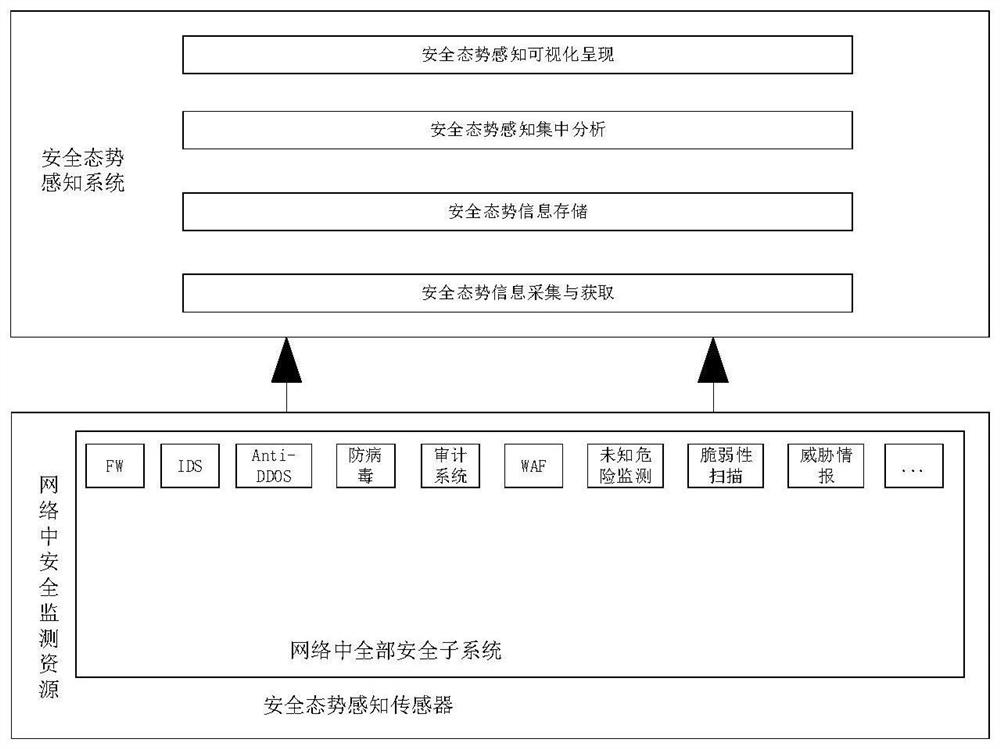
Patents
Literature
45results about How to "Comprehensive security protection" patented technology
Efficacy Topic
Property
Owner
Technical Advancement
Application Domain
Technology Topic
Technology Field Word
Patent Country/Region
Patent Type
Patent Status
Application Year
Inventor
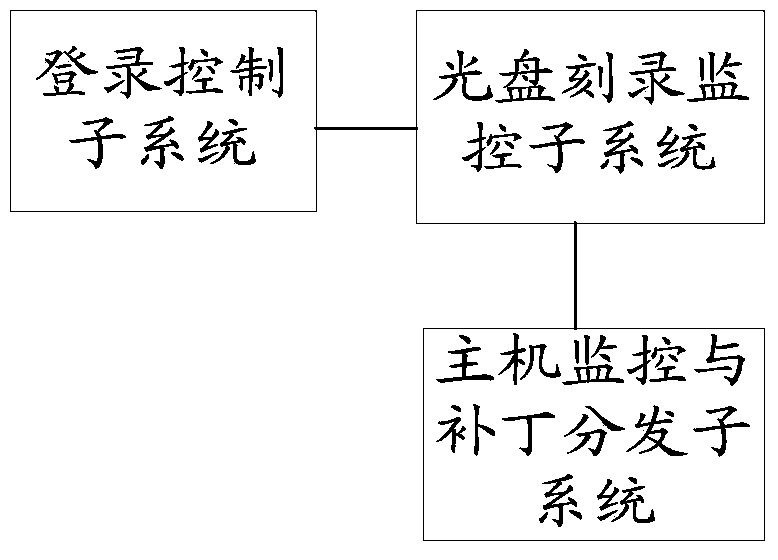
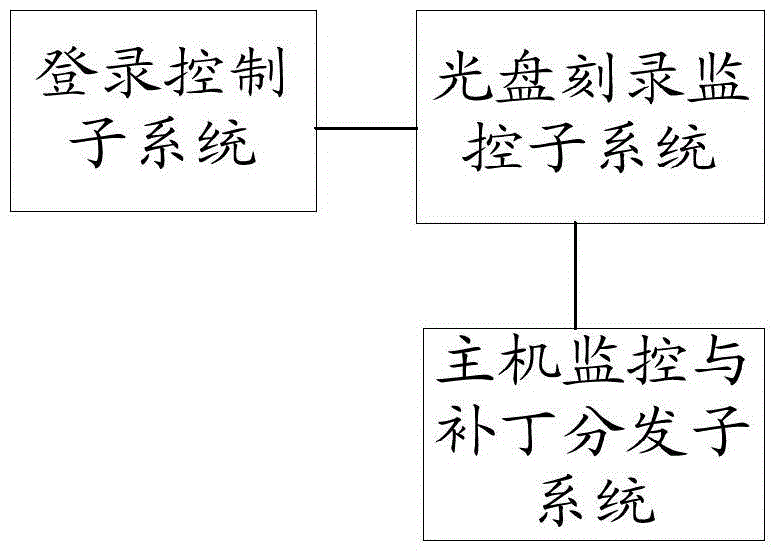
Security defending system for single host
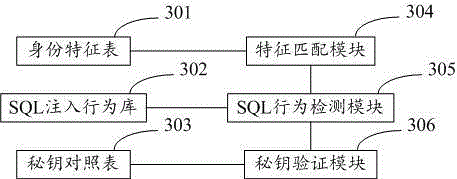
ActiveCN103413083AComprehensive Security ProtectionImprove the protective effectUser identity/authority verificationDigital data authenticationCompact discSecurity monitoring
The invention relates to the field of security defense of a single host and particularly relates to a security defending system for a single host. The security defending system comprises a login control subsystem, a main engine monitoring and patch distributing subsystem and a compact disc recording monitoring subsystem, wherein the login control subsystem is used for controlling a login process of a user login single host operation system by a USBkey (Universal Serial Bus key); the main engine monitoring and patch distributing subsystem is used for carrying out security monitoring on an operation process of the single host and managing patch distribution; the compact disc recording monitoring subsystem is used for carrying out the security monitoring on compact disc recording. The security defending system provided by the invention can comprehensively carry out security defense on the single host and the defending performance is preferable.
Owner:水利部信息中心 +1
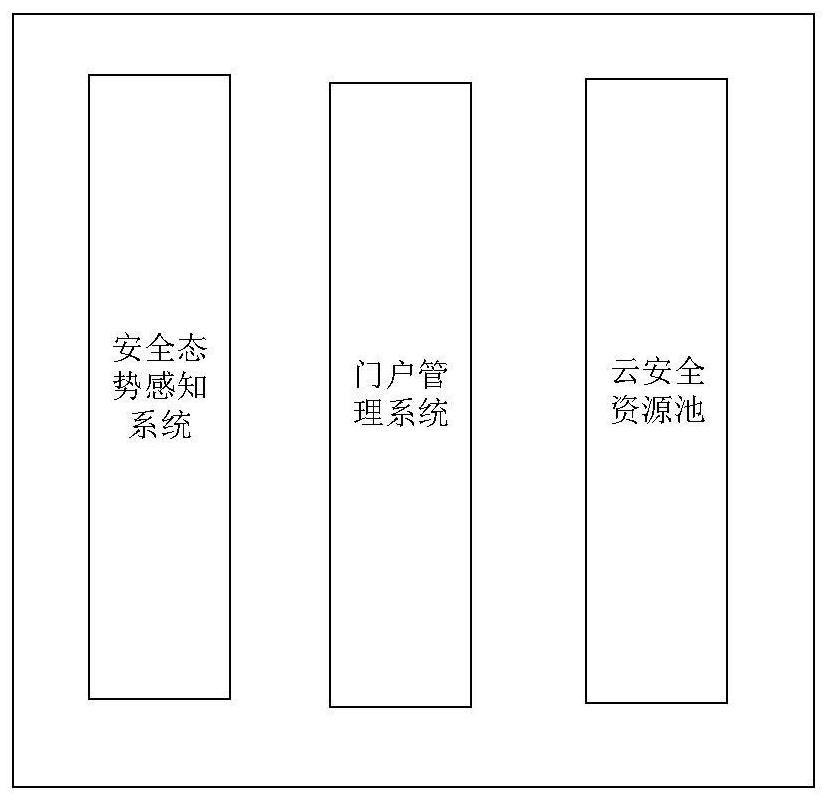
Tenant-based security capability and security service chain management platform
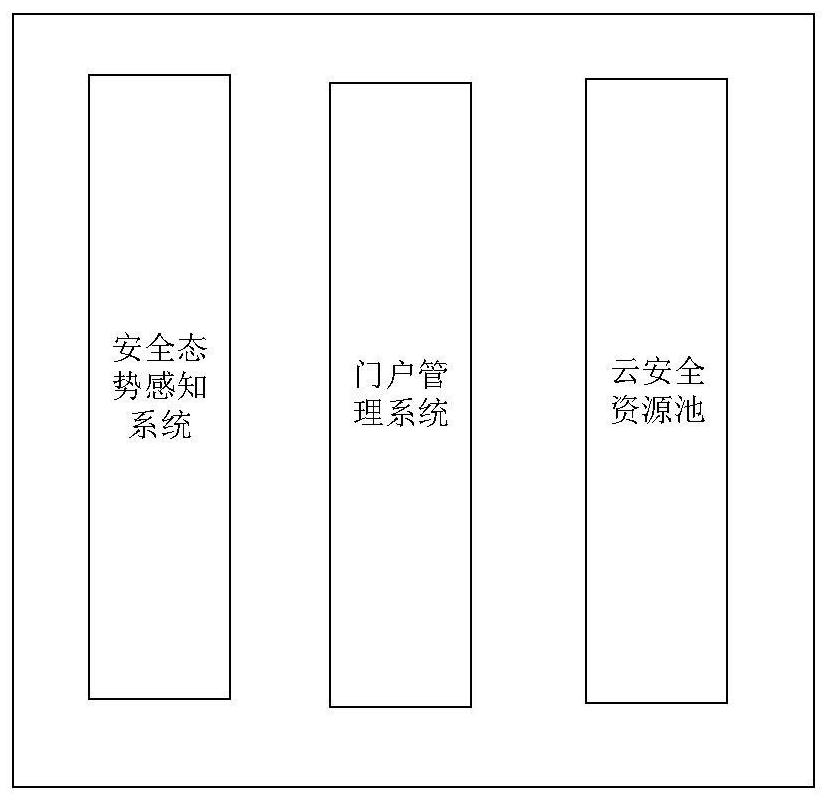
ActiveCN112291232AEfficient and reliable storageEfficient retrievalDatabase distribution/replicationPlatform integrity maintainanceResource poolWeb application
The invention discloses a lessee-based security capability and security service chain management platform, and relates to the field of network security. The system comprises a security situation awareness system, a portal management system and a cloud security resource pool; a security situation awareness system is used for collecting security element information of tenants in the platform, analyzing the collected security element information to generate a corresponding security situation prediction result, and generating and executing a corresponding security disposal strategy based on the security situation prediction result; a portal management system is used for management personnel to log in the portal management system to manage tenants in the platform and used for the tenants to login the portal management system to manage resources of the tenants; a cloud security resource pool comprises a detection probe system, a service auditing system, a web application protection system and a vulnerability scanning system. The platform is utilized to perform the same management on the tenants and the network, so the information security and the network security of the tenants are ensured, and the security of private network use in a private network platform is improved.
Owner:中国联合网络通信有限公司深圳市分公司
Power grid industrial control security collaborative monitoring method and device based on deep protocol analysis
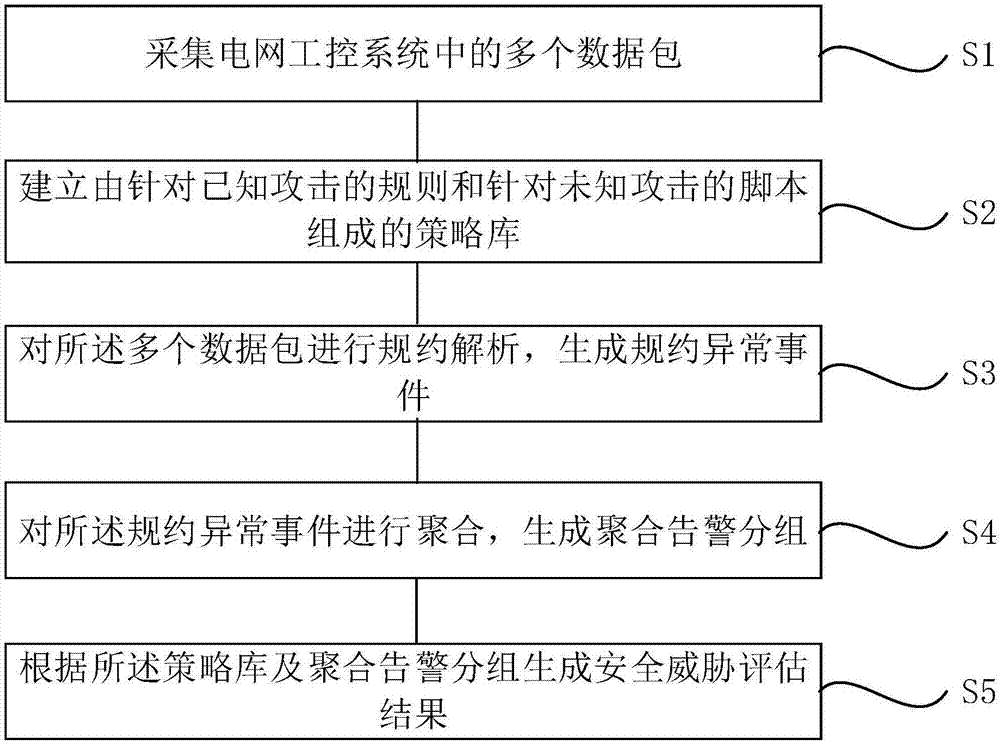
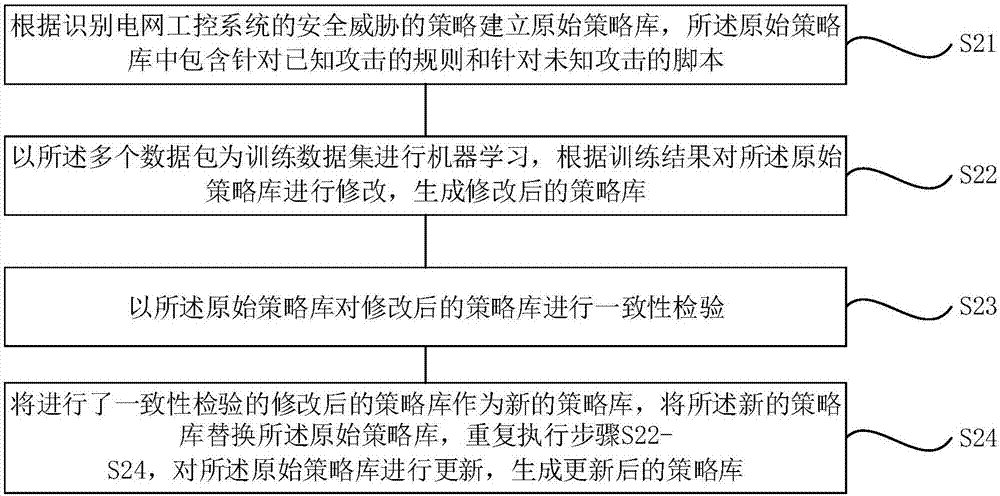
ActiveCN107465667AComprehensive security protectionImprove safety monitoring accuracyTransmissionPower gridIndustrial control system
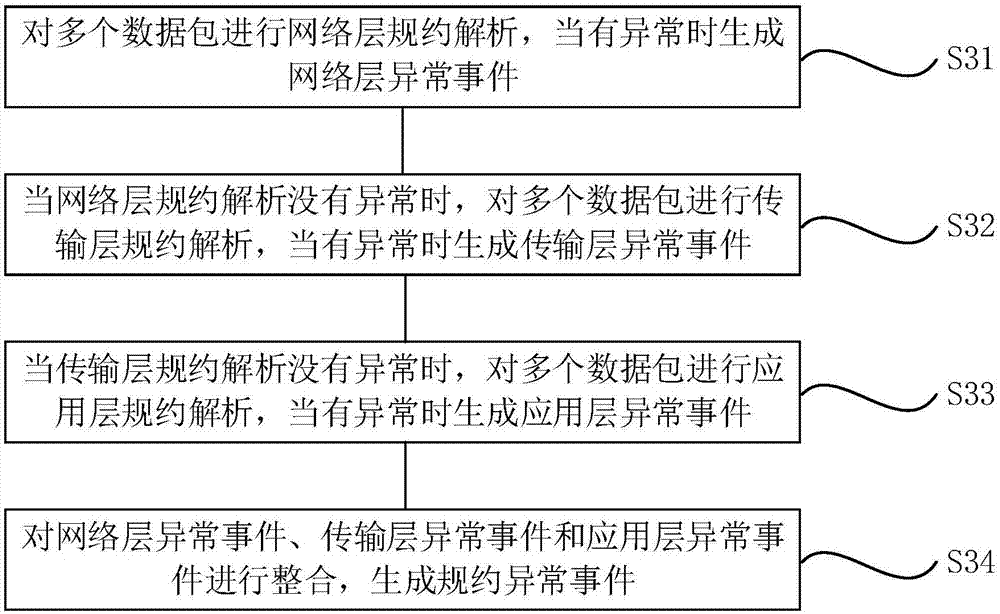
The invention provides a power grid industrial control security collaborative monitoring method and device based on deep protocol analysis. The power grid industrial control security collaborative monitoring method comprises the steps of collecting a plurality of data packets in a power grid industrial control system; establishing a strategy library composed of rules for known attacks and scripts for unknown attacks; carrying out protocol analysis on the plurality of data packets to generate protocol abnormity events; aggregating the protocol abnormity events to generate aggregated alarm groups; and generating a security threat assessment result according to the strategy library and the aggregated alarm groups. According to the method and the device, security threats is effectively identified, positioned and assessed; comprehensive protection is realized; the security monitoring precision of the power grid industrial control system is improved; and the security monitoring expandability is improved.
