Distributed signature method and system based on identity
A distributed and identity technology, applied in the field of information key security, can solve the problems of key generation center PKG security risks, private key leakage, etc., achieve safe and reliable digital signature business, overcome untrustworthiness, and improve security
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
[0032] The principles and features of the present invention are described below in conjunction with the accompanying drawings, and the examples given are only used to explain the present invention, and are not intended to limit the scope of the present invention.
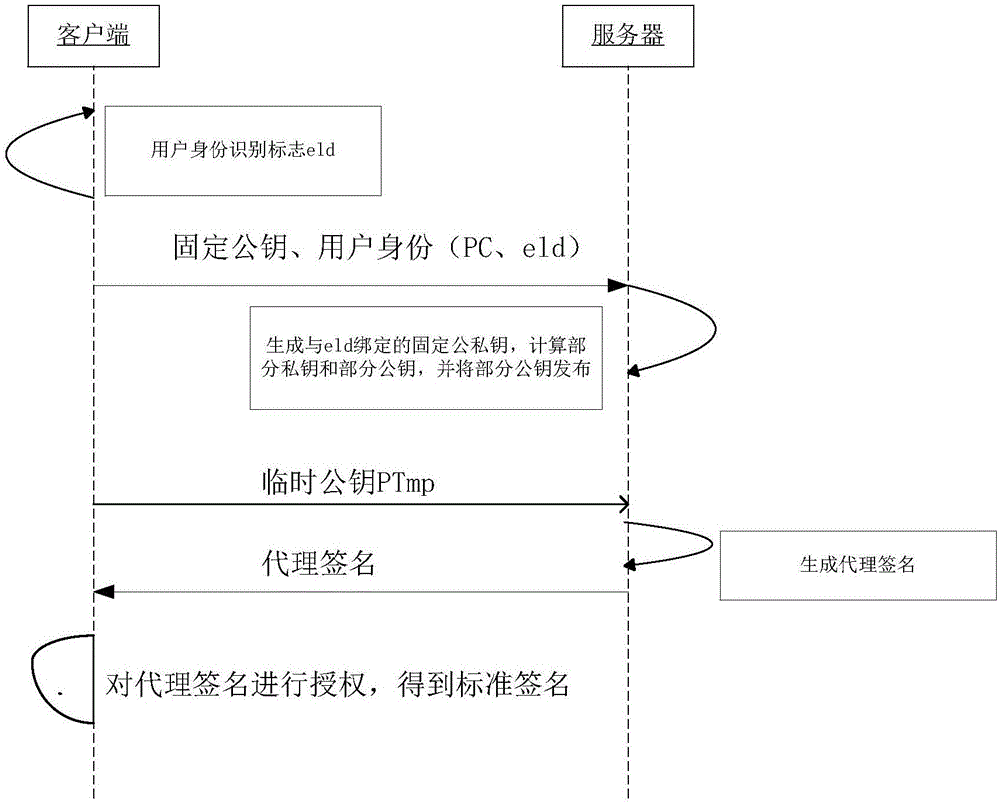
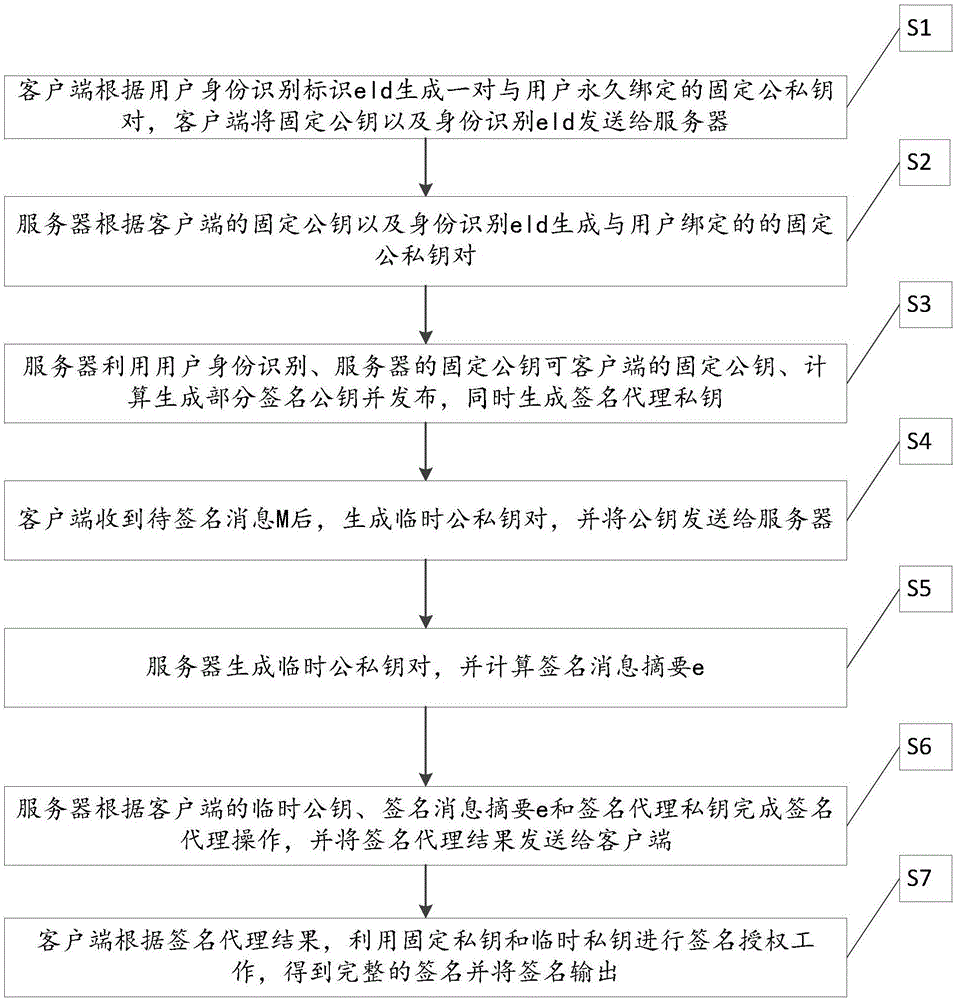
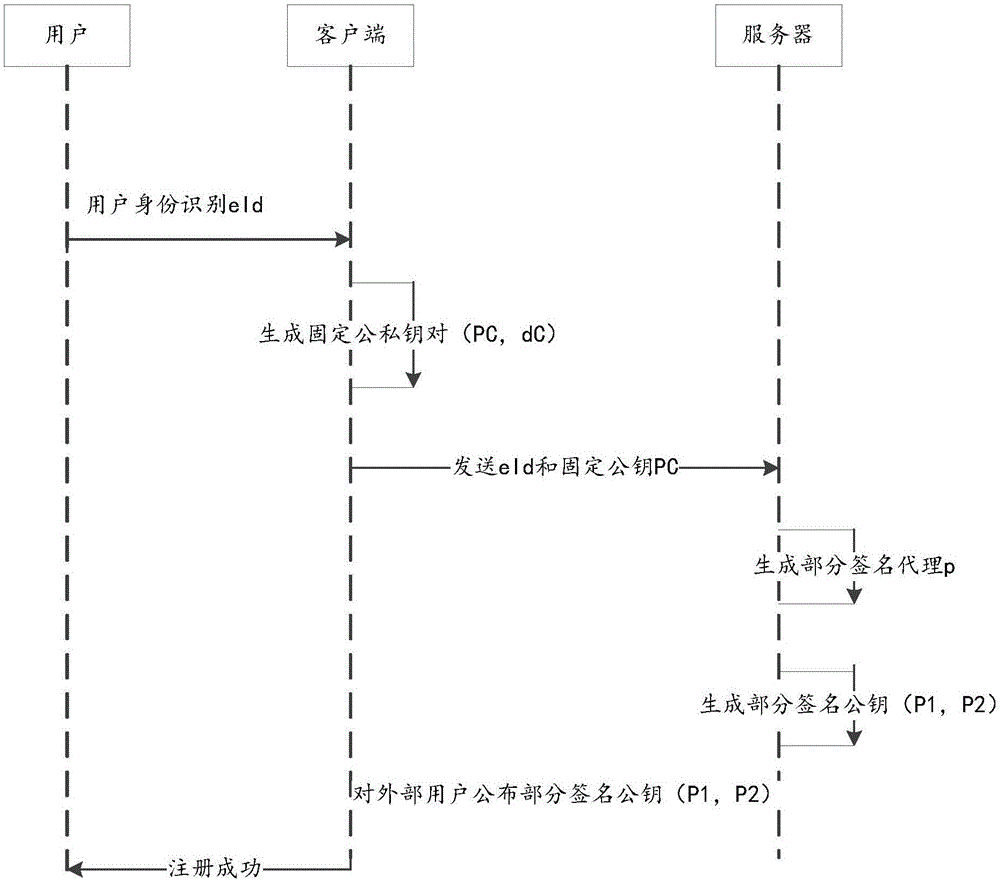
[0033] as attached figure 1 , figure 2 and image 3 As shown, an identity-based distributed signature method, the distributed signature method includes the following steps:
[0034] Both the client and the server support the SM2 standard algorithm, the SM2 elliptic curve parameters E(Fp), G and n, the elliptic curve E is an elliptic curve defined on the finite prime number field Fp, and G is the nth order base point on the elliptic curve E. The user identity eld mentioned below refers to the one that can uniquely identify the user in a security domain (or within the application range of the information system), such as mobile phone number, email address, ip address, Weibo account, WeChat ID, QQ number , bank acc...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com