Patents
Literature
33results about How to "Protect personal privacy information" patented technology
Efficacy Topic
Property
Owner
Technical Advancement
Application Domain
Technology Topic
Technology Field Word
Patent Country/Region
Patent Type
Patent Status
Application Year
Inventor
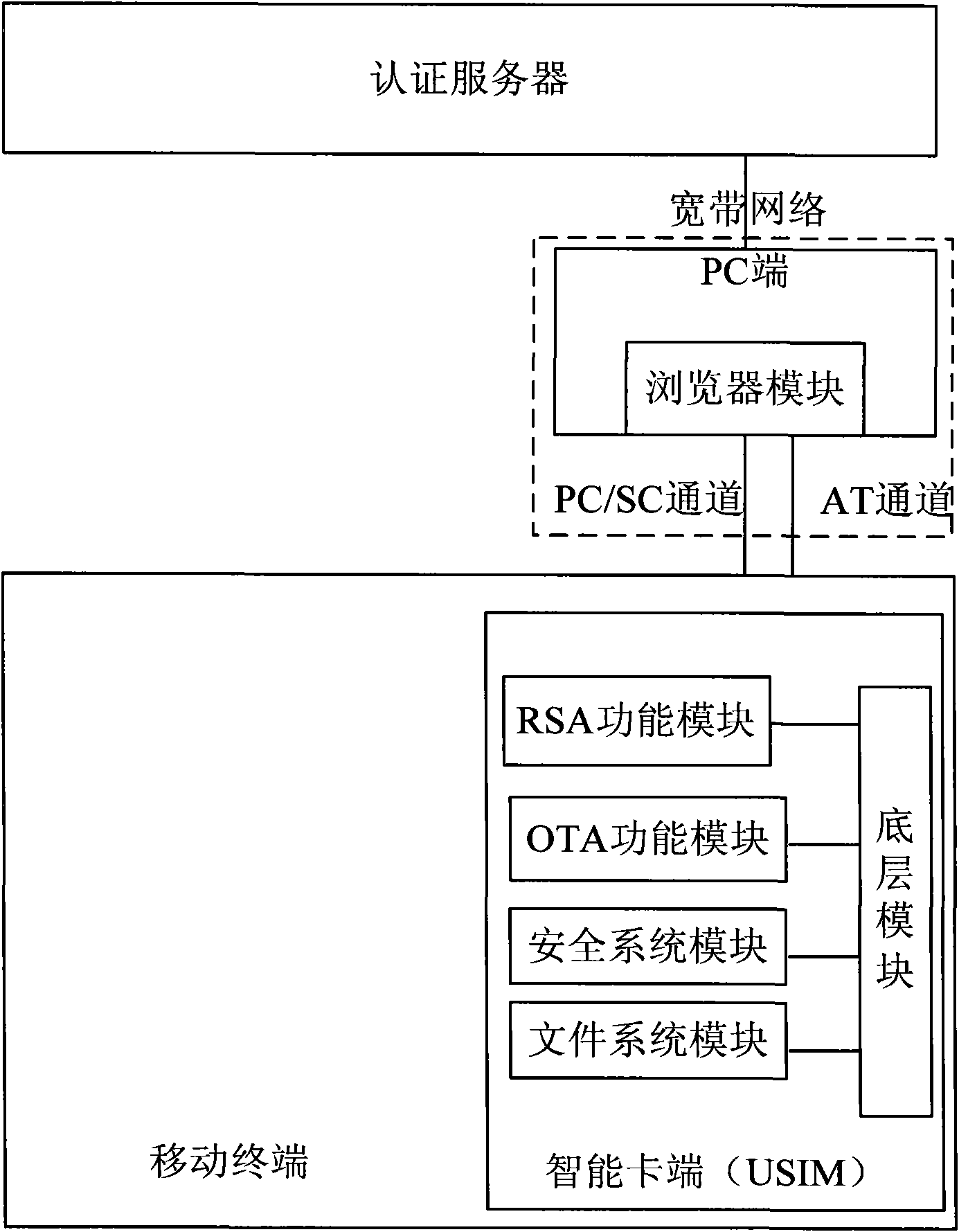
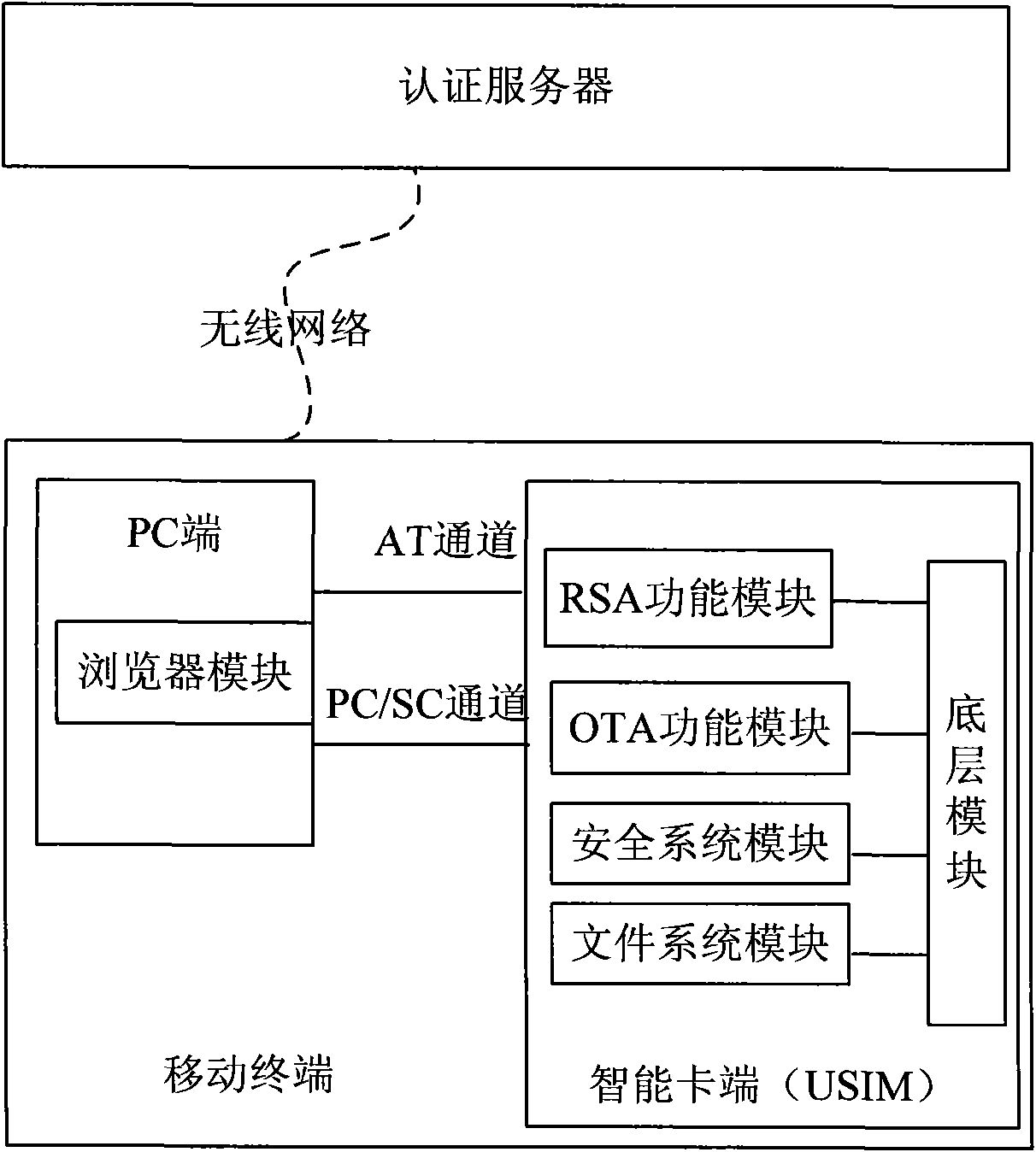
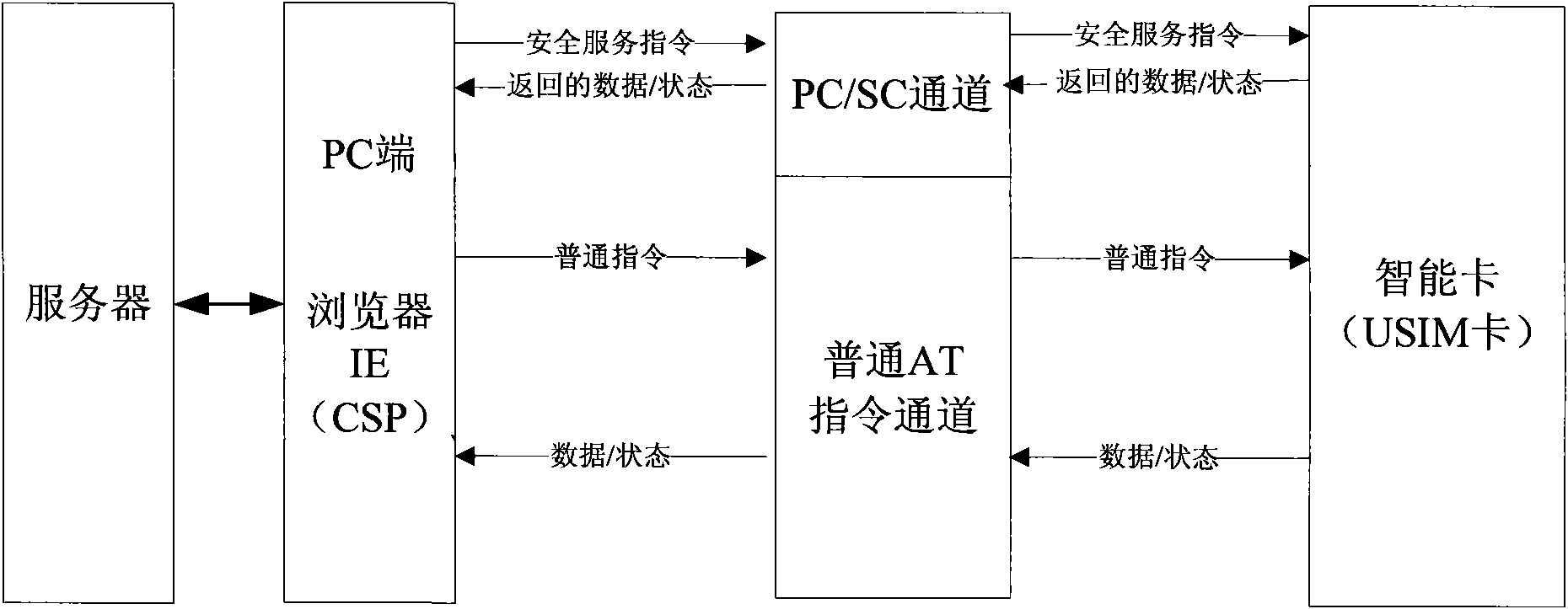
Mobile terminal signature-based remote payment system and method
InactiveCN101938520AImprove securityImprove portabilityPayment protocolsTransmissionSmart cardAuthentication server
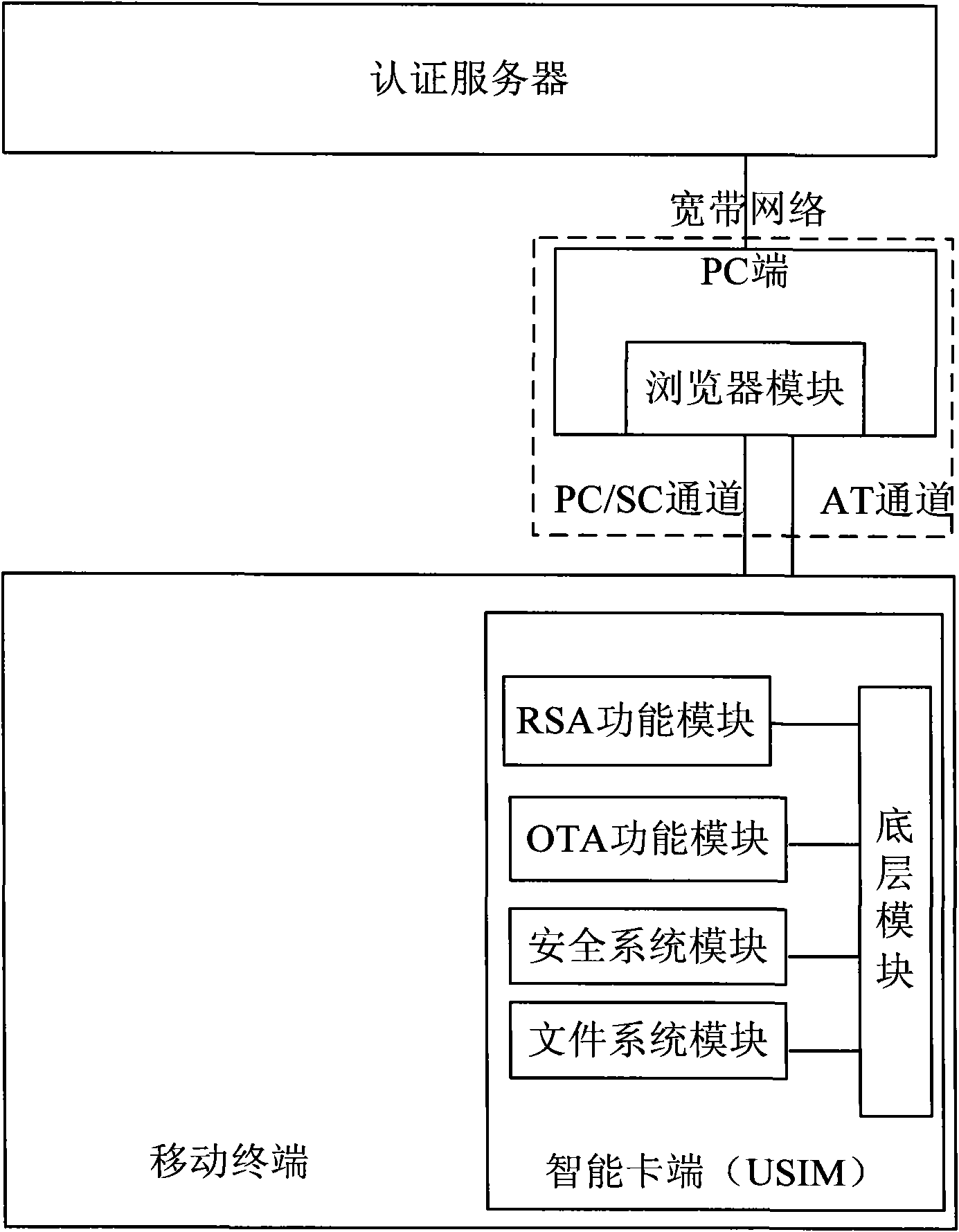
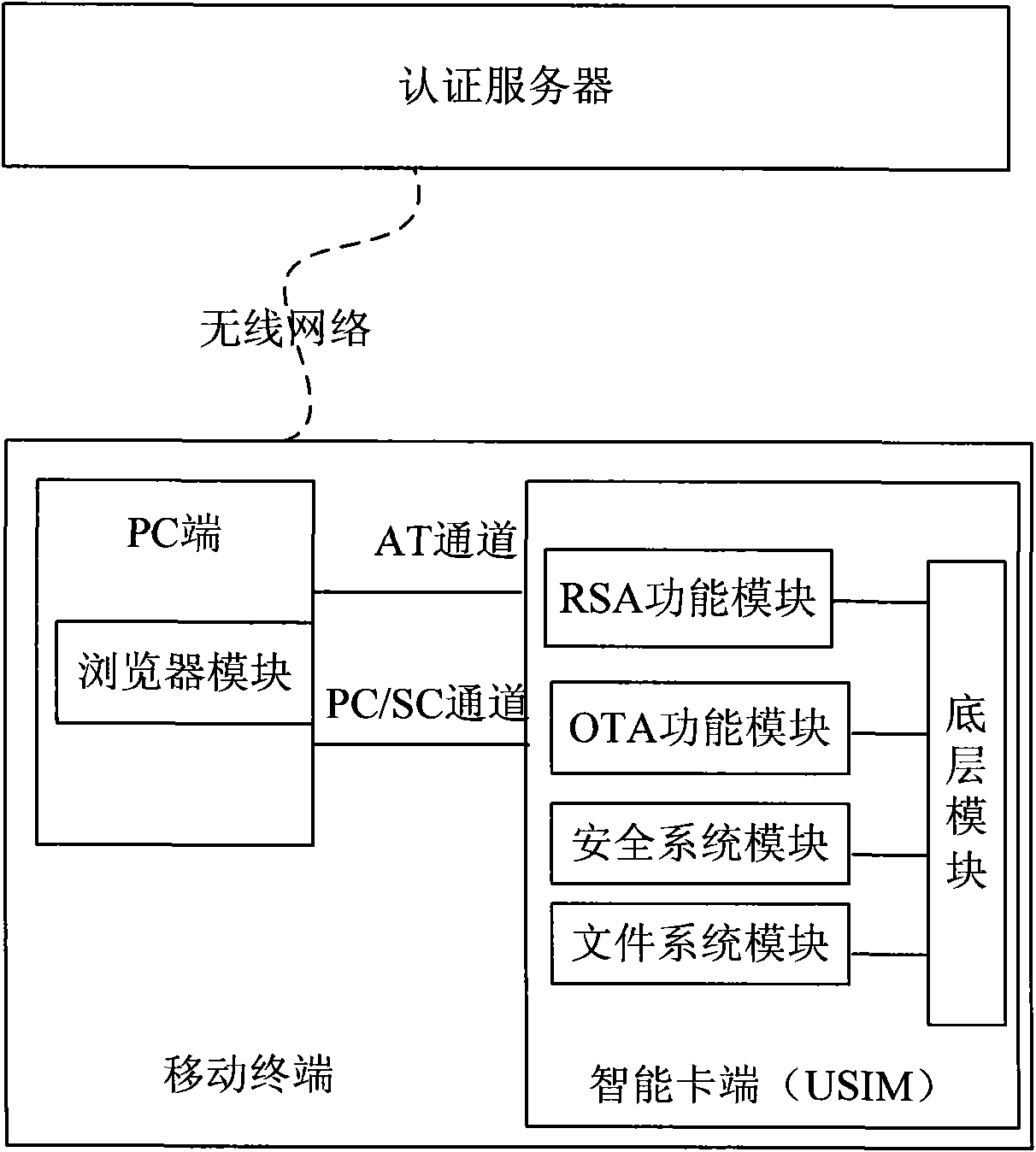
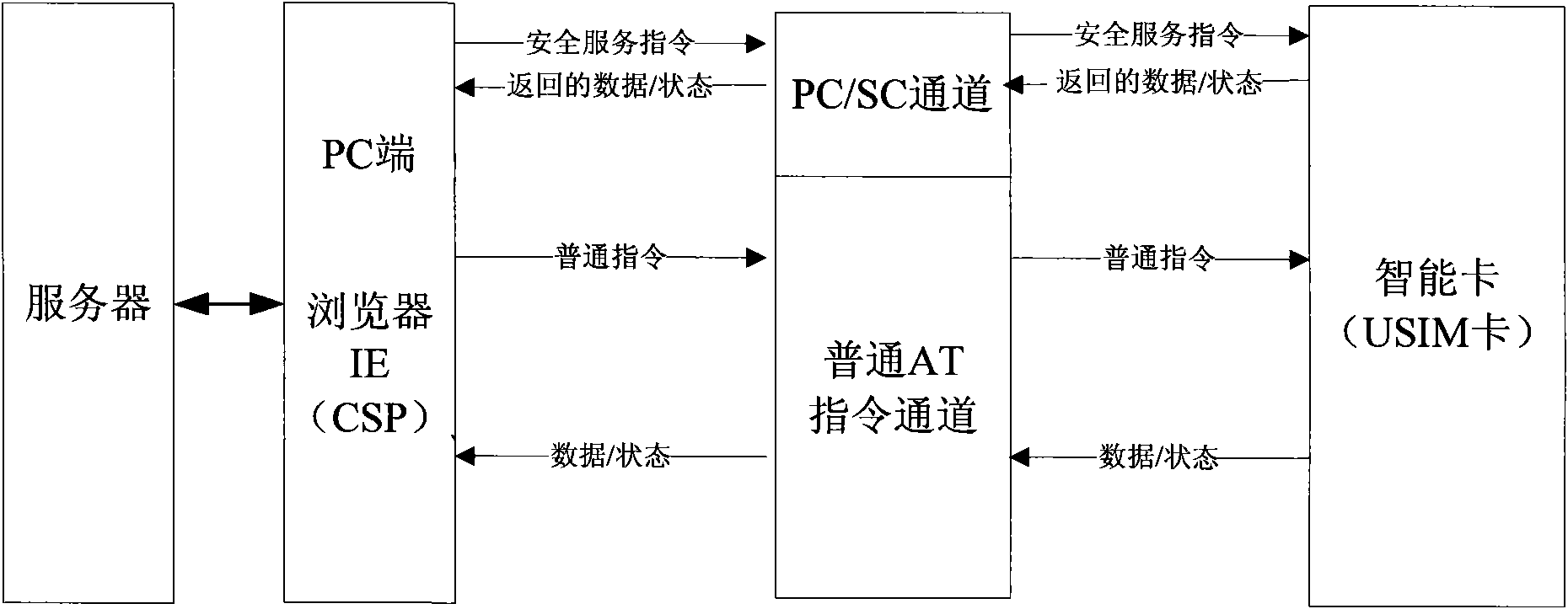
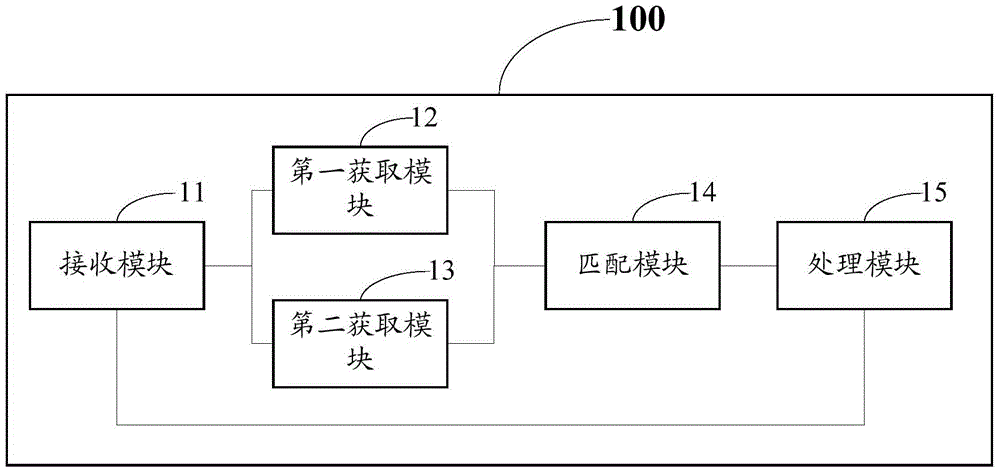
The invention discloses a mobile terminal signature-based remote payment system and a mobile terminal signature-based remote payment method, and a mobile terminal and an intelligent card of the mobile terminal in the system. The intelligent card (such as a USIM card) of the mobile terminal is improved, and a PC / SC channel interacted with the PC side is provided; a digital certificate is stored on the intelligent card, and during authentication, after being exported by the intelligent card, the stored digital certificate is sent by the mobile terminal to an authentication server for certificate register; and the authentication server transmits a signature instruction to the mobile terminal, the mobile terminal sends a private key signature instruction to the built-in intelligent card, and a signature result is sent by the intelligent card and is reported to the authentication server by the mobile terminal, wherein the digital certificate can be acquired by interacting the intelligent card with the authentication server on line. The remote payment system has high safety and portability, is convenient for users to use during remote payment, and is favorable for protecting personal privacy information of the users and guaranteeing the safety of the remote payment.
