Authentication and key negotiation method, gateway, sensor and electronic equipment
A key agreement, sensor technology, applied in key distribution, can solve the problem of important data leakage, and achieve the effect of ensuring security and realizing anonymity
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment 1
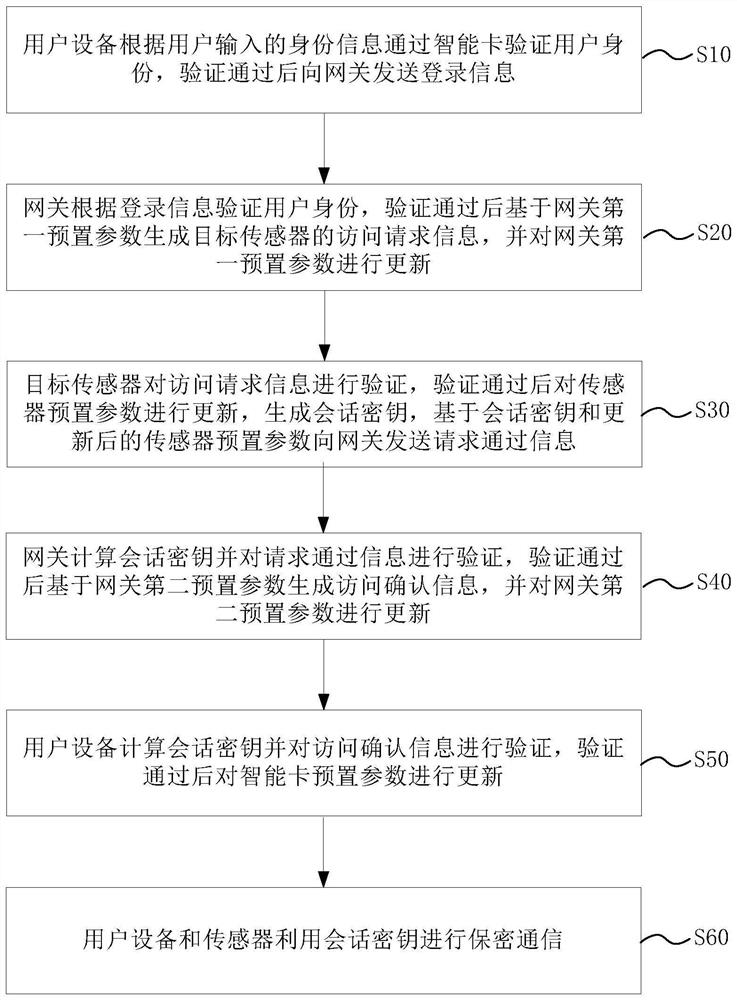
[0067] The authentication and key negotiation method for a wireless sensor network in this embodiment is applied to a wireless sensor network. The wireless sensor network includes a sensor, a gateway, a smart card, and a user device. Wherein, the user logs in and accesses the target sensor through the user device and the smart card, and the user device can Terminal devices such as mobile phones, tablets, and computers are not limited here; there can be one or more sensors and gateways, and each sensor is connected to the gateway through a wireless network. The sensor is used to collect data and send the collected data to the gateway. The gateway processes the data and sends the processed data results to the user device; the user needs to register with the gateway before logging in, and then perform security authentication and key negotiation through the gateway and the sensor.
[0068] figure 1 It is a schematic flow diagram of the authentication and key agreement method of th...
