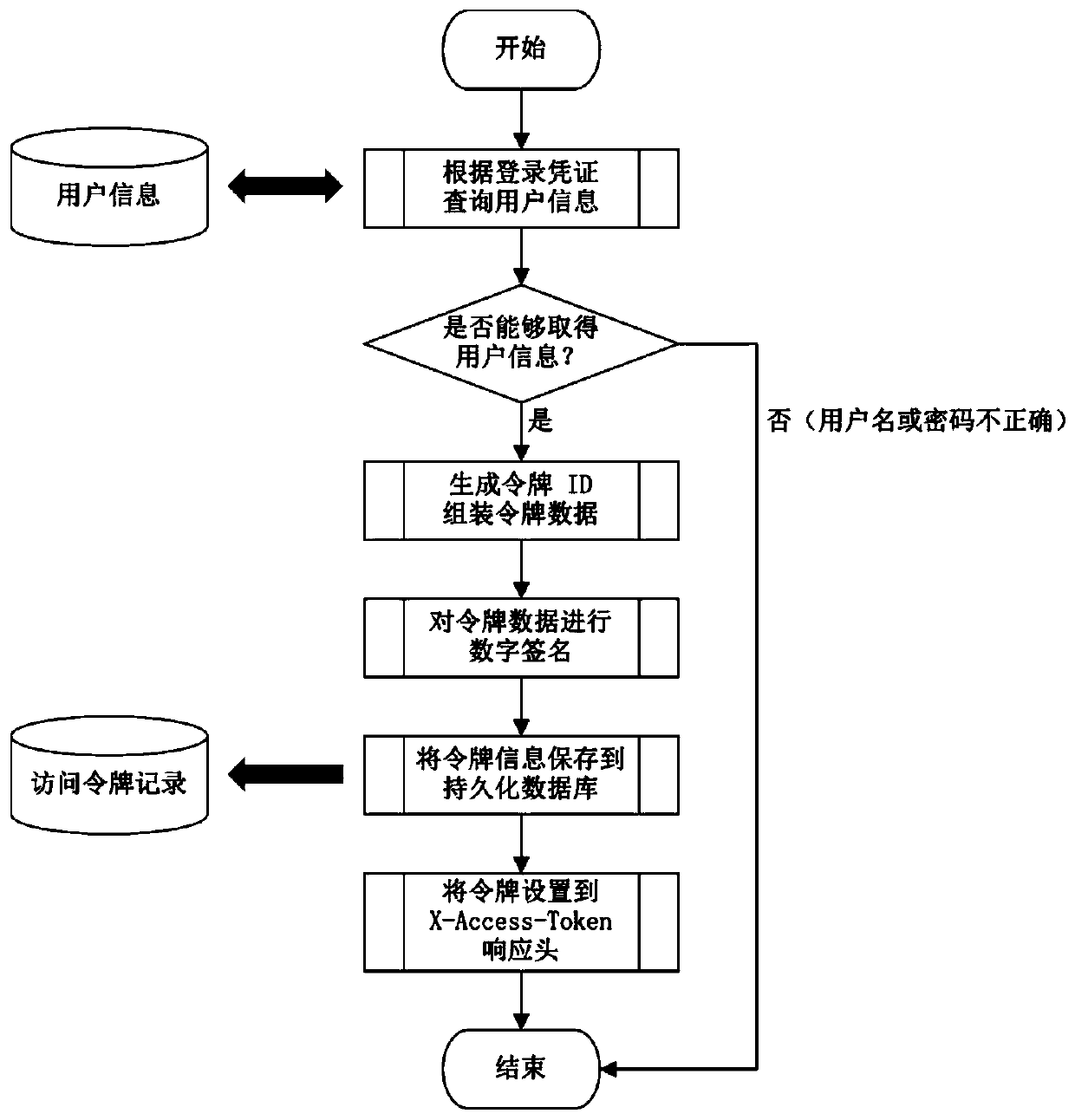
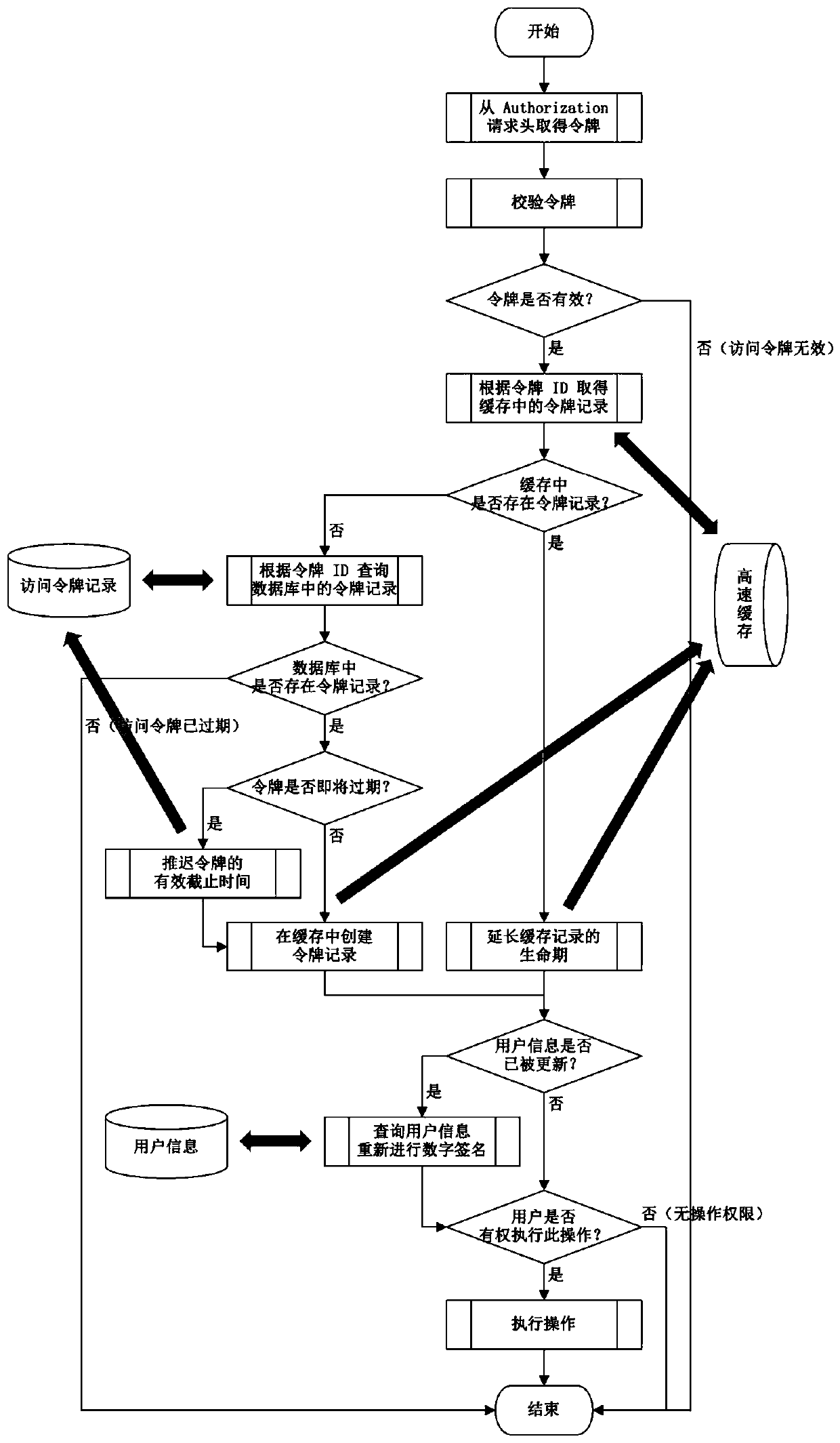
[0035] A JWT-based manually revocable authorization method, including providing a login credential verification program and a server-to-access token verification process;
[0036] The verification procedure for providing login credentials includes the following steps:
[0037] 1a: Query user information based on login credentials;
[0038] 2a: Determine whether the user information can be obtained, and if the user information can be obtained, generate a token ID to assemble the token data;
[0039] 3a: Digitally sign the token data in 2a above;
[0040] 4a: Save the token information to the persistent database, and create an access token record;
[0041] 5a: Set the token to the X-Access-Tok...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com