Owner:GLOBAL ENERGY INTERCONNECTION RES INST CO LTD +3
Mobile information multi-layer network secure auditing system
InactiveCN101242658AComprehensive Security ProtectionReal-time protectionRadio/inductive link selection arrangementsSecuring communicationInformatizationInformation security
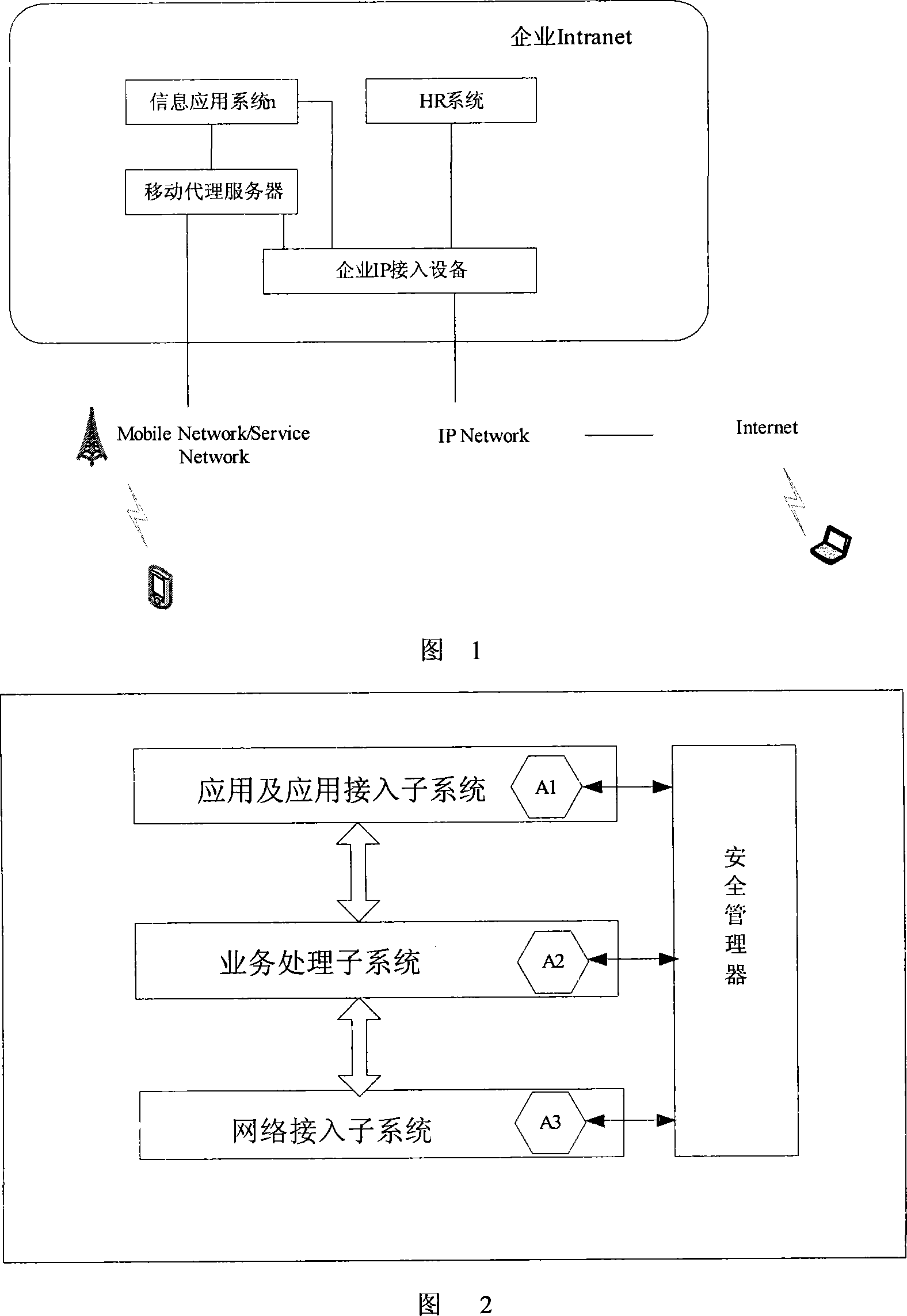
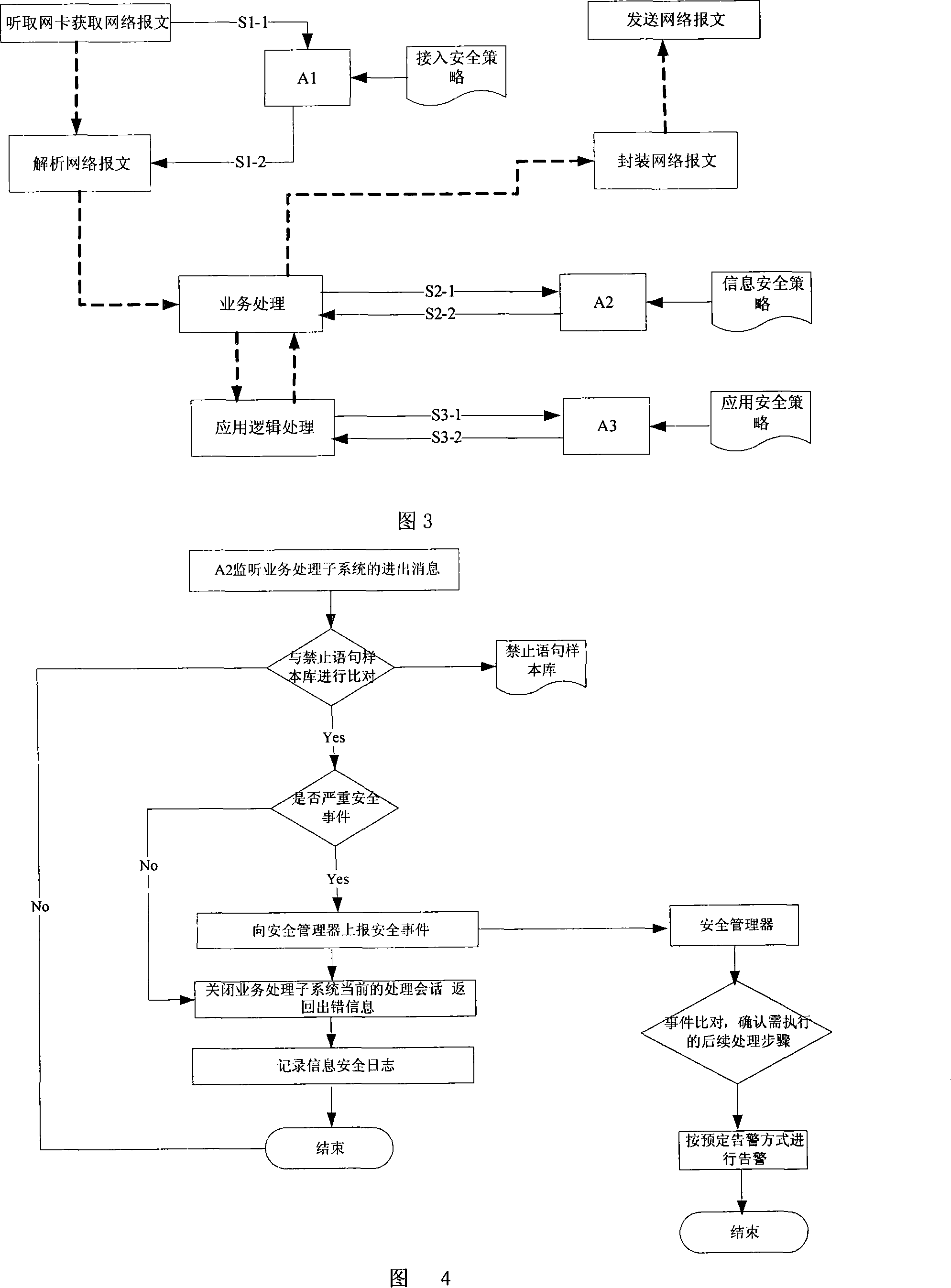
The invention relates to a mobile information multi-layer network security audit system, which pertains to fields of mobile informatization and information security technology. The system includes mobile proxy server, security manager and security audit proxy module; subsystems of mobile proxy server comprises proxy module of access, processing and application security audit which are communicating with security manager. Comparing with conventional technique, the invention provides controllable multi-layer enterprise network security audit mechanism under mobile informatization scenarios, can implement definition, execution of security rules, security log and security alarm, and protects inner resource of the enterprise depending on the mechanism.
Owner:金柘苗 +1
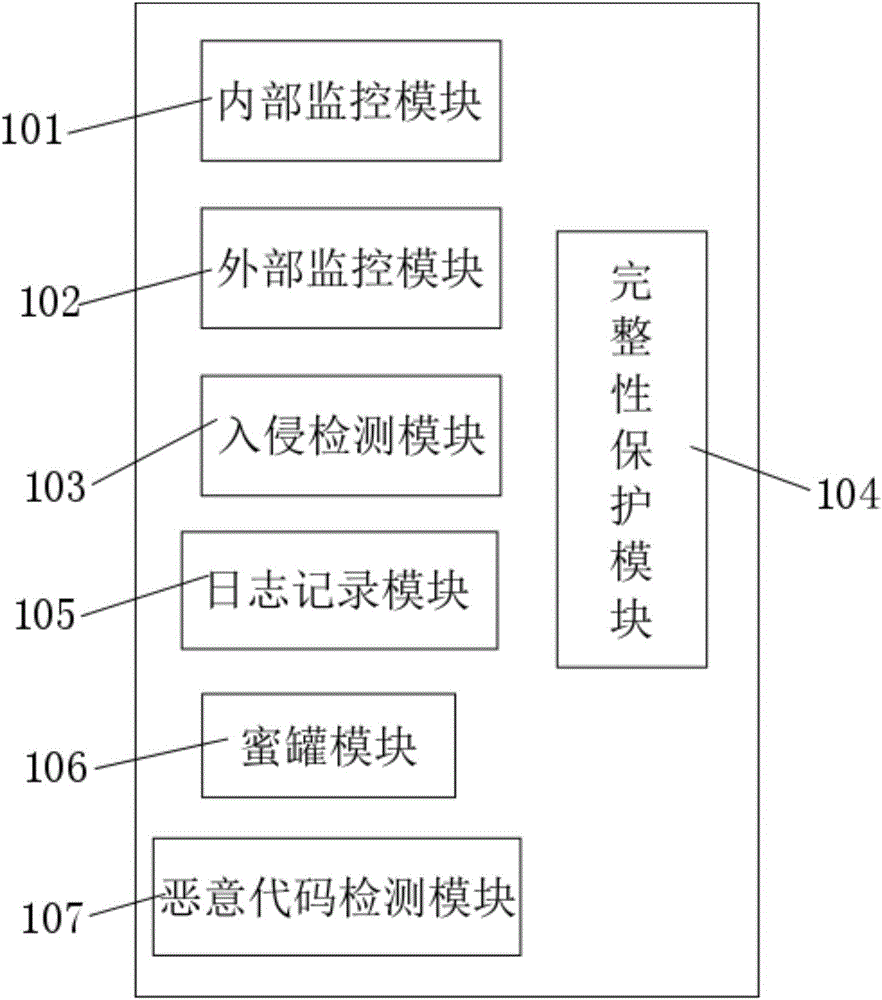
Virtual machine anti-escape device
InactiveCN106778257AReduce performance overheadImprove versatilityHardware monitoringPlatform integrity maintainanceVirtual machineHost machine
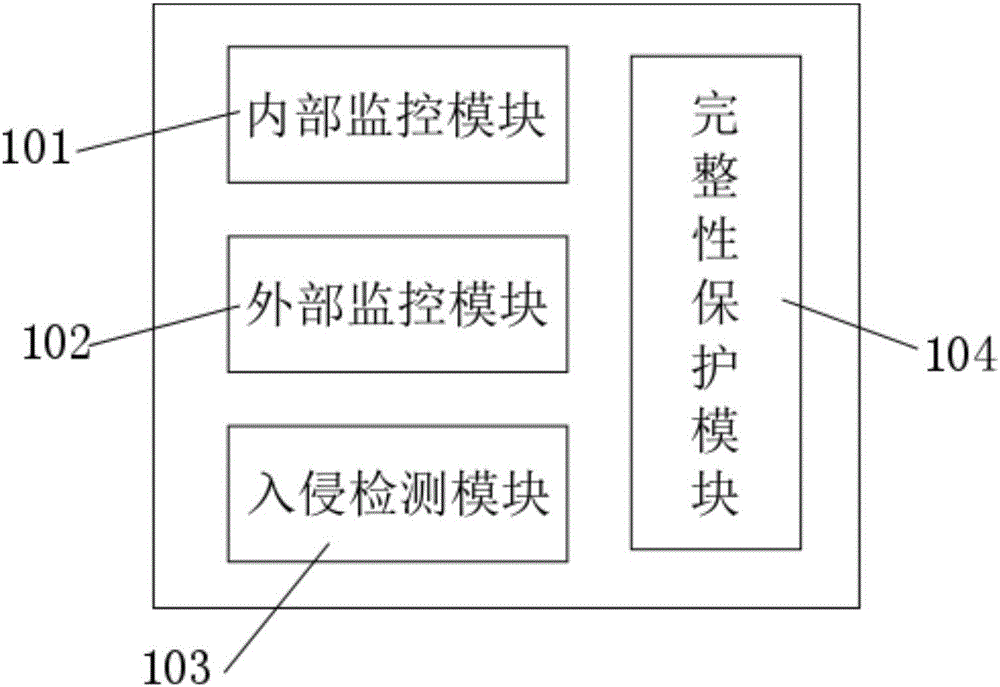
The invention discloses a virtual machine anti-escape device and belongs to the technical field of the virtual machine security. The device includes an internal monitoring module, an external monitoring module, an intrusion detection module, an integrity protection module and the like. Comprehensive, high-efficiency and high-level safety protection can be provided for a virtual machine and a host machine, the occurrence possibility, influences and harm of a virtual machine escape attack are thus largely reduced, and the device is an important improvement to the prior art.
