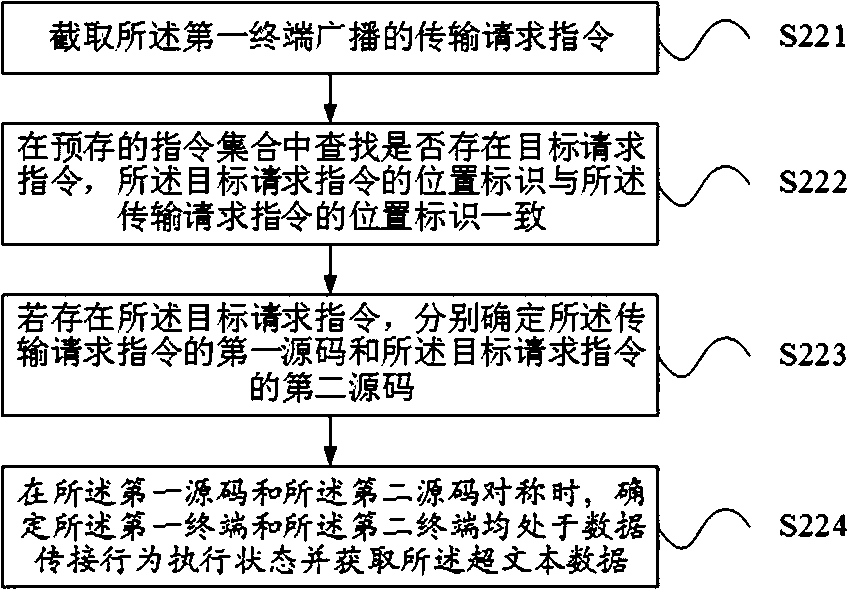
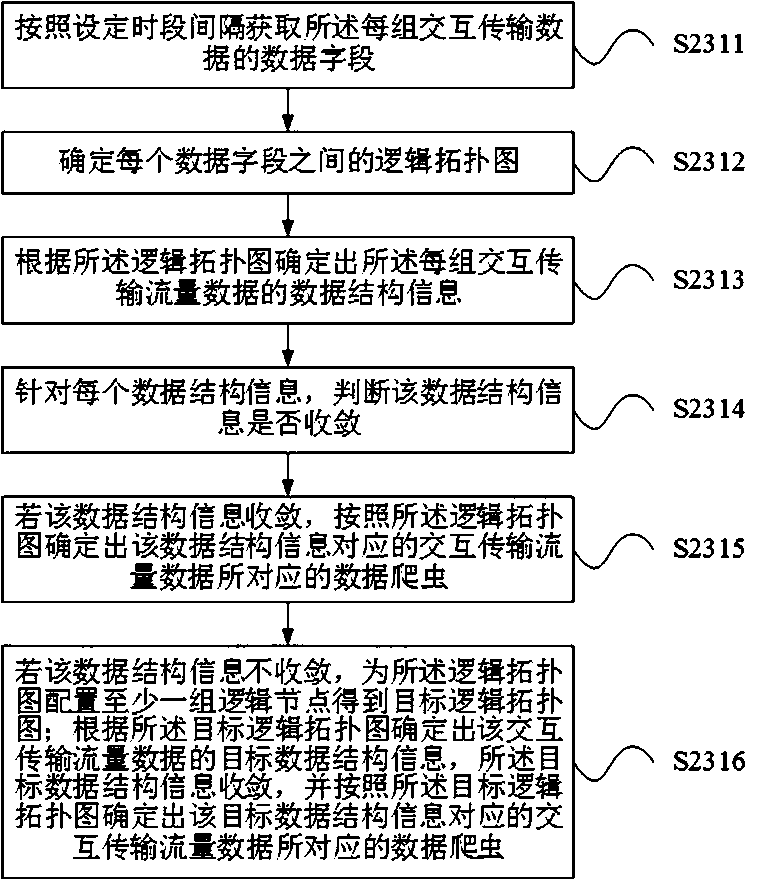
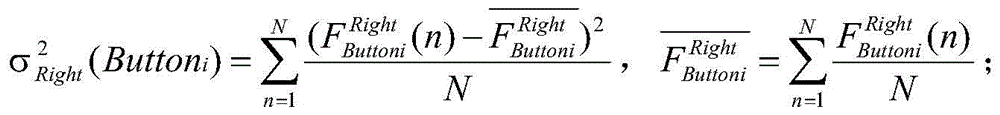Patents
Literature
42results about How to "Prevent camouflage" patented technology
Efficacy Topic
Property
Owner
Technical Advancement
Application Domain
Technology Topic
Technology Field Word
Patent Country/Region
Patent Type
Patent Status
Application Year
Inventor
Novel offline payment method
InactiveCN105205664AConvenient paymentPrevent illegal tamperingPayment architecturePaymentMobile device
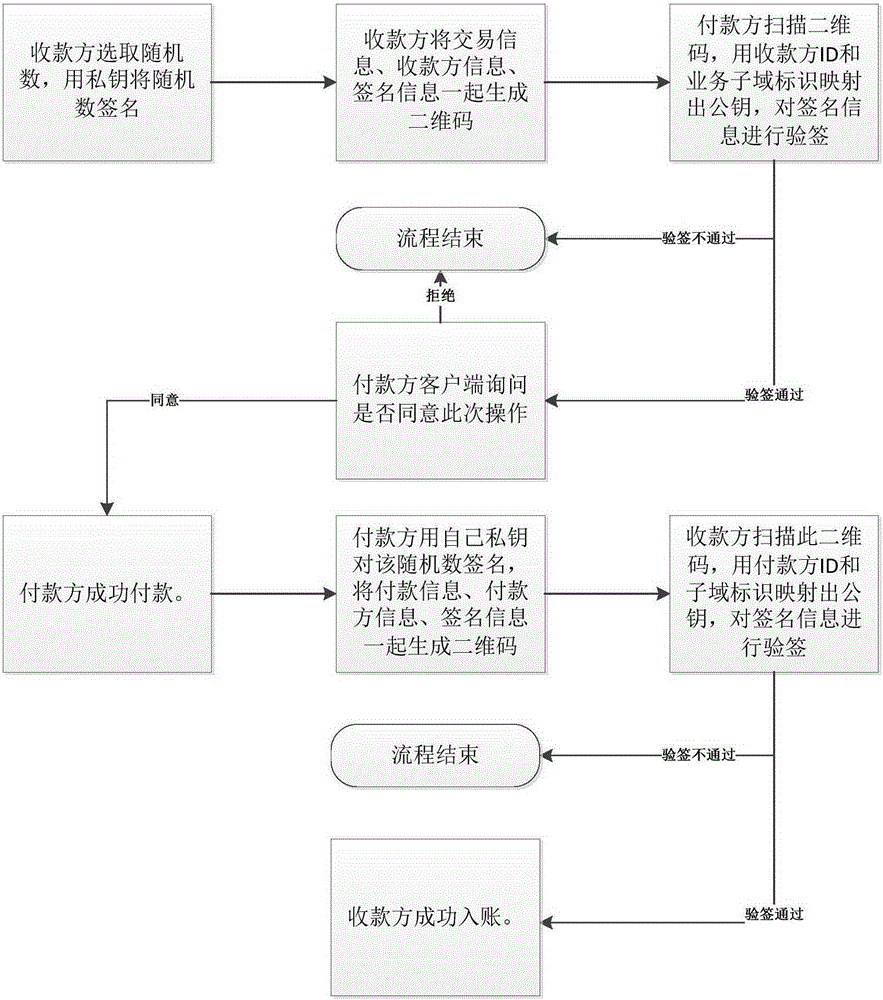
The invention discloses a novel offline payment method. The method comprises the steps that account numbers of an accountee party and a receiving party serve as IDs, and a corresponding public key and private key are mapped according to business sub-domain identifications; a random number is selected from the receiving party, signature is conducted on the random number through the private key, and a two-dimension code is generated; the two-dimension code is scanned through the accountee party, the public key is mapped by means of the receiving party ID and the service sub-domain identification, and attestation is conducted on a signing message; if attestation succeeds, the accountee party successfully pays according to transaction information; signature is conducted on the random number by the accountee party through the private key after payment to generate a two-dimension code; the receiving party scans the two-dimension code, the public key is mapped through the accountee party ID and the business sub-domain identification, and attestation is conducted on a signing message; if attestation succeeds, posting is successfully conducted on the receiving party. According to the novel offline payment method, payment does not rely on the support of a network any more, payment is achieved on various mobile equipment, and the payment process is greatly facilitated. The two-way authentication process based on the identifications is adopted by the two payment parties, the legality of transactions is fully guaranteed, and illegal manipulation of information and information disguising are prevented.
Owner:CHINA SMARTCITY TECH
Equipment identification system based on equipment fingerprint
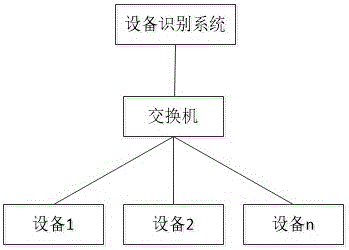
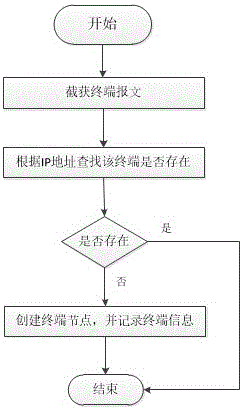
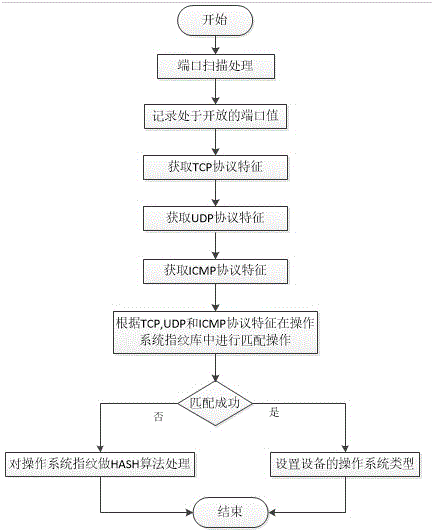
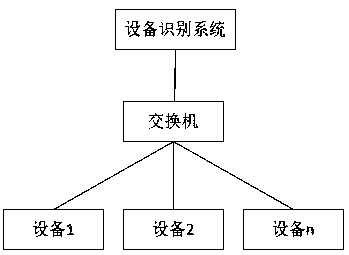
The invention belongs to the field of network admission control technology, and particularly relates to an equipment identification system based on an equipment fingerprint, wherein the equipment fingerprint information comprises hardware information, operating system information and application service information of the equipment. The system comprises the components of an equipment fingerprint database, an equipment discovery module, an equipment fingerprint acquisition module, an equipment fingerprint processing module, an equipment fingerprint matching module and an artificial identification module. The equipment fingerprint information comprises the MAC OUI hardware information and the operating system information of the equipment and the application service information in a port list. The formats of the fingerprint database comprise MAC OUI, operating system information, port list and equipment type. The equipment fingerprint acquisition module comprises operating system fingerprint information and port fingerprint information. The equipment identification system has advantages of performing network admission control on network equipment through the equipment type, making different security strategies on different kinds of equipment, preventing equipment counterfeiting, and ensuring high safety of enterprise network.
Owner:BEIJING VRV SOFTWARE CO LTD
Secure communication method based on intelligent vehicle
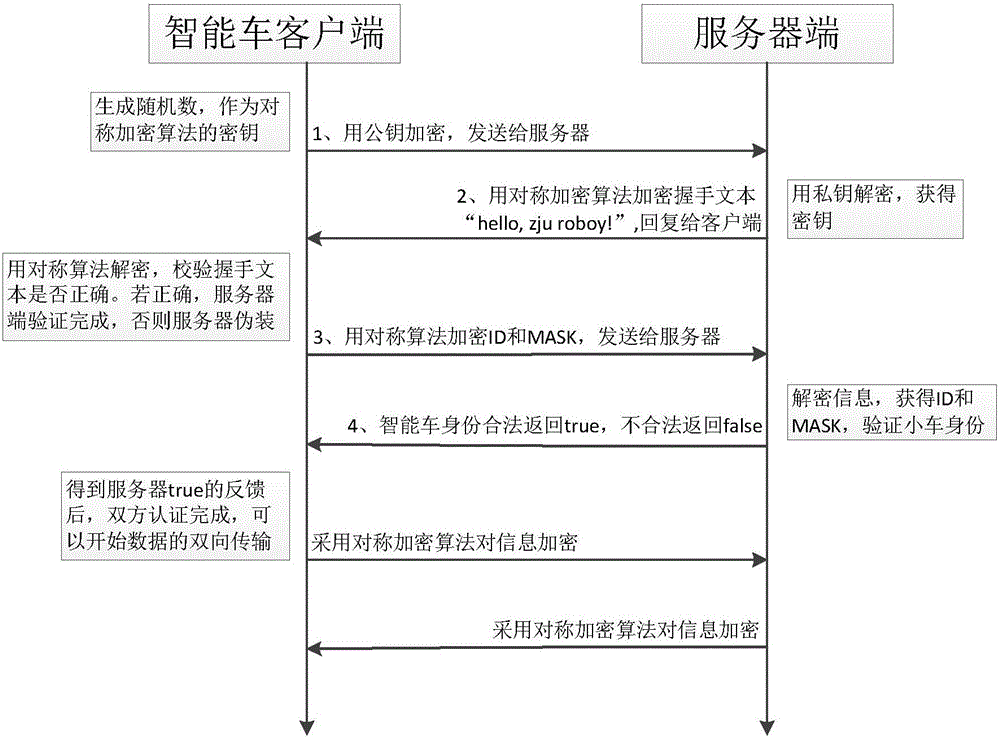
ActiveCN105049401APrevent theftTrue and valid identityTransmissionSecurity arrangementSecure communicationSerial code
The invention discloses a secure communication method based on an intelligent vehicle. The secure communication method comprises the steps: an intelligent vehicle client randomly generates a number which is used as the secret key for a communication symmetric encryption algorithm and verifies a server, and generates a symmetric secret key by using an asymmetric encryption algorithm and sends the symmetric secret key to the server; the server uses a private key to decrypt messages, and uses the symmetric encryption algorithm to encrypt a handshake text 'hello, zjuroboy !' and replies the encrypted handshake text 'hello, zjuroboy !' to the client; the client uses the symmetric encryption algorithm to decrypt the handshake text; the client uses the symmetric encryption algorithm to encrypt an intelligent vehicle serial number and MASK if verification is successfully; the server decrypts the verification information to obtain the serial number and the MASK so as to verify the identity of the intelligent vehicle; and based on the established connection, the intelligent vehicle and the server use the symmetric encryption algorithm to perform bidirectional communication. The secure communication method based on an intelligent vehicle can remove three hidden dangers that the communication content is eavesdropped; the communication identity is camouflaged; and the communication content is tampered during the communication process between the intelligent vehicle and the server.
Owner:ZHEJIANG UNIV
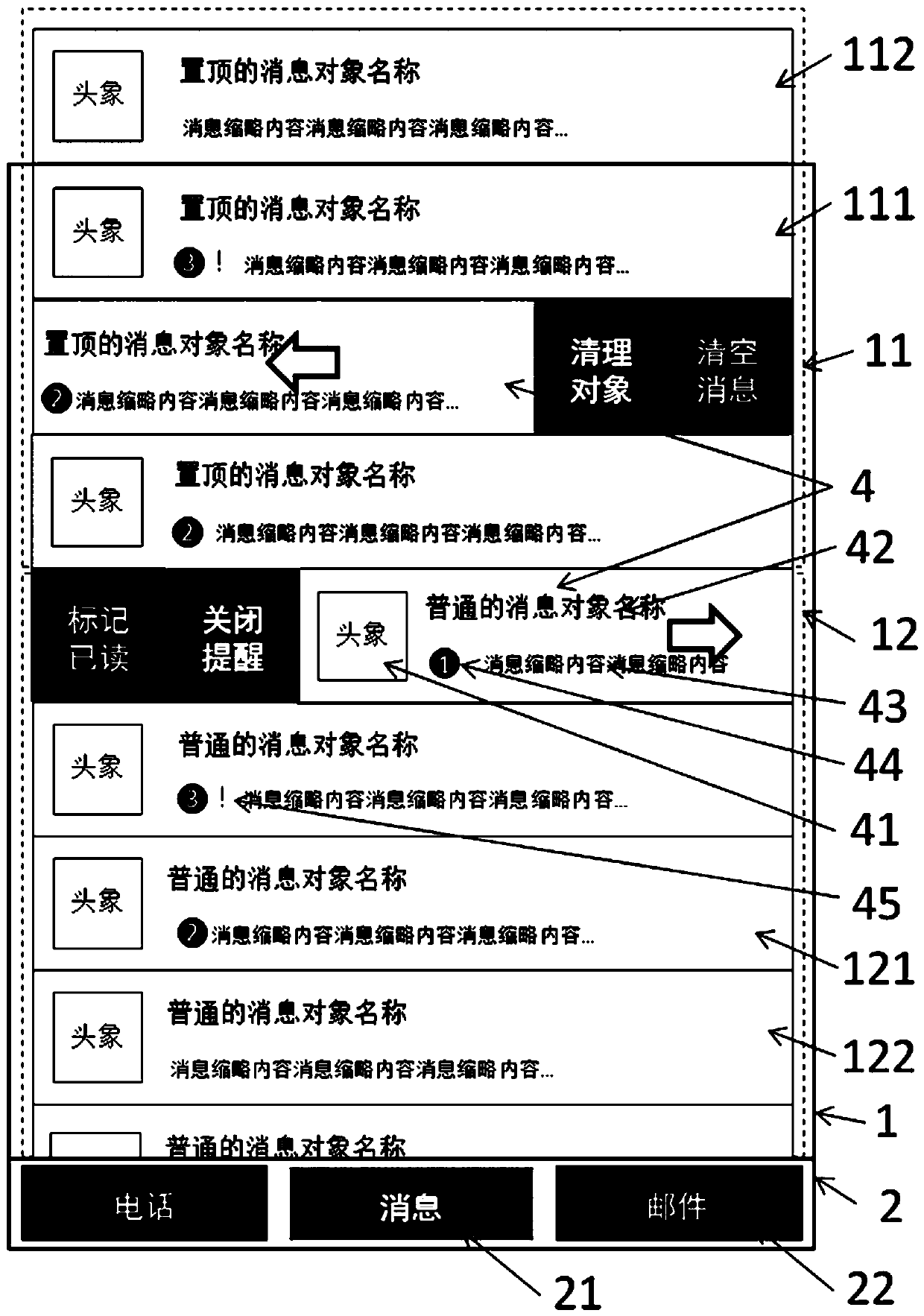
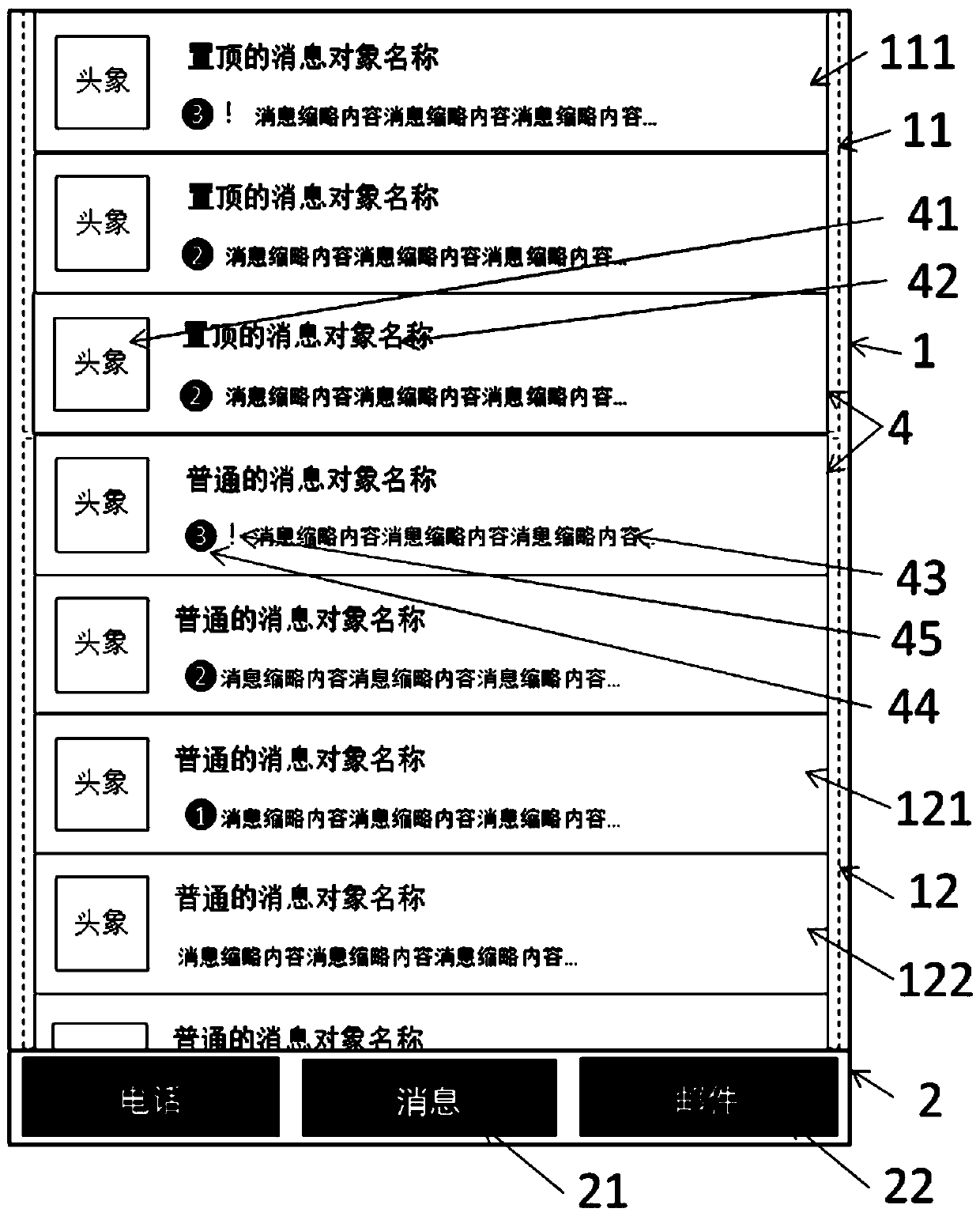
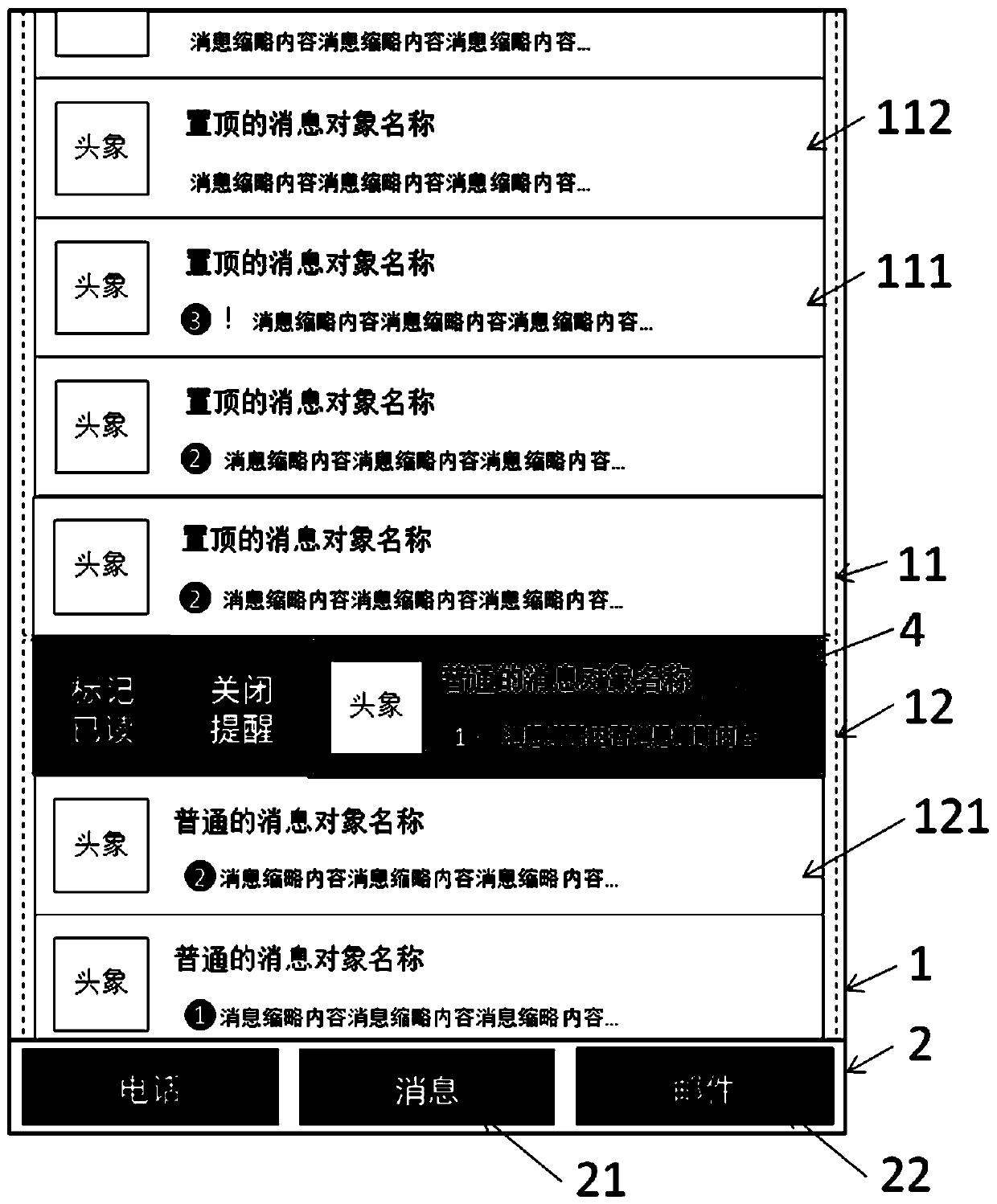
Message object list display method
InactiveCN107943376ADoes not affect viewingEasy to viewInput/output processes for data processingComputer hardwareEngineering
The invention discloses a message object list display method. The method comprises a content area and a function tab bar, wherein the content area comprises a stick area and a common area; the function tab bar is arranged at the bottom; message read sticky objects are hidden in the stick area in a rolling manner; reminding cancelled objects do not participate updating and sorting; through markingread and unread, positions of the objects can be changed; for each line of objects, head portraits, names, breviary messages, unread message number and important prompt icons are displayed; and through long-pressing popup menus or trailing objects, functions such as state switching of read marking, unread marking, prompt cancelling, prompt recovery, sticking and sticking cancelling, message emptying, object clearing are realized. The method has the advantages of eminently pay close attention to emphasis, avoiding interference, being flexible in setting and simple to operate, and enabling liststo be more clean and tidy.
