Patents
Literature
137 results about "Monitoring procedure" patented technology
Efficacy Topic
Property
Owner
Technical Advancement
Application Domain
Technology Topic
Technology Field Word
Patent Country/Region
Patent Type
Patent Status
Application Year
Inventor
Holter monitoring is a procedure that uses a portable heart monitor that is worn by the individual. The Holter monitoring device is a portable battery operated device. The Holter monitoring procedure involves the application of electrodes to the chest of the individual.
Method and system for substituting media content
A business entity can replace original advertising content in which the business has little or no economic interest with alternative advertising content in which the business has more economic interest. A media program, such as a television show, can have associated original advertising content that can provide economic benefit to the program's producers, affiliates, or sponsors. The original advertising content can appear during a commercial break or a program intermission. A machine or a human can monitor the program to detect the commercial break or an occurrence of some other advertising event connected with presentation of the original advertising content. In response to detecting the commercial break, presentation of the original advertising content can be manually or automatically interrupted, suspended, or stopped. The alternative advertising content can be presented during the commercial break as a replacement or substitution for the original advertising content, thereby benefiting the business entity.
Owner:MEDIA IP HLDG LLC
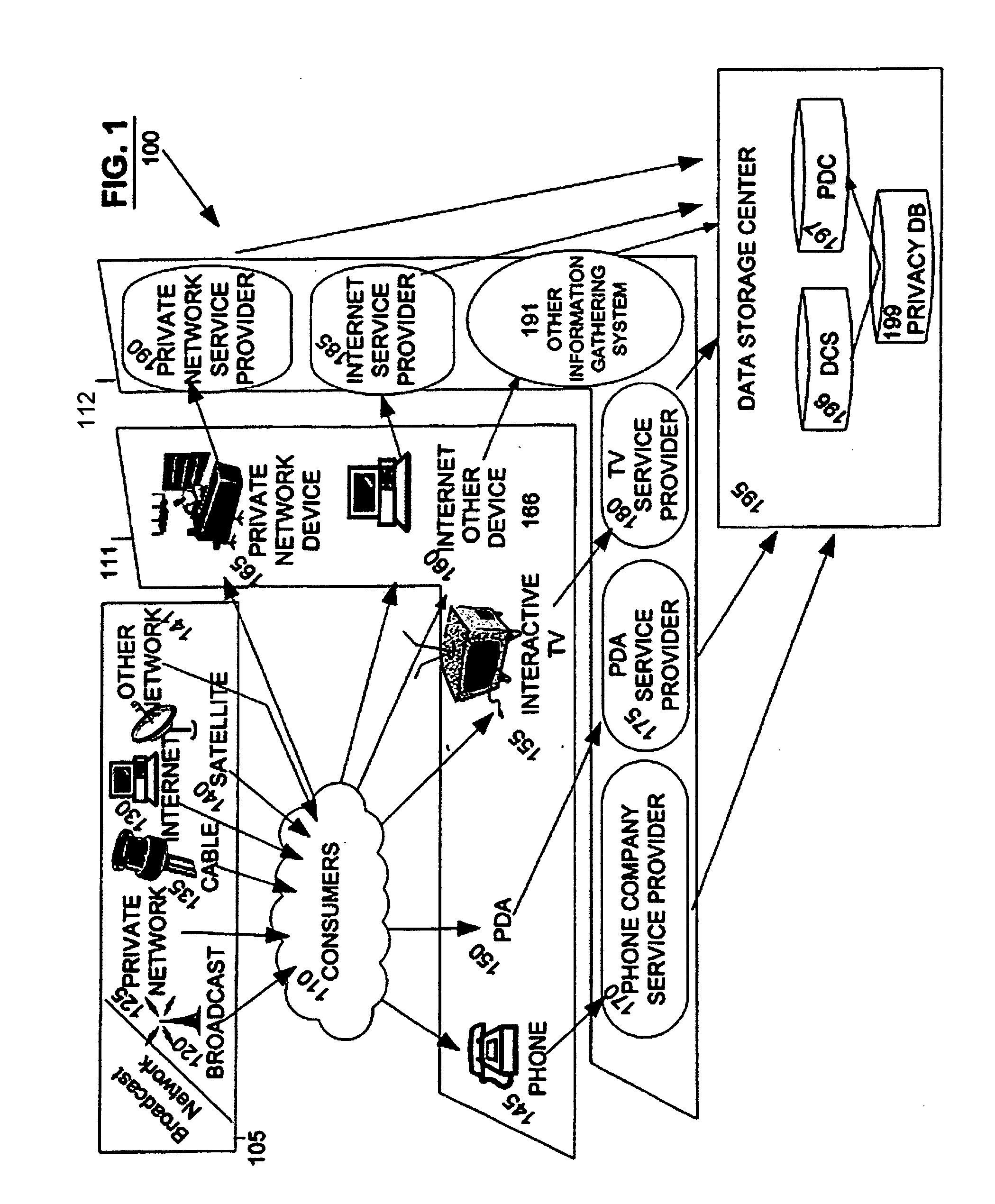
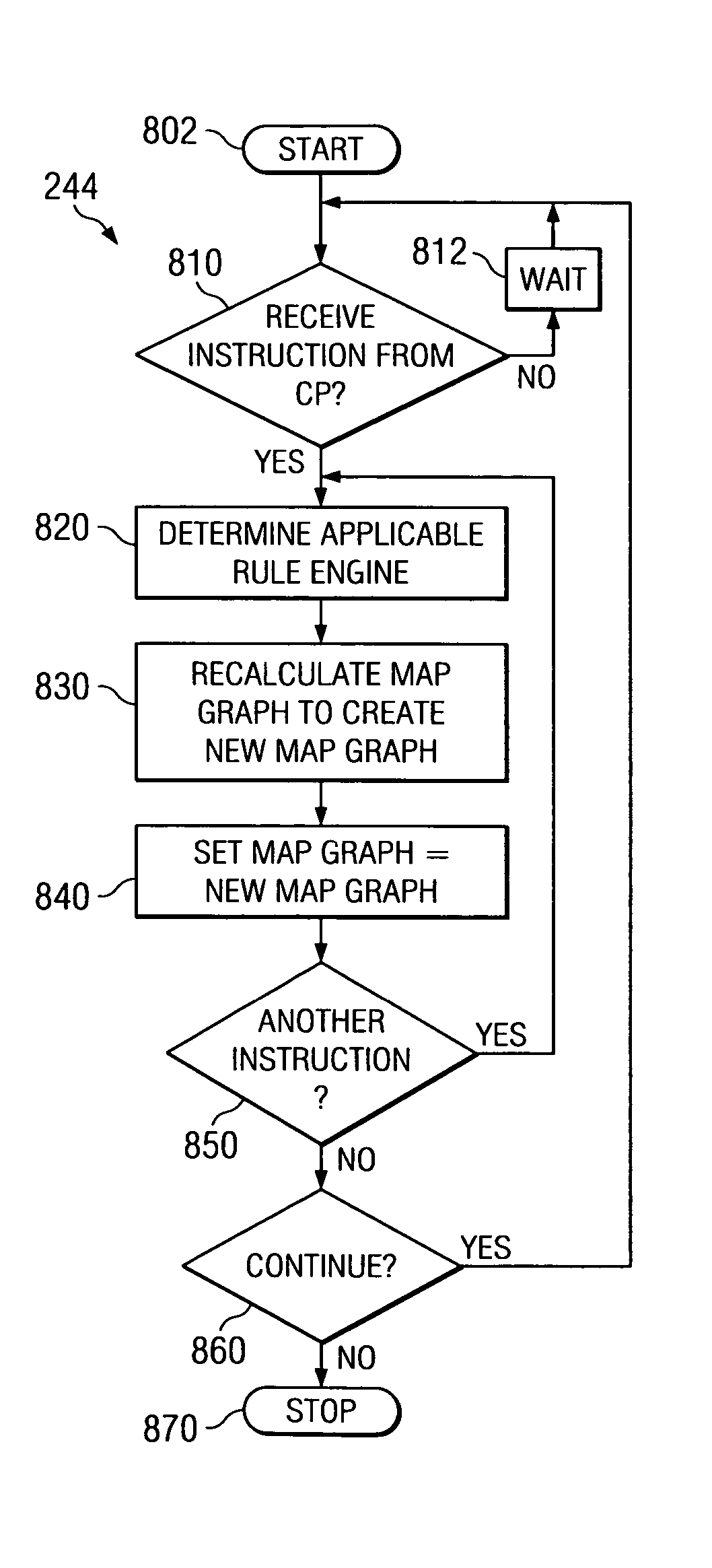
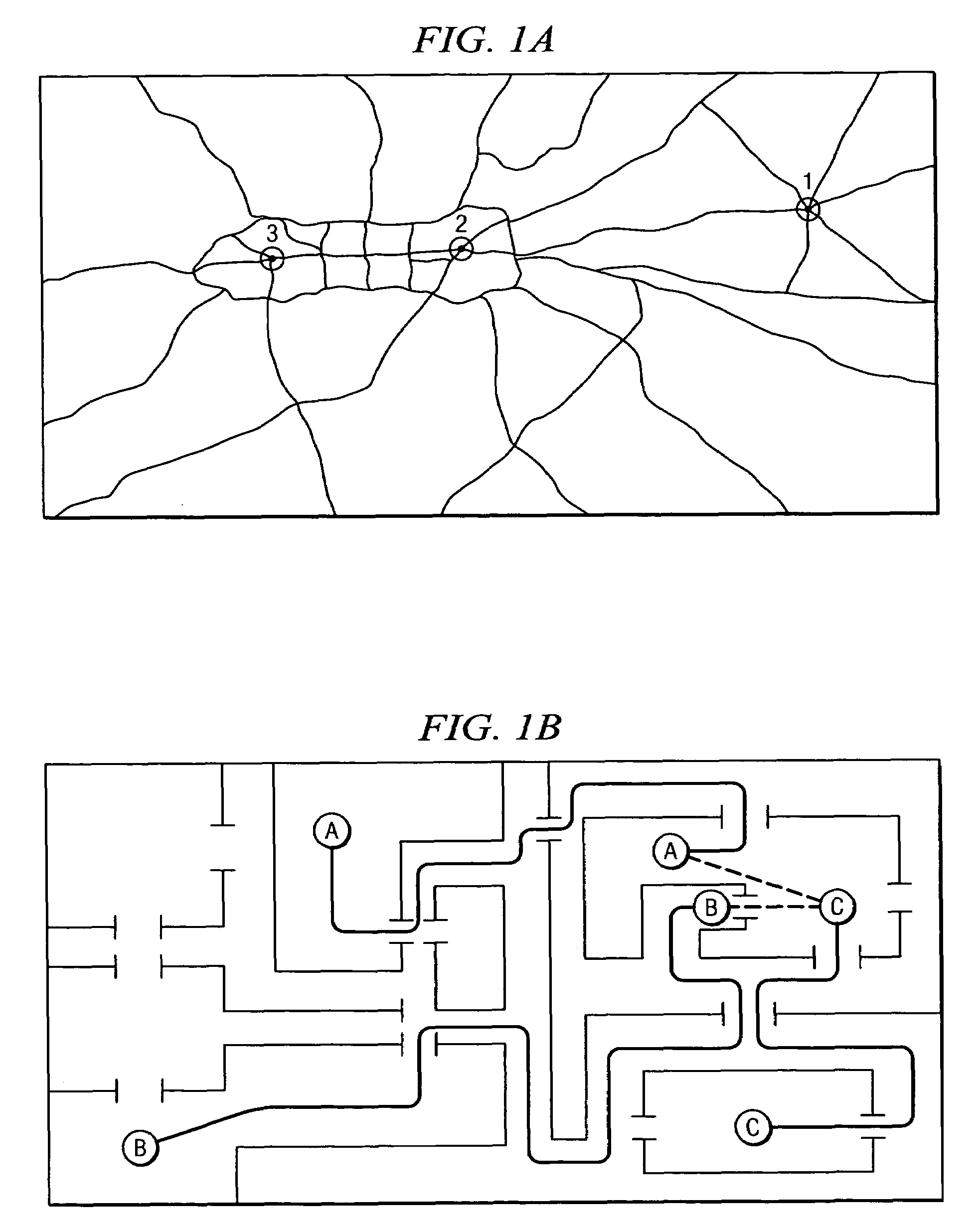
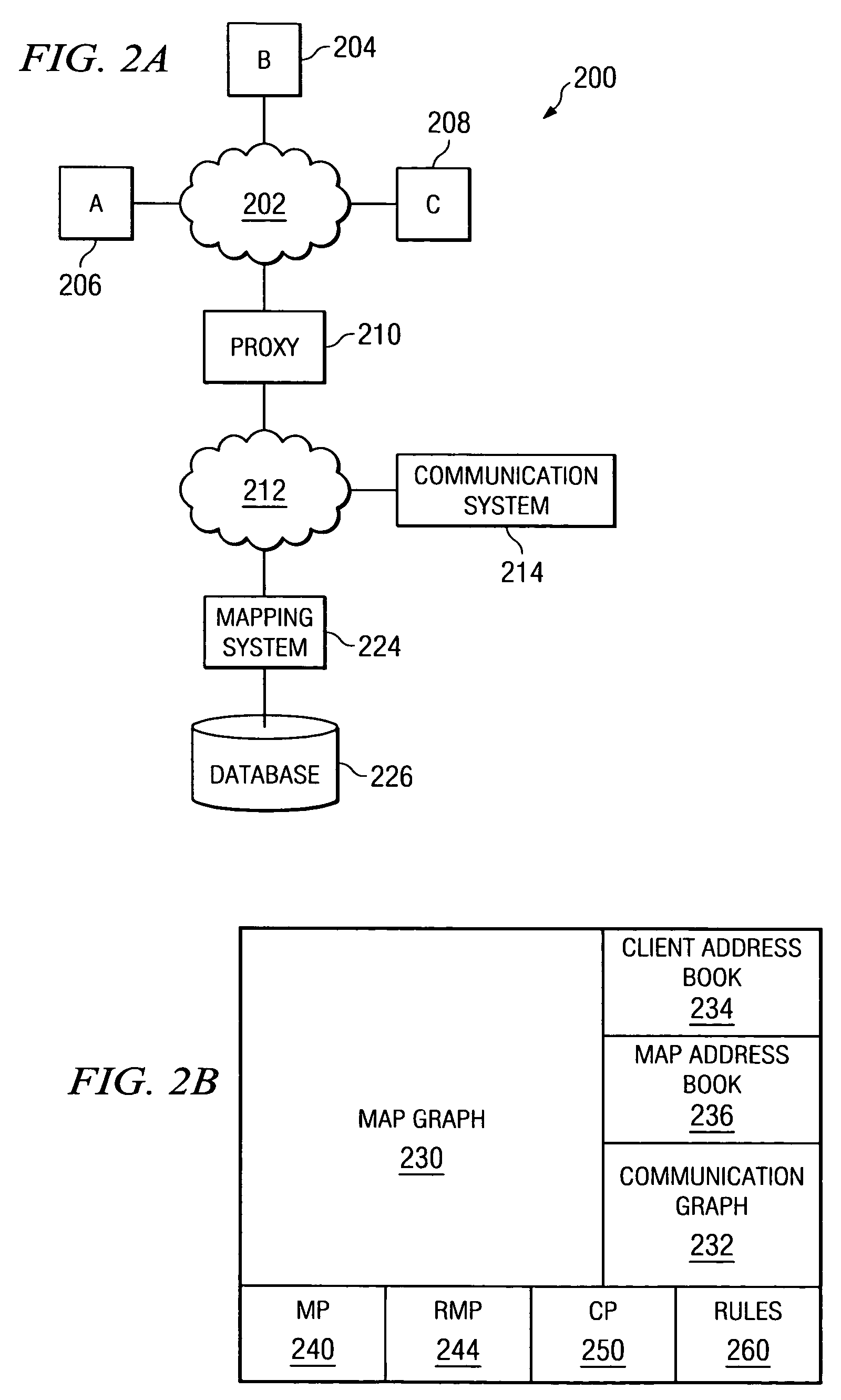
Method for distributing and geographically load balancing location aware communication device client-proxy applications
InactiveUS7428588B2Resource allocationMultiple digital computer combinationsThe InternetApplication software
A method and system for balancing server work load for cellular phone client-proxy applications in an environment where the clients change position within a given geographic area is disclosed. The method comprises the steps of mapping, monitoring, automatically re-mapping the system when required, updating a map address book, and updating a client address book. The system has a mapping system and a communication system connected to a plurality of servers, proxy servers and applications by an internal network. The proxy servers are connected to a plurality of clients by the Internet. If a threshold is exceeded, the monitoring program sends a message to a mapping program. Upon receipt of the message, the mapping program uses a rules engine to calculate a new map graph to remove load from an overloaded server (or servers) and to adjust communication requirements for data by reconfiguring partitions.
Owner:ACTIVISION PUBLISHING
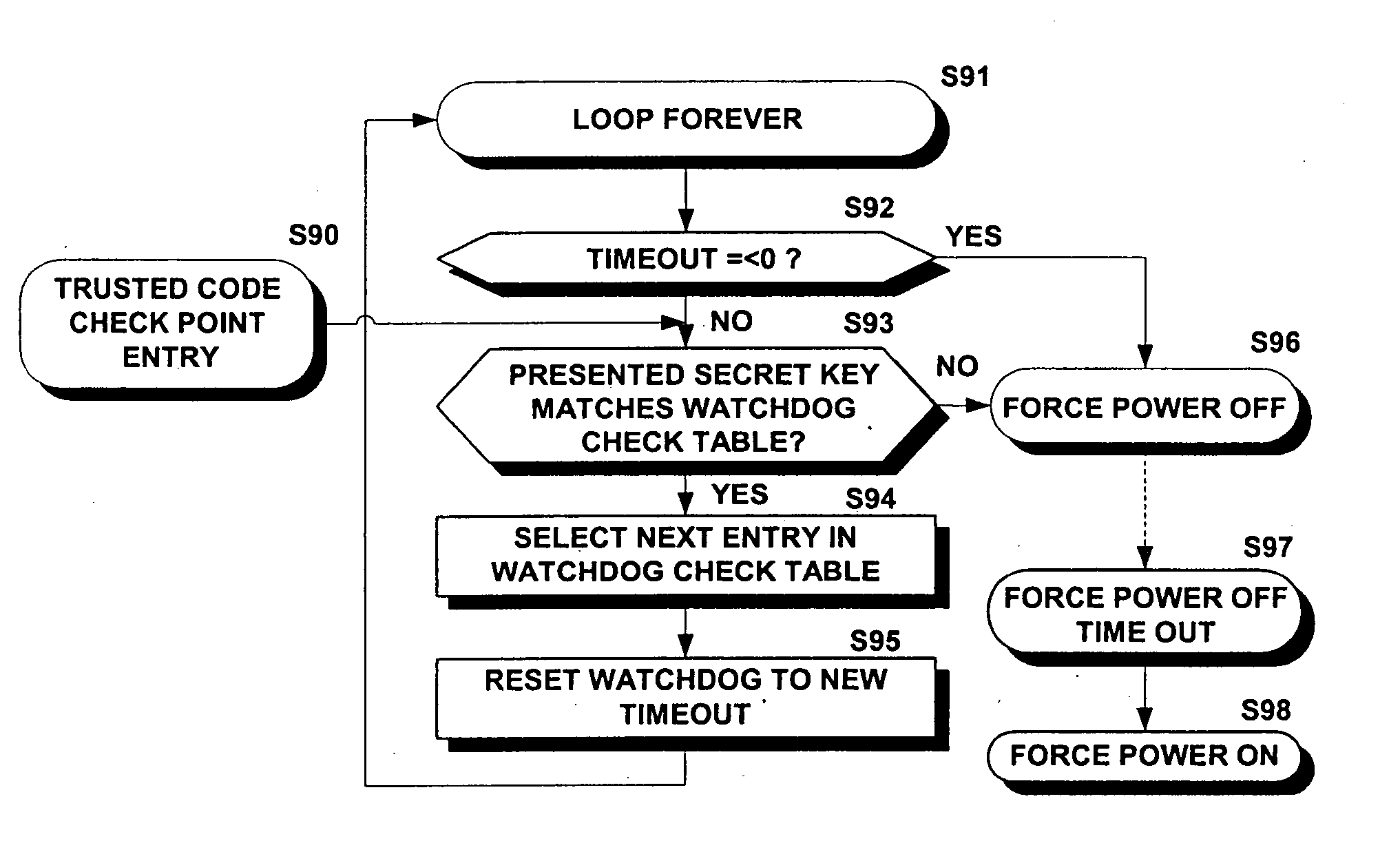
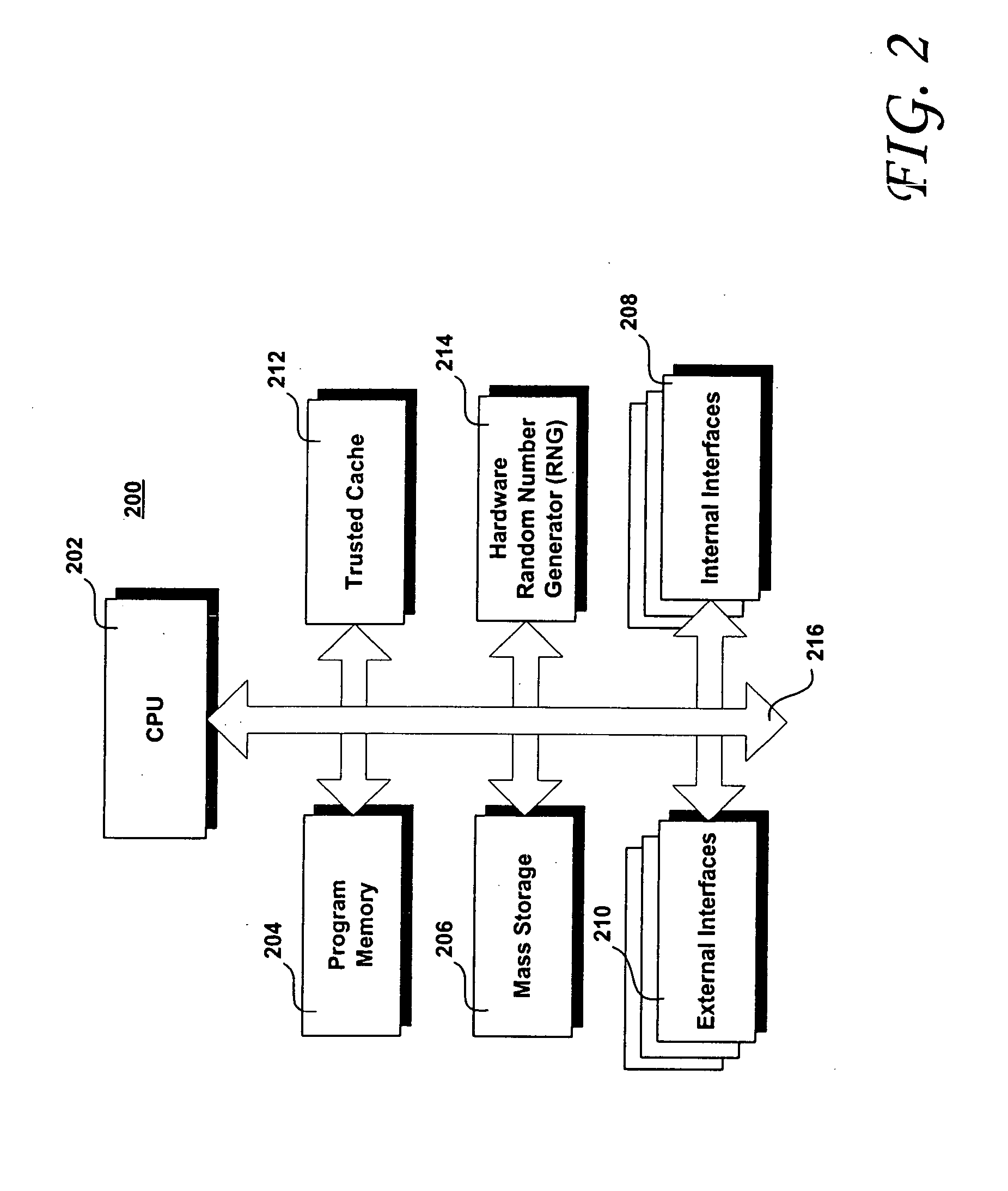
Trusted watchdog method and apparatus for securing program execution
InactiveUS20050097342A1Unauthorized memory use protectionHardware monitoringElectronic controllerPrivate network
An electronic controller for conducting trusted lightweight e-commerce transactions. A trusted transactional cache and the associated transactional protocol allow e-commerce transactions to be committed to a remote server extremely quickly and with little network overhead. The end-to-end transactions are completed is just a few seconds or less. The invention operates equally well on robust private networks as on unpredictable Internet or wireless networks. The transaction is automatically completed following a temporary communication failure with the central site or following a temporary local controller failure. The invention can advantageously be used in embedded Internet products such as fixed or mobile Internet kiosks, transactional terminals, and Internet Appliances.
Owner:CYBERVIEW TECH
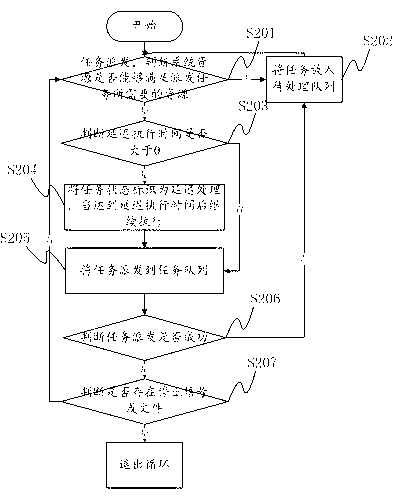
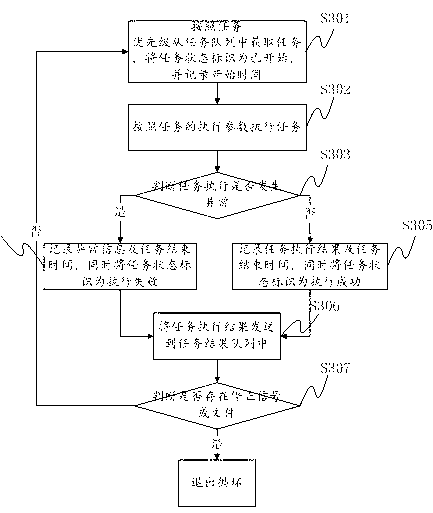
Task flow control method and task flow control system
ActiveCN103294533AMeet needsSolve problems that are not relatedMultiprogramming arrangementsData recordingRecovery procedure
The invention provides a task flow control method and a task flow control system. The task flow control method comprises the following steps: task dispatch, according to a system environment, tasks are dispatched to a task queue or a queue to be processed; the tasks are obtained from the task queue and are carried out by a task execution procedure; a task result recovery procedure reads the task execution result from the task result queue, whether the tasks are dispatched once again is judged according to the specific execution result, or sub-tasks are generated; a task monitoring procedure judges whether the quantity of the current tasks to be processed approximates a preset threshold value via inquiring a queue of the tasks to be processed, and through being combined with a matched data record, the state changes of the specific tasks can be traced. The invention further provides a system suitable for the task flow control method, which comprises a task dispatch module, a task execution module, a task execution result recovery module and a task monitoring module. The task flow control method solves the problems that in the prior art, the joint management of the tasks can not achieved, and the management method is not flexible.