Owner:BEIJING CHINA POWER INFORMATION TECH +3
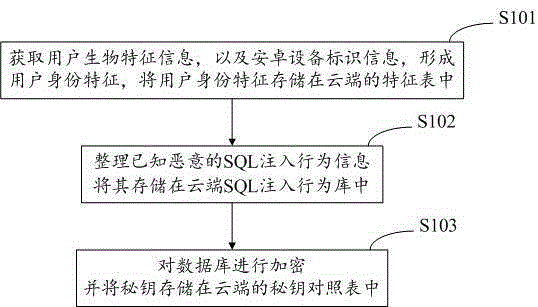
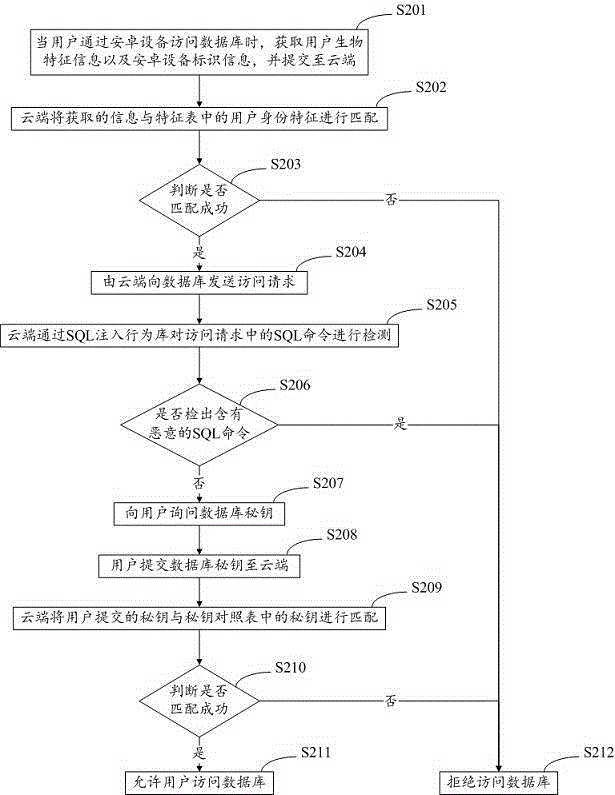
Cloud computing-based android database security protection method and system
ActiveCN105989270AEnsure high efficiencyGuarantee stabilityDigital data protectionDigital data authenticationSQL injectionComputer terminal
The invention proposes a cloud computing-based android database security protection method and system. A security mechanism of database protection is realized based on a cloud terminal by virtue of a cloud computing technology; and three-layer protection of a database is realized through a user bio-feature identification-based authentication method, an SQL injection protection method and a hybrid encryption algorithm. According to the cloud computing-based android database security protection method and system, the deficiencies of lack of an SQL injection detection mechanism and difficulty in ensuring performance and efficiency in an existing android platform database protection technology are made up for and the security protection is realized based on the cloud terminal, so that the load pressure of a local mobile terminal is effectively reduced, the device performance is ensured, the security protection of the android database is perfecter and more reliable, and the high efficiency and stability of the security protection are ensured.
Owner:WUHAN ANTIY MOBILE SECURITY
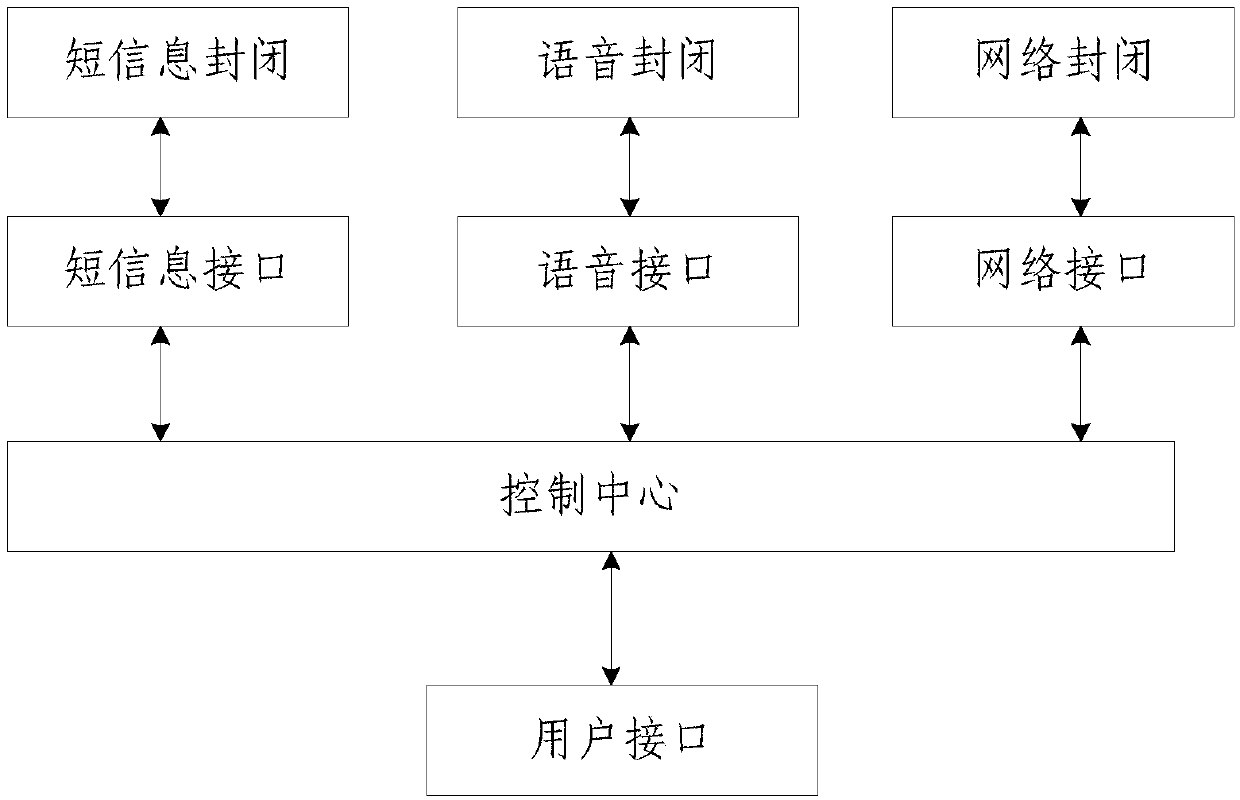
Computer network safeguard system
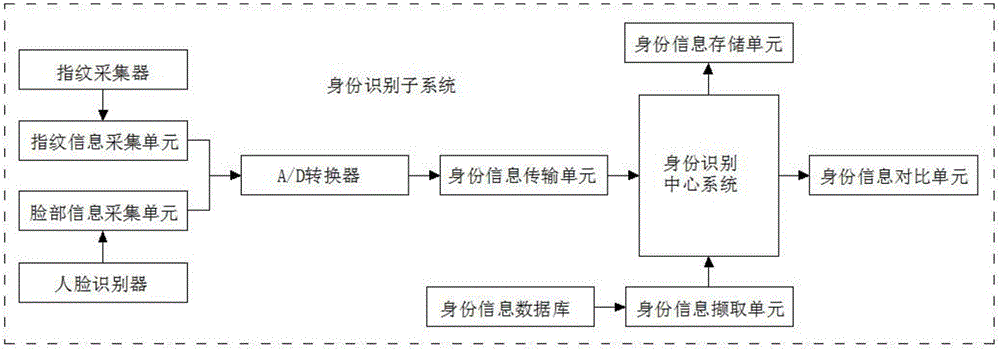
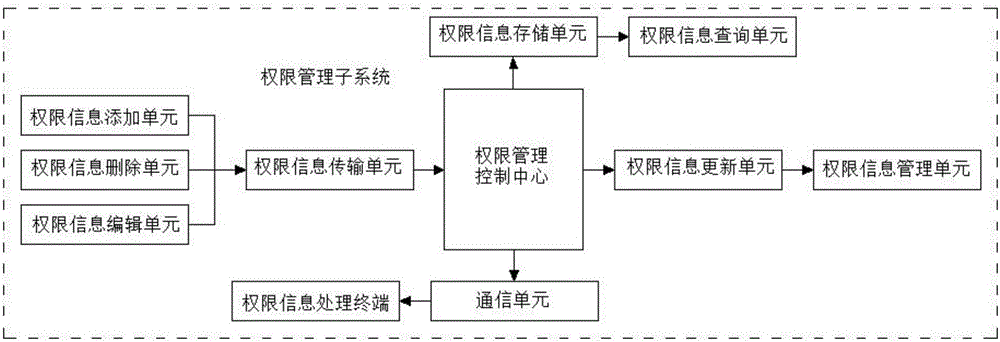
ActiveCN106503524ARealize self-testAchieve self-healingDigital data authenticationPlatform integrity maintainanceUSBVirus
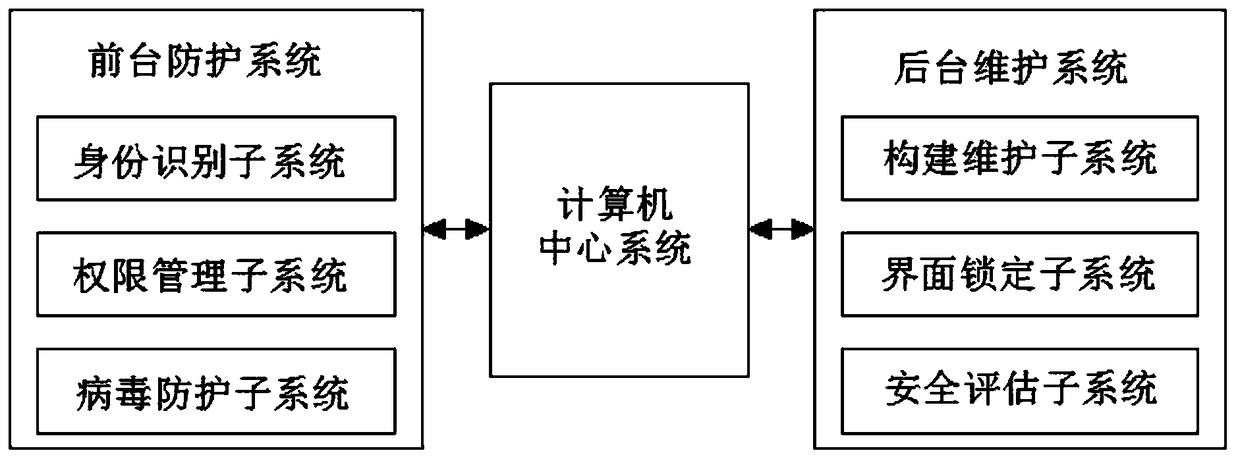
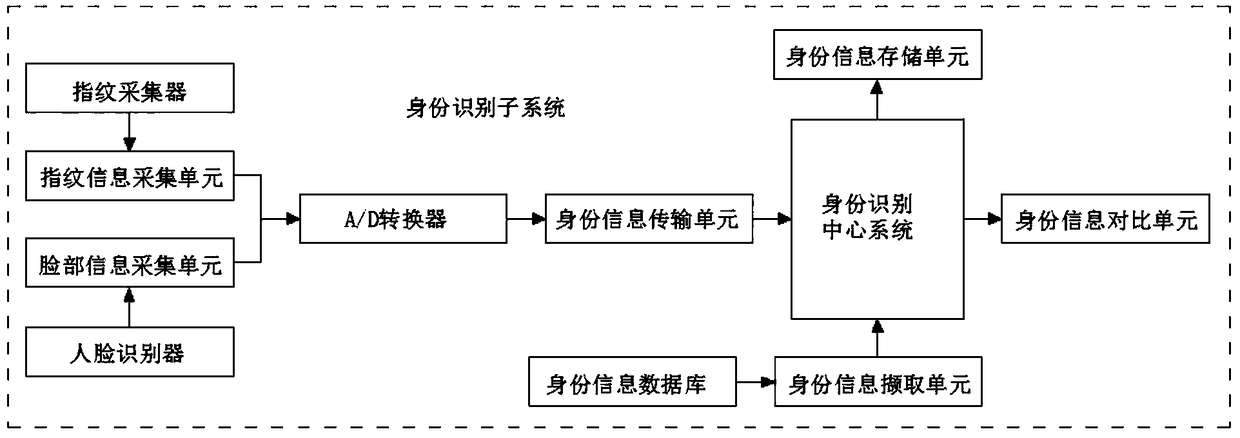
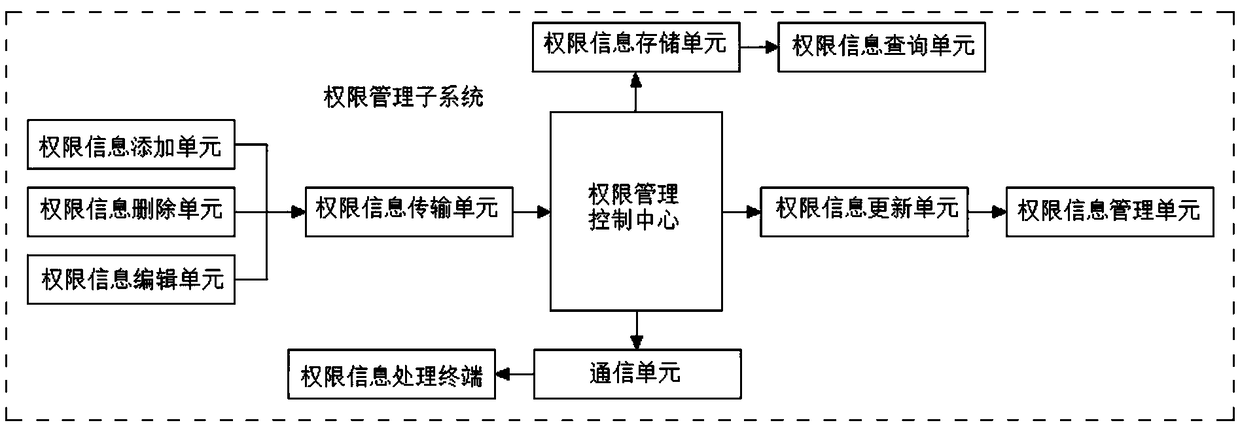
The invention discloses a computer network safeguard system in the technical field of computer safety systems. The computer network safeguard system comprises a foreground safeguard system and a background maintenance system, wherein the foreground safeguard system and the background maintenance system are bidirectionally and electrically connected through a computer center system. The foreground safeguard system comprises an identity identification subsystem, an authority management subsystem and a virus defense subsystem. The background maintenance system comprises an establishment maintenance subsystem, an interface locking subsystem and a safety evaluation subsystem. The virus defense subsystem of the computer network safeguard system can check files in a computer and remove viruses after virus behavior analysis, and the interface locking subsystem achieves USB interface outage and power supply closing when the system is not used. The computer network safeguard system prevents computer file leakage, is high in safeguard performance and achieves all-around computer network safeguard.