Owner:ZHEJIANG HUINAO INFORMATION TECH CO LTD
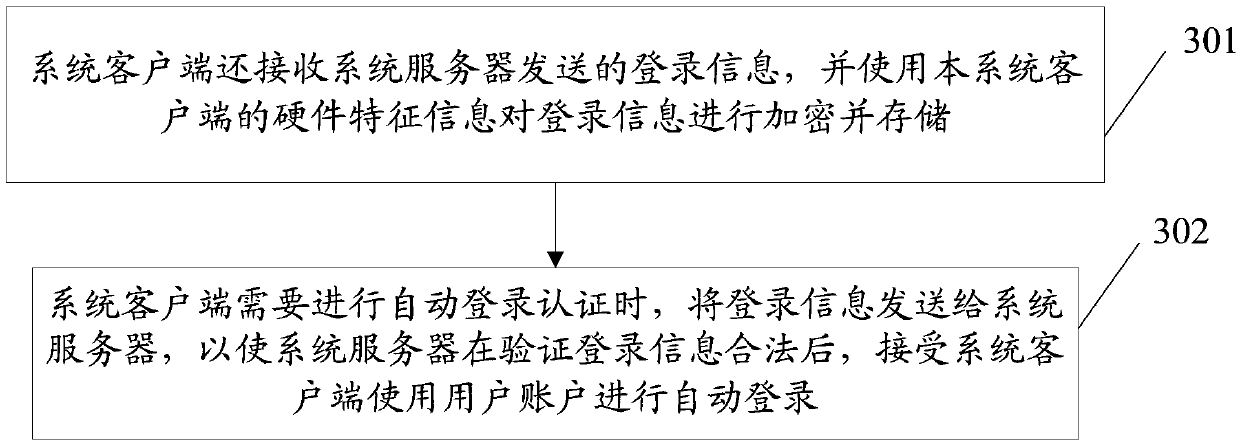
Login method, terminal device and communication system
The invention discloses a login method, a terminal device and a communication system. The method comprises that: a software client builds long connection with a software server and applies for safe starting parameters; the software client applies to a system server for a temporary certificate through a system client, wherein the application comprises the safe starting parameters; the system server generates the temporary certificate; after receiving the temporary certificate, the software server searches a first database to obtain a first safe starting parameter according to the connection information of the long connection and sends the temporary certificate and the first safe starting parameter to the system server; the system server searches a second database according to the first safe starting parameter so as to obtain a second safe starting parameter and a login certificate and returns the login certificate when the two parameters are in accord; the software server sends the login certificate to an account server for verification and accepts login of the software client after the verification is successful.
Owner:NETEASE (HANGZHOU) NETWORK CO LTD
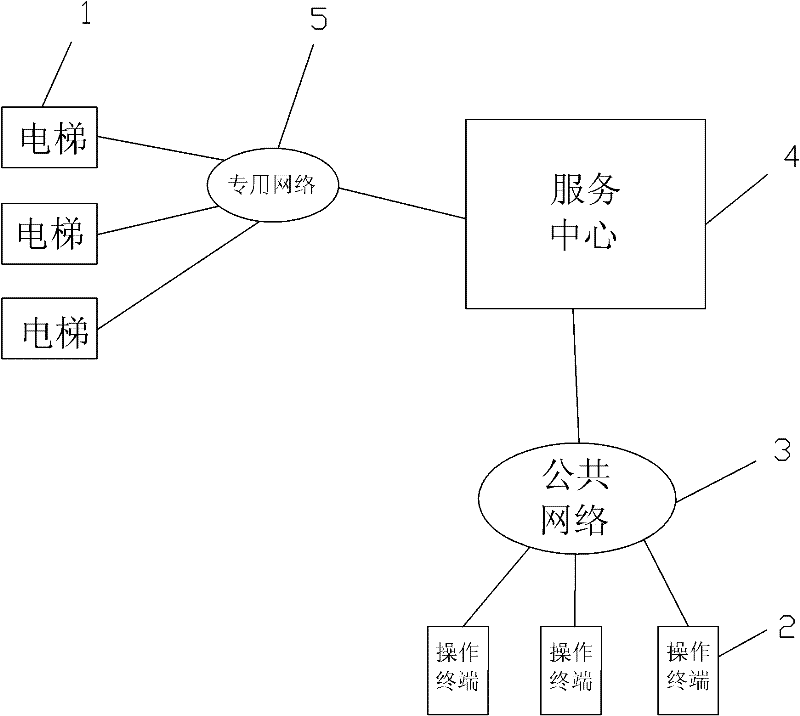
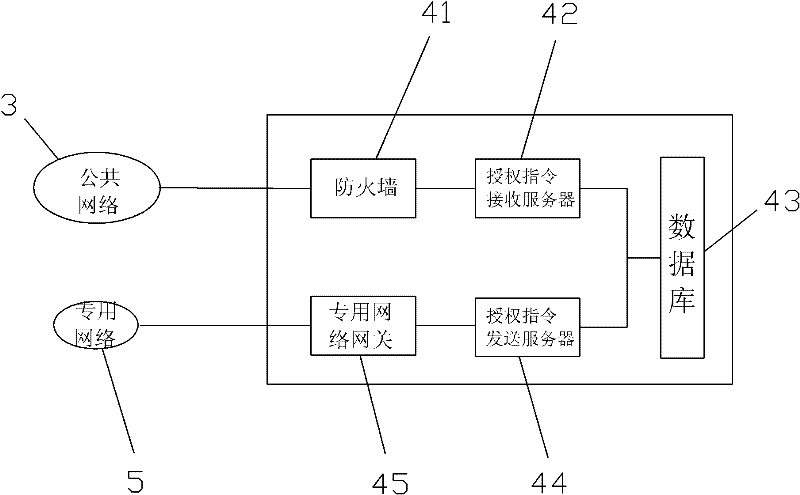
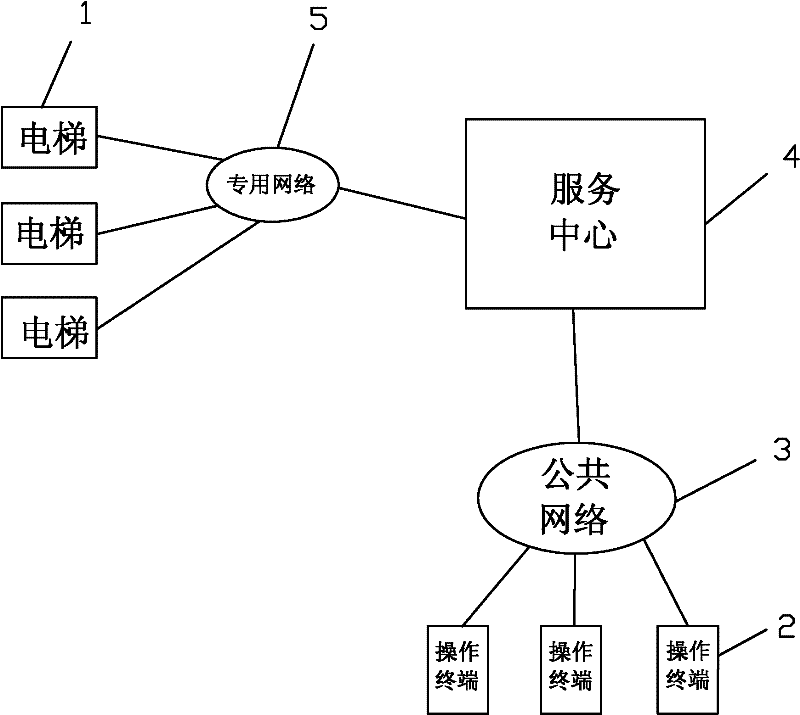
Remote elevator authorization management system and method
The invention relates to a remote elevator authorization management system and a method. The system comprises elevators, operating terminals, a public network, a service center, a private network and an elevator controller, wherein the operating terminals send authorization commands to the service center via the public network; after carrying out security auditing on the permissions of the operating terminals, the service center detects the elevator conditions via the private network and sends an authorization command to the elevator controller; and the elevator controller releases the operation of limiting the elevators according to the authorization command and the elevator conditions. The system and the method have the following beneficial effects: the ordinary operating terminals are used for elevator authorization, the centralized service center is used for receiving the information of the ordinary operating terminals, various security technologies are used for security auditing, professional staff are used for monitoring, the technical means is continuously upgraded and the private network is directly connected to the elevator controller, thus avoiding changing elevator lines and adding additional lines, and improving the elevator security.
Owner:HITACHI ELEVATOR CHINA
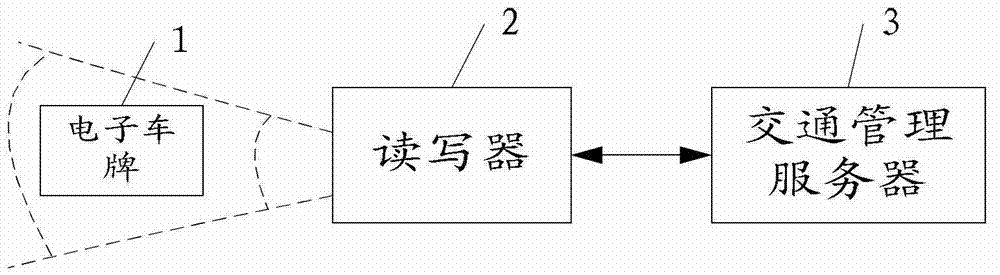
Electronic license plate and method for reading information from electronic license plate
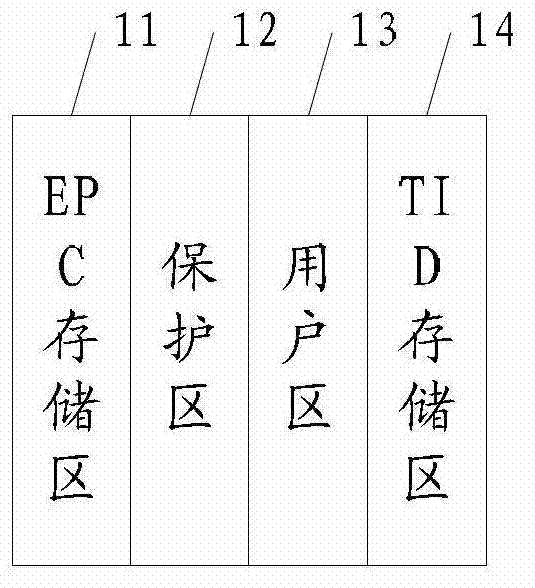
InactiveCN103042998AEnable selective readImprove reading efficiencySensing record carriersVehicle componentsPersonalizationLicense
The invention provides an electronic license plate and a method for reading information from the electronic license plate. The electronic license plate comprises an electronic product code (EPC) storage area and a user area, wherein the EPC storage area is used for storing common management information of vehicles, and the user area is used for storing individualized information of vehicles. The electronic license plate is partitioned, so that the information inside the electronic license plate can be read selectively, and the reading efficiency can be improved.
Owner:重庆市城投金卡信息产业(集团)股份有限公司
Electronic license plate and method for reading information in electronic license plate
ActiveCN103496350AEnable selective readImprove reading efficiencySensing record carriersVehicle componentsPersonalizationLicense
The invention provides an electronic license plate and a method for reading information from the electronic license plate. The electronic license plate comprises an electronic product code (EPC) storage area and a user area, wherein the EPC storage area is used for storing common management information of vehicles, and the user area is used for storing individualized information of vehicles. The electronic license plate is partitioned, so that the information inside the electronic license plate can be read selectively, and the reading efficiency can be improved.
Owner:重庆市城投金卡信息产业(集团)股份有限公司
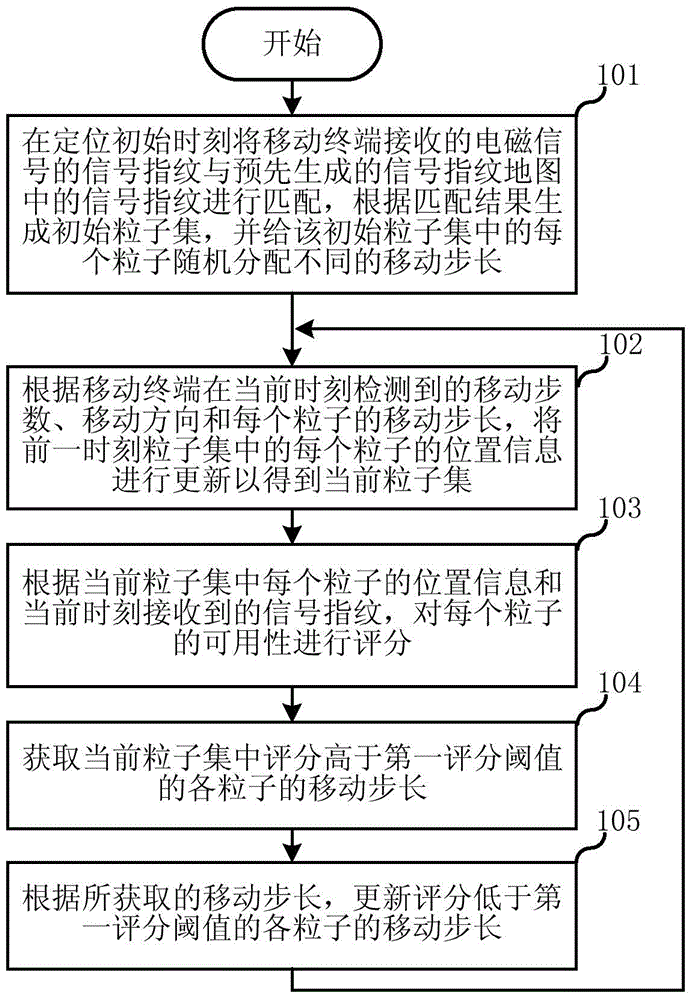
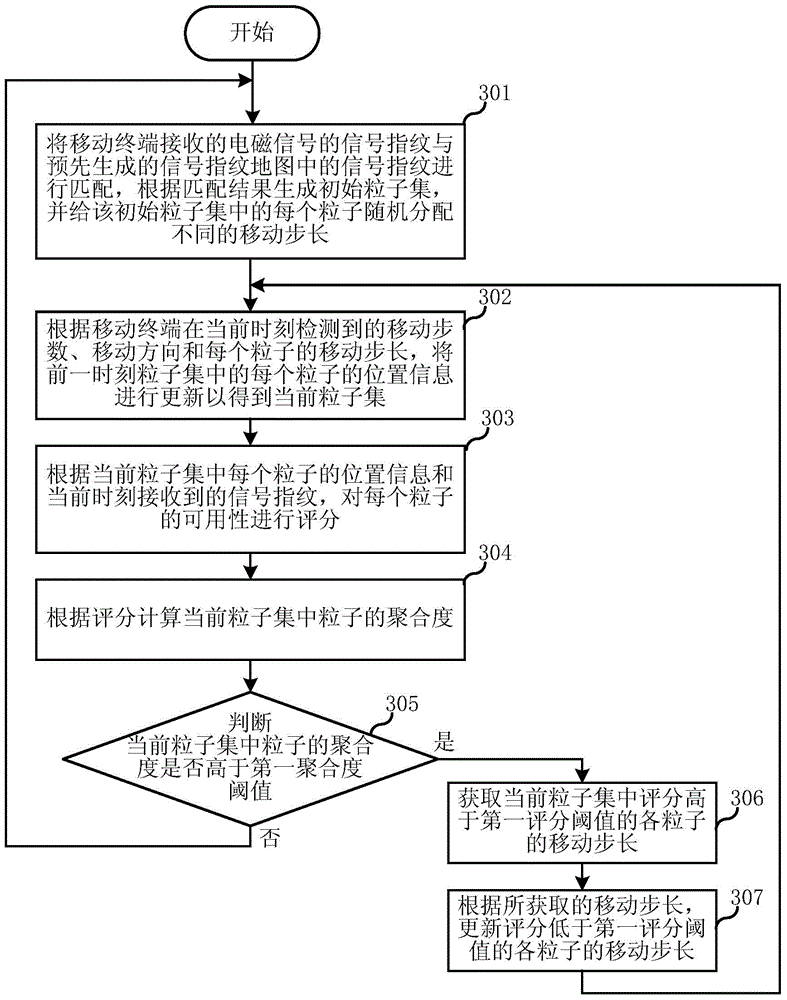
Mobile terminal location method on the basis of electromagnetic signals and mobile terminal location device on the basis of electromagnetic signals
ActiveCN105451330AMove step heightMove step in timeParticular environment based servicesPosition fixationComputational physicsElectromagnetic shielding
The present invention relates to the communication field, and discloses a mobile terminal location method on the basis of electromagnetic signals and a mobile terminal location device on the basis of electromagnetic signals. The mobile terminal location method comprises the following steps: generating an initial particle set at the location initial moment, performing random distribution of different moving step lengths to each particle in the initial particle set; repeatedly executing the following step: updating the position information of each particle in the particle set at the previous time to obtain the current particle set; scoring the availability of each particle according to the position information of each particle in the current particle set and the signal fingerprint received at present; acquiring the moving step length of each particle which has a score higher than a first preset threshold value in the current particle set; updating the moving step length of each particle which has a score lower than the first preset threshold value according to the acquired moving step lengths. According to the invention, the moving step length being closest to the actual step length of a located person may be obtained in the location process, and is able to update the moving step length with the changing of the step length of the located person.
Owner:ALIBABA GRP HLDG LTD
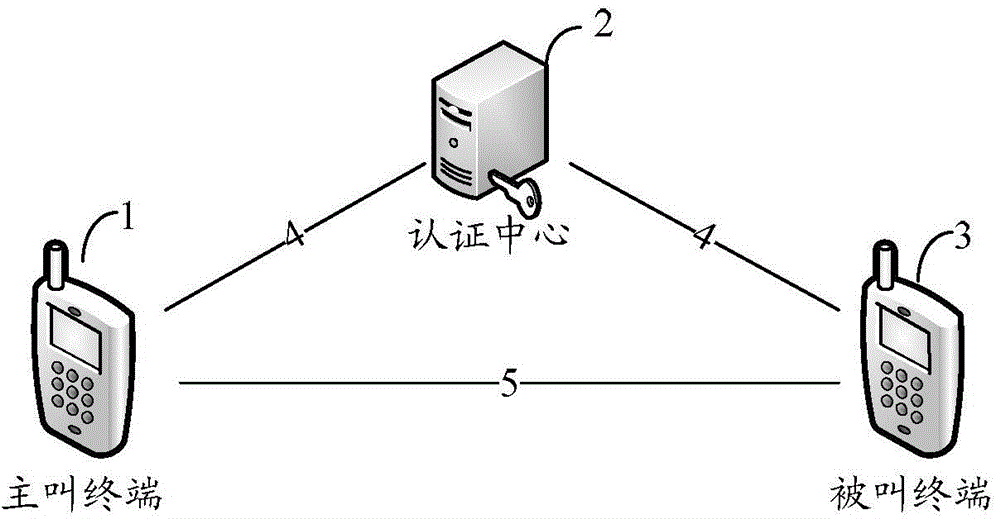
Method and system for secure call and terminals
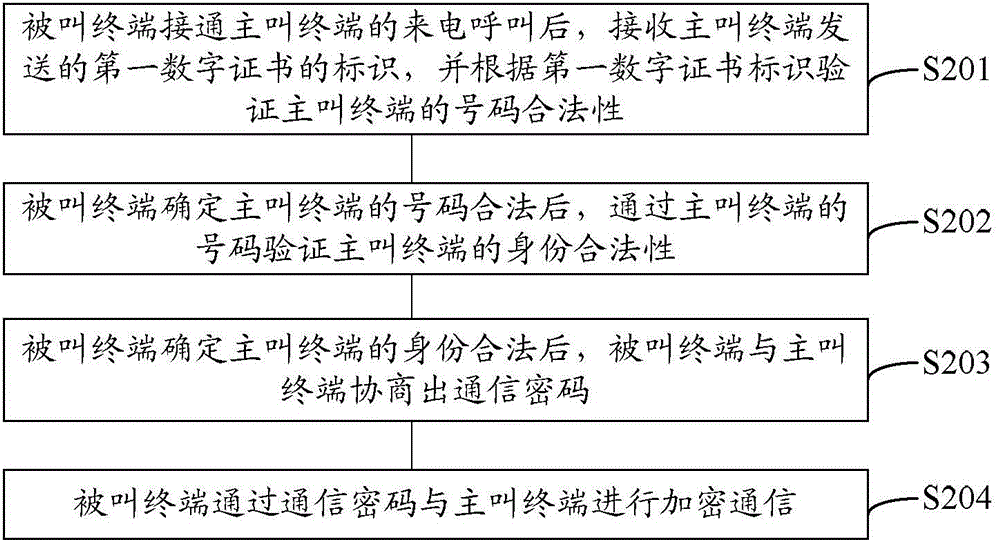
InactiveCN105790942APrevent camouflageImprove securityUser identity/authority verificationSecurity arrangementComputer terminalComputer science
Embodiments of the invention disclose a method and a system for a secure call and terminals. The method comprises the following steps that a called terminal receives an identifier of a first digital certificate sent by a calling terminal and verifies the legality of a number of the calling terminal according to the identifier of the first digital certificate after the called terminal is connected to an incoming call of the calling terminal; the called terminal verifies the legality of the identity of the calling terminal according to the number of the calling terminal after the called terminal determines that the number of the calling terminal is legal; a signal code is negotiated by the called terminal and the calling terminal after the called terminal determines that the identity of the calling terminal is legal; and the called terminal carries out encryption communication with the calling terminal through the signal code.