Owner:BEIJING ANTIY NETWORK SAFETY TECH CO LTD
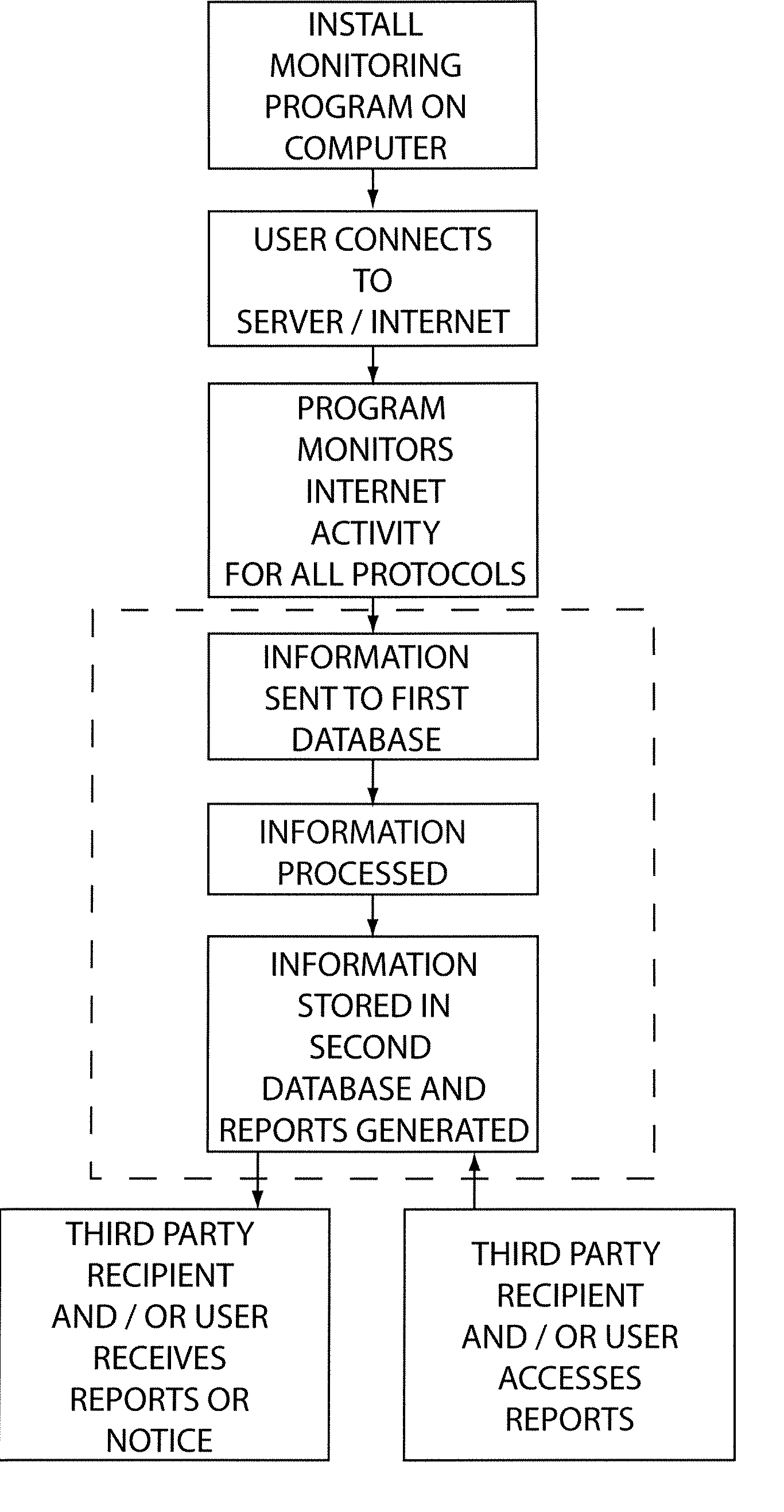
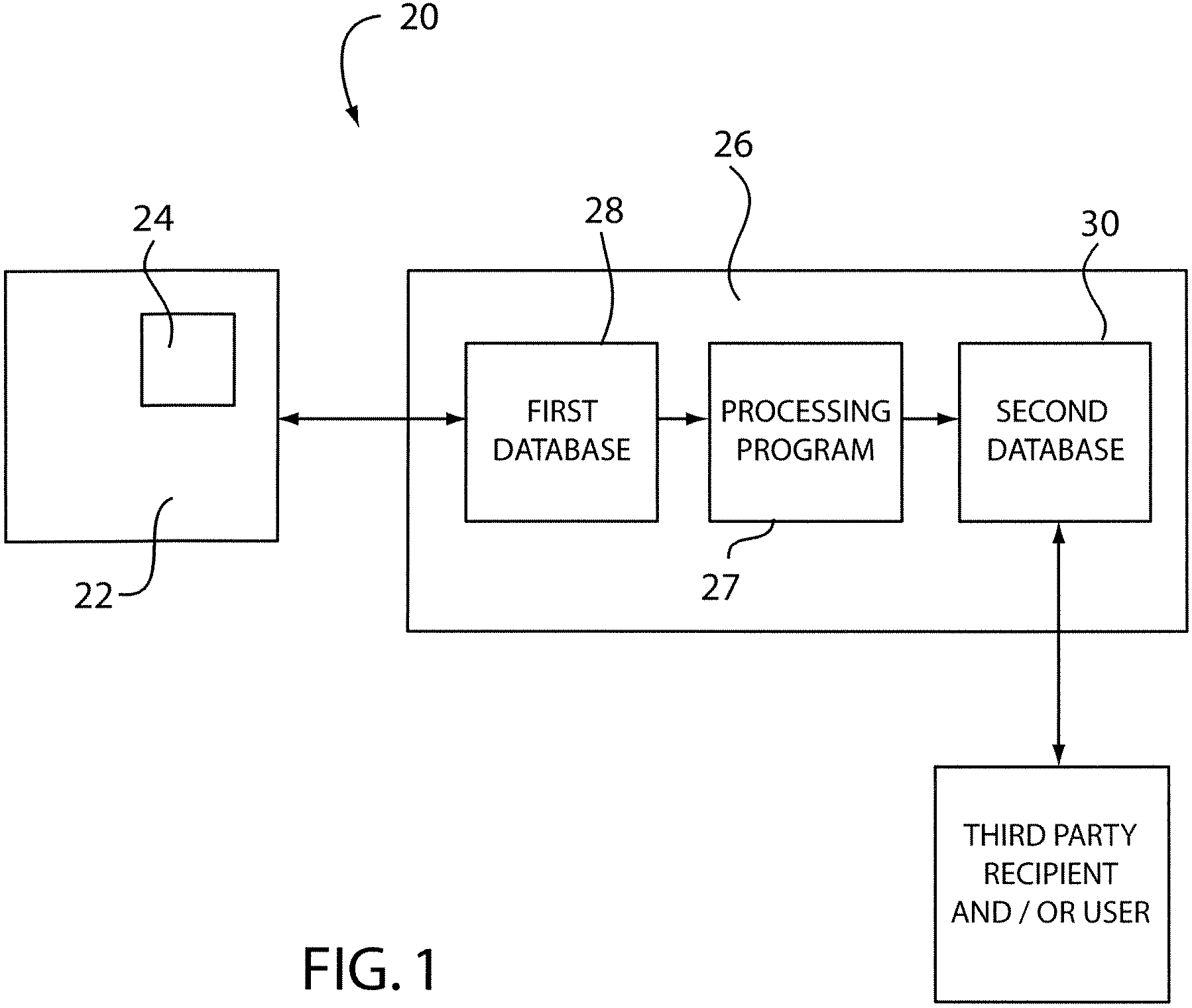
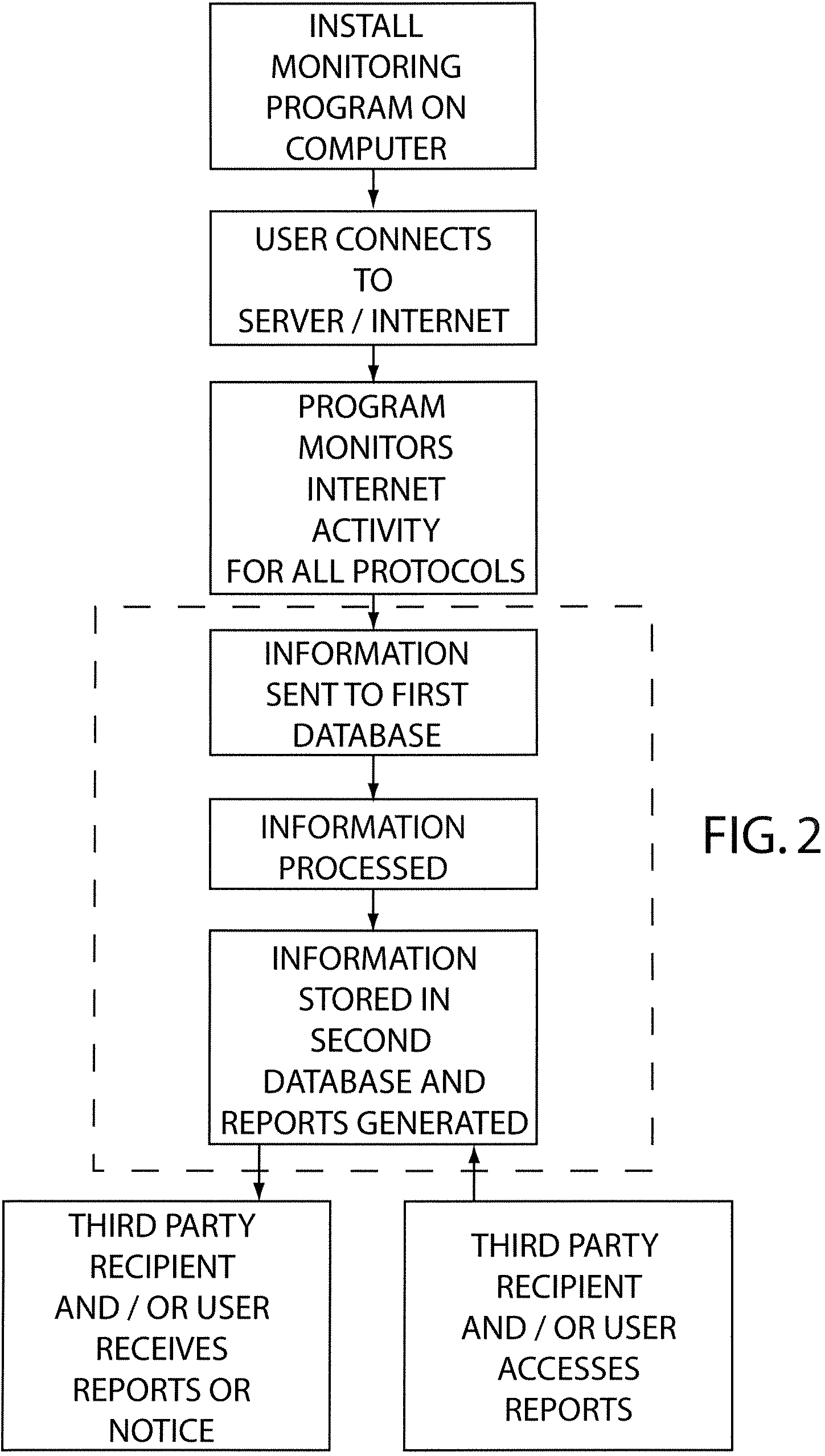
Internet use monitoring system and method
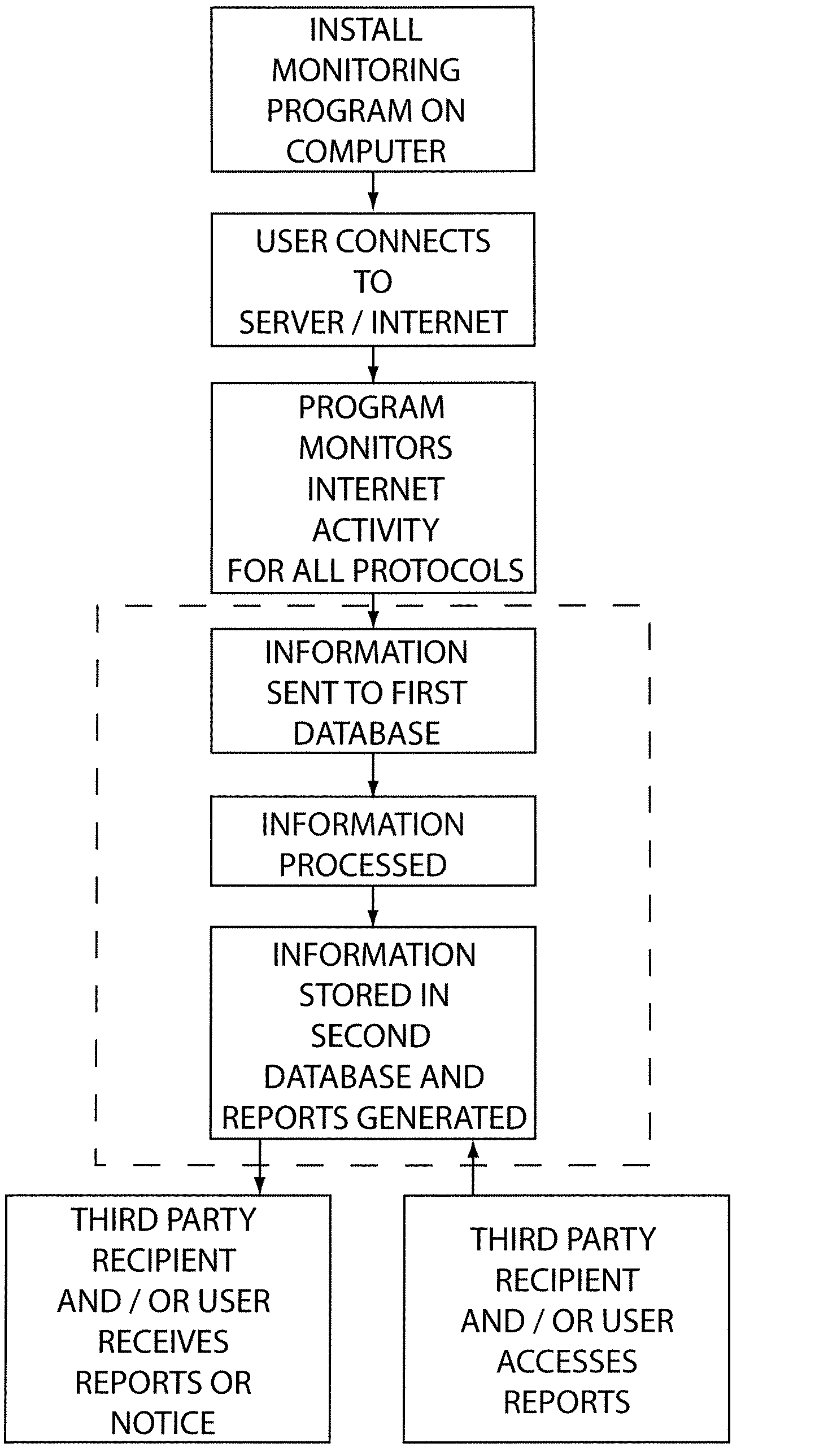
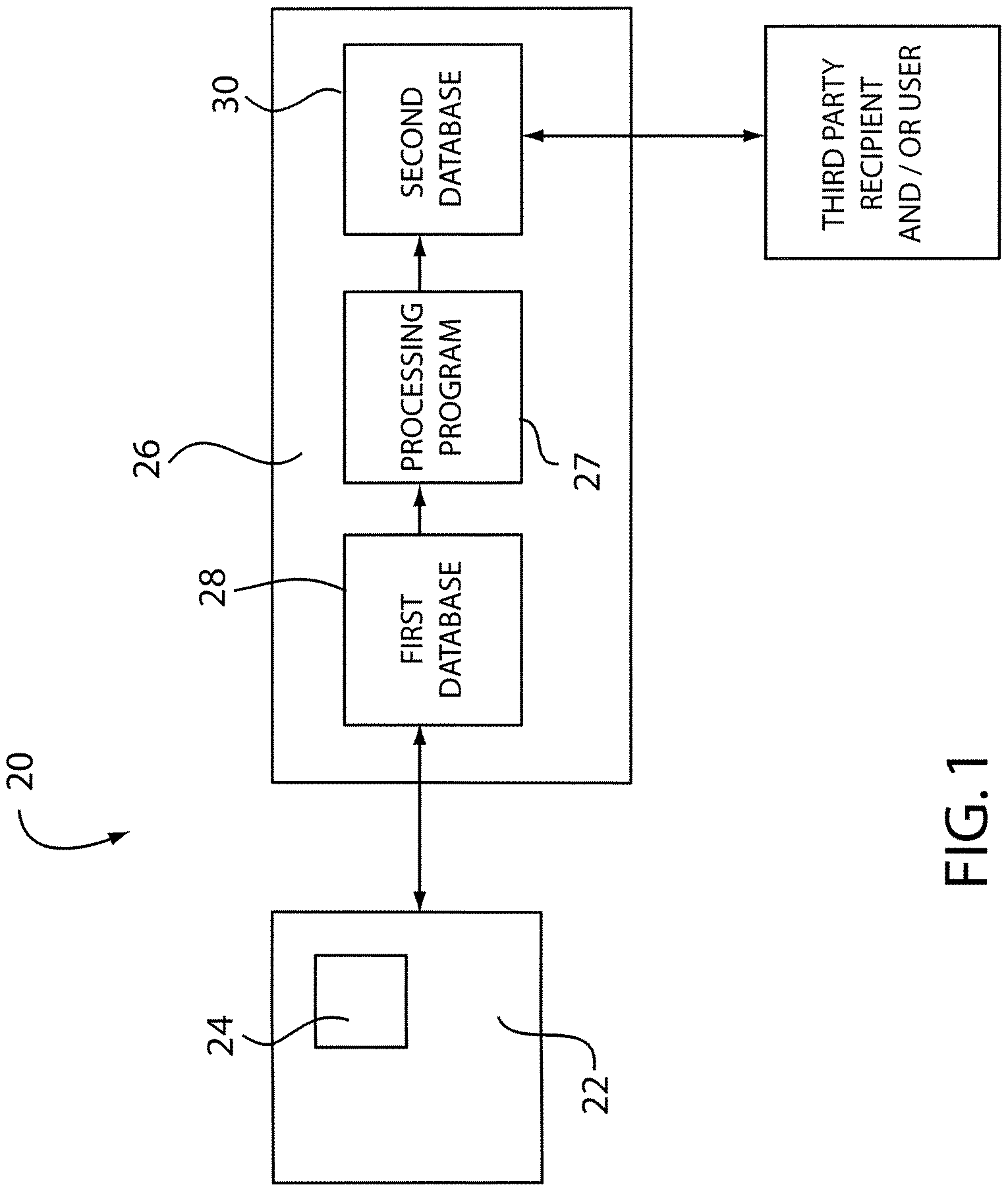
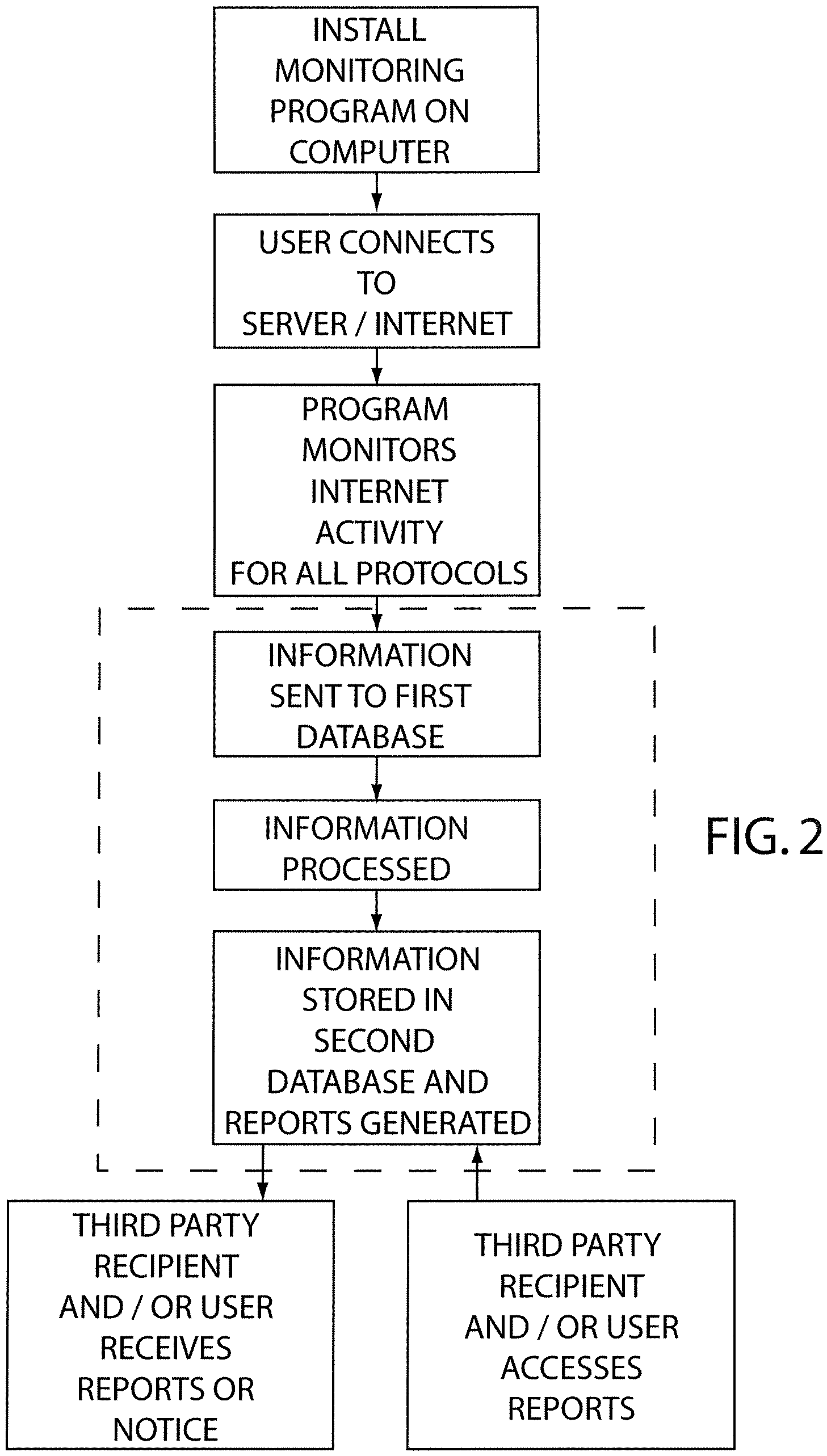
A system for monitoring Internet use of a selected computer user includes a remote server and a computer having a monitoring program voluntarily installed thereon by the user communicatively connected to the remote server. The monitoring program is configured to monitor various Internet access activity of the computer user and record the Internet access activity on the remote server. The Internet access activity includes access of at least one Internet protocol from the group consisting of newsgroups, file sharing programs, file transfer programs, chat rooms, peer to peer chats, and electronic mail activity. A method of using a monitoring system includes the steps of a computer user voluntarily installing a monitoring program on a selected computer, recording the Internet access activity, and providing the recorded information to a third party recipient. A report may be provided that includes a variety of information and may include a plurality of portions.
Owner:COVENANT EYES
Communication system
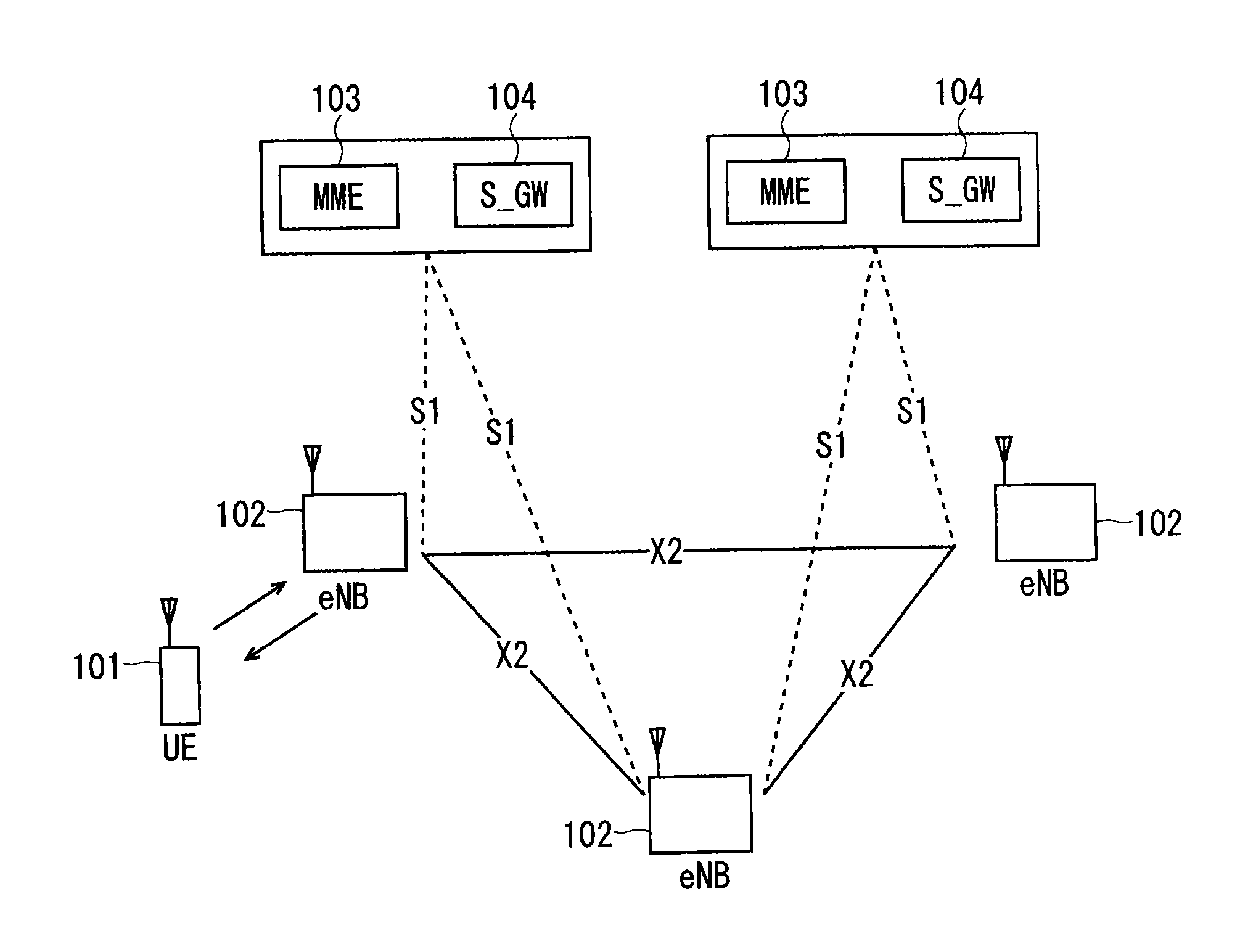
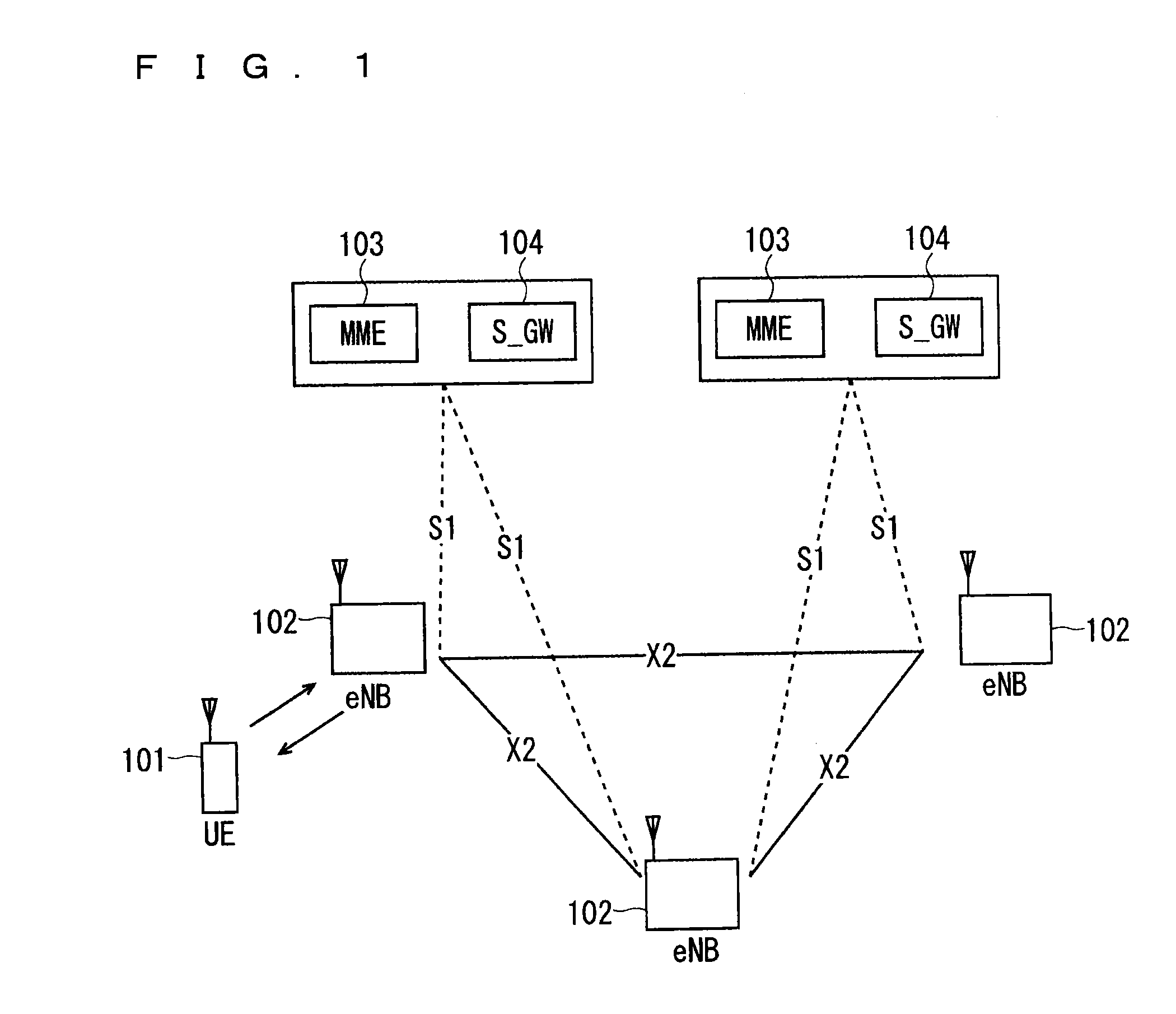
ActiveUS20150092554A1Reduce processing loadReduce power consumptionError preventionFrequency-division multiplex detailsCommunications systemMonitoring procedure
In a communication system, an eNB and a UE transmit and receive a UE monitoring message for confirming the state of the UE in a predetermined UE monitoring period. For example, in UE monitoring periods, a UE monitoring procedure is performed, so that the UE transmits the UE monitoring message to the eNB. Upon receipt of the UE monitoring message, the eNB transmits delivery confirmation information to the UE. The UE monitoring period is set as, for example, a period shorter than a TAU period. This allows the UE monitoring process to confirm the state of the UE even if the TAU period is lengthened. The eNB may transmit the UE monitoring message to the UE.
