A secure access control method for lowpan nodes based on neighbor discovery
A neighbor discovery and access control technology, applied in digital transmission systems, electrical components, transmission systems, etc., can solve problems such as long processing time and calculation process, abuse of NDP duplicate address detection, high cost of hosts, etc., to achieve a wide range of The effect of high applicability, scalability, and strong feasibility
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
[0036]The present invention will be described in further detail below in conjunction with the accompanying drawings and embodiments.
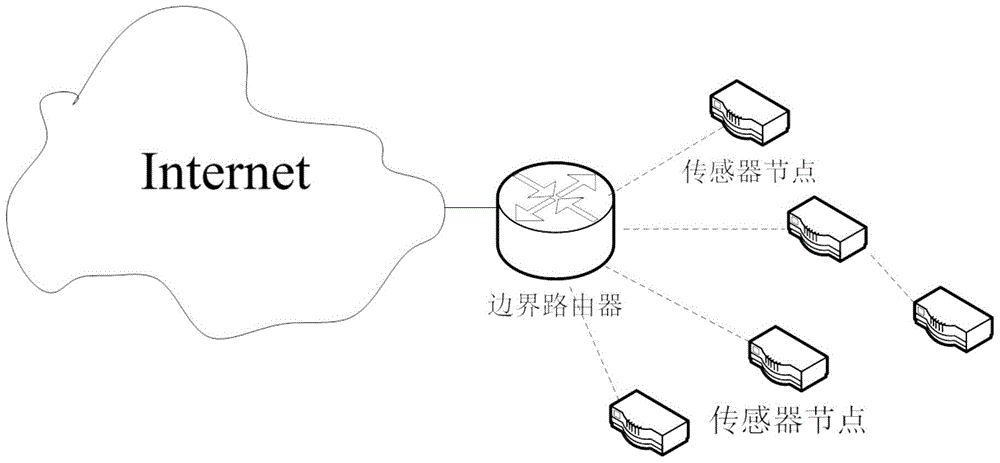
[0037] The technical scheme of the present invention relies on the optimized 6LoWPAN network neighbor discovery process, realizes an effective node access control scheme, and provides security protection for the network. In the 6LoWPAN network, the border router plays an important role. In addition to connecting the WSN network to the Internet, it is also responsible for notifying the link prefix (subnet information) route and other configuration information, and maintaining the IPv6 address of each node within the network range. information and MAC information, so that it can perform two-layer address resolution and duplicate address detection. The border router needs to be manually configured, such as figure 1 shown.
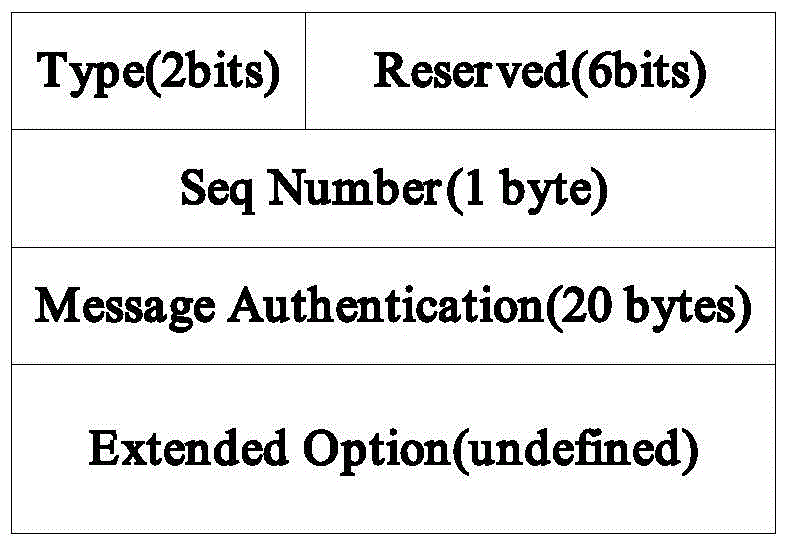
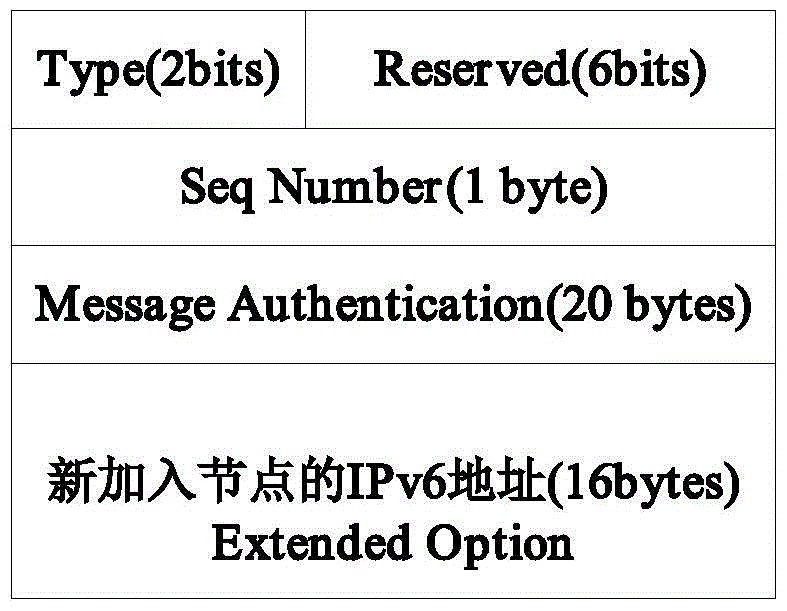
[0038] Internet Protocol Version 6 (IPV6) Neighbor Discovery is a set of messages and procedures defined in RFC4861 for dete...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com