Owner:ZTE CORP
Identification system and method of industrial control equipment, medium and electronic equipment
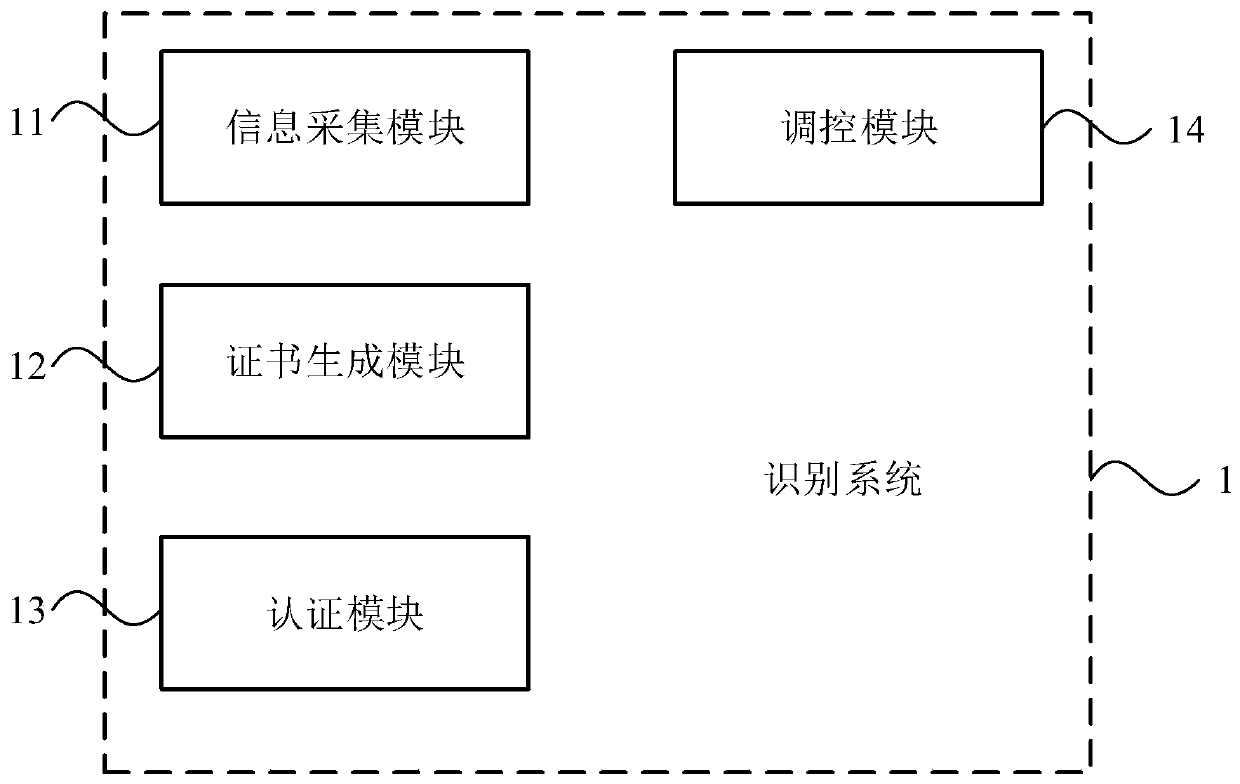
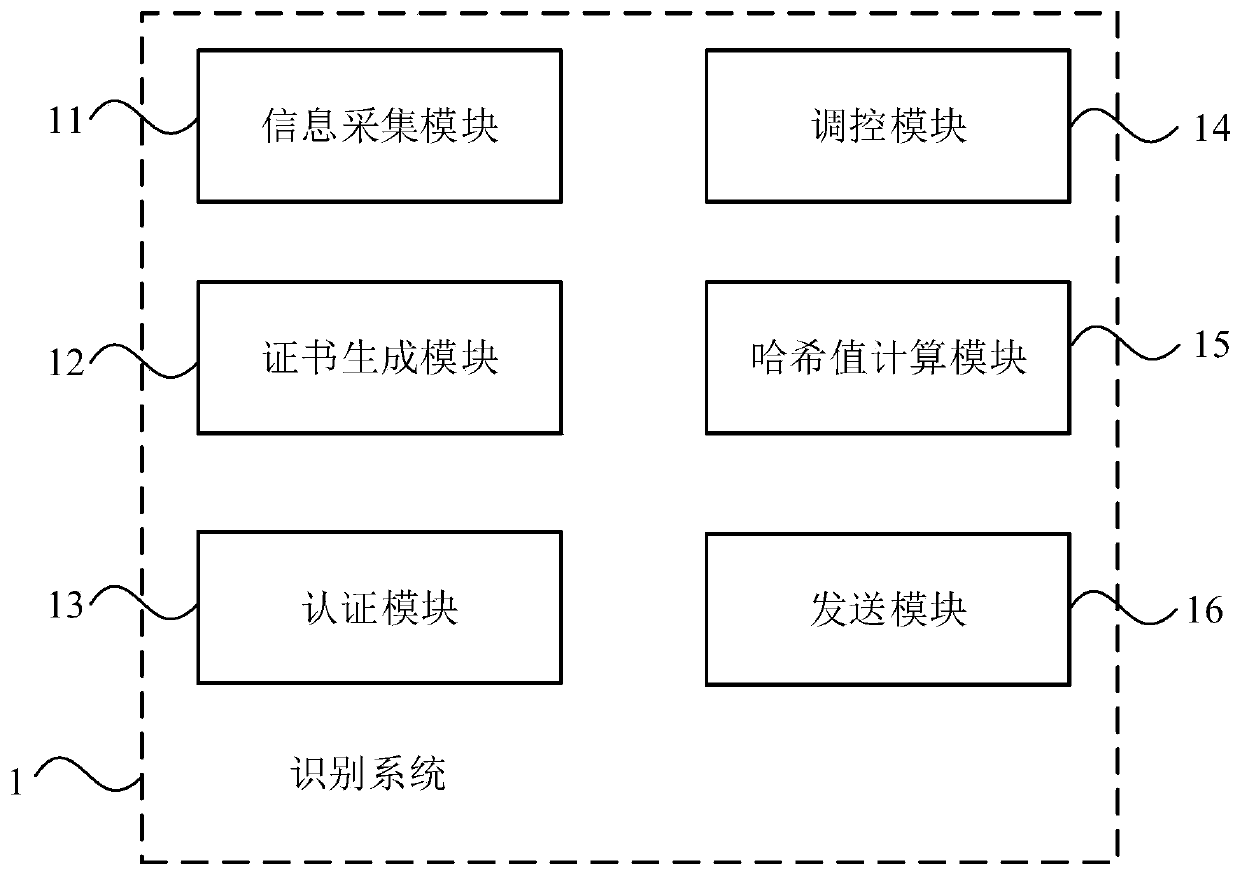
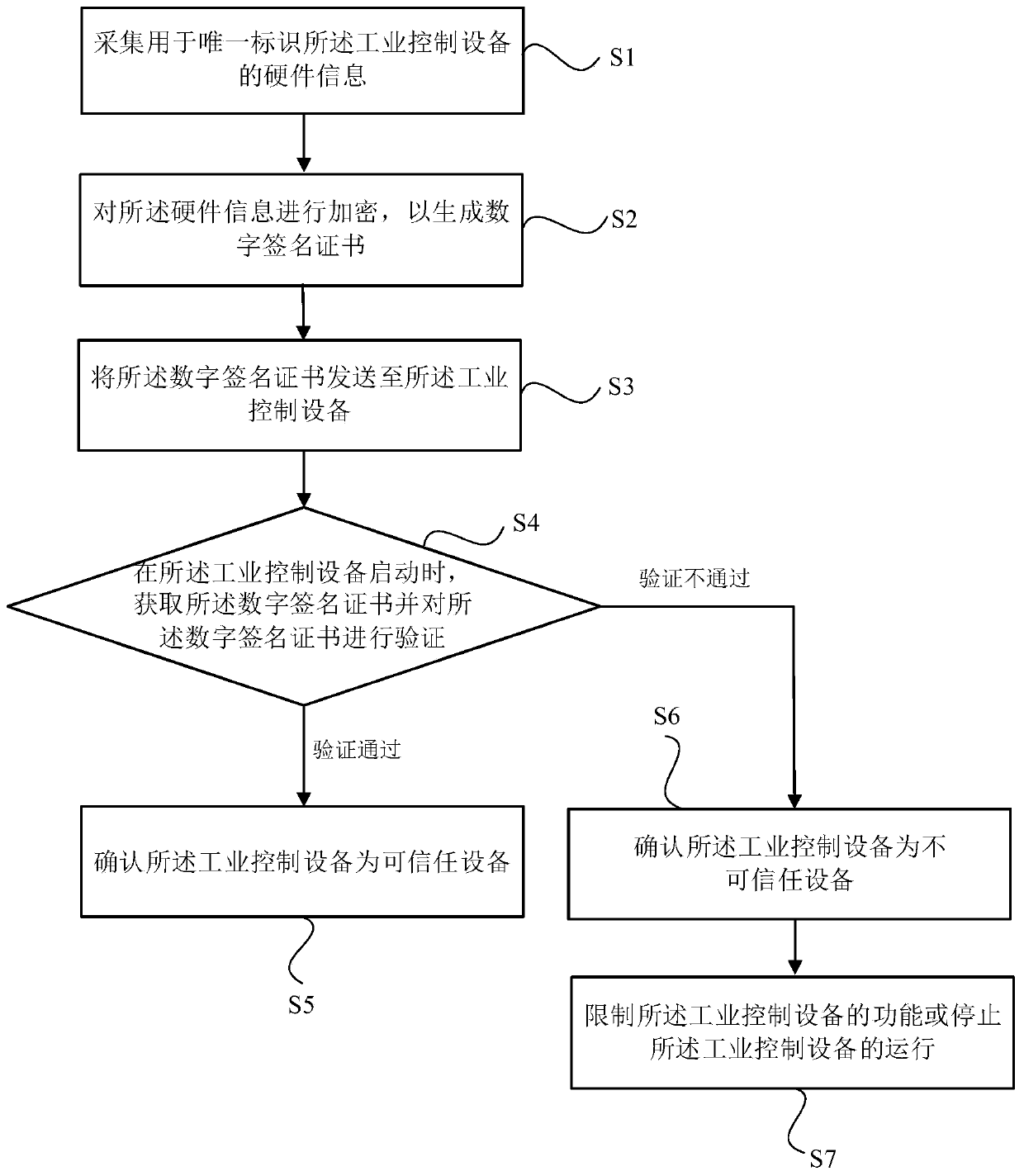
PendingCN111030824ARandom combinationGuarantee information securityEncryption apparatus with shift registers/memoriesUser identity/authority verificationDigital signatureInformation security
The invention discloses an identification system and method for industrial control equipment, a medium and electronic equipment. The identification system comprises an information acquisition module and a certificate generation module. The information acquisition module is used for acquiring hardware information for uniquely identifying the industrial control equipment. The certificate generationmodule is used for encrypting the hardware information to generate a digital signature certificate. According to the invention, the digital signature certificate can be generated by utilizing the hardware information uniquely identifying the industrial control equipment before the equipment leaves a factory; and the identity or the source of the industrial control equipment can be identified through the digital signature certificate, so that the identification accuracy is improved, illegal equipment is effectively prevented from being disguised as legal equipment, and the information securityof an industrial control system is guaranteed.
Owner:STATE NUCLEAR POWER AUTOMATION SYST ENGCO
Safety prompting method, device and communication system
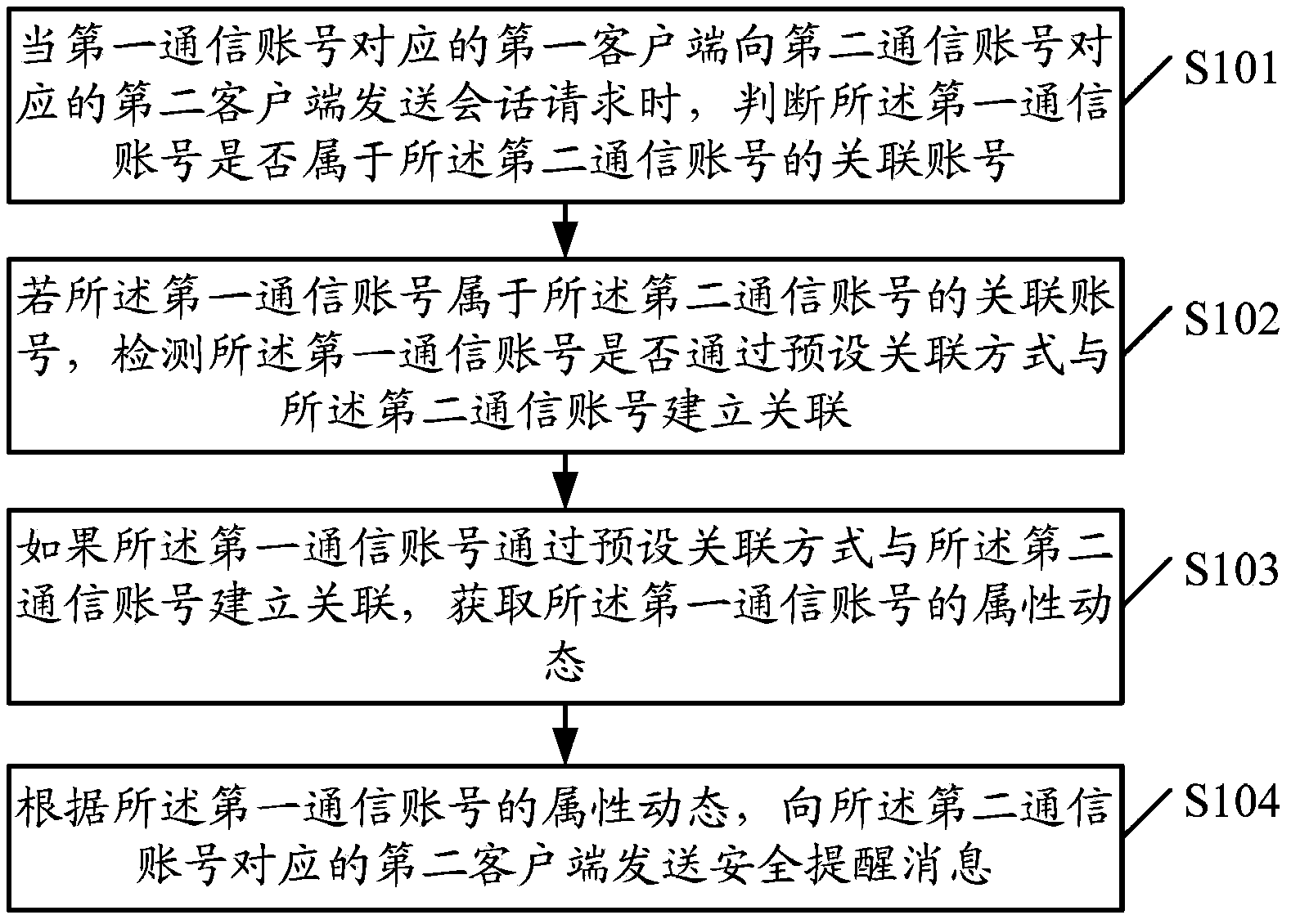
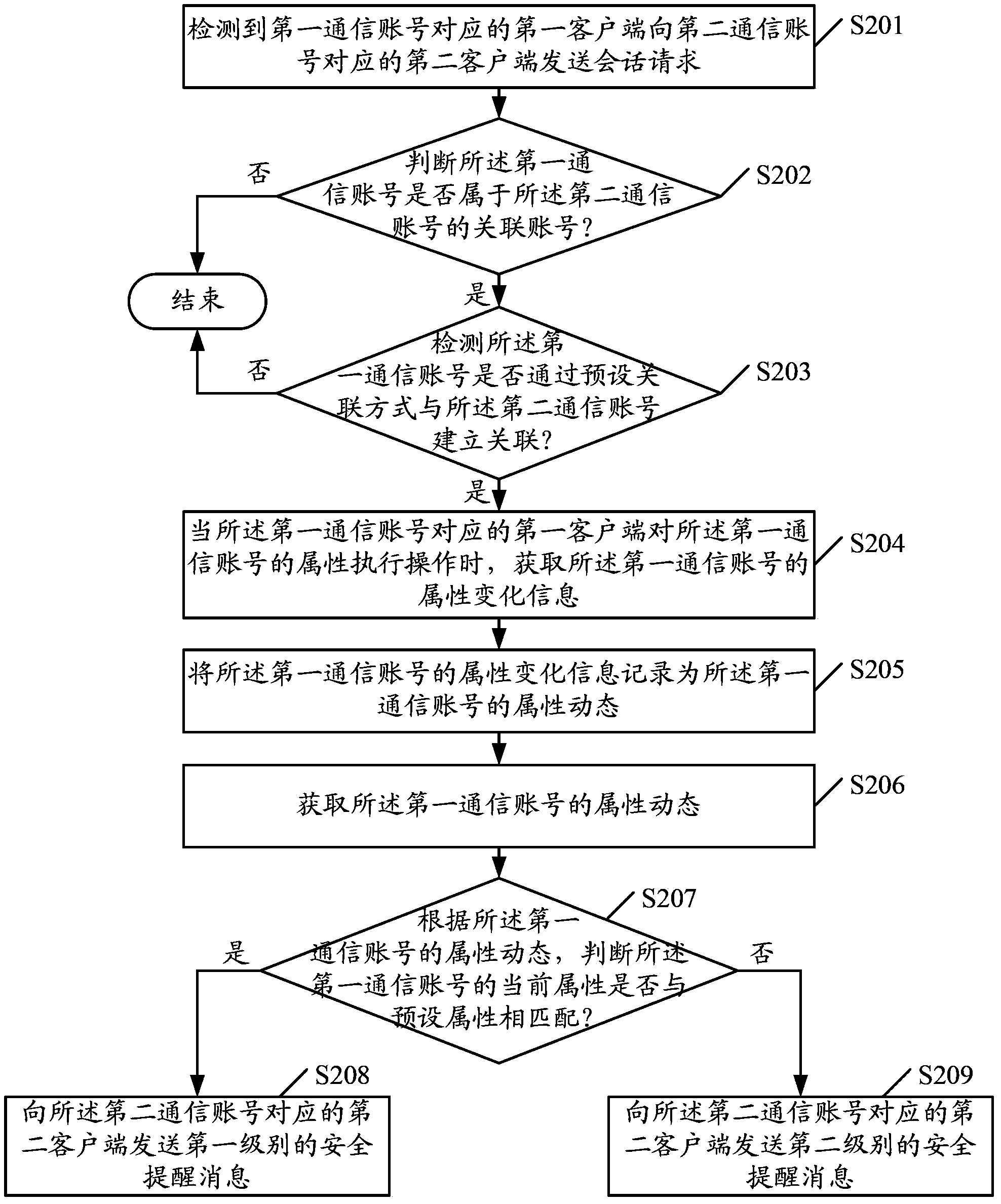
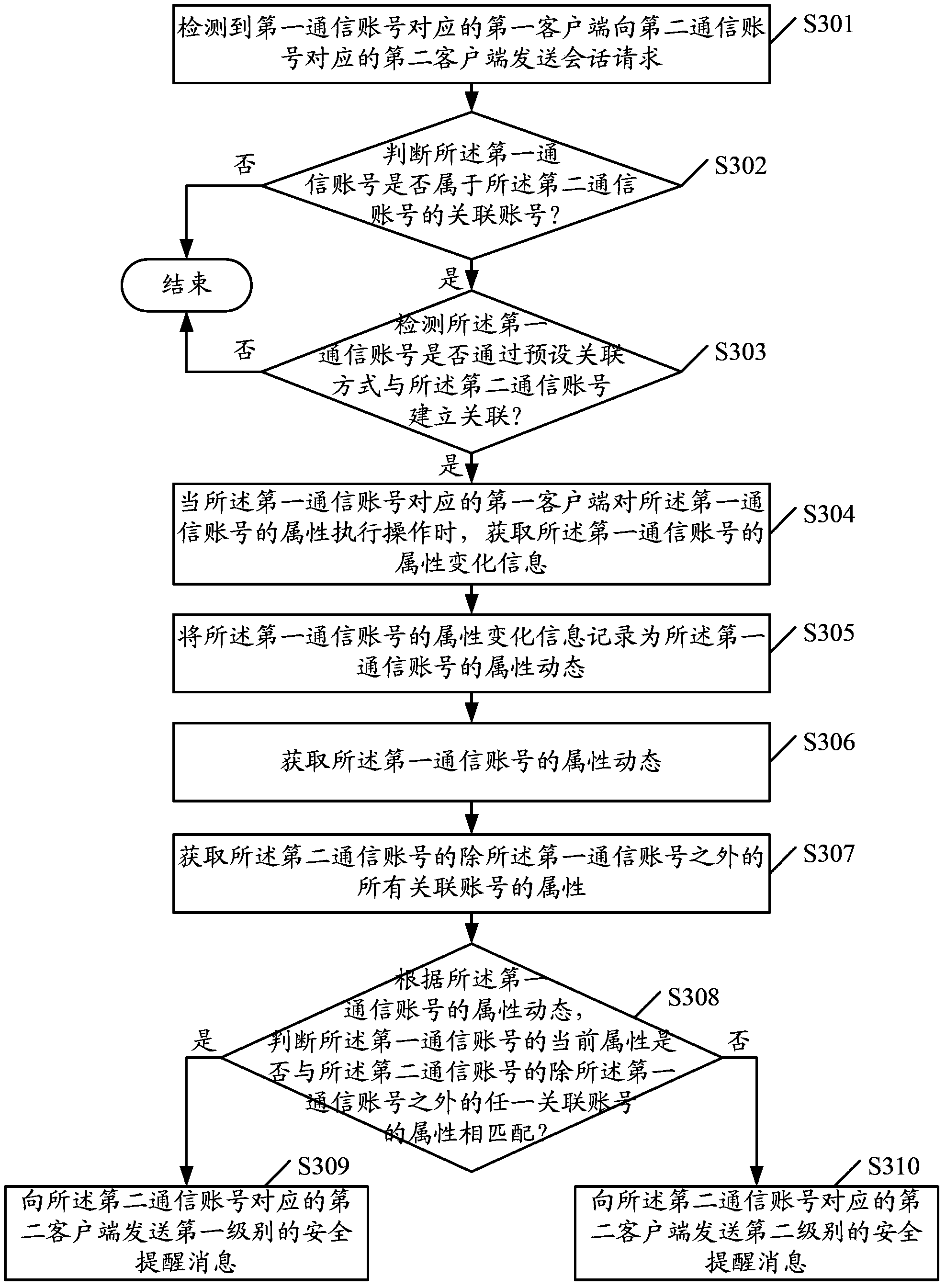
ActiveCN104125130APrevent information masqueradingImprove information securityData switching networksClient-sideReal-time computing
The embodiment of the invention provides a safety prompting method, a device and a system. the method can contains the following steps: when a first client corresponding to a first communication account sends a session request to a second client corresponding to a second communication account, whether the first communication account belongs to an associated account of the second communication account is judged; if the first communication account belongs to an associated account of the second communication account, whether a relationship between the first communication account and the second communication account is established through a preset association mode is detected; if the relationship between the first communication account and the second communication account is established through the preset association mode, attribute dynamic condition of the first communication account is obtained; and a safety prompting message is sent to the second client corresponding to the second communication account according to the attribute dynamic condition of the first communication account. According to the invention, Internet information camouflage can be prevented effectively, and information security during information interaction process is raised.
