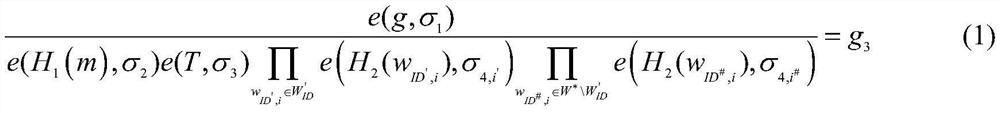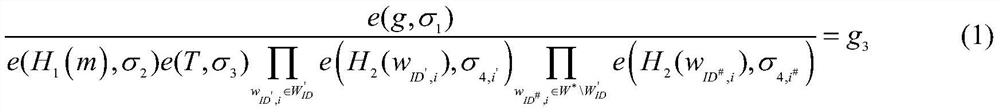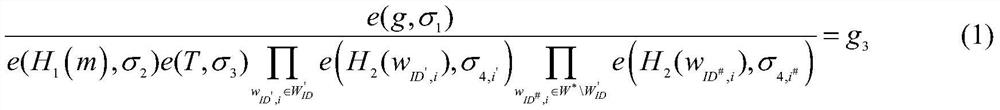Attribute-Based Linkable Network Ring Signature Method
A ring signature and attribute technology, applied in digital transmission systems, user identity/authority verification, secure communication devices, etc., can solve problems such as failure to resist collusion attacks, difficulty in solving secondary signatures, and failure to achieve linkability. High security, strong anonymity, and the effect of ensuring anti-collusion attack
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment
[0053] A specific embodiment of the present invention is an attribute-based linkable network ring signature method, and the process of the proposed method is as follows:
[0054] (1) System establishment stage
[0055] a) System public parameter generation
[0056] First, the attribute authorization center AA is in the finite domain Randomly select an integer α as the system master key MSK, where q is greater than 2 512 is a safe prime number; then, the attribute authorization center AA randomly selects two cyclic multiplicative groups G with order p 1 , G 2 , and define a bilinear map e:G 1 ×G 1 →G 2 ; Finally, the attribute authorization center AA from the group G 1 Randomly select two elements in the public key as a g 1 and public key three g 3 , at the same time the public key - g 1 Perform modular exponent operation to get the public key 2g 2 : public key 2 , public key three g 3 Perform bilinear pairing operation to generate public key 4g 4 , g 4 =e(g ...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com