Owner:MITSUBISHI ELECTRIC CORP
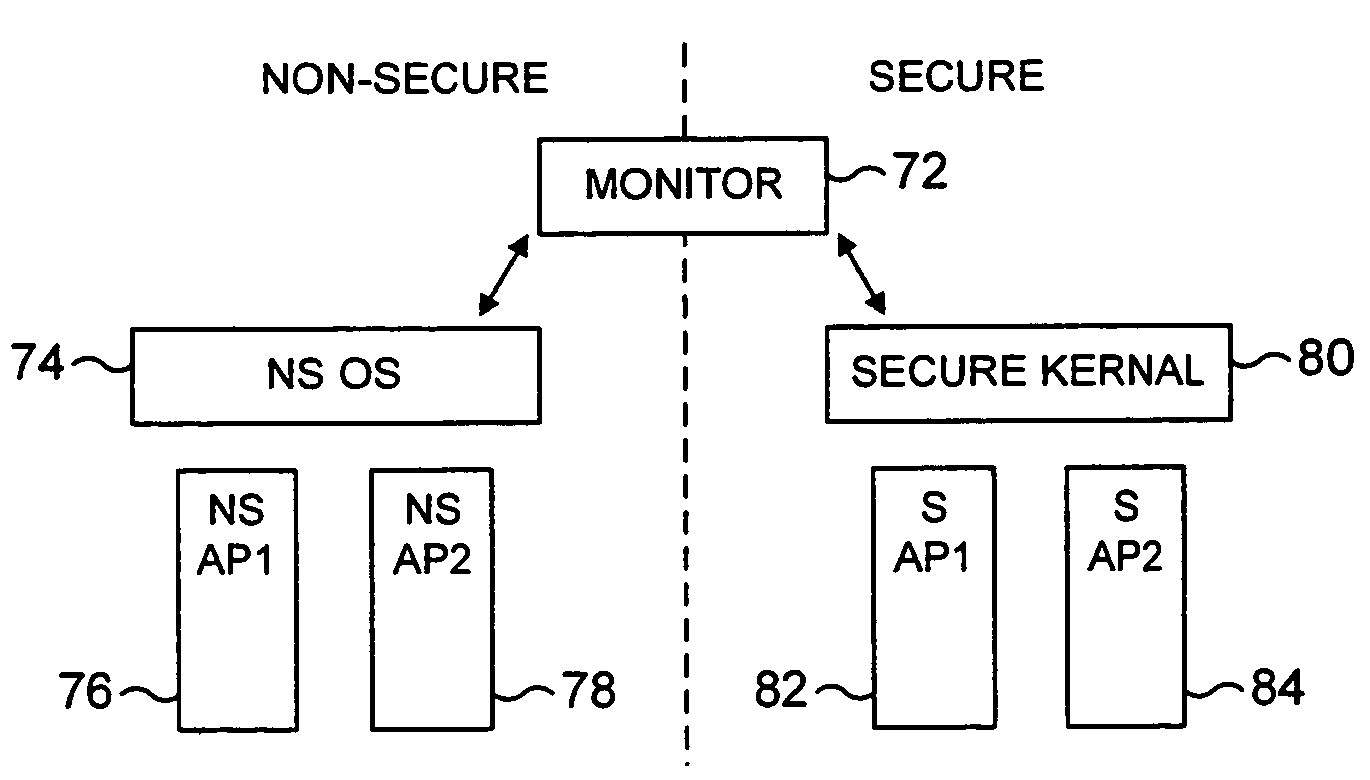
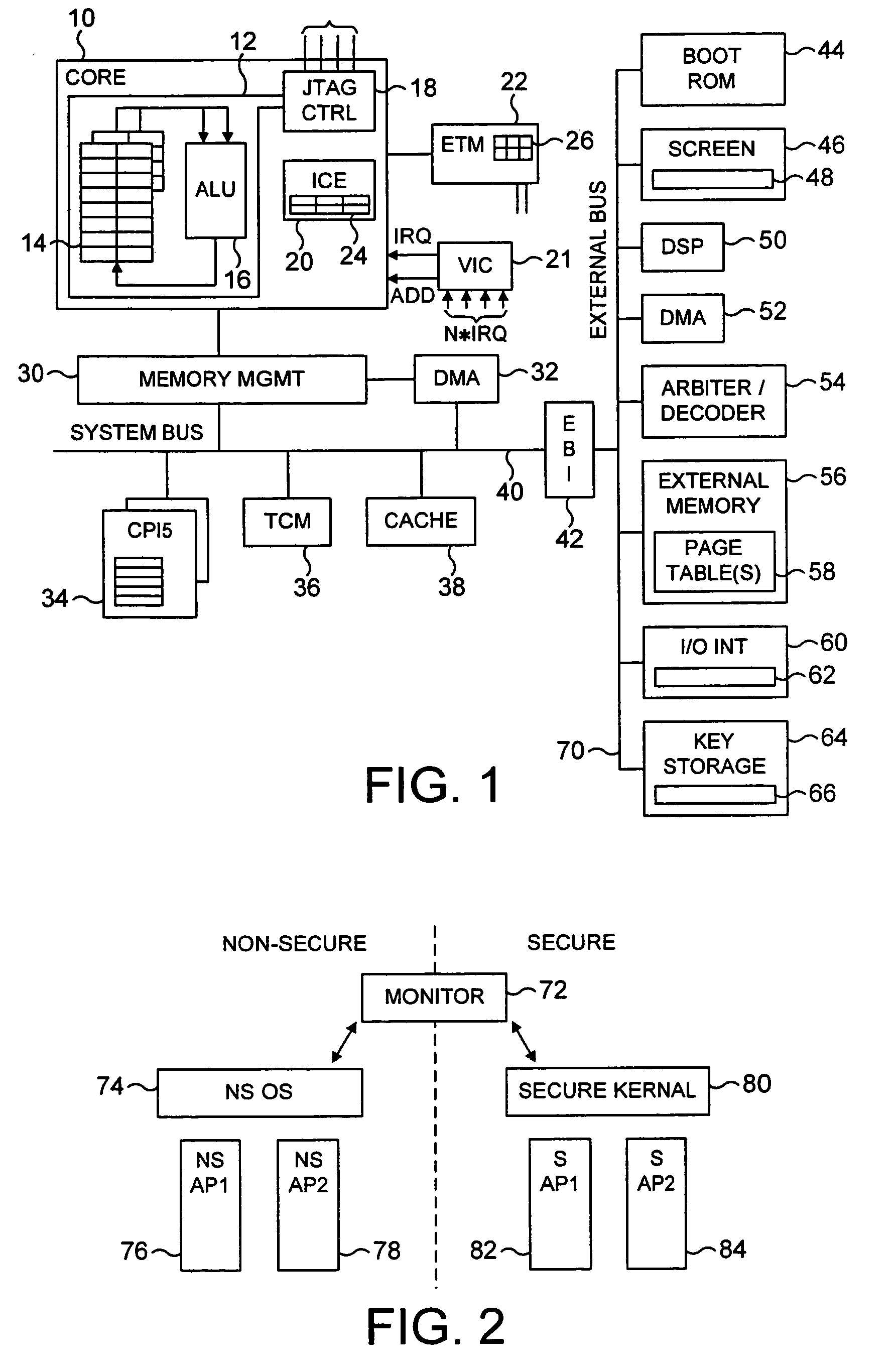
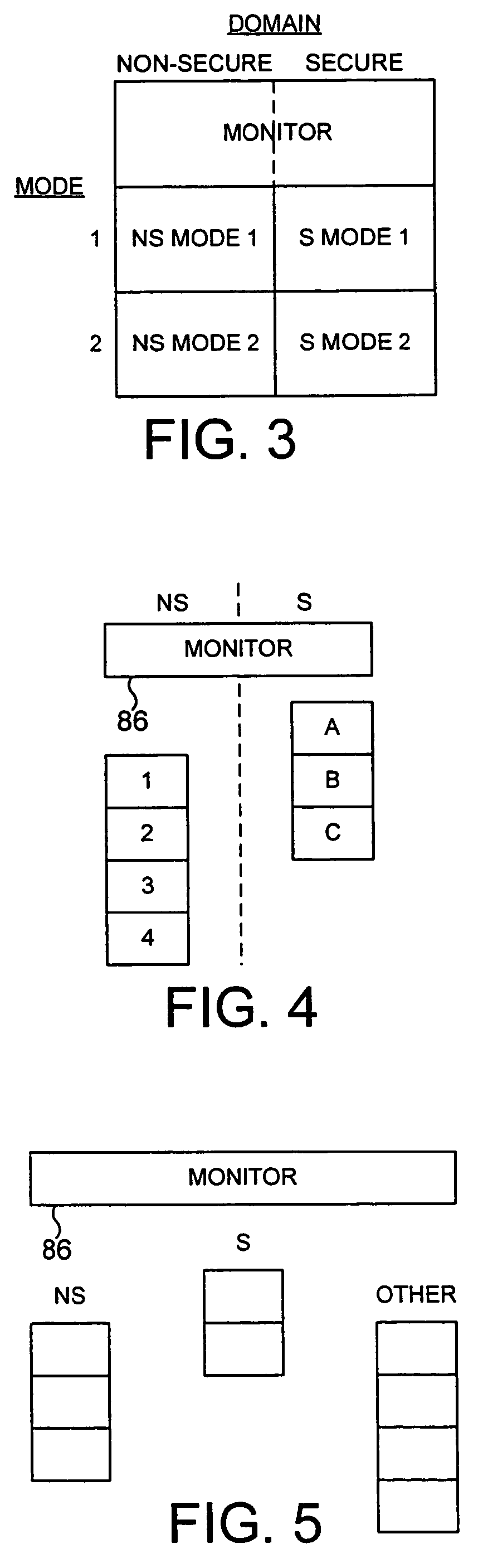
Switching between secure and non-secure processing modes
ActiveUS7849310B2Reduce riskFacilitates proper structuringDigital data processing detailsAnalogue secracy/subscription systemsData processing systemMonitor mode
A data processing system including a processor operable in a plurality of modes and in either a secure domain or a non-secure domain. The system includes at least one secure mode being a mode in the secure domain, at least one non-secure mode being a mode in the non-secure domain, and a monitor mode. When the processor is executing a program in a secure mode the program has access to secure data which is not accessible when the processor is operating in a non-secure mode. Switching between the secure and non-secure modes takes place via the monitor mode and the processor is operable at least partially in the monitor mode to execute a monitor program managing switching between the secure and non-secure modes.
Owner:ARM LTD
Method and apparatus for preventing the interception of data being transmitted to a web site by a monitoring program
InactiveUS7394900B1Digital data processing detailsAnalogue secracy/subscription systemsWeb siteOperation mode
The present invention relates to a method and apparatus for preventing the use of data transmitted by a computer to a web site by a program operating on the computer. Initially, a first association between a set of labels and a first set of codes is created. The set of labels contains information to be displayed on the computer, while each code in the first set of codes is associated with a particular label. An encryption key is then linked with the first association. The set of labels, the first set of codes, and the first encryption key is then sent to the computer. Some time later, codes from the first set of codes and the first encryption key are received back from the computer. The codes returned from the computer are then matched to labels from the set of labels using the first encryption key. Afterwards, subsequent associations between the set of labels and other sets of codes are created. These associations are different than the association between the set of labels and the first set of codes. Additional encryption keys are also created to identify the subsequent associations. The present invention also relates to a method and a computer program product for determine the meaning of a code that describes a user's selection of an item on a web page. In this mode of operation, the information that defines the web page is first analyzed. Then, an association between the codes and labels presented on the web page is created. Afterwards, the code describing an item selected by a user is captured. Finally, the label associated with the code is identified by referencing the association between the codes and labels.
Owner:SOUTHWEST AIRLINES
Method and apparatus to autonomically profile applications
InactiveUS20050071516A1Software testing/debuggingInput/output processes for data processingData processing systemAnalysis data
A method, apparatus, and computer instructions for profiling an application in data processing system. The execution of an instruction associated with an indicator is detected. The instruction is located in a routine. A determination is made as to whether the instruction has been executed more than a threshold value. If the instruction has been executed more than the threshold value, an interrupt is generated to pass control to a monitoring program in which the monitoring program identifies information regarding a caller of a routine.
Owner:IBM CORP
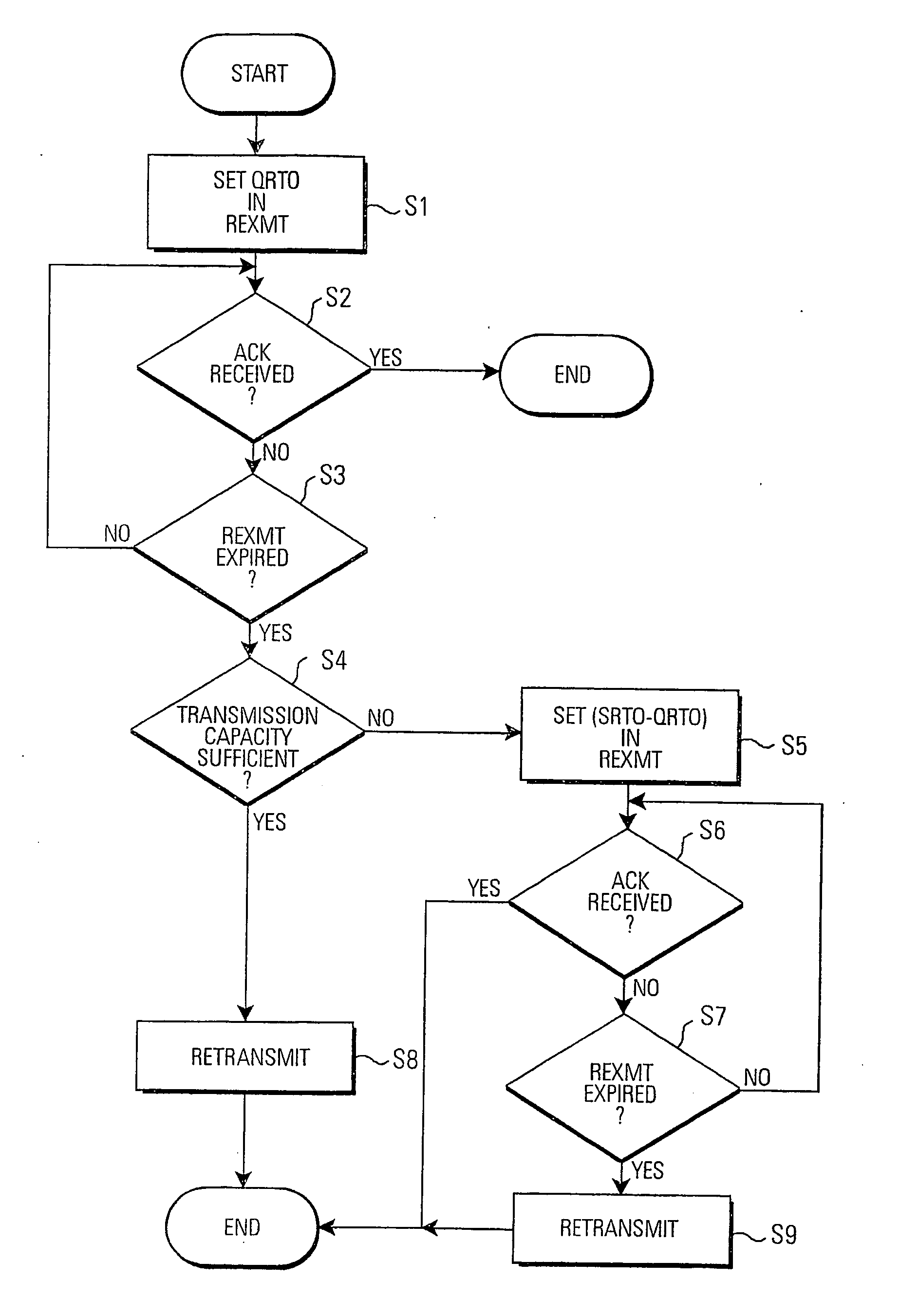
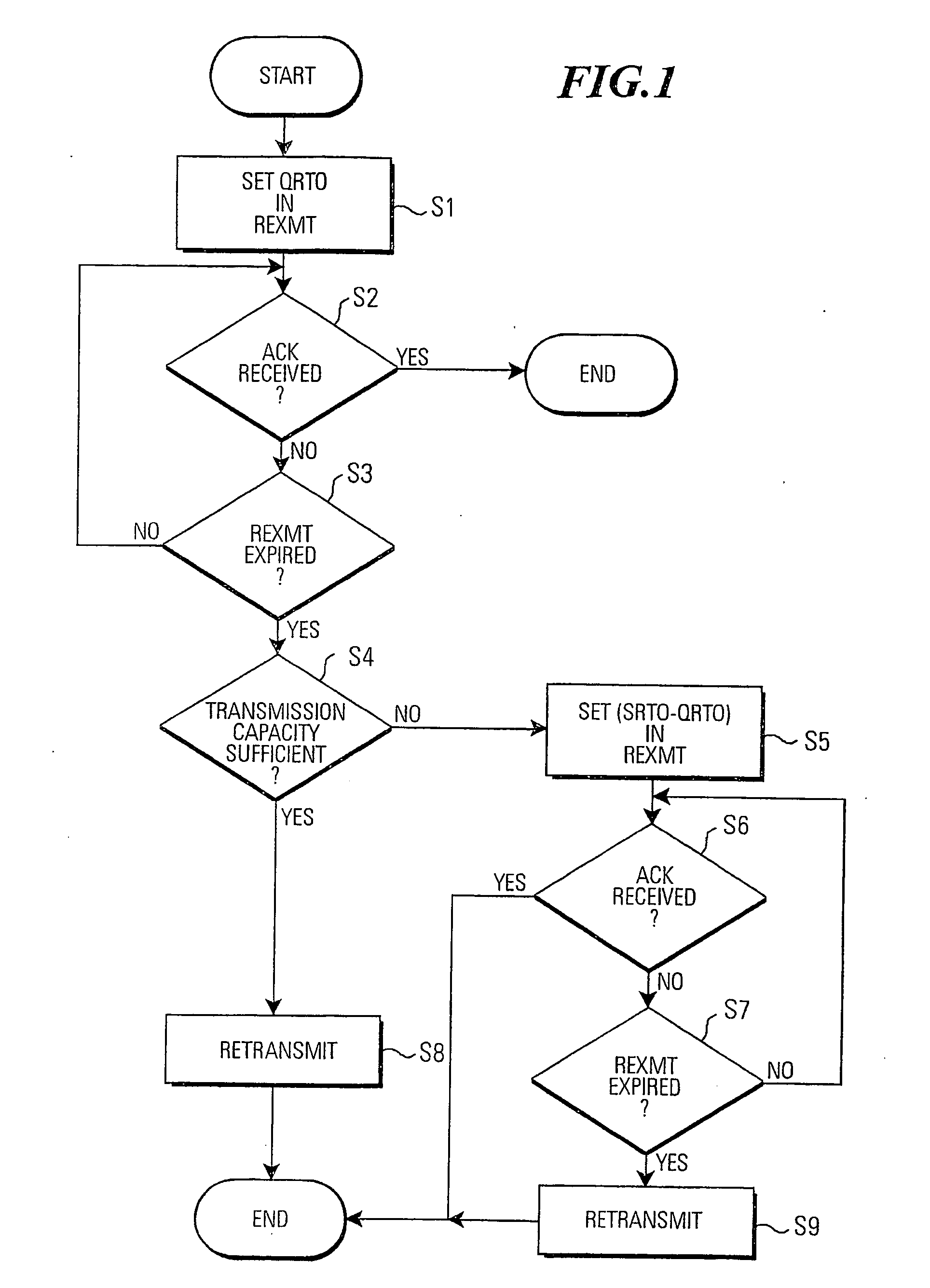
Data unit sender and method of controlling the same
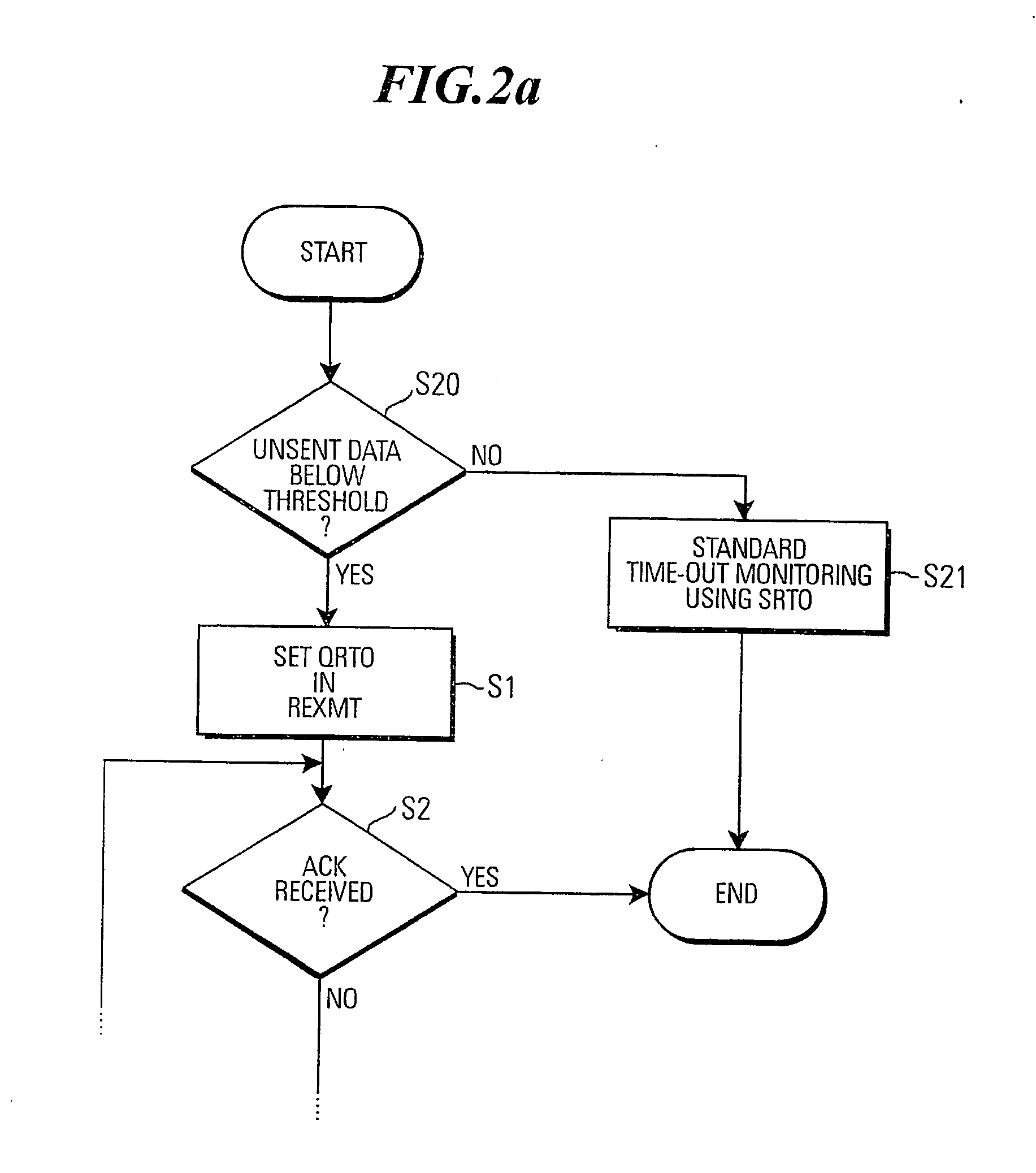
ActiveUS20060156164A1Faster and more aggressive time-outImprove data throughputError prevention/detection by using return channelTransmission systemsCapacity valueControl data
A data unit sender and method of controlling a data unit sender are presented, in which a time-out monitoring procedure implements a first, longer time-out period (SRTO), and a second, shorter time-out period (QRTO), where a retransmission is executed after the shorter time-out period if the available transmission capacity value for unsent data is greater or equal to the size of a designated data unit that is to be retransmitted as a result of said time-out monitoring procedure.
Owner:TELEFON AB LM ERICSSON (PUBL)
Network node scanning detection method and system for LAN environment
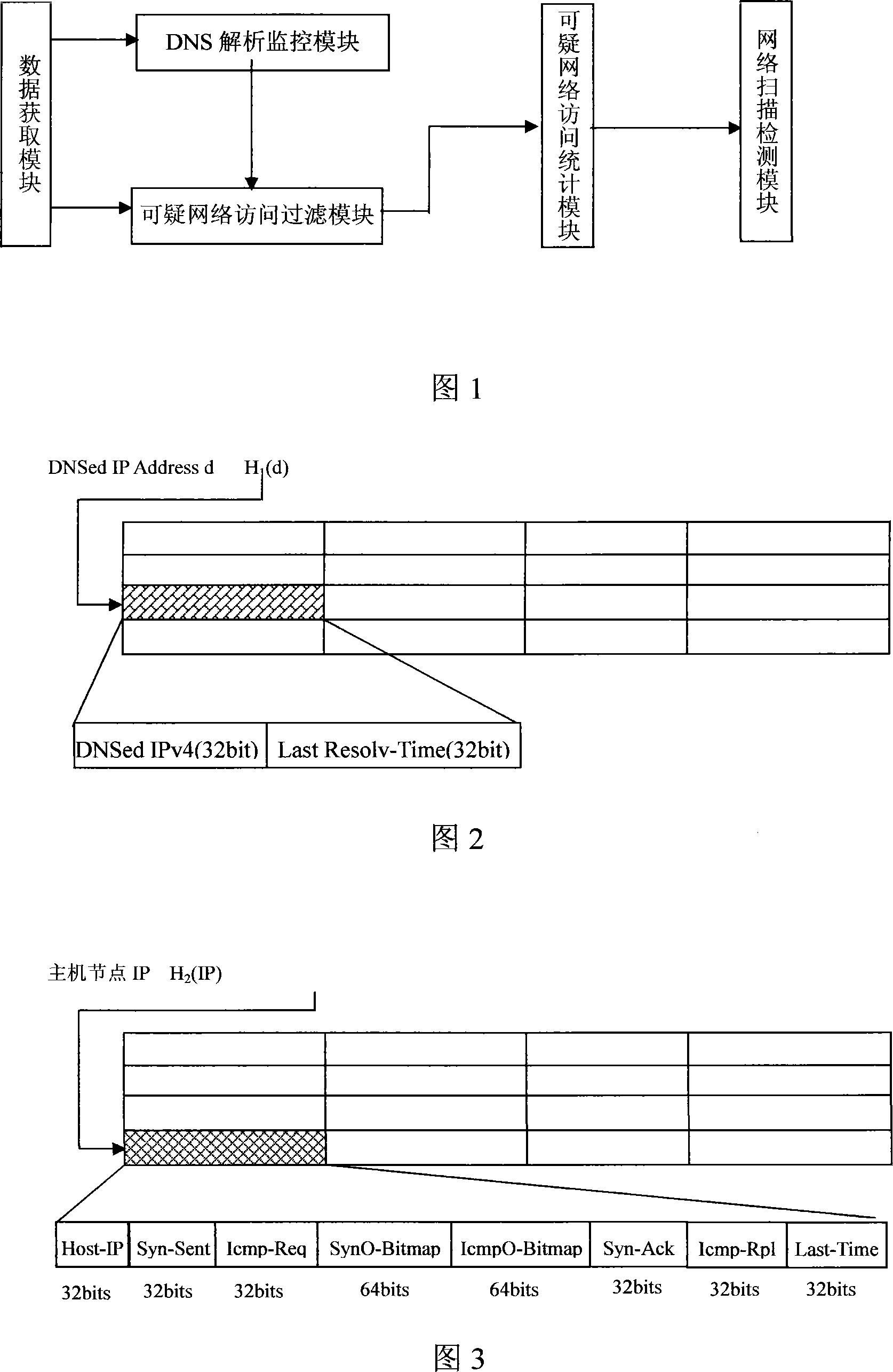
The invention relates to a network node scanning detection method and system applicable to both the local network environment and the high-speed local network environment, comprising a network terminal and a local network. The invention is composed of a data gathering procedure, a DNS analysis and monitoring procedure, a suspected network visiting and filtering procedure, a suspected network visiting statistics procedure and a network scanning and detecting procedure. The invention is characterized in that all the network visiting access requests sent by the nodes of each mainframe are correlated with the IP address lists analyzed by the DNS recently in the local network and the network visiting access requests related to the normal network visiting flow rate are filtered to the maximum extent. By adopting the suspected network visiting access request response rate and the target IP address divergence of the suspected network visiting access request as the network scanning detection index, the invention has the advantages of the application to the network safety products of monitoring the scanning behavior of the nodes of each mainframe in the local network by the network node scanning detection system in the local network environment.