Owner:ZTE CORP
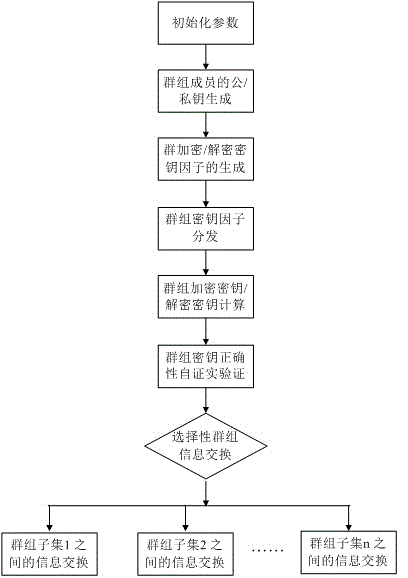
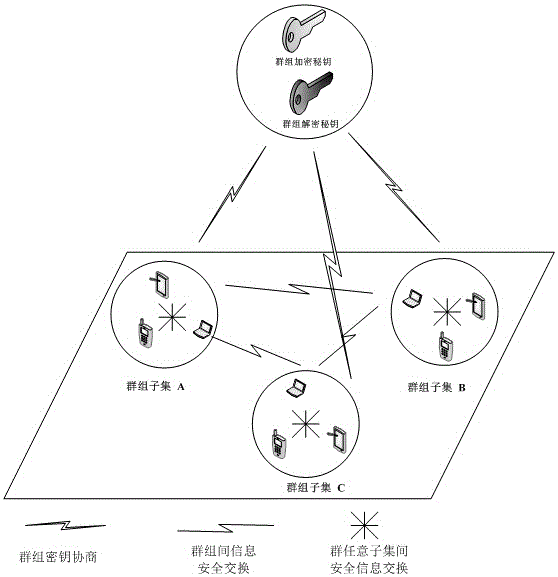
Flexible asymmetric group key negotiation method
ActiveCN106027241AConducive to the protection of personal privacy informationProtect personal privacy informationKey distribution for secure communicationNon symmetricProtocol for Carrying Authentication for Network Access
The invention discloses a flexible asymmetric group key negotiation method. The method comprises the steps of carrying out parameter initialization by members participating in group key negotiation, thereby generating public / private key pairs; blinding group contribution key shares through the public / private key pairs, and broadcasting group key shares; after the rest members receive corresponding broadcasting key shares, carrying out combination calculation, thereby obtaining group keys; and verifying whether calculated group keys are correct or not by the group members, encrypting communication information through the group keys if the calculated group keys are correct, and exchanging group security information. According to the method, members in or out of a group can select any one subset object in the group for secret information exchange; an object not selected by an information sender cannot decrypt the shared information; the group members can negotiate an encryption key and a decryption key which are consistent; the group members can verify the correctness of the keys; anonymity of the members participating in group key negotiation can be realized; and the personal private information of the group members can be protected.
Owner:河南招源科技有限公司
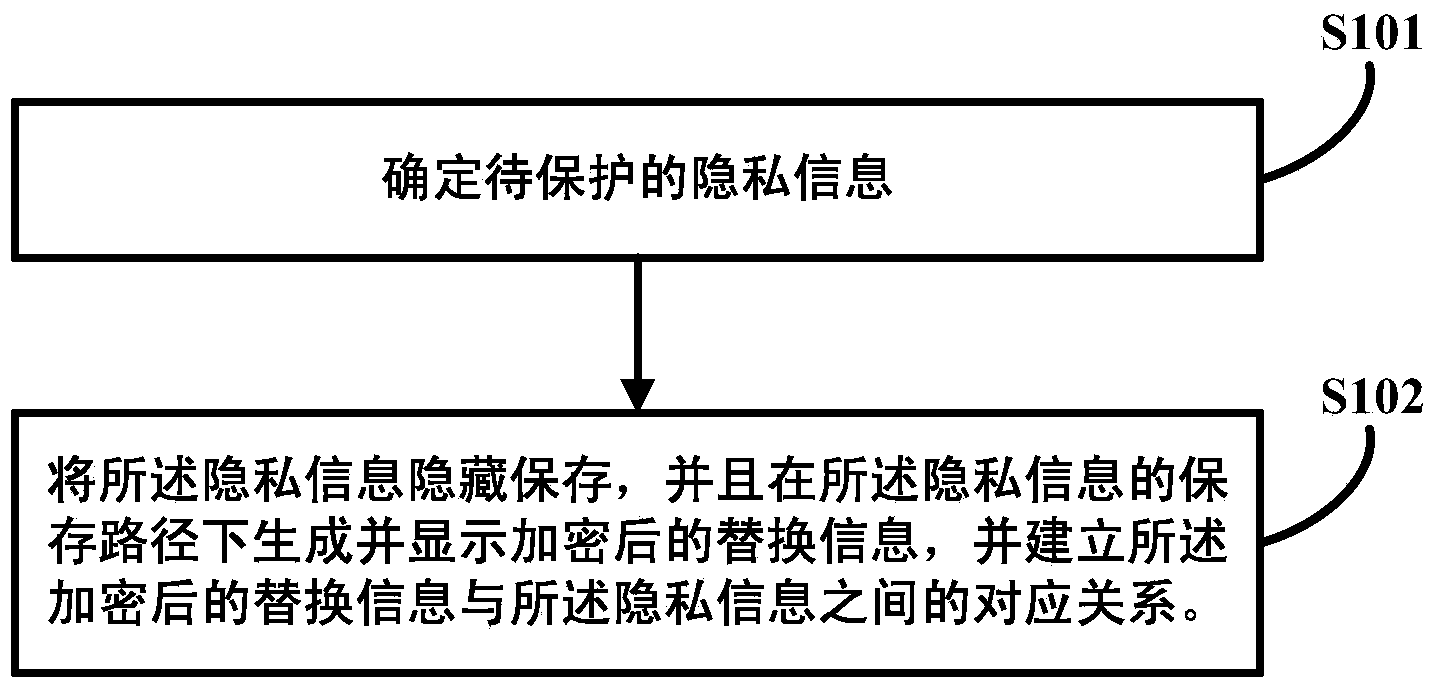
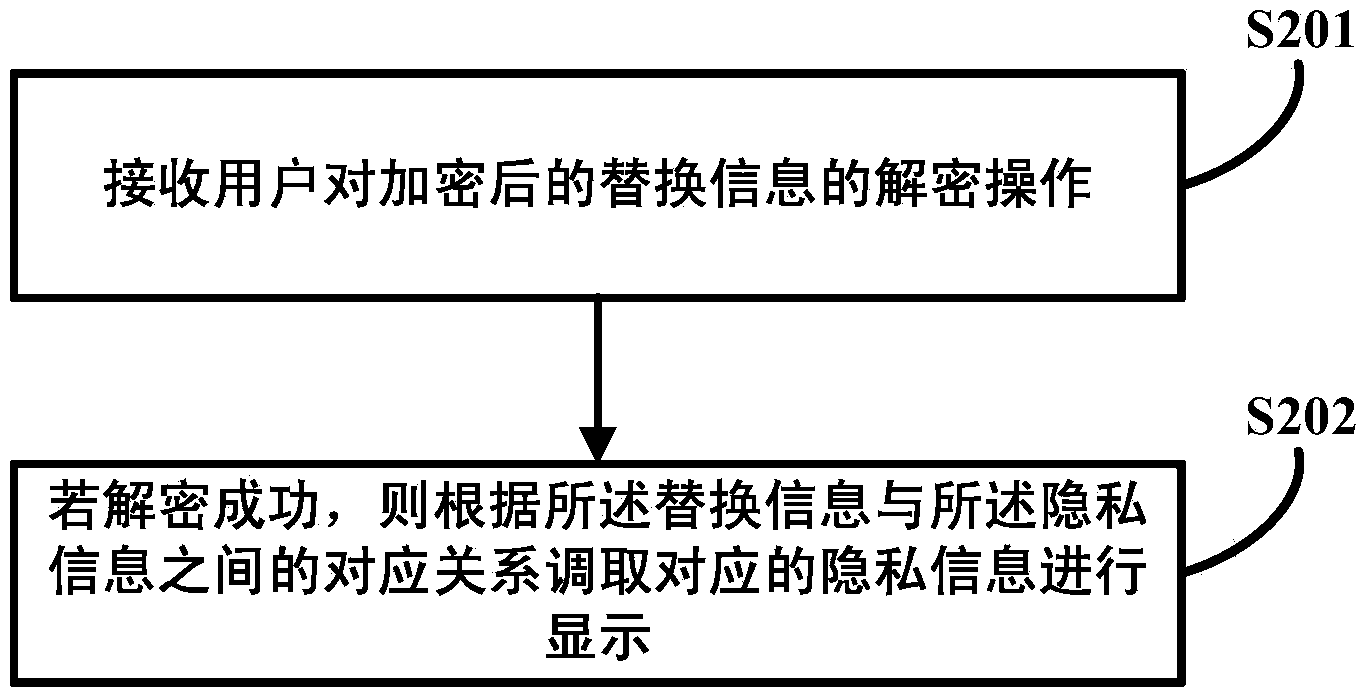
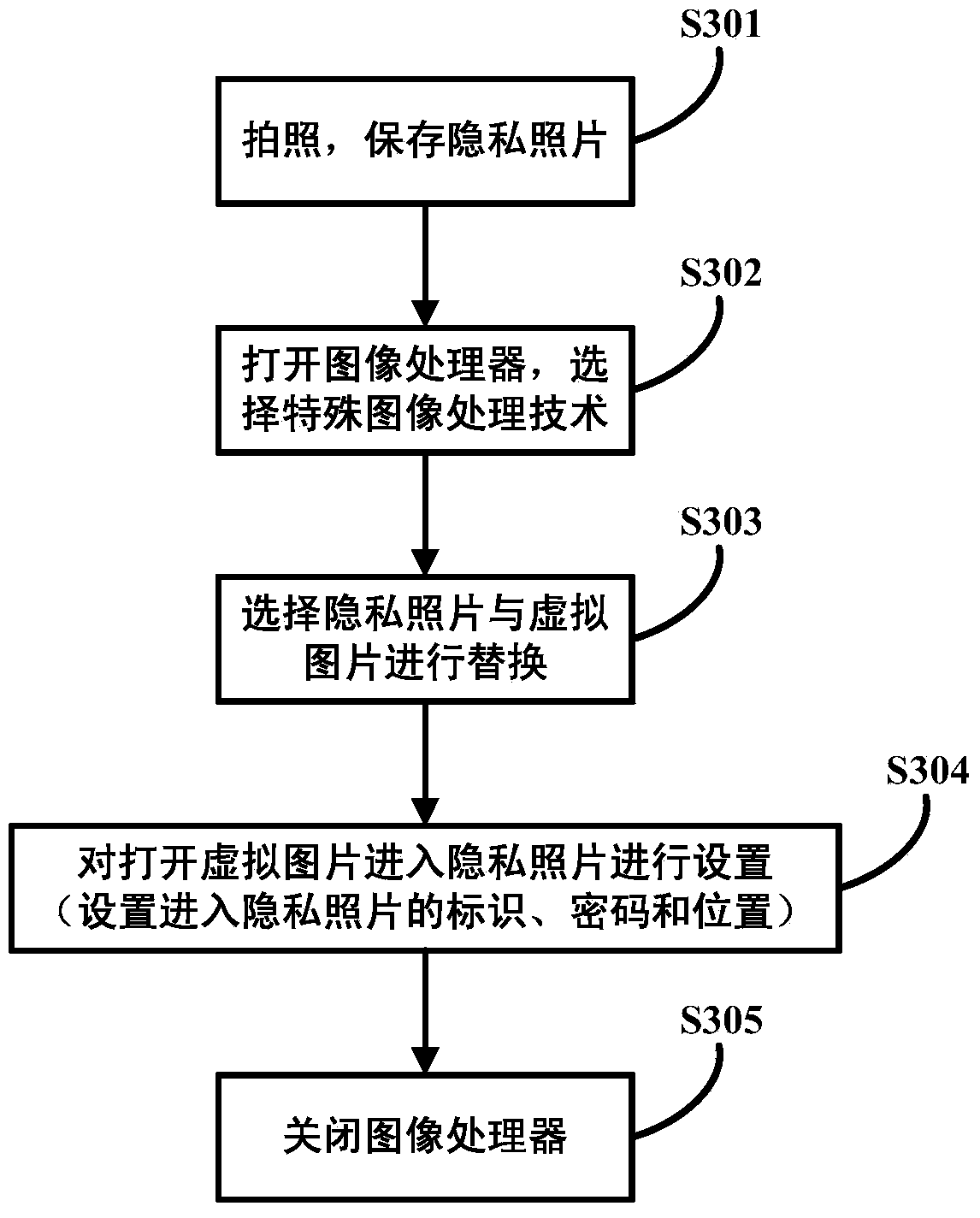
Method and device for protecting and displaying privacy information
InactiveCN103559451AEliminate the leading roleProtect personal privacy informationDigital data protectionInternet privacyInformation hiding
The invention discloses a method and a device for protecting and displaying privacy information. The method comprises the steps of: determining to-be-protected privacy information; saving the privacy information in a hiding manner and generating and displaying encrypted replaced information in a save path of the privacy information, and establishing a corresponding relationship between the encrypted replaced information and the privacy information. Through the technical scheme, the problem of privacy information leakage due to that the conventional encryption protection method may generate and display an encryption mark on the privacy information to guide a non-user is solved. The privacy information is displayed as non-privacy normal information by generating and displaying the encrypted replaced information in the save path of the privacy information, the guide function of the conventional encryption mark for a non-user is removed, the user per se is helped to save the privacy information on the terminal in the hiding manner, random encryption and recovery functions are achieved, and personal privacy information of the user per se is protected at any time.
Owner:YULONG COMPUTER TELECOMM SCI (SHENZHEN) CO LTD
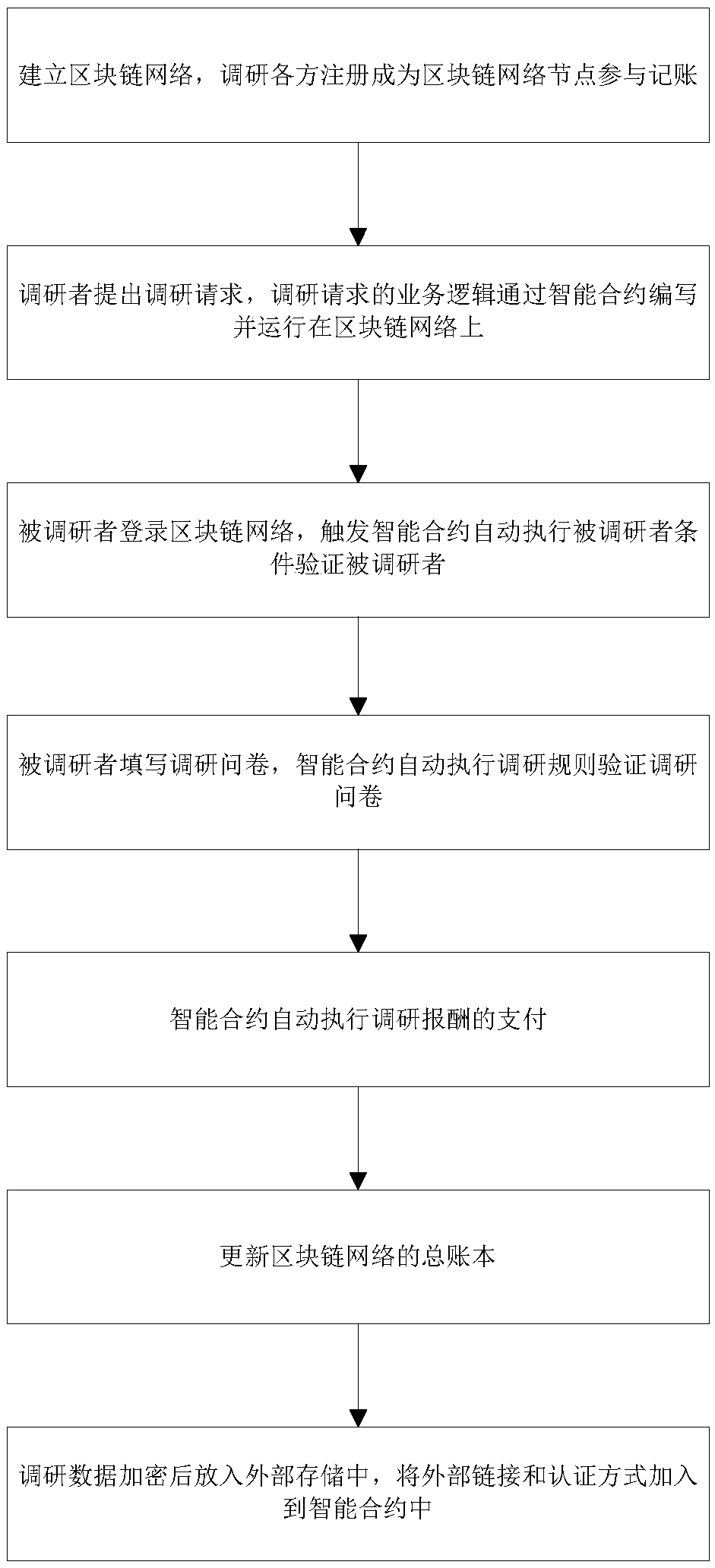
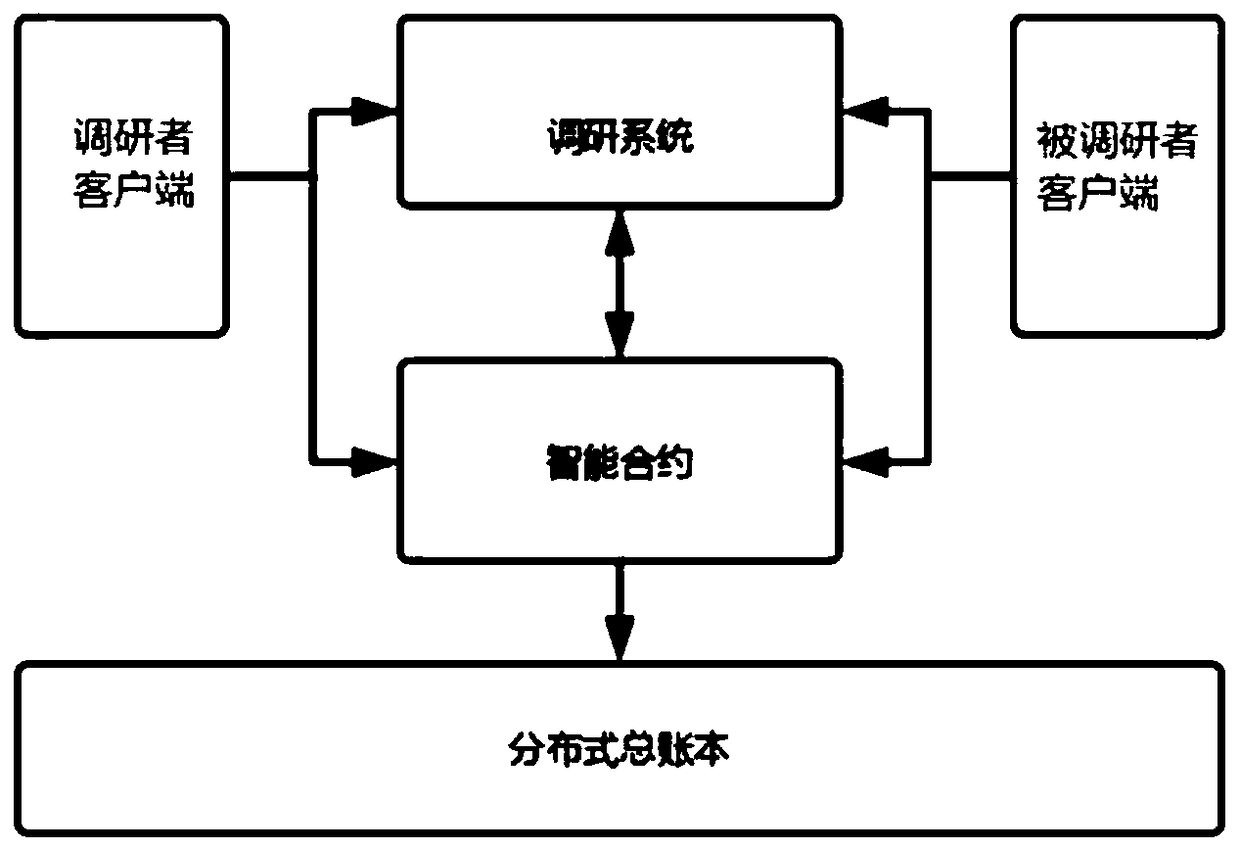
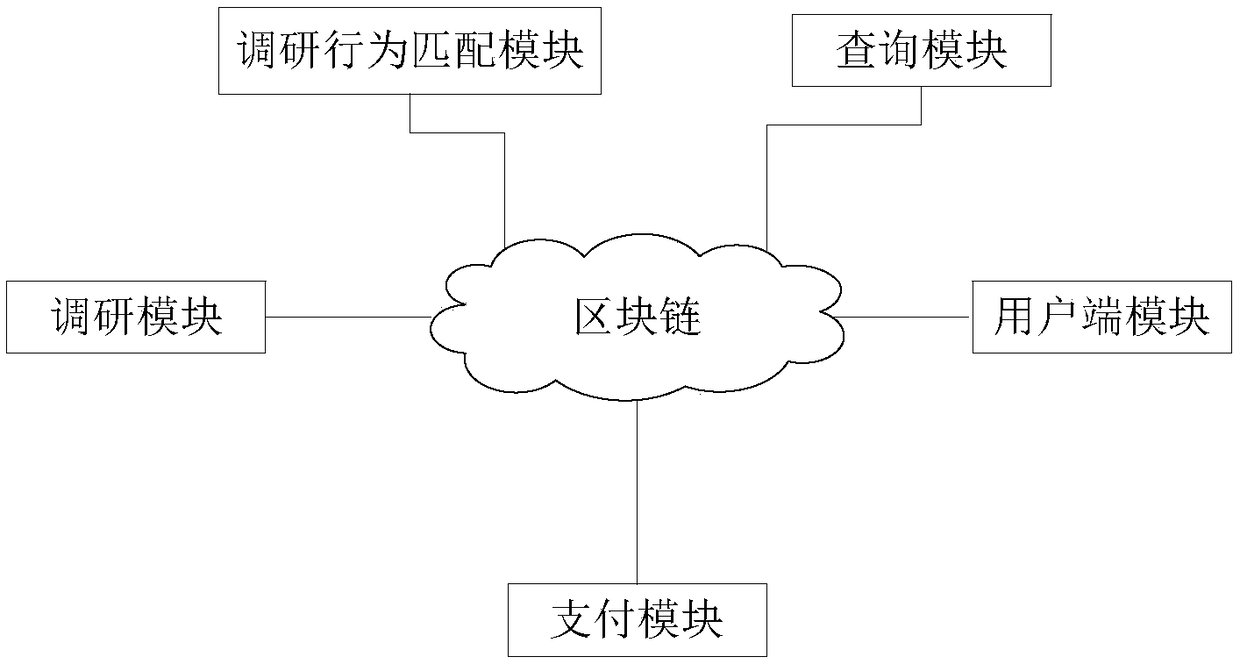
A research method and system based on block chain
PendingCN109146547AReduce storage costsIncrease credibilityMarketingInvestigation methodsResearch data
The invention relates to the technical field of block chain, intelligent contract and user investigation, in particular to an investigation method and system based on block chain. The invention discloses a research method based on block chain, which utilizes block chain and intelligent contract technology, realizes the decentralized data and reward exchange process, realizes double blindness between the researcher and the investigated, ensures the credibility of the research data, and protects the personal privacy of the user. The invention also provides a research system based on a block chain, comprising a client, a research system, an intelligent contract and a distributed general ledger.
