Secure neighbor discovery between hosts connected through a proxy
A technology of neighbor discovery and proxy connection, applied in security devices, wireless communication, network data management, etc., can solve the problems of RSA signature invalidation, discarding, insecurity, etc.
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
[0035] The innovative teachings of the present invention are described below with specific reference to various exemplary uses and aspects of the preferred embodiment. It should be understood, however, that this embodiment provides only a number of examples of the many advantageous uses of the innovative teachings of the present invention. In general, statements made in the specification of the present application do not necessarily limit any of the various claimed aspects of the invention. Additionally, some statements may apply to some inventive features but not to others. In the description of the figures, like reference numerals refer to like elements of the invention.
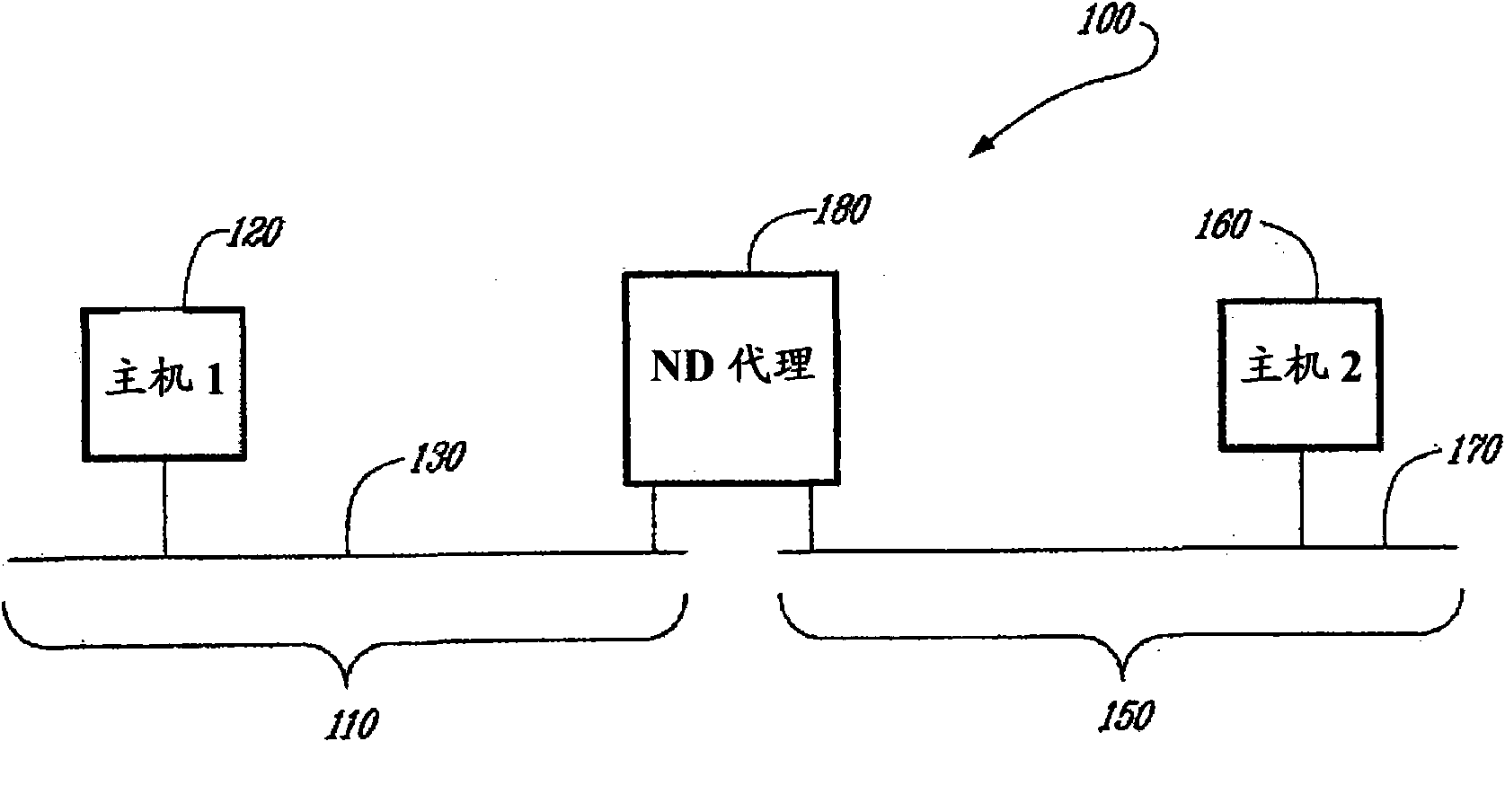
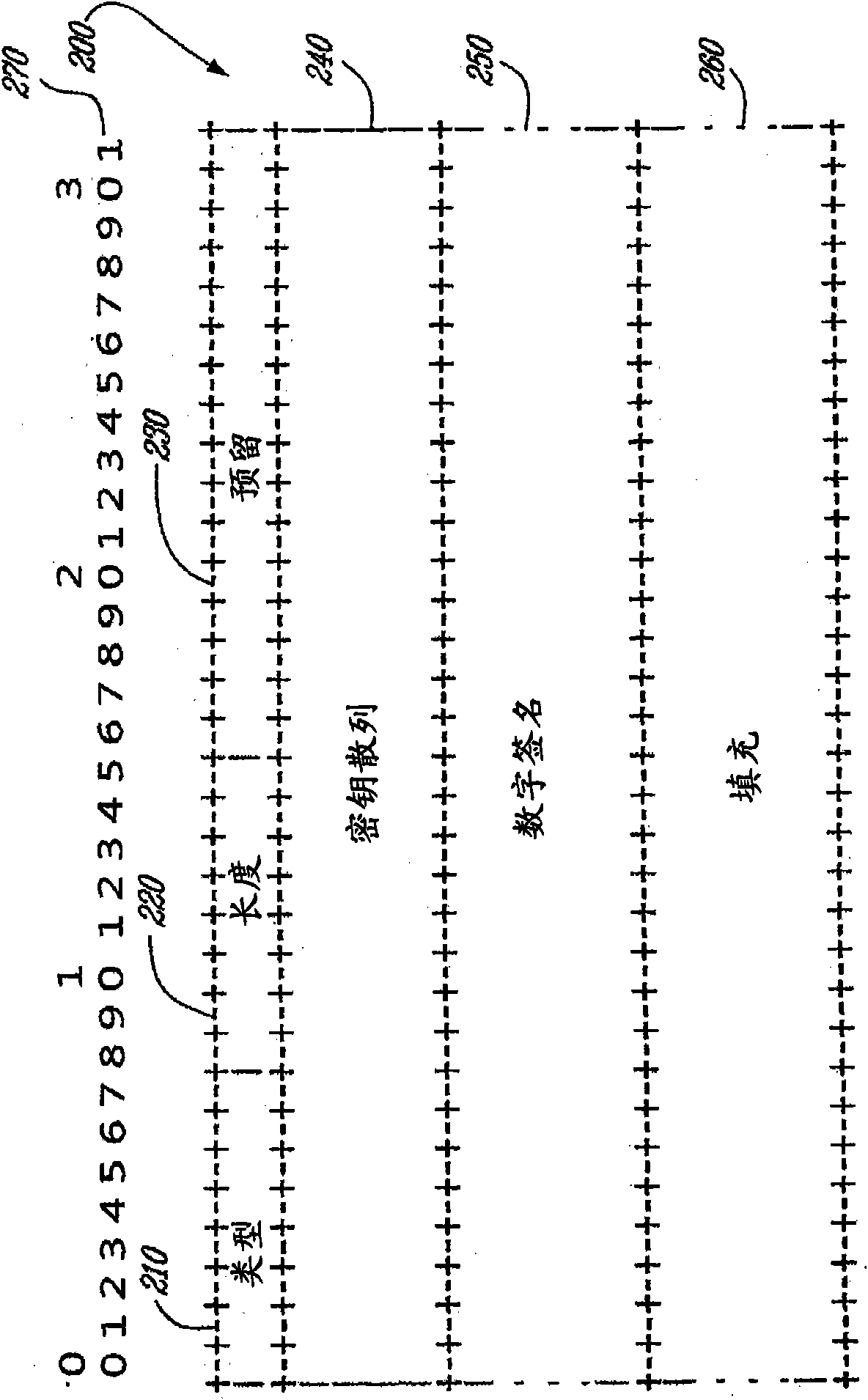
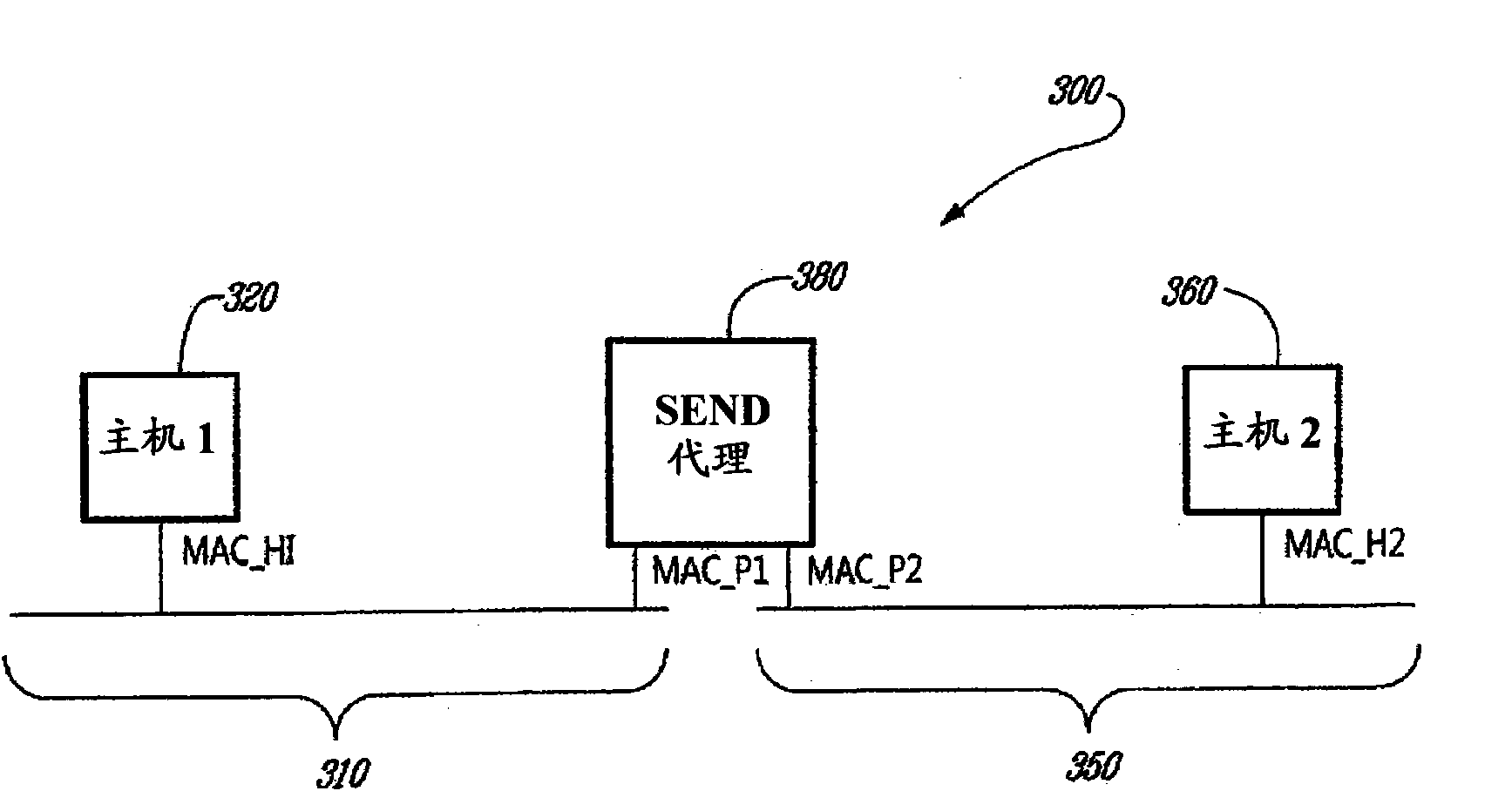
[0036] According to the invention, the roles of address ownership and address advertisement are clearly separated. The normal operation of a standard Neighbor Discovery (ND) proxy is defined in Internet Task Engineering Task Force (IETF) Request for Comments (RFC) number 4389. The present invention prov...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com