Flexible asymmetric group key negotiation method
A group key agreement and group key technology, which is applied in the field of elastic asymmetric group key agreement, can solve the problem that there is no precedent for selective information exchange technology work
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment 1
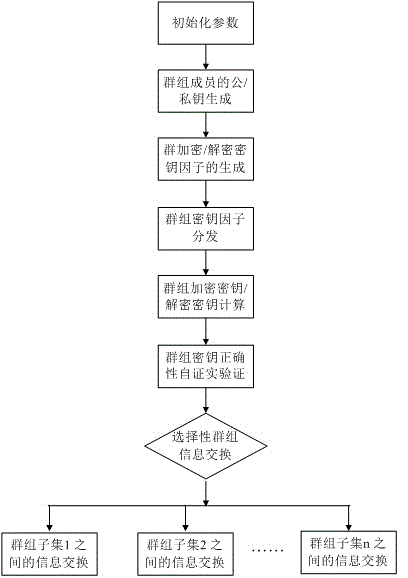
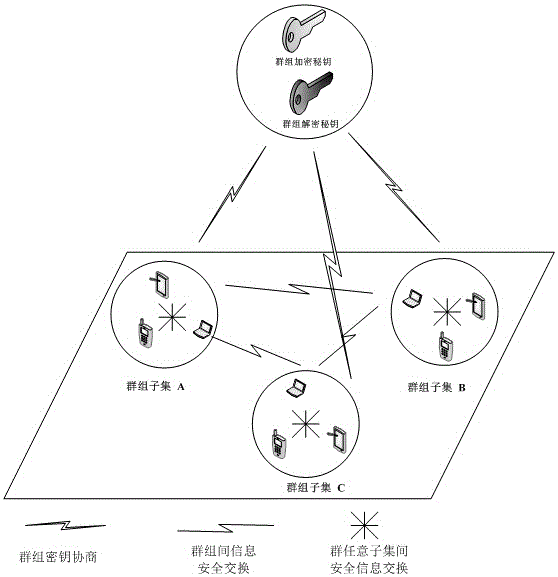
[0061] Group communication members in a complex network environment are often distributed in different security domains and different access rights. In the process of group information exchange, different information has different degrees of confidentiality, and often only specific group members are required to share it. A method of flexible asymmetric group key agreement agreement, such as figure 1 As shown, the steps are as follows: ①The members participating in the group key agreement first initialize the parameters, and then respectively generate their own public / private key pairs; ②Blind their respective group contributions through their respective public / private key pairs Key shares and broadcast these group key shares; ③After the remaining members receive the corresponding broadcast key shares, they will combine and calculate these key shares to obtain the group key; ④The group members calculated by self-verification Whether the group key is correct; ⑤If the calculation...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com