Owner:武汉研众科技有限公司
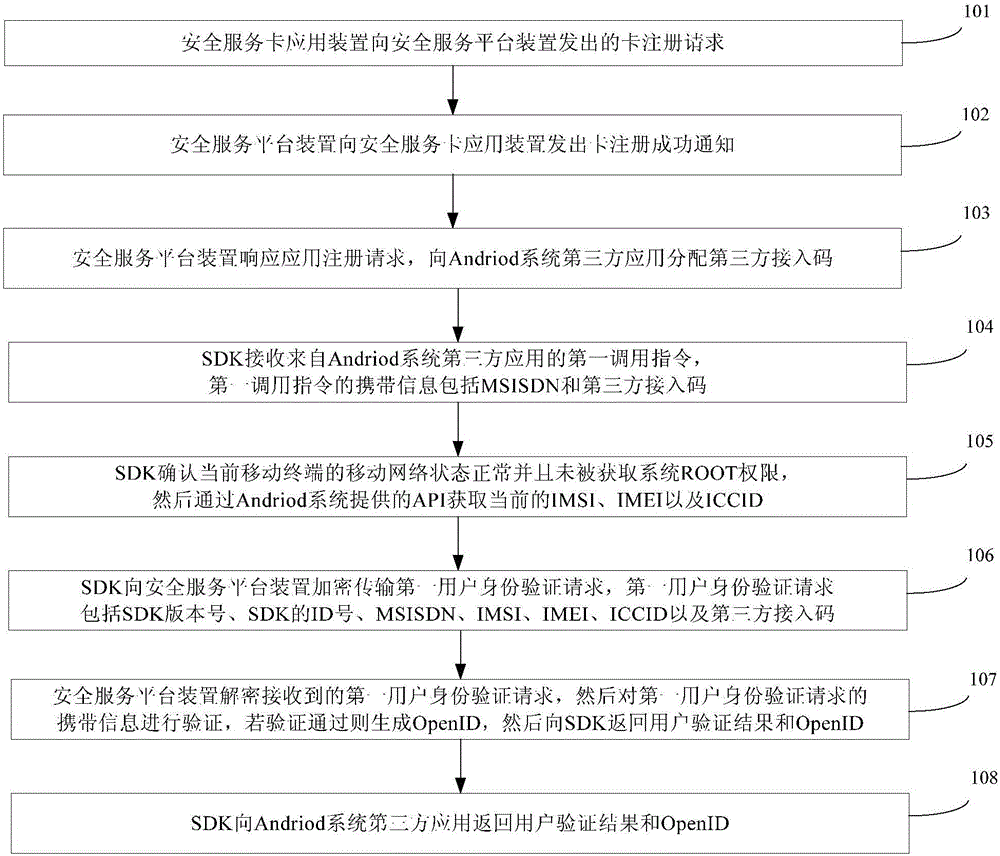
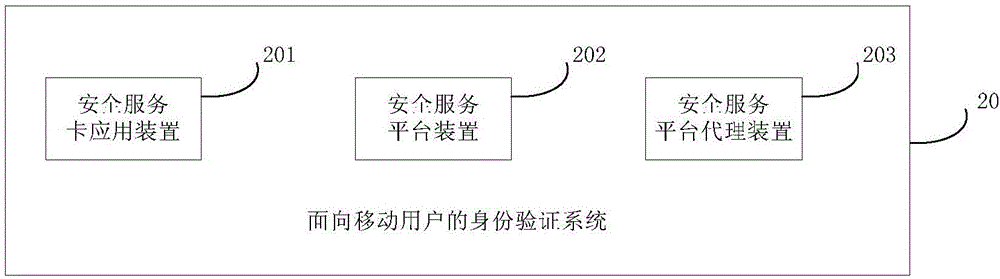
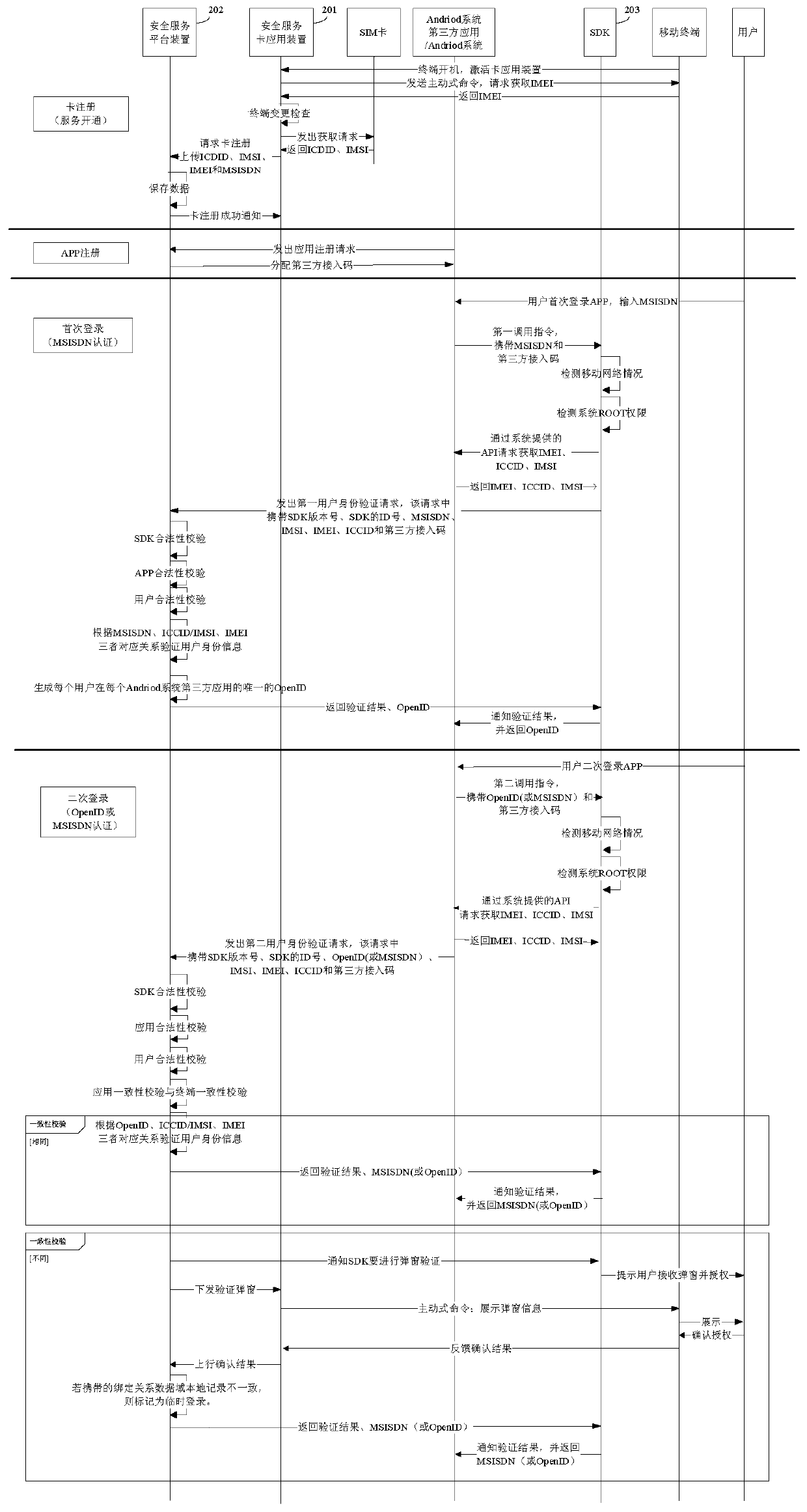
Authentication method and system for mobile subscribers
ActiveCN106304074AProtect personal privacy informationEasy to useSecurity arrangementInformation repositoryThird party
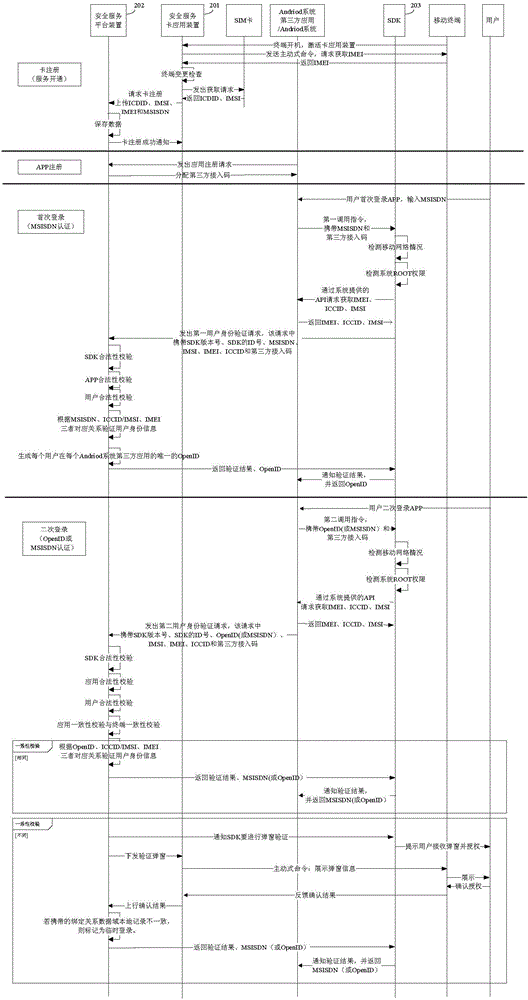
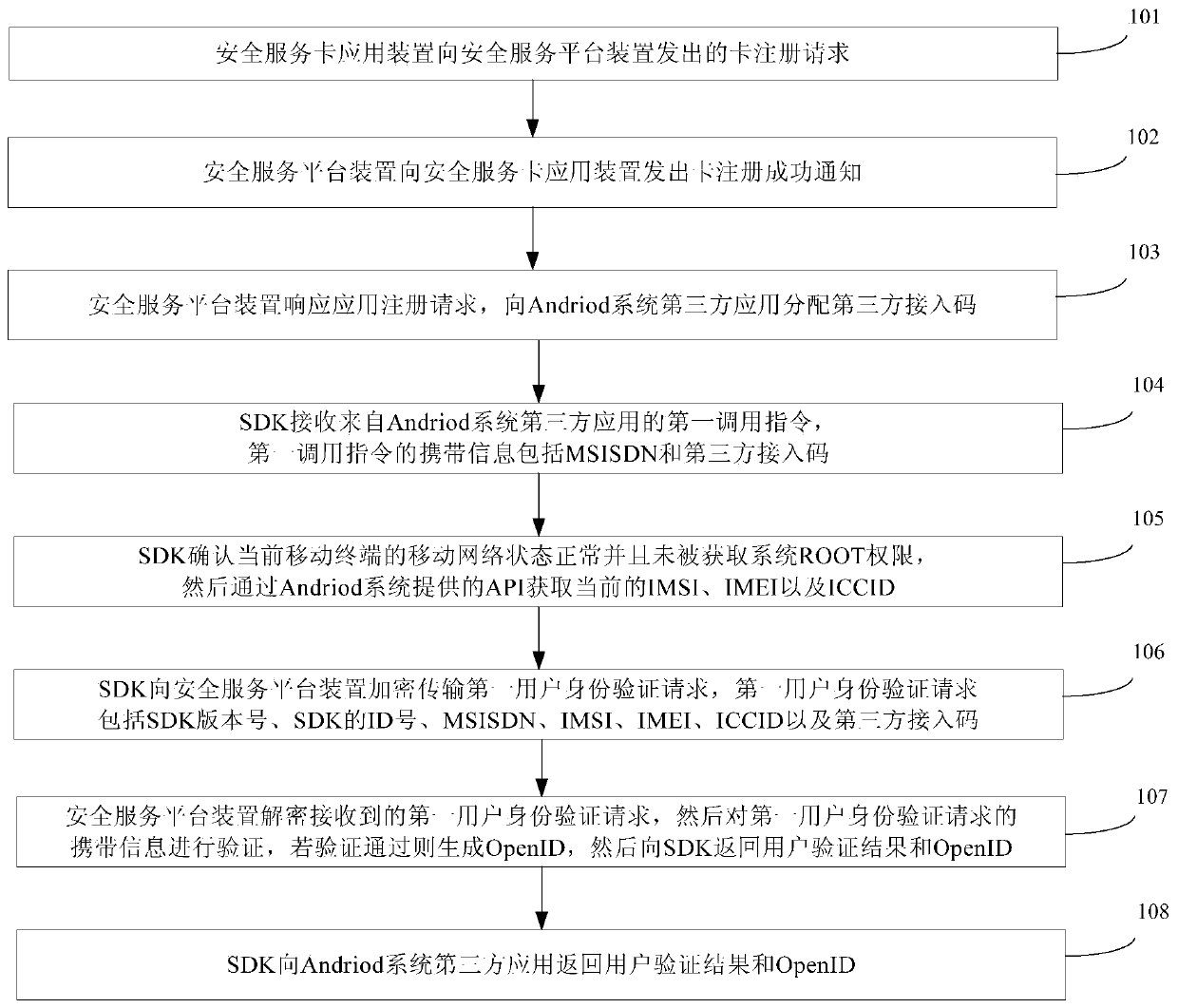
The invention provides an authentication method and system for mobile subscribers, which can realize the password-free registration and login and have advantages of convenience in use, high safety and low cost. The authentication method for the mobile subscribers of a third-party application of an Andriod system or an iOS system comprises the following steps: completing access registration of a third-party application on a safety service platform apparatus; and registering a safety service card application apparatus so as to establish a user information database; and when a user logs in at a first time, transmitting, by the safety service platform proxy apparatus SDK, a mobile phone number of a user to the safety service platform apparatus to perform the authentication, if the mobile phone number of the user passes the authentication, generating, by the safety service platform apparatus, an exclusive OpenID, and returning, by the safety service platform apparatus, a user authentication result and the OpenID to the third-party application by virtue of the SDK; and when the user logs in at a second time, transmitting, by the SDK, the OpenID to the safety service platform apparatus to perform the authentication, and if the OpenId passes the authentication, returning, by the safety service platform apparatus, the user authentication result and the user mobile phone number to the third-party application by virtue of the SDK.
Owner:尹子栋
Block chain-based investigation payment platform
InactiveCN108710808AGuarantee authenticityProtect personal privacy informationDigital data protectionPayment circuitsPayment orderSmart contract
The invention discloses a block chain-based investigation payment platform. The platform comprises an investigation module, a user side module and a payment module, wherein the investigation module isused for storing investigation contents published by different investigation publishers and payment information corresponding to the different investigation contents; the investigation contents and the corresponding payment information are written into a block chain in an intelligent contract form; the user side module is connected with the block chain and is used for receiving data transmitted by the investigation module; the payment module is connected with the block chain and is used for generating payment costs according to the search contents and the corresponding payment information after users complete operations of the user side module, and transmitting the payment costs and corresponding virtual currencies to block chain accounts of the users through the block chain so as to complete the payment of investigation rewards; and the investigation module, the user side module and the payment module are connected through the block chain. According to the investigation payment platform provided by the invention, when the investigation participators obtain reliable investigation rewards, personal account information of the investigation participators are not leaked, so that the confidence, for participating investigation behaviors, of the investigation participators is strengthened.
Owner:武汉研众科技有限公司
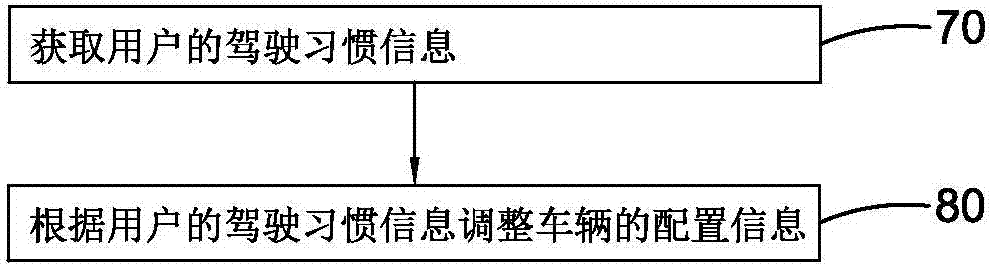
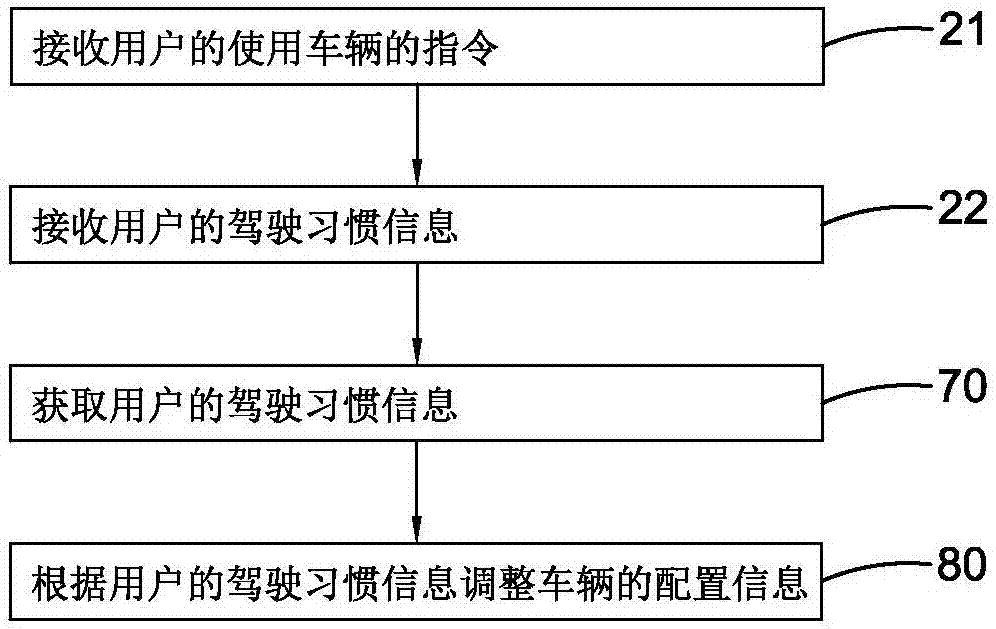
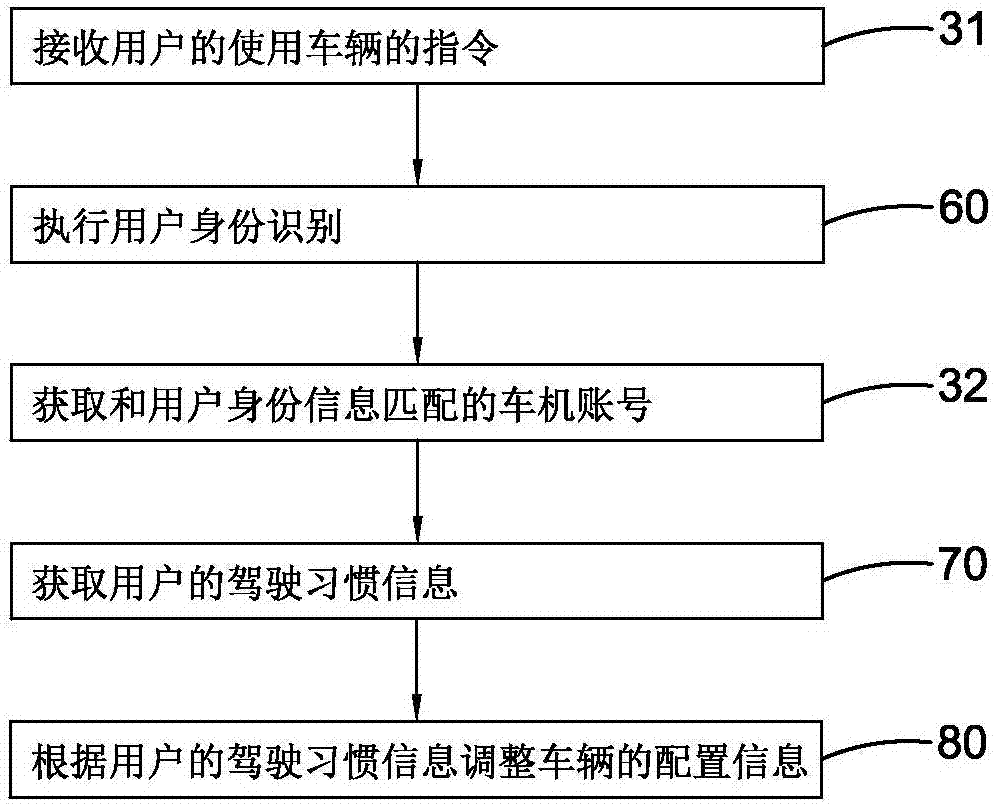
System and method for adjusting vehicle disposition on basis of driving habits
InactiveCN106926795ASuitable for driving environmentDriving habitsElectric/fluid circuitEngineeringAutomotive engineering
The invention provides a system and method for adjusting vehicle disposition on the basis of driving habits. The method for adjusting vehicle disposition on the basis the driving habits comprises the following steps that (A), driving habit information of at least one user is obtained; and (B), according to the driving habit information of the users, disposition information of at least one vehicle is adjusted. The disposition information of the vehicles can be adjusted through obtaining of the driving habit information of at least one user and on the basis of the driving habit information of the users, and therefore driving environments conforming to the driving habits of the users are provided for the users.
Owner:斑马信息科技有限公司
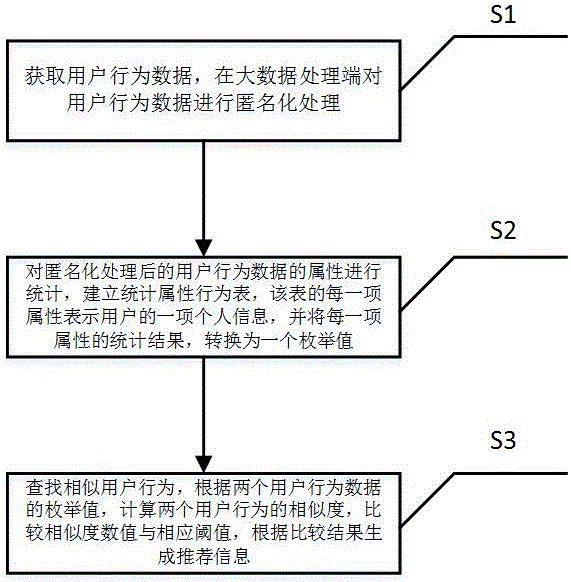
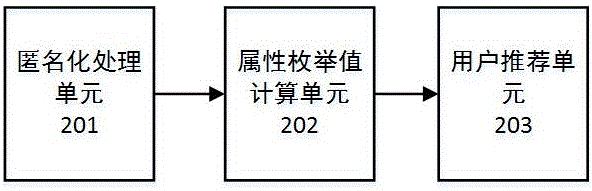
Big data recommendation method and system with privacy protection function
ActiveCN105138664AProtect personal privacy informationEasy to calculateDigital data protectionSpecial data processing applicationsPrivacy protectionComputer science
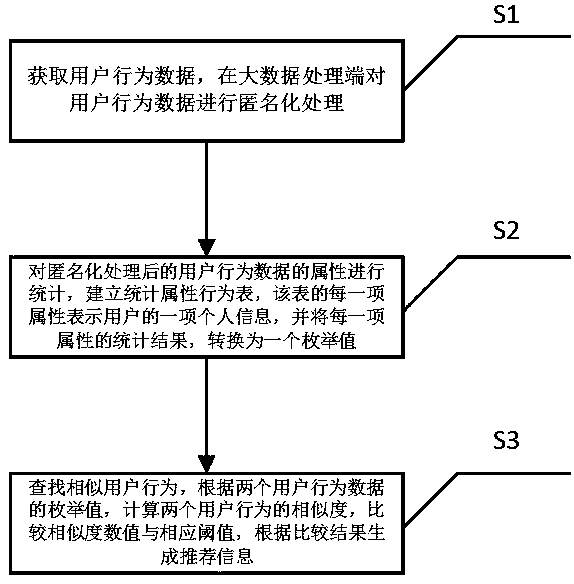
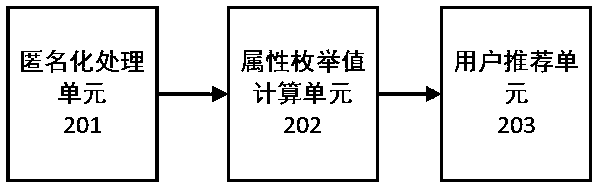
The invention discloses a big data recommendation method and system with the privacy protection function. The method includes the following steps that behavior data of users are acquired and are subjected to anonymization processing on a big data processing end; the attributes of the behavior data, subjected to anonymization processing, of the users are subjected to statistics, a statistical attribute behavior list is established, each attribute of the list represents one piece of personal information of each user, and the statistical result of each attribute is converted into an enumeration value; similar user behaviors are searched for, the similarity of every two user behaviors is calculated according to the enumeration values of data of the two user behaviors, a similarity value and a corresponding threshold are compared, and recommendation information is generated according to a comparison result. The big data recommendation method and system can protect the privacy of the users, encryption is not needed, use is convenient and fast, the calculation amount is small, and implementation is easy.
