Terminal and method for protecting user privacy information
A technology for user privacy and private information, which is applied in the field of information security of mobile terminals and can solve problems such as leakage of users' personal privacy information.
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment 1
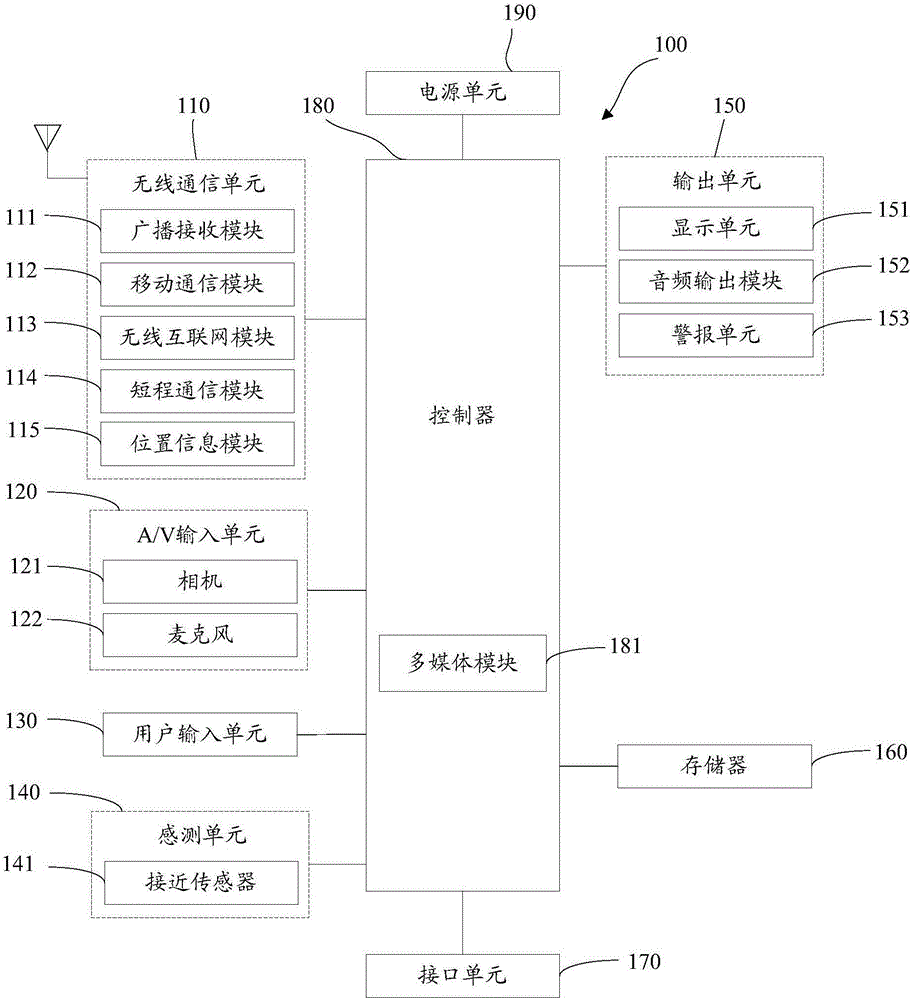
[0074] The method for protecting user privacy information provided by the present invention can be implemented on a terminal for protecting user privacy information, wherein the terminal can include mobile phones, smart phones, notebook computers, digital broadcast receivers, personal digital assistants (PDAs), Mobile terminals such as tablet computers (PAD), portable multimedia players (PMP), navigation devices, etc.
[0075] If the mobile terminal has an operating system, the operating system can be UNIX, Linux, Windows, Mac OSX, Android, Windows Phone, and the like.
[0076] Application software (Application, APP) is a third-party application program for smart terminals. Users can use various application software for office work, entertainment, and information acquisition. The formats include ipa, pxl, deb, apk, etc. Format.
[0077] image 3 It is a flow chart of Embodiment 1 of the method for protecting user privacy information in the present invention, as shown in im...
Embodiment 2
[0101] Figure 4 It is a flow chart of Embodiment 2 of the method for protecting user privacy information in the present invention, as shown in Figure 4 As shown, the method for protecting user privacy information provided by the embodiment of the present invention is applied on a mobile phone, and the method may include the following steps:
[0102] Step 401, judging whether the current user account status is the same user account status.
[0103] The mobile phone determines whether the current user account status is the same user account status, that is, determines whether the current user account status is the same user account status or two or more user account statuses, and if the current user account status is not the same user account status, then execute step 402 ; If the current user account status is the same user account status, execute step 403.
[0104] Step 402 , end the current task, and return to step 401 .
[0105] The mobile phone ends the current process...
Embodiment 3
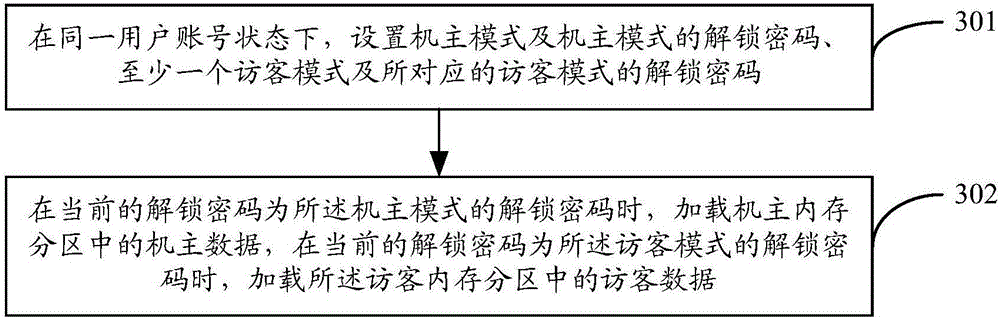
[0126] Figure 7 It is a schematic structural diagram of a terminal embodiment for protecting user privacy information in the present invention, as shown in Figure 7 As shown, the terminal 07 for protecting user privacy information provided by the embodiment of the present invention includes: a setting module 71 and a loading module 72; wherein,
[0127] The setting module 71 is used to set the host mode and the unlock password of the host mode, at least one visitor mode and the unlock password of the corresponding visitor mode under the same user account status;
[0128] The loading module 72 is configured to load the owner data in the owner memory partition when the current unlock password is the unlock password of the owner mode, and when the current unlock password is the unlock password of the guest mode, Loading guest data in the guest memory partition;
[0129] Wherein, the owner memory partition is isolated from the guest memory partition; the owner data includes ap...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com