Owner:EASTERN LIAONING UNIV
Security policy configuration method and device
InactiveCN110677396AComprehensive security protectionTimely automatic updateTransmissionDomain nameWeb service
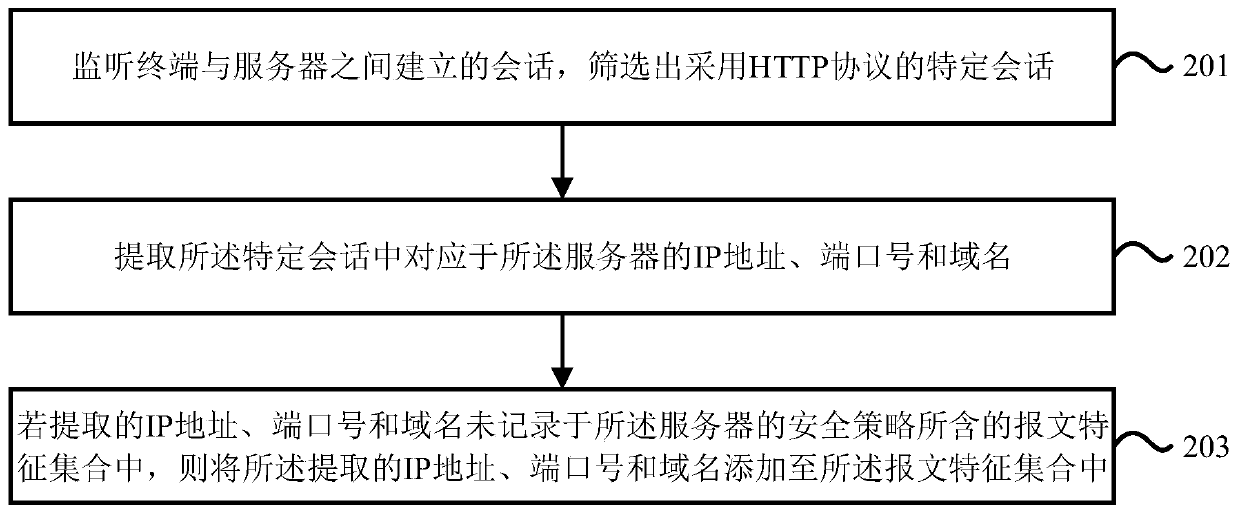
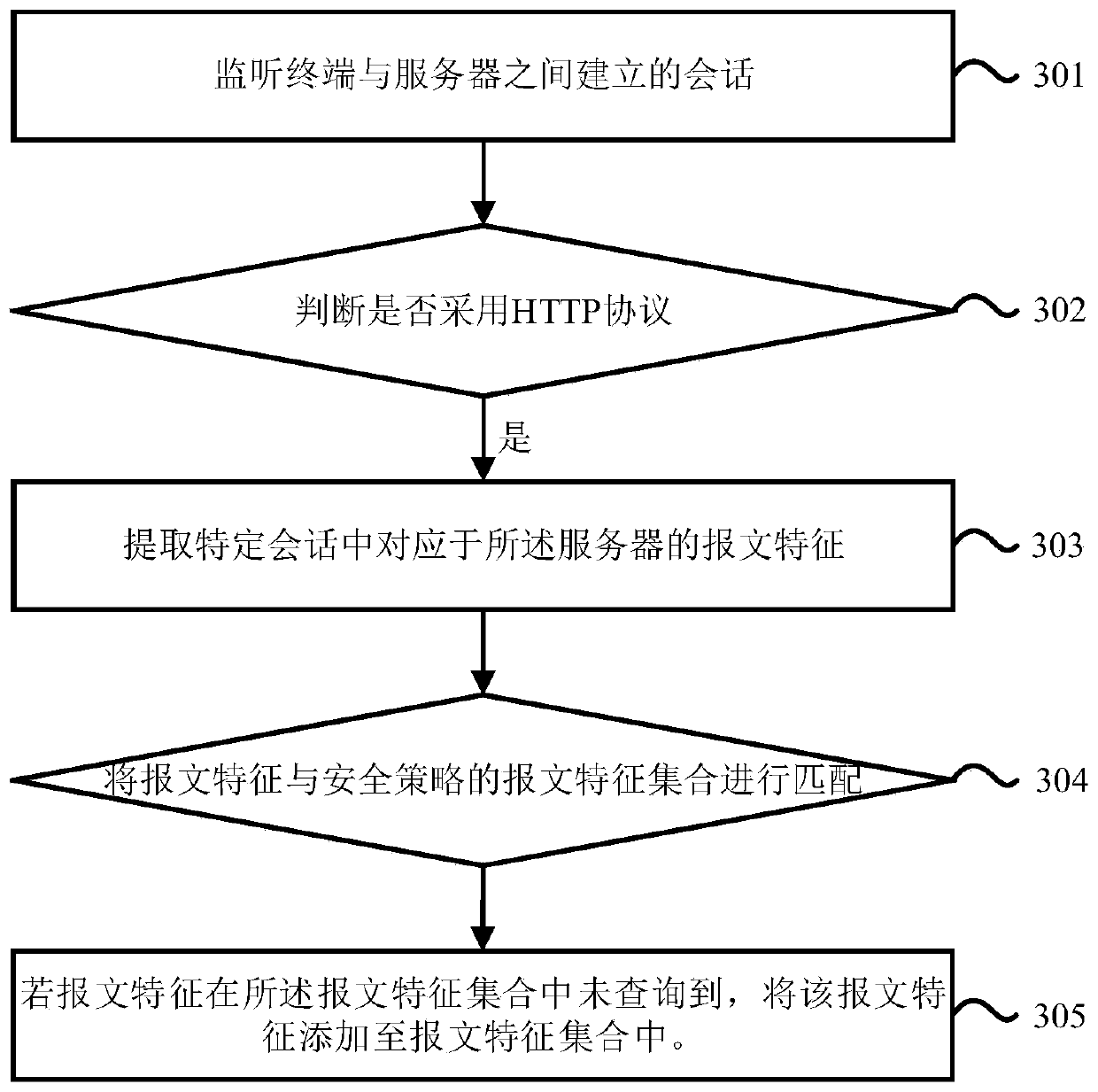
The invention provides a security policy configuration method and device, which are applied to network security equipment. The method comprises steps of screening out a specific session adopting an HTTP by monitoring a session established between a terminal and a server; extracting an IP address, a port number and a domain name corresponding to the server in the specific session; and if the extracted IP address, the extracted port number and the extracted domain name are not recorded in a message feature set contained in a security policy of the server, adding the extracted IP address, the extracted port number and the extracted domain name into the message feature set. By means of the technical scheme, the message feature set contained in the security policy of the server can be automatically updated, it is guaranteed that the security policy covers all Web services, and comprehensive security protection is provided for the server.
Owner:HANGZHOU DPTECH TECH
Computer security apparatus and method
ActiveCN101504708AThorough security protectionComprehensive security protectionInternal/peripheral component protectionProgram loading/initiatingData linesMotherboard
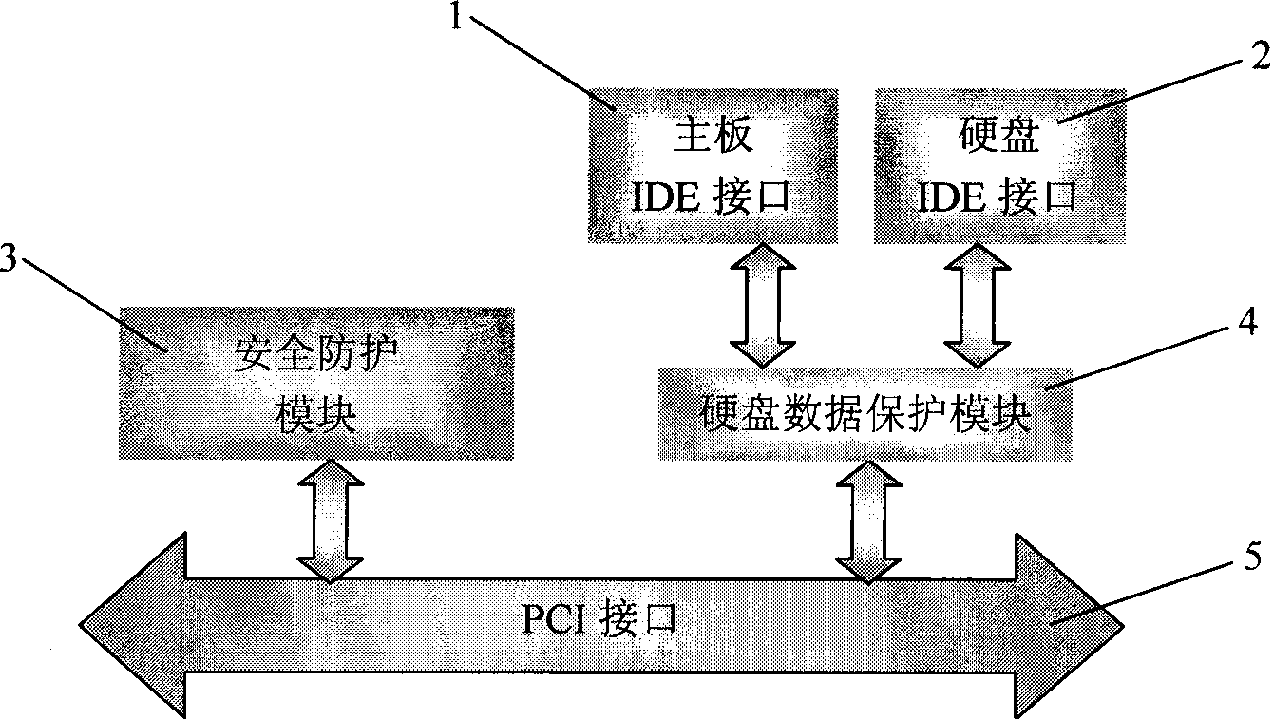
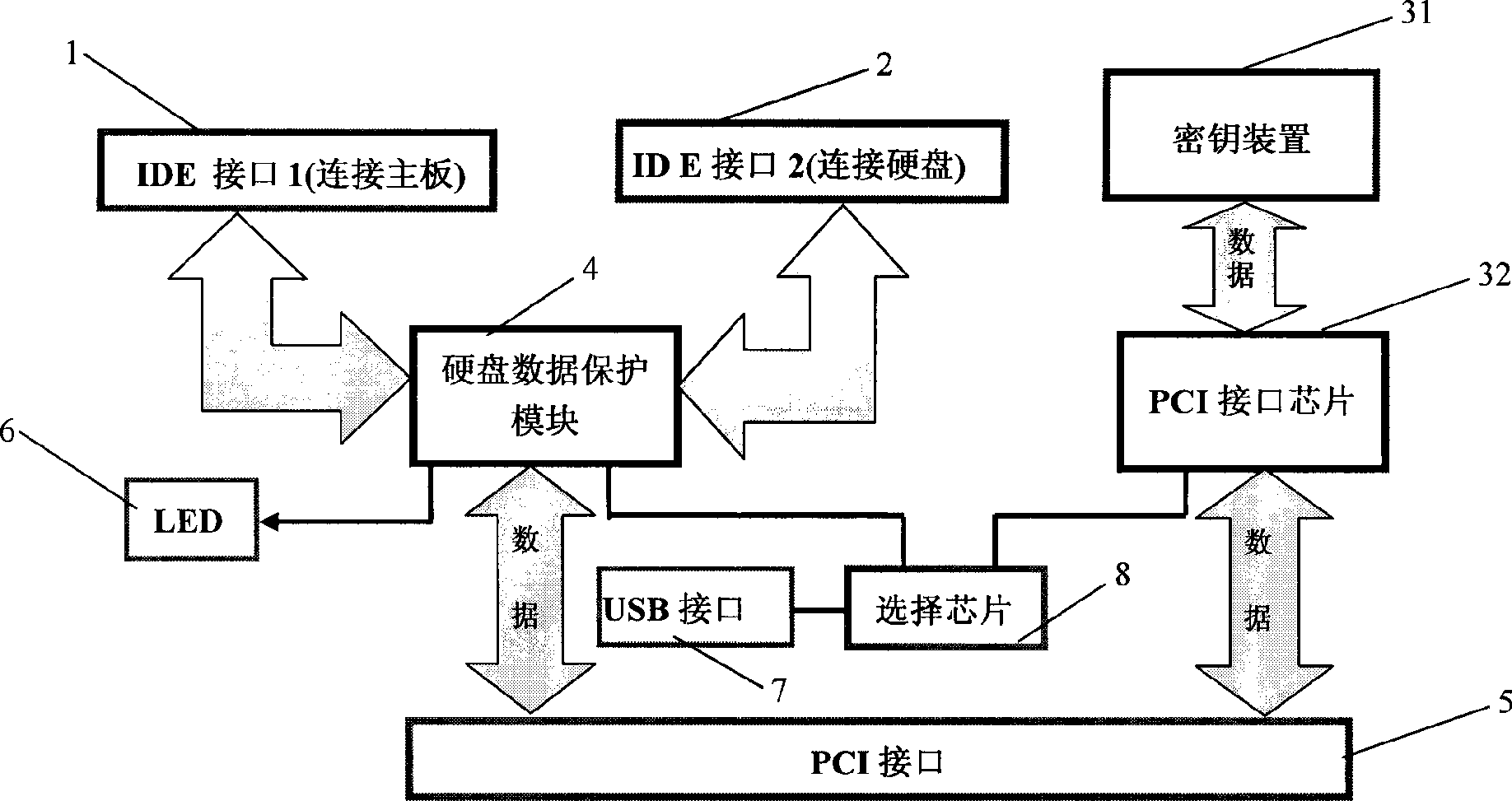
The invention discloses a computer security protection device and a method thereof. The device comprises a motherboard interface connected with a computer motherboard, a hard disk interface connected with a computer hard disk, and a hard disk data protection module connected between the motherboard interface and the hard disk interface. The hard disk data protection module performs physical interception on hard disk data, and modifies an IDE data wire which originally is connected to the hard disk from the computer motherboard into the IDE data wire which passes through the hard disk data protection module and then is connected to the hard disk, thereby realizing the protection processing on all the hard disk data including a computer operating system.