Owner:BEIJING VENUS INFORMATION TECH
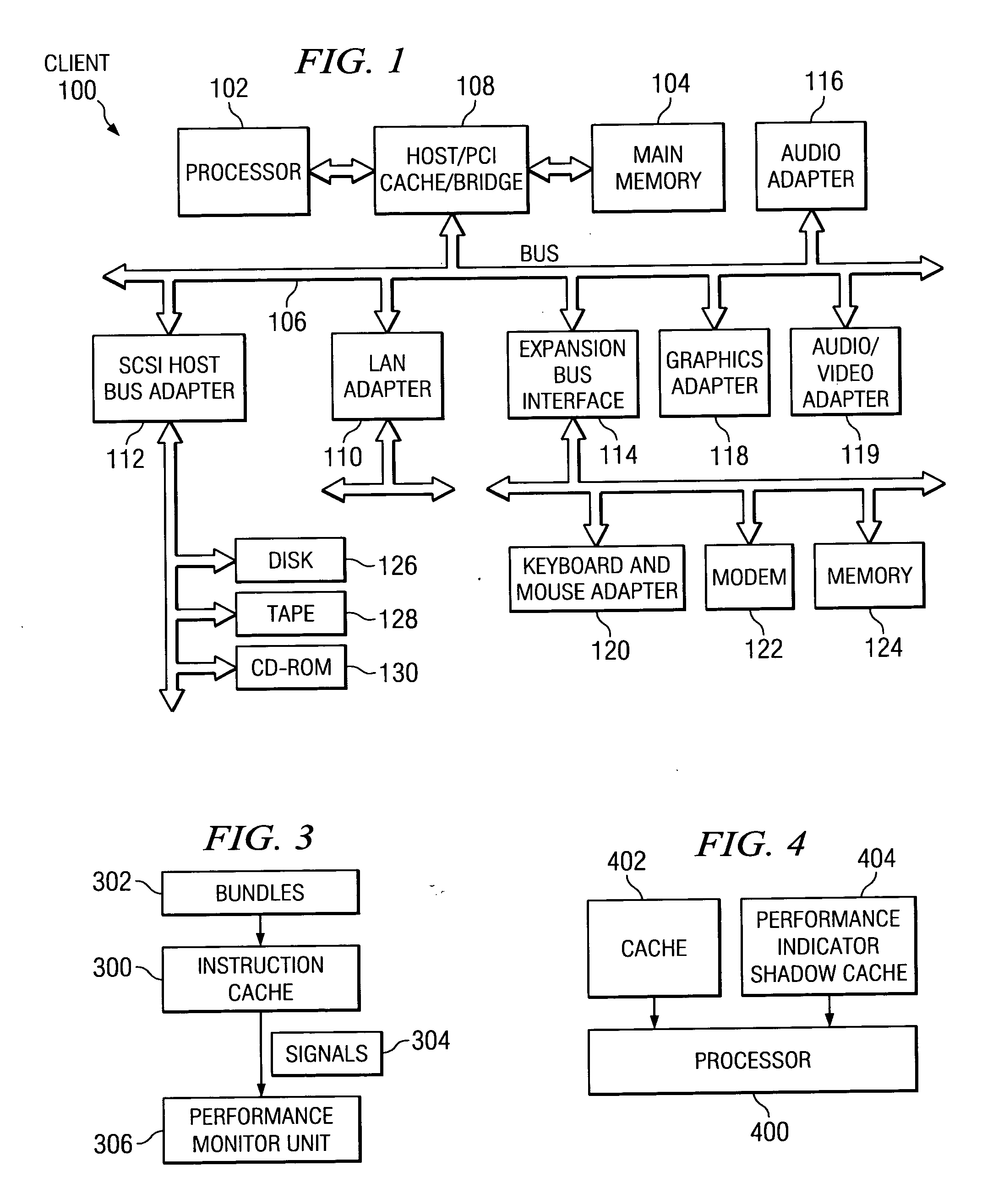
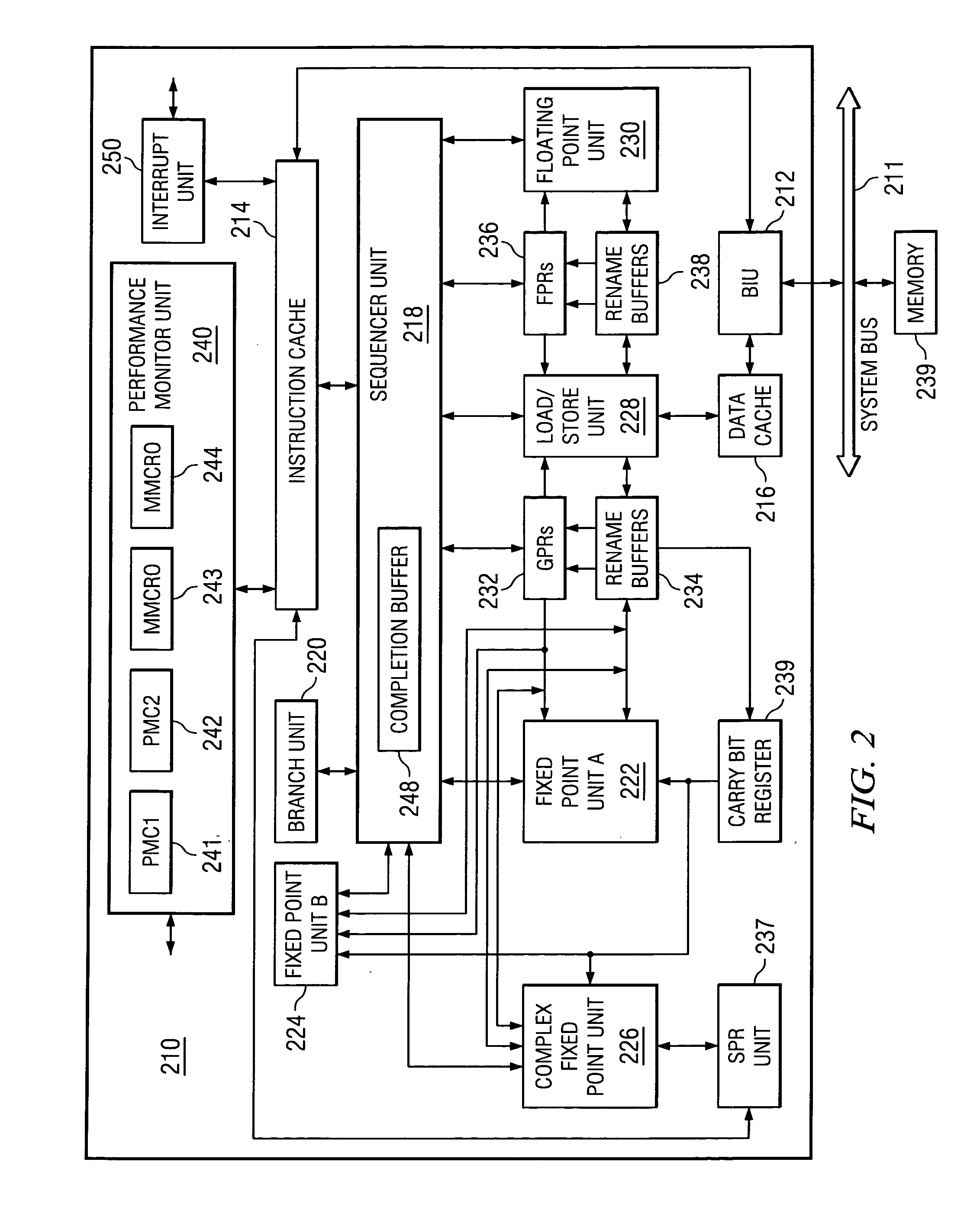
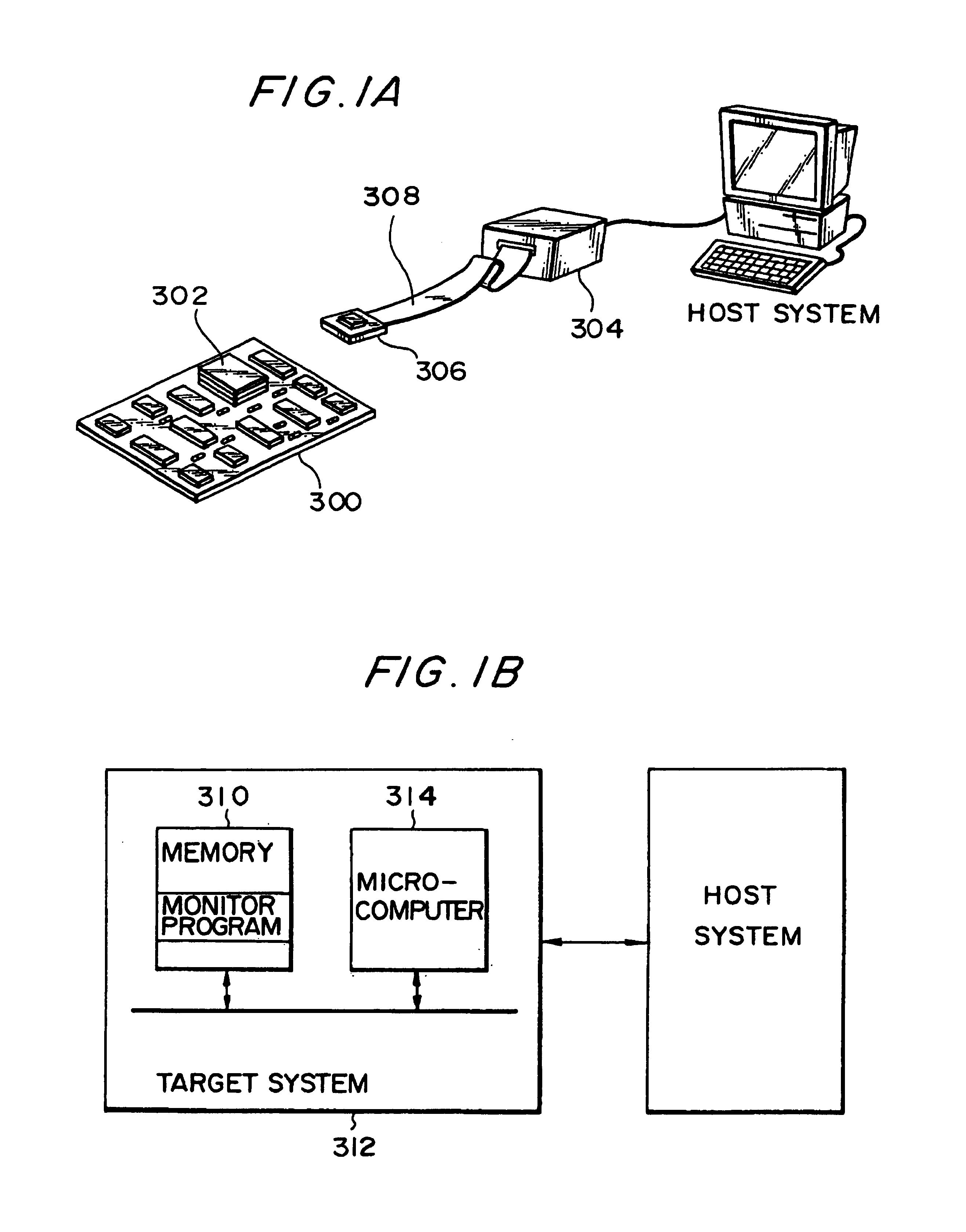
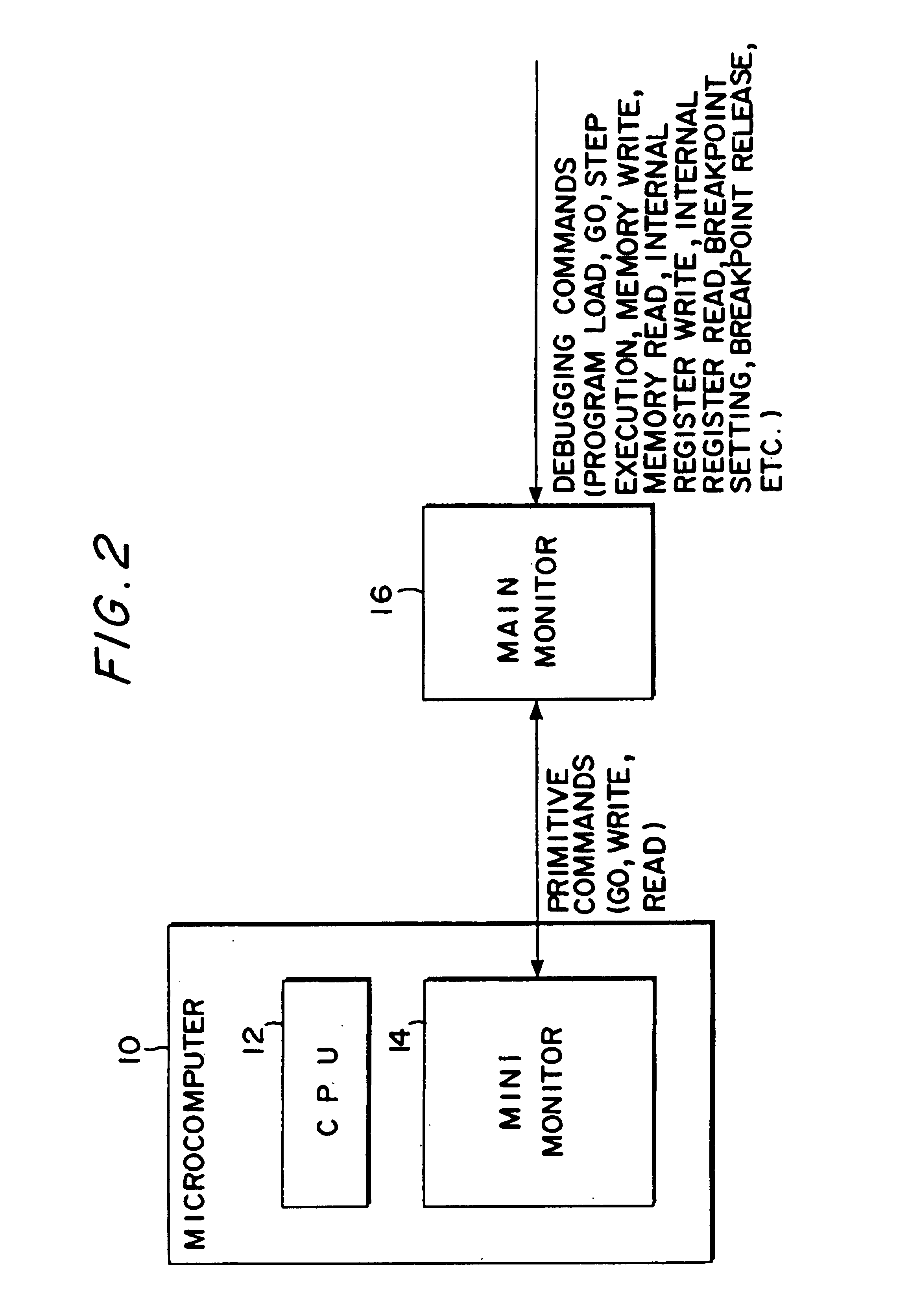
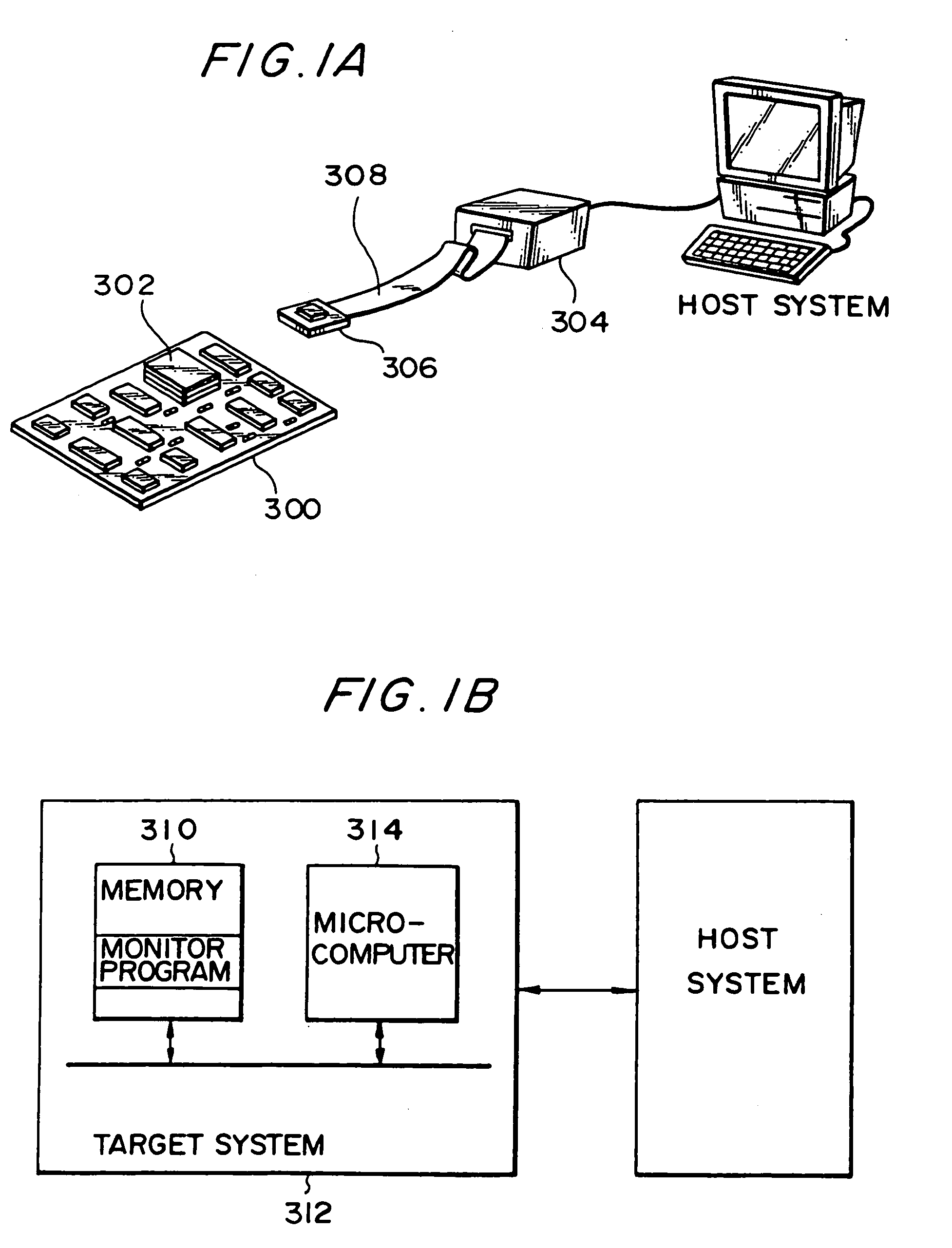
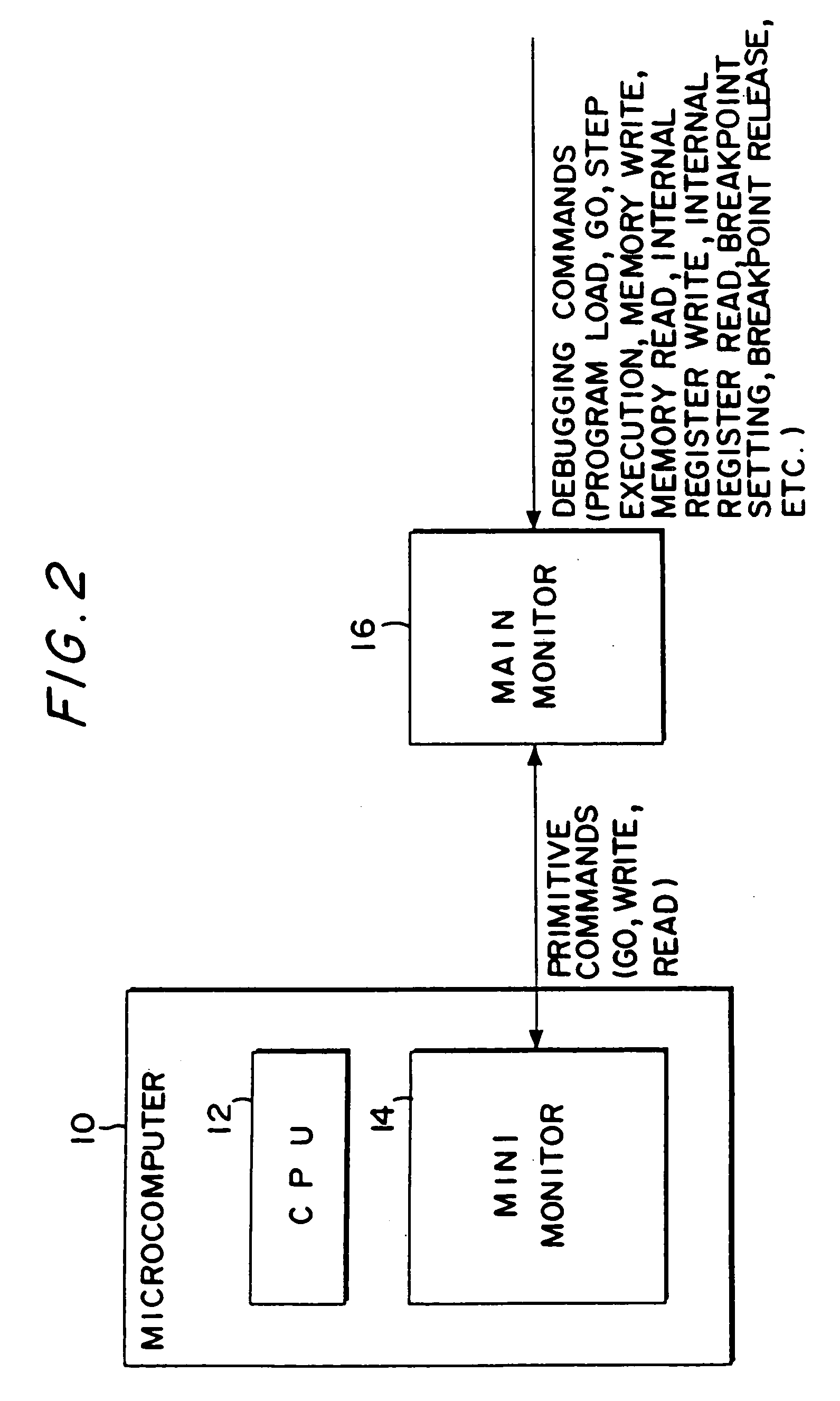
Microcomputer, electronic equipment and debugging system
InactiveUS7100086B1Small sizeIncrease in memory areaError preventionDetecting faulty computer hardwareMemory mapFixed length
An object is to provide a microcomputer, electronic instrument and debugging system which can realize an on-chip debugging function through a reduced size of instruction code or a reduced circuit scale. A main monitor section (16) converts a debugging command into a primitive command. A mini monitor section (14) transfers data to and from the main monitor section (16) to execute a primitive command determined based on the receive data. The primitive commands include go, write and read commands. A control register having its address allocated on a memory map in the debugging mode is provided together with a mini monitor RAM. The mini monitor section (14) serving as a slave is connected to the main monitor section (16) serving as a master through a half-duplex bidirectional communication line so that transfer data can be fixed-length. The receive data includes a command identifying data. A mini monitor program has been stored in a ROM. The mini monitor section (14) and main monitor section (16) use a clock in common to generate a sampling clock while transferring data in the start-stop synchronization.
Owner:SEIKO EPSON CORP
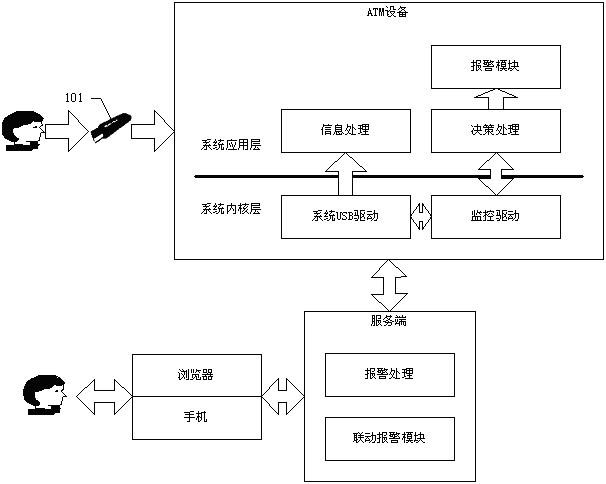
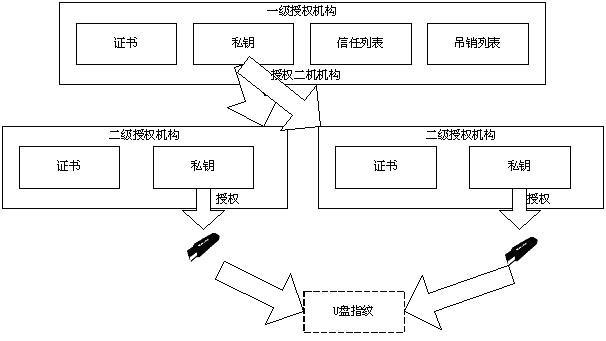
USB (Universal Serial Bus) flash disk authorization method and system based on ATM (Automatic Teller Machine) equipment
ActiveCN102629403AComprehensive security protectionAvoid accessComplete banking machinesDigital data authenticationInformation securityUSB
The invention discloses a USB (Universal Serial Bus) flash disk authorization method and a USB flash disk authorization system based on ATM (Automatic Teller Machine) equipment. The method comprises the following steps: acquiring USB flash disk hardware information in advance, specifying target equipment information capable of being visited and authorized valid information and generating USB flash disk fingerprint information; signing on the USB flash disk fingerprint information by adopting a USB flash disk signature private key, transmitting signed USB flash disk fingerprint files into a specified monitoring procedure of the ATM equipment; and after a USB flash disk is inserted into the ATM equipment, monitoring a driver program through the ATM equipment to acquire the current hardware information inserted into the USB flash disk and the USB flash disk fingerprint information, validating whether the inserted USB flash disk is legal by using a USB flash disk signature public key, allowing the normal operation if the inserted USB flash disk is legal, forbidding the current operation of the USB flash disk if the inserted USB flash disk is not legal and simultaneously alarming to a server. The USB flash disk authorization method and the USB flash disk authorization system have the beneficial effects that the authorization to the USB flash disk can be quickly realized, the ATM equipment safely and accurately identify the inserted USB flash disk according to the authorized information to prevent the illegal operation of the USB flash disk, so that the safety is improved.
Owner:SHENZHEN ZIJIN FULCRUM TECH +3
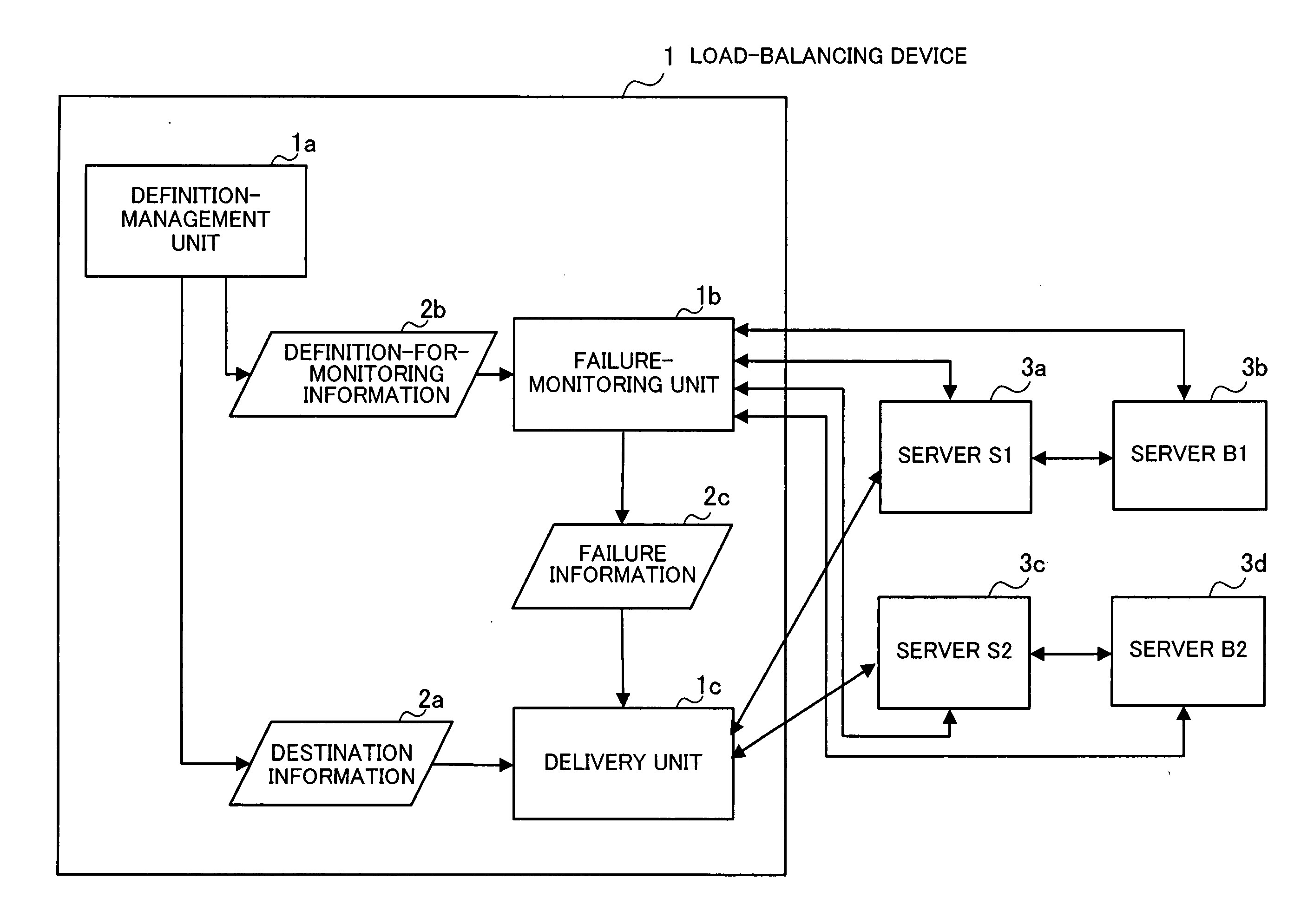
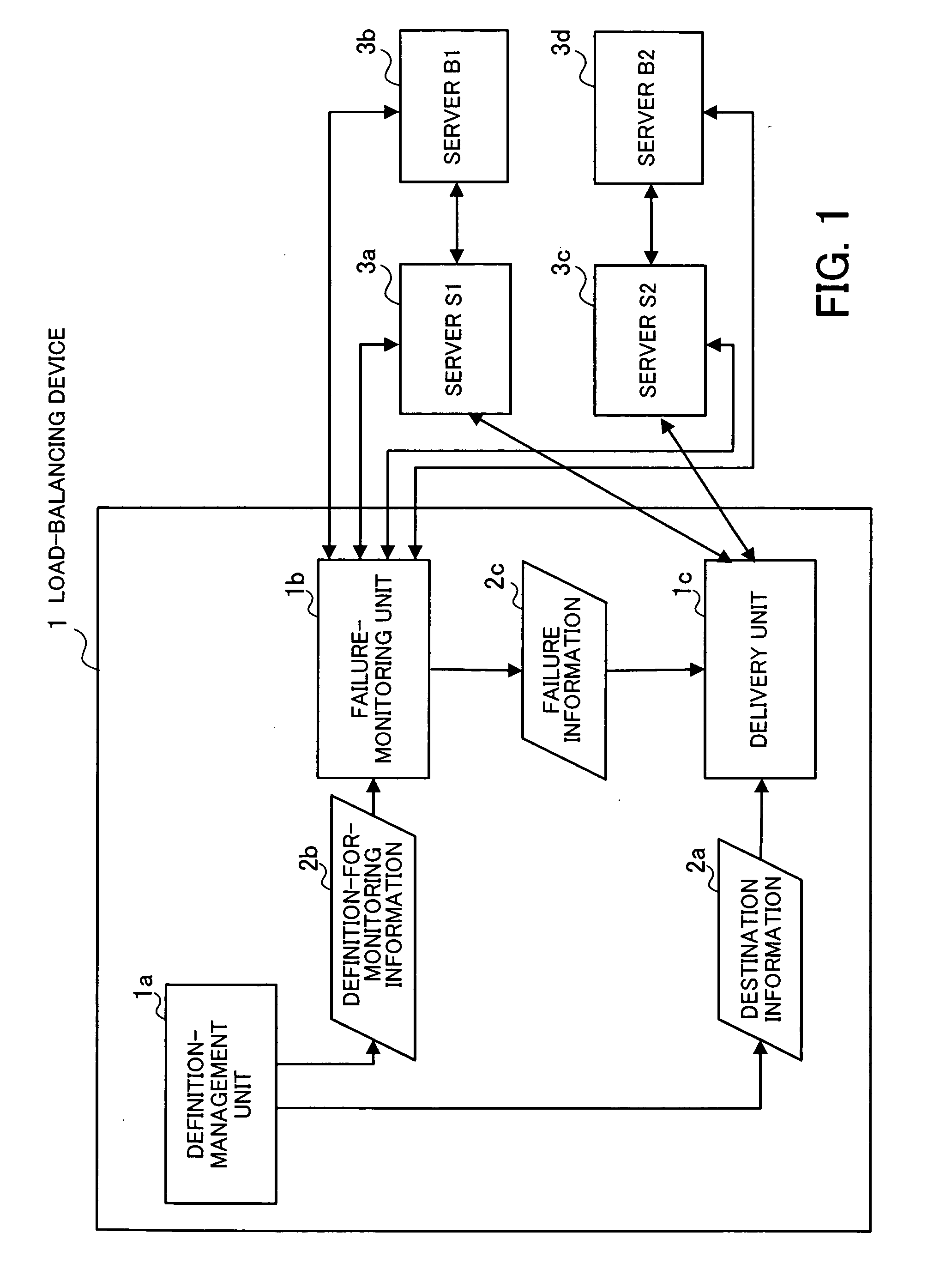
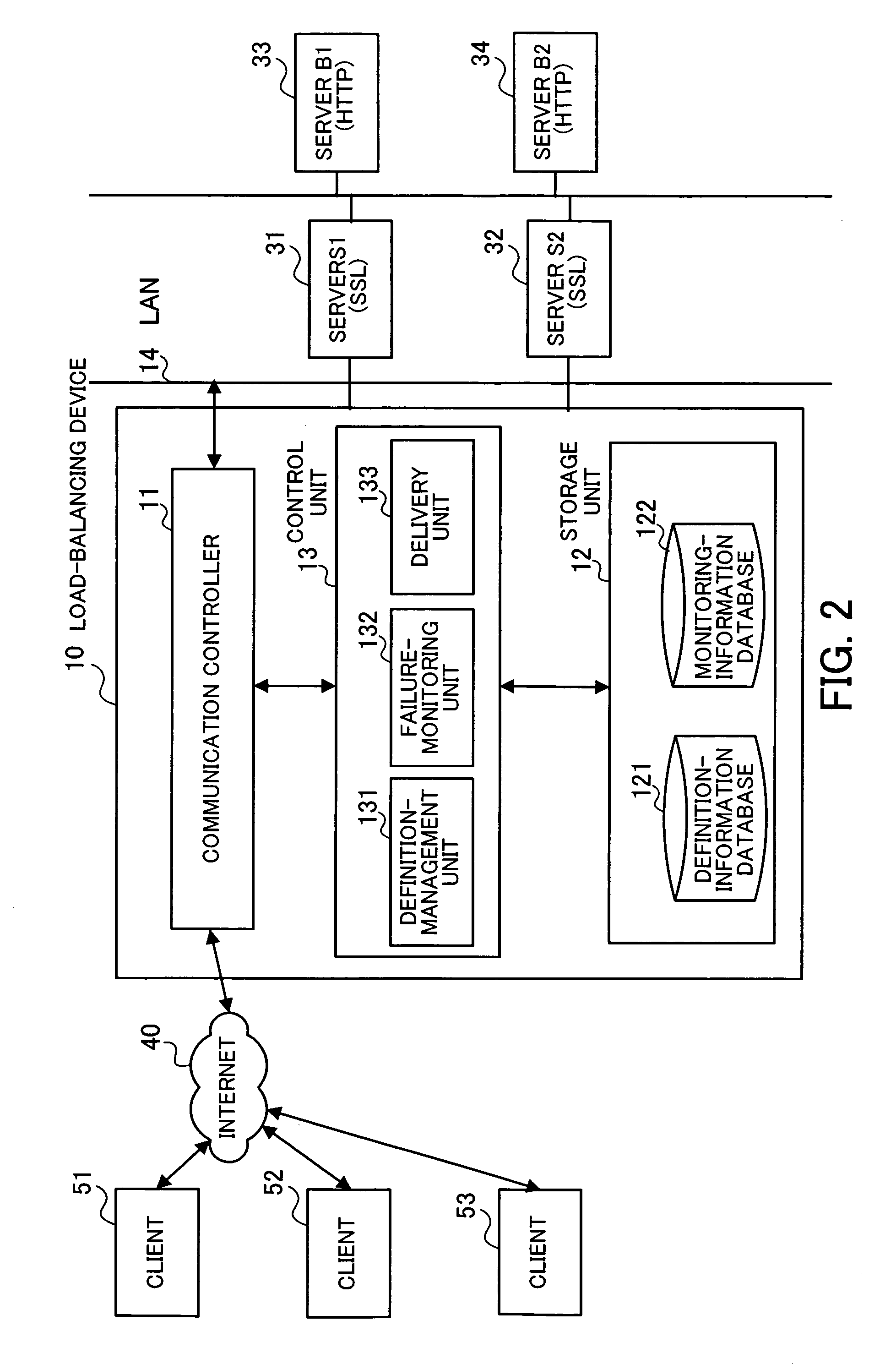
Failure-monitoring program and load-balancing device
InactiveUS20060221815A1Load balancingError preventionResource allocationMonitoring procedureReal-time computing
In a method for monitoring servers including destination servers for failure: definition-for-monitoring information including servers to be monitored, a monitoring procedure including a definition of a monitoring packet used in diagnosis of the servers to be monitored, and a criterion for determining normality of the servers to be monitored is generated and stored for each destination server; the monitoring packet is transmitted to each server to be monitored, in accordance with the definition-for-monitoring information; and it is determined that the server to be monitored is faulty and delivery of request packets to one of the destination servers corresponding to the server to be monitored is not allowed, when no response is returned from the server to be monitored, or when a response packet received from the server to be monitored does not satisfy the criterion.