Owner:TENCENT TECH (SHENZHEN) CO LTD
Link state maintenance method and device
ActiveCN109981468ASolve the inability to know non-adjacent nodesResolution statusData switching networksTelecommunications linkCommunication link
The invention provides a link state maintenance method and device. The method comprises the following steps: selecting at least one of a plurality of superior nodes corresponding to a current node according to a priority to establish a communication link; first dynamic routing information is broadcasted to the corresponding superior node through the communication link; and receiving second dynamicrouting information broadcasted by the corresponding upper-level node through the communication link and broadcasting the second dynamic routing information to the lower-level node communicated withthe current node. Wherein during static configuration, the lower-level node selects the upper-level node according to the priority, and supports the situation that the lower-level node simultaneouslycorresponds to a plurality of upper-level nodes, so that information can be transmitted through other upper-level nodes when the upper-level node is abnormal, transmission interruption is avoided, thetransmission reliability is improved, and the application requirement can be met. In addition, non-adjacent node link state maintenance is supported through dynamic routing state broadcast, and the transmission reliability is further improved.
Owner:THE PEOPLES BANK OF CHINA NAT CLEARING CENT
Self-service bank monitoring system
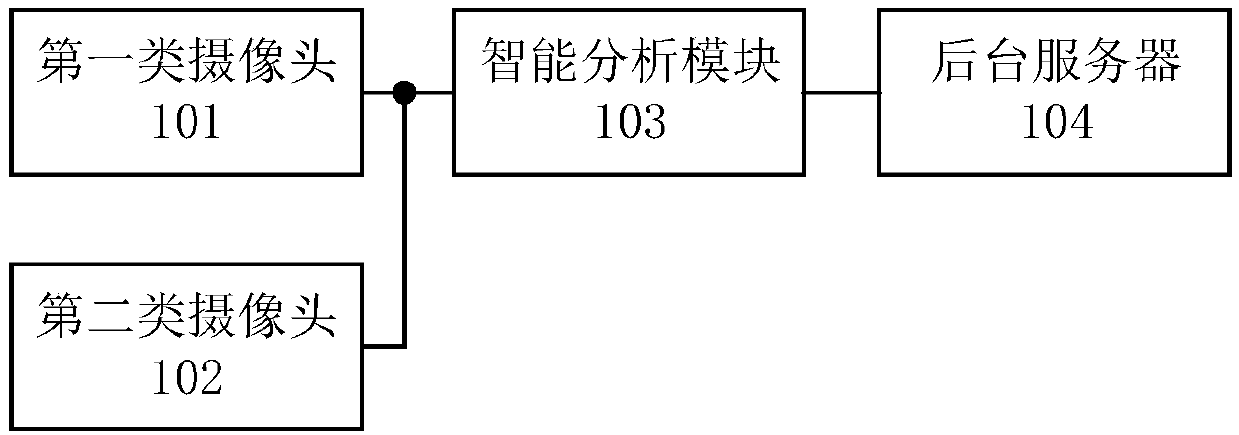
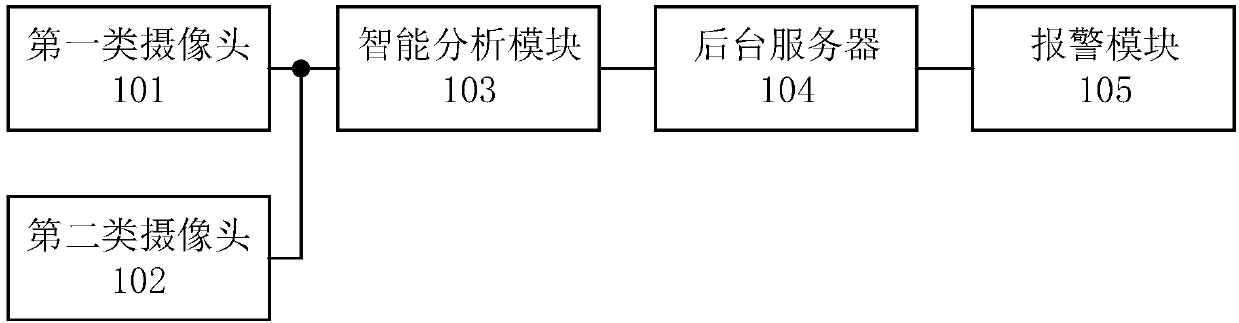
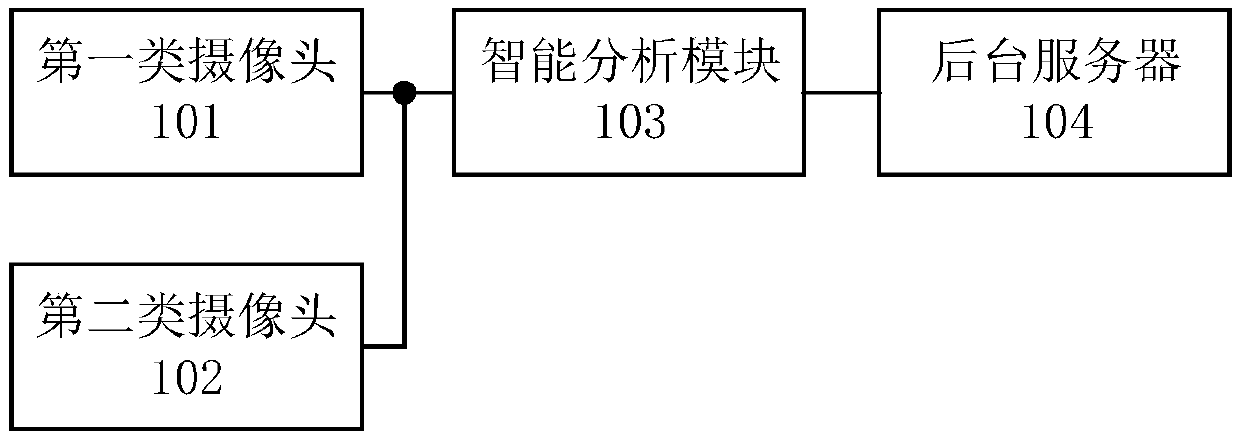
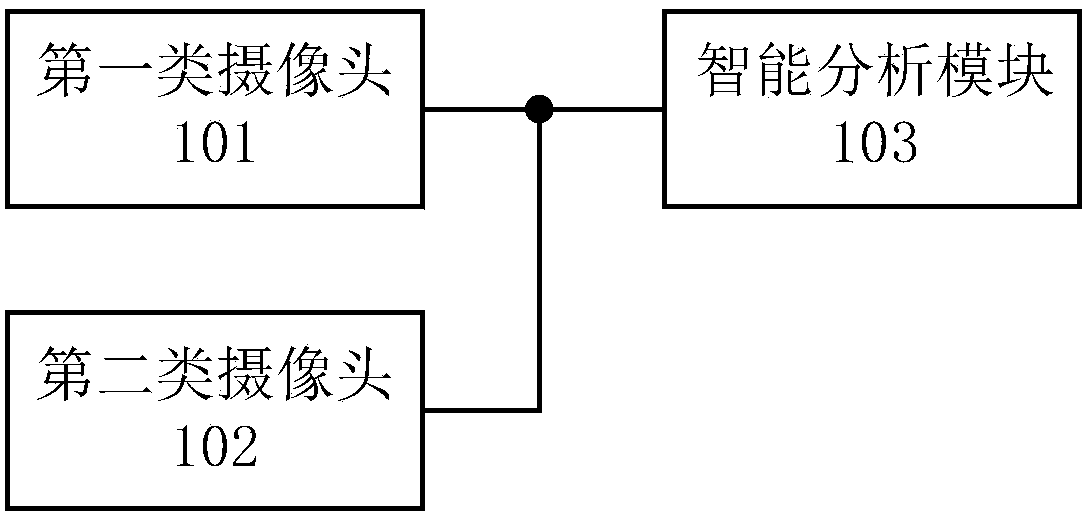
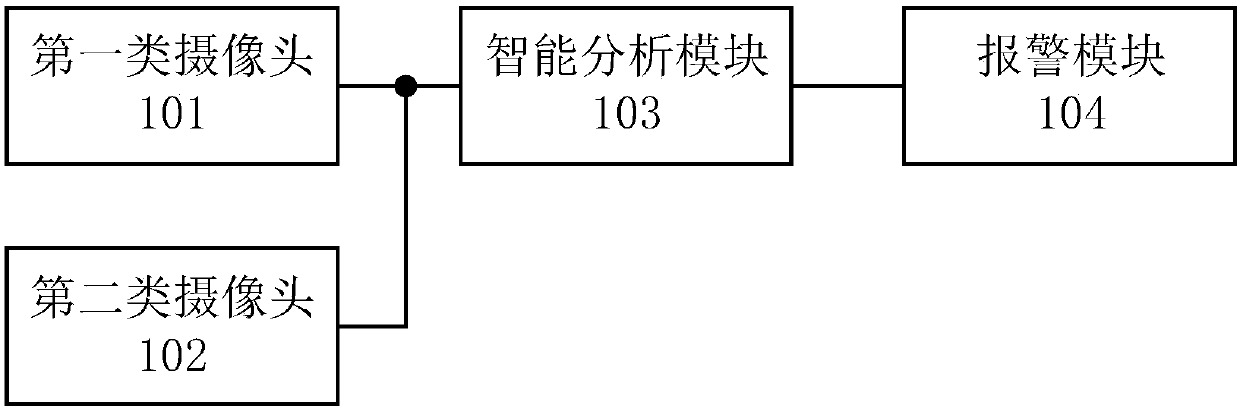
InactiveCN109961587APrevent camouflageGet analysis results in real timeComplete banking machinesClosed circuit television systemsMonitoring systemComputer module
The invention discloses a self-service bank monitoring system, which comprises first-type cameras, second-type cameras, an intelligent analysis module and a background server, wherein the first-type cameras comprise at least two environmental monitoring cameras arranged in different positions in the self-service bank; each environmental monitoring camera is respectively connected with the intelligent analysis module for collecting environmental information in the self-service bank and transmitting the collected first-type video stream to the intelligent analysis module in real time; the second-type camera is arranged in an automatic teller machine and is connected with the intelligent analysis module for collecting the information of a person operating on the automatic teller machine and transmitting the collected second-type video stream to the intelligent analysis module in real time; the intelligent analysis module is used for recognizing faces in the first-type video stream and thesecond-type video stream and performing correlation analysis on the first-type video stream and the second-type video stream to generate an analysis result; and the background server is used for receiving the analysis result.
Owner:TENDYRON CORP
Logistics safety payment method for realizing payment in cash on delivery
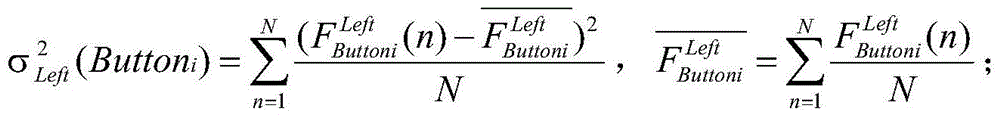
InactiveCN105761063AGuarantee property securityPrevent camouflageLogisticsProtocol authorisationKey pressingPassword
The present invention relates to a logistics safety payment method for realizing payment in cash on delivery. Left and right hand pressing database aiming at each button is constructed through the mobile terminal of each recipient when lawful owners are in normal state so as to verify the identity of a payment operator; after an express delivery man's hand-held POS terminal is connected with a recipient's mobile intelligent terminal through an optimum NFC relay, the hand-held POS terminal and the mobile intelligent terminal respectively send each current position and noise and air humidity of the current position and obtain the air humidity to an authentication mechanism; when the authentication mechanism determines the payment both sides are located at the same safe position, transaction secret keys are sent to both sides with payment in cash on delivery; the mobile intelligent terminal sends correct payment passwords inputted by the lawful owners through buttons to a bank system, and the bank system transfers cost to a logistics company account; and after the payment transaction is finished, the logistics company transfers corresponding cost to dealers through the bank system, so that the efficiency and the payment safety of the payment process of payment in cash on delivery are guaranteed.
Owner:ZHEJIANG WANLI UNIV
Electronic voting module and electronic voting method
InactiveCN1471022APrevent tamperingSimple structureVoting apparatusUser identity/authority verificationTime informationNegation
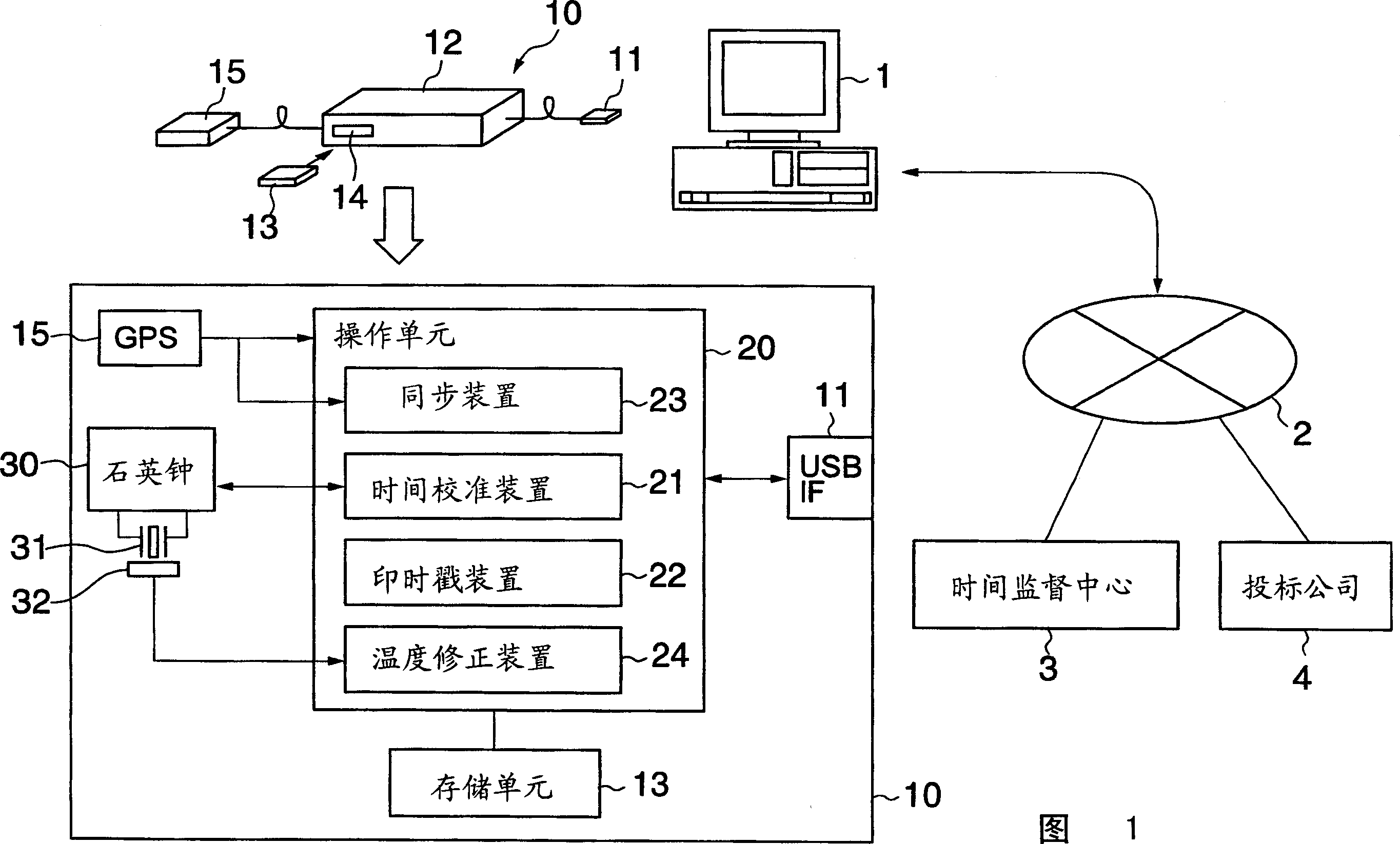
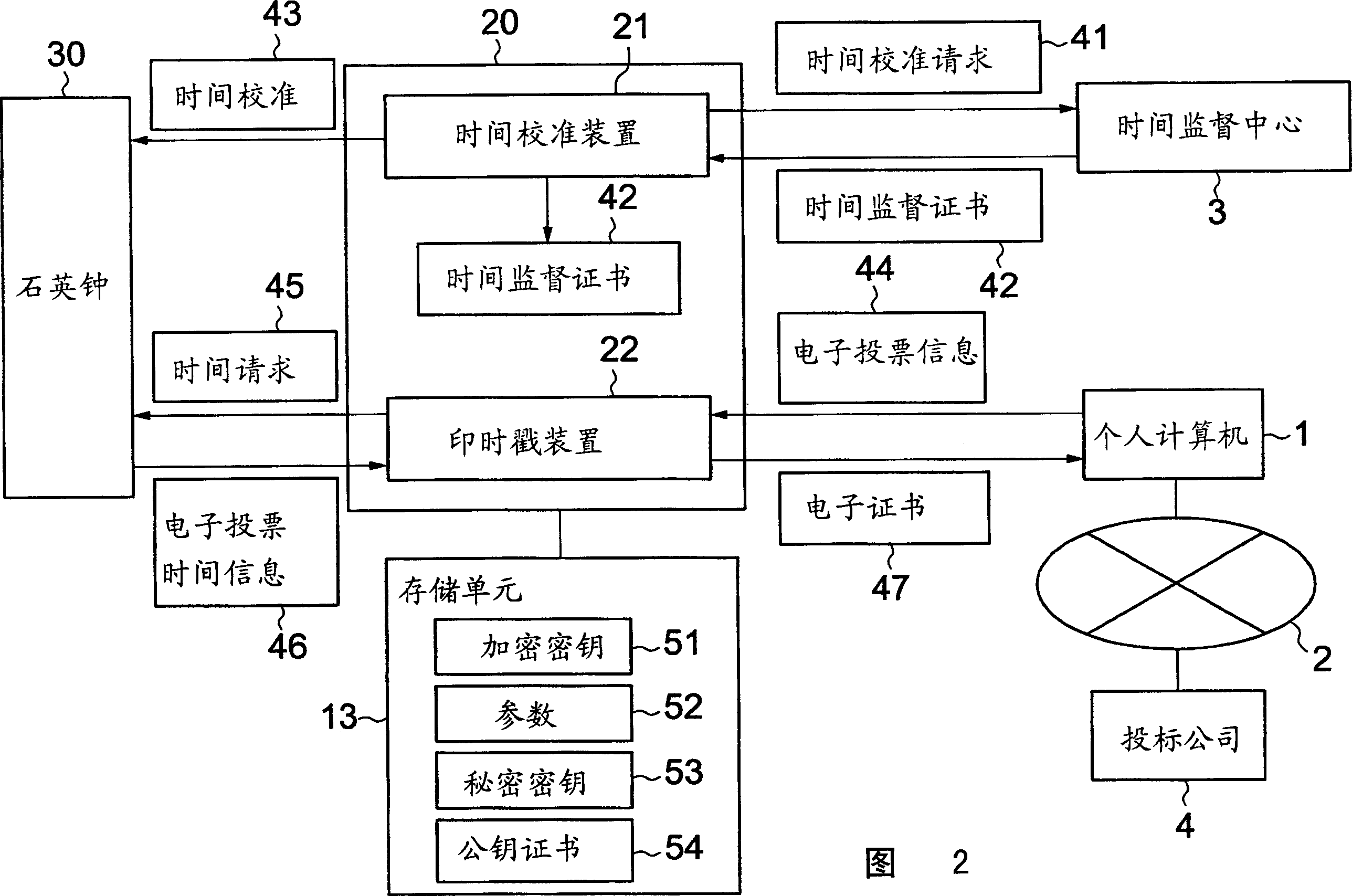
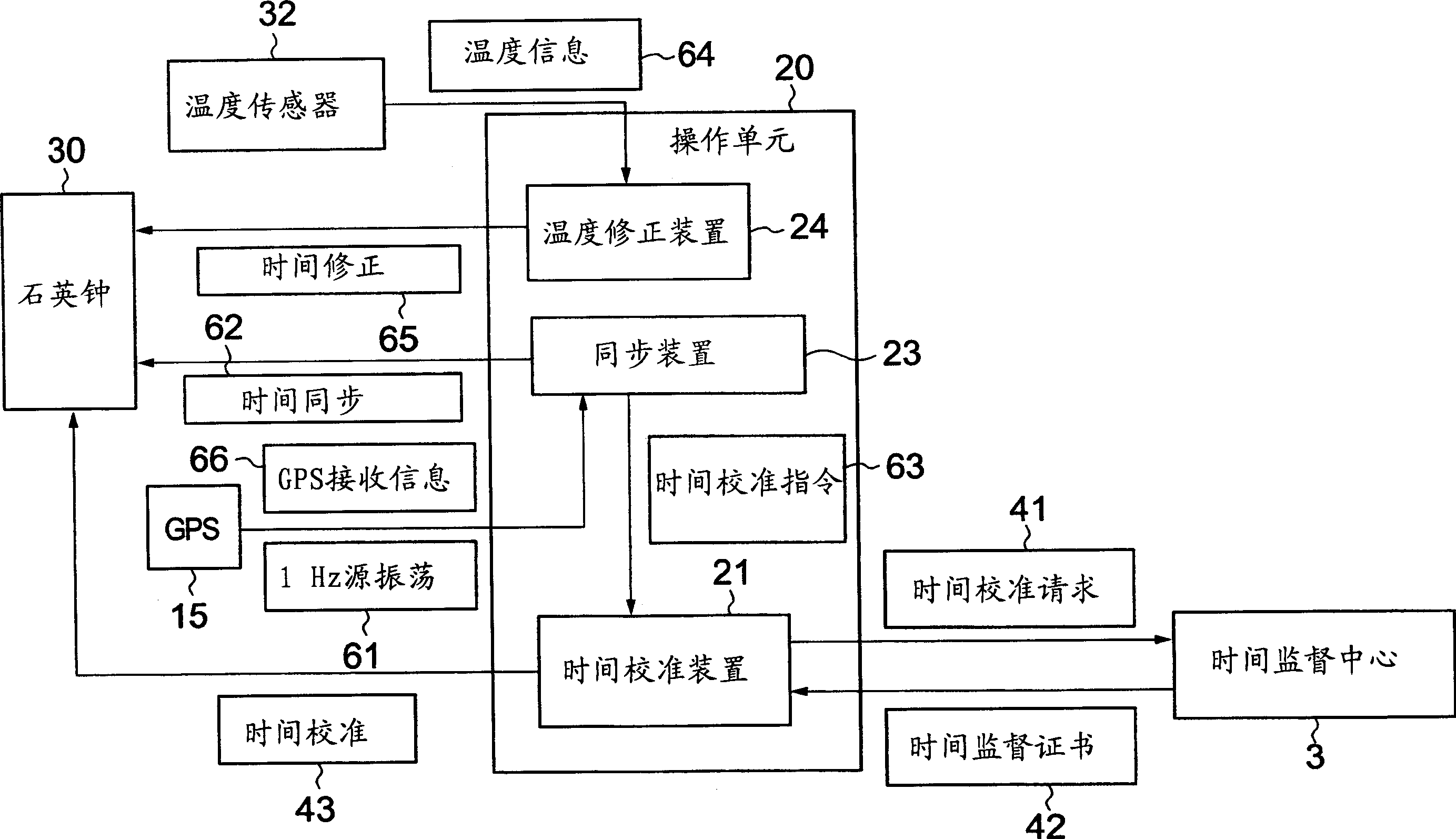
Though simple in construction, an electronic balloting module and an electronic balloting method according to the invention can prevent disguise and negation, can eliminate a time difference resulting from an area difference and can also prevent tampering of an electronic balloting content. The electronic balloting module includes an interface 11 connected to an electronic equipment terminal for conducting electronic balloting through a network, a timepiece for generating time information, a storage unit and an operation unit each having a tamper-resistant structure, time calibration means connected to a predetermined time supervisory center through the electronic equipment terminal at least when the calibration means is operated, subjected to time calibration by the quartz timepiece and receiving a time supervision certificate, and time stamp means for acquiring time information of the time as electronic balloting time information from the quartz timepiece and outputting. an electronic certificate obtained by affixing a signature to the electronic balloting information and the electronic balloting time information by a secrete key of a predetermined public key cipher system with the time supervision certificate to the electronic balloting means provided that the time stamp means receives electronic balloting data from the electronic balloting means of the electronic equipment terminal or electronic balloting information comprising a unidirectional function value of the electronic balloting data.