Owner:智网安云(武汉)信息技术有限公司
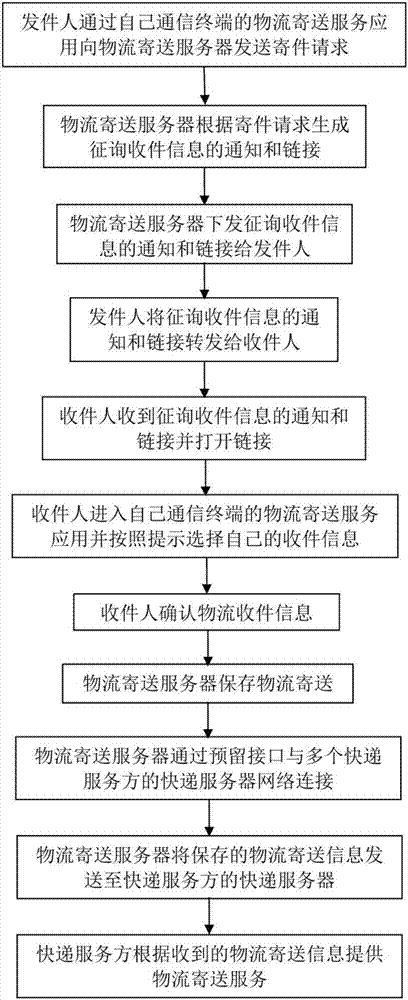
Intelligent logistics delivery method and system
InactiveCN107085786AEasy to passFacilitate communicationLogisticsInformation transmissionWorld Wide Web
The invention relates to an intelligent logistics delivery method and system. A logistics delivery server manages information of a sender and a recipient, so that logistics and express ordering and information transmission and communication between the sender and the recipient become very convenient, fast and safe, the personal privacy information of the sender and the recipient is protected to a great extent, and the accuracy, reality and non-repudiation of signing for express delivery are also ensured. The logistics delivery server asks for delivered information from the recipient and issues a link according to the information through WeChat messages, qq messages or text messages, the sender then transmits the express delivery notification information and the link to the recipient, the recipient opens the link after receiving the express delivery notification information and the link and selects a consignee address of the recipient according to the prompt, in this way, the sender does not need to obtain the recipient information from messages replied by the recipient in an existing traditional mode and to input the information in a related ordering system any more, and the process is very simple, convenient and more user-friendly.
Owner:张振斌
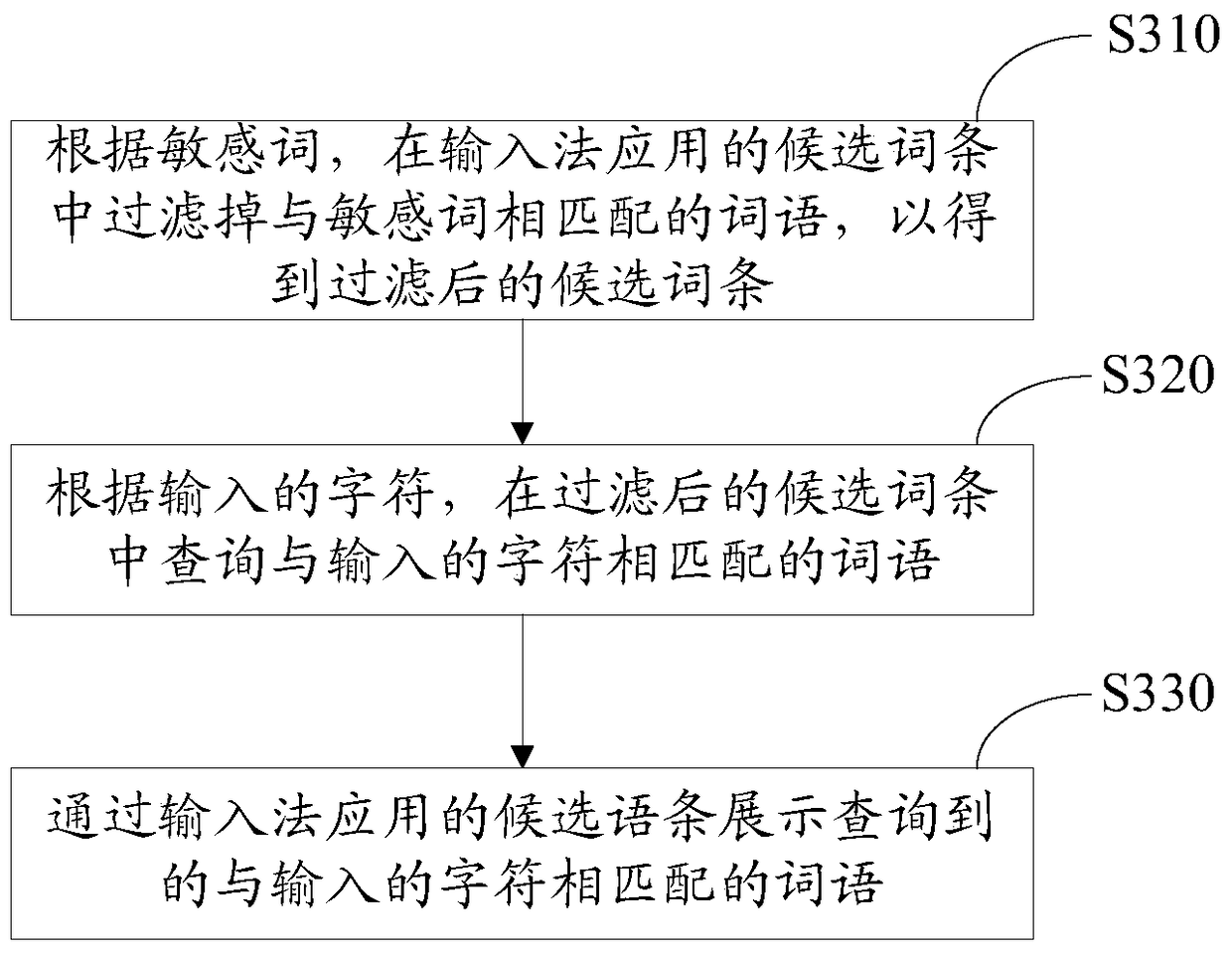
Application method and device for input method
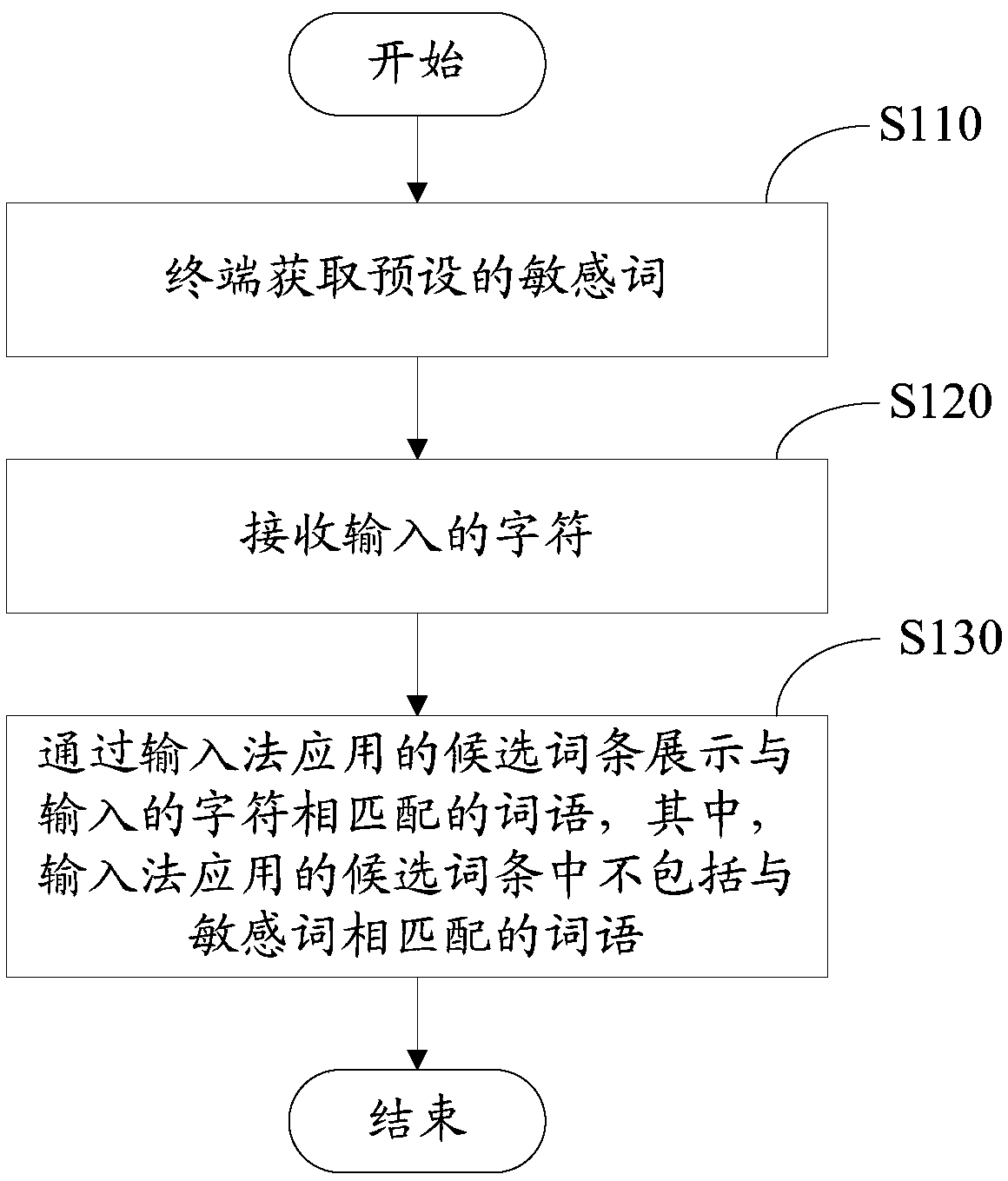
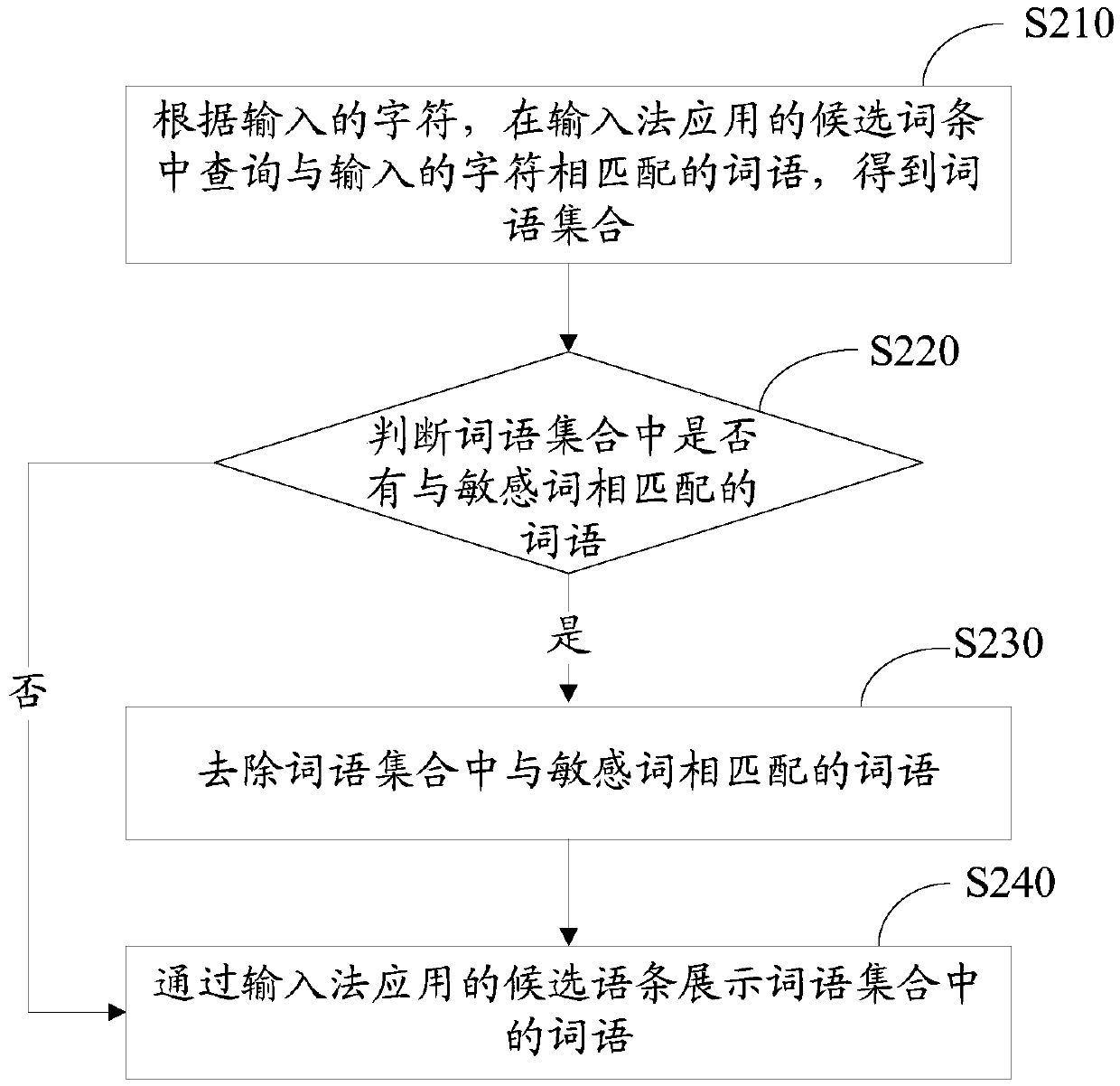
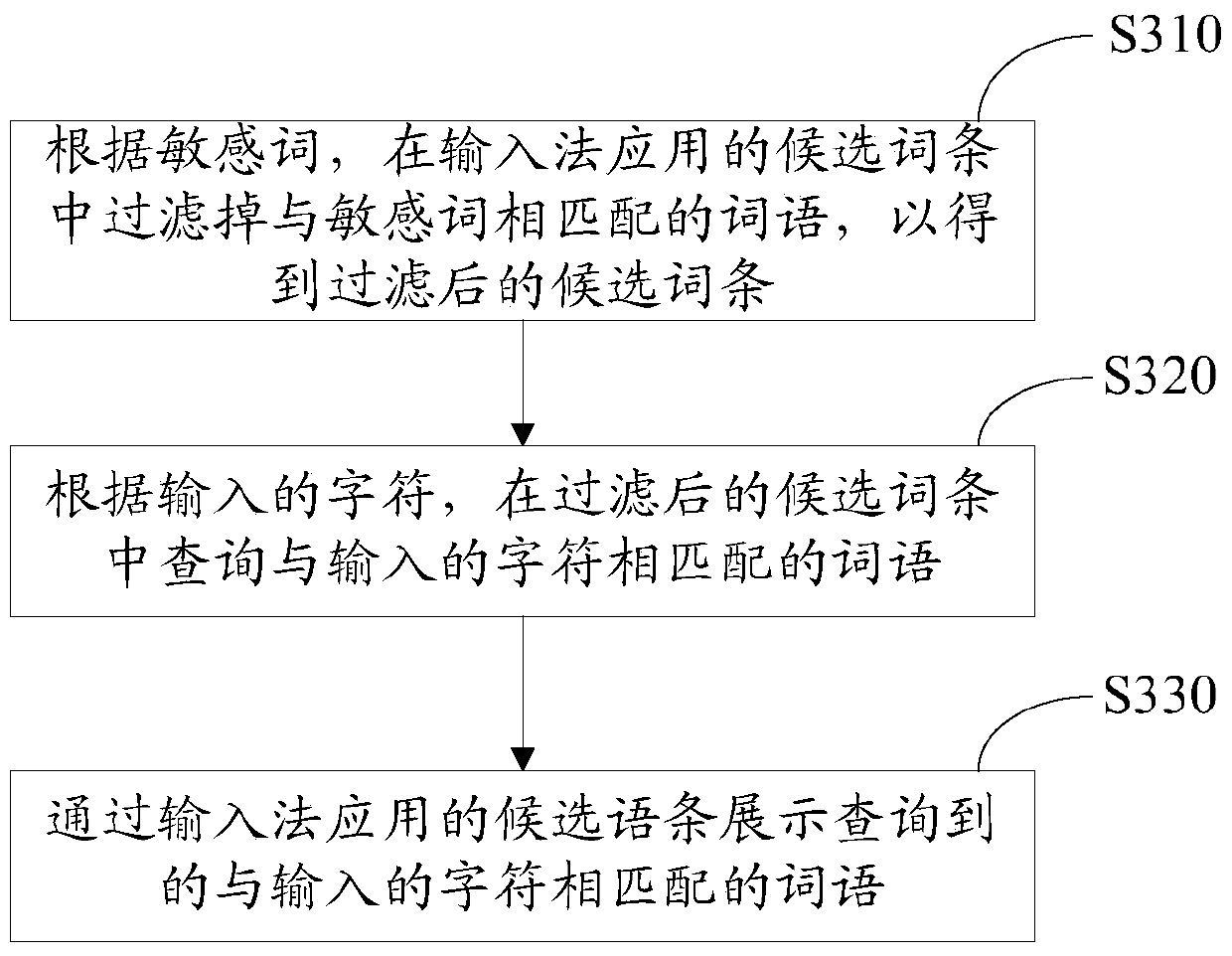
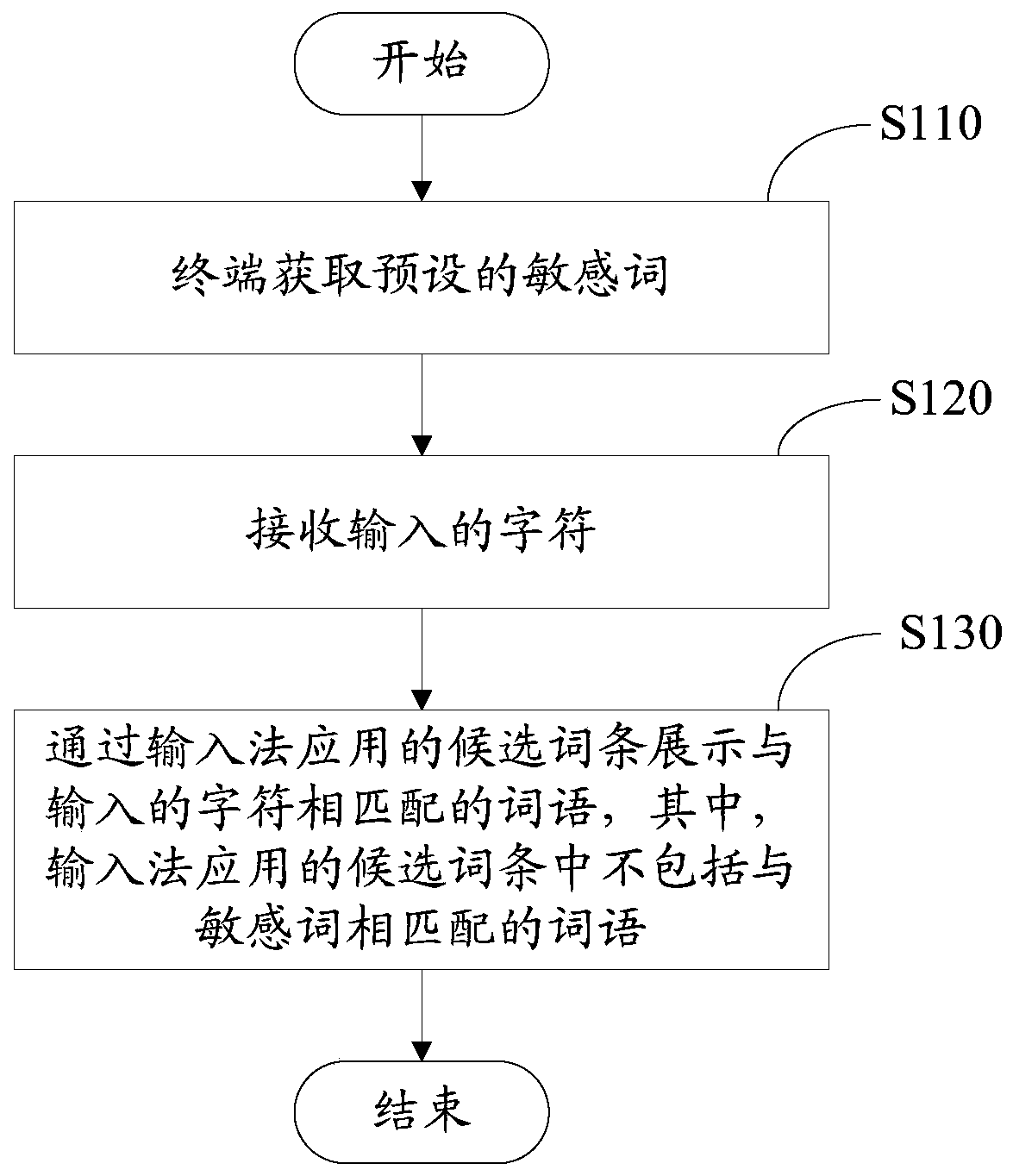
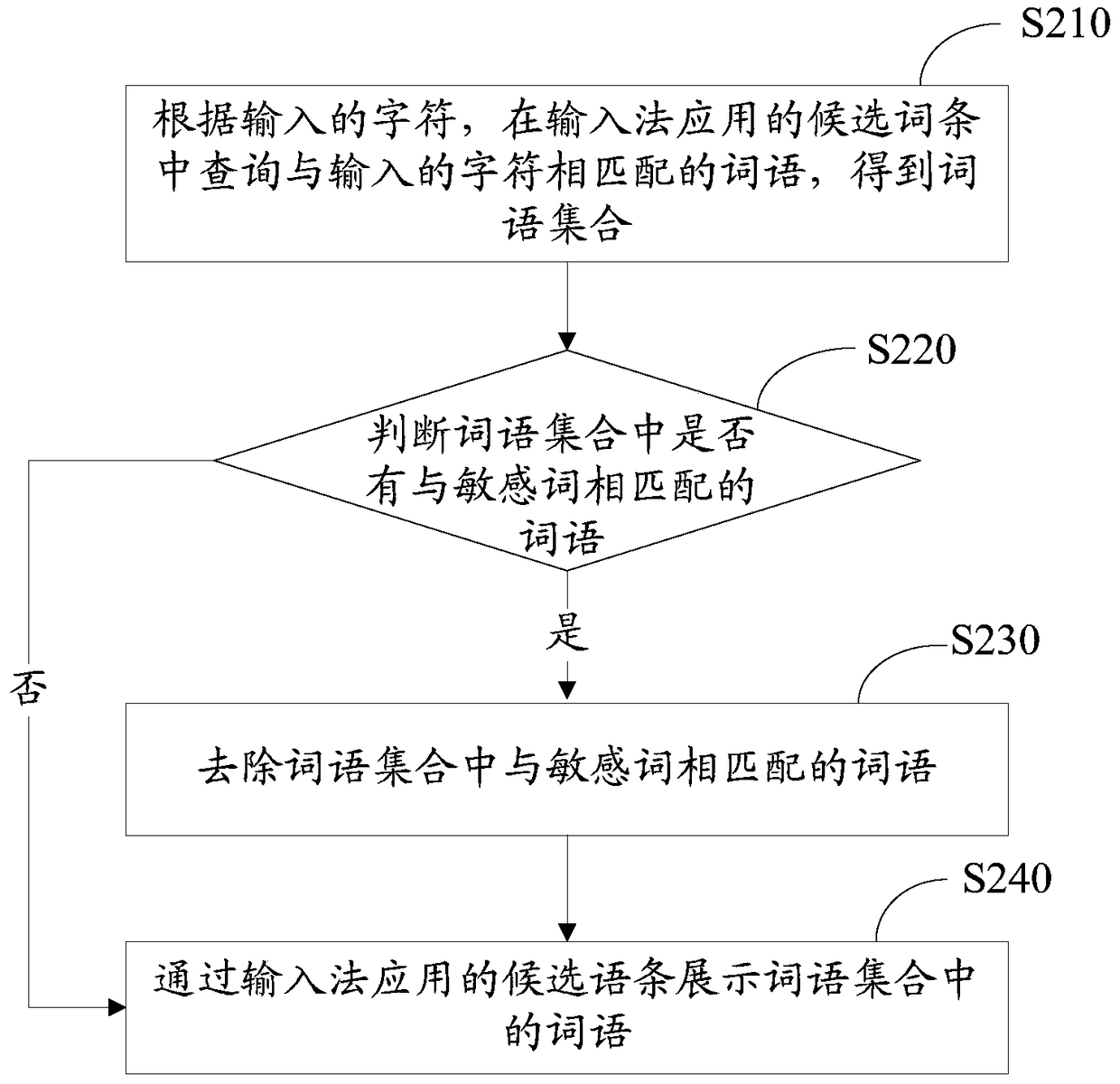
InactiveCN105511638AProtect personal privacy informationGuaranteed input efficiencyNatural language data processingSpecial data processing applicationsComputer terminalHuman–computer interaction
The invention relates to an application method and device for an input method. The application method includes the following steps that a terminal acquires preset sensitive words; input characters are received; words matched with the input characters are displayed through a candidate entry applied to the input method, wherein the candidate entry applied to the input method does not contain words matched with the sensitive words. By means of the application method and device for the input method, personal privacy information of a user can be effectively protected; besides, the associating and recommending function still can be achieved, and input efficiency can be guaranteed.