Owner:FUJITSU LTD
Microcomputer, electronic equipment and debugging system
InactiveUS7114101B2Small sizeIncrease the areaError preventionDetecting faulty computer hardwareMemory mapFixed length
Owner:SEIKO EPSON CORP
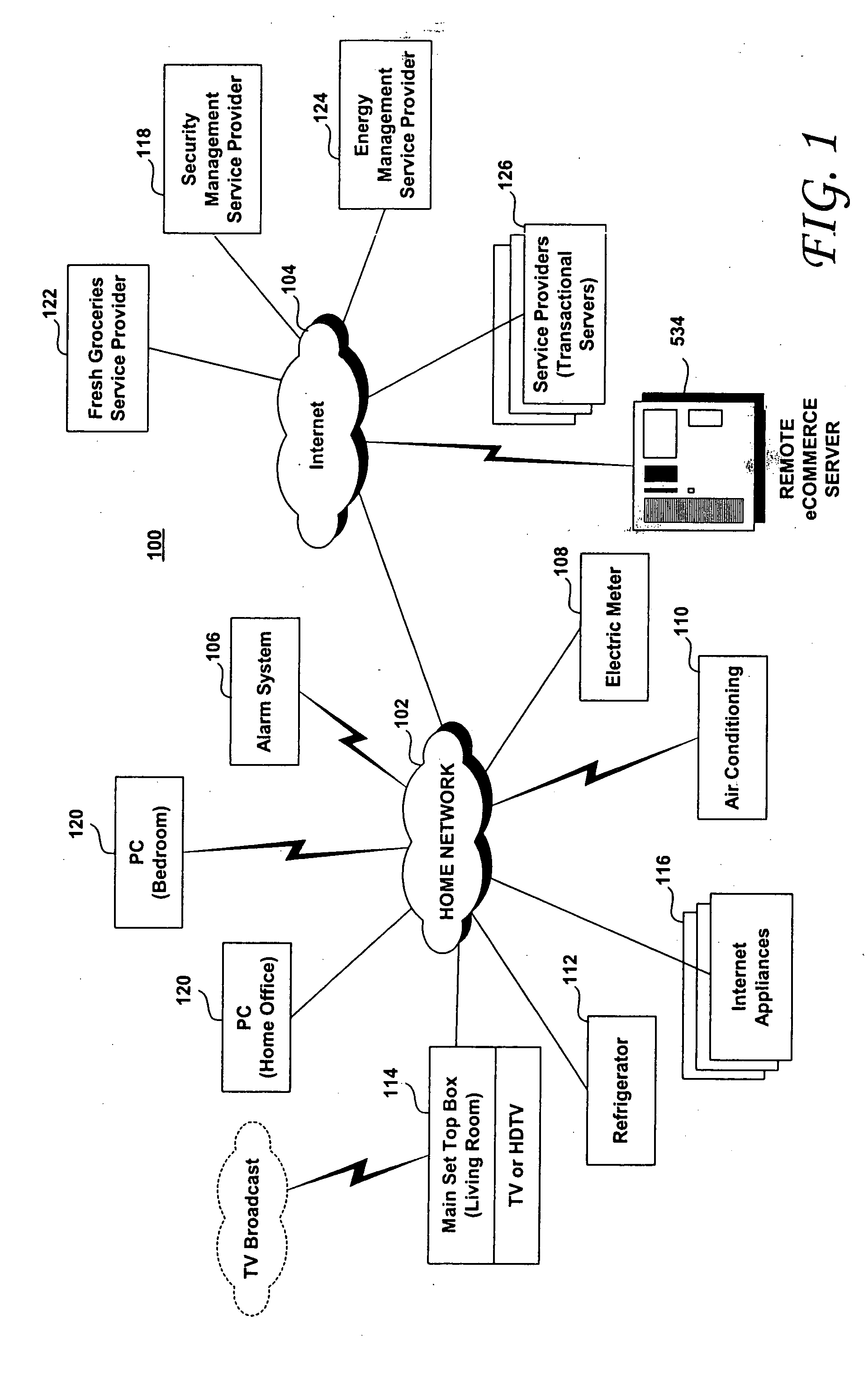
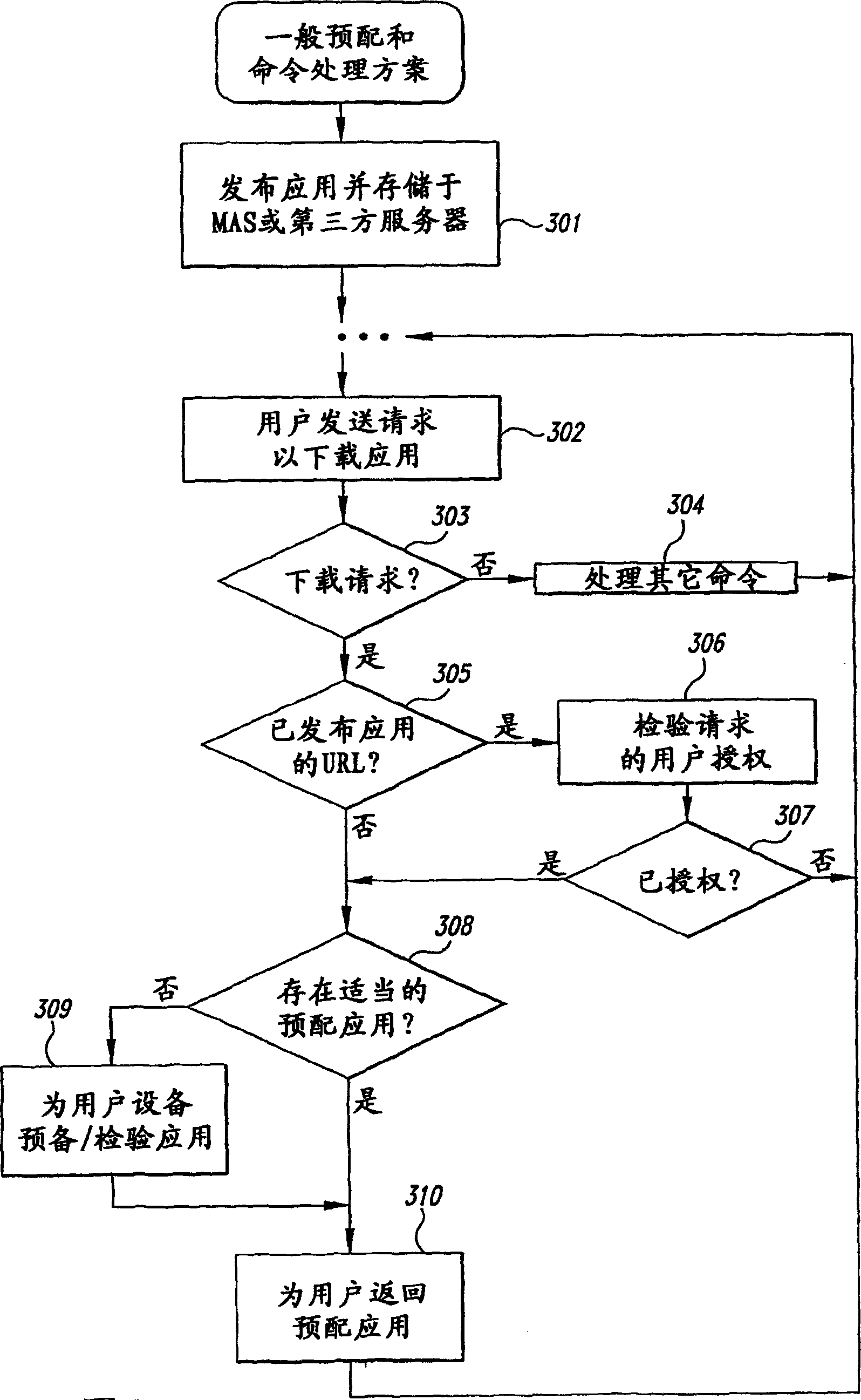
Method and system for maintaining and distributing wireless applications
InactiveCN1489736AMetering/charging/biilling arrangementsAccounting/billing servicesWireless Application ProtocolApplication computers
Computer- and network-based methods and systems for maintaining and provisioning wireless applications are provided. Example embodiments provide a Mobile Application System (MAS), which is a collection of interoperating server components that work individually and together in a secure fashion to provide applications and resources to mobile subscriber devices, such as wireless devices. Embodiments of the present invention can also be used to deploy applications and resources for wired subscriber devices. Application, resources, and other content is provisioned and verified by the MAS for authorized access by the subscriber, compatibility with a requesting subscriber device, and the security and billing policies of the carrier and system administrators of the MAS. In this manner, applications, resources, and other content can be downloaded to devices, such as wireless devices, with greater assurance of their ability to successfully execute. In one embodiment, content is provisioned by one or more of the steps of inspecting the content for malicious or banned code, optimizing the content for smaller size and greater speed, instrumentation of code that implements security, billing, and other carrier policies, and packaging of code for the intended subscriber device. Additional security is provided through application filters that are used to prevent applications that contain designated API from being downloaded to a subscriber's device. In one embodiment, the MAS includes a Protocol Manager, Provisioning Manager, Cache, Deployment Manager, Billing Manager, Logging Manager, Administrator, and Heartbeat Monitor, which interoperate to provide the provisioning functions.
Owner:4THPASS INC
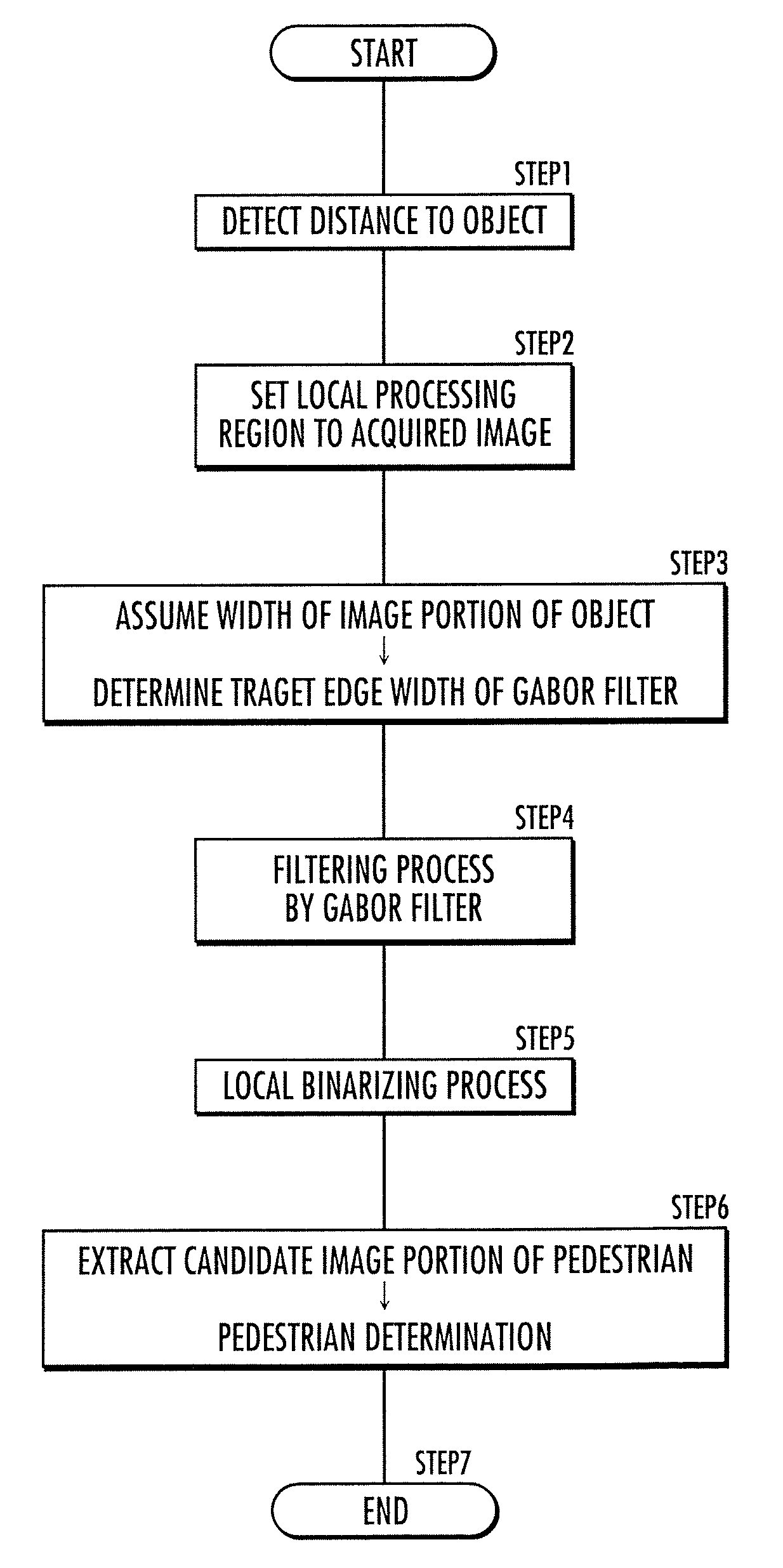
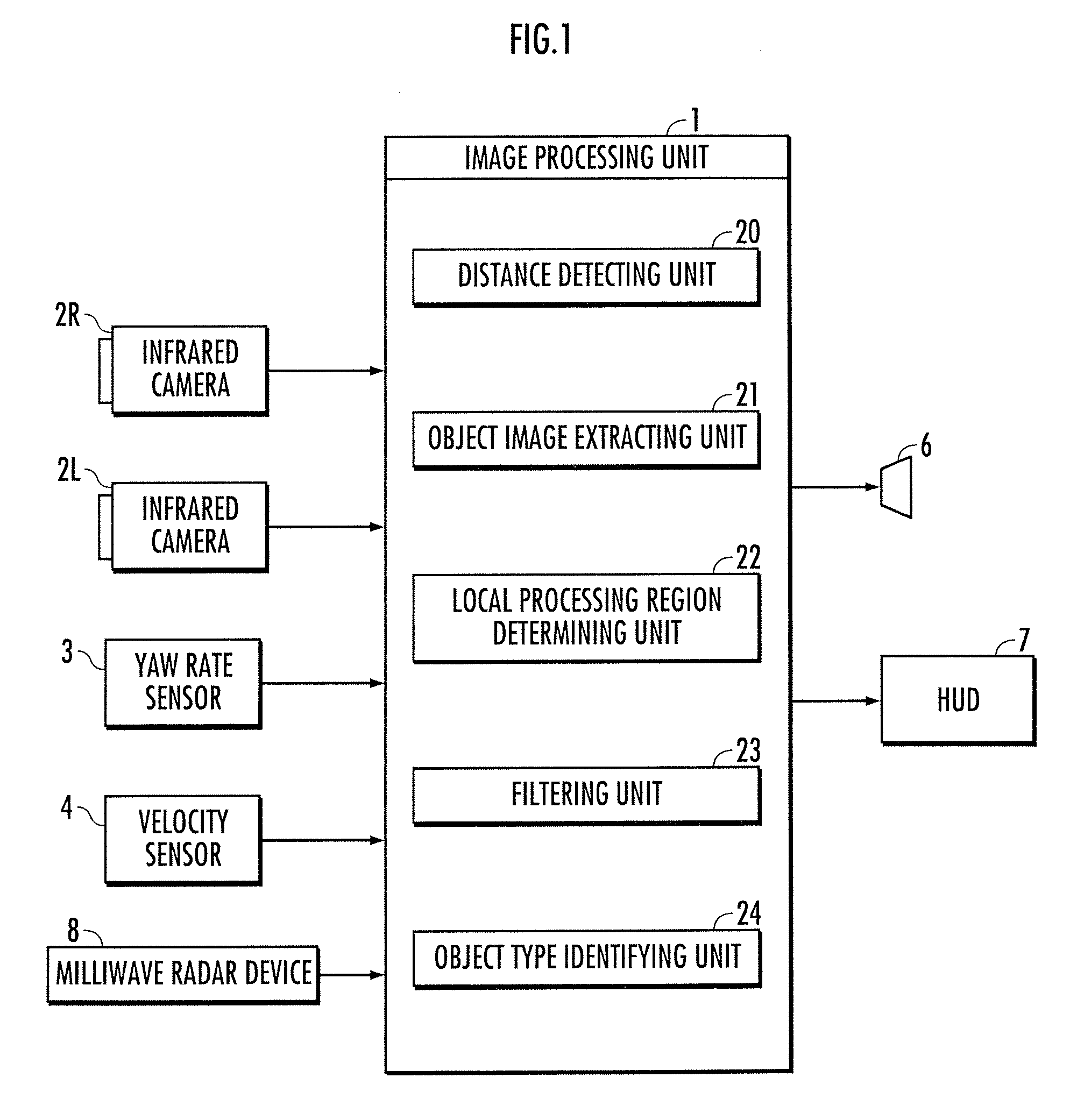
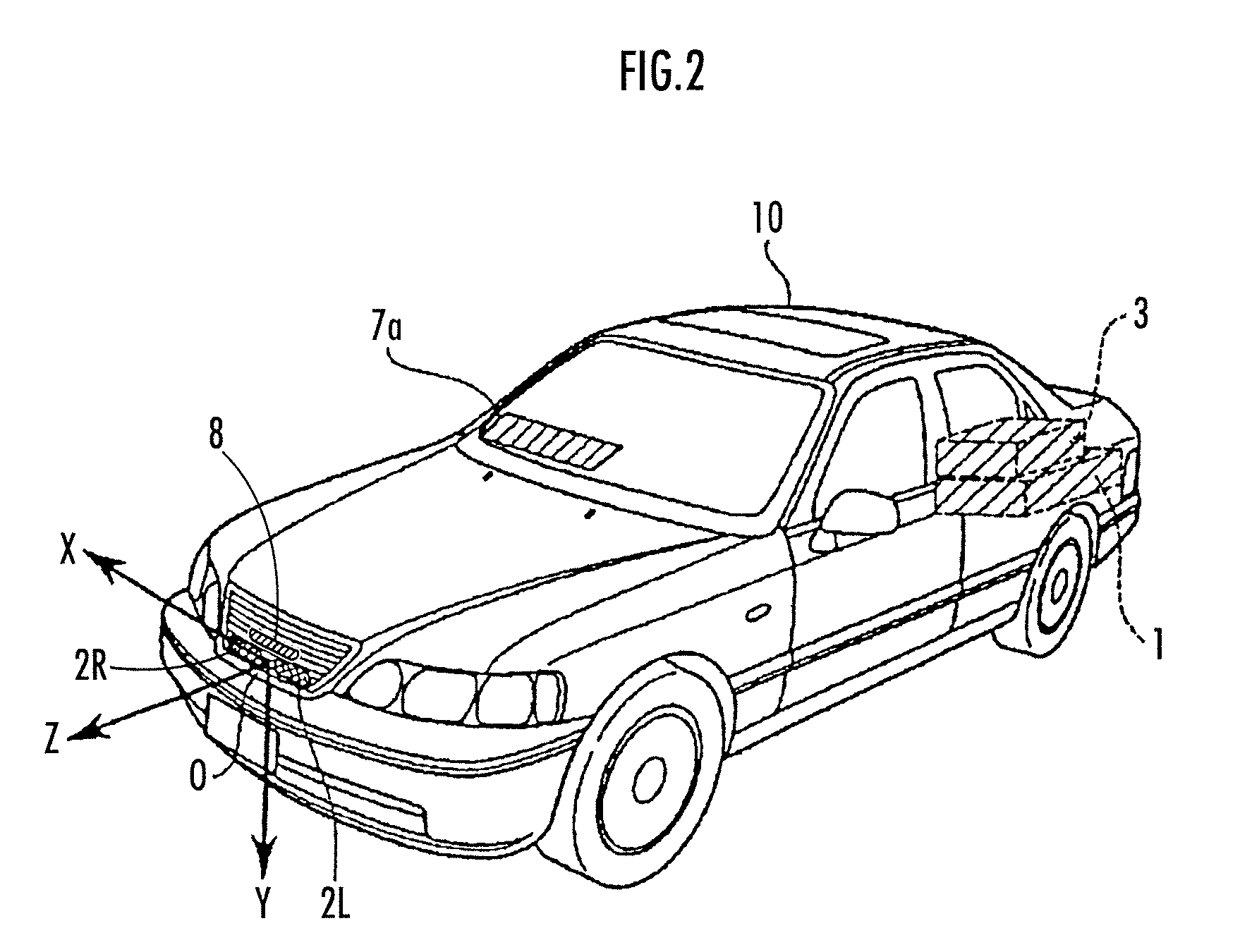
Vehicle periphery monitoring device, vehicle, vehicle periphery monitoring program, and vehicle periphery monitoring method
ActiveUS20100283845A1Improve accuracySmall sizeImage analysisColor television detailsImage extractionDistance detection
A vehicle periphery monitoring device comprising a distance detecting unit which detects the distance between cameras and an object, an object image extracting unit which extracts a first image portion of the object from the acquired image, a filtering unit which performs a filtering process to the acquired image, in which a target edge width is set to be narrower as the assumed value of the width is smaller and the distance is longer, and in which a target edge direction is set to a direction orthogonal to the predetermined direction, and an object type identifying unit which identifies, on the basis of a shape of a second image portion extracted by the filtering process, whether or not the type of the object in real space corresponding to the second image portion is the specific type.
Owner:ARRIVER SOFTWARE AB
Method and system for monitoring execution performance of software program product
ActiveUS20100281468A1Improve efficiencyError detection/correctionSpecific program execution arrangementsData processing systemData field
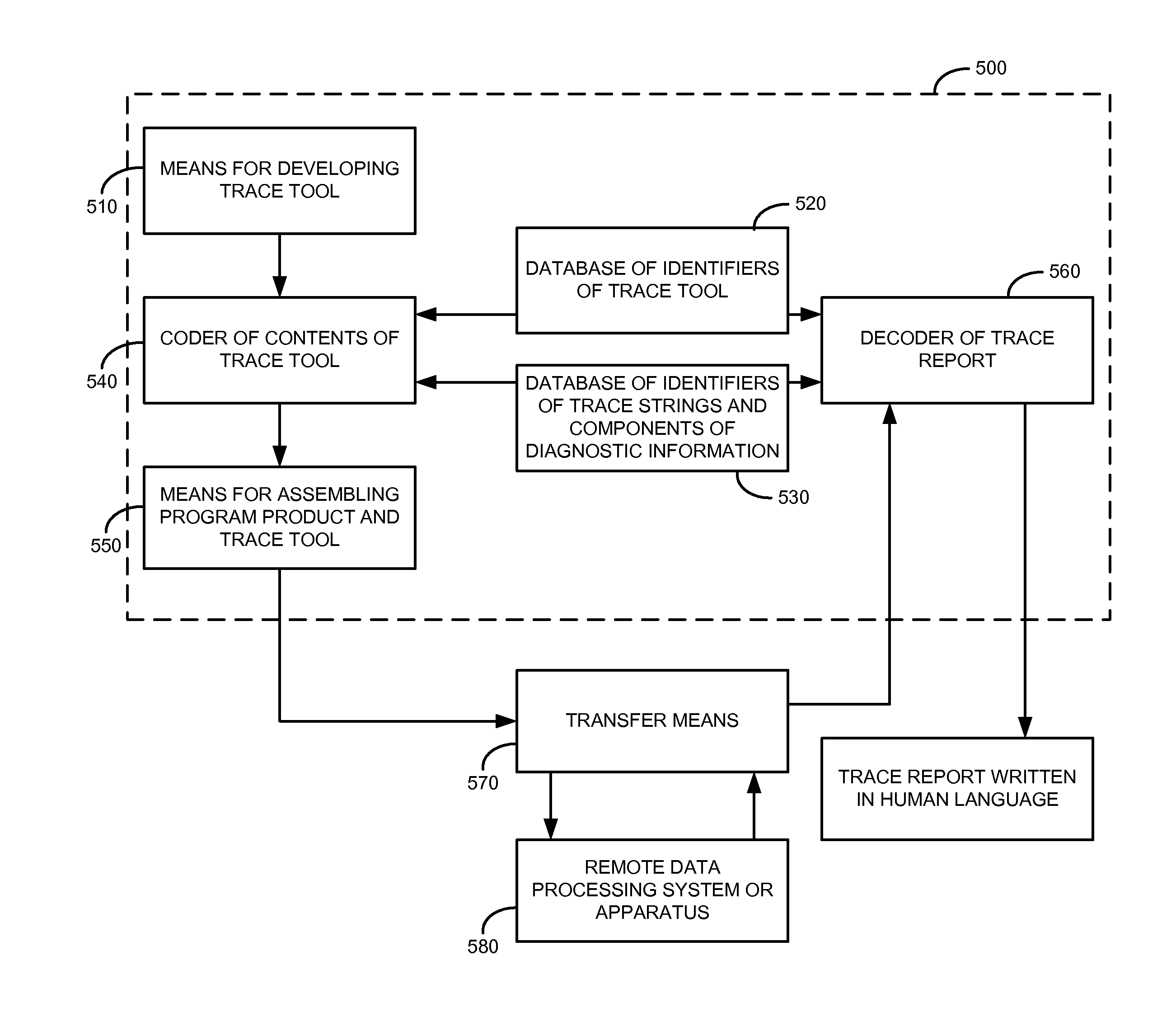
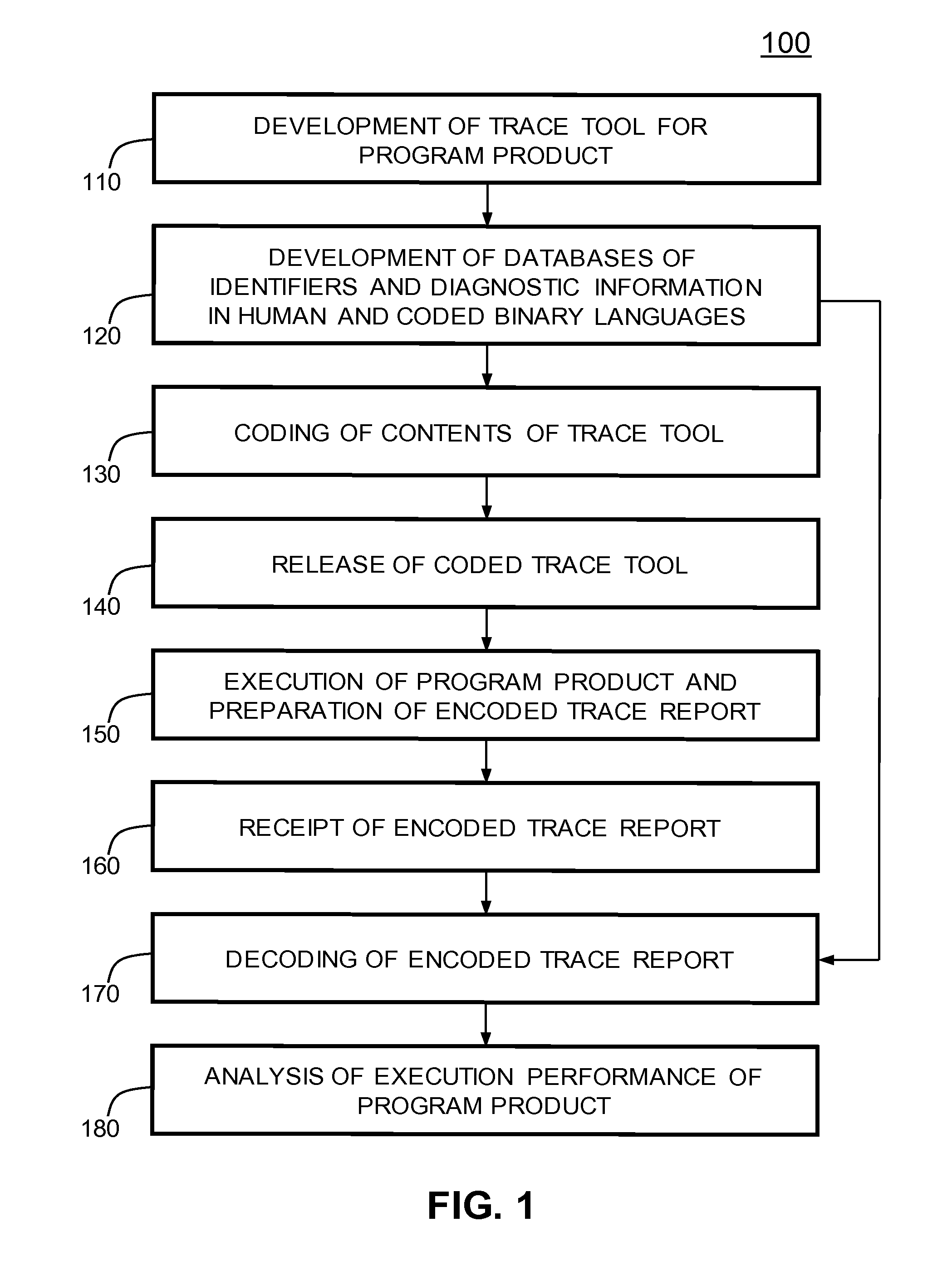
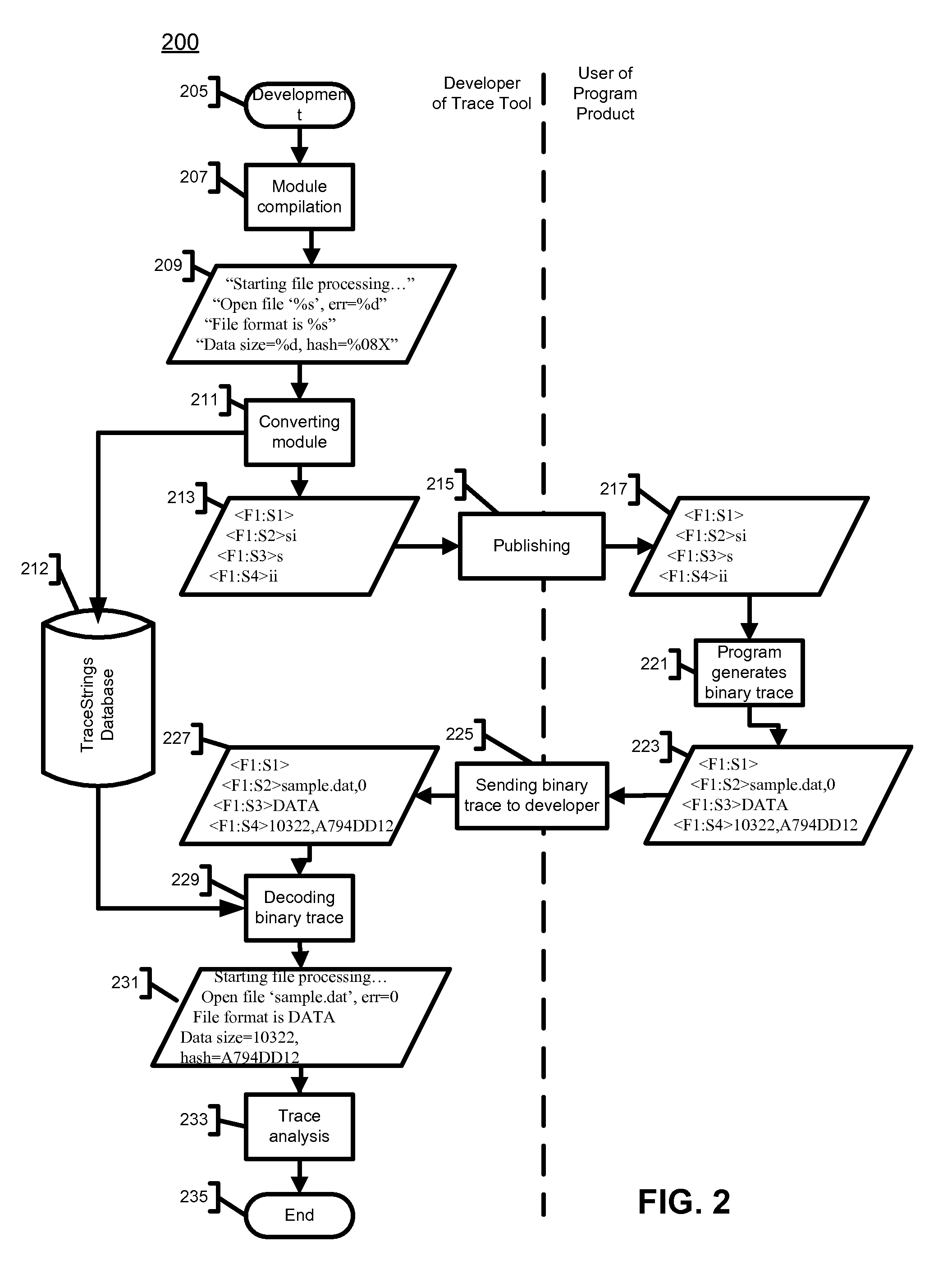
A method, computer program product and system for monitoring execution behavior of a program product in a data processing system include development of a trace tool having trace strings written in a human language and provided with data fields for diagnostic information relevant to executable portions of the program product. Identifiers of the trace tool, trace strings, and data fields and components of the diagnostic information are encoded using a coded binary language. After monitoring execution of the program product, a trace report of the trace tool is translated for an intended recipient from the coded binary language into the human language, whereas an unauthorized access to the contents of the trace record is restricted. The encoding or decoding operations are performed using databases containing the respective identifiers and components of the diagnostic information in the coded binary language and the human language.
