Machine-type communication authentication and key agreement method based on proxy
A technology of machine-type communication and key agreement, which is applied in the field of communication, can solve problems such as battery capacity that does not consider the long-term communication ability of the group, and achieve the effects of avoiding signaling congestion, reducing signaling load, and ensuring confidentiality and reliability
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
[0030] The present invention will be further described below in conjunction with the accompanying drawings.
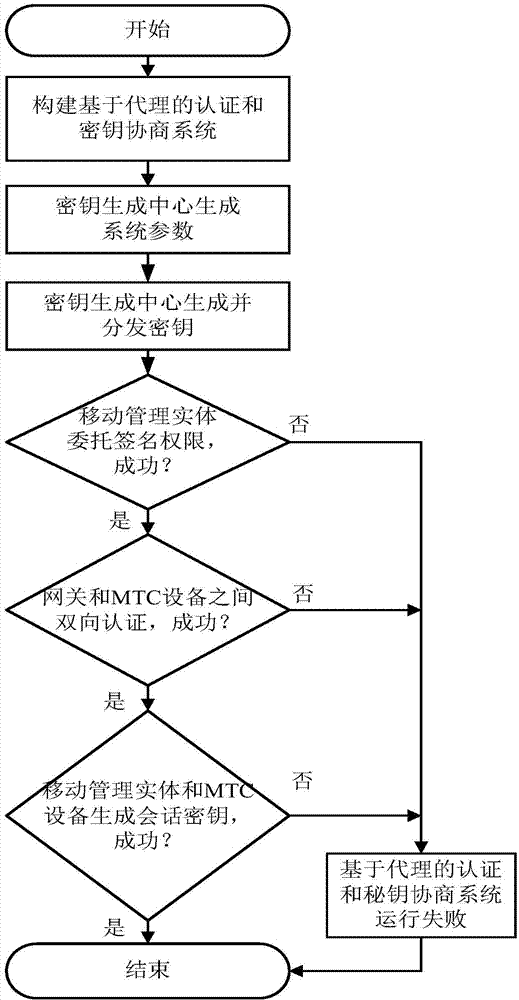
[0031] refer to figure 1 , the implementation steps of the present invention are as follows:
[0032] Step 1, build an agent-based authentication and key agreement system.
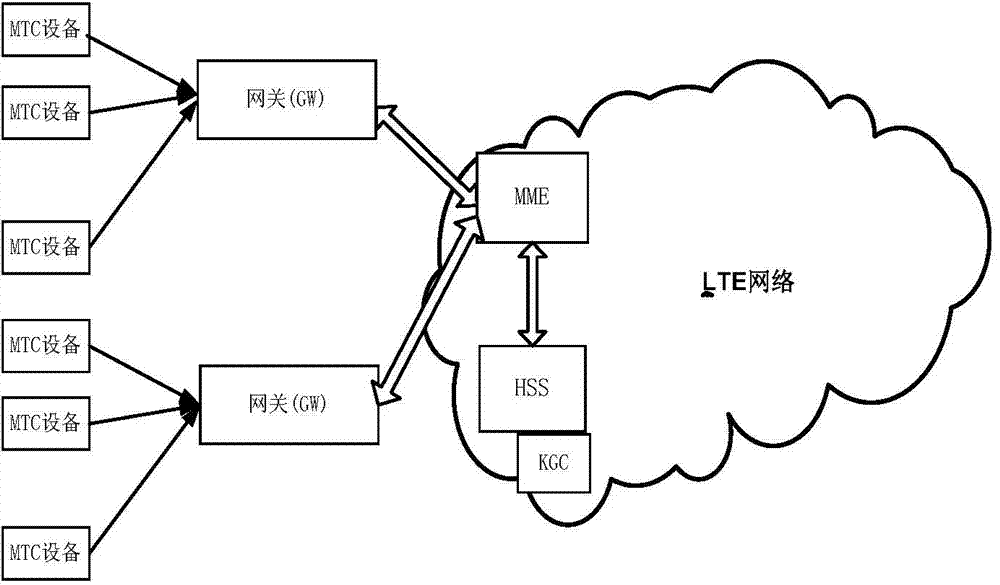
[0033] (1a) In the LTE network, the key generation center KGC and the home subscriber server HSS are physically connected together, and a temporary connection between the home subscriber server HSS and the mobility management entity MME is generated through the network domain security mechanism NDS Session key to build a parameter transmission channel;
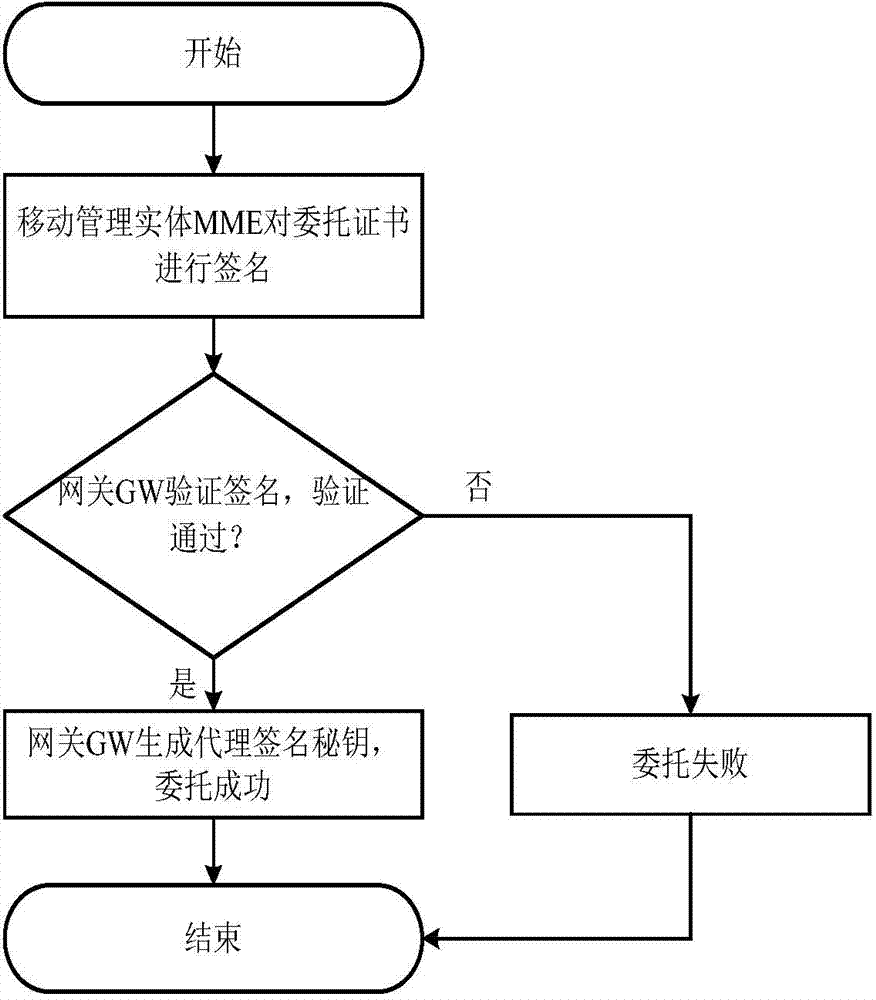
[0034] (1b) Between the LTE network and the machine type communication device MTCD, a proxy authorization channel is established between the gateway GW and the mobility management entity MME through the following process:
[0035] First, the gateway GW uses the device certificate stored by itself to complete the device authentication with the co...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com