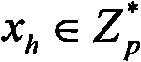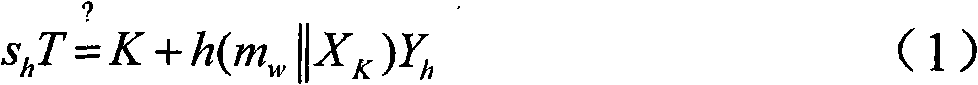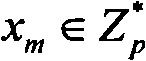Key exchange authentication method with no need of hometown network participation when in roaming
A technology of key exchange authentication and home network, which is applied in the field of key exchange authentication, can solve the problems of unable to authenticate request information verification, and achieve the effect of eliminating security weaknesses and reducing communication load
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
[0025] The relevant technical terms are as follows:
[0026] MN-Mobile Node (Mobile Node);
[0027] FN-Foreign Network;
[0028] HN-Home Network (Home Network);
[0029] F-AS-foreign authentication server (Foreign Authentication Server);
[0030] H-AS-Home Authentication Server (Home Authentication Server);
[0031] DoS - denial of service (Denial-of-Server);
[0032] AS - a trusted third-party authentication server (A trustworthy authentication server);
[0033] IDM-the identification of the mobile node MN (The identity of mobile node);
[0034] IDH-The identity of home network;
[0035] IDF-The identity of foreign network;
[0036] E. K (m) - encrypt the message m with the symmetric key K;
[0037] E. K -1 (m) - use the symmetric key K to decrypt the message m;
[0038] || - the concatenation operation of two bit strings;
[0039] h(.) - hash function;
[0040] p - a large prime number with a length of at least 160 bits;
[0041] {x} - information labeled x; ...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com