Owner:SEIKO INSTR INC
Fire wall controlling system and method based on NGN service
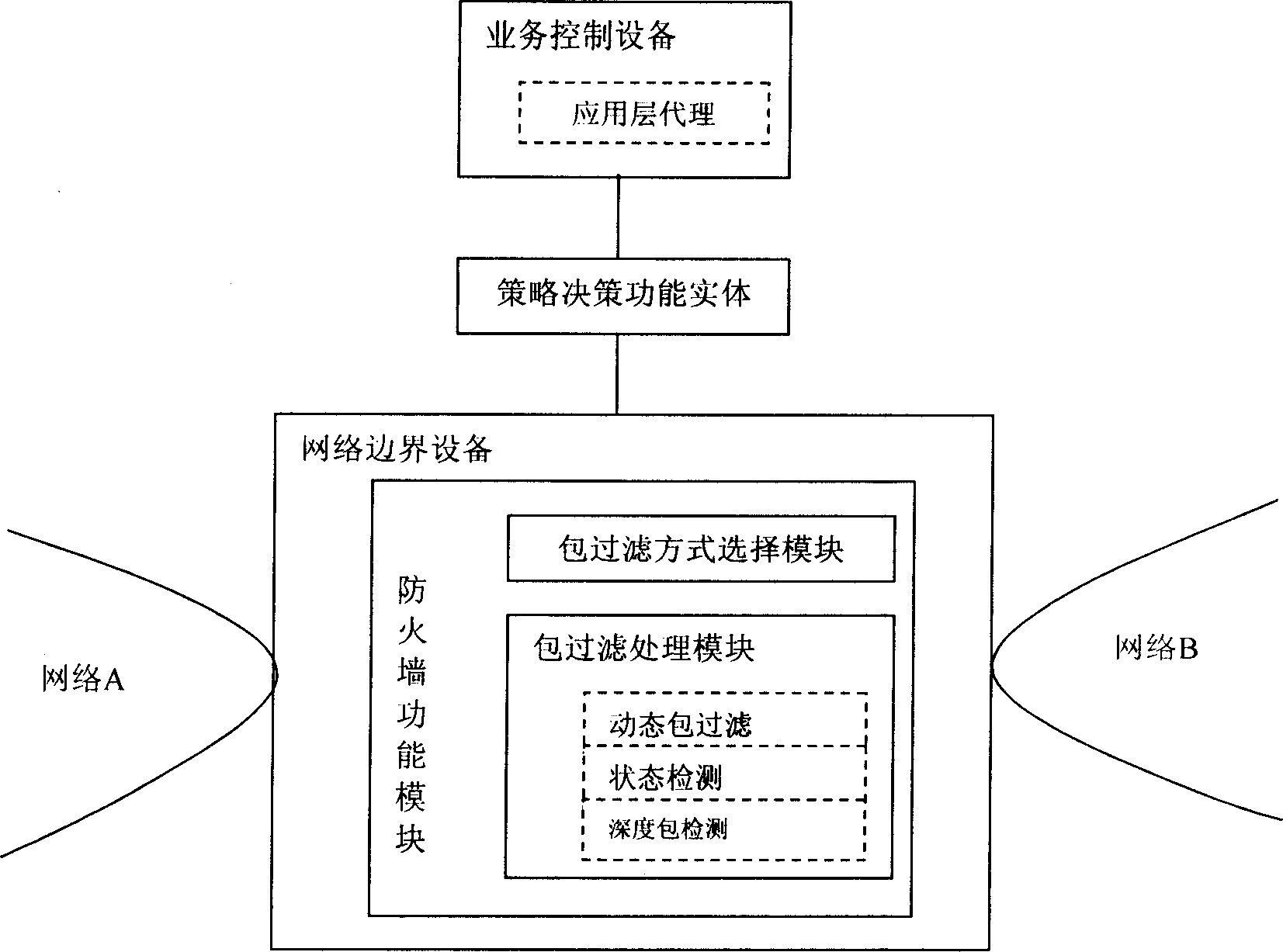
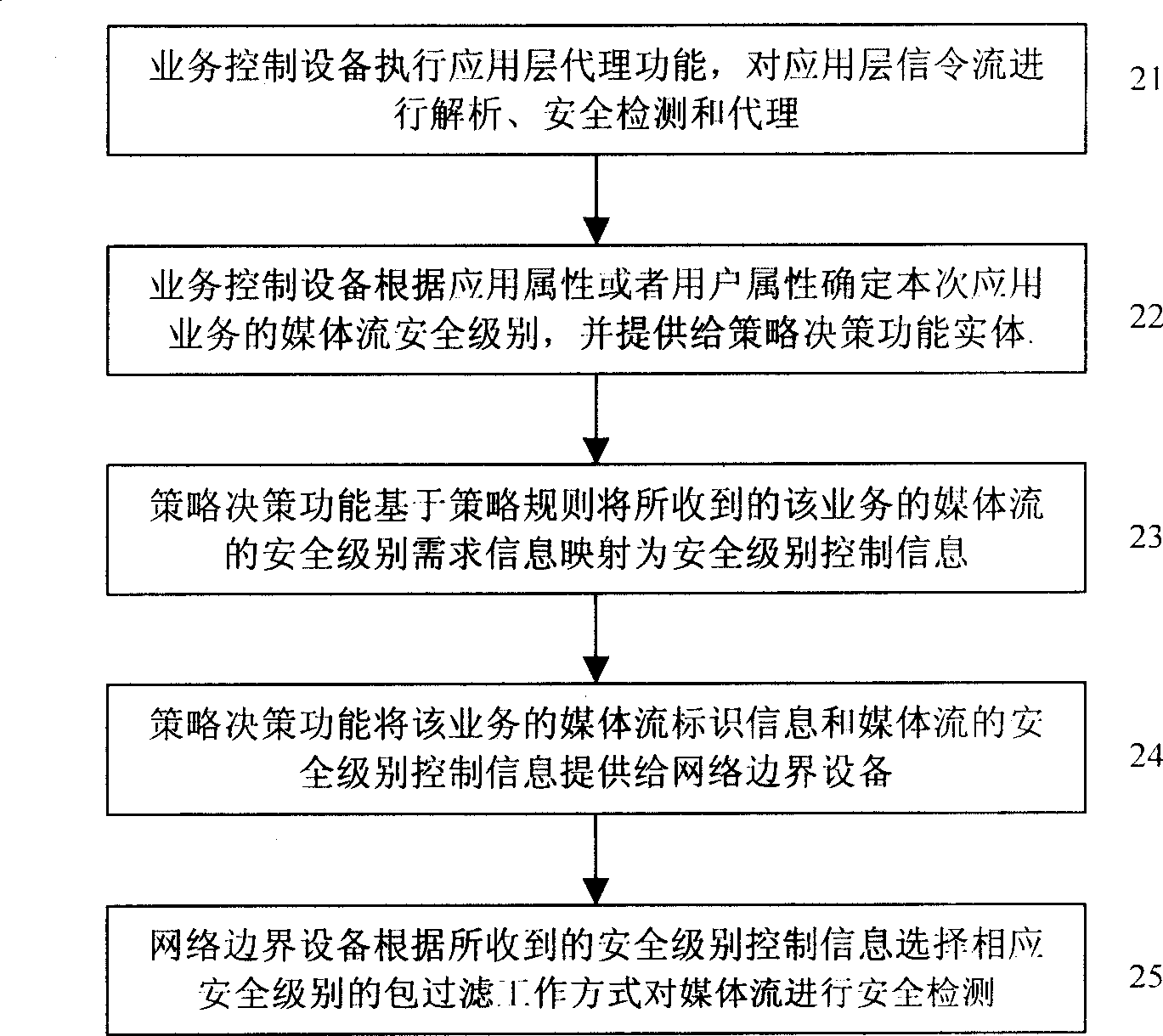
The invention provides an NGN service-based firewall control system and method. And its kernel comprises: first, application layer agent module in service control equipment analyzes application layer signaling and makes safe detection on signaling flow, determining safety grade request information of service media flow and providing the request information for policy making functional entity; then the policy making functional entity determines corresponding media flow safety grade control information according to the request information and the stored policy information and providing the control information for network boundary equipment; and finally, the packet filtration-based firewall functional module in the network boundary equipment makes safe detection on the service media flow according to the control information. Therefore, it can prevent resource embezzlement and IP address counterfeiting and put an end to service and advanced application invasion and other network attacks.
Owner:HUAWEI TECH CO LTD
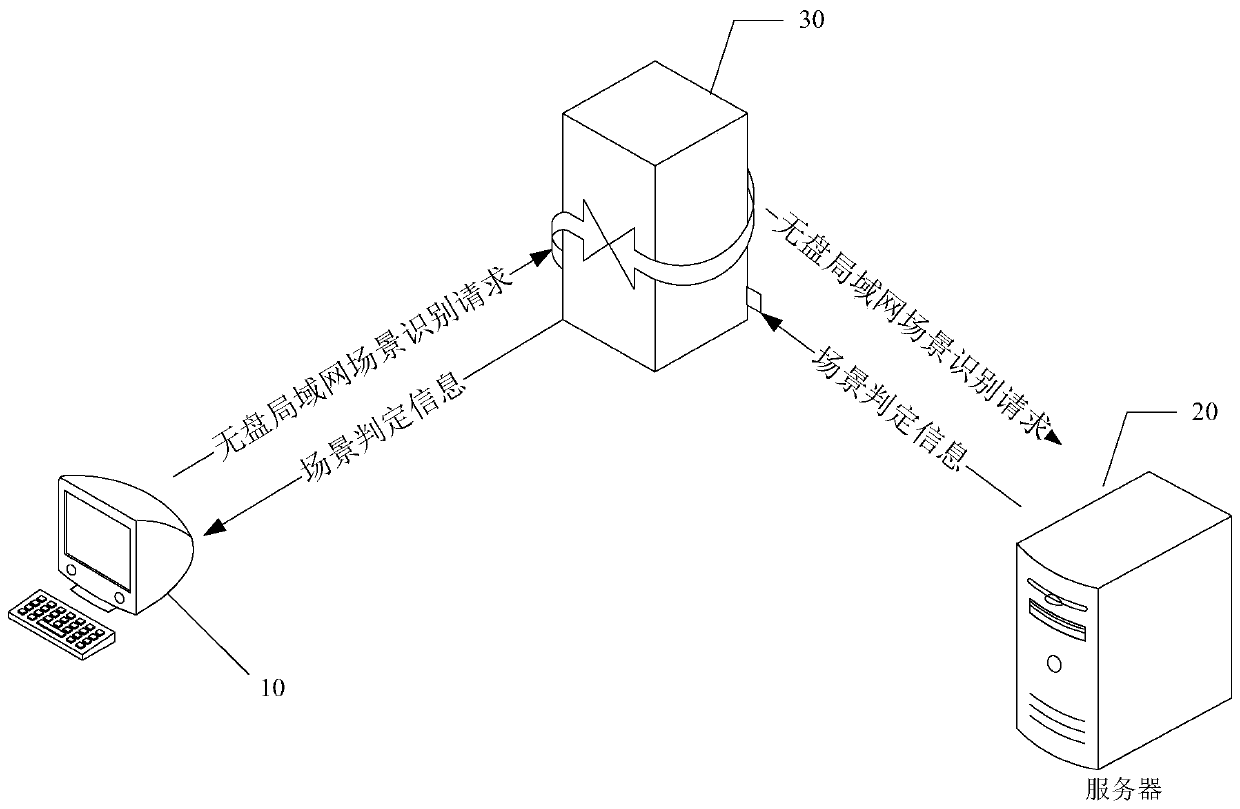
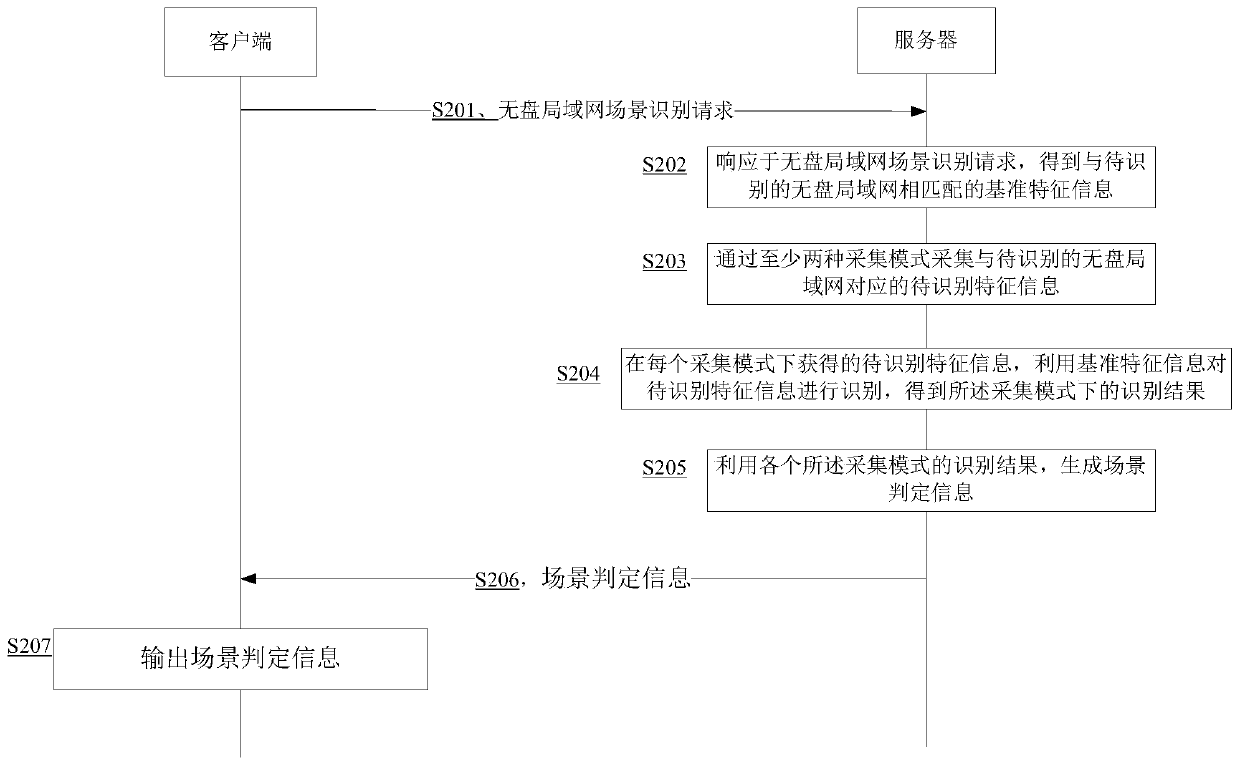
Diskless local area network scene recognition method and device and terminal
ActiveCN110572302AAccurate identificationPrevent camouflageData switching networksLocal area networkPattern recognition
The invention discloses a diskless local area network scene recognition method and device and a terminal, and belongs to the field of artificial intelligence. According to the method, when a disklesslocal area network scene is identified, to-be-identified feature information of a to-be-identified diskless local area network is acquired through at least two acquisition modes, wherein the to-be-identified feature information at least comprises the network configuration dimension and the machine information dimension, i.e., the multi-dimensional information. The disguise and tampering of the diskless local area network information can be effectively avoided by identifying the feature information of different dimensions in different acquisition modes, so that the specific diskless local areanetwork scene can be accurately identified.