Owner:AO KASPERSKY LAB
Method to identify transactions and manage the capacity to support the transaction
ActiveUS20050262235A1Quick checkDigital computer detailsHardware monitoringAddress Resolution ProtocolActivity level
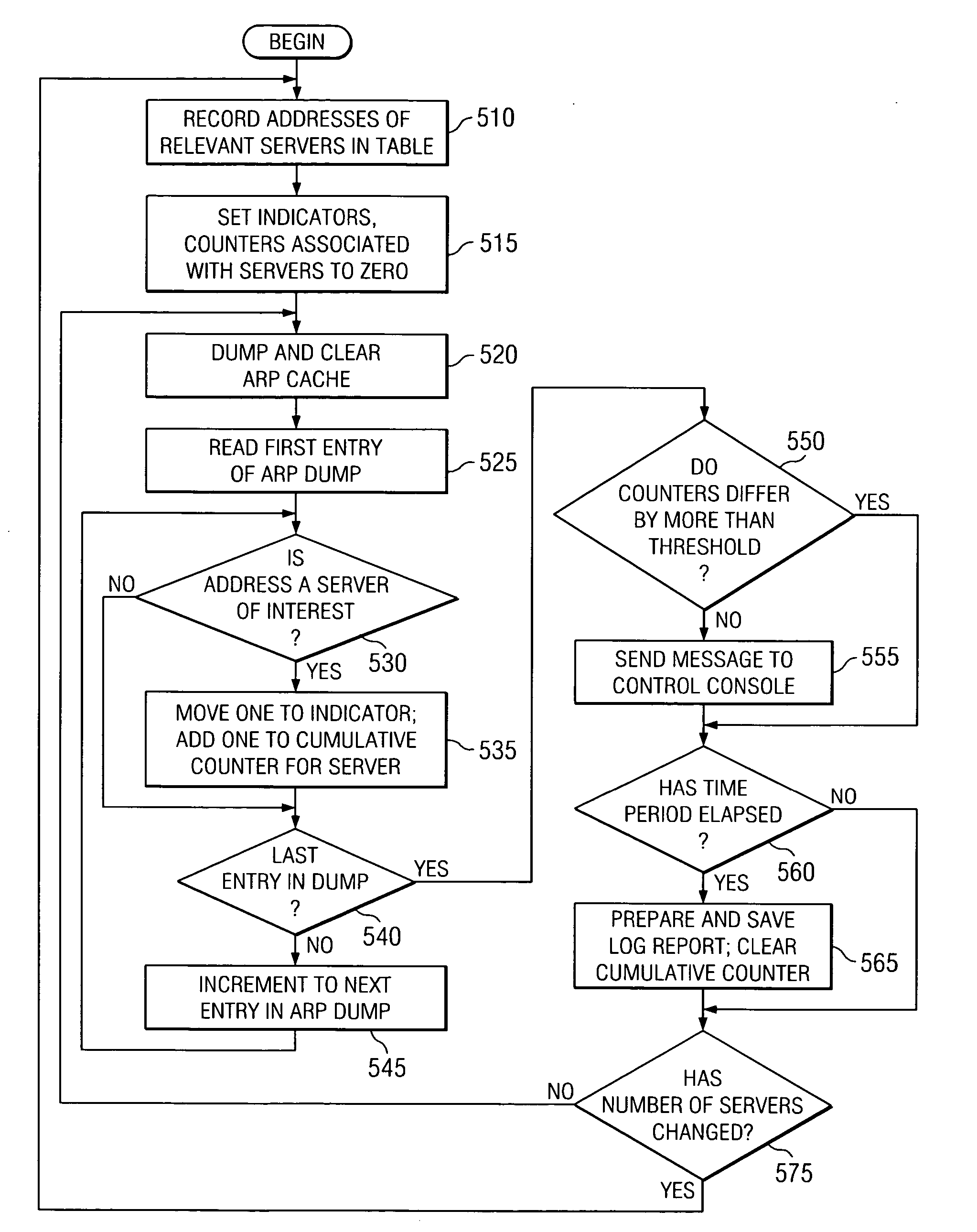
A monitoring program contains a method for detecting a load imbalance in a group of servers and providing notification so that corrections can be made. An embodiment of the invention reads from the address resolution protocol (ARP) cache to determine which server addresses are present, then clears the ARP cache. The address resolution protocol will repopulate the cache from traffic it snoops and from new requests. By performing this query and clear operation periodically, the tracking program can form a picture of the activity levels of the servers. When a significant imbalance exists, the program notifies a control console for human intervention to solve the problem. The tracking program will periodically write its results to a log file, allowing reports for various time periods to be produced as needed. By this mechanism, not only can an imbalance be quickly detected, but underutilization can be picked up by comparing known capability of a resource to its actual usage.
Owner:IBM CORP
System and method for generating alert conditions in a surveillance system
InactiveUS20030095687A1Television system detailsColor television detailsVideo monitoringSurveillance camera
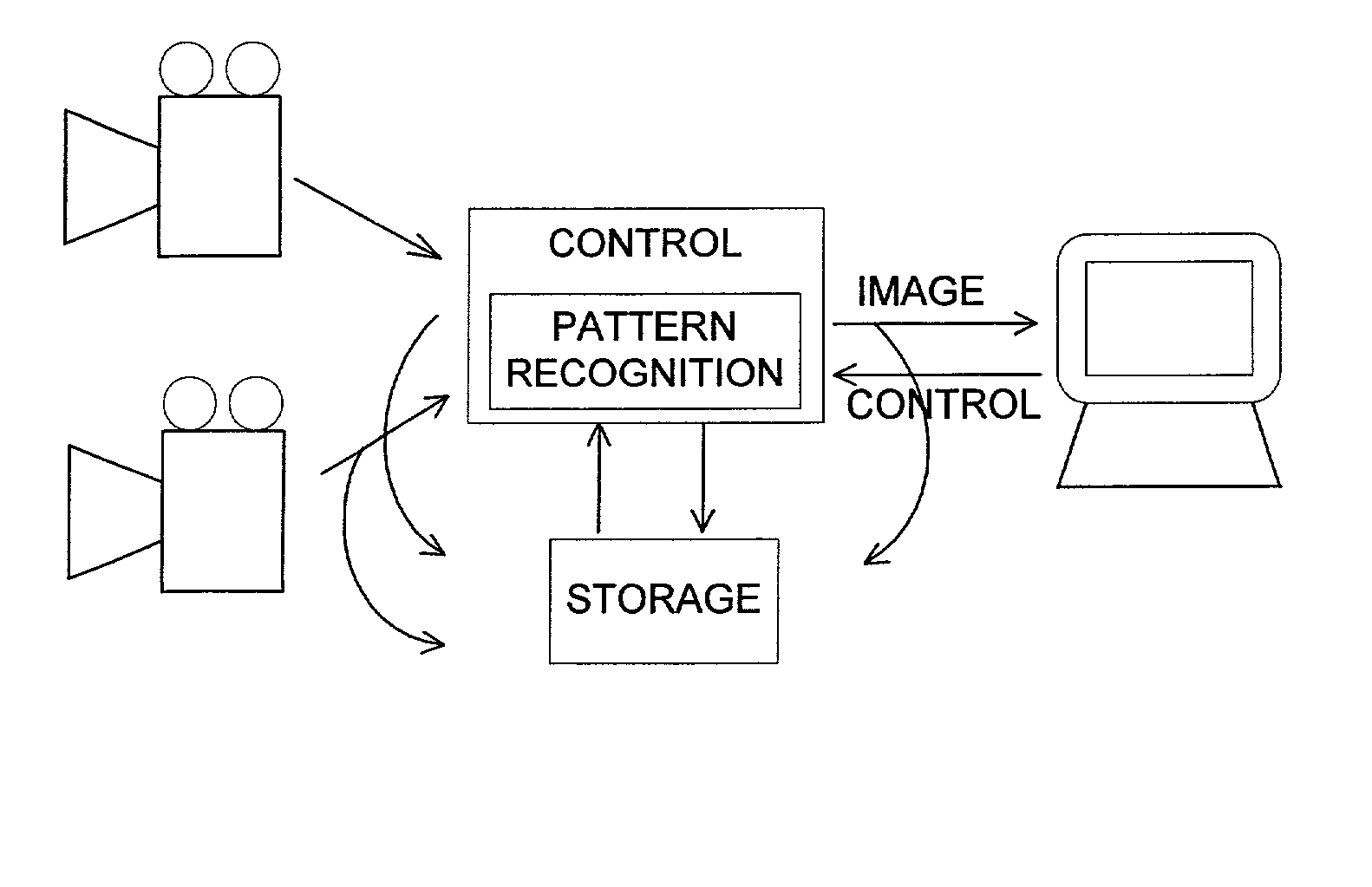
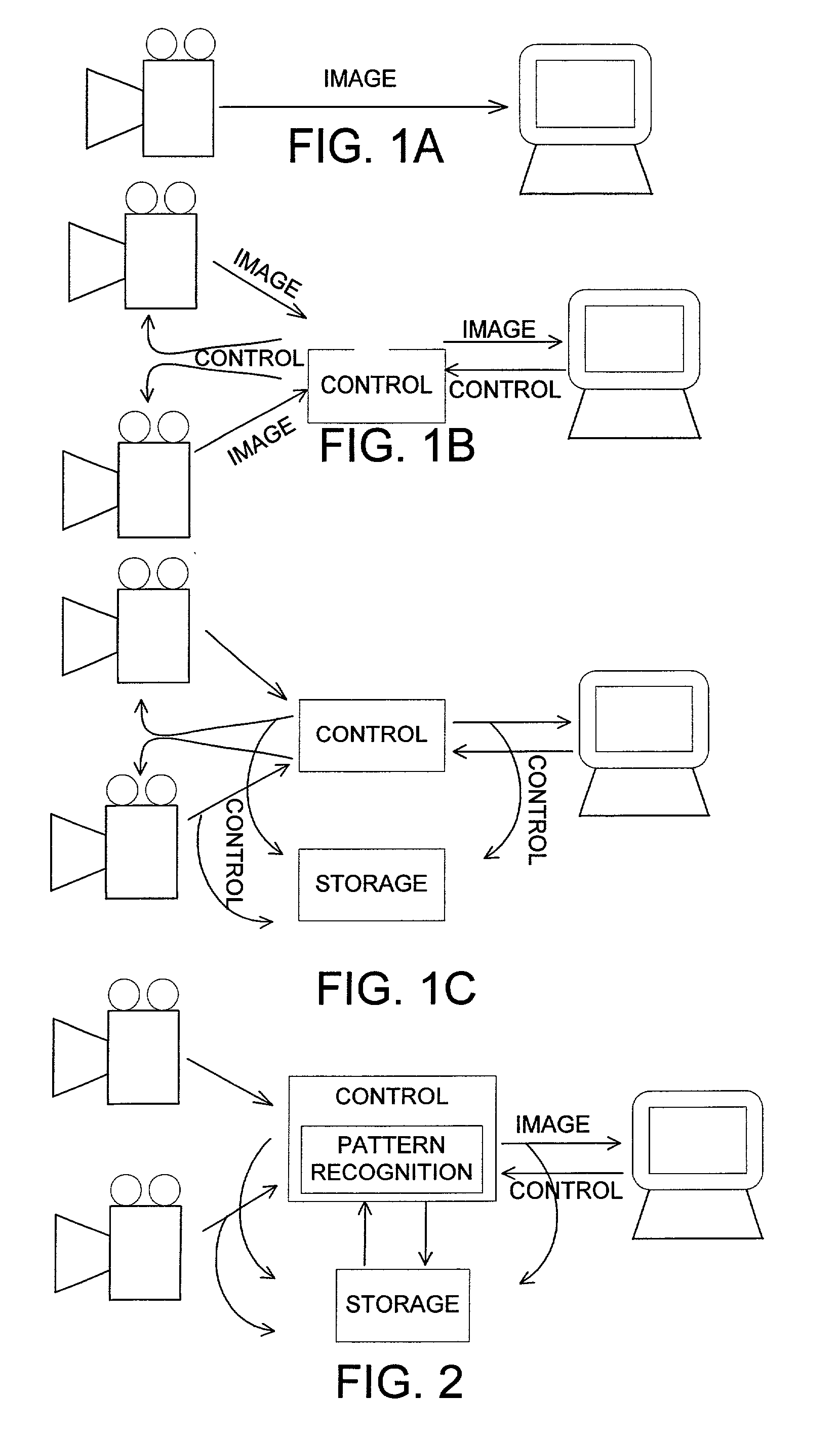
A monitor program in a video surveillance system monitors images coming from one or more surveillance cameras. When an image or set of images satisfies certain conditions, the monitor program takes an appropriate action. For example, in a video surveillance system in a bank, there may be a surveillance camera in the bank's lobby as well as a surveillance camera inside the bank's vault. If, using appropriate pattern recognition techniques, the monitor program recognizes a cleaning person in the lobby doing cleaning, it might not take any action since that would be a legitimate place for the cleaning person to be. If, however, the monitoring system recognized that cleaning person as being in the vault, it might send an alert to the surveillance system operator for further inspection, since cleaning personnel typically should not be in the vault.
Owner:ETREPPID TECH
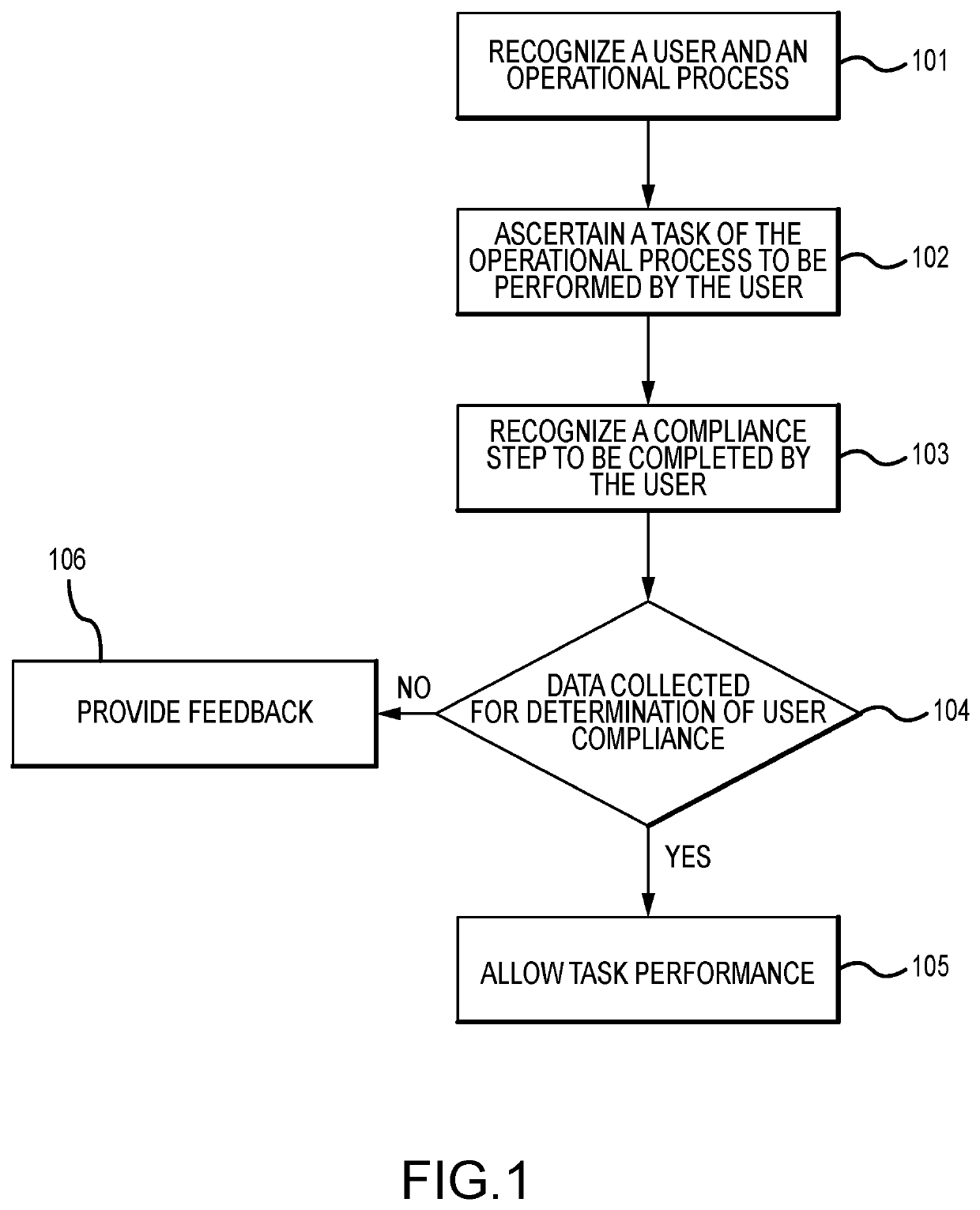
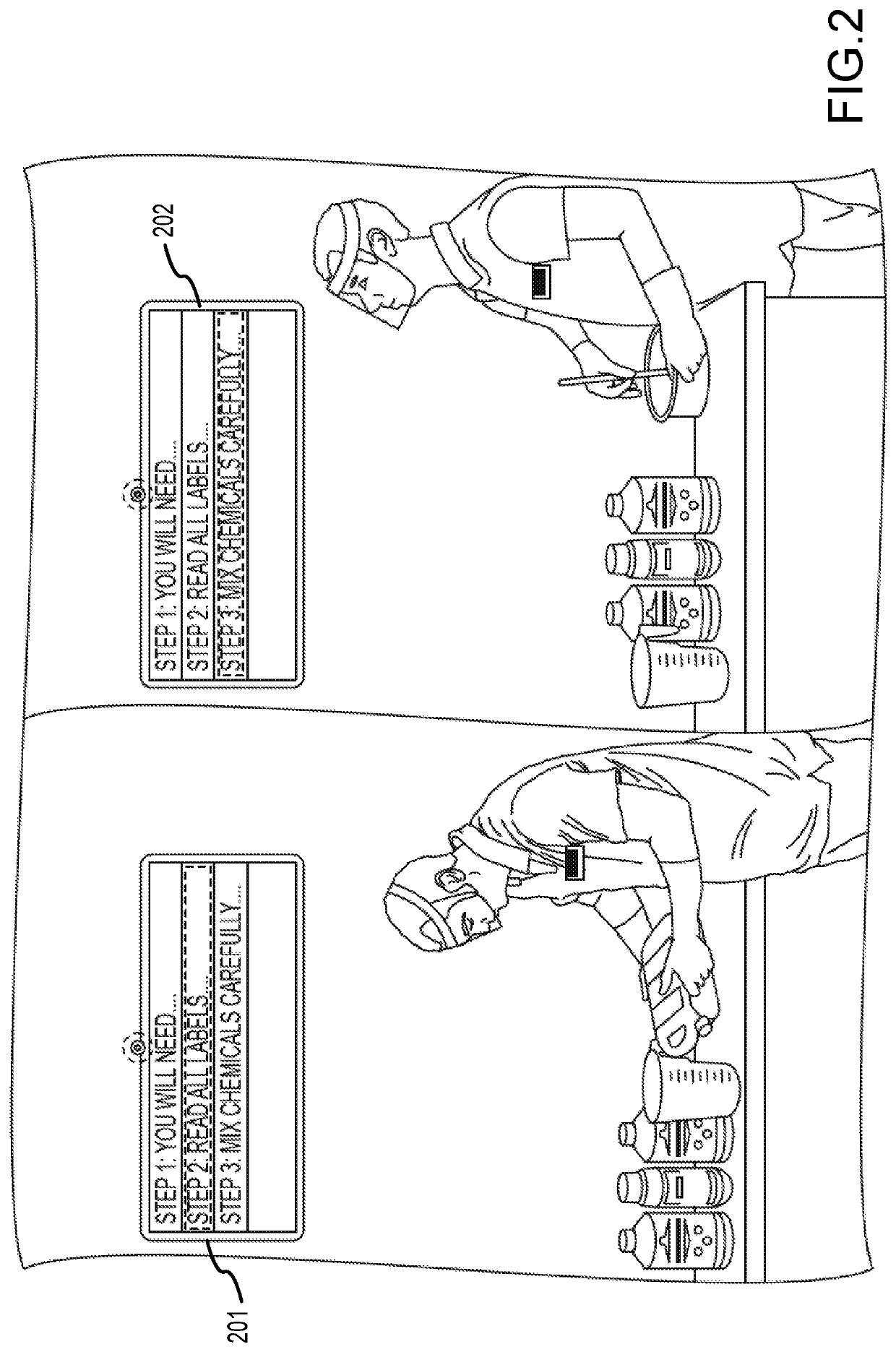
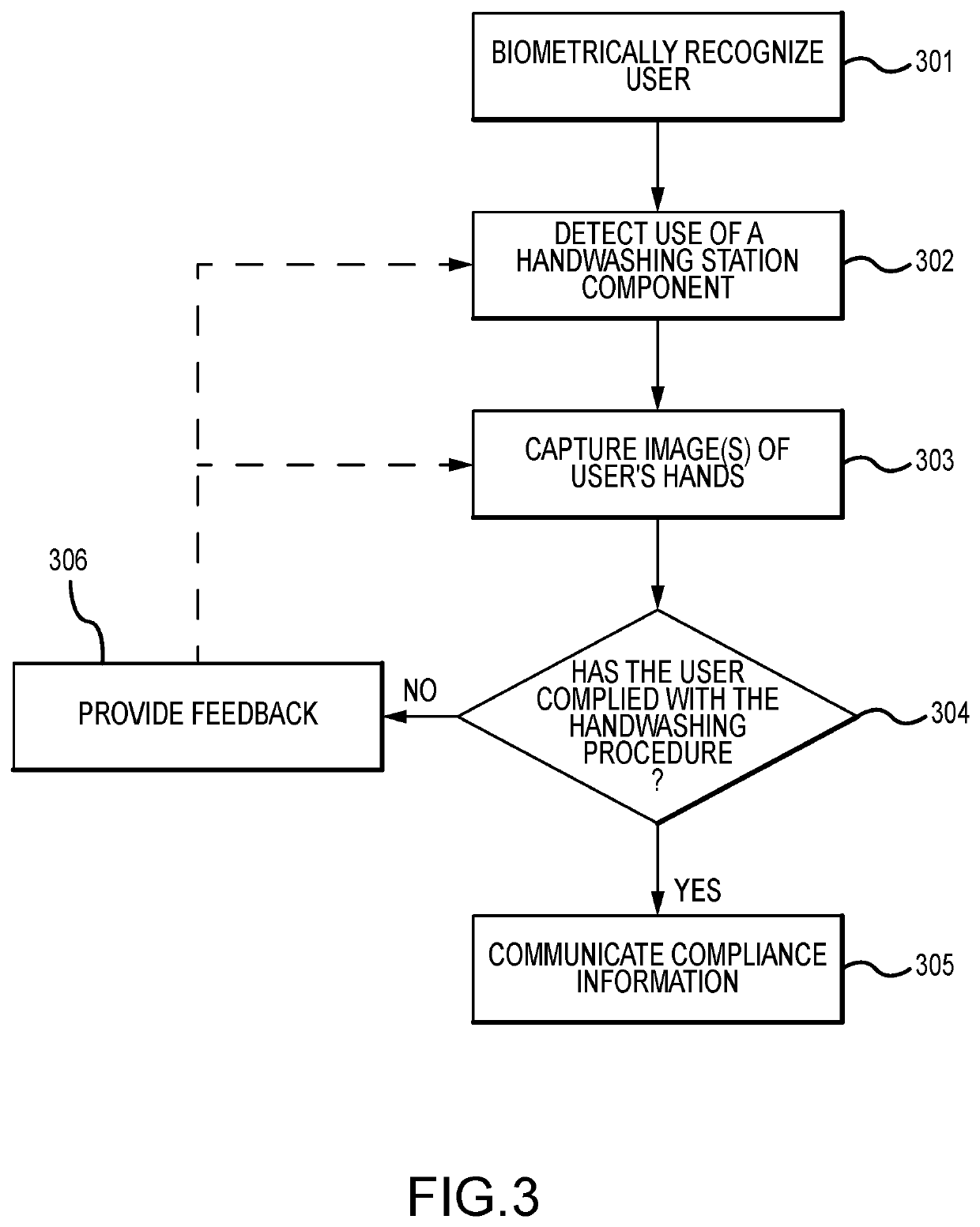
System and method for monitoring procedure compliance
ActiveUS20190354753A1Biometric pattern recognitionMatching and classificationComputer scienceImaging data
A method of monitoring a user performing a handwashing procedure, including: recognizing a user based upon biometric information obtained at a handwashing station, a user; detecting use of a component of the handwashing station; capturing image data of the user at the handwashing station; capturing data describing components and consumables used at the handwashing station; analyzing, using a processor, the image data; determining compliance with a handwashing procedure based at least in part on the analysis of the image data and the use of the component; and communicating compliance information.