Owner:北京鼎普科技股份有限公司
Mobile energy storage container for intelligent fire control
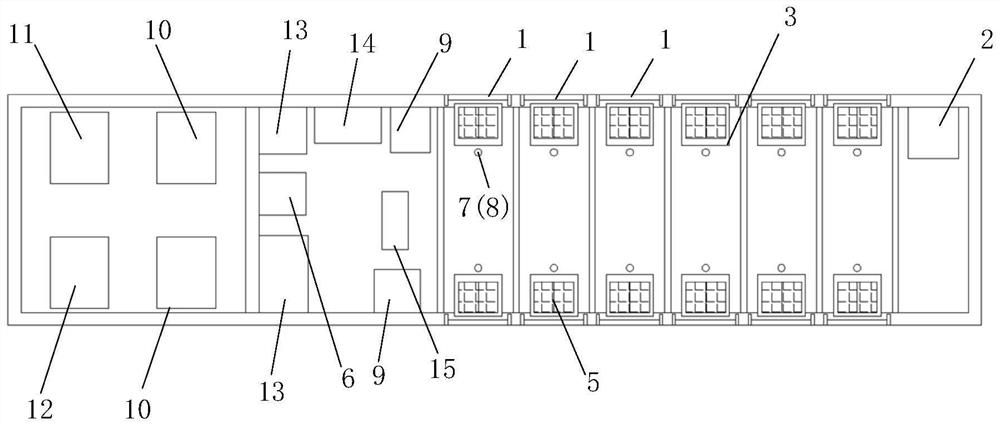
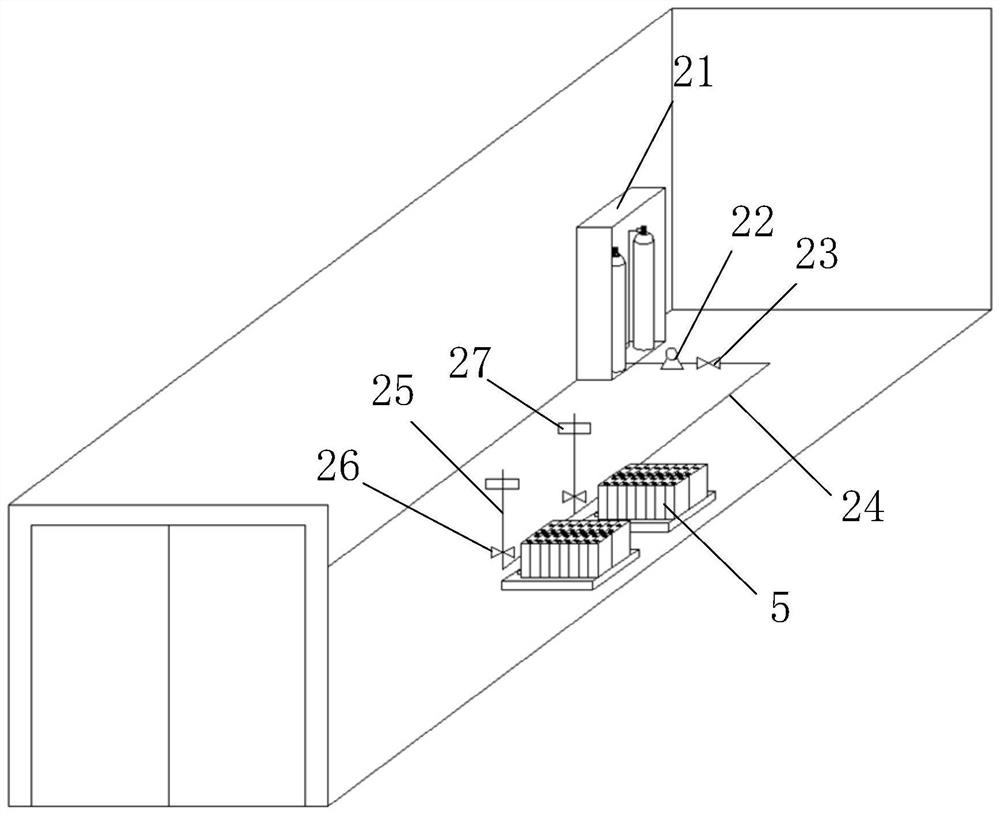
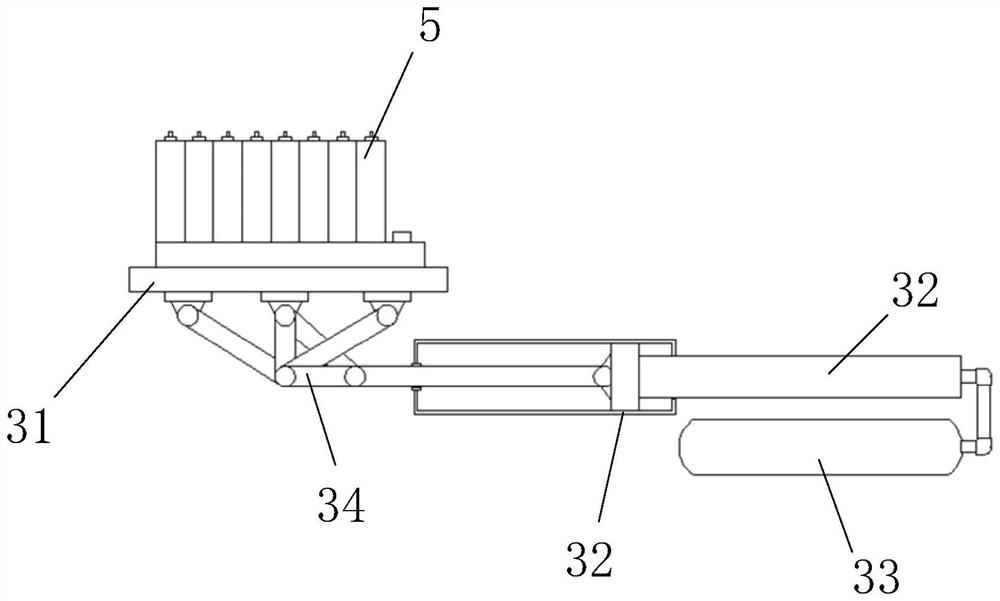
PendingCN114374008APrevention and control placementComprehensive security protectionBattery isolationSecondary cellsElectrical batteryFire control
The invention discloses an intelligent fire-fighting control mobile energy storage container which is characterized by comprising a container body, a distributed fireproof rolling shutter door, a solution atomization system, a temperature smoke sensing monitoring system and a battery pop-up device are arranged in the container body, and the intelligent fire-fighting control mobile energy storage container further comprises a battery thermal management system, a three-dimensional infrared imaging temperature measuring device and a fire-fighting suppression unit; according to the technical scheme, the area where the thermal runaway battery pack is located is accurately positioned through the temperature and smoke sensing monitoring systems distributed in multiple areas, the area where the dangerous battery pack with faults is located is accurately positioned through the temperature and smoke sensing monitoring systems, and the dangerous battery pack is popped out of the container body through the battery popping device. And the dangerous battery pack and the container body are physically isolated through the fireproof rolling shutter door, and the fireproof rolling shutter door is extinguished and cooled by utilizing the heat exchange characteristics of heat absorption after solution vaporization and wide coverage after atomization. Electrical fire and large-space fire prevention and control in the container energy storage station are considered, and meanwhile safety protection is more comprehensive.
Owner:福建华工智能设备有限公司
Safety management system
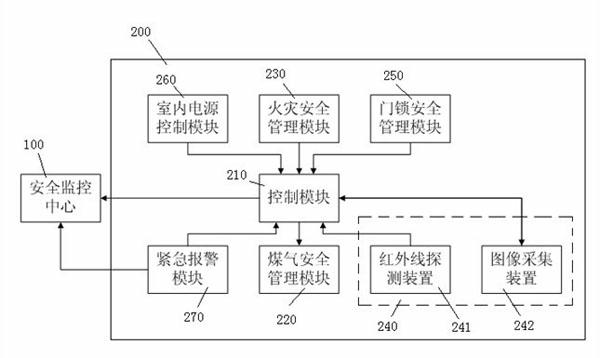
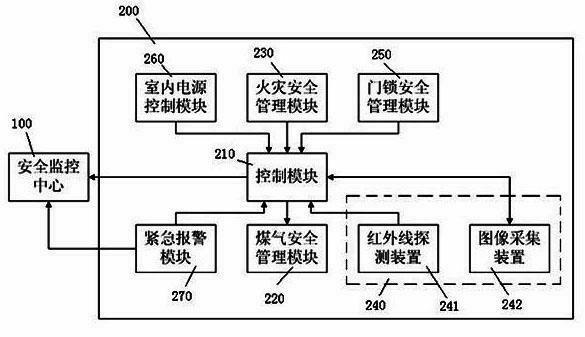
InactiveCN102682566AComprehensive security protectionProtection securityAlarmsData transmissionFire safety
The invention discloses a residence safety management system, comprising a plurality of user safety management units and a safety monitoring center connected with the user safety management units via network. The user safety management unit comprises a control module, and a coal gas safety management module, a fire safety management module, an indoor personnel safety management module, a door lock safety management module and an indoor power supply control module, which are respectively in data transmission with the control module. The residence community safety management system provided by the invention can comprehensively protect indoor safety of the residents, properly handle the exceptional conditions in time and notify the community safety monitoring center, so that the community security guards can know the indoor safety problem of the residents in time, thereby wining precious time for handling dangerous cases and rescuing people in time.
Owner:苏州奇可思信息科技有限公司
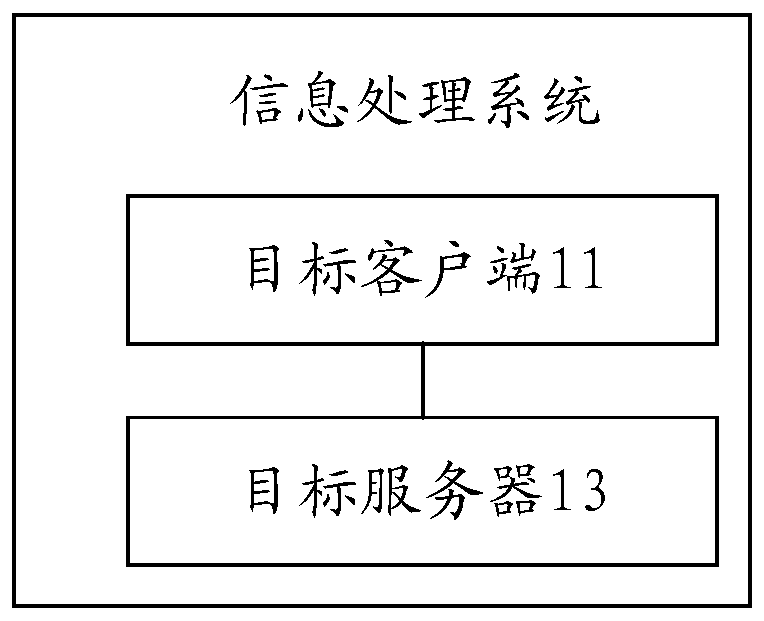
An information processing system and a trusted security management system
ActiveCN110677483AAccurate safety protectionIncrease interest in useDigital data protectionTransmissionInformation handling systemSafety management systems
The invention discloses an information processing system and a trusted security management system. The information processing system comprises a target client and a target server end; the target server end is used for establishing communication connection with the target client registered at the target server end, sending trusted protection software to the target client and processing related information of the target client after the target client starts the trusted protection software; the trusted protection software is used for carrying out active security protection on the target client; and the target client is used for receiving and installing the trusted protection software, and performing security protection on the trusted protection software based on the pre-configured permissioninformation in the operation process of the trusted protection software.