Owner:MEIZU TECH CO LTD
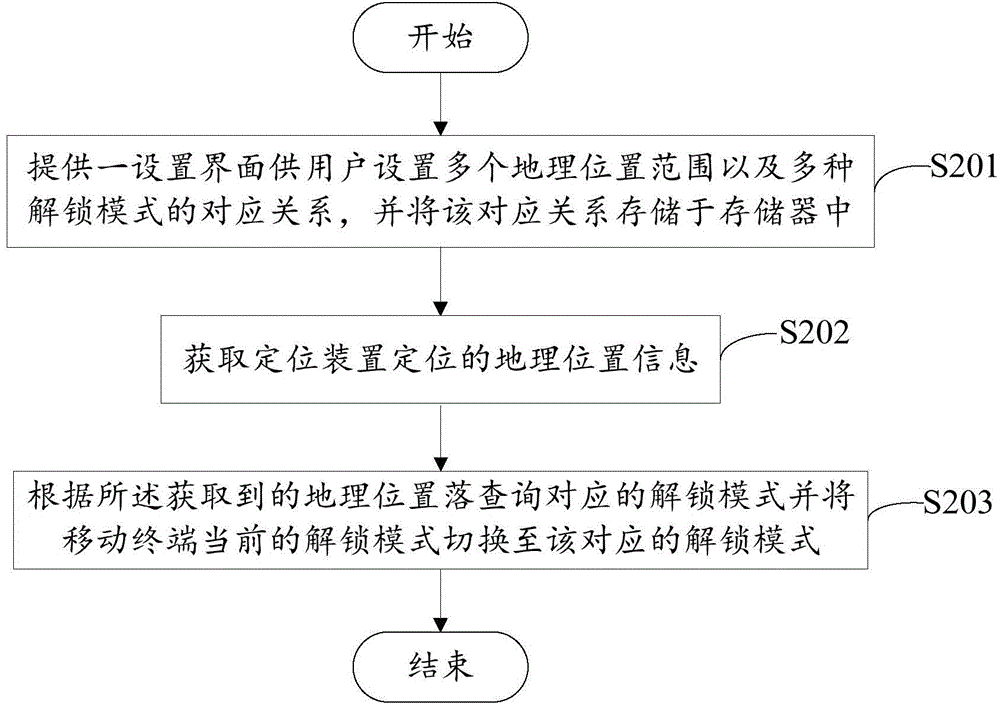
Unlocking mode switching system and method
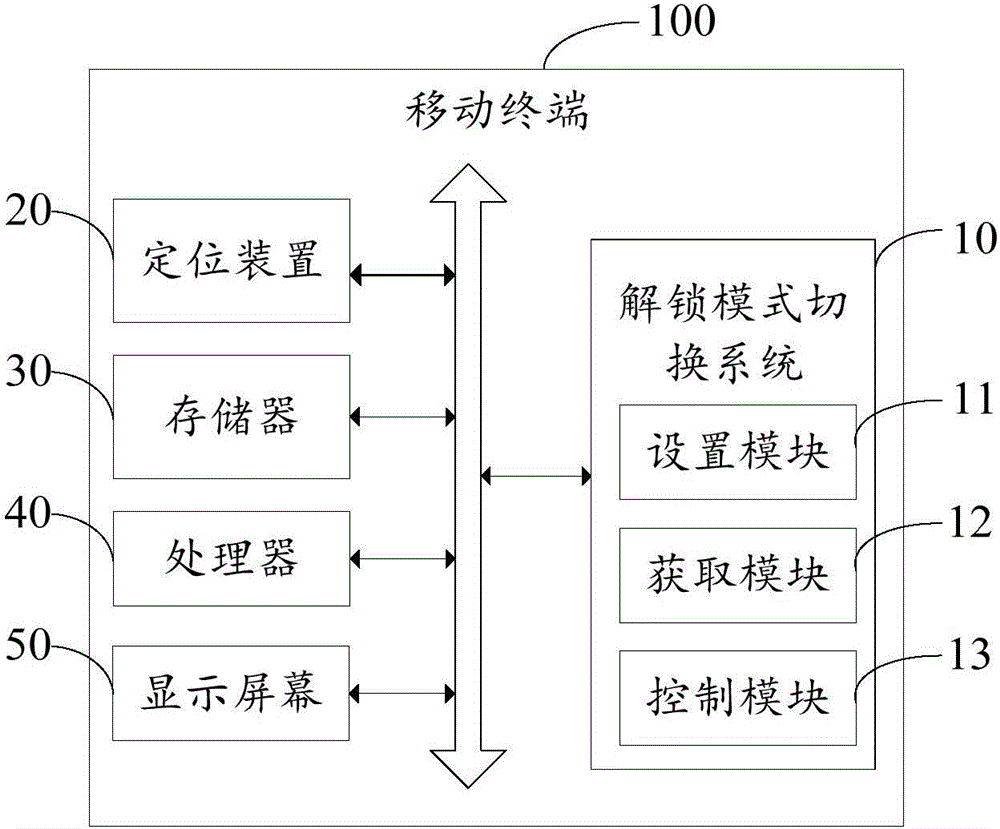
InactiveCN105812542AEasy to useImprove experienceSubstation equipmentLocation information based serviceGeolocationComputer science
The invention discloses an unlocking mode switching system and method, and the unlocking mode switching system is installed and operates in a mobile terminal. The mobile terminal comprises a positioning device and a storage device; the positioning device is used for positioning the geographic position of the mobile terminal; the storage device stores a plurality of preset geographic positions ranges in advance and the corresponding relations of a plurality of unlocking modes. The unlocking mode switching system comprises an obtaining module which is used for obtaining the geographic position information positioned by the positioning device, and a control module which is used for searching the corresponding unlocking mode from the correspondence relation which is stored in the storage device according to the geographic range where obtained geographic position falls into and switching the current unlocking mode of the mobile terminal to the corresponding unlocking mode. The unlocking mode switching system and method can automatically switch the unlocking mode according to the geographic position where the mobile terminal is positioned and provides convenience to usage while protecting the user personal privacy.
Owner:FU TAI HUA IND SHENZHEN +1
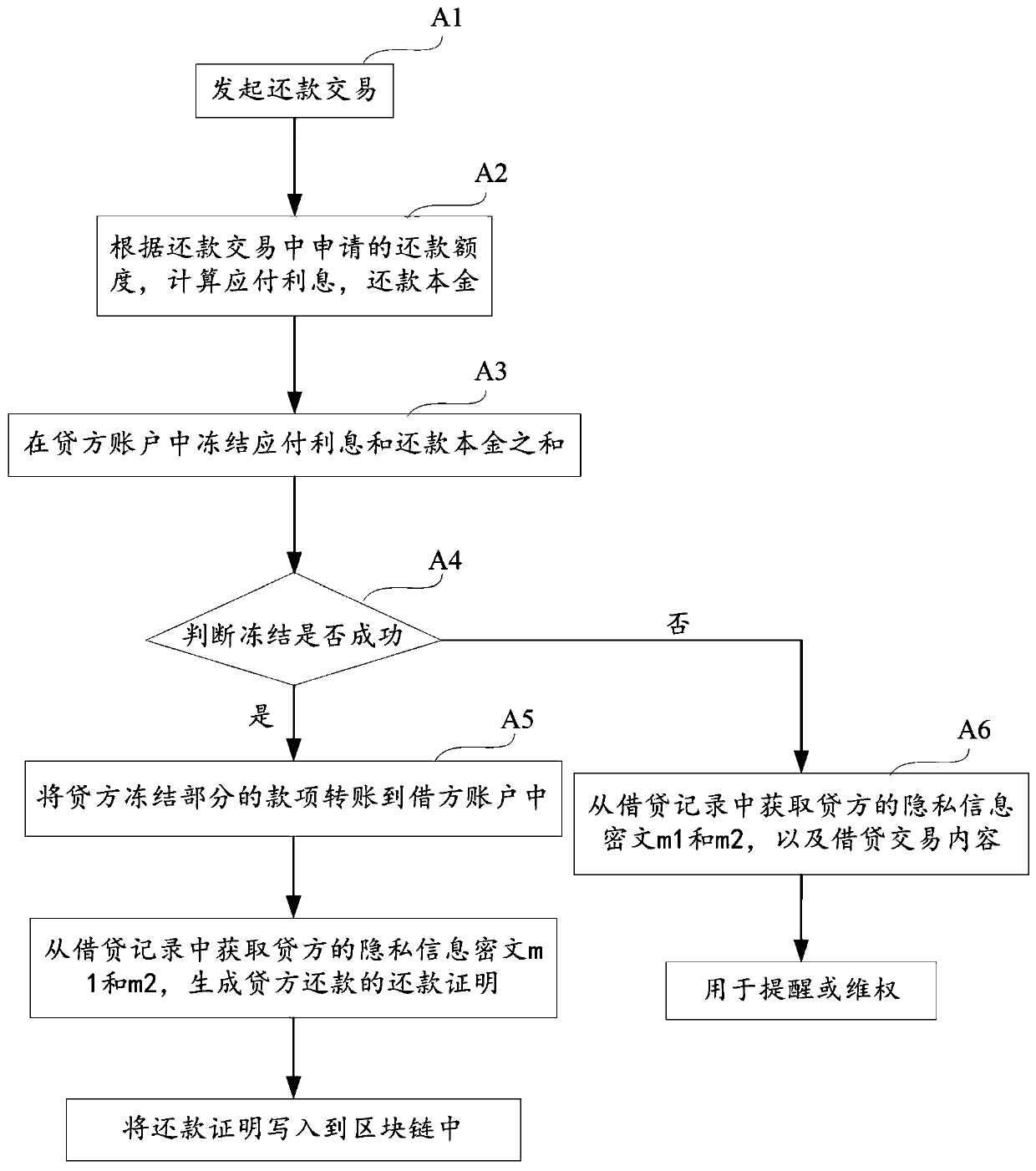
Privacy information protected repayment method and system, equipment and storage medium
ActiveCN110084066AImprove identityProtect personal privacy informationFinanceDigital data protectionPresent methodInternet privacy
The invention discloses a privacy information protected repayment method and system, equipment and a storage medium in the technical field of block chains. The method comprises the following steps ofinitiating a repayment transaction, calculating payable interest and repayment income according to the repayment limit applied in the repayment transaction, freezing the sum of the payable interest and the repayment income in the creditor account, and judging whether freezing is successful or not; if the credit is frozen successfully, transferring the money of the frozen part of the credit to theaccount of the borrower; writing the repayment proof into the block chain; and if the freezing fails, acquiring privacy information ciphertext m1 and m2 of the creditor and the content of the loan transaction from the loan record and are used for reminding or rights protection. Privacy information of borrowers and lenders on an open block chain system is easy to leak. The identity information of the repayment person can be protected, the real identity information of the borrower can be obtained through decryption when the repayment is not carried out due to overdue conditions, and the real identity information and the corresponding borrowing information are used as evidence for later legal right protection.
Owner:HANGZHOU FUZAMEI TECH CO LTD
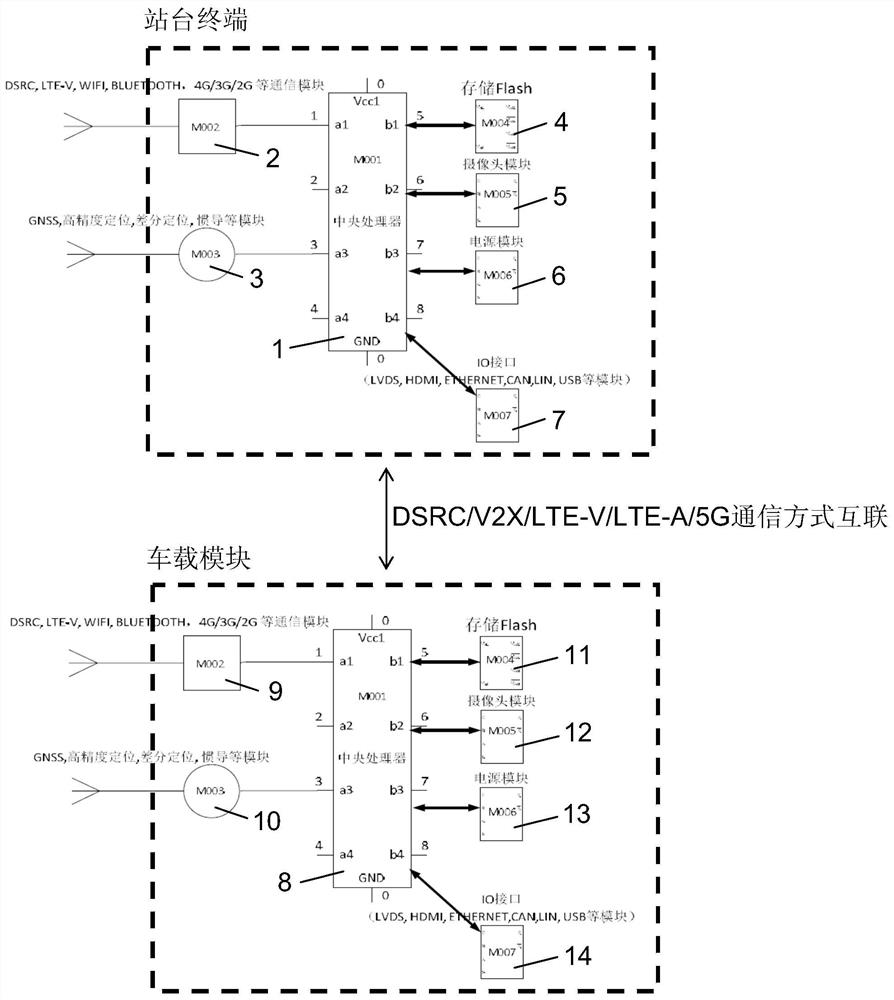
Intelligent network connection technology-based vehicle, people, road and object interaction system and use method
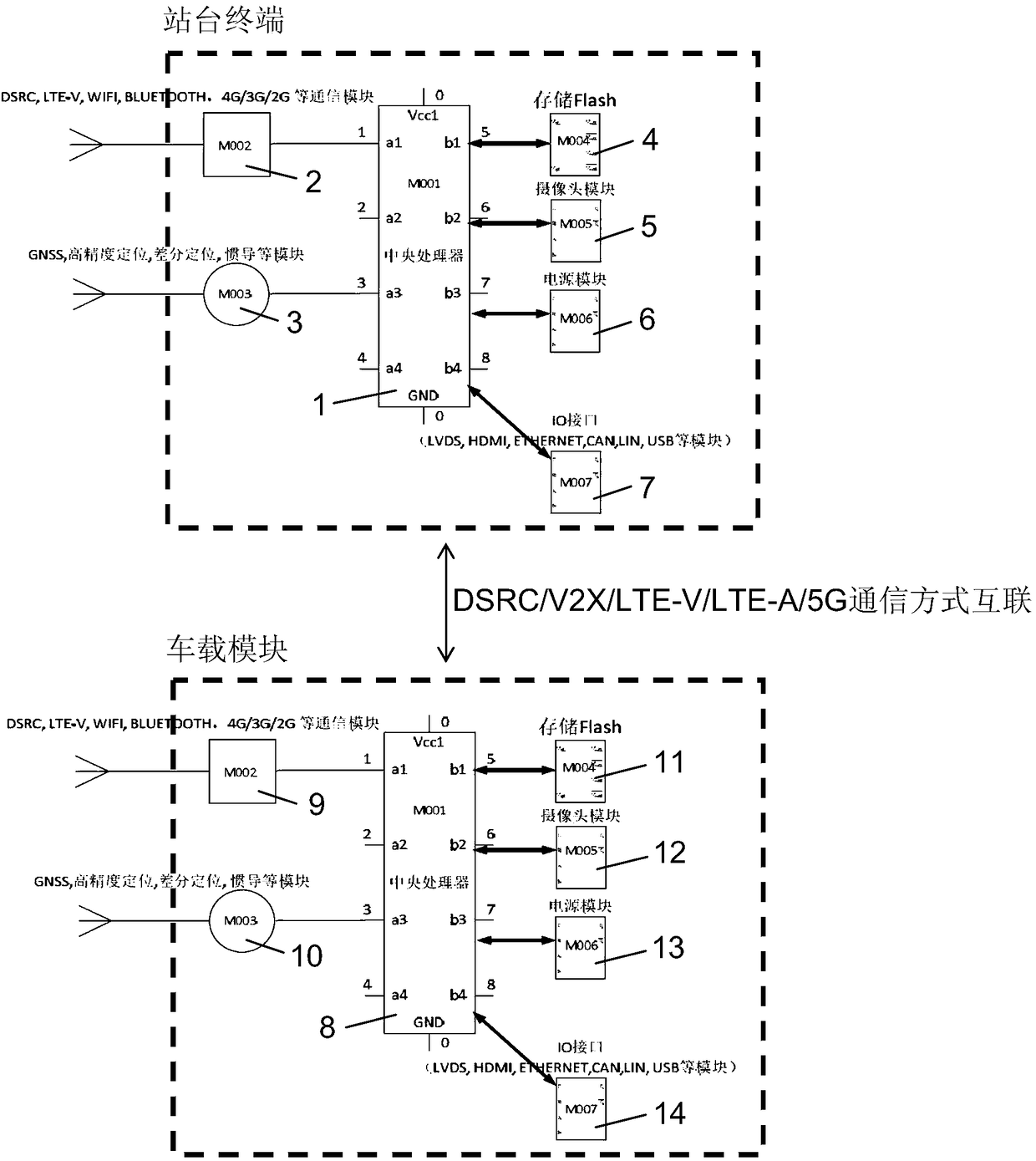