Owner:TENCENT TECH (SHENZHEN) CO LTD
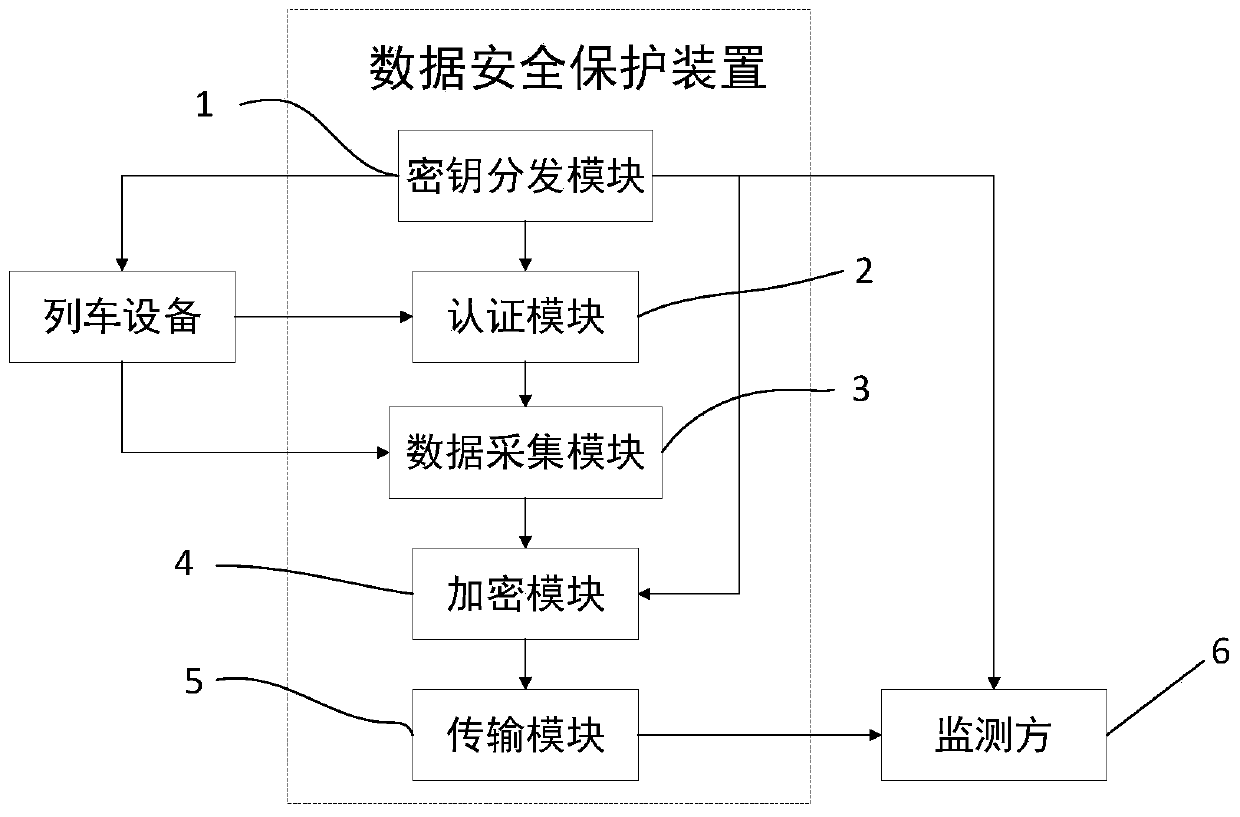
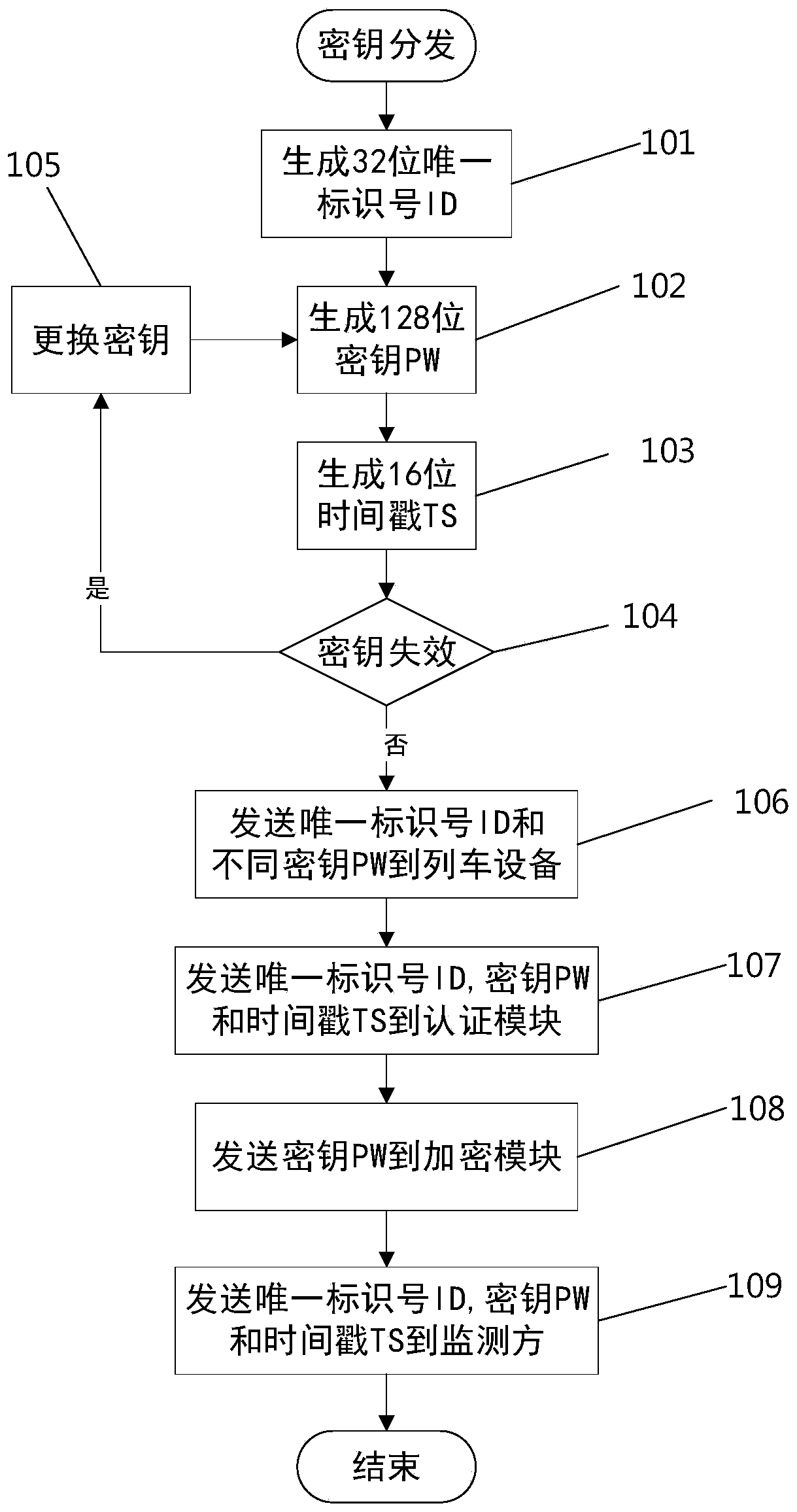
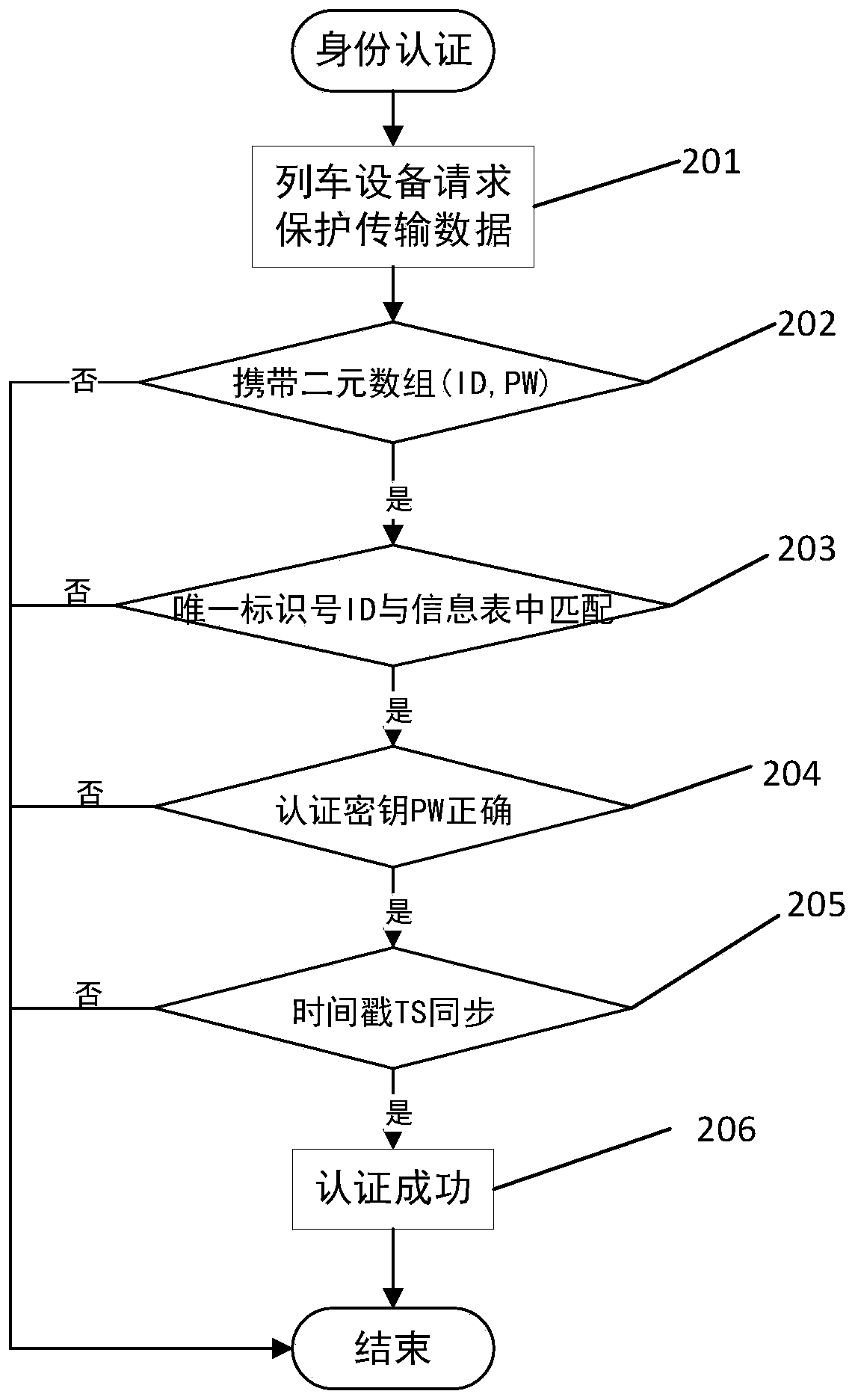
Safety protection method and device for train data
InactiveCN111343606AImprove integrityImprove confidentialityParticular environment based servicesFor mass transport vehiclesConfidentialityData transport
The invention discloses a safety protection method for train data. The method comprises a secret key distribution step, an authentication step, an encryption step and a transmission step, wherein thesecret key distribution step is used for distributing a unique recognition number ID and a corresponding secret key PW to each train needing to be monitored and sending the unique recognition number ID and the corresponding secret key PW of each train to a monitoring party; in the authentication step, identity authentication is carried out on all nodes accessed to the train network; in the encryption step, the identity of a train is identified according to a unique recognition number ID carried by the train, and the collected train data of the train is symmetrically encrypted by using a secretkey PW corresponding to the train. In the transmission step, the encrypted train data is transmitted to a monitoring party; and the monitoring party decrypts the data by using the secret key PW corresponding to the train and then monitors and checks the data. According to the invention, the integrity and confidentiality of train data are protected, the occurrence of equipment camouflage, eavesdropping and tampering is prevented, and the real-time protection of the train data is improved.
Owner:CENT SOUTH UNIV
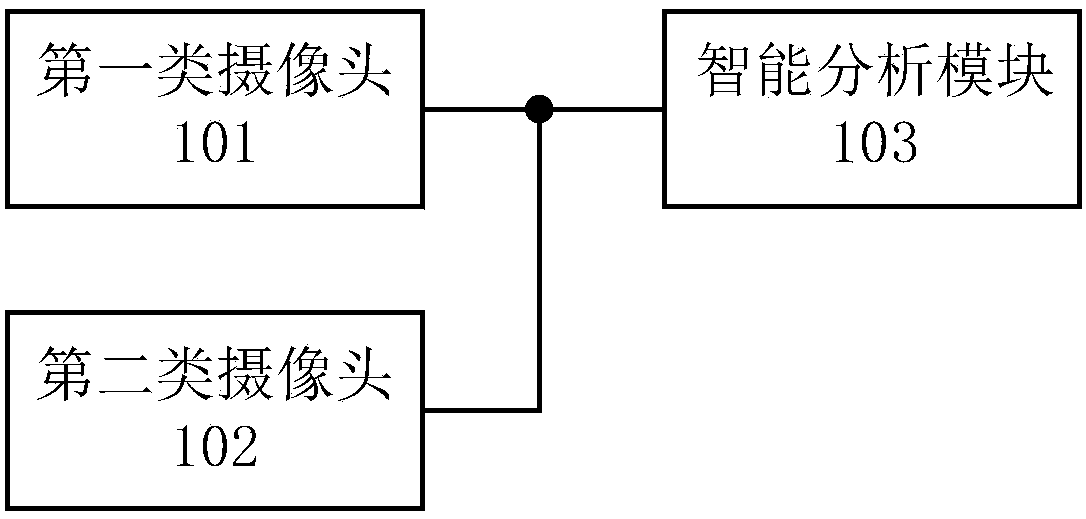
Monitoring system
InactiveCN109961588ARealize liveness detectionPrevent camouflageComplete banking machinesATM surveillanceReal-time computingMonitoring system
The invention discloses a monitoring system comprising a first type of camera, a second type of camera and an intelligent analysis module. The first type of camera includes at least two environmentalmonitoring cameras arranged at different positions in a self-service bank respectively; each environment monitoring camera connected with the intelligent analysis module is used for collecting environmental information in the self-service bank and sending a collected first-type video stream to the intelligent analysis module in real time. The second type of camera that is arranged at an automaticteller machine and is connected with the intelligent analysis module is used for collecting information of the personnel operating the automatic teller machine and sending a collected second-type video stream to the intelligent analysis module in real time. The intelligent analysis module arranged at the local self-service bank is used for receiving the first-type video stream and the second-typevideo stream, identifying faces in the first-type video stream and the second-type video stream, and carrying out associated analysis on the first-type video stream and the second-type video stream togenerate an analysis result.
Owner:TENDYRON CORP
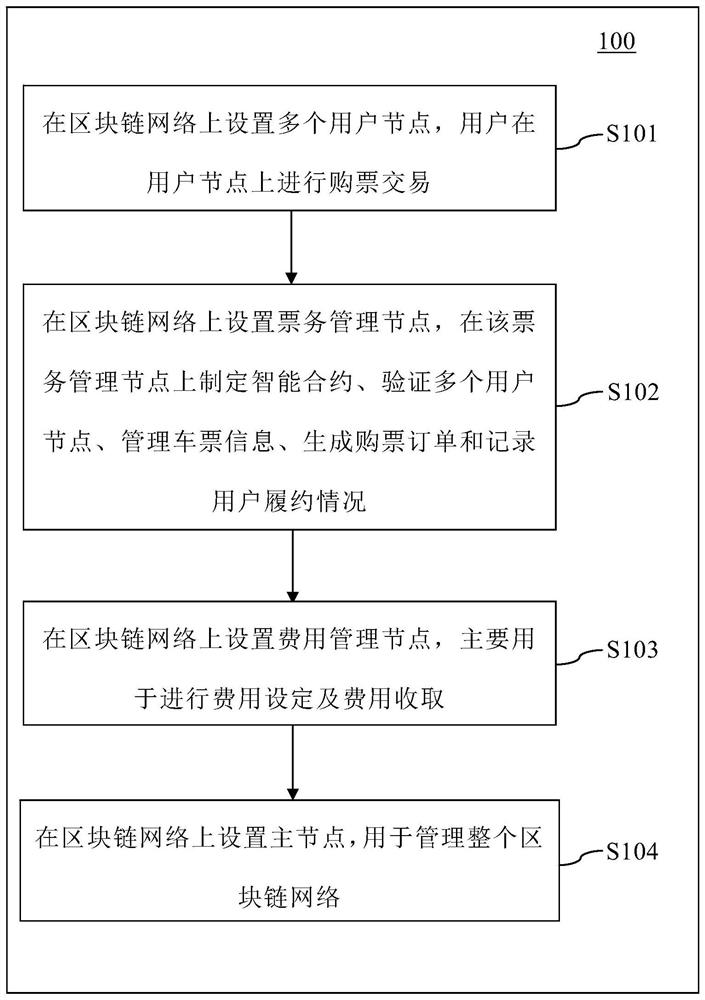
Electronic ticket selling method and system based on block chain, electronic equipment and storage medium
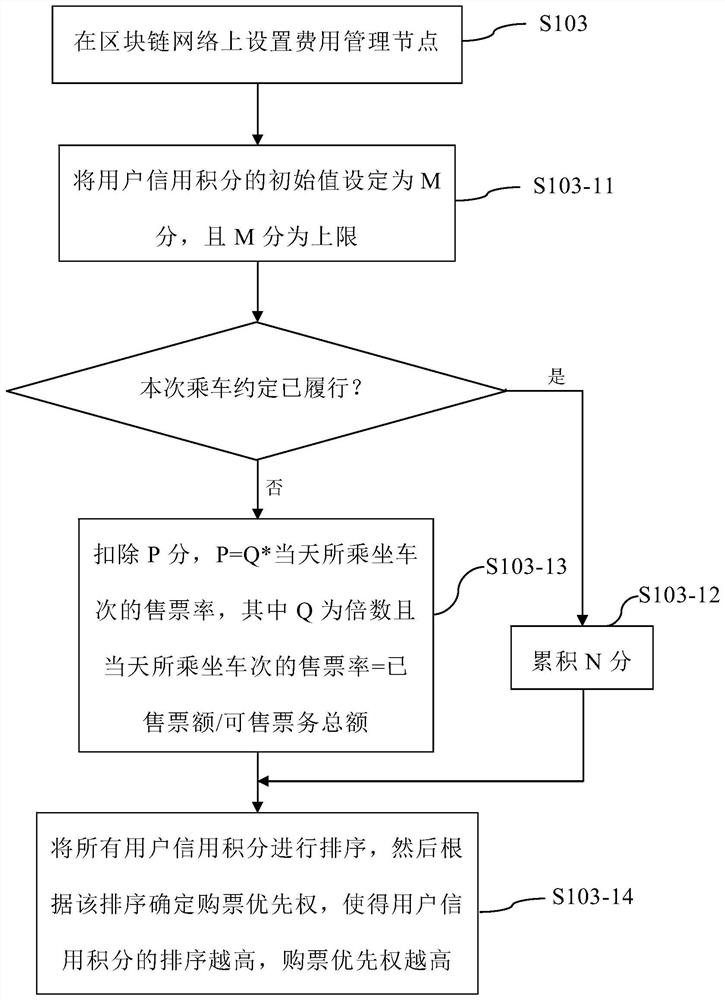
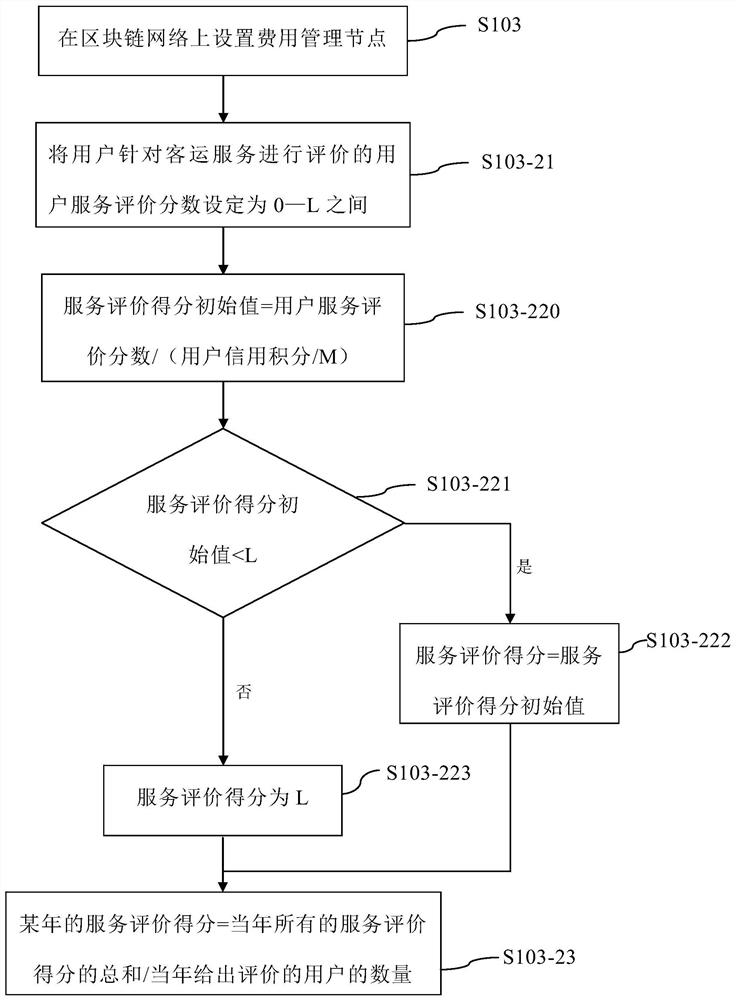
The invention relates to an electronic ticket selling method based on a block chain. The method comprises the following steps: setting a plurality of user nodes on a block chain network; and setting aticket management node on the blockchain network. The method also comprises the following steps: setting a cost management node on the blockchain network, wherein the cost management node is used forperforming cost setting and cost collection; and executing the following steps on the cost management node: a) setting an initial value of the user credit score as M score, wherein M is an upper limit; b) if the user performs the appointment once, accumulating N scores; c) if the user fails to keep an appointment for one time, deducting P score, wherein P = Q * the ticket selling rate of the current day, Q is a multiple and the ticket selling rate of the current day= sold ticket amount / available ticket total amount, and d) sequencing all user credit points, and then determining ticket buyingpriority according to the sequencing, so that the higher the sequencing of the user credit points is, the higher the ticket buying priority is. The invention further relates to an electronic ticketingsystem based on the block chain, electronic equipment and a storage medium.
Owner:CHINA UNITED NETWORK COMM GRP CO LTD
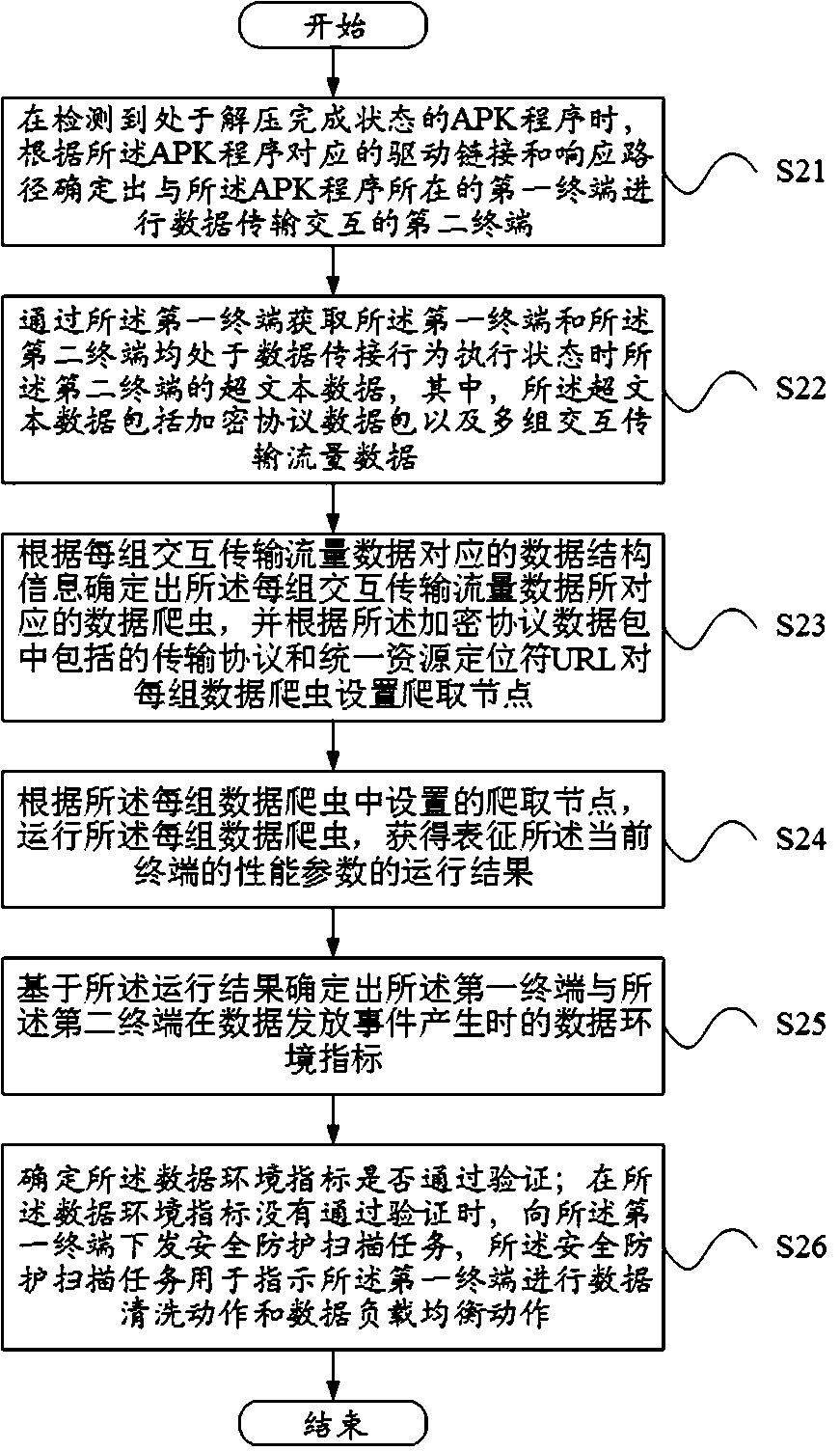
Data security protection method and device and service equipment
ActiveCN110769008AImprove timelinessImprove reliabilityWeb data indexingTransmissionPathPingData transport
The embodiment of the invention relates to the technical field of data processing. Specifically, the present invention relates to a data security protection method and device and service equipment. According to the data security protection method, a target terminal can be determined from a complex data interaction scene based on a drive link and a response path of an APK program; the target terminal is prevented from being disguised through the virtual identifier; the comprehensiveness and the accuracy of determining the target terminal are improved; hypertext data is used as an analysis basis; the reliability of verifying the target terminal can be improved; the operation efficiency of the data crawler determined according to the hypertext data is ensured; the timeliness and reliability of safety protection can be realized based on the operation result of the data crawler; and when it is judged that the data environment index does not pass the verification, the security protection scanning task is issued to the current terminal, and the current terminal can execute the data cleaning action and the data load balancing action, and the data transmission risk caused by continuous connection with the target terminal is avoided, and the timeliness and reliability of data security protection are improved.
