Method of providing a signing key for digitally signing verifying or encrypting data and mobile terminal
A signature key and mobile terminal technology, which is applied in the field of mobile terminals and gateways, can solve the problem that the signature key is not very safe, and achieve the effect of improving adaptability
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
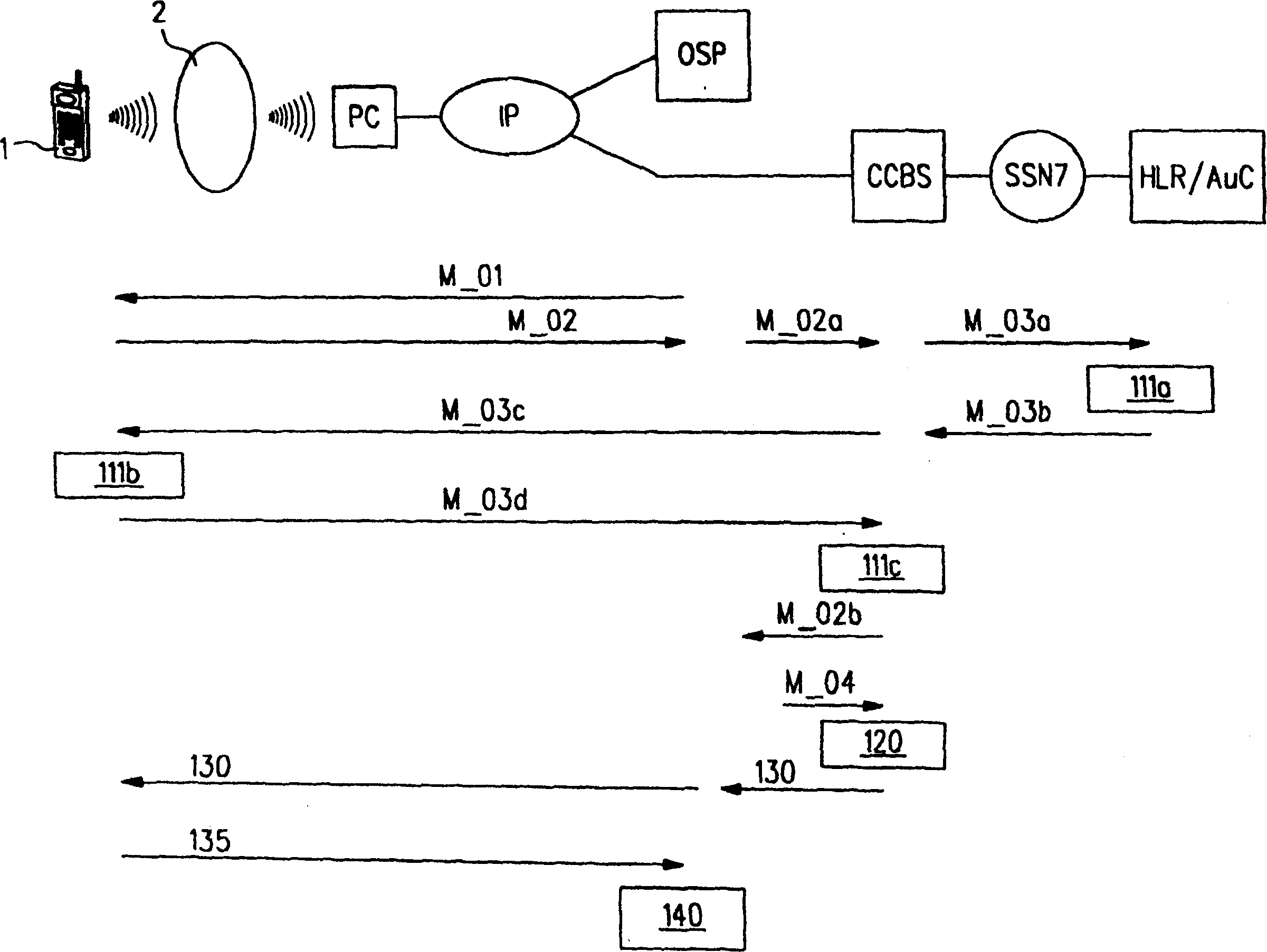
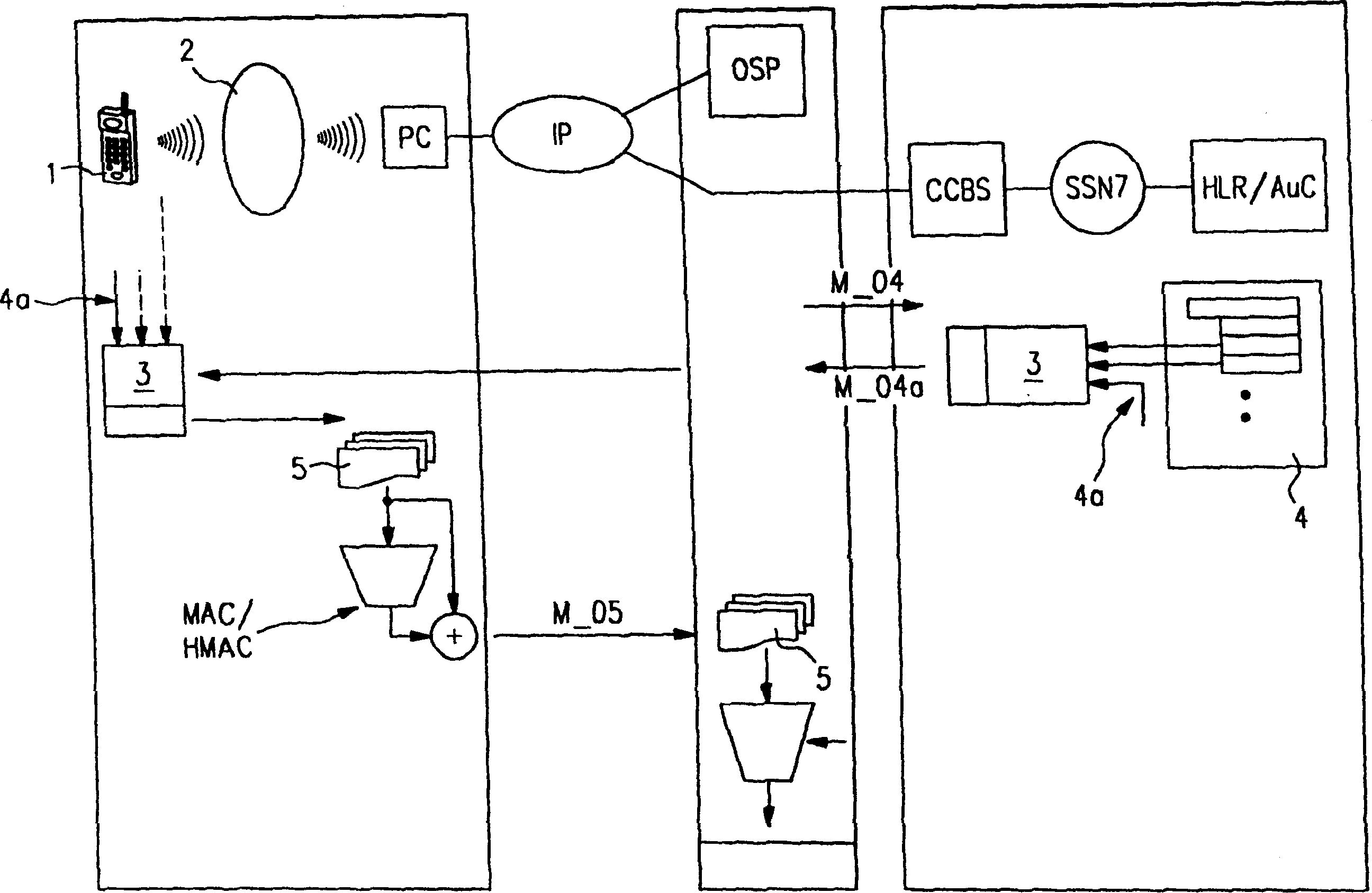
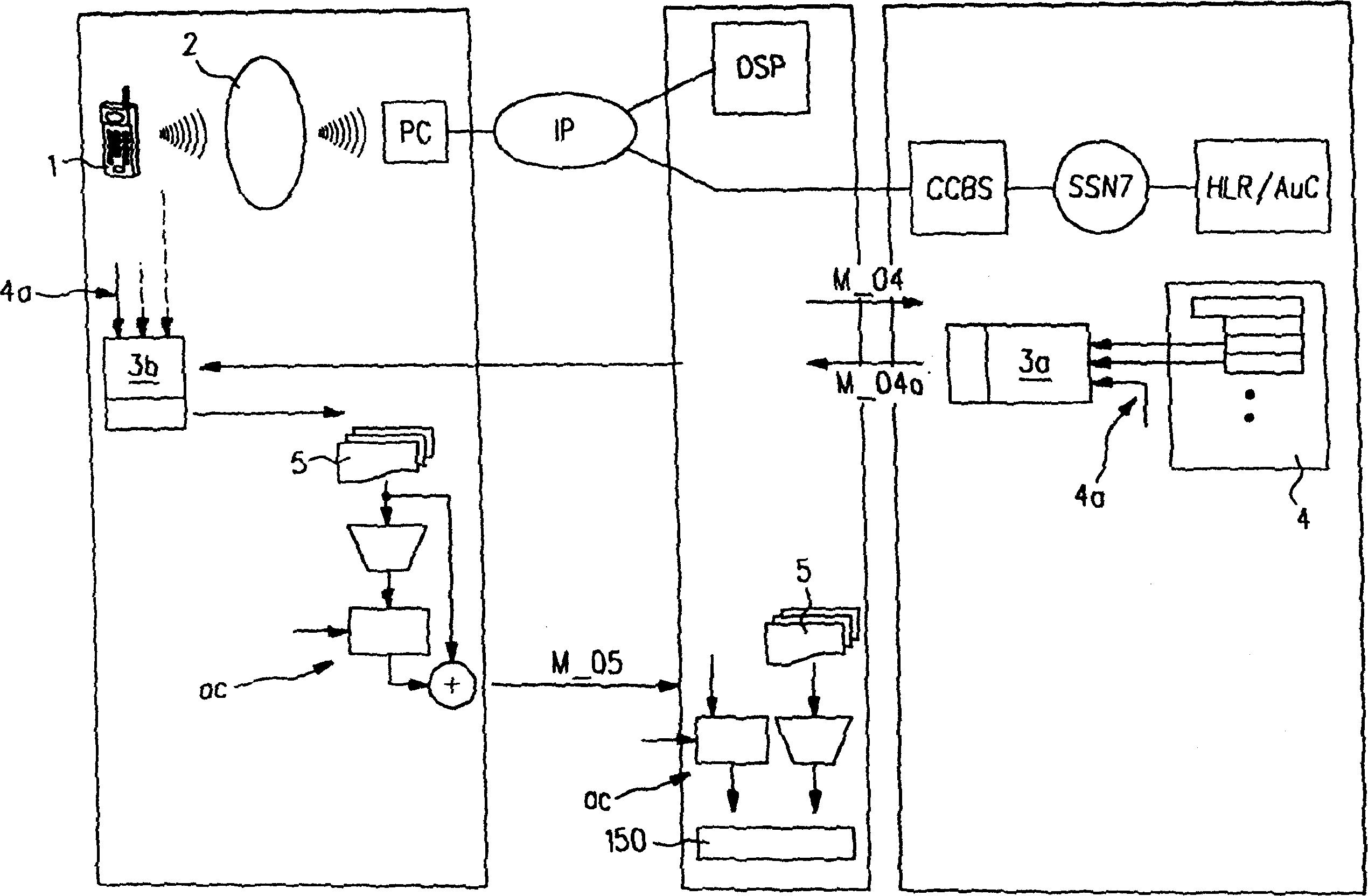
[0035] Figure 1a Shown is a mobile terminal 1 of a first contracted party who is contracted with an online service provider OSP constituting a second contracted party.
[0036] from Figure 1a As can be seen in the figure, between the mobile terminal 1 and the online service provider OSP firstly through the wireless access network 2 (which may be based on a specific network such as DECT, bluetooth or infrared data communication), secondly through the personal computer PC (in turn connected to said online service provider via Internet IP) to establish a connection. Both the mobile terminal 1 and the personal computer PC have interfaces corresponding to DECT, bluetooth or infrared data communication.
[0037] Any other type of access point such as a WLAN (Wireless Local Area Network) router or similar may be used instead of the personal computer PC.
[0038] The first party wants to use an online service provided by the online service provider OSP and is therefore required to ...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com