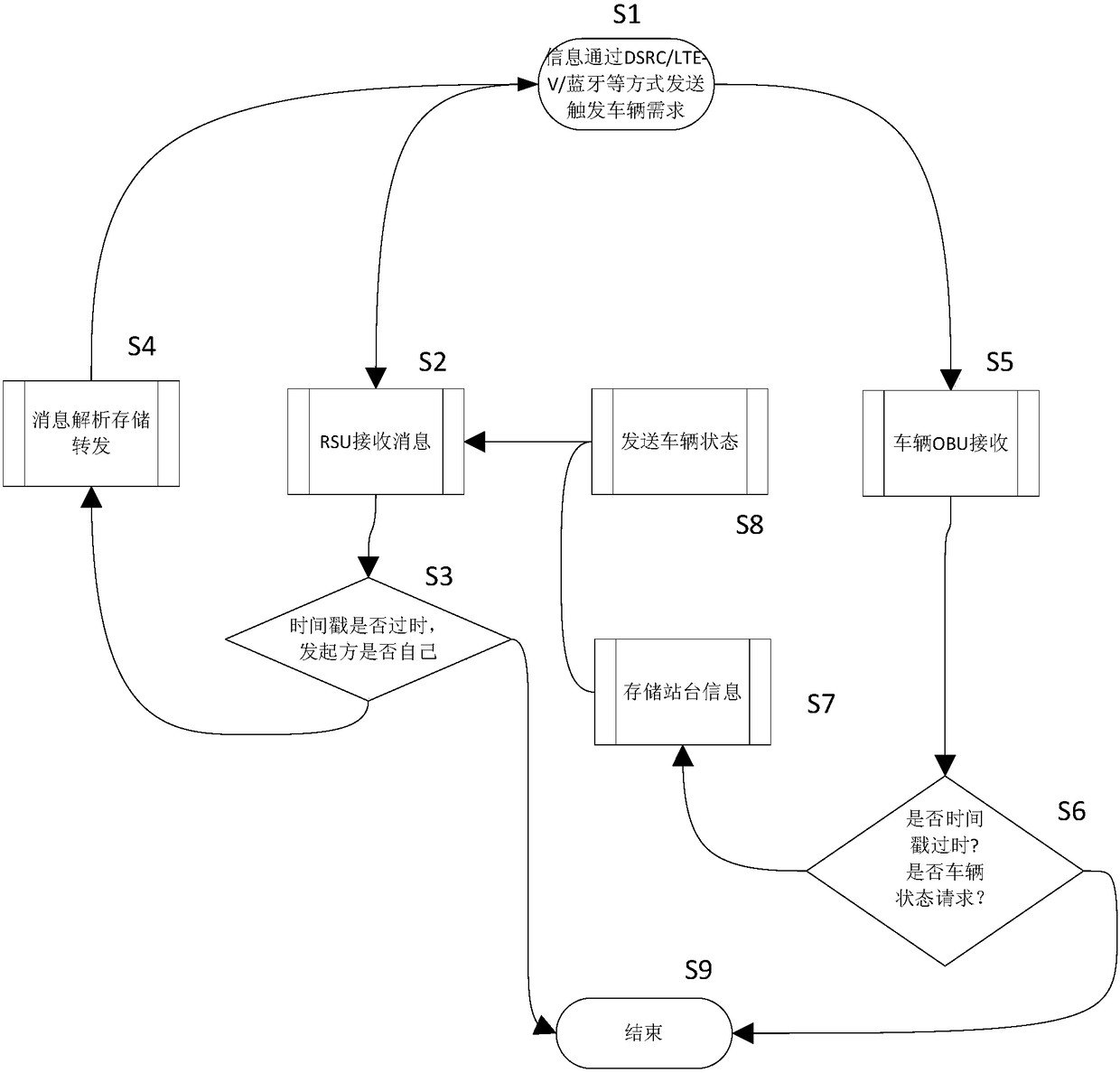
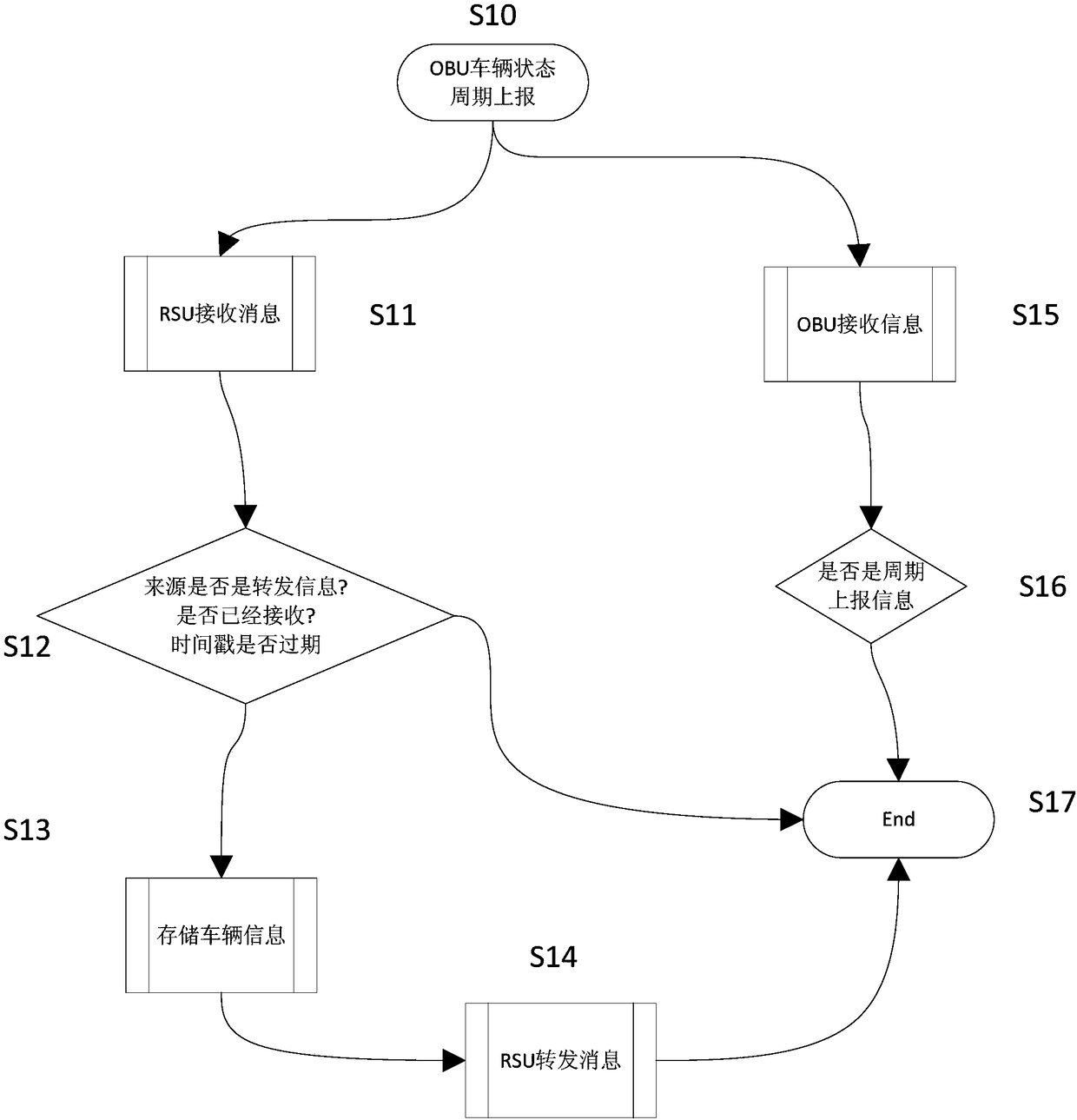
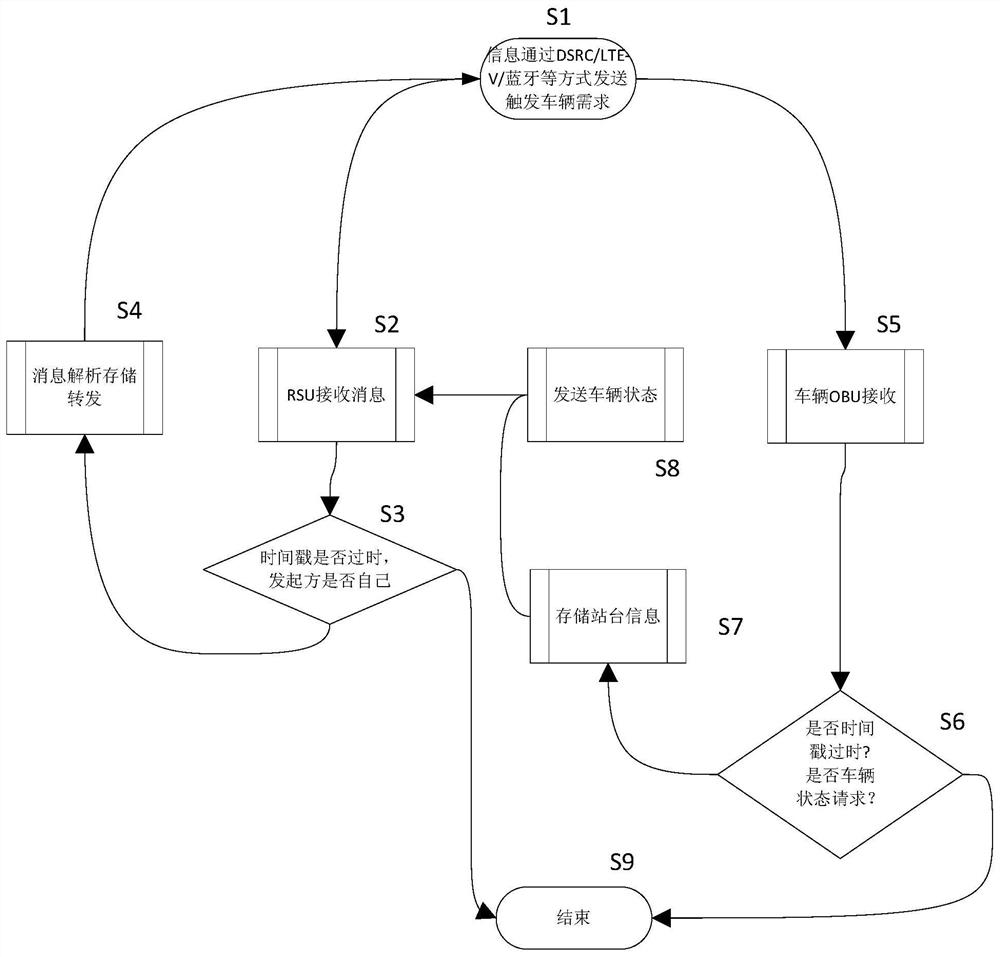
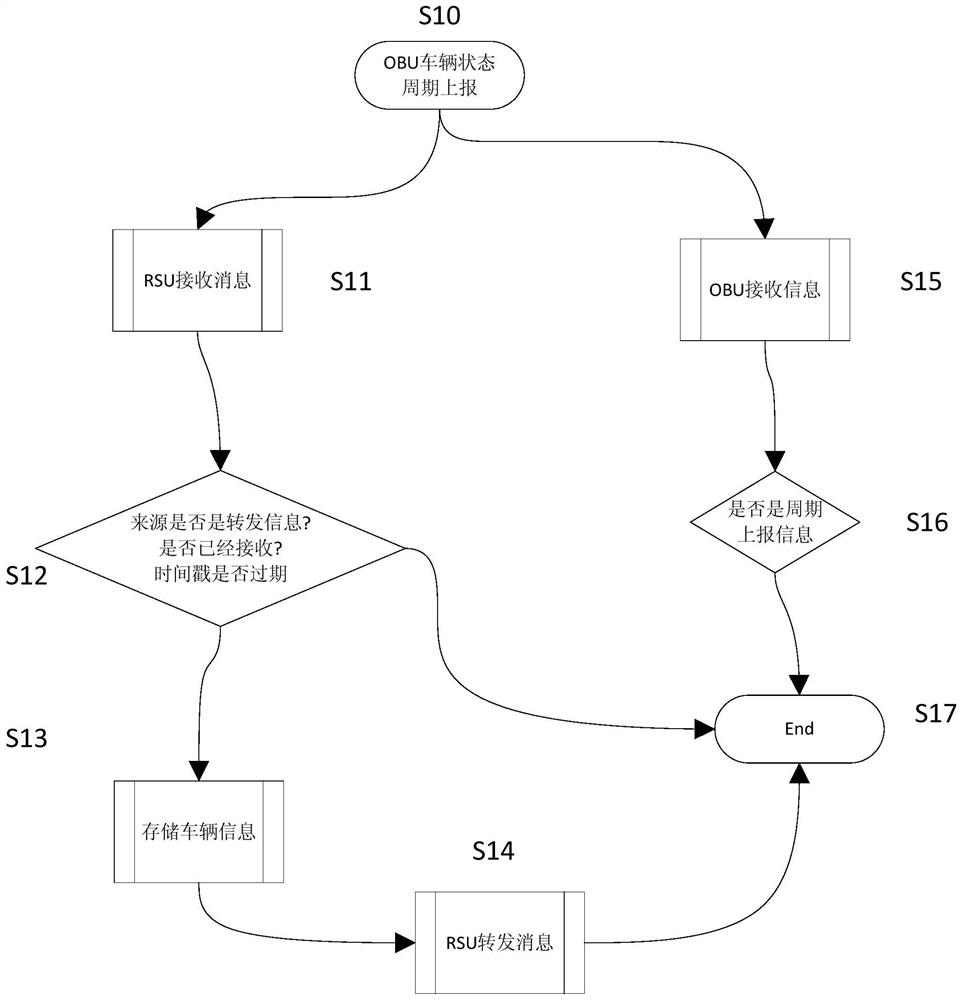
ActiveCN108122421AEnough privacyGuaranteed accuracyArrangements for variable traffic instructionsTransmissionIntelligent NetworkInteraction systems
The invention discloses an intelligent network connection technology-based vehicle, people, road and object interaction system and a use method. The system comprises a plurality of vehicle platforms and a plurality of vehicles; the system further comprises platform terminals and vehicle-mounted modules; the platform terminals are connected with the vehicle-mounted modules through a V2X / DSRC / LTE-V / LTE-A communication mode; the platform terminals are used for initiating vehicle positioning and vehicle demand requesting information, and transmitting the information to the vehicle-mounted modules;a plurality of platform terminals are provided and are respectively arranged on the vehicle platforms; a plurality of vehicle-mounted modules are provided and are respectively arranged on the vehicles and are in signal connection with the platform terminals and other vehicle-mounted modules; and the vehicle-mounted modules are used for receiving information sent by the platform terminals and theother vehicle-mounted modules. With the intelligent network connection technology-based vehicle, people, road and object interaction system and the use method of the invention adopted, the service ofa cloud server is not required, the interconnection of all things can be realized, cost for building the cloud server can be omitted, and the independence of data and the protection of privacy are ensured.
Owner:上海固厚寿记贸易有限公司
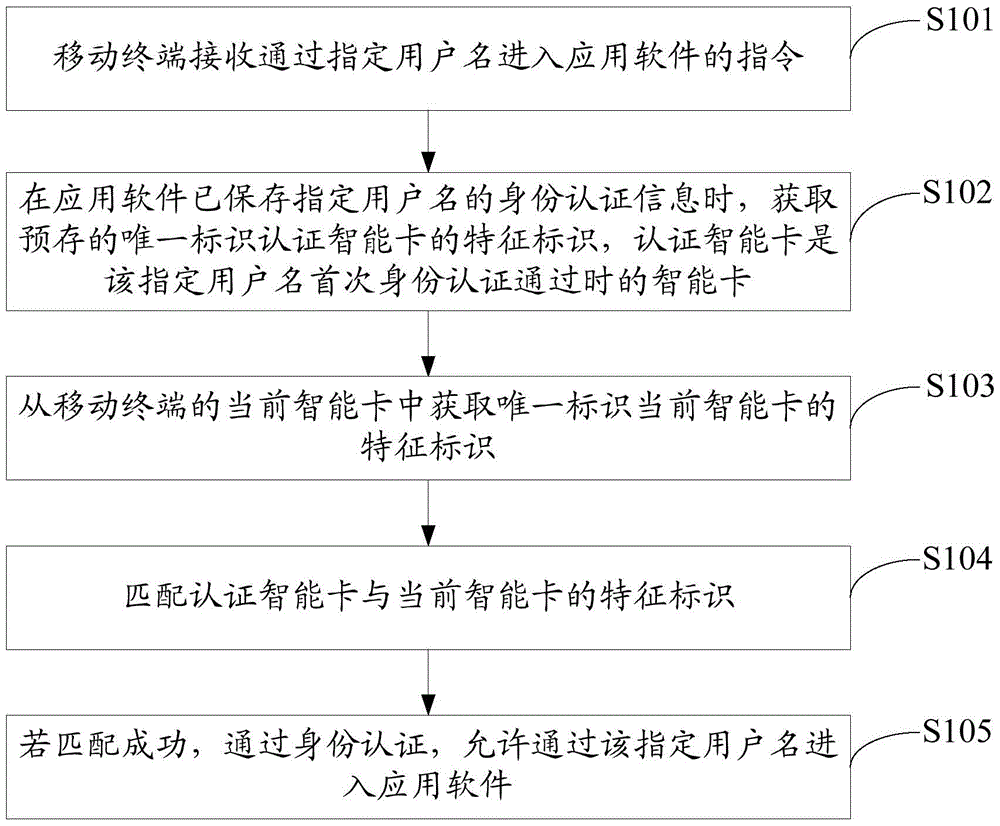
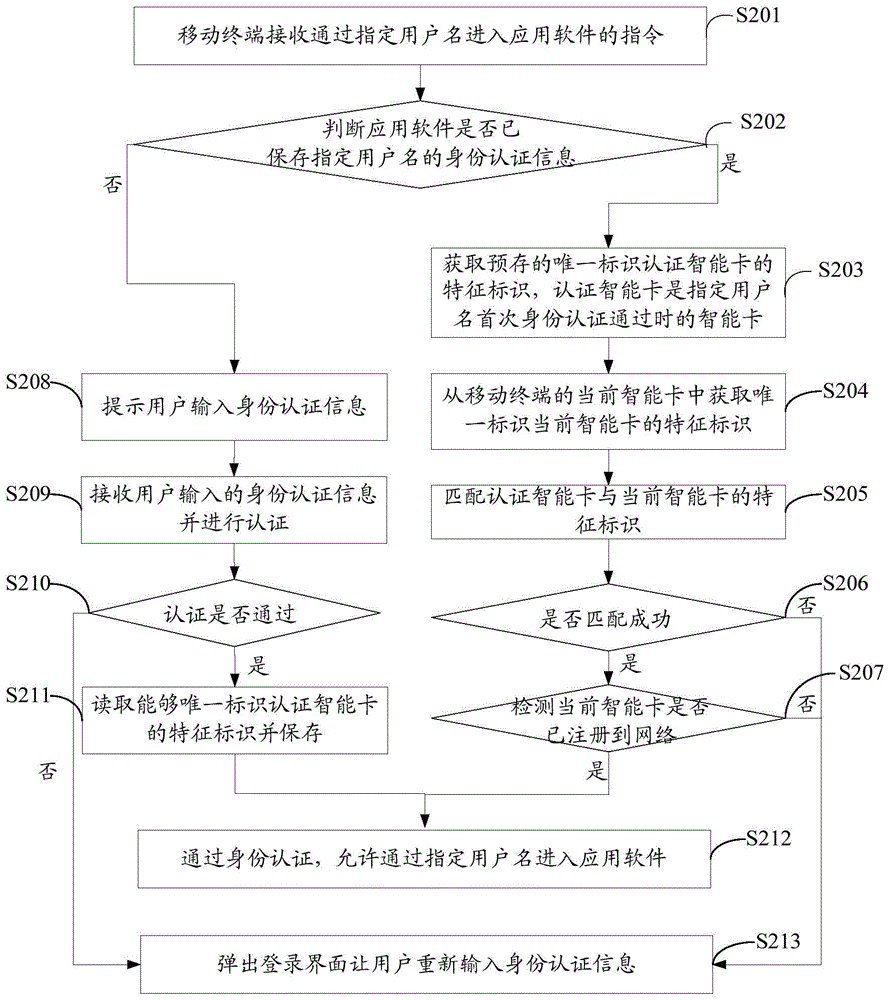
Privacy protecting method and mobile terminal
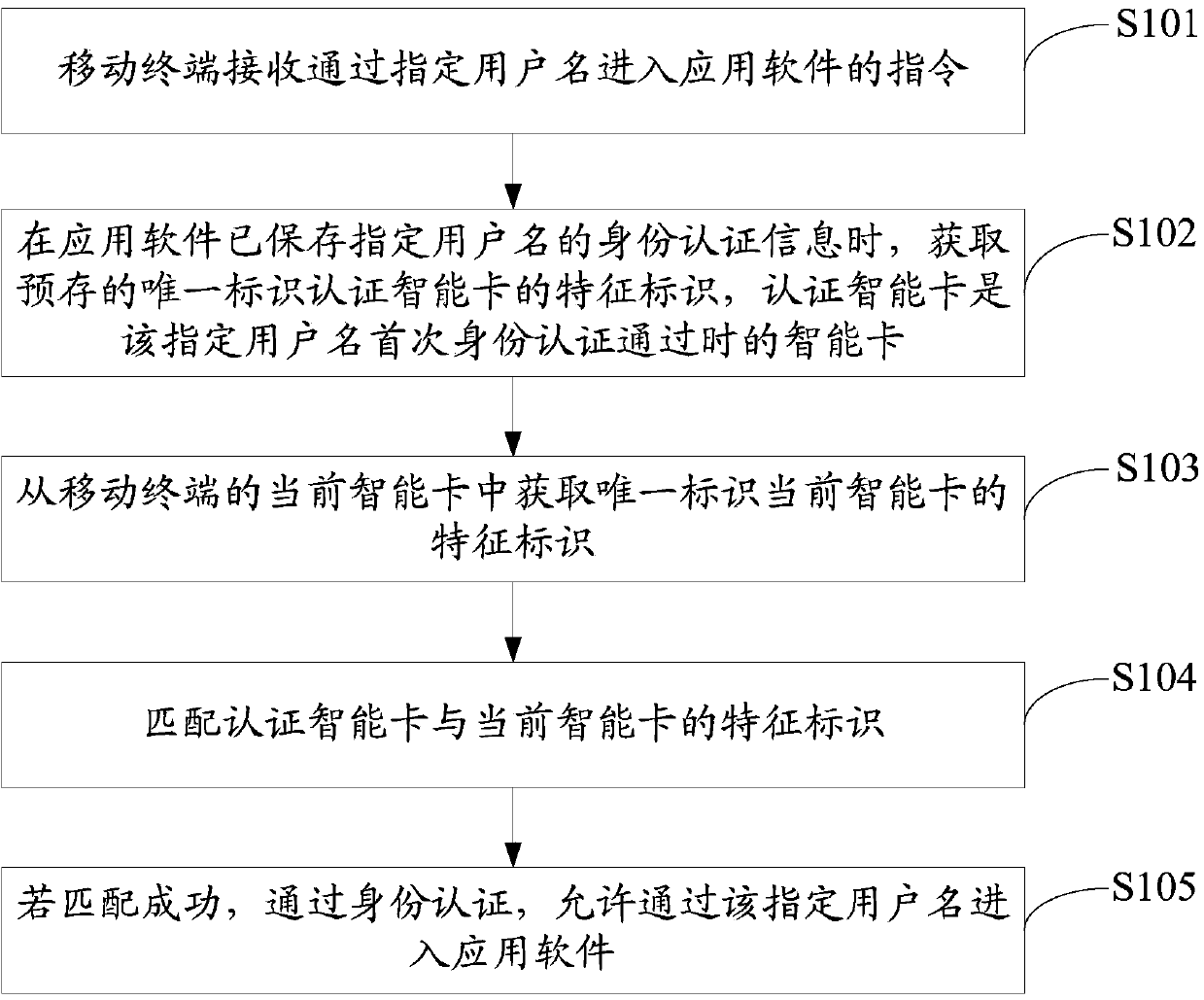
ActiveCN103634467AWithout compromising usabilityDo not reduce experienceSubstation equipmentSecurity arrangementSmart cardUsability
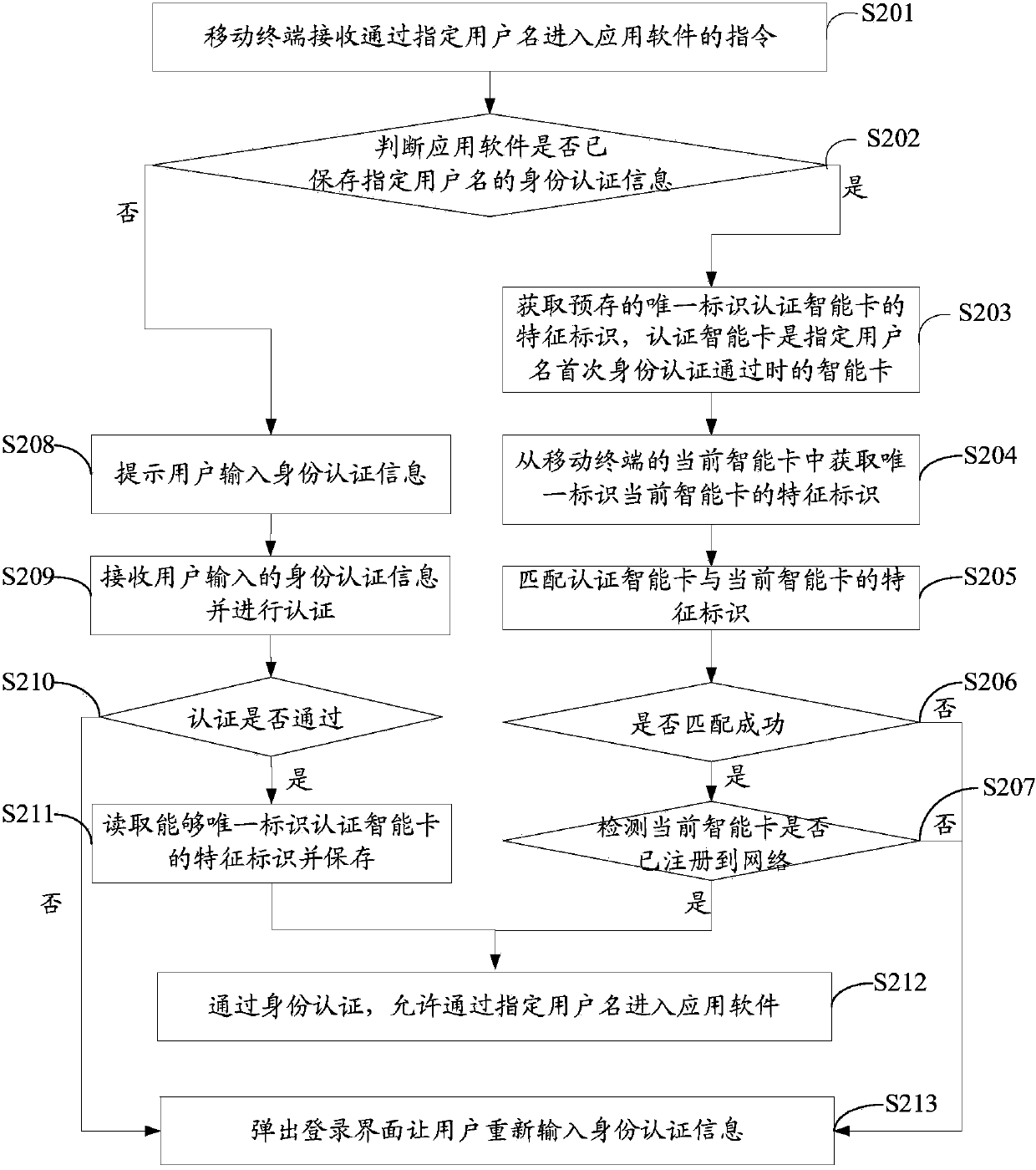
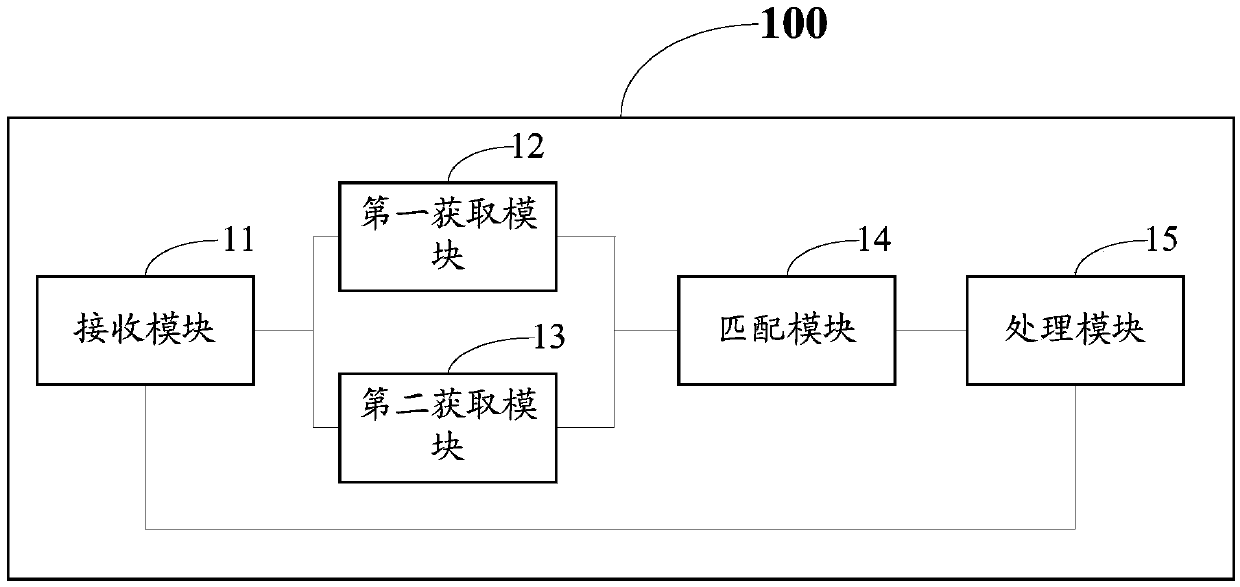
The embodiment of the invention discloses a privacy protecting method and a mobile terminal. The privacy protecting method comprises the steps: receiving an instruction for entering application software by virtue of a designated user name by a mobile terminal; when identity authentication information of the designated user name is stored in the application software, obtaining a characteristic identity of a pre-stored unique identity authenticated intelligent card, wherein the authentication intelligent card is an intelligent card which is used when the identity authentication of the designated user name passes for the first time; obtaining a characteristic identity which uniquely identifies the current intelligent card from the current intelligent card in the mobile terminal; matching the authenticated intelligent card and the characteristic identity of the current intelligent card, wherein if the matching is successful, the identity authentication passes, entering the application software by virtue of the designated user name is permitted. According to the method, under the condition that the usability and experiences of a user are not lowered, the personnel privacy information stored in the mobile terminal can be effectively protected.