Owner:DISNEY ENTERPRISES INC
Method and system for power load management
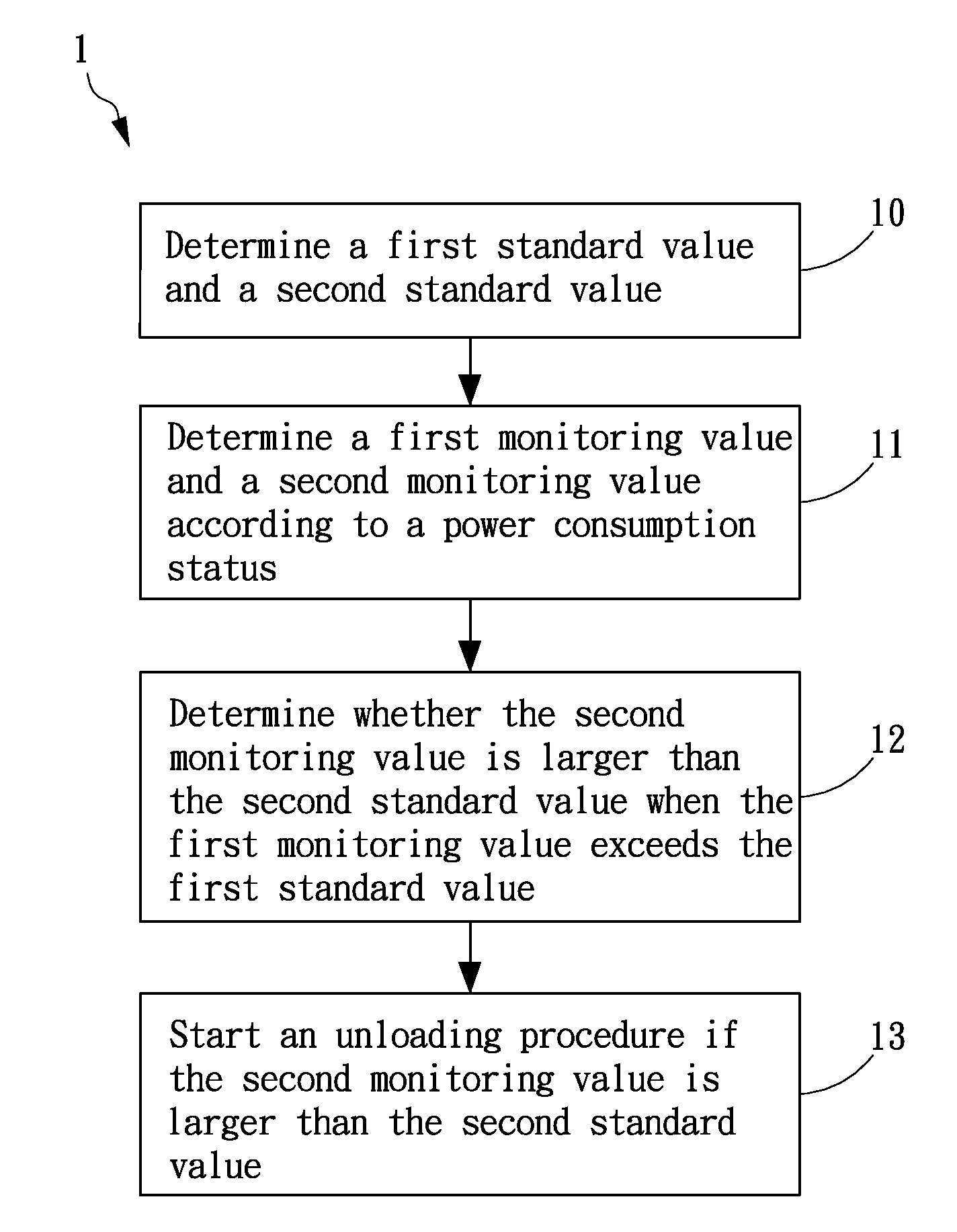
ActiveUS20100026096A1Reduce power consumptionAssure accuracyProgramme controlDc network circuit arrangementsElectrical devicesEngineering
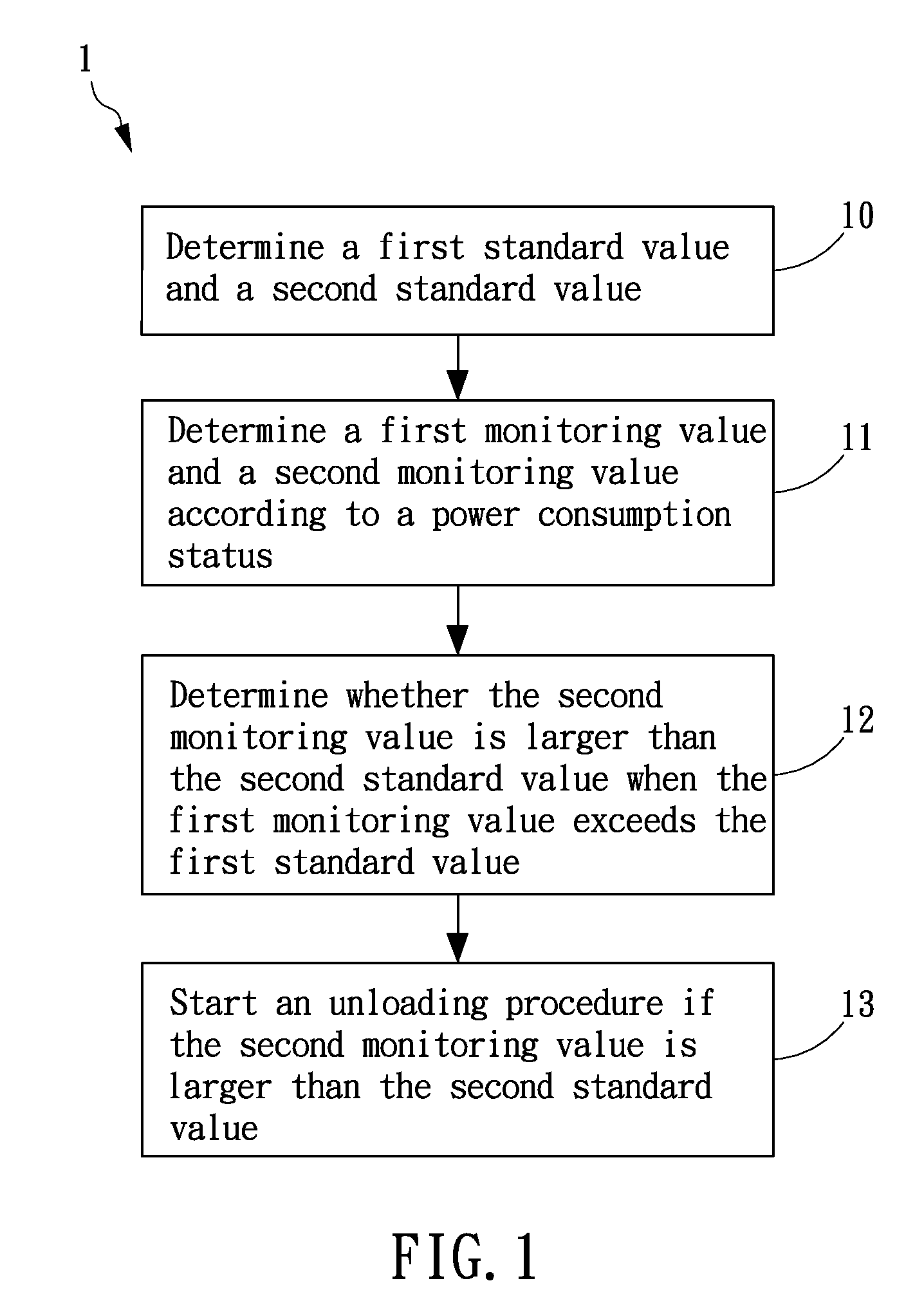
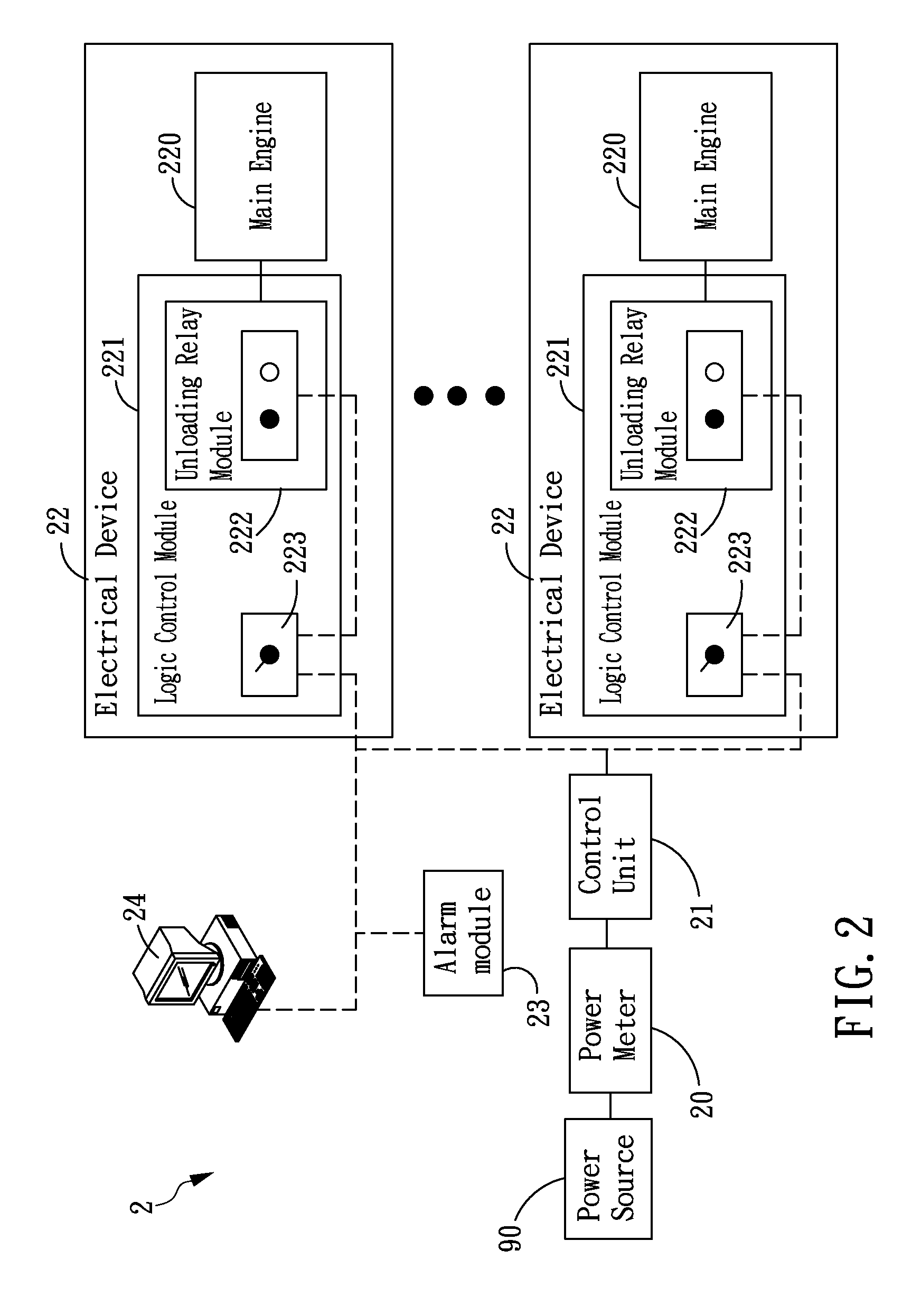
A method for power load management is provided in the present invention, wherein two different standard values are determined to be a basis for regulating power consumption. When power consumption exceeds a first standard value, a monitoring procedure is started to monitor consumption status. If the power consumption exceeds a second standard value, an unloading procedure is processed to reduce the power consumption of electrical devices under operation. In another embodiment, the present invention also provides a system for power load management comprising a control unit coupled to at least one electrical device and a power meter. By means of real-time recording of power consumption in the power meter, the control unit is capable of determining the power consumption status and determining whether it is necessary to unload or reload the at least one electrical device.
Owner:IND TECH RES INST
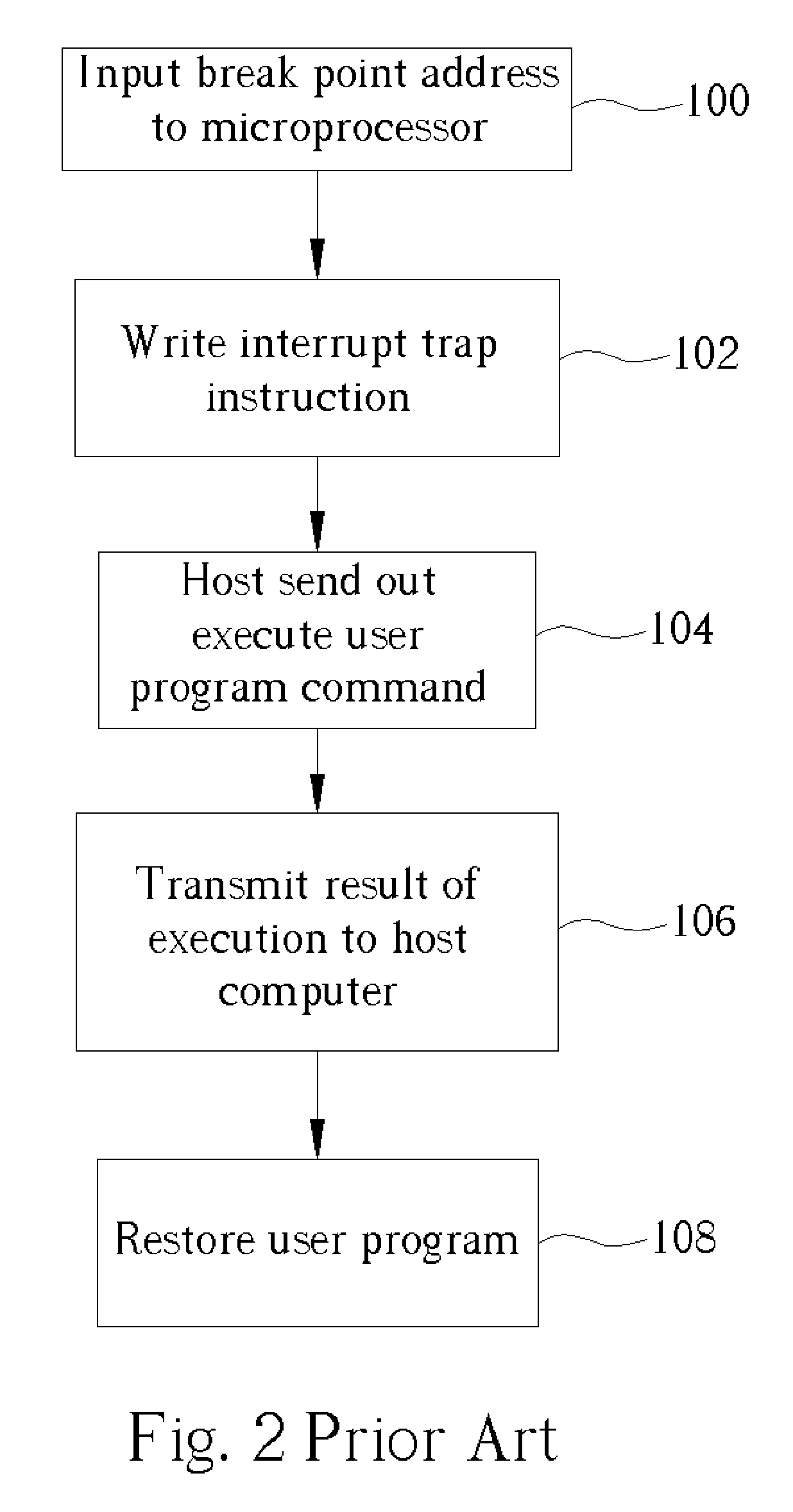
Microprocessor system with software emulation processed by auxiliary hardware
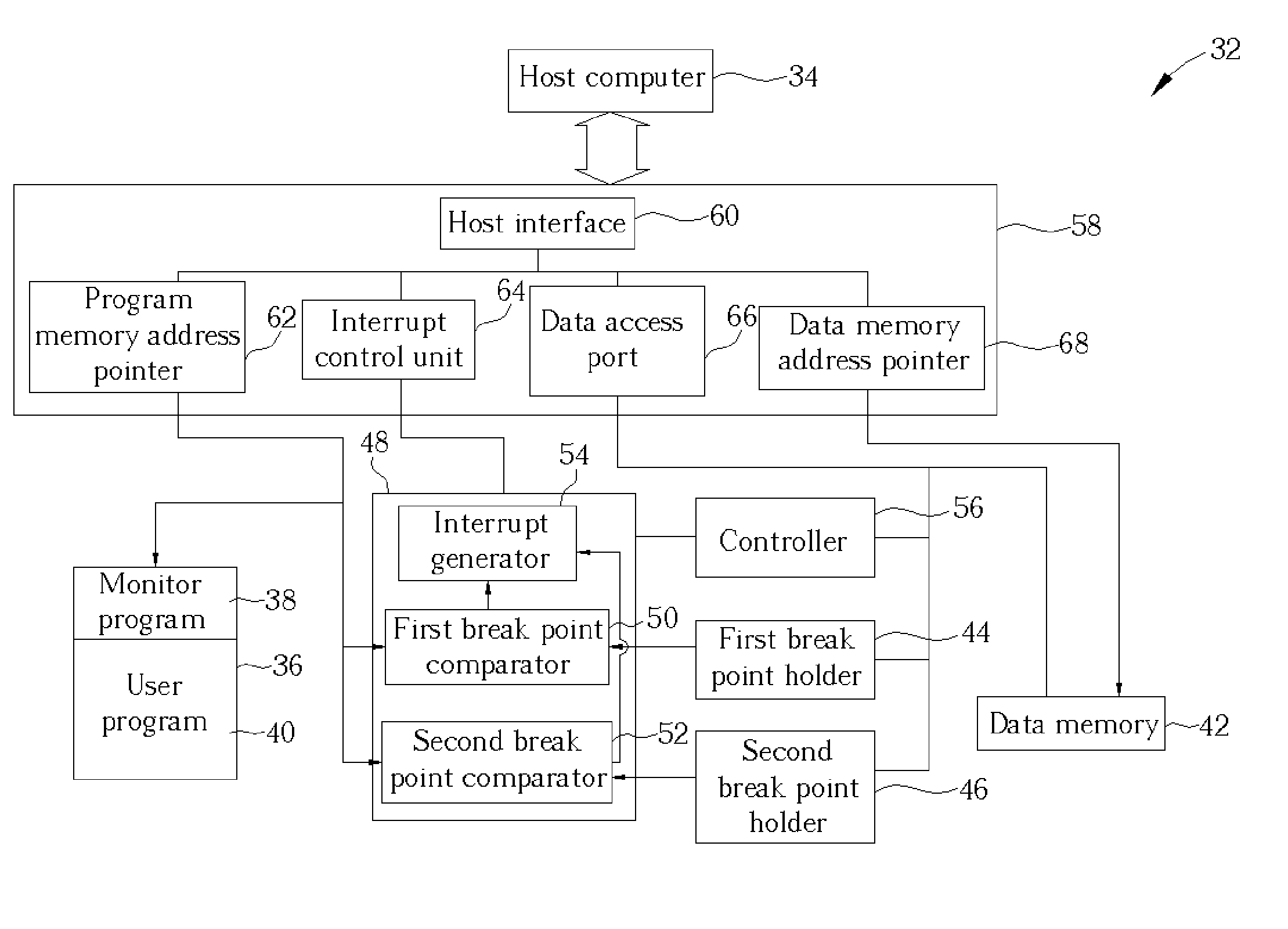
InactiveUS20050060690A1Stop executionError detection/correctionSpecific program execution arrangementsSoftware emulationControl signal
A microprocessor system capable of software debug includes a host computer for executing remote debug, and a program memory for storing a monitor program for proving monitoring of the host computer and a user program. At least one break point address holder temporarily stores a break point address from the host computer. A break point comparator unit is connected to the break point address holder for comparing the break point address from the break point address holder with an address of the user program being executed, and for outputting an interrupt control signal when the addresses match. A controller controls the break point comparator unit, and a microprocessor is electrically connected to the host computer.
Owner:CONWISE TECH CORP
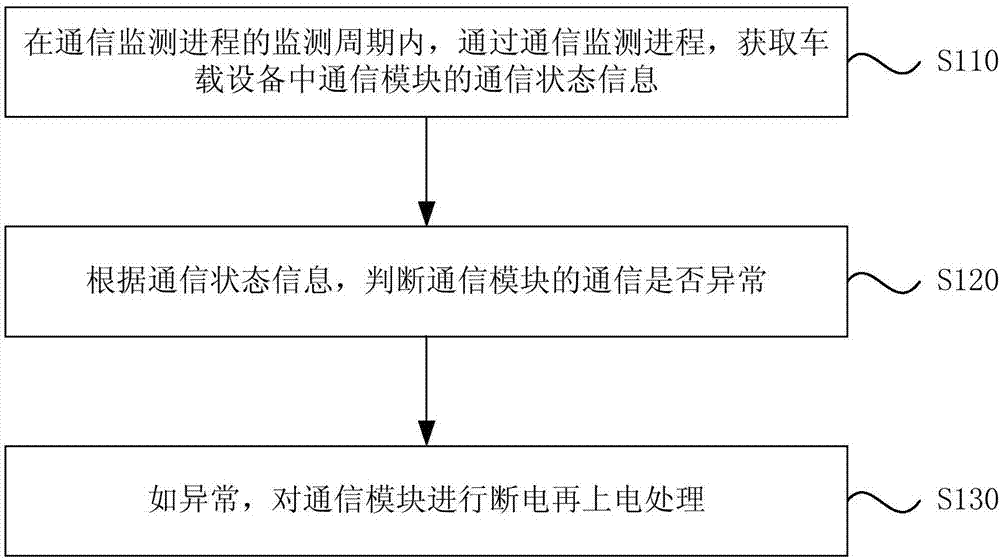
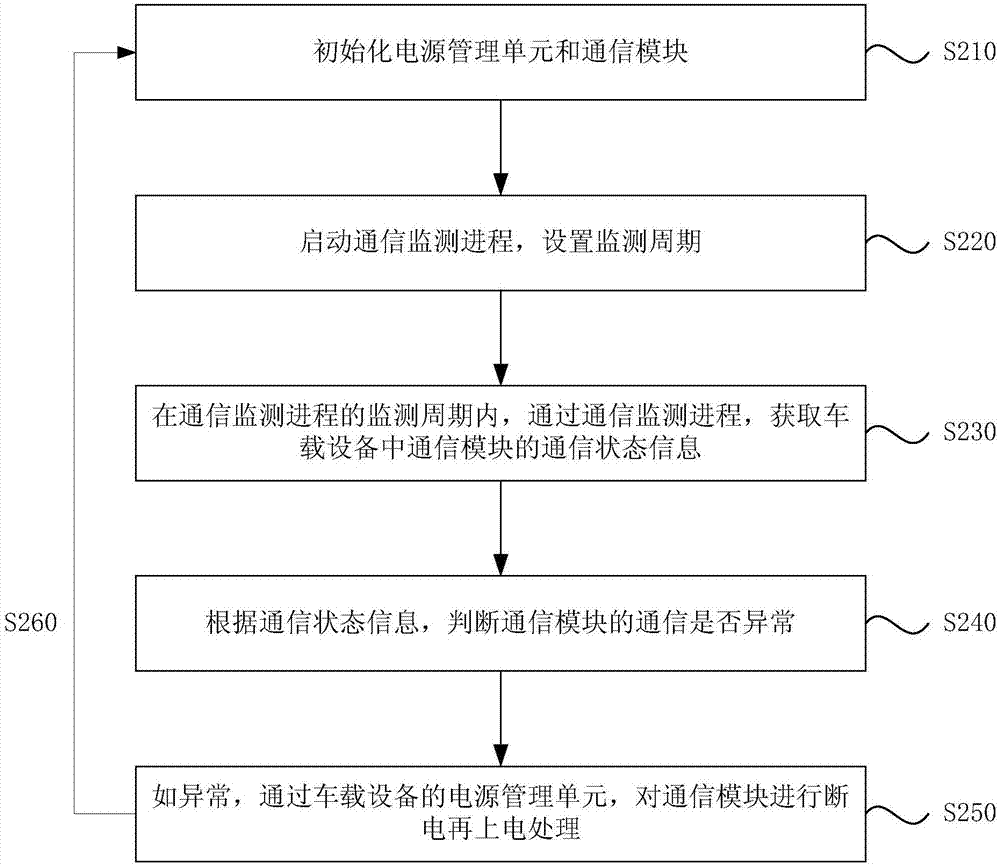
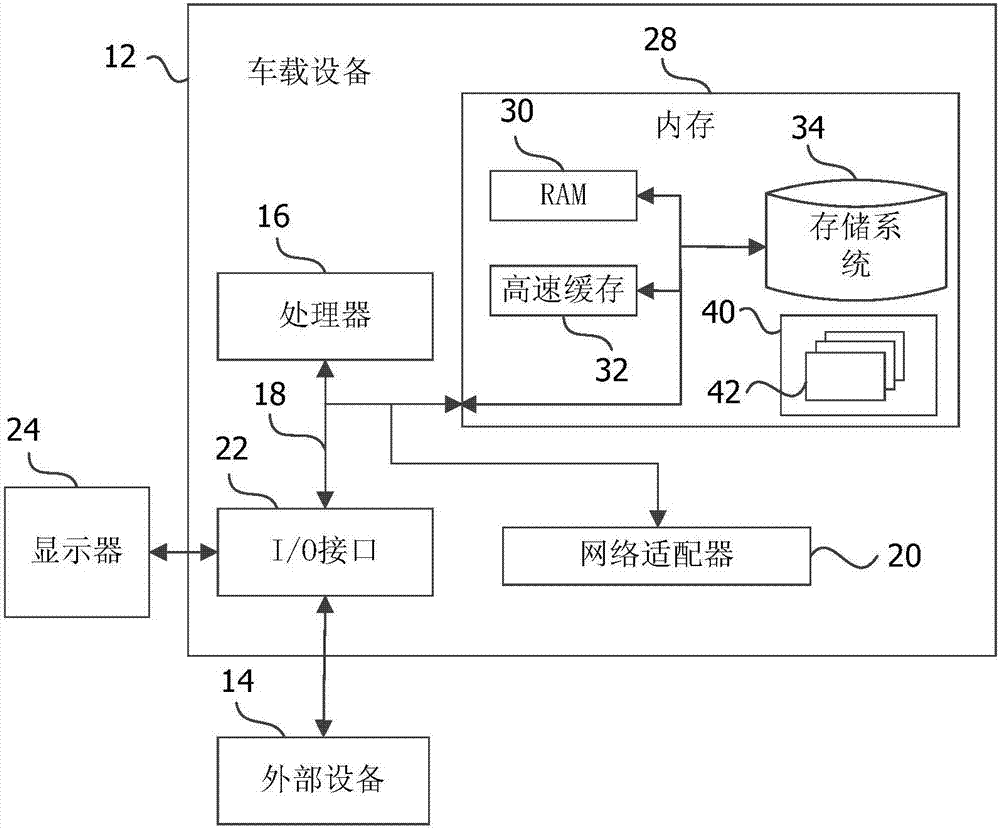
Processing method of communication abnormality, vehicle-mounted equipment and storage medium
The embodiment of the invention discloses a processing method of communication abnormality, vehicle-mounted equipment and a storage medium. The processing method of the communication abnormality is applied to vehicle-mounted equipment, and comprises the following steps: acquiring communication state information of a communication module in the vehicle-mounted equipment through a communication monitoring procedure in the monitoring period of the communication monitoring procedure; judging whether the communication of the communication module is abnormal according to the communication state information; if the communication is abnormal, performing power outage on the communication module and then performing the power-on processing. The vehicle-mounted equipment can automatically perform the power outage on the communication module and then perform the power-on processing when monitoring the fact that the communication of the communication module in the vehicle-mounted equipment is abnormal through the communication monitoring procedure, thereby enabling the communication module to recover a communication function and guaranteeing the communication stabilization of the vehicle-mounted equipment.
Owner:SHENZHEN CHUANGWEI AUTOMOBILE INTELLIGENT CO LTD
Virtual CPU dispatching method
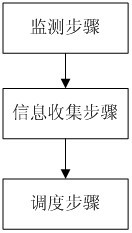
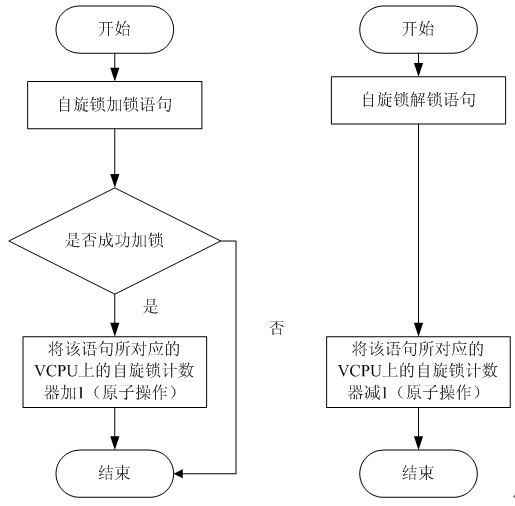
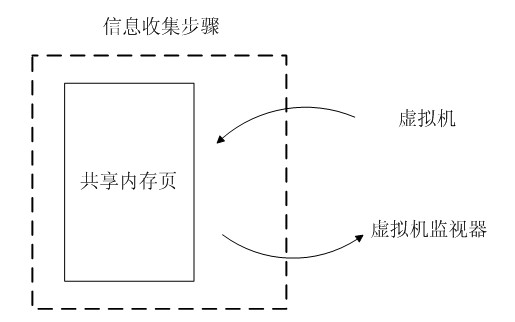
InactiveCN102053858AImprove accuracyHigh precisionSoftware simulation/interpretation/emulationVirtualizationExtensibility
A virtual CPU (Central Processing Unit) dispatching method belongs to the technical field of computing system virtualization, solves the problem of lock holder preemption, and improves the performance of a virtual machine in a multiple processor system. The virtual CPU dispatching method is used in a multiprocessor virtualized environment and comprises a monitoring procedure, an information collecting procedure and a dispatching procedure, wherein the monitoring procedure performs real-time monitoring to spin lock operating commands of all virtual machine operating systems; the information collecting procedure extracts spin lock amount obtained by the monitoring procedure, to form spin lock counting information; and the dispatching procedure adopts fair and efficient dispatching method todispatch the virtual CPU according to the spin lock counting information extracted from the information collecting procedure. Compared with the prior art, the method can detect whether dispatching isavailable more accurately, so as to improve the utilization ratio of physical CPU, ensure that dispatching strategy has flexibility and expandability, as well as fairness, effectively solve the problem of lock holder preemption, and greatly improve the performance of virtual machine in a multiple processor system.
