Computing device and methods for performing secure neighbor discovery
A computing device, technology of equipment, applied in secure communication device, key distribution
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
specific Embodiment approach
[0027] The foregoing and other features will become more apparent on reading the following non-limiting description of illustrative embodiments, given by way of example only with reference to the accompanying drawings.
[0028] Aspects of the present disclosure generally address one or more issues related to the performance of fabric deployments in a data center, including various network configurations.
[0029] This disclosure will first describe each aspect of architecture deployment individually, and then describe the integrated architecture deployment process including all individually described aspects. Separately described aspects include generating fabric-wide IPv6 addresses, generating one or more link IPv6 addresses, and performing secure neighbor discovery.
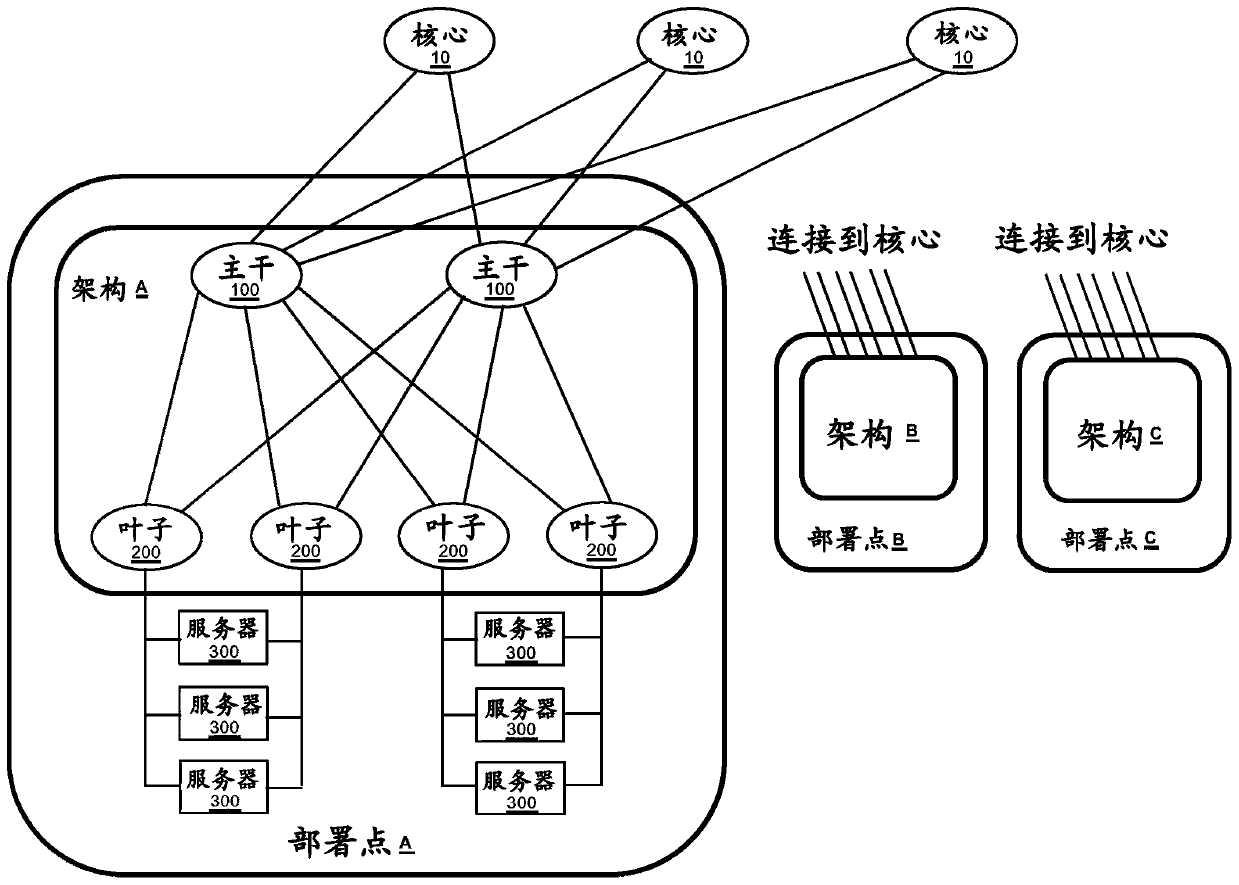
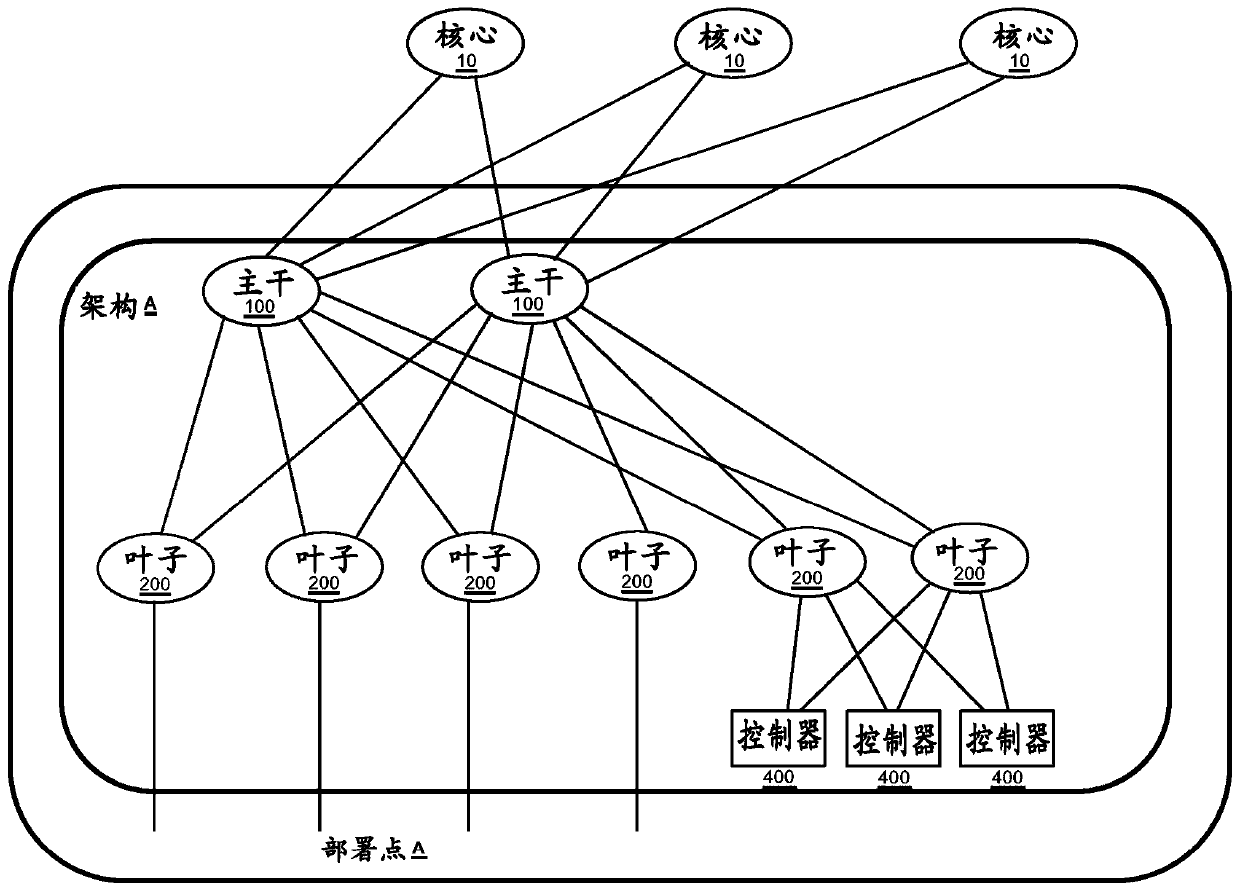
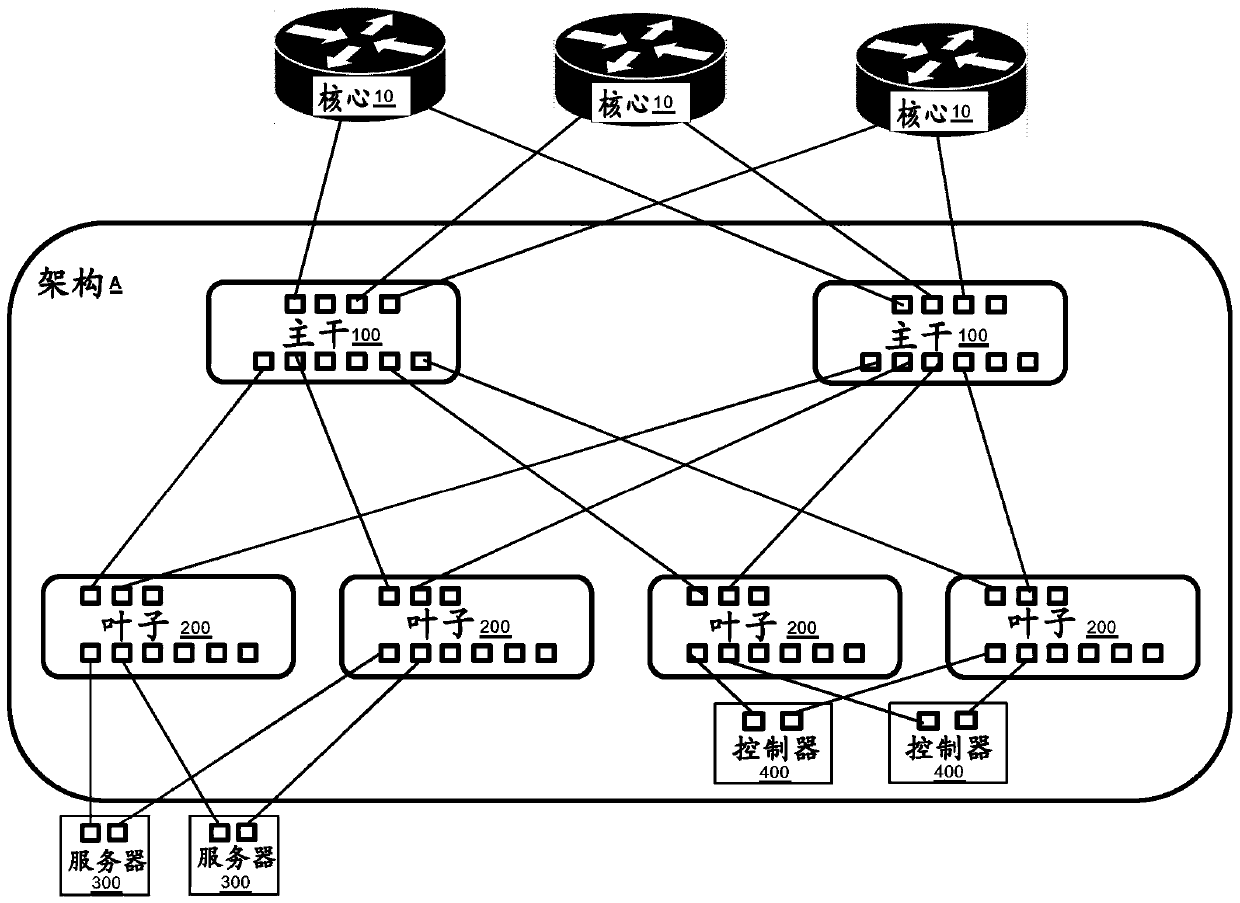
[0030] Data Center Network Architecture
[0031] Now also refer to figure 1 -4, illustrates the network architecture of the data center. The network architecture represented in the figures is for illustratio...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com