Owner:BEIJING KEXIN HUATAI INFORMATION TECH
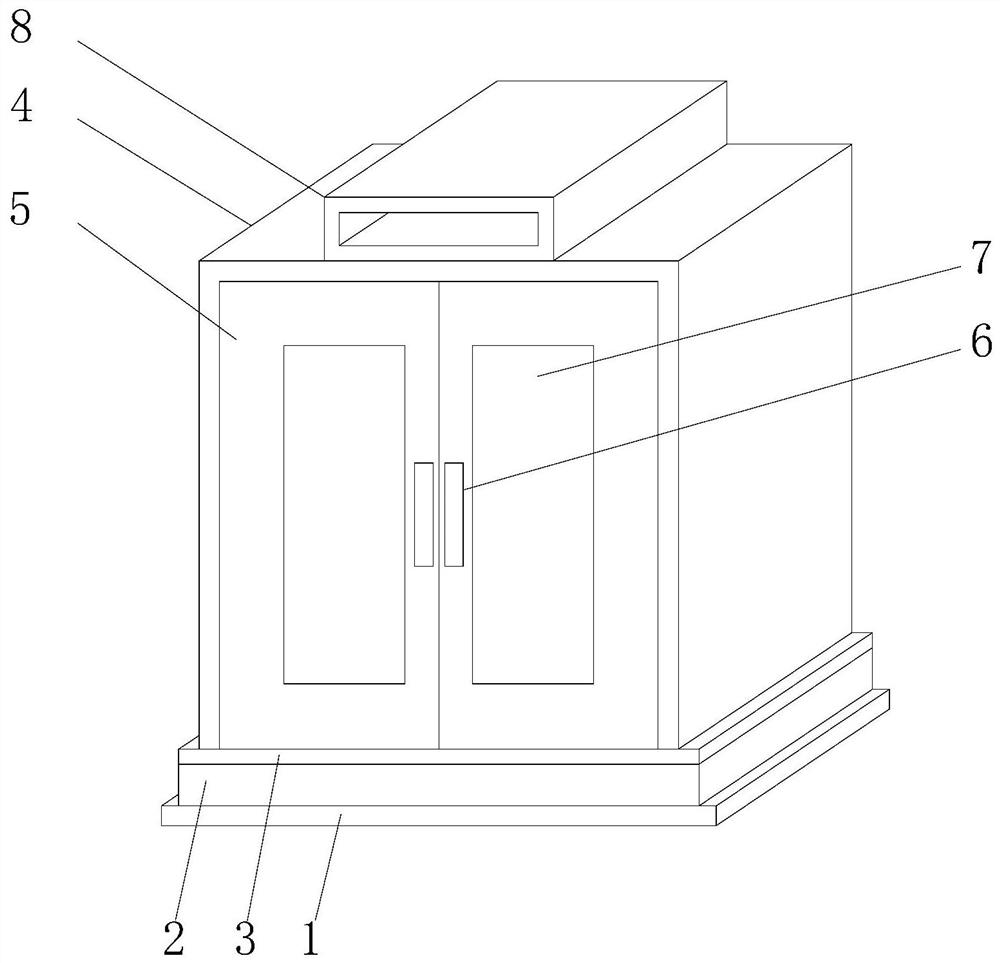
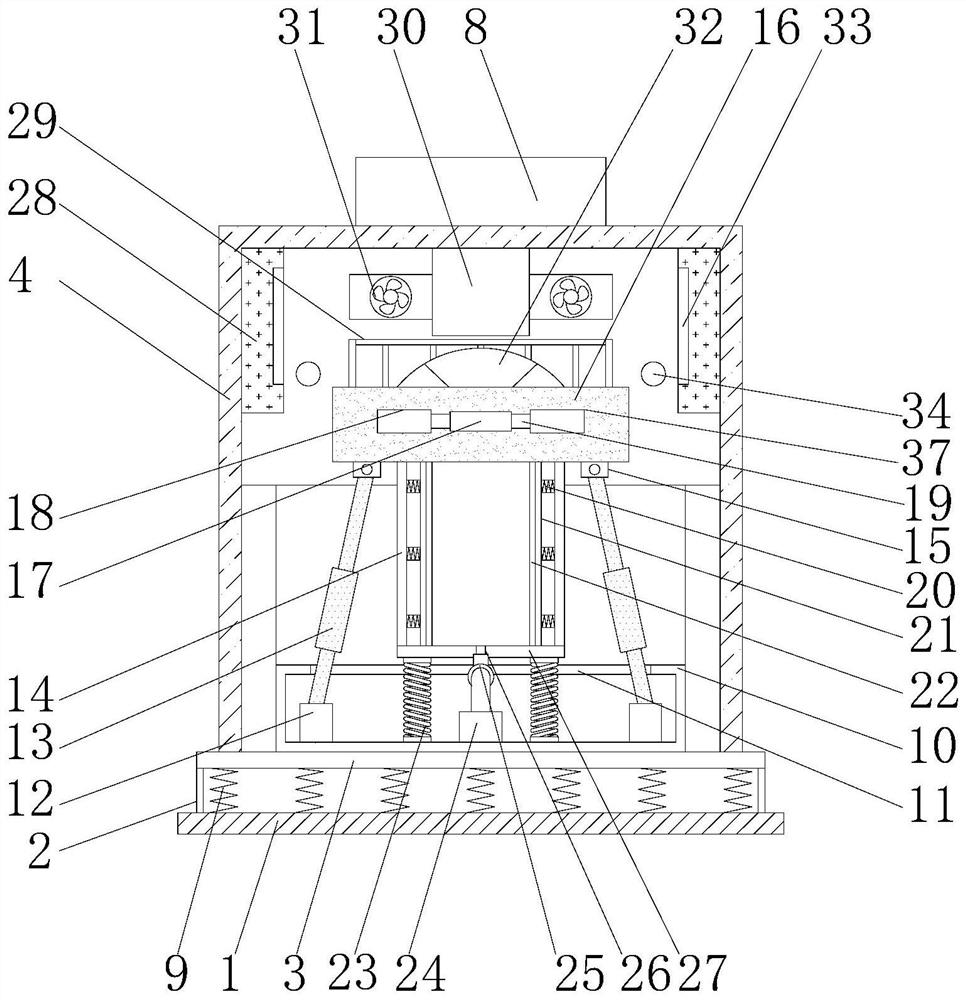
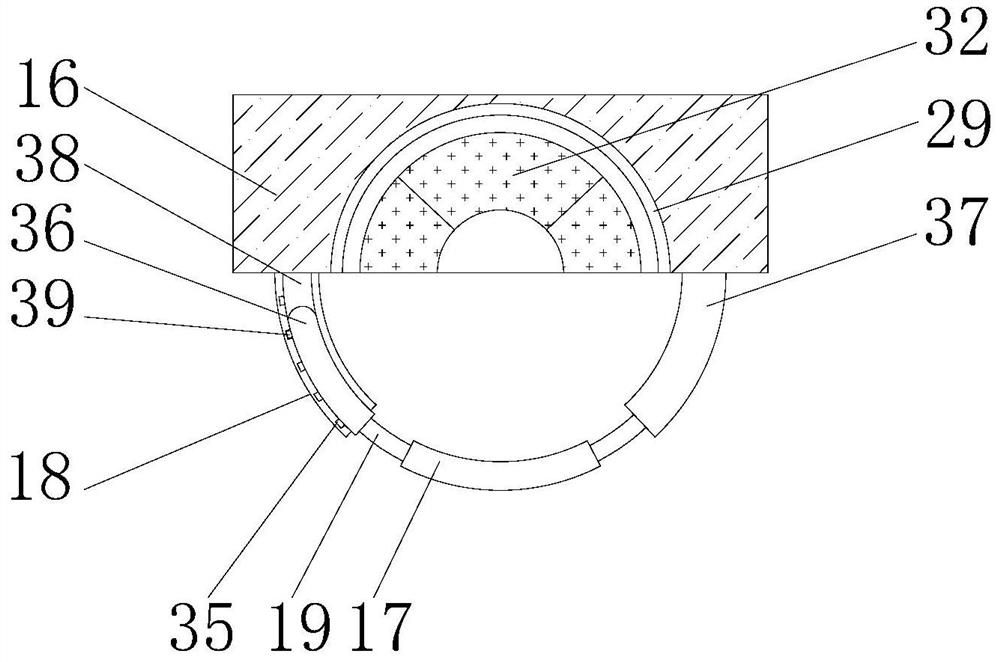
System integration control cabinet having high safety coefficient
InactiveCN108631179AComprehensive security protectionImprove fire extinguishing efficiencySubstation/switching arrangement cooling/ventilationSubstation/switching arrangement casingsComputer fanSafety coefficient
The invention discloses a system integration control cabinet having a high safety coefficient and relates to the technical field of system integration control. The system integration control cabinet includes a cabinet body, support posts, a suspension fire extinguisher and an electromagnetic chuck. Four corners of the bottom of the cabinet body are equipped with the support posts. A leaking watersensor is mounted in the center of the bottom face of the cabinet body. The suspension fire extinguisher is mounted in the middle of the top face of the inner wall of the cabinet body. A smoke sensoris mounted on the top face of the inner wall of the cabinet body on a side adjacent to the suspension fire extinguisher. A temperature sensor is mounted on the inner wall of the cabinet body. A leaking water alarm, a smoke alarm and a temperature alarm are mounted on the upper end of the cabinet body side by side in sequence. Heat dissipation ports are arranged in two side faces of the cabinet body. A heat dissipation fan is mounted in the heat dissipation port. A cabinet door is hinged to one side of the cabinet body flexibly. An armature is mounted on one side of the inner side face of the cabinet door away from the hinged end. The electromagnetic chuck corresponding to the armature is mounted on a side of the cabinet body away from the hinged end. The invention is complete in safety protection and is high in safety coefficient.
Owner:芜湖广智天和信息技术有限公司
Computer network security protection system for task management
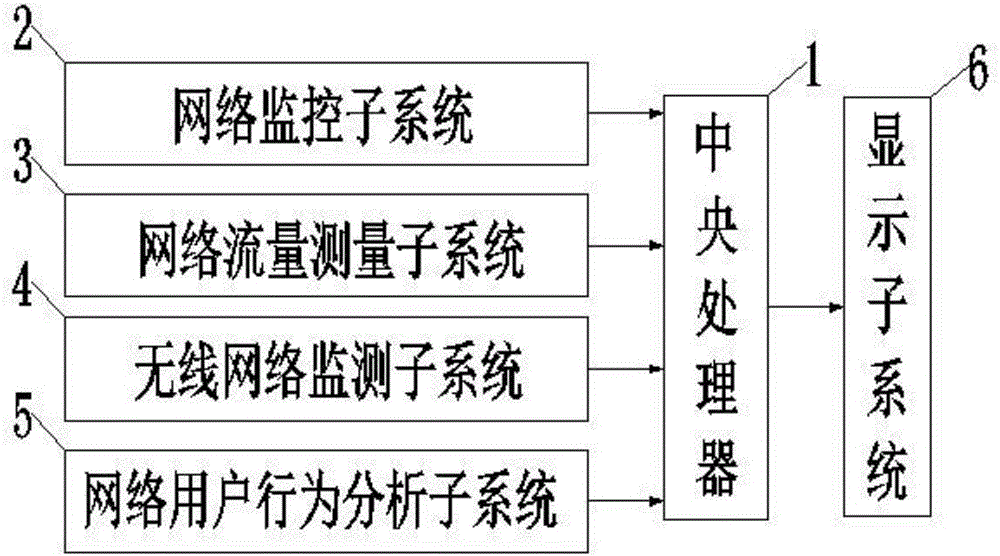
ActiveCN106533828AComprehensive security protectionEasy to monitorData switching networksProtection systemTask management
The invention discloses a computer network security protection system for task management and relates to the technical field of computer network security. The system comprises a central processing unit, wherein the central processing unit is in electrical input connection with a network monitoring subsystem, a network traffic measurement subsystem, a wireless network monitoring subsystem and a network user behavior analysis subsystem; and the central processing unit is in electrical output connection with a display subsystem. According to the system, an operation state of a network is monitored and analyzed through the network monitoring subsystem; usage data of traffic in the network is measured and analyzed through the network traffic data measurement subsystem; the usage data of a wireless network is monitored and analyzed through the wireless network monitoring subsystem; and the data of usage behaviors of network users is monitored and analyzed through the network user behavior analysis subsystem.
Owner:NORTH CHINA UNIVERSITY OF SCIENCE AND TECHNOLOGY
Guard fence device of raking machine
InactiveCN102979569AReduce stress deformationEnsure personal safetyEarth drilling and miningUnderground transportEngineeringMechanical engineering
The invention relates to a guard fence device of a raking machine. The guard fence device comprises a framework made by welding of angle iron, the framework is internally provided with a plurality of steel pipes arranged with the same spacing, and each steel pipe is vertically provided with two fixed screw holes with the same spacing; and an anchor rope penetrates through each steel pipe, is fixedly tightened by bolts through the fixed screw holes and extends out of the corresponding steel pipe. The guard fence device has the advantages of convenience and easiness in use, durable structure and comprehensive safety protection, and the coefficient of safety operations can be improved.
Owner:安徽恒源煤电股份有限公司
Free combat cushion with leather shell fabric and preparation method for same
The invention discloses a free combat cushion with a leather shell fabric. According to the free combat cushion, four side cushion bodies are arranged around a main cushion body, right-angled folding grooves are formed in the lower sides of the junctions of the side cushion bodies and the main cushion body, and the both ends of the side cushion body are 40-degree inclined surfaces; a magic tape device is arranged between the adjacent side cushion bodies; the main cushion body sequentially comprises an XPE foamed plastic layer, a non-woven fabric layer and a leather layer from bottom to top, and the side cushion bodies are the same as the main cushion body in hierarchical structure. The free combat cushion is simple and reasonable in structure, convenient, fast and stable to install, relatively low in cost, safe and comfortable to use, and beneficial to ensure that sportsmen wholeheartedly go into a match, and ensure the exertion of the best technological level, thus being of great significance.