Owner:HUAZHONG UNIV OF SCI & TECH
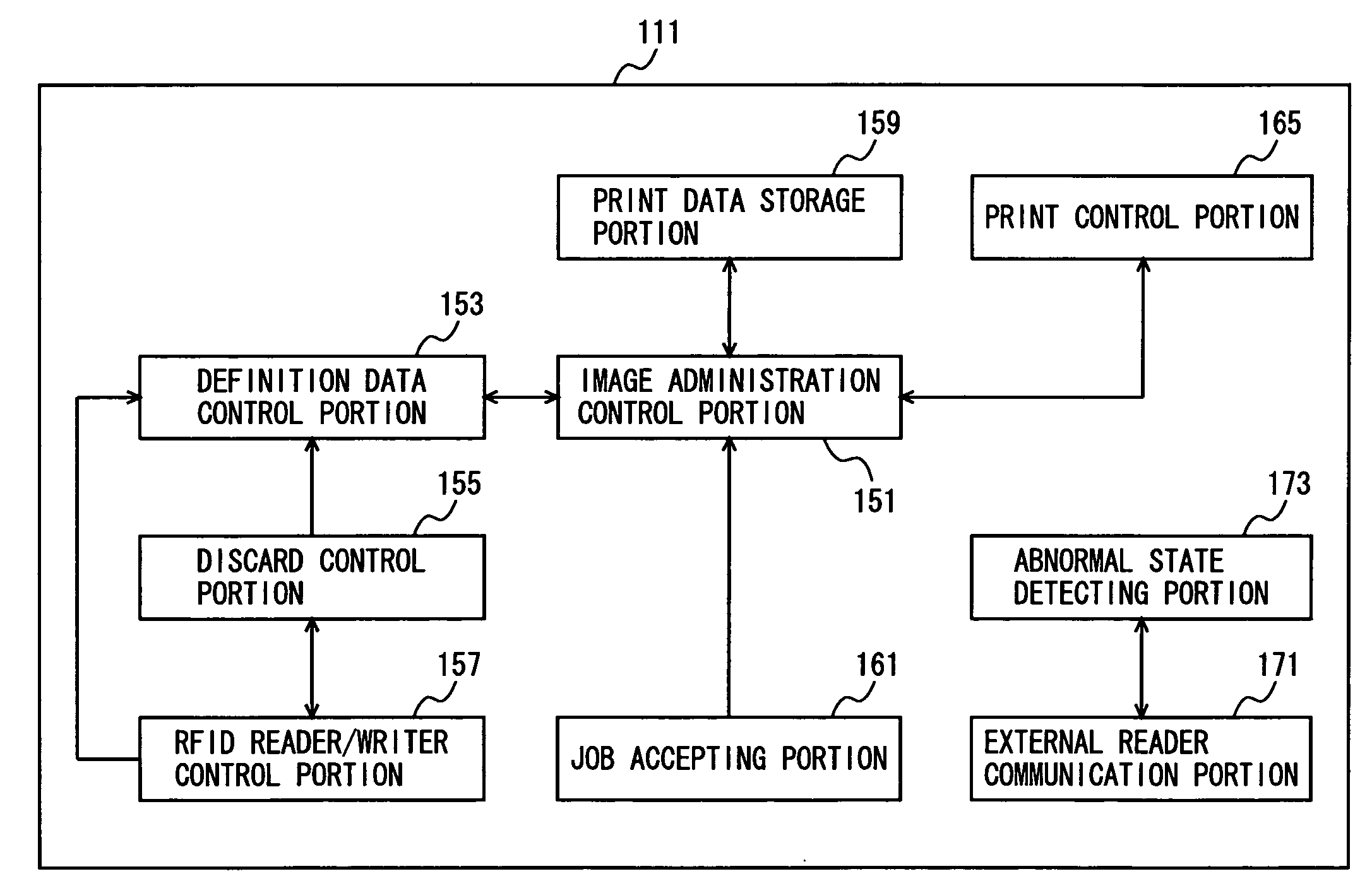
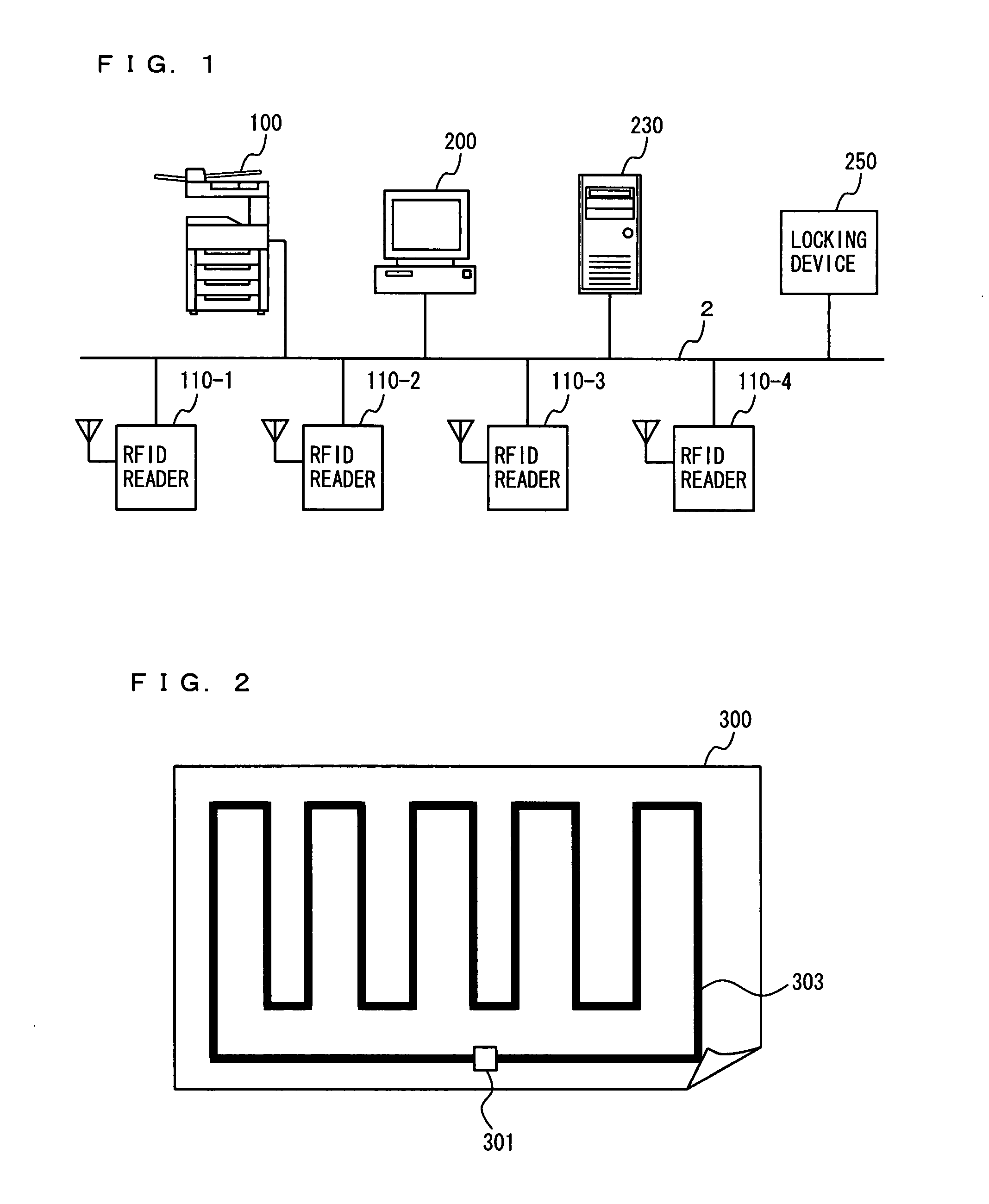
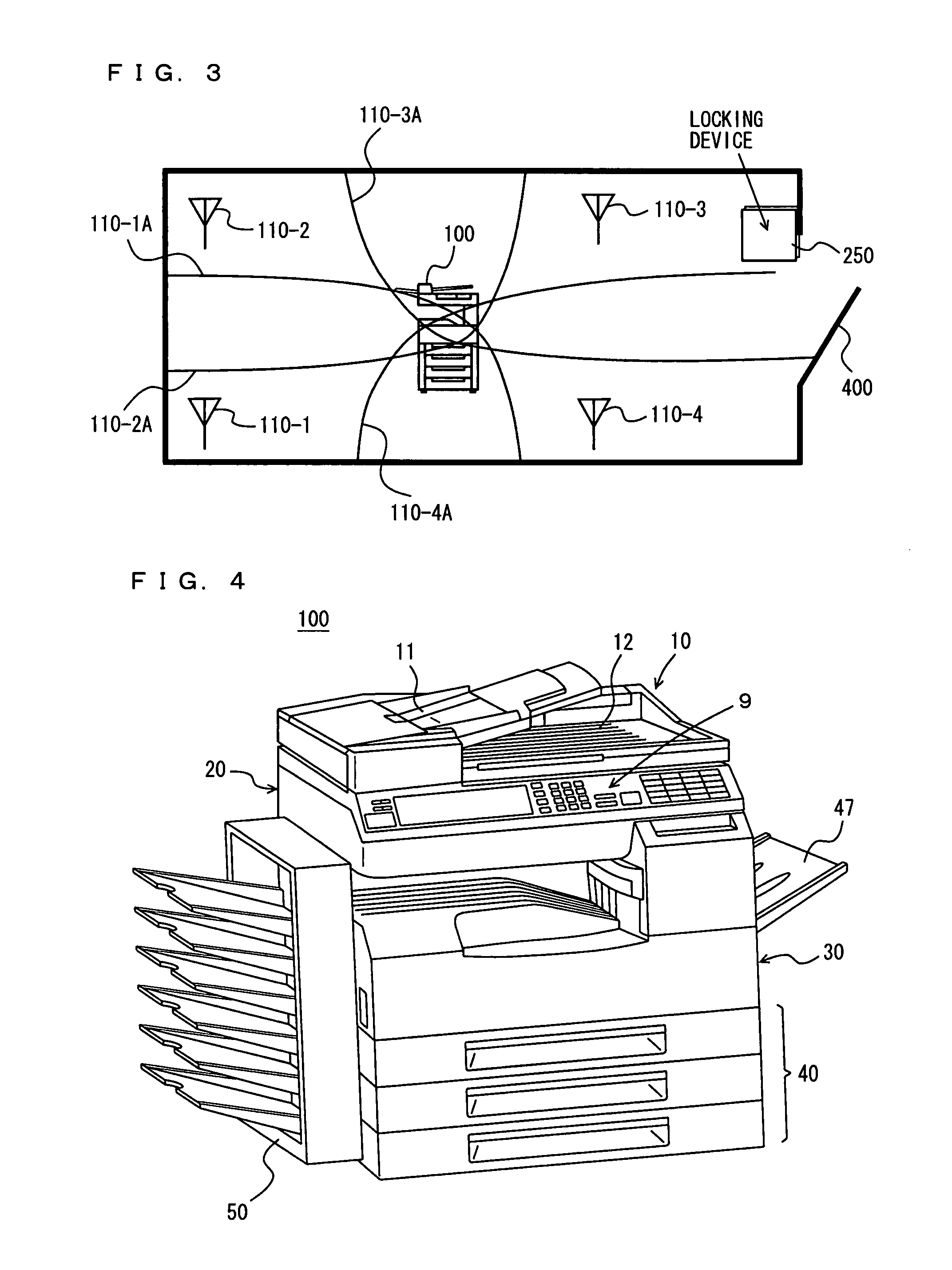
Image monitoring system for preventing confidential information outflow, image monitoring method, and computer image monitoring program stored on a computer readable medium
ActiveUS20080151313A1Visual presentationBurglar alarm by hand-portable articles removalData controlImage formation
In order to prevent a sheet of paper on which confidential information is formed as an image from being taken out, an MFP has a print data accepting portion to accept print data, an image-forming portion to form an image based on the print data onto a sheet of paper having an RFID tag provided with a memory and a data communication portion, an RFID reader / writer control portion to acquire tag identification information for identifying the RFID tag provided by the sheet of paper on which the image is formed based on the print data, a definition data control portion to store definition data including the acquired tag identification information, an external reader communication portion to communicate with a communicable RFID reader, and an abnormal state detecting portion to judge as an abnormal state the case where the external reader communication portion communicating with a communicable RFID reader is detected to be non-communicable with the RFID tag specified by the tag identification information included in the definition data.
Owner:KONICA MINOLTA BUSINESS TECH INC
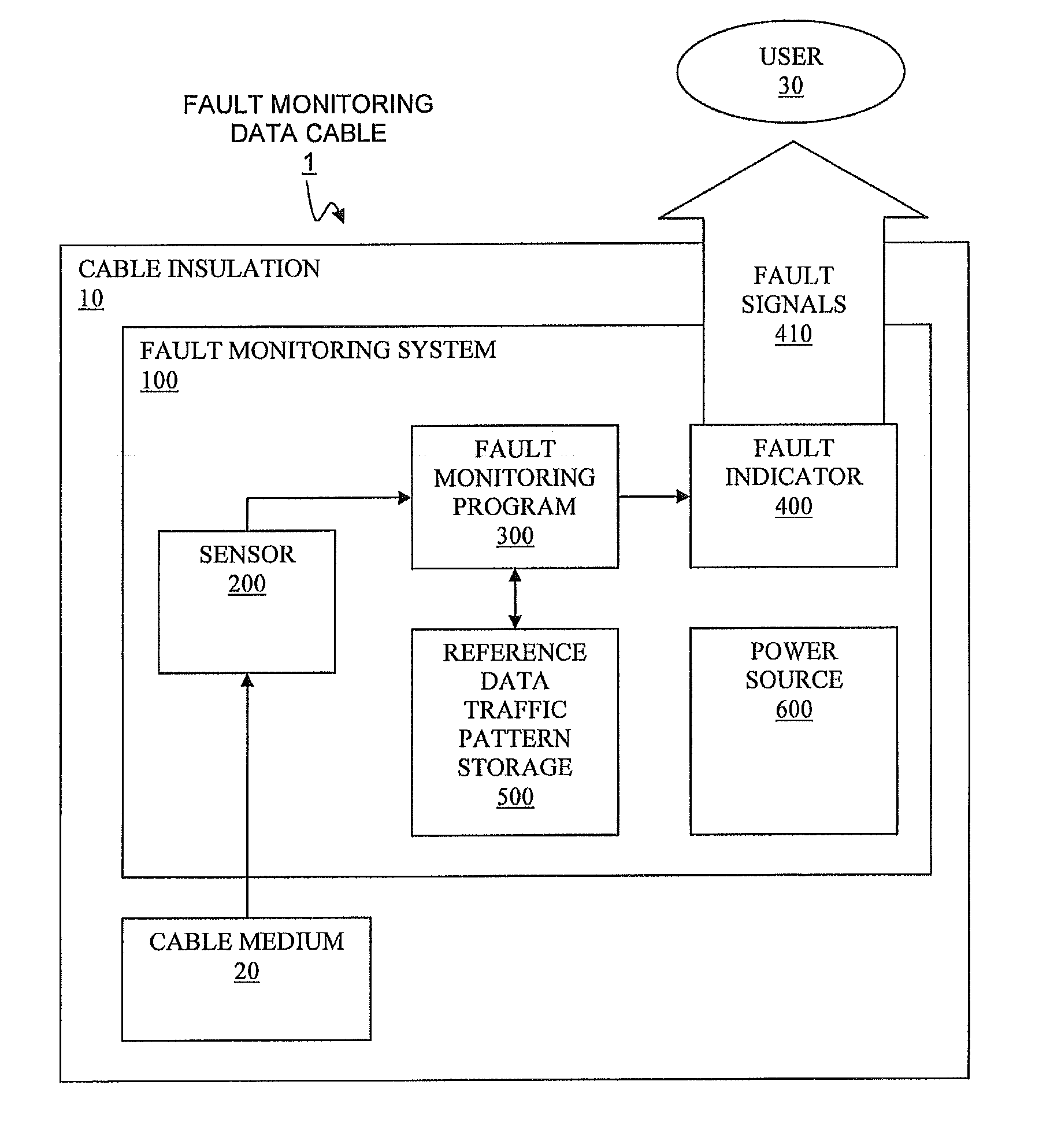
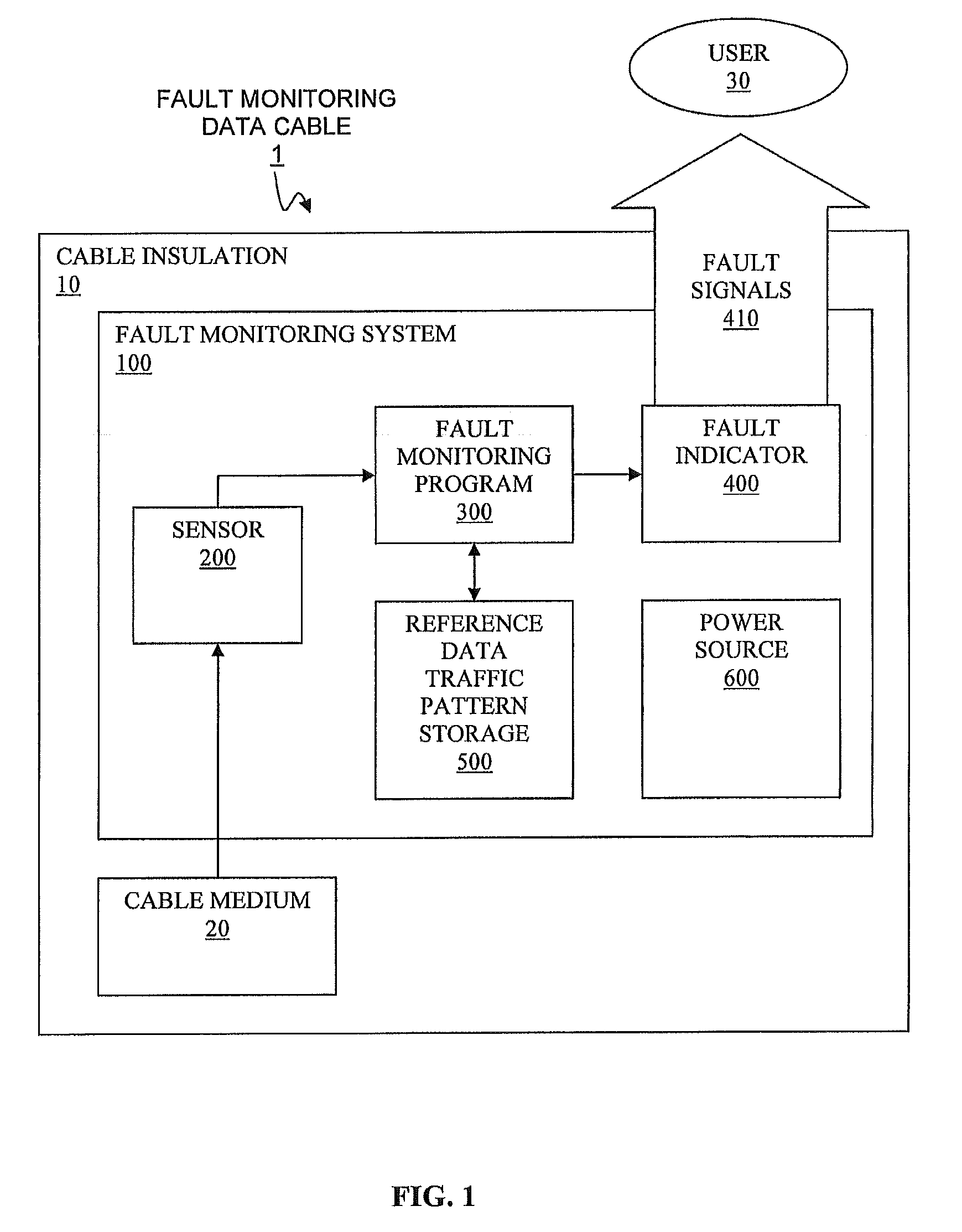
Method and system for monitoring and instantly identifying faults in data communication cables
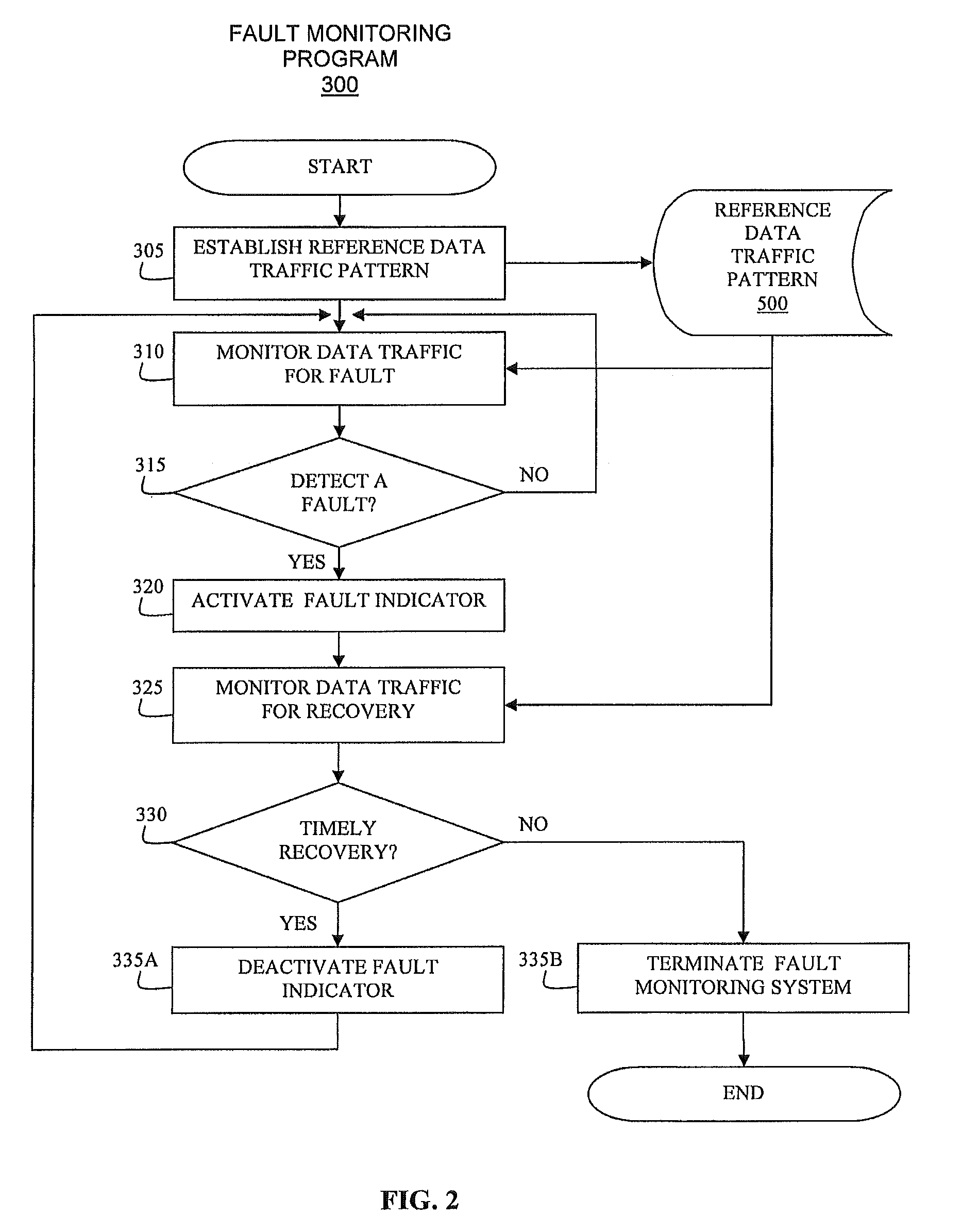
ActiveUS20090063674A1Overcome disadvantagesLaser detailsError preventionFault indicatorRecovery period
A method and an associated system for monitoring and instantly identifying faults in a data communication cable are disclosed. A fault monitoring program learns a reference data traffic pattern communicated through the data communication cable by reading inputs from a sensor. The reference data traffic pattern is stored and is used for determining normalcy of data traffic through the data communication cable. The fault monitoring program monitors for a fault in a data traffic, and, if a fault is detected, activates a fault indicator sending out fault signals to notify users of the fault. If the fault is not recovered within a predefined recovery period, the fault monitoring program deactivates the fault indicator and shuts down a power source for later use of the data communication cable.
Owner:TWITTER INC
Internet use monitoring system and method
A system for monitoring Internet use of a selected computer user includes a remote server and a computer having a monitoring program voluntarily installed thereon by the user communicatively connected to the remote server. The monitoring program is configured to monitor various Internet access activity of the computer user and record the Internet access activity on the remote server. The Internet access activity includes access of at least one Internet protocol from the group consisting of newsgroups, file sharing programs, file transfer programs, chat rooms, peer to peer chats, and electronic mail activity. A method of using a monitoring system includes the steps of a computer user voluntarily installing a monitoring program on a selected computer, recording the Internet access activity, and providing the recorded information to a third party recipient. A report may be provided that includes a variety of information and may include a plurality of portions.
Owner:COVENANT EYES
Method for monitoring a technical system
InactiveUS20050033558A1Simple and and regulationOptimum and simple and cost-effective monitoring and regulationProgramme controlError detection/correctionEmbedded systemMonitoring procedure
A method for monitoring and / or regulating an technical system, in particular of a vehicle, having at least two control units interconnected via a bus system, which have at least one computing element each and which perform monitoring-relevant control procedures and monitoring procedures, a trans-controller software frame, which is implementable on the control unit, in particular in the computing element of the control unit, which monitors and / or regulates the user software of the control unit.
Owner:ROBERT BOSCH GMBH
Local damage monitoring system and method based on extrinsic optical-fiber acoustic emission
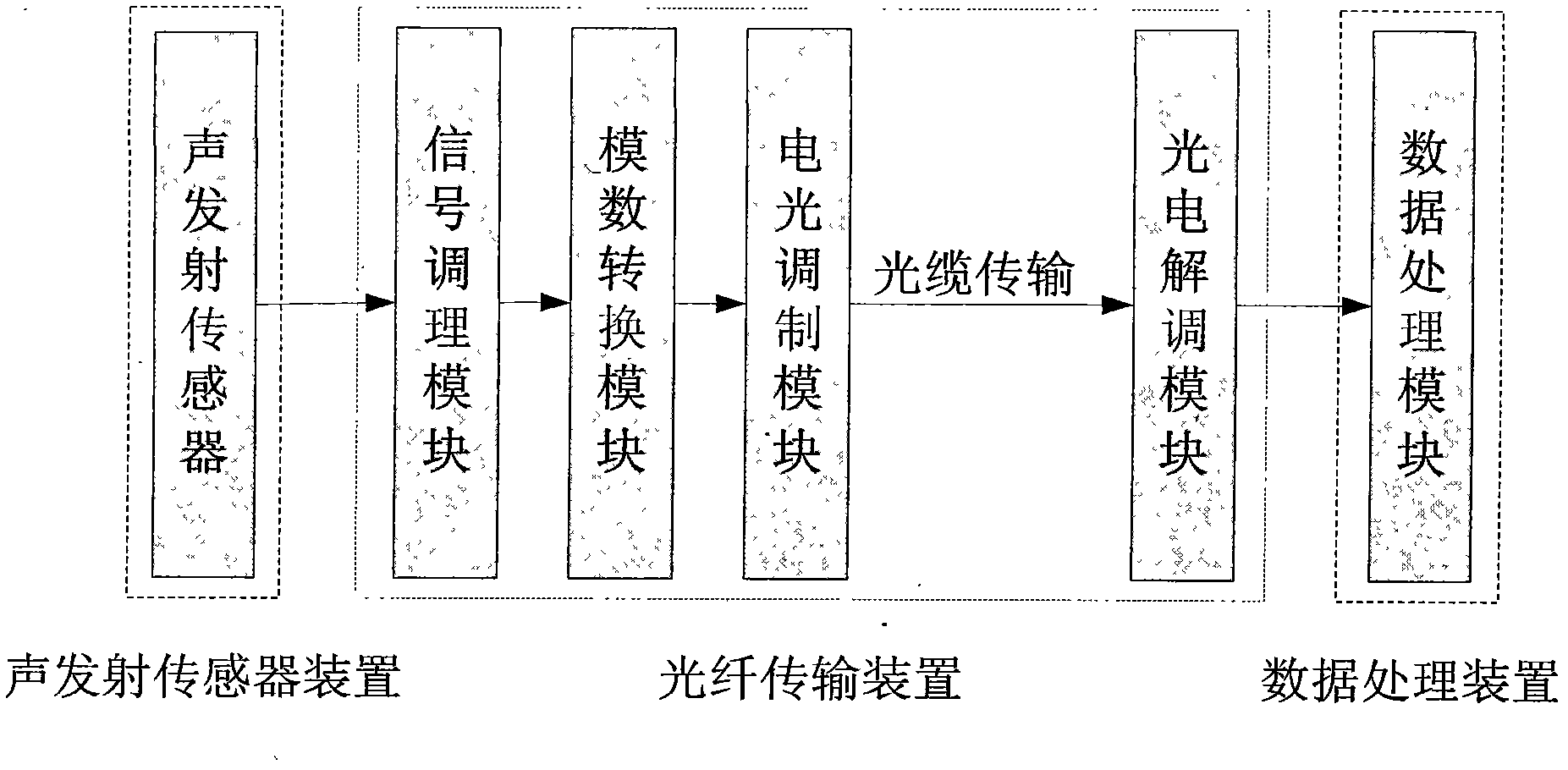
InactiveCN102830176AReduce the impactImprove anti-interference abilityNon-electrical signal transmission systemsMaterial analysis using acoustic emission techniquesEngineeringDigital signal
The invention discloses a local damage monitoring system and local damage monitoring method based on extrinsic optical-fiber acoustic emission. The system comprises an acoustic emission sensor apparatus; an optical-fiber transmission apparatus; and a data processing apparatus. The acoustic emission sensor apparatus is used for monitoring acoustic emission signals of a monitored object and for converting the acoustic signals into electric signals. A sending terminal of the optical-fiber transmission apparatus is connected with the acoustic emission sensor apparatus. Electric signals transmitted from the acoustic emission sensor apparatus are subjected to signal conditioning and analog-to-digital conversion, such that the signals are converted into digital signals. The digital signals are modulated into optical signals, and are transmitted to a receiving terminal through optical fiber transmission. With an optoelectronic demodulation module, the receiving terminal restores the optical signals into electric signals. The data processing apparatus carries out data analysis upon the electric signals containing the acoustic emission signals collected on-site by the acoustic emission sensor apparatus; and damage information is picked up, and a processing result is finally generated. The system and the method provided by the invention are rarely affected by work site complexity and harsh environments, and have high interference resistance. The system and the method are advantaged in accurate monitoring. With the system and the method, distant structure-activity defect monitoring can be implemented, and network monitoring can easily be formed. The system and the method are suitable for distant monitoring, and a monitoring procedure is safe.
Owner:CHINA SPECIAL EQUIP INSPECTION & RES INST
Features
- R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
Why Patsnap Eureka
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Social media
Patsnap Eureka Blog
Learn More Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com