Owner:HUAWEI TECH CO LTD
Online shopping delivery method for protecting private information
InactiveCN108596534AProtect personal privacy informationReduce workloadCo-operative working arrangementsFranking apparatusCommunity orLogistics management
The invention relates to an online shopping delivery method for protecting the private information. The method comprises steps that a, when an order is made by a user on the e-commerce network, only the mobile phone number and the express reception address are provided; b, a two-dimensional code is generated by a seller from the information provided by the user, the two-dimensional code is attached to a parcel box or a parcel bag, in the express waybill, only the name and the address of a family community of a location city or an office building in which the company is located are written in;c, the express is delivered by a logistics company to the city and is delivered by a dispatcher to an intelligent logistics placement box of the family community or the office building; and d, the extracted information is sent by the intelligent logistics placement box to the mobile phone number collected by the CPU from the two-dimensional code, and the user is reminded to pick up the express. The method is advantaged in that the personal private information of the online shopping user is completely protected.
Owner:NANJING COMM INST OF TECH
Terminal and method for protecting user privacy information
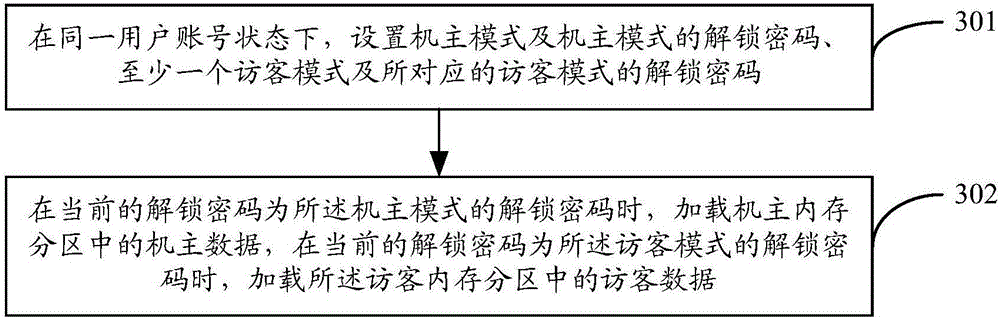
InactiveCN106506786AProtect personal privacy informationProtect private informationUnauthorised/fraudulent call preventionInternet privacyUser privacy
The invention discloses a terminal for protecting user privacy information. The terminal comprises the steps of a setting module which is used for setting an owner mode, an unlocking cipher of the owner mode, at least one visitor mode and the corresponding unlocking cipher of the visitor mode in the same user account state; and a loading module which is used for loading owner data in an owner memory partition when the current unlocking cipher is the unlocking cipher of the owner mode, and loading the visitor data in a visitor memory partition when the current unlocking cipher is the unlocking cipher of the visitor mode, wherein the owner memory partition and the visitor memory partition are isolated, the owner data comprises applications installed by an owner and the privacy information of the owner, and the visitor data comprises the applications installed by a visitor and the privacy information of the visitor. The invention also discloses a method for protecting the user privacy information. Through application of the terminal and the method, the user personal privacy information can be effectively protected and the privacy is prevented from being leaked.
Owner:NUBIA TECHNOLOGY CO LTD
Intelligent application start method and apparatus
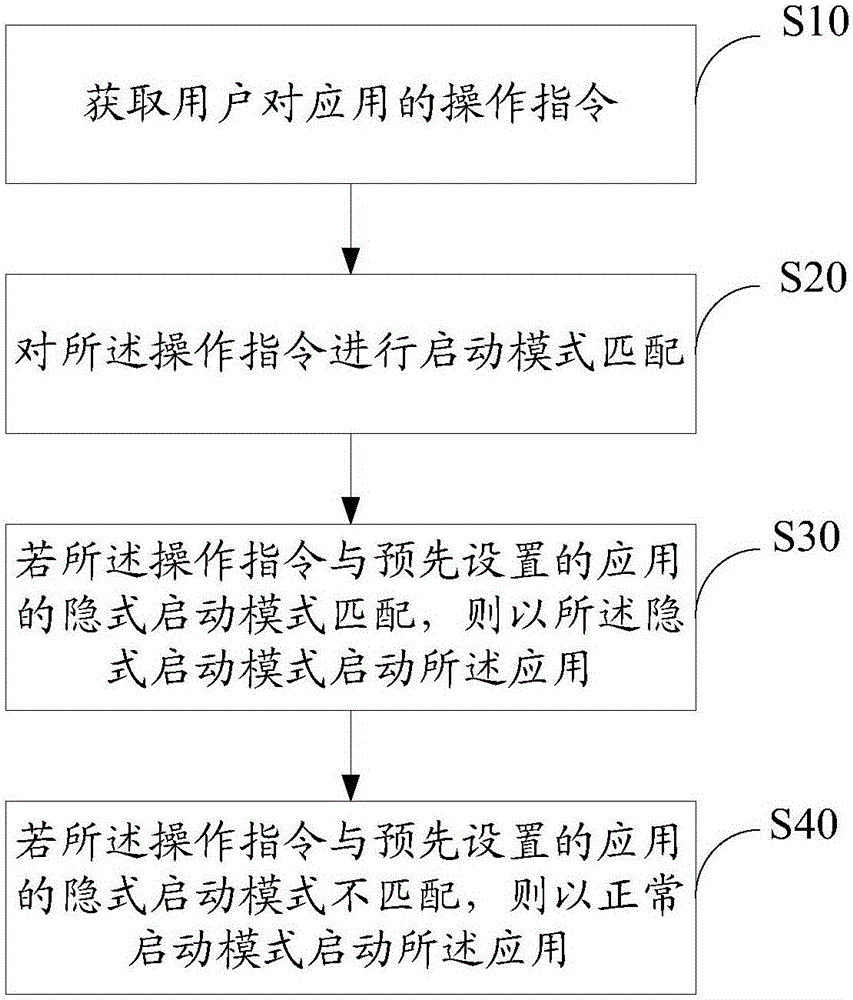
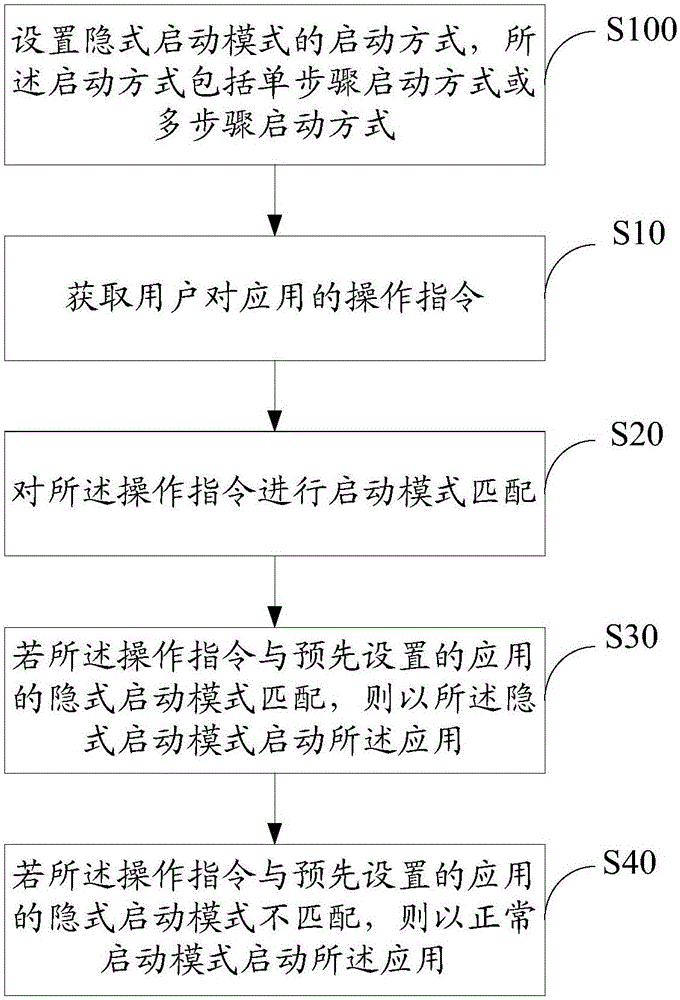
InactiveCN106569862AProtect personal privacy informationPrevent leakageSubstation equipmentProgram loading/initiatingOperating systemComputer science
The invention provides an intelligent application start method and apparatus. The method comprises the following steps: acquiring an operation instruction of a user to the application; initiating a pattern matching to the operation instruction; starting the application according to an implicit start mode if the operation instruction matches the implicit start mode of the pre-set application, and starting the application according to a normal start mode if the operation instruction does not match the implicit start mode of the pre-set application. The intelligent application start method protects the privacy information of the user through the scheme, and effectively prevents the disclosure of the user's privacy information.
Owner:SHENZHEN TCL NEW-TECH CO LTD
Goods monitoring method and system
InactiveCN103927500AImprove securityReduce lossInternal/peripheral component protectionWireless transceiverComputer terminal
The invention provides a goods monitoring method and system. The system comprises a private goods server side and at least one private goods terminal. The server side is carried by a goods owner, and the server side comprises a goods owner identity information confirmation module and a wireless transceiver module with the adjustable transmitting efficiency. Each terminal is in physical connection with private goods and is provided with a wireless transceiver module, each terminal is subject to the only server side, the server side sends a connection request instruction to the terminal subject to the server side, the terminal sends a response as soon as receiving the instruction, the server side stores the response time of the terminal, if no response is obtained when the time difference between the last response time and the current response time exceeds the preset time, it is determined that the server side loses contact with the terminal, and a prompt message indicating that the terminal cannot be found is sent to the owner. According to the goods monitoring method and system, the safety of the personal private goods can be improved, the probability that the goods are lost or stolen is reduced, and personal privacy information in electronic equipment can be more effectively protected at the same time.
Owner:何川丰
Vehicle-Road-Character Interaction System and Application Method Based on Intelligent Network Connection Technology
ActiveCN108122421BEnough privacyGuaranteed accuracyArrangements for variable traffic instructionsTransmissionIntelligent NetworkIn vehicle
The invention discloses a vehicle-road character interaction system based on intelligent network connection technology and a method for using it, including several vehicle platforms and several vehicles, and also includes a platform terminal and a vehicle-mounted module. ‑V / LTE‑A communication mode interconnection, the platform terminal is used to initiate vehicle positioning and vehicle request information, and transmit the information to the vehicle module. There are several station terminals, which are respectively installed on each corresponding vehicle platform. There are also several modules, which are respectively arranged on each vehicle, and are connected to the station terminal and other vehicle-mounted modules for receiving information sent by the station terminal and other vehicle-mounted modules. The present invention realizes the interconnection of all things without the service of the cloud server, reduces the cost of building the cloud server, and at the same time ensures the independence of data and the protection of privacy.
Owner:上海固厚寿记贸易有限公司
Input method application method and device
InactiveCN105511638BProtect personal privacy informationGuaranteed input efficiencyNatural language data processingSpecial data processing applicationsEngineeringHuman–computer interaction
The invention relates to an application method and device for an input method. The application method includes the following steps that a terminal acquires preset sensitive words; input characters are received; words matched with the input characters are displayed through a candidate entry applied to the input method, wherein the candidate entry applied to the input method does not contain words matched with the sensitive words. By means of the application method and device for the input method, personal privacy information of a user can be effectively protected; besides, the associating and recommending function still can be achieved, and input efficiency can be guaranteed.
Owner:MEIZU TECH CO LTD
Mobile terminal signature-based remote payment system and method
InactiveCN101938520BImprove securityImprove portabilityPayment protocolsTransmissionPasswordAuthentication server
The present invention discloses a method for remote payment based on a mobile terminal. The method includes: an authentication server asking a mobile terminal for a digital certificate, the mobile terminal transmitting an certificate reading instruction to the built-in smart card, and after the smart card exports the stored digital certificate, the mobile terminal transmitting it to the authentication server for certificate registration, and the authentication server sending a signature instruction to the mobile terminal, the mobile terminal transmitting a private key signature instruction to the built-in smart card, the smart card sending out the signature result and the mobile terminal reporting the signature result to the authentication server. The present invention also discloses a system for remote payment based on mobile terminal, a mobile terminal and a smart card. The present invention not only breaks through the limitation of short of transmitting the personal ID and password by using short message and WAP.
Owner:ZTE CORP
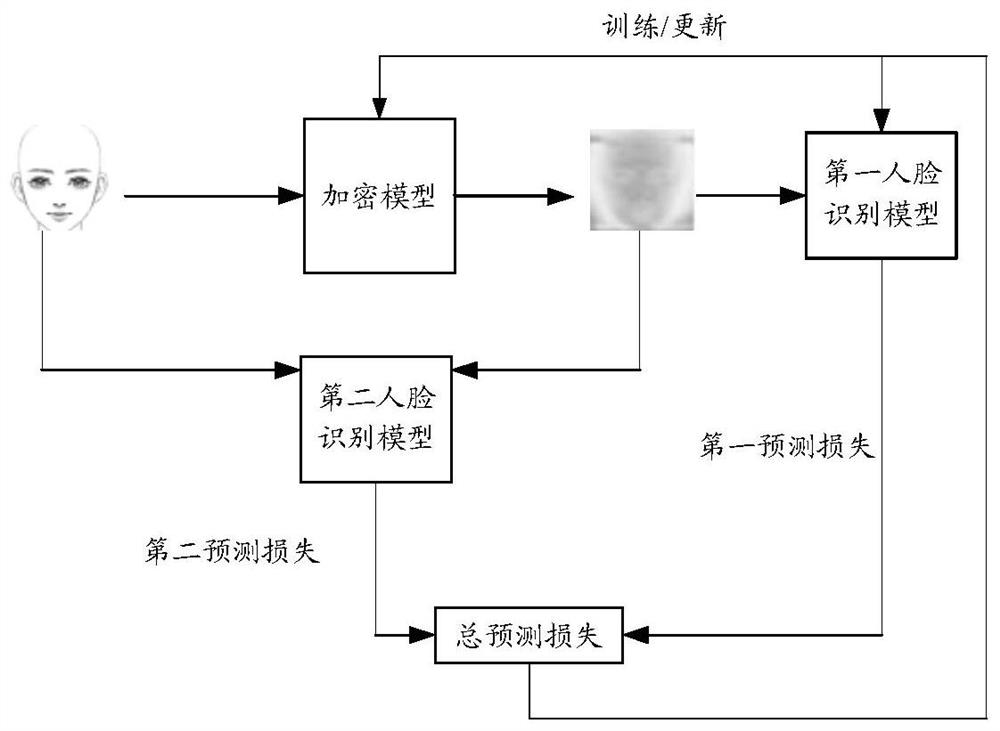
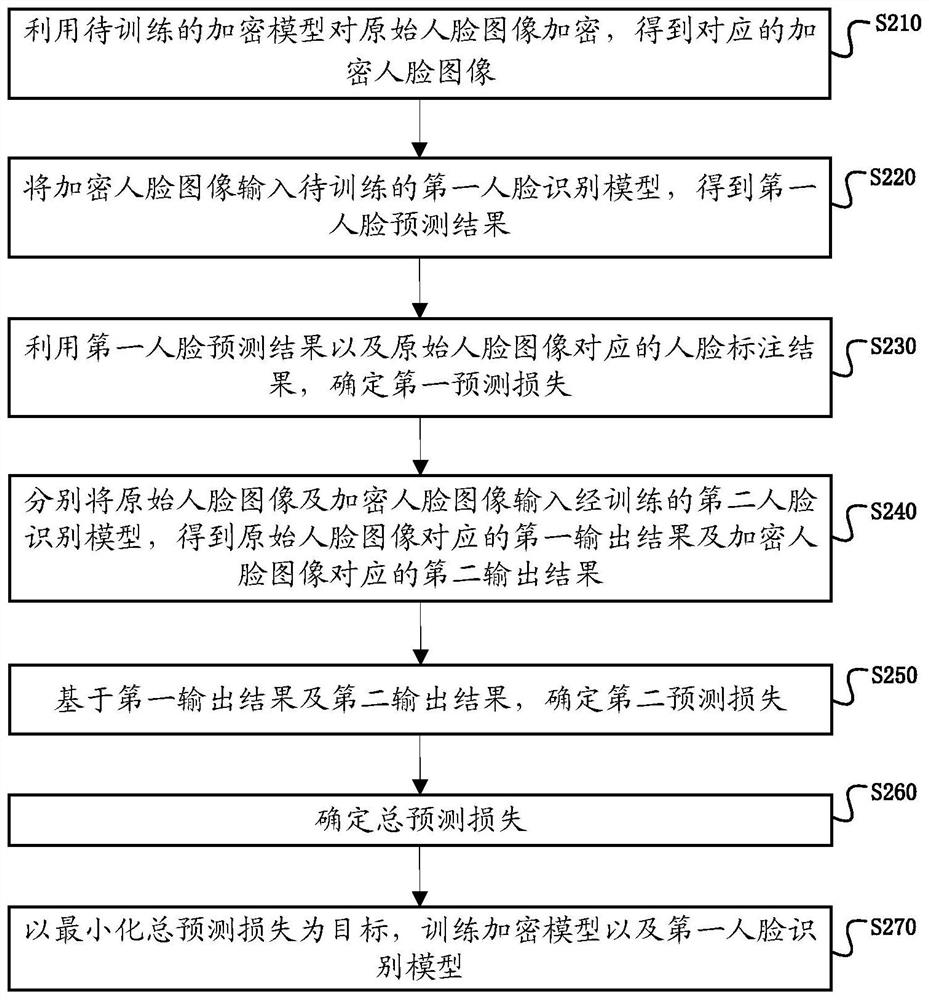
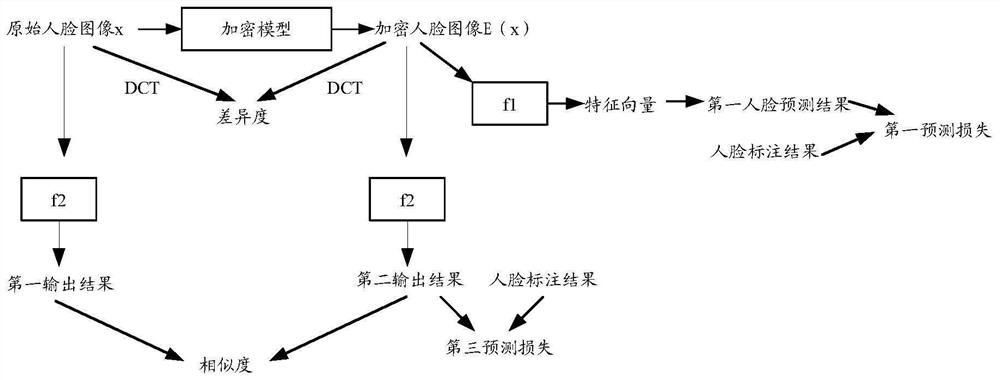
Encryption model training method and device, image encryption method and device and encrypted face image recognition method and device
PendingCN113486839AGuaranteed accuracyImplement encryptionCharacter and pattern recognitionDigital data protectionPattern recognitionImage pair
The embodiment of the invention provides an encryption model training method and device, an image encryption method and device and an encrypted face image recognition method and device. The encryption model training method comprises the steps: encrypting an original face image through a to-be-trained encryption model, and obtaining an encrypted face image; inputting the encrypted face image into a to-be-trained first face recognition model to obtain a first face prediction result; determining a first prediction loss by using the first face prediction result and a face labeling result corresponding to the original face image; inputting the original face image and the encrypted face image into a trained second face recognition model to obtain a first output result and a second output result corresponding to the original face image and the encrypted face image; determining a second prediction loss based on the first output result and the second output result; determining a total predicted loss based on a positive correlation with the first predicted loss and the second predicted loss; and training an encryption model and a first face recognition model by taking minimization of the total prediction loss as a target.
Owner:ALIPAY (HANGZHOU) INFORMATION TECH CO LTD
Bridge type contact power supply lens shielding element and electronic equipment
PendingCN114466119AProtect personal privacy informationProtection securityTelevision system detailsColor television detailsElectrically conductiveMechanical engineering
The invention discloses a bridge type contact power supply lens shielding element and electronic equipment, and the bridge type contact power supply lens shielding element is arranged on a PCB of the electronic equipment and covers a camera of the electronic equipment. The bridge type contact power supply lens shielding element comprises a mounting base, a light shielding sheet, a driving assembly, a metal reinforcing plate and a contact conductive copper sheet, the driving assembly comprises a swing arm rotationally connected with the mounting base, the swing arm is connected with the light shielding sheet, and the swing arm rotates to drive the light shielding sheet to reciprocate between a first position and a second position; when the anti-dazzling screen is located at the first position, the anti-dazzling screen covers the side, away from the camera, of the view-finding hole, and when the anti-dazzling screen is located at the second position, the camera is exposed out of the view-finding hole. According to the invention, the anti-dazzling screen can move to the first position to shield the view-finding hole, so that a picture cannot be obtained even if the camera is turned on. Therefore, the camera is prevented from shooting or peeping the surrounding environment and even recording videos, and the personal privacy information and safety of the user are protected.
Owner:SHENZHEN FUNDER ELECTRONICS CO LTD
Authentication method and system for mobile users
ActiveCN106304074BProtect personal privacy informationEasy to useSecurity arrangementUser verificationInformation repository
The invention provides a mobile user-oriented identity verification method and system, which can realize password-free registration and login, and has the advantages of convenient use, high security, low cost and the like. Among them, the mobile user identity verification method applicable to third-party applications of the Andriod or iOS system includes: completing the access registration of the third-party application on the security service platform device; completing the registration of the security service card application device to establish a user information database . When the user logs in for the first time, the security service platform proxy device SDK sends the user's mobile phone number to the security service platform device for identity verification. If the verification is passed, the security service platform device generates a unique OpenID, and then the security service platform device returns to the user for verification via the SDK. Results and OpenID to third-party applications. When the user logs in for the second time, the SDK sends the OpenID to the security service platform device for identity verification. If the verification is passed, the security service platform device returns the user verification result and the user's mobile phone number to the third-party application through the SDK.