Owner:TAISHAN SPORTS IND GRP +1
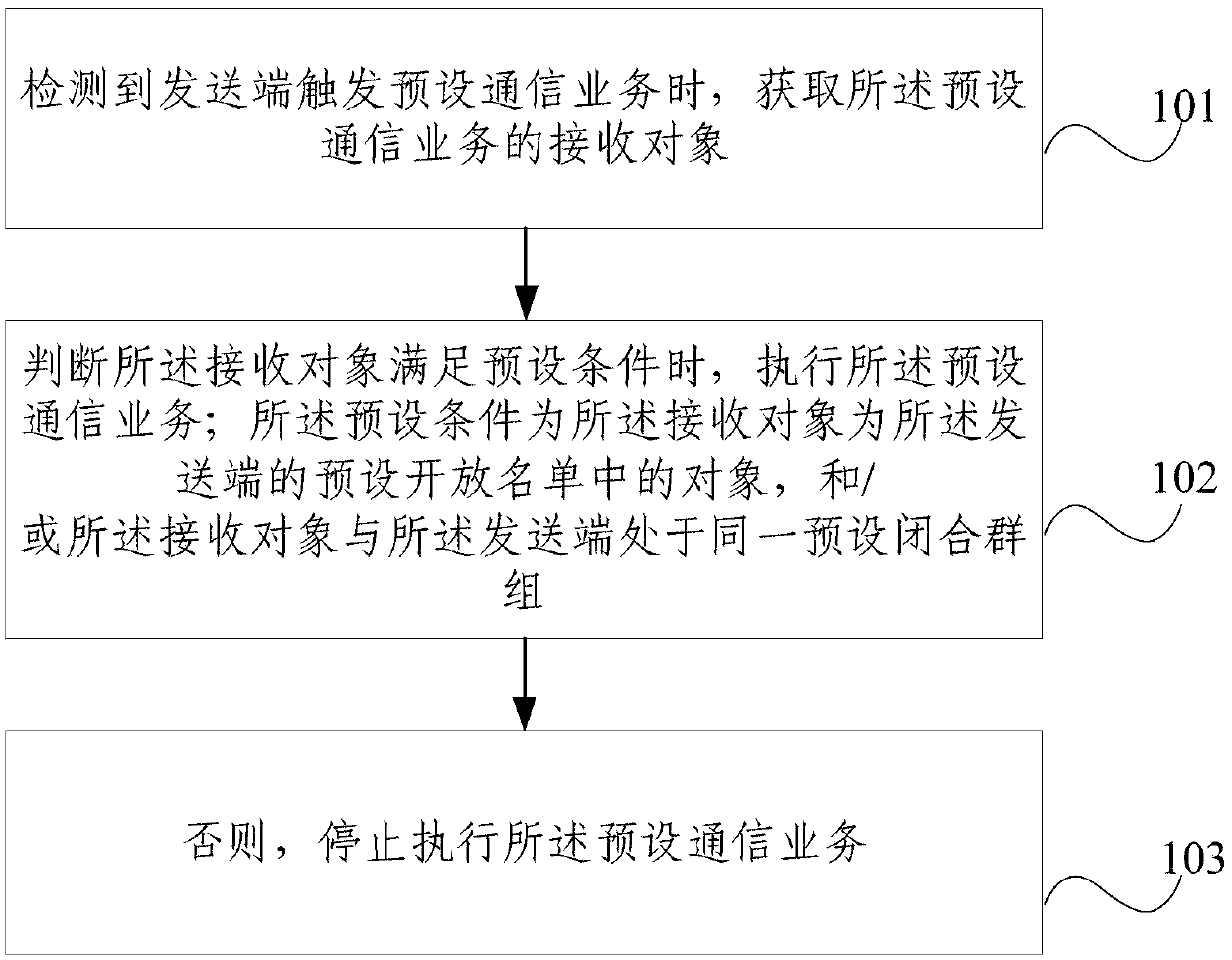
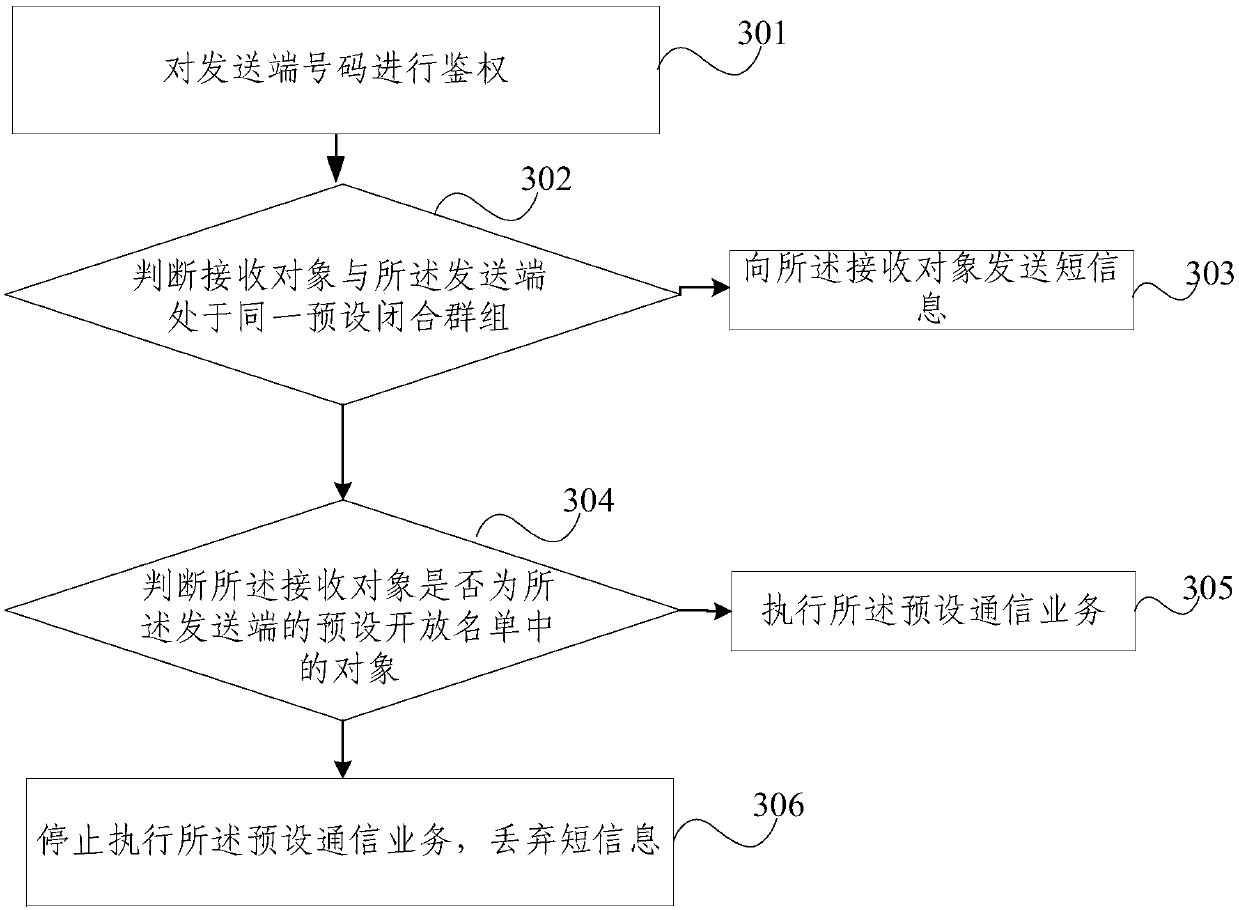
Communication service processing method and device
ActiveCN111246409AEasy to useAvoid connectionCommmunication supplementary servicesSubstation equipmentComputer networkEngineering
Owner:CHINA MOBILE GROUP ZHEJIANG +1
Construction safety protection equipment
PendingCN110021143AComprehensive security protectionSolve poor protection accuracyAlarmsTransmissionEngineeringRemote communication
The invention discloses construction safety protection equipment. The construction safety protection equipment comprises a safety helmet and further comprises a super-close distance communication module, a first close-distance communication module, a remote communication module, a microprocessor and a battery module which are arranged on the safety helmet, and in addition, the construction safetyprotection equipment further comprises a background computer and a second close-distance communication module arranged in a real-name system channel and / or a safety channel; the super-close distance communication module is used for radio frequency identification, the second close-distance communication module is used for communicating with the first close-distance communication module, the outputend of the first close-distance communication module is connected with the first input end of the microprocessor, the output end of the microprocessor is connected with the input end of the remote communication module, the remote communication module is used for communicating with the background computer, and the battery module supplies power to the super-close distance communication module, the first close-distance communication module, the remote communication module and the microprocessor. The construction safety protection equipment integrates multiple functions and is low in cost and suitable for various places.
Owner:南京傲途软件有限公司
Sanda pad of leather fabric and preparation method thereof
The invention discloses a Sanda mat made of leather fabric, which is provided with four side pads around the main pad body, and a right-angle folding groove is arranged on the lower side of the joint between the side pad body and the main pad body, and the two sides of the side pad body The end is a 45-degree slope; there is a hook and loop device between the adjacent side pads; the main pad is XPE foam layer, non-woven fabric layer, leather layer from bottom to top, and the side pad and main pad are layered. same. Its structure is simple and reasonable, its installation is convenient, fast and stable, its cost is relatively low, and it is safe and comfortable to use. It is beneficial to ensure that athletes can fully devote themselves to the competition and ensure the best technical level, which is of great significance.
Owner:TAISHAN SPORTS IND GRP +1
A tenant-based security capability and security service chain management platform
InactiveCN112291232BImprove securityEnsure safetyDatabase distribution/replicationPlatform integrity maintainanceResource poolWeb application
The invention discloses a tenant-based security capability and security service chain management platform, which relates to the field of network security and includes: a security situation awareness system, a portal management system, and a cloud security resource pool; the security situation awareness system is used to collect information about tenants in the platform Security element information, analyze the collected security element information to generate corresponding security situation prediction results, generate and execute corresponding security disposal strategies based on the security situation prediction results; the portal management system is used for managers to log in to the portal management system to manage tenants in the platform , and for tenants to log in to the portal management system to manage tenants' own resources; the cloud security resource pool includes: detection probe system, business audit system, web application protection system and vulnerability scanning system; use this platform to manage tenants and the network in the same way , to ensure the information security and network security of tenants, and improve the security of private network use in the private network platform.
Owner:中国联合网络通信有限公司深圳市分公司
Large shipyard safety education training device and method based on VR technology
InactiveCN112289111AComprehensive security protectionAvoid harmCosmonautic condition simulationsSimulatorsPhysical medicine and rehabilitationThree degrees of freedom
The invention discloses a large shipyard safety education training device based on VR technology, which comprises a bottom plate, a shell, a supporting device, a protection device and a simulation device, and is characterized in that the supporting device comprises a first spring fixedly connected to the top end of the bottom plate, the top end of the first spring is fixedly connected with a supporting plate, the top end of the supporting plate is fixedly connected with the shell, a radiator is installed at the top end of the shell and connected with an exhaust fan through a pipeline, the protection device comprises a supporting frame fixedly connected to the bottom end in the shell, an installation base is fixedly connected into the supporting frame, one end of the installation base is provided with one end of a three-degree-of-freedom air cylinder, and the output end of the three-degree-of-freedom air cylinder is rotationally connected with a connecting base through a rotating shaft.The safety education training device is reasonable in structure, damage to an experiencer due to large shaking vibration can be avoided, safety education training can be conducted more comprehensively, and real feelings can be conveniently provided through a loudspeaker box and a loudspeaker, so that most employees are educated to achieve the purposes of enhancing the safety risk awareness and improving the protection skill.
Owner:SHANGHAI WAIGAOQIAO SHIP BUILDING CO LTD
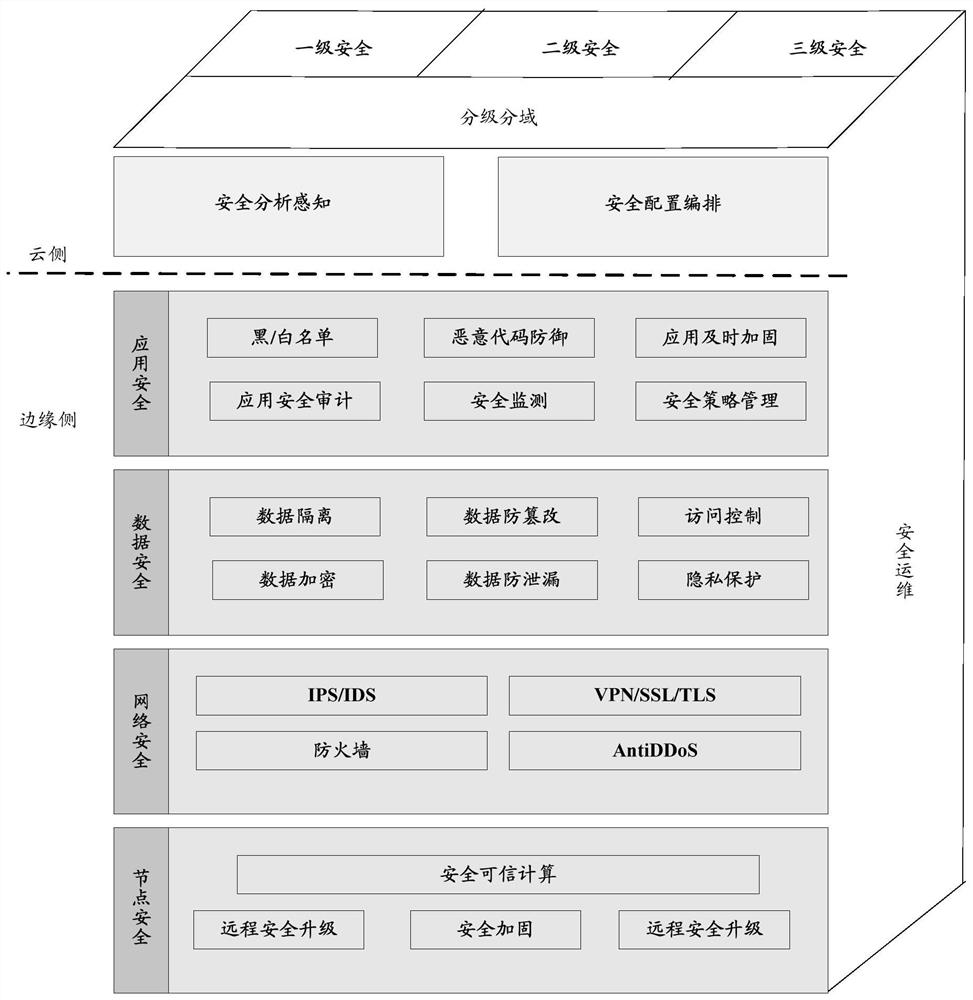
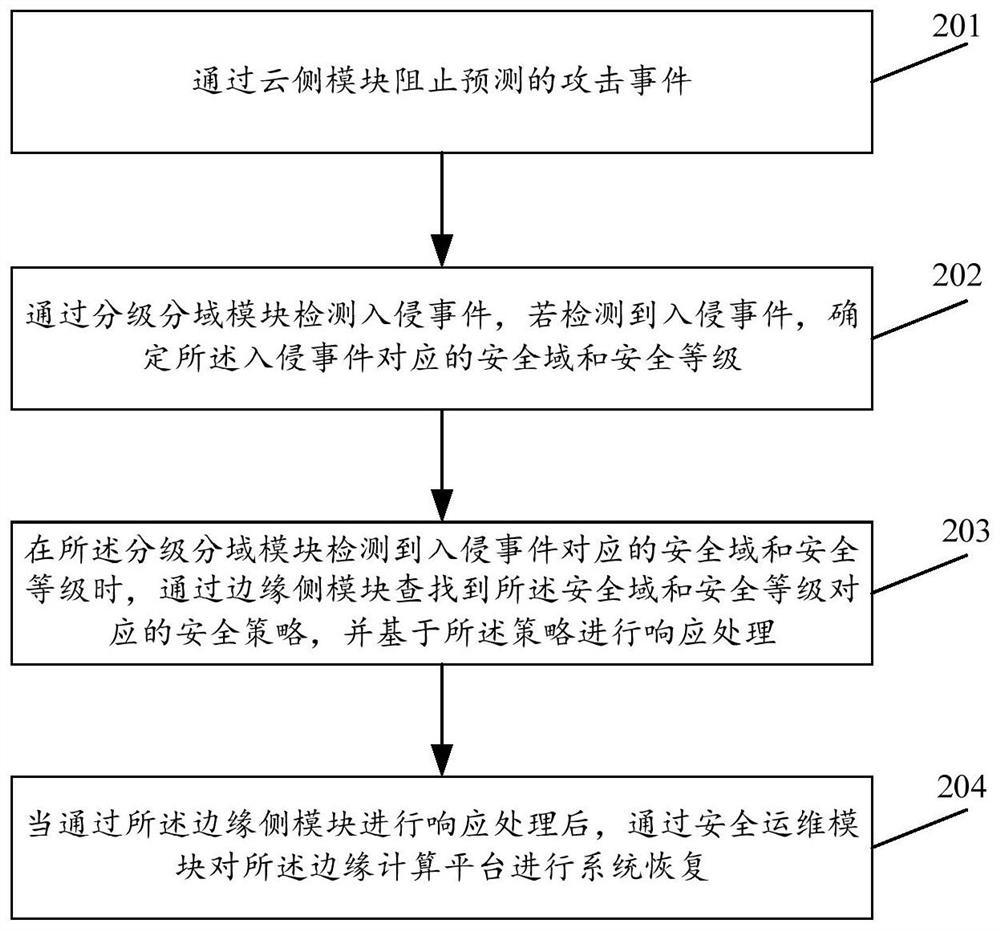
Security protection method and device for edge computing platform
The invention provides an edge computing platform security protection method and device, and the method comprises the steps: carrying out the following protection through an established edge computing platform security service model during the security protection of an edge computing platform: preventing a predicted attack event through a cloud side module; detecting an intrusion event through a grading and domain-dividing module, and if the intrusion event is detected, determining a security domain and a security level corresponding to the intrusion event; when the grading and domain dividing module detects a security domain and a security level corresponding to an intrusion event, searching a security policy corresponding to the security domain and the security level through an edge side module, and performing response processing based on the policy; after response processing is carried out through the edge side module, carrying out system recovery on the edge computing platform through the security operation and maintenance module. According to the method, comprehensive safety protection can be carried out on the edge computing platform.
Owner:CHINA ACADEMY OF INFORMATION & COMM
Monitoring system and method for monitoring computer network security
PendingCN111314376AComprehensive security protectionImprove practicalityInternal/peripheral component protectionTransmissionInternet trafficWeb environment
The invention discloses a monitoring system and method for monitoring computer network security. The system comprises a security monitoring module, an exception analysis module, a monitoring processing module, a computer and a security monitoring module, and is used for monitoring and counting network traffic, monitoring and counting internet surfing behaviors and monitoring and counting access conditions of confidential information or mobile hard disk interface access conditions; the exception analysis module is used for analyzing whether the network flow is exceptional or not, analyzing whether Internet surfing behaviors influencing the network environment exist or not, and analyzing whether access to confidential information or access to a mobile hard disk interface is normal access ornot; and the monitoring processing module is used for determining network flow, internet surfing behaviors and confidential information or a management and control scheme of a mobile hard disk interface according to a result obtained by analysis of the anomaly analysis module. According to the invention, the network flow, the internet surfing behavior, the confidential information access or the mobile hard disk interface access are monitored at the same time, the comprehensive protection of the computer network security is achieved, and the practicability is very high.