Owner:长沙豆芽文化科技有限公司
A Device Identification System Based on Device Fingerprint
The invention belongs to the field of network admission control technology, and particularly relates to an equipment identification system based on an equipment fingerprint, wherein the equipment fingerprint information comprises hardware information, operating system information and application service information of the equipment. The system comprises the components of an equipment fingerprint database, an equipment discovery module, an equipment fingerprint acquisition module, an equipment fingerprint processing module, an equipment fingerprint matching module and an artificial identification module. The equipment fingerprint information comprises the MAC OUI hardware information and the operating system information of the equipment and the application service information in a port list. The formats of the fingerprint database comprise MAC OUI, operating system information, port list and equipment type. The equipment fingerprint acquisition module comprises operating system fingerprint information and port fingerprint information. The equipment identification system has advantages of performing network admission control on network equipment through the equipment type, making different security strategies on different kinds of equipment, preventing equipment counterfeiting, and ensuring high safety of enterprise network.
Owner:BEIJING VRV SOFTWARE CO LTD
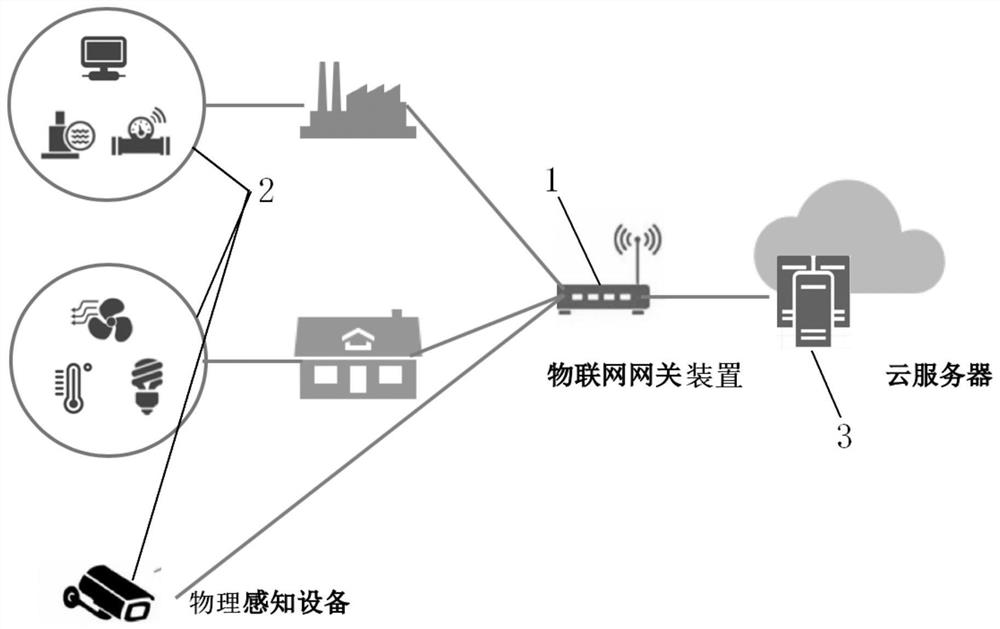
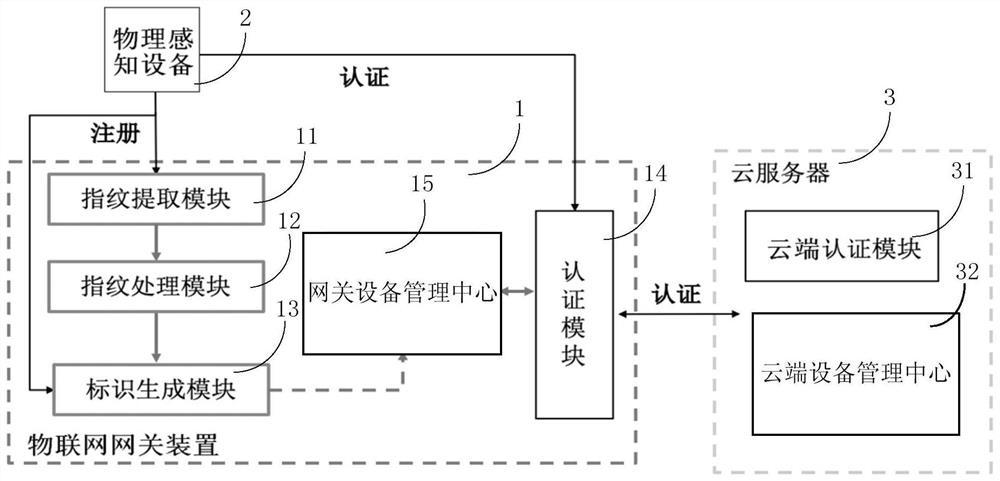
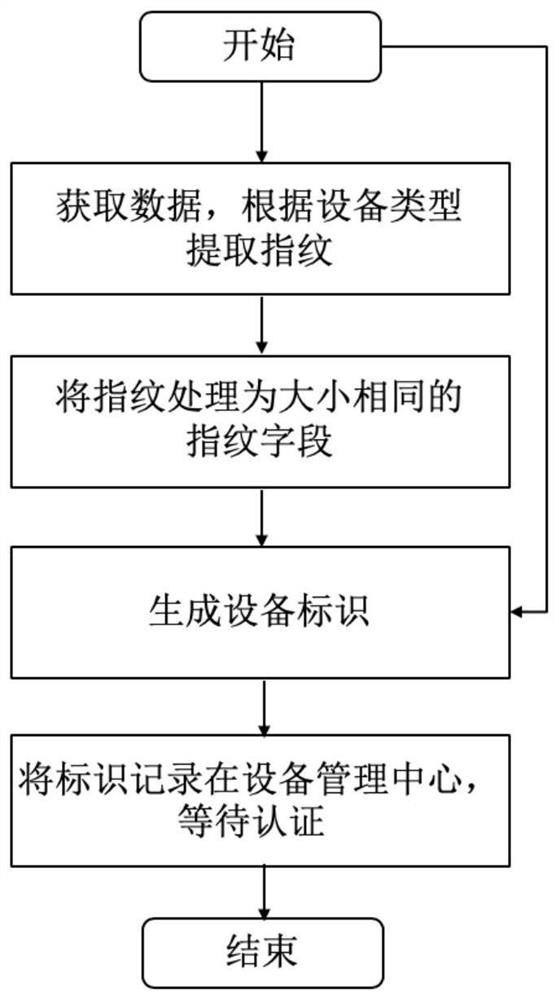
IoT gateway device capable of securely authenticating physical perception devices and access method thereof
ActiveCN112469034BImprove securityReliable identificationDigital data protectionInternal/peripheral component protectionComputer hardwareInformation processing
The invention discloses an Internet of Things gateway device capable of securely authenticating a physical perception device and an access method thereof. The device comprises: a device fingerprint extraction module, which can extract device fingerprint information of the connected physical perception device; a fingerprint processing module, which can extract the device fingerprint information of the connected physical perception device; The device fingerprint information extracted by the device fingerprint extraction module is processed into a fingerprint field with a fixed number of digits corresponding to the connected physical sensing device; the identification generation module can use the fingerprint field corresponding to the connected physical sensing device as the physical sensing device. Generate a unique device identifier containing a fingerprint field; the authentication module is respectively connected with the identification generation module, the physical perception device and the cloud server, and uses the unique device identifier containing the fingerprint field generated by the identification generation module to interact with the cloud server to access the Physically aware devices perform two-way authentication. It can use the unique device identifier constructed by the device fingerprint of the physical sensing device to realize two-way authentication and improve the security of the communication of the physical sensing device.
Owner:UNIV OF SCI & TECH OF CHINA
Narrow-band frequency hopping radio signal identification method
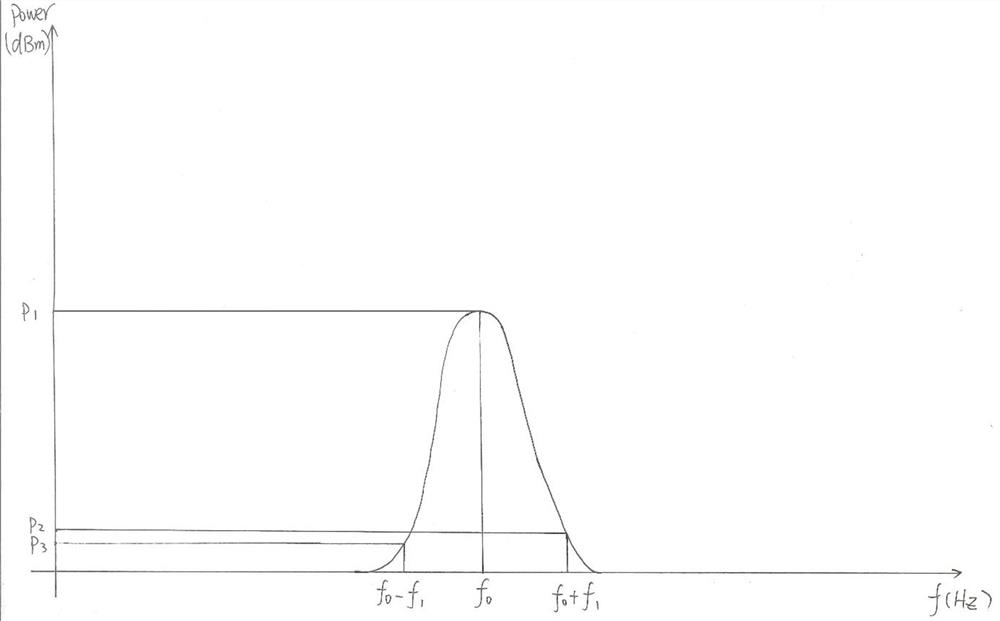
InactiveCN112653489AImprove securityPrevent camouflageCommunication jammingTransmissionTransmitterRadio signal
The invention discloses a narrow-band frequency hopping radio signal identification method, which comprises the following steps: simultaneously or within a short time interval, detecting and demodulating radio signals of a predetermined frequency of a narrow-band frequency hopping radio signal and adjacent frequencies on two sides of the narrow-band frequency hopping radio signal; comparing the preset frequency of the narrow-band frequency hopping radio signal with the power corresponding to the radio signals with the adjacent frequencies on the two sides of the narrow-band frequency hopping radio signal; and when the power corresponding to the radio signals with the adjacent frequencies on the two sides is smaller than a first threshold value of the power corresponding to the preset frequency of the narrow-band frequency hopping radio signal, and the power difference corresponding to the radio signals with the adjacent frequencies on the two sides is smaller than a second threshold value, judging that the narrow-band frequency hopping radio signal is a legal signal, otherwise, judging that the narrow-band frequency hopping radio signal is an illegal signal. The method can effectively distinguish whether a signal to be received is a frequency hopping radio signal sent by a legal transmitter according to a preset frequency or a fixed frequency radio signal covering the whole frequency band and sent by an illegal transmitter. The application of frequency hopping radio communication with increased security can be extended to the field of narrow-band wireless communication.
Owner:MARELLI AUTOMOBILE ELECTRONIS GUANGZHOU CO LTD
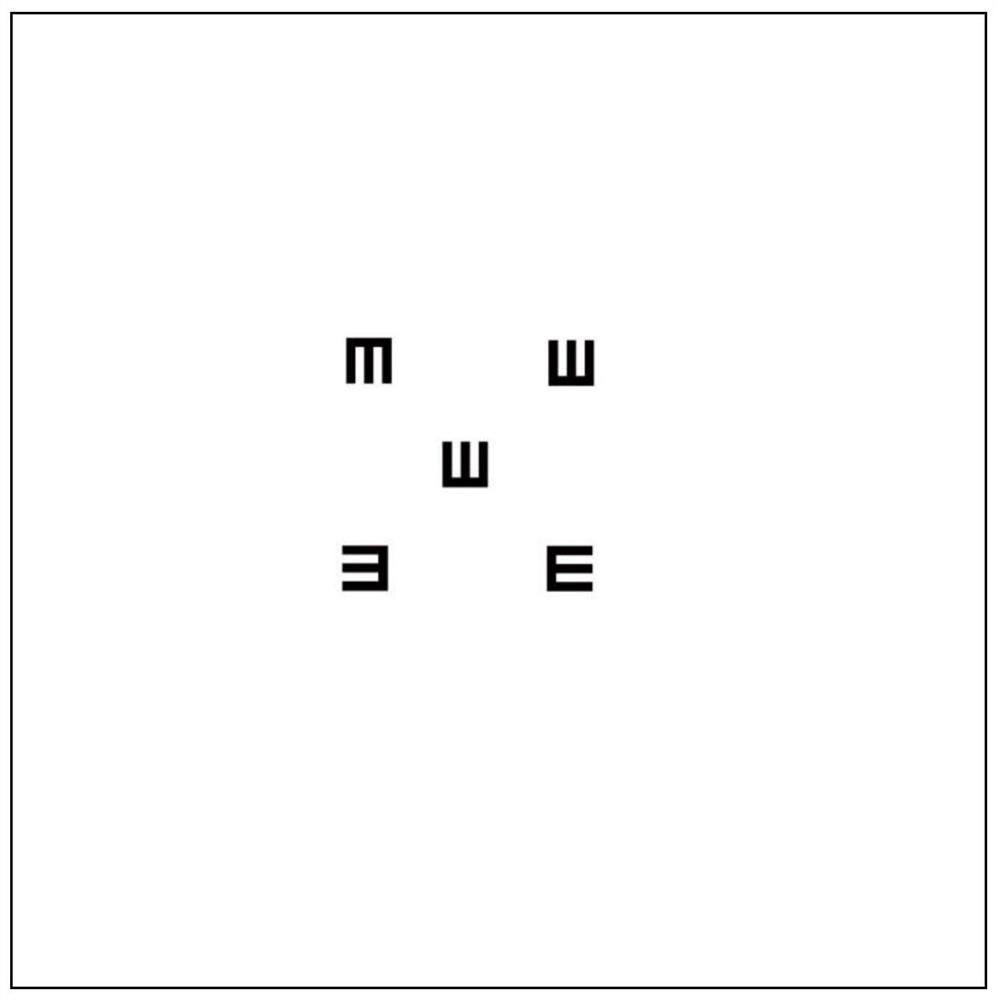
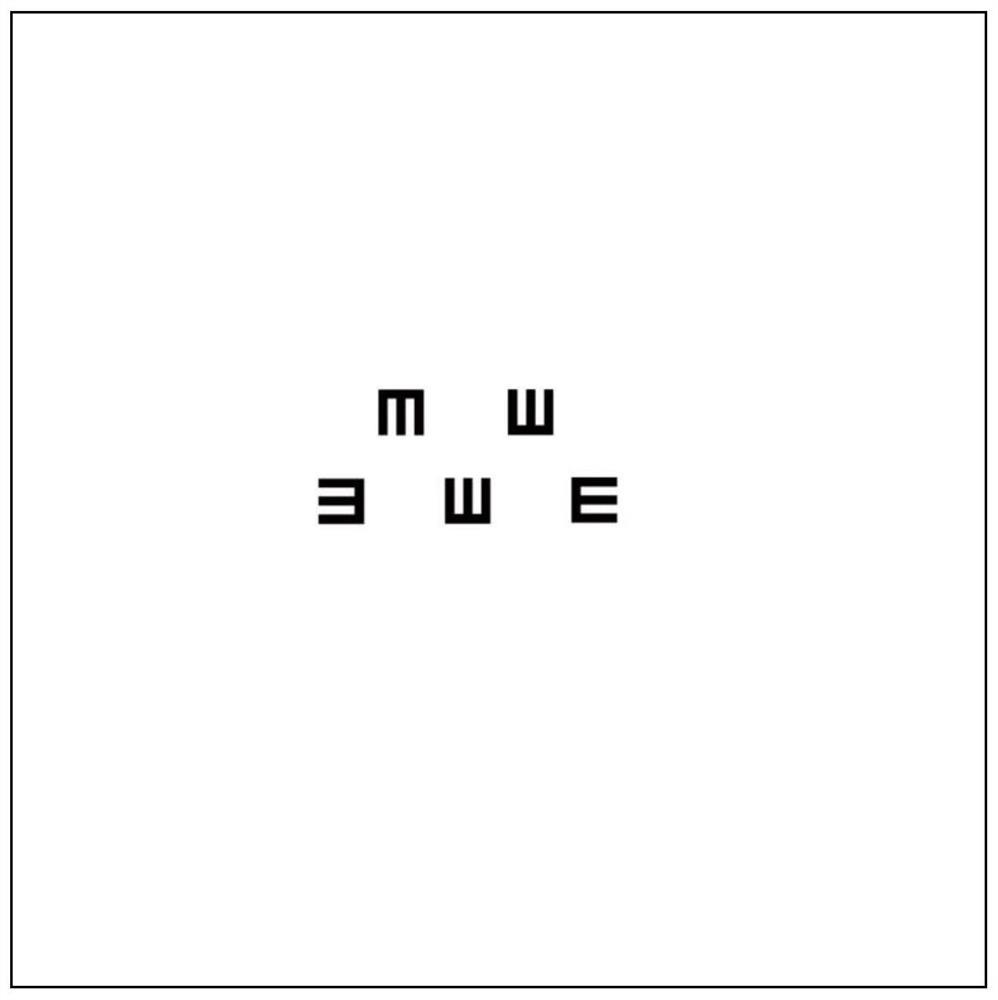
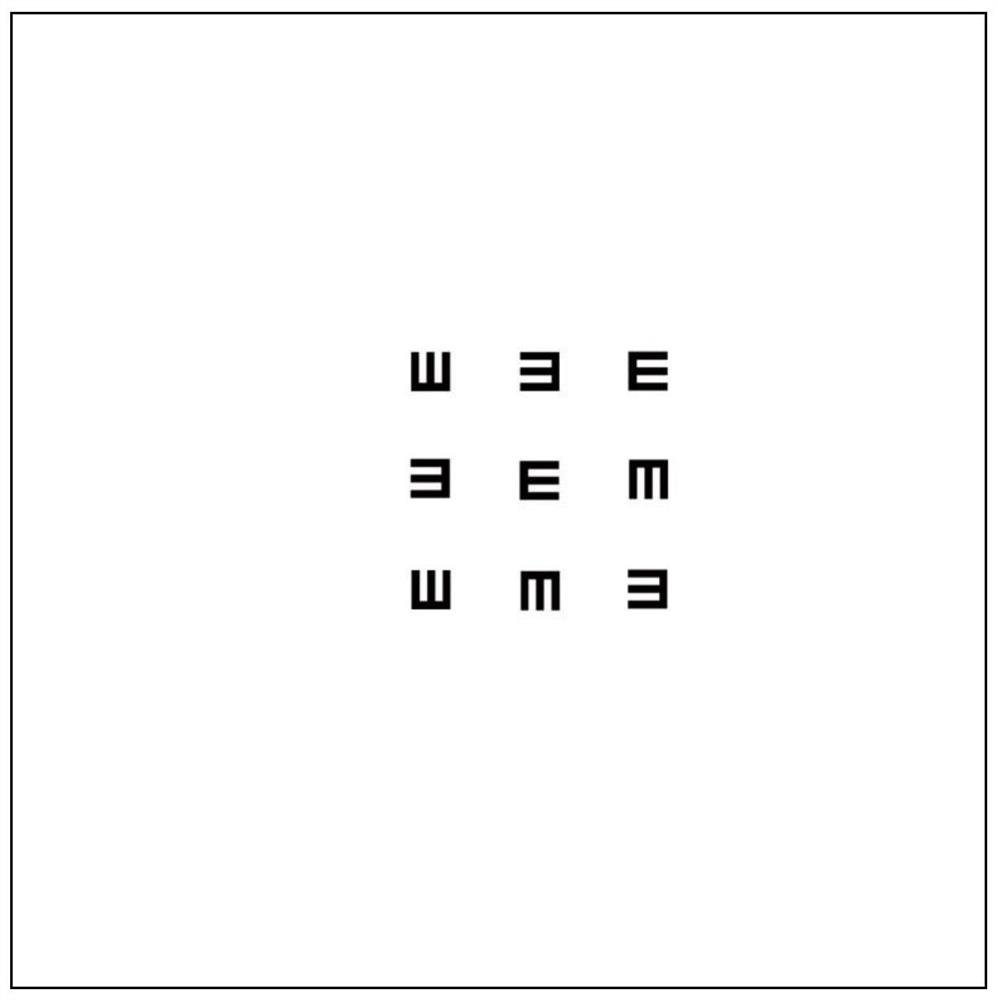
A single vision chart and visual inspection method
ActiveCN110301885BPrevent camouflageImprove inspection accuracyEye diagnosticsSingle viewTest subject
The invention relates to a single vision chart and a visual inspection method. The single vision chart is a plan view composed of at least 5 visual targets of the same size. In the visual chart, there are 4 directions of visual targets, and any adjacent 2 The blank distance between two optotypes is more than half of the width of a single optotype, and any two adjacent optotypes in the vertical direction have different directions, and any two adjacent optotypes in the horizontal direction have different directions. In the present invention, by changing the structure of the eye chart, multiple inspections are carried out on the inspected person to obtain the authenticity of the inspected person's main vision. The reciteability is reduced, and the examinee can only rely on the real vision to identify the best vision target, and cannot fake vision. It can effectively overcome the examinee's fake high vision and discover the fake vision, and improve the accuracy of the test.