Owner:尹子栋
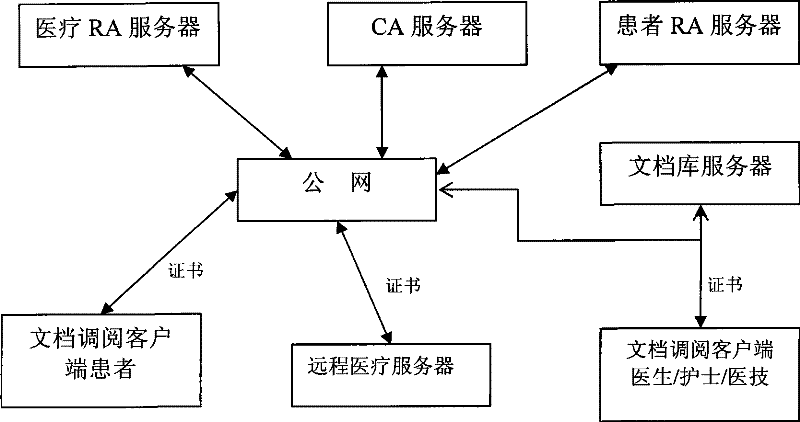
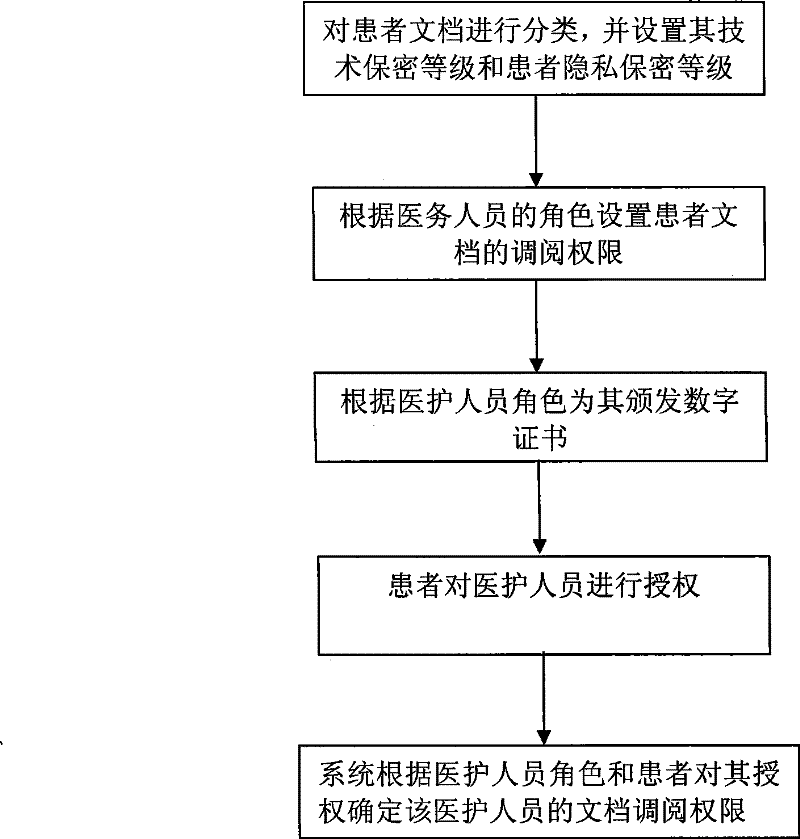
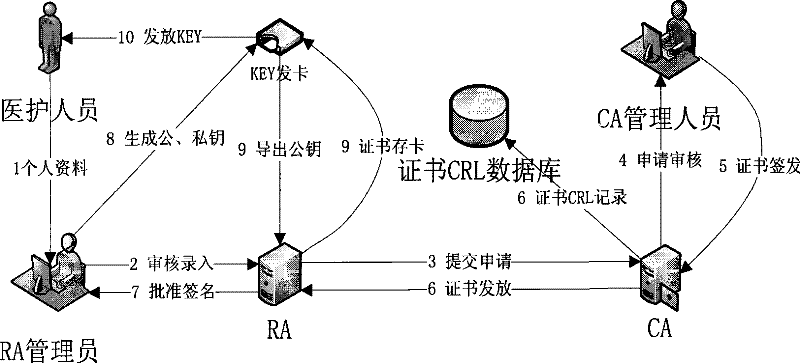
Patient document retrieval authorization control method and system
InactiveCN101727534BEasy to useProtect intellectual propertySpecial data processing applicationsRegistration authorityIntellectual property
The invention discloses patient document retrieval authorization control method and system, belonging to the technical field of computer software. The method comprises the following steps of: firstly, classifying patient documents, setting access rights to the documents for medical personnel according to the roles of the medical personnel and issuing corresponding digital certificates to the medical personnel; then signing own documents by patients and meanwhile setting diagnosis activity participation roles and the access time of the medical personnel; and finally, determining the document retrieval rights of the medical personnel according to the roles, the diagnosis activity participation roles and the access time of the medical personnel by the system. The system comprises a medical personnel certificate registration mechanism, a patient certificate registration mechanism, a certificate authorization mechanism, a safety service interface, an access control module, a document retrieval client and a document base server. Compared with the prior art, the invention not only protects the individual privacy information of patients and the intellectual property of medical units, but also are convenient for the medical personnel to conveniently use the documents of the patients.
Owner:NEW FOUNDER HLDG DEV LLC +1
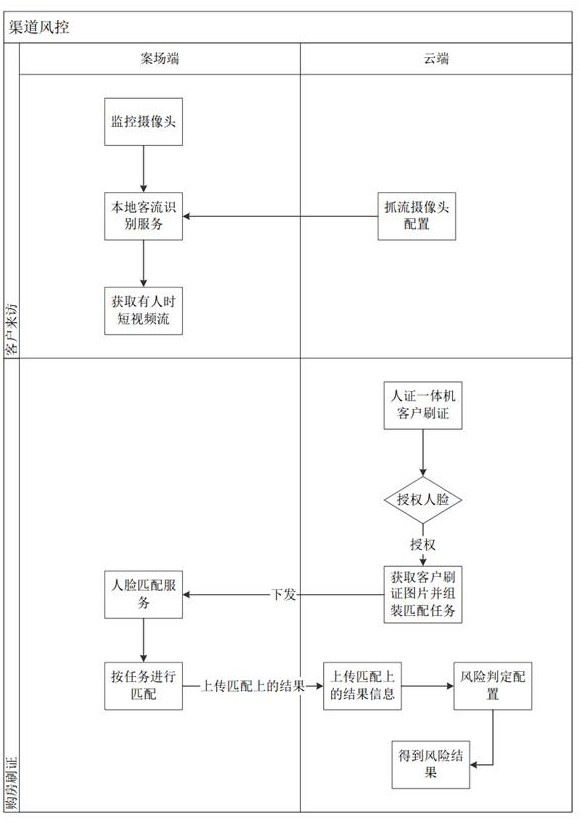
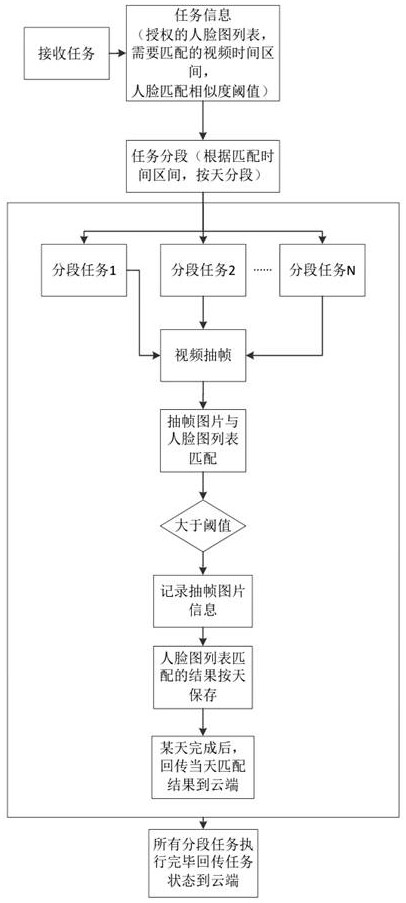
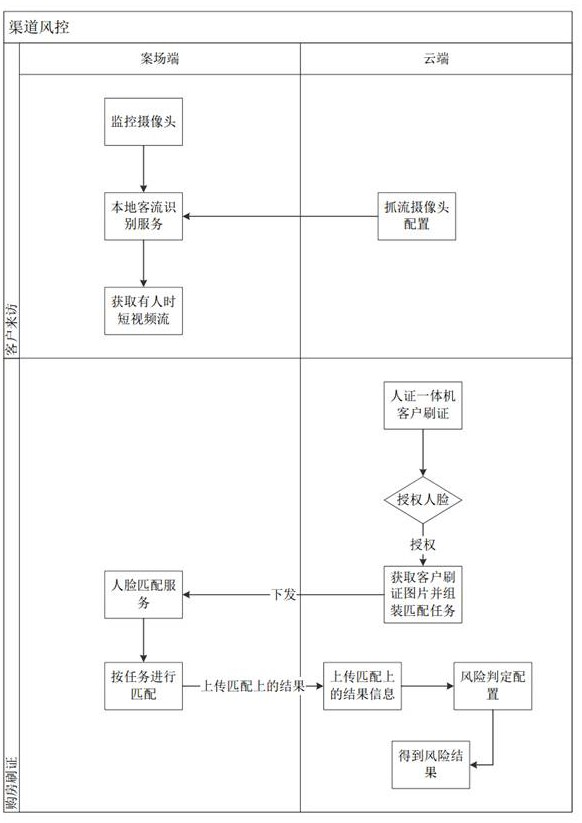
Channel risk control system based on video backtracking mode
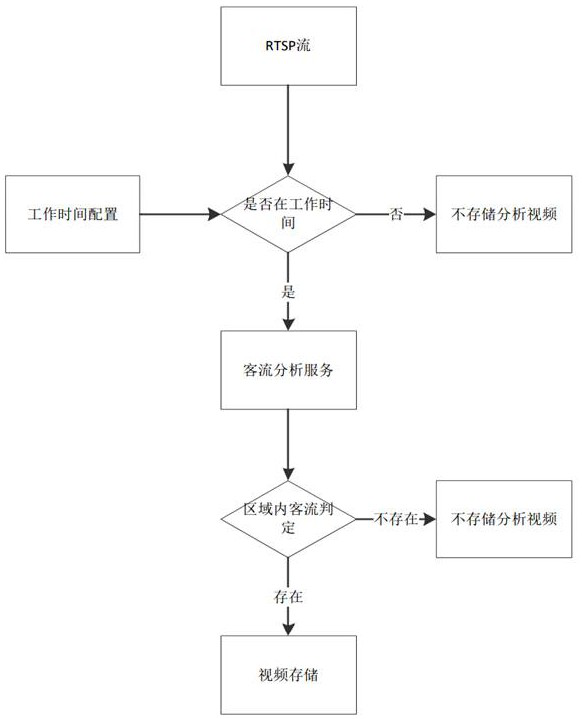
ActiveCN113810667BProtect personal privacy informationCompatible with privacy securityClosed circuit television systemsTransmissionRisk ControlEdge server
The invention discloses a channel risk control system based on a video backtracking mode, which includes a surveillance camera, an all-in-one witness machine, a case edge server, and a cloud server; the surveillance camera is used to record a case surveillance video, and The stream is transmitted to the edge server of the case field; the all-in-one machine is used for identity authentication of the customer's face information, and when the identity authentication is passed, the client's authorized face is transmitted to the cloud server; the cloud server is used for the management algorithm Configuration and risk judgment management, assemble matching tasks according to customer face information, and send the matching tasks to the edge server of the case field; the edge server of the case field is used video, and according to the matching task issued by the cloud server, perform video backtracking on the captured video and match the authorized face. The present invention not only is compatible with privacy security, but also completes early warning of channel risks.
Owner:成都旺小宝科技有限公司
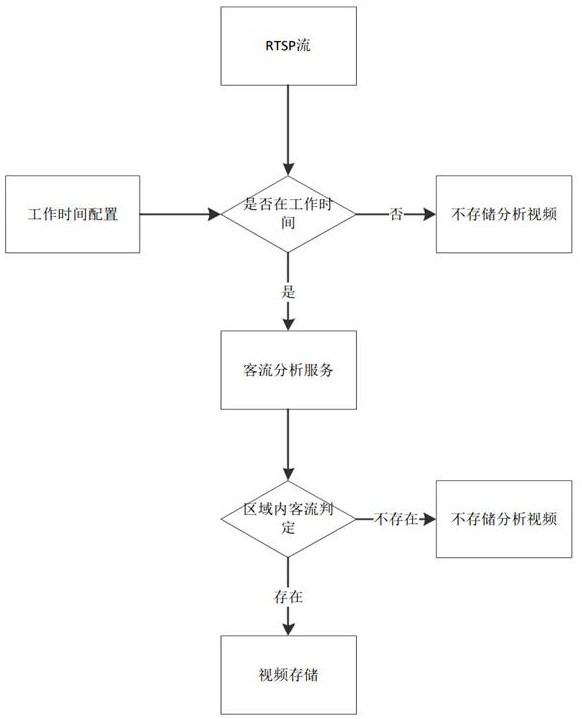
Channel risk control system based on video backtracking mode
ActiveCN113810667ACompatible with privacy securityProtect personal privacy informationClosed circuit television systemsTransmissionSurveillance cameraVideo streaming
The invention discloses a channel risk control system based on a video backtracking mode. The channel risk control system comprises a monitoring camera, a human-certificate all-in-one machine, a field edge server and a cloud server. The monitoring camera is used for recording a field monitoring video and transmitting a field monitoring video stream to the field edge server; the human-certificate all-in-one machine is used for carrying out identity authentication on the face information of the client and transmitting the authorized face of the client to the cloud server after the identity authentication is passed; the cloud server is used for managing algorithm configuration and risk judgment management, assembling a matching task according to customer face information, and issuing the matching task to the field edge server; and the field edge server is used for carrying out dynamic line analysis on a video stream transmitted by the monitoring camera, storing necessary videos, and carrying out video backtracking and authorized face matching on the captured videos according to a matching task issued by the cloud server. According to the system, the privacy security is compatible, and channel risk early warning is completed.
Owner:成都旺小宝科技有限公司
A method and mobile terminal for protecting privacy
ActiveCN103634467BProtect personal privacy informationSubstation equipmentSecurity arrangementPrivacy protectionEngineering
The embodiment of the invention discloses a privacy protection method and a mobile terminal. The method for protecting privacy includes: the mobile terminal receives an instruction to enter the application software through a specified user name; when the application software has saved the identity authentication information of the specified user name, obtains the pre-stored unique identification authentication smart card feature identification, and the authentication smart card is the specified user name. The smart card when the identity authentication passes for the first time; obtain the characteristic identifier uniquely identifying the current smart card from the current smart card of the mobile terminal; match the authentication smart card with the characteristic identifier of the current smart card; if the match is successful, pass the identity authentication and allow the specified user name to enter the application. Through the above method, the present invention can effectively protect the personal privacy information stored in the mobile terminal without reducing the usability and experience of the user.
Owner:HUAWEI TECH CO LTD
A privacy-protected big data recommendation method and system
ActiveCN105138664BProtect personal privacy informationEasy to calculateDigital data information retrievalDigital data protectionPrivacy protectionEncryption
The invention discloses a big data recommendation method and system with the privacy protection function. The method includes the following steps that behavior data of users are acquired and are subjected to anonymization processing on a big data processing end; the attributes of the behavior data, subjected to anonymization processing, of the users are subjected to statistics, a statistical attribute behavior list is established, each attribute of the list represents one piece of personal information of each user, and the statistical result of each attribute is converted into an enumeration value; similar user behaviors are searched for, the similarity of every two user behaviors is calculated according to the enumeration values of data of the two user behaviors, a similarity value and a corresponding threshold are compared, and recommendation information is generated according to a comparison result. The big data recommendation method and system can protect the privacy of the users, encryption is not needed, use is convenient and fast, the calculation amount is small, and implementation is easy.
Owner:智网安云(武汉)信息技术有限公司
Password input control device, method and computer-readable storage medium
ActiveCN107688388BProtect personal privacy informationPrevent leakageComplete banking machinesInput/output for user-computer interactionPasswordInput control
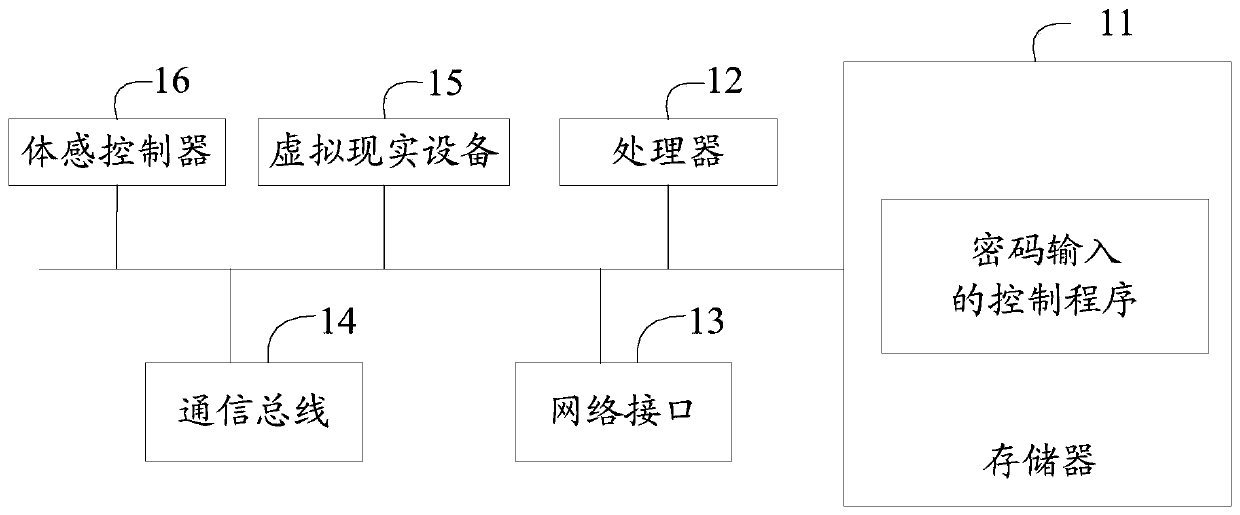
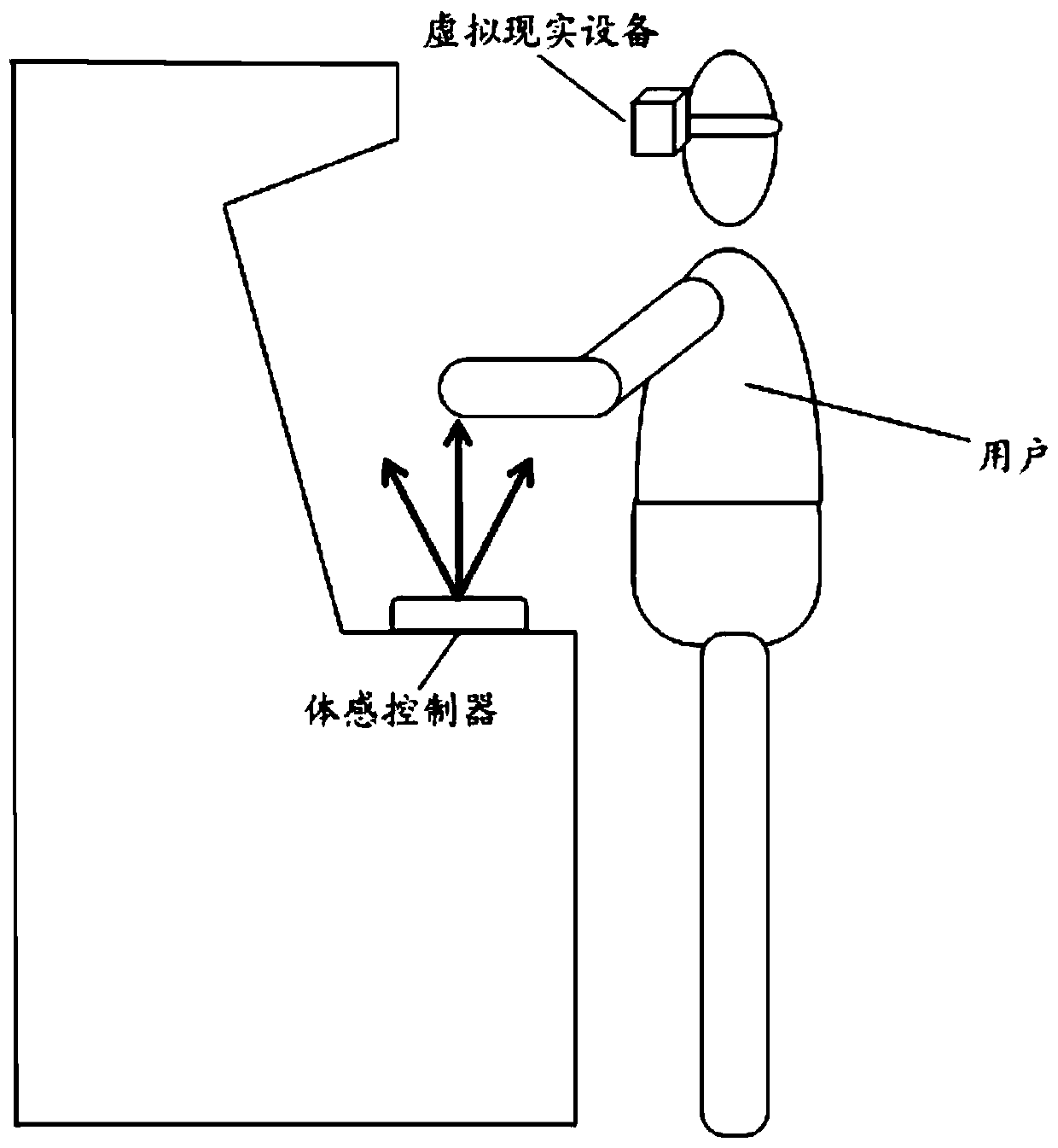
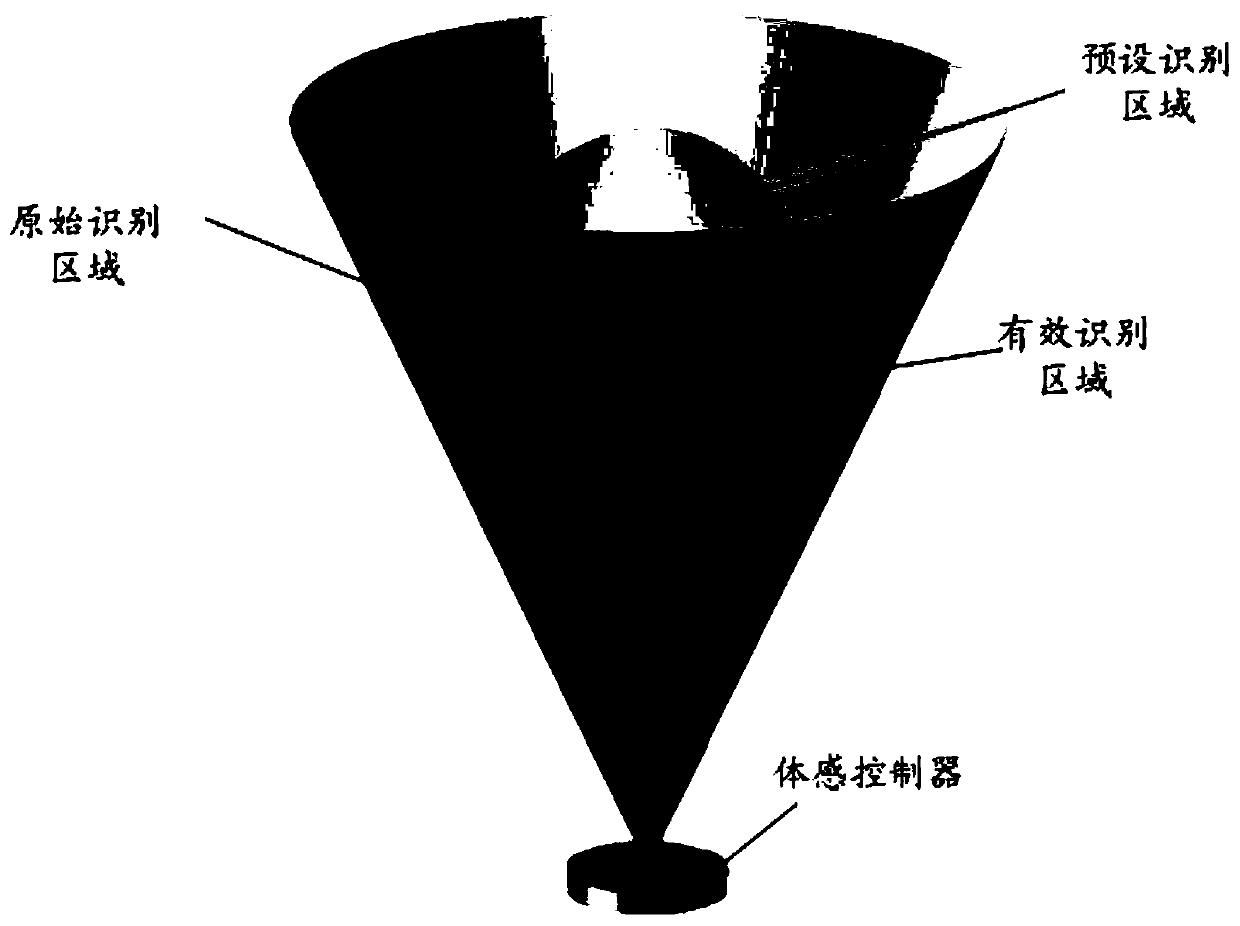
Disclosed are a password input control device and method, and a computer readable storage medium. The control device comprises a memory, a processor and a password input control program stored in the memory and operating on the processor, and further comprises a virtual reality device and a somatosensory controller, the program when executed by the processor implementing the following steps: displaying, on the basis of a virtual reality device worn by a user, a virtual scene provided with a virtual keyboard (S10); collecting in real time, in a preset recognition area, by means of the somatosensory controller, first position coordinates of a hand of the user (S20); converting, according to a coordinate transformation rule, the first position coordinates into second position coordinates in the virtual scene, and displaying a virtual hand at a position corresponding to the second position coordinates (S30); and determining whether the virtual hand triggers a key area on the virtual keyboard, if so, determining a character corresponding to the triggered key area and displaying same in the virtual scene (S40). The control device and control method improve the security of password input.
Owner:PING AN TECH (SHENZHEN) CO LTD
Features
- R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
Why Patsnap Eureka
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Social media
Patsnap Eureka Blog
Learn More Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com