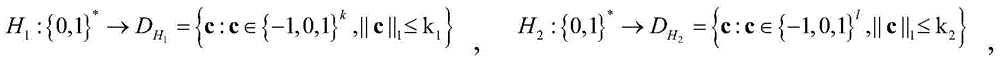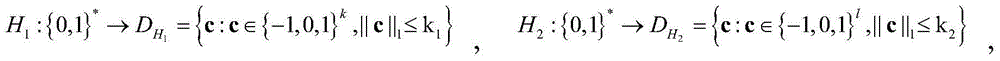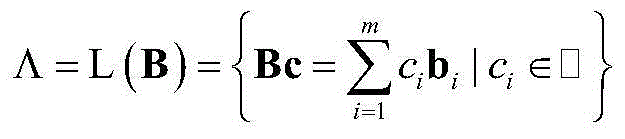Proxy signature method and system based on lattice
A proxy signature and proxy technology, which is applied in the field of information security and encryption, can solve problems such as increasing the norm of the private key, unprotected proxy, and excessive public and private key sizes.
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
[0067] The invention discloses a lattice-based proxy signature method. First, some knowledge is clarified:
[0068] 1. Grid, let B=(b 1 ,...,b m )∈□ m×m is a matrix of order m×m, and b 1 ,...,b m ∈□ m is a linearly independent vector. An m-dimensional full-rank lattice Λ is defined as the vector b 1 ,...,b m The set formed by the linear combination of all integer coefficients, that is
[0069]
[0070] here b 1 ,...,b m constitute a set of basis for lattice Λ. Our main concern is the integer lattice, the lattice
[0071] Definition 1 Let α be a vector, then l of α p The norm is defined as ||α|| p =(∑α i p ) 1 / p , when p=2, we call the Euclidean norm. For the Euclidean norm, we generally put ||α|| 2 The subscript in is omitted, and is recorded as ||α||.
[0072] 2. Difficult questions:
[0073] Definition 2[14] The shortest vector problem (shortest vector problem, SVP): given a set of bases B of the lattice, find the shortest vector u in the lattice L(B...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com