Privacy protecting method and mobile terminal
A mobile terminal and privacy protection technology, applied in the field of privacy protection, can solve the problems of personal privacy information leakage, user property loss, mobile terminal loss, etc., and achieve the effect of protecting personal privacy information
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
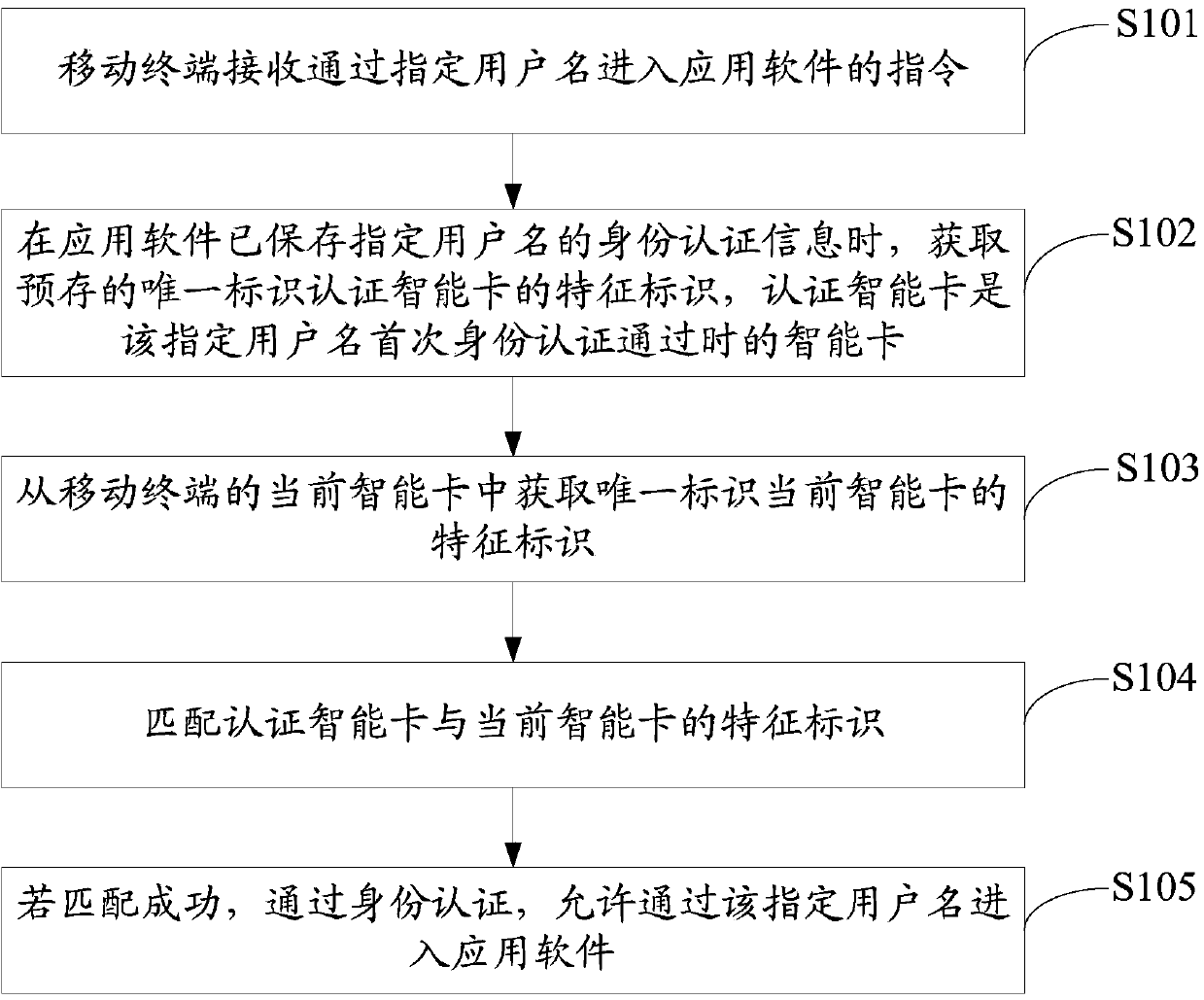
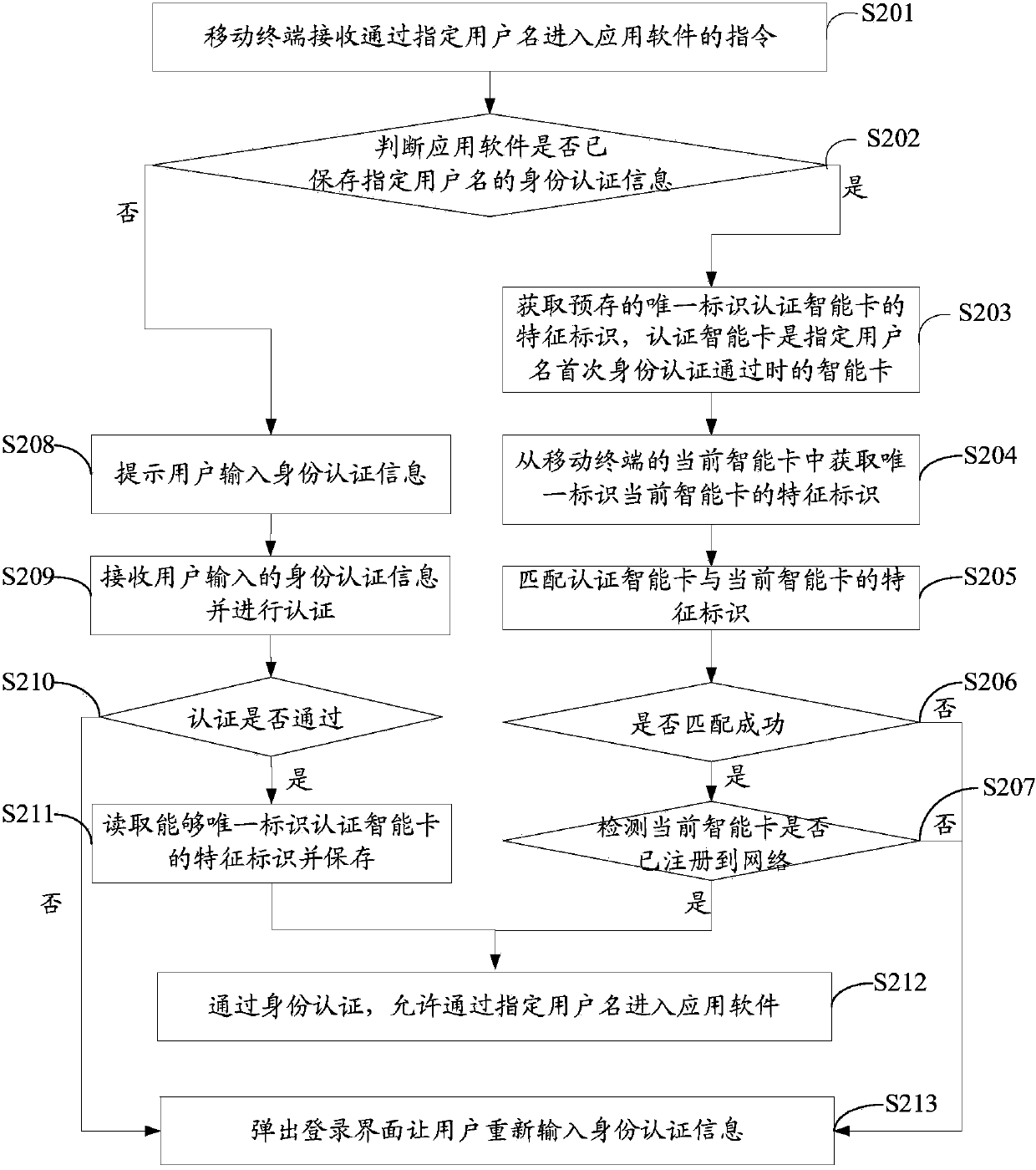
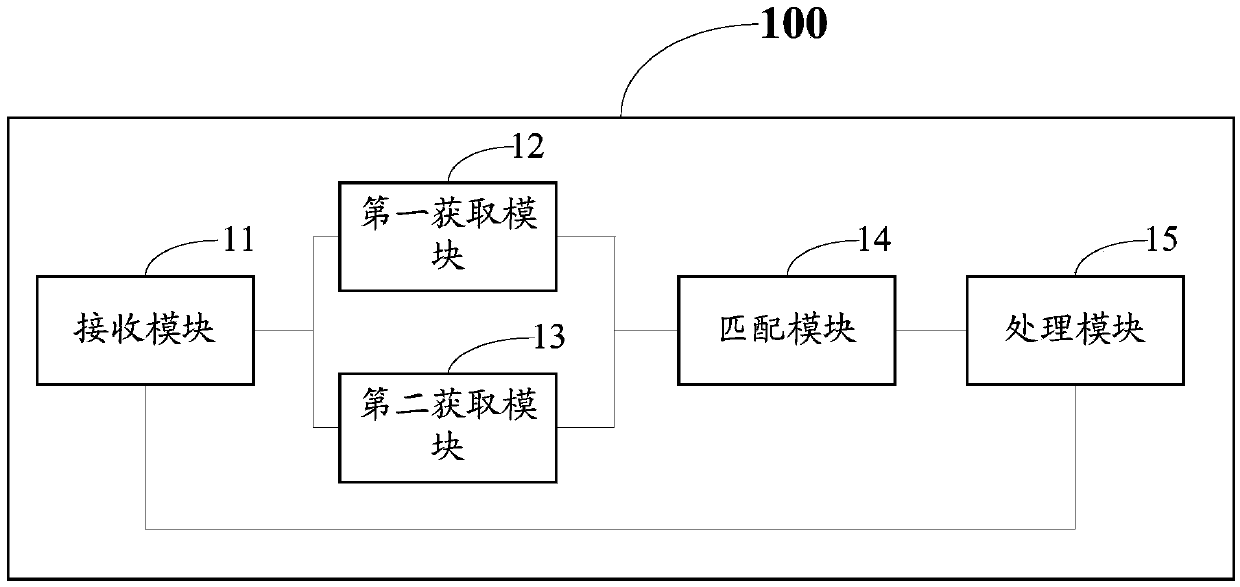
[0022] With the continuous development of smart mobile terminals, their applications and functions are diversified, and users can install various application software on mobile terminals. During the login process of some application software, it may be necessary to input user identity authentication information for identity authentication before entering.
[0023] In the prior art, one login method is to enter the identity authentication information for authentication every time you enter the application software. This method ensures the security of the user identity information, but compared with the mobile terminal with a smaller screen, the input efficiency is low. Bring great inconvenience to the user's use. Another login method is to remember the identity authentication information of the user after passing the first authentication, and log in to the application software directly without authentication when entering the application again. In this way, there is a certain ...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com