Owner:QINGDAO UNIV
A data security protection method, device and service equipment
ActiveCN110769008BImprove timelinessImprove reliabilityWeb data indexingTransmissionPathPingData transport
Owner:长沙豆芽文化科技有限公司
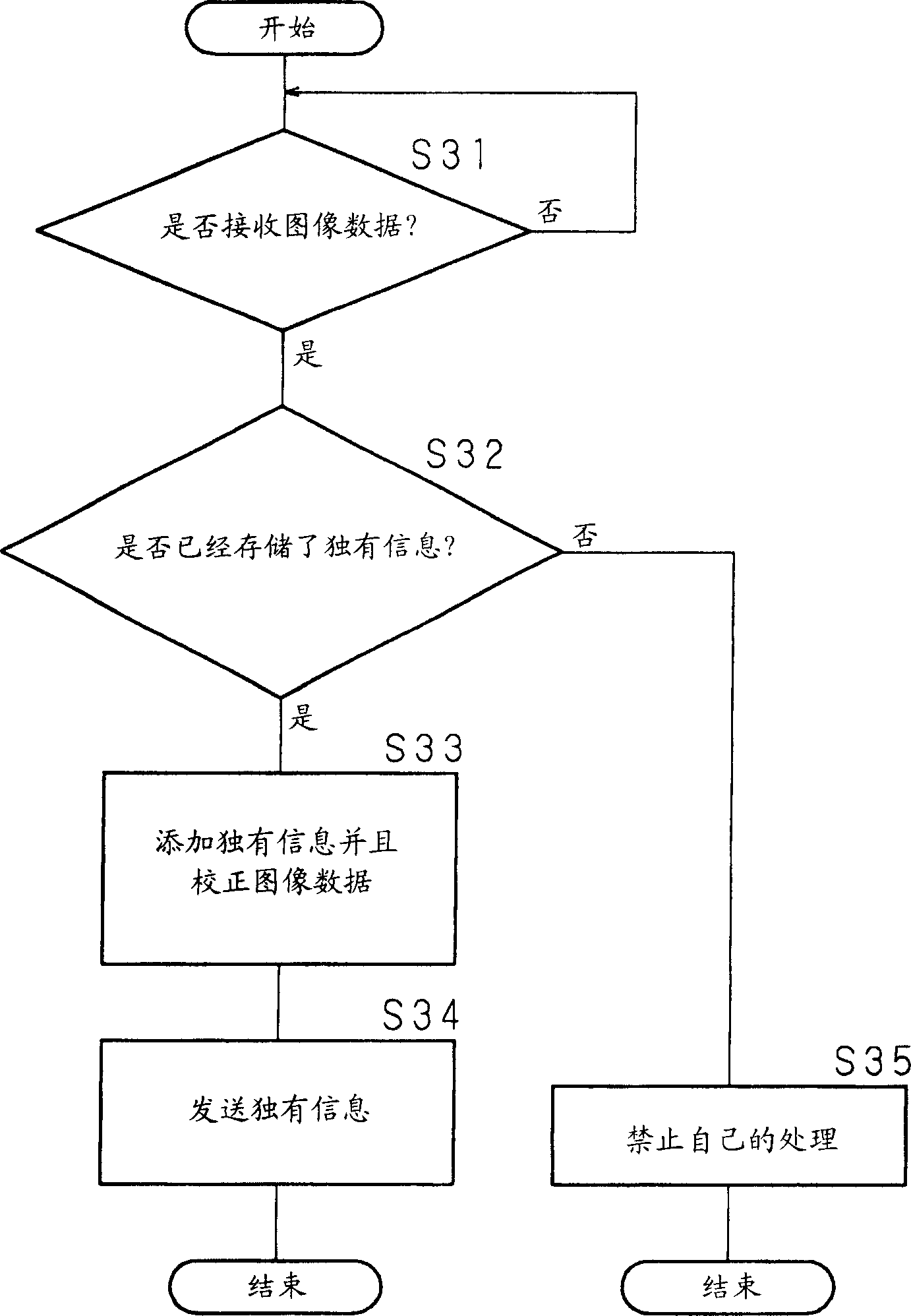
Image recording system and trunking
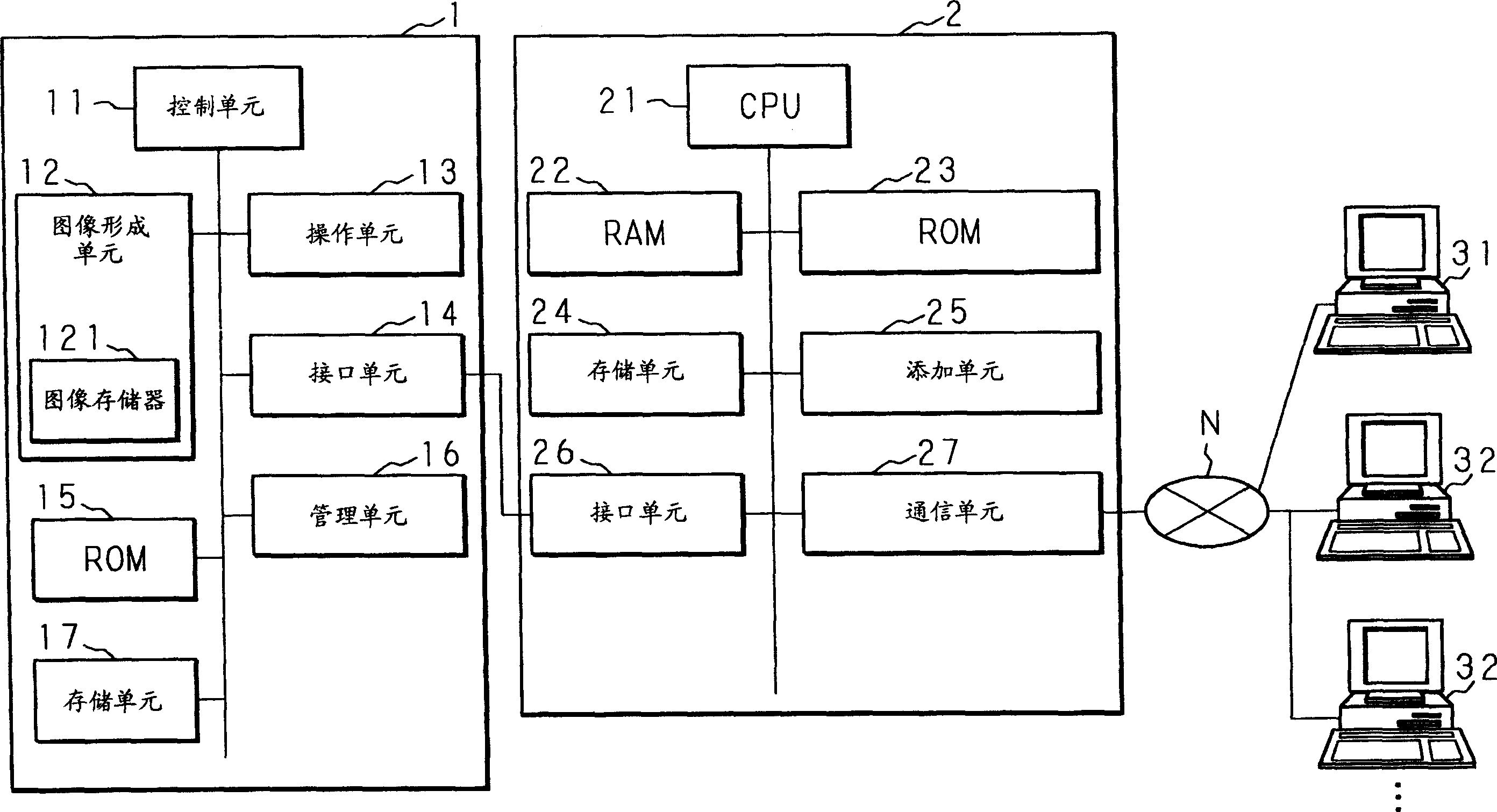
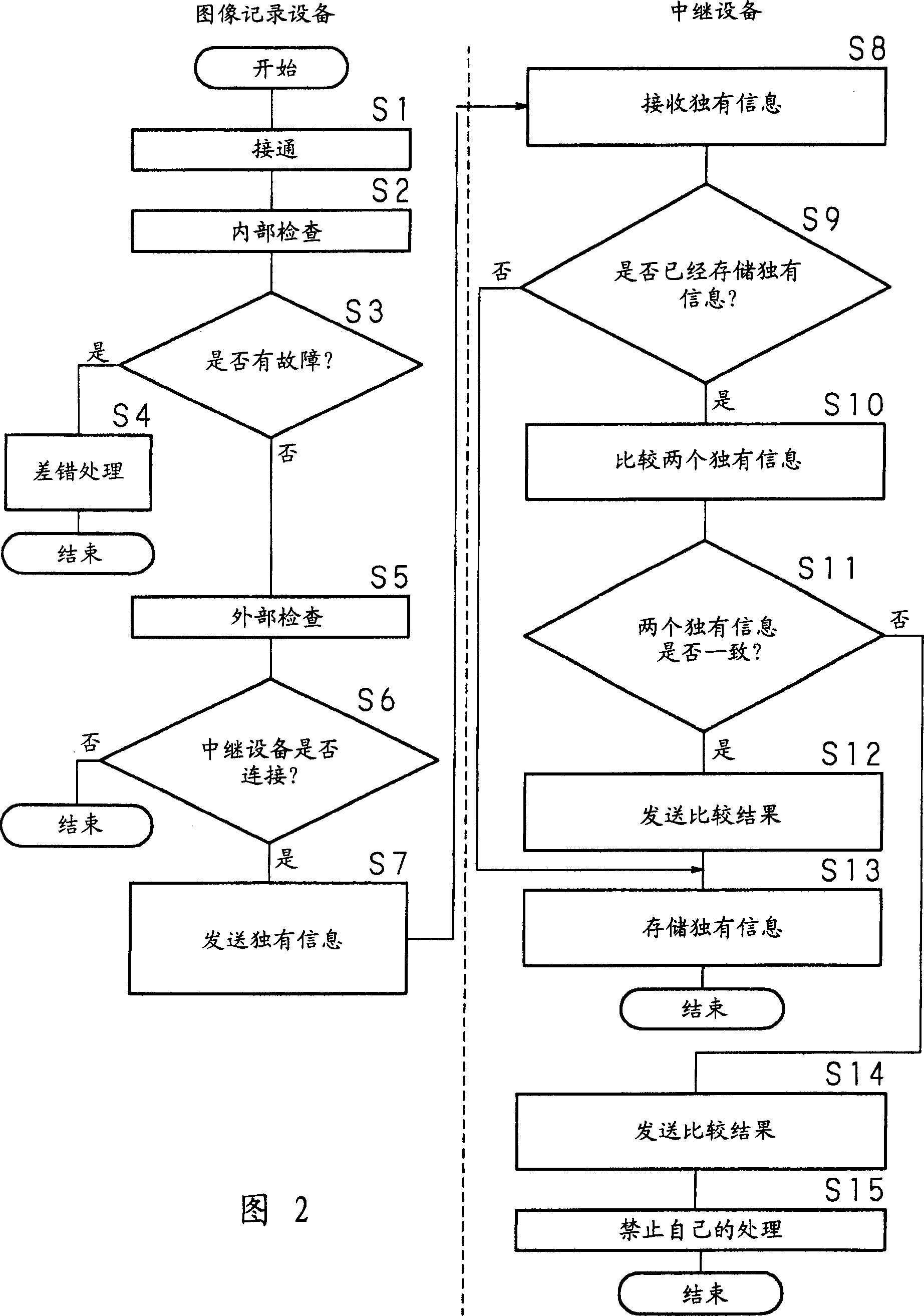
InactiveCN1625216ALow costPreventing Image Quality DeteriorationTelevision system detailsDigital computer detailsComputer hardwareImage recording
A relay device (relay unit) 2 is provided between the PC 32 that transmits image data and the image recording device (image recording unit) 1 . The relay device 2 performs processing for correcting the color of the image data sent from the PC 32 to the image recording device 1 . Furthermore, the storage unit 24 of the relay device 2 stores information unique to the image recording device 1 such as a production number. The relay device 2 performs processing for correcting the image data and for adding unique information to the image data sent from the PC 32 , and then sends the processed image data to the image recording device 1 . Thereby, an image recording system and a relay device are realized in which it is not necessary to provide a circuit for performing a process of embedding unique information into image data in the image recording device 1, so that resulting in image quality degradation.
Owner:SHARP KK
Link state maintenance method and device
ActiveCN109981468BAvoid transmission interruptionImprove transmission reliabilityTransmissionTelecommunications linkEngineering
The present invention provides a link state maintenance method and device, which selects at least one of multiple upper-level nodes corresponding to the current node to establish a communication link according to the priority; broadcasts the first dynamic route to the corresponding upper-level node through the communication link Information: receiving the second dynamic routing information broadcast by the corresponding upper-level node through the communication link and broadcasting to the lower-level node communicating with the current node. Among them, in the static configuration, the lower-level node selects the upper-level node according to the priority, and supports the situation that the lower-level node corresponds to multiple upper-level nodes at the same time, so that when the upper-level node is abnormal, the information can be transmitted through other upper-level nodes, avoiding transmission interruption and improving transmission reliability. meet application requirements. In addition, the link state maintenance of non-adjacent nodes is supported through dynamic routing state broadcast, further improving transmission reliability.
Owner:THE PEOPLES BANK OF CHINA NAT CLEARING CENT
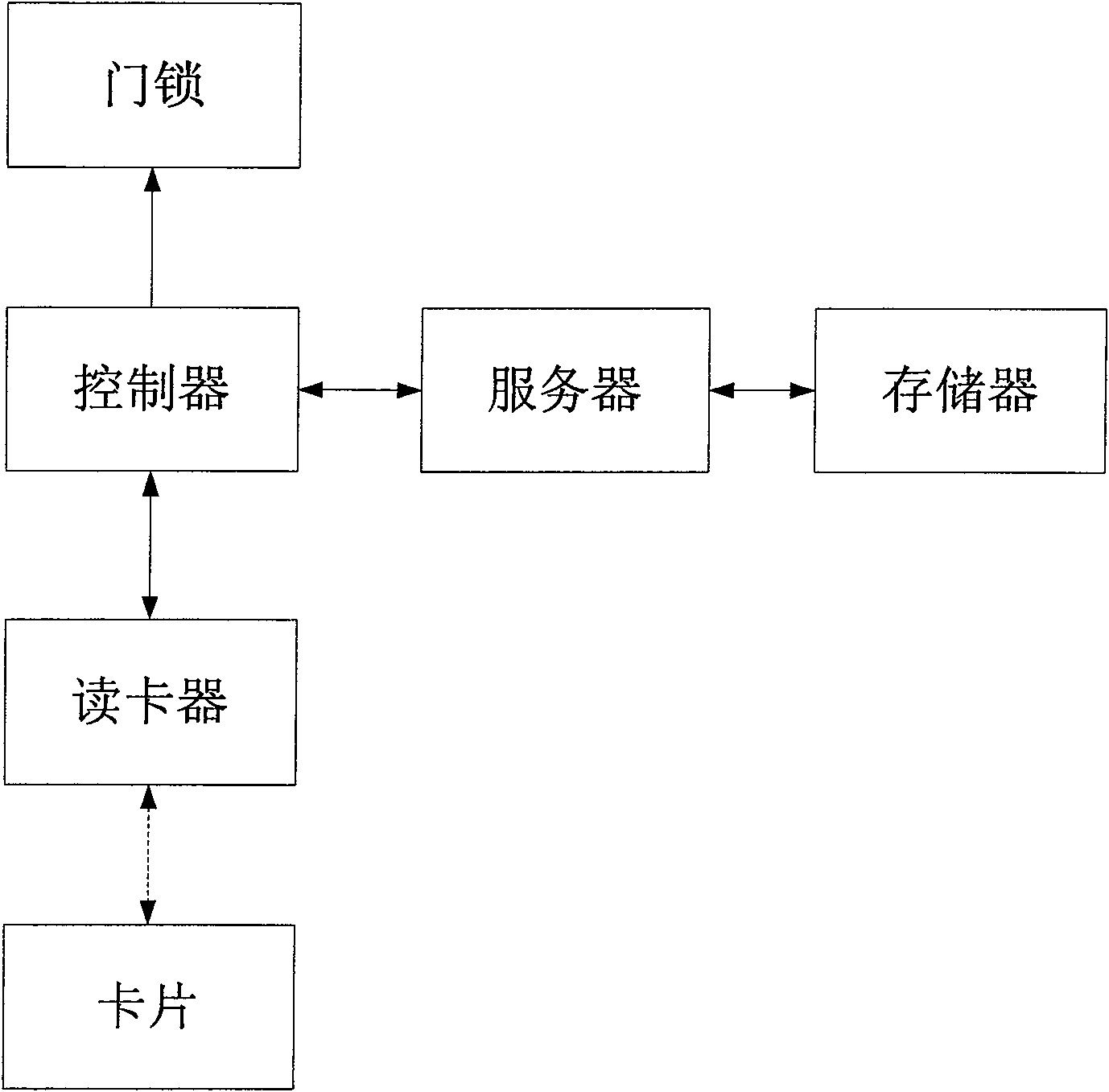
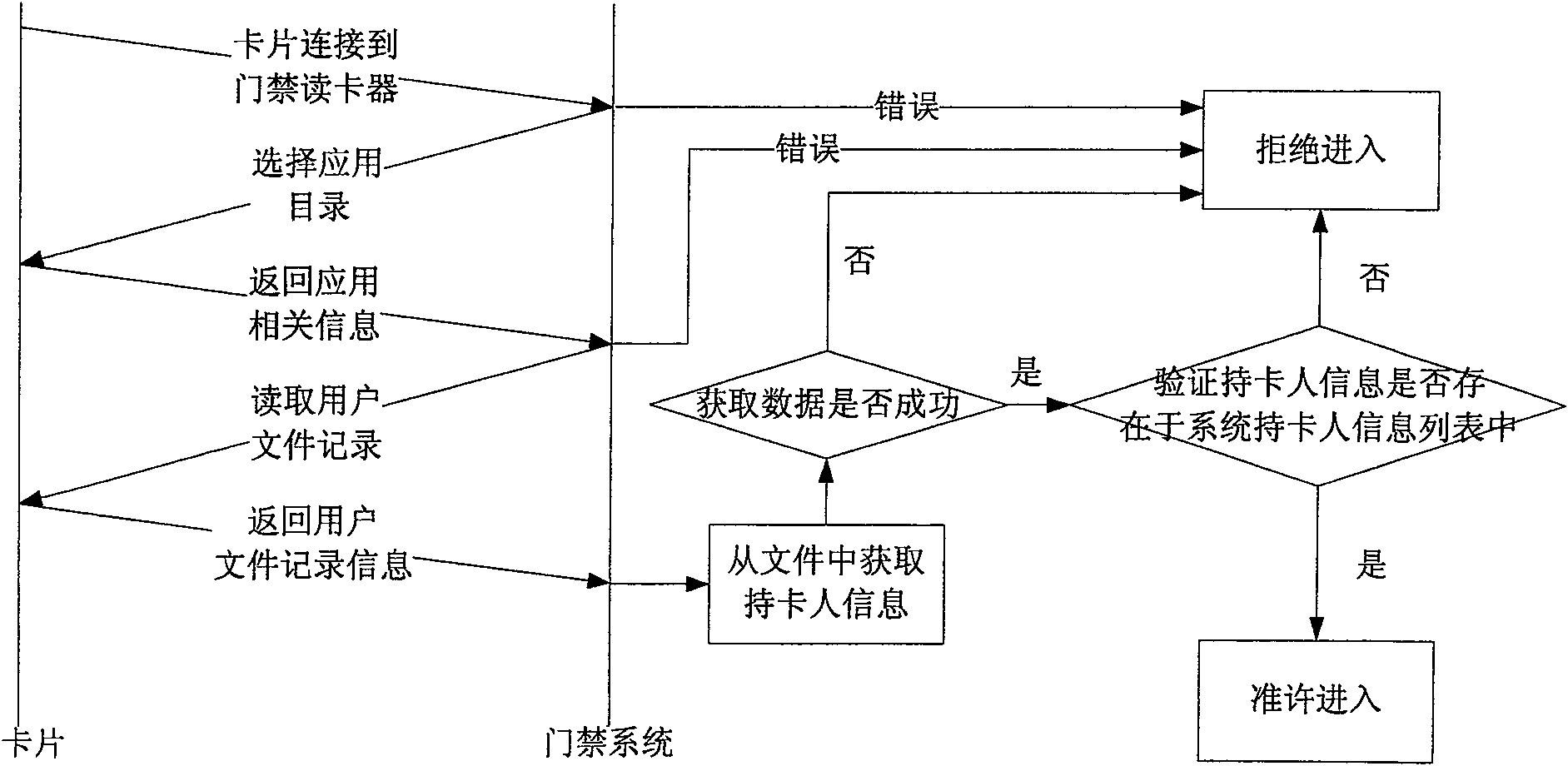
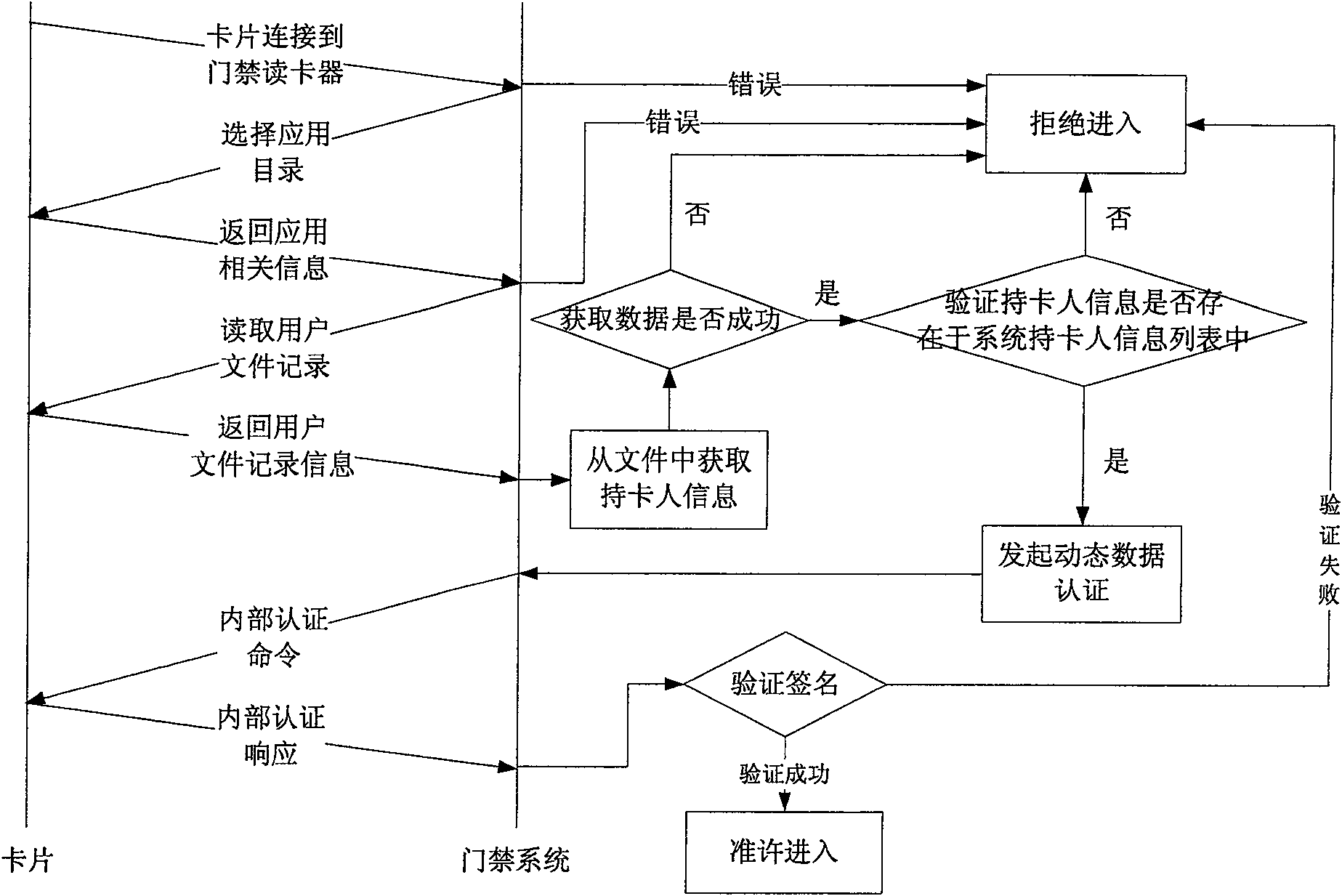
Application method of IC card in gate inhibition system based on financial criterion
ActiveCN100555339CReduce the link of issuing cardsAvoid monitoringIndividual entry/exit registersControl systemSecurity level
The invention provides an application method of an IC card based on financial norms in an access control system, and relates to the technical field of access control system security. In combination with the financial norms, the present invention proposes a technical scheme of applying IC cards to the access control system to replace the special access control cards of the original access control system, replacing the access control cards with IC cards based on financial norms, which can reduce the card issuance links of the access control system and prevent users from carrying The inconvenience of special access control cards, in addition, from a security point of view, the security level of the access control system that supports dynamic data authentication has also been greatly improved compared with the traditional access control system.
Owner:FEITIAN TECHNOLOGIES
Features
- R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
Why Patsnap Eureka
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Social media
Patsnap Eureka Blog
Learn More Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com