Embodiment 2
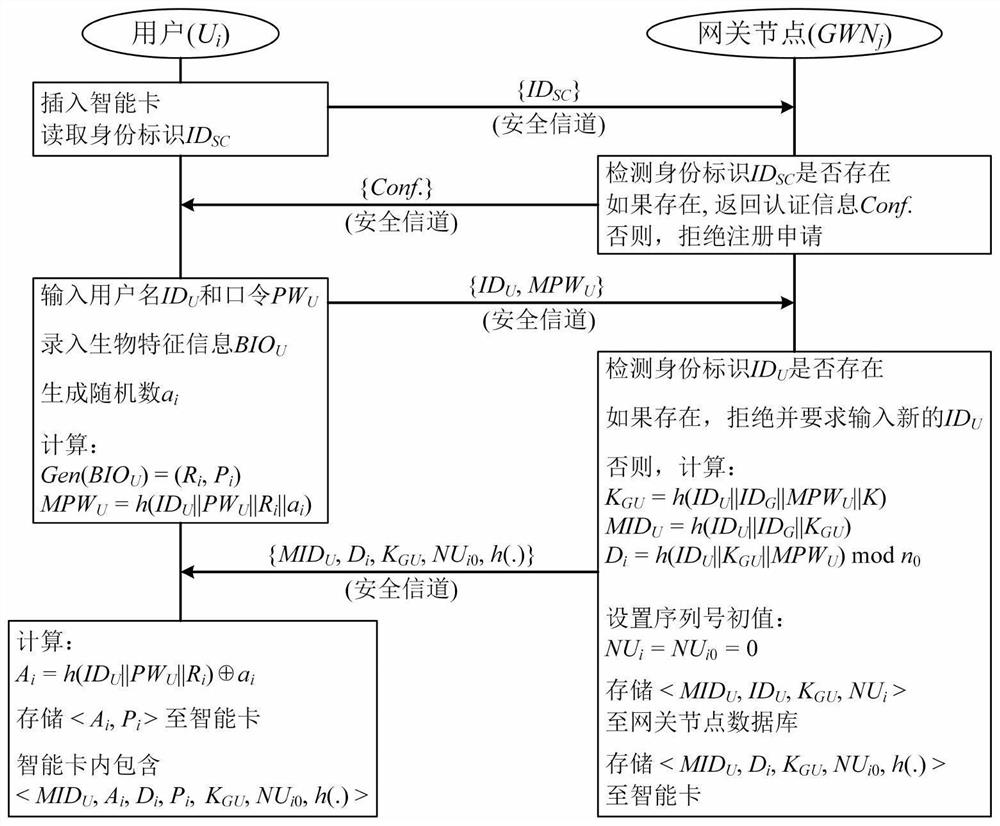
[0112] In this embodiment, on the basis of the first embodiment, the specific implementation process of the method proposed in the application is described in detail. The method includes four execution subjects: user, smart card, sensor node and gateway node. The user here refers to the device used on the user side. The steps of the method include:
[0113] S1. Device initialization, including:
[0114] Step a1, the gateway node selects two random integers as the gateway node identity ID G and the master key K of the gateway node, and store it in the memory of the gateway node;
[0115] Step a2, the gateway node selects the sensor node identity ID for the sensor node S , and store it in the memory of the sensor node;
[0116] Step a3, the gateway node pre-initializes all smart cards, and selects a smart card ID for each smart card SC and store it on the smart card.
[0117] S2. User registration and sensor node registration.
[0118] When new users want to access the dat...
Embodiment 3
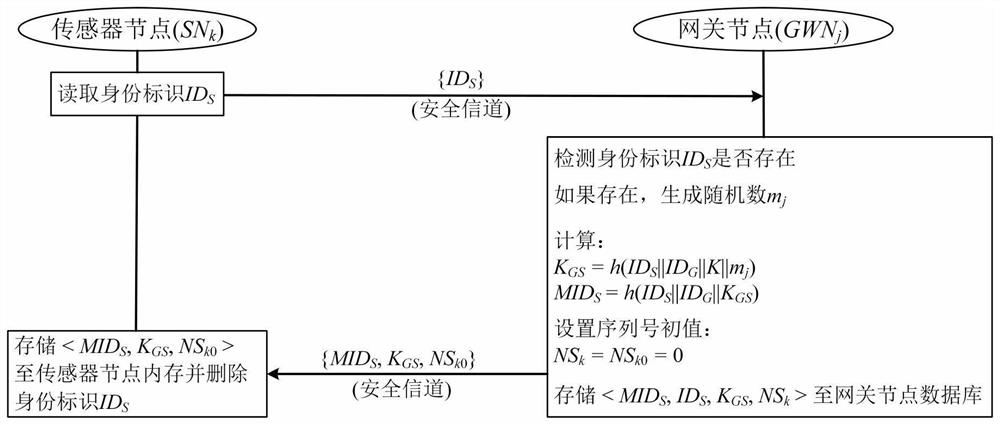
[0244] The second aspect of the present application provides a sensor through Embodiment 3, Figure 6 It is a schematic diagram of the sensor structure in Embodiment 3 of the present application, such as Figure 6 As shown, the sensor includes:
[0245] The first verification module 11 is configured to verify the access request information;
[0246] The parameter update module 12 is used to update the sensor preset parameters after the verification is passed, and the sensor preset parameters include a pseudo-random sensor identification, a shared key between sensor nodes and gateway nodes;
[0247] The key generation module 13 is used to generate a session key, and sends request passing information to the gateway based on the session key and the updated sensor preset parameters;
[0248] The first communication module 14 is configured to use the session key to perform secure communication with the user equipment.
[0249] The sensor provided in this embodiment can be used t...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com