Block chain hidden data segmentation transmission method
A technology of data segmentation and transmission method, applied in digital transmission systems, transmission systems, and key distribution, can solve the problems of poor practicability and poor concealment of data concealment transmission, and achieve high practicability, anonymity, and strong anonymity. Effect
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment
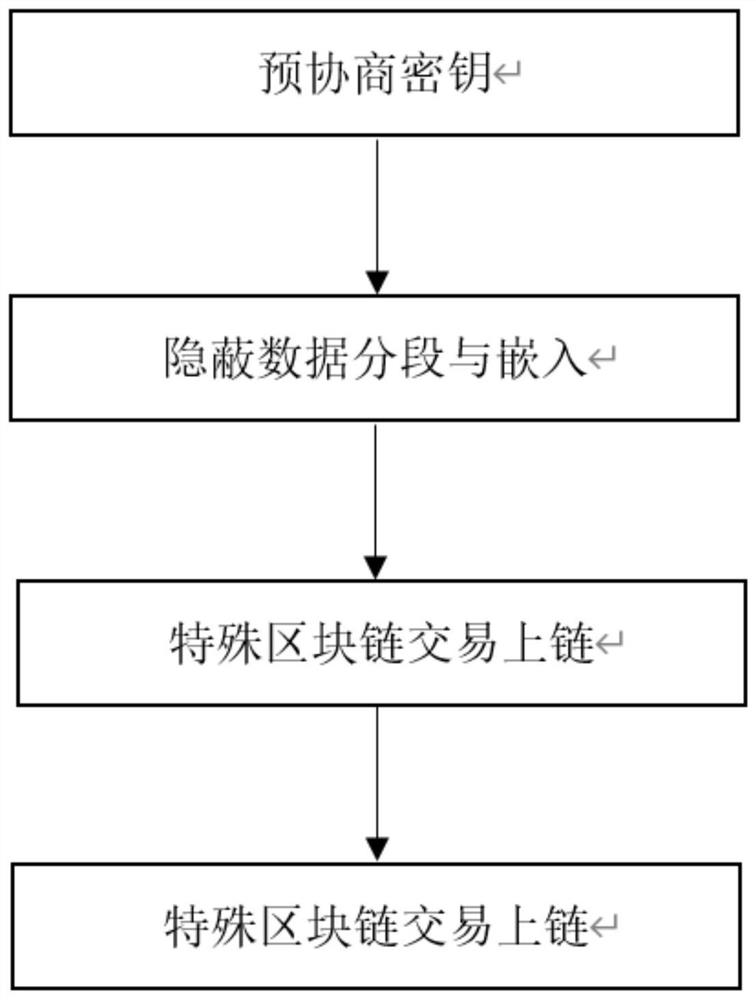
[0040] Such as figure 1 As shown, a blockchain concealed data segment transmission method includes the following steps:
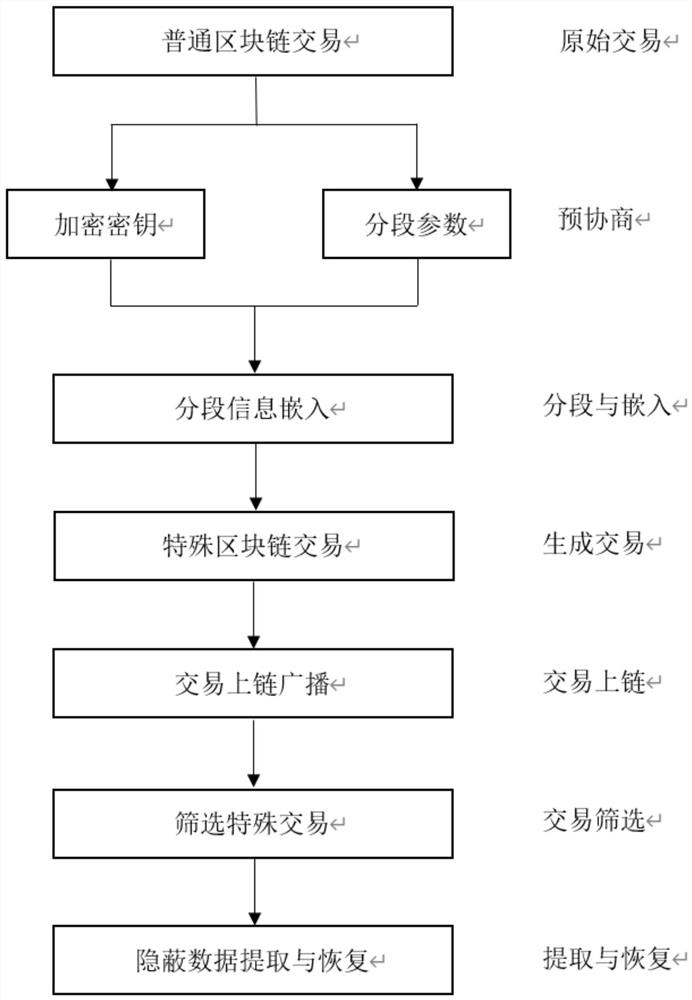
[0041] Step 1: Pre-negotiate the key. The sender and the receiver negotiate in advance the screening method of the special transaction, the key used to encrypt the hidden information and the relevant parameters of the hidden information segment.
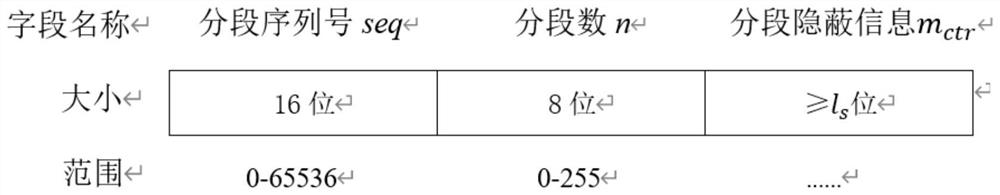
[0042] Specifically, the sender and the receiver pre-negotiate the encrypted one-time key K, and the number of segments negotiated in advance between the sender and the receiver is n. Such as figure 2 shown.
[0043] In this embodiment, a secure symmetric key cryptosystem SKE is used to encrypt segmented covert messages, and the SKE scheme includes an encryption algorithm Enc and a decryption algorithm Dec, wherein:
[0044] Encryption algorithm: c←Enc(K,m), means to receive a key K and a hidden information m as input, and output a ciphertext c.
[0045] Decryption algorithm: m←Dec(K,c), means to receive a k...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com