Owner:SHANDONG VOCATIONAL COLLEGE OF SCI & TECH
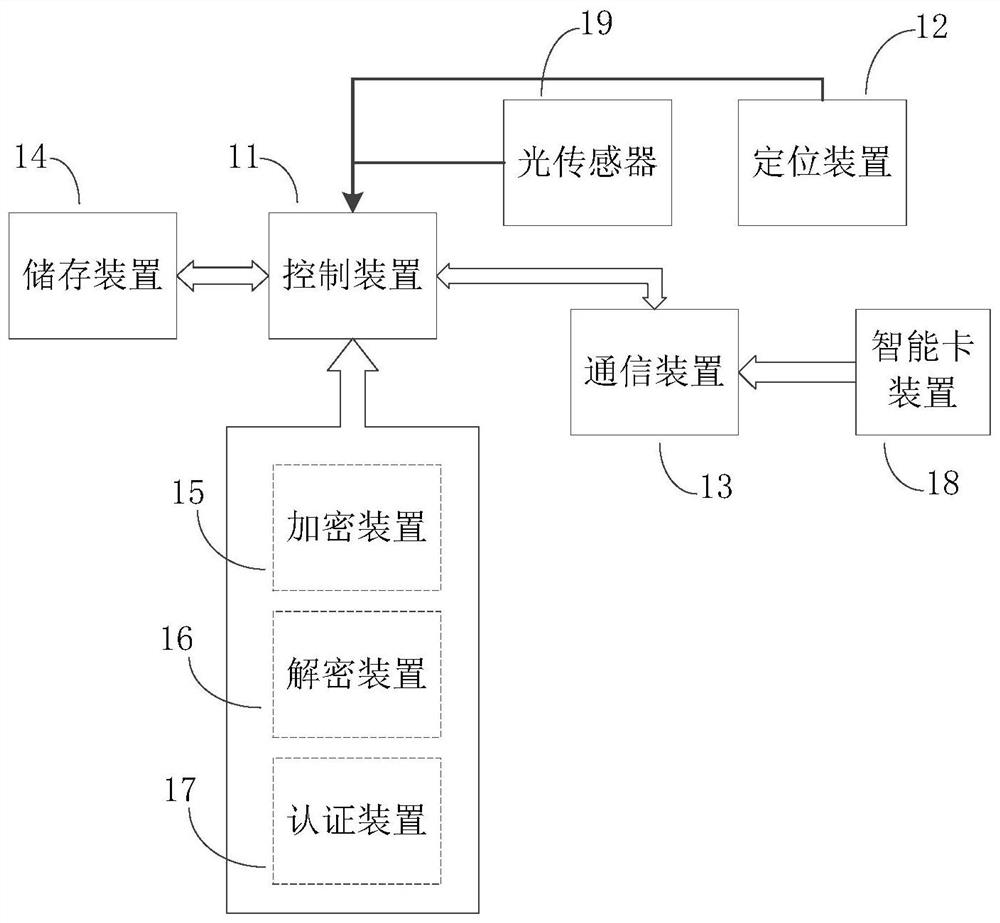
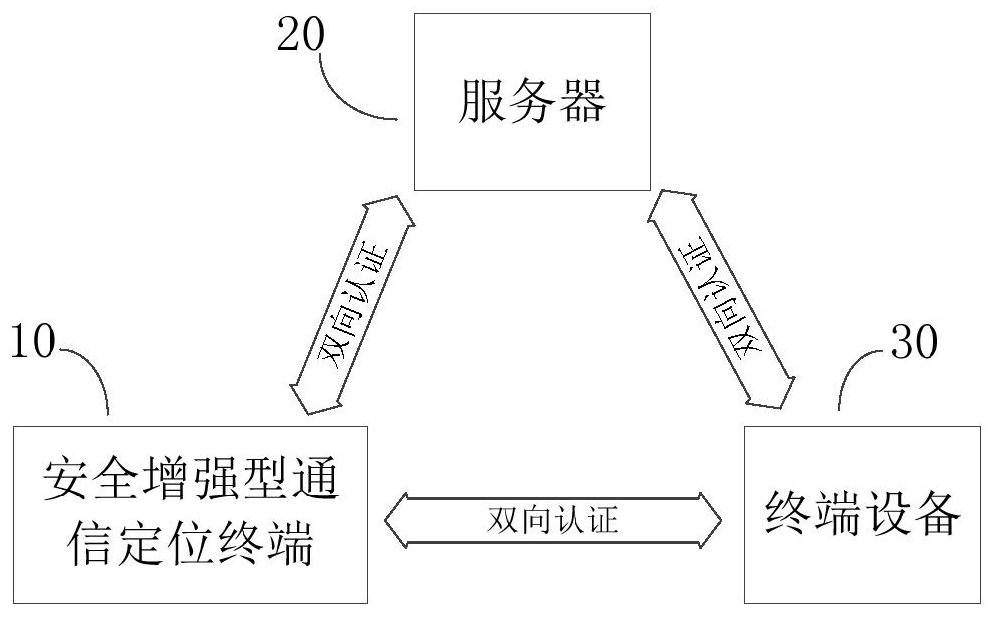
Security enhanced communication positioning terminal
InactiveCN111641646AUniqueness guaranteedEasy to manage at scaleKey distribution for secure communicationShort range communication serviceTerminal equipmentData needs
The invention discloses a security enhanced communication positioning terminal, which comprises a control device, a positioning device, a communication device, a storage device, an encryption device and a decryption device, the control device is connected with the positioning device, the communication device and the storage device through I / O interfaces. The positioning device is used for acquiring position information; wherein the communication device is used for establishing communication connection with terminal equipment / a server; the communication device receives the unique identificationkey distributed by the server and stores the unique identification key in the storage device; a public key matrix is also stored in the storage device; the encryption device negotiates based on the unique identification key and the public key matrix to obtain a session key, and encrypts data needing to be sent; and the decryption device decrypts the data to be received by using the session key. The data encryption, identity authentication and hardware protection are combined, and comprehensive safety protection is provided for the safety-enhanced communication positioning terminal.
Owner:上海万位科技有限公司
Stand-alone security system
ActiveCN103413083BComprehensive Security ProtectionImprove the protective effectUser identity/authority verificationDigital data authenticationCompact discOperational system
The invention relates to the field of security defense of a single host and particularly relates to a security defending system for a single host. The security defending system comprises a login control subsystem, a main engine monitoring and patch distributing subsystem and a compact disc recording monitoring subsystem, wherein the login control subsystem is used for controlling a login process of a user login single host operation system by a USBkey (Universal Serial Bus key); the main engine monitoring and patch distributing subsystem is used for carrying out security monitoring on an operation process of the single host and managing patch distribution; the compact disc recording monitoring subsystem is used for carrying out the security monitoring on compact disc recording. The security defending system provided by the invention can comprehensively carry out security defense on the single host and the defending performance is preferable.
Owner:水利部信息中心 +1
Clinical skull breaking repair device suitable for neurosurgery department
PendingCN114099143AImprove ductilityImprove seismic performanceHead bandagesNeck bandagesNeurosurgerySkull bone
The invention discloses a clinical skull fracture repairing device suitable for neurosurgery department, the clinical skull fracture repairing device comprises a fixing ring, a ventilation system, a fitting positioning mechanism and a safety protection mechanism, the safety protection mechanism comprises supports, a connecting frame, an elastic piece, a top plate and a medical protection cap, and the top of the fixing ring is fixedly connected with four sets of supports; through integrated structure connection of the fixing rings and the safety protection mechanism, the device is convenient to use and wear, meanwhile, an umbrella-shaped frame body composed of the support and the connecting frame is used as a protection system and can be matched with multiple sets of erected elastic pieces to serve as an elastic buffering structure to be attached to a medical protection cap, and the protection effect is good. According to the medical protective cap, the surface of the medical protective cap is protected, impact acting force borne by the surface of the medical protective cap is resisted, impact force from outside to inside is relieved, the situation that the skull gets loose or deviates due to the fact that the acting force makes direct contact with the seam of the skull is prevented, the ductility and shock resistance of a protective system are enhanced, and the safety of skull repair is improved.
Owner:冯基高
Software forced safety protection method based on external environment model learning
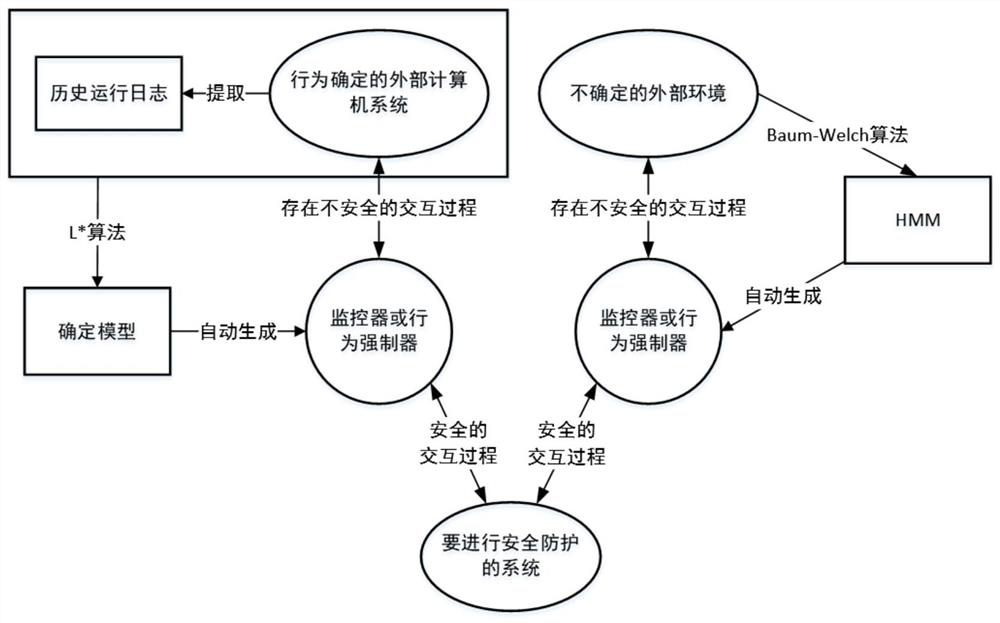
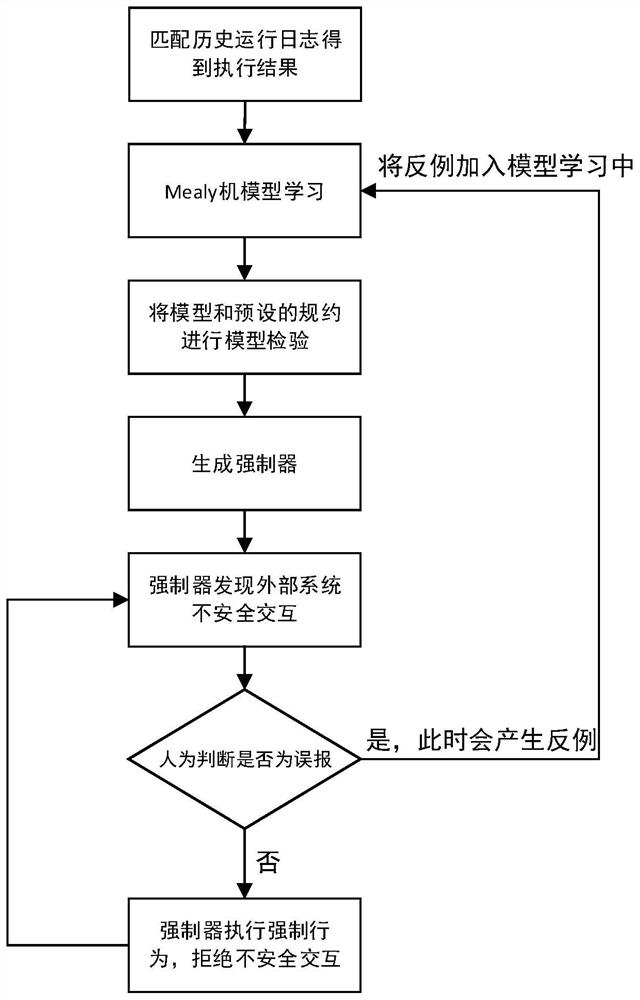
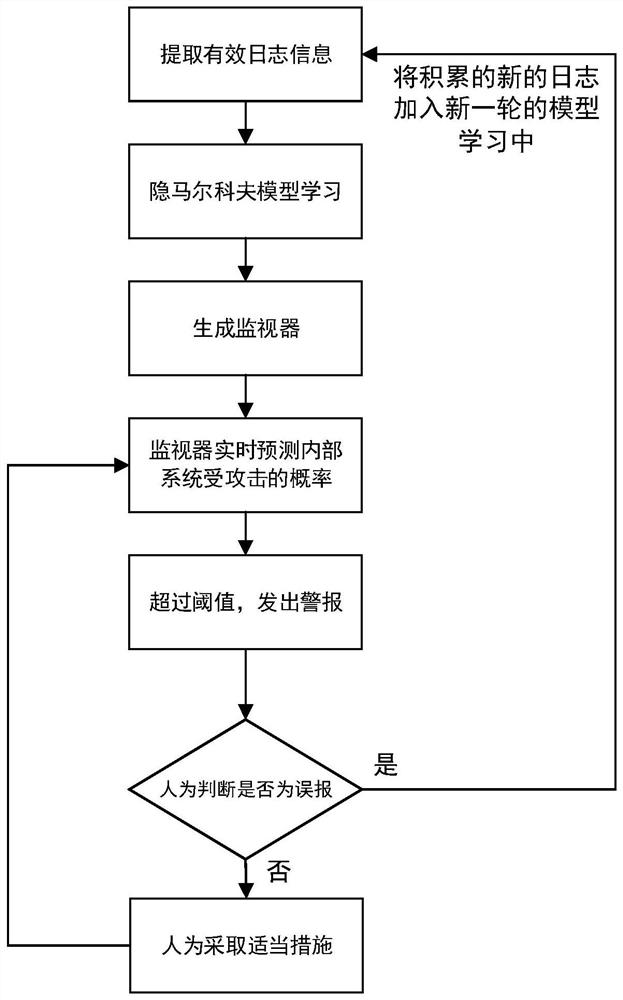
PendingCN112733155AShorten the timeImprove learning efficiencyPlatform integrity maintainanceMachine learningProbit modelPathPing
The invention discloses a software forced safety protection method based on external environment model learning, which comprises the following steps: for an external computer system, collecting a historical operation log of the external computer system and matching an execution result of a software operation sequence queried by parts in an MAT framework, calculating the execution result according to a preset first model learning algorithm to obtain a Mealy machine model, analyzing the Mealy machine model in combination with a preset protocol to obtain a program path violating the protocol, and generating a forcifier according to the program path violating the protocol; for the external environment, obtaining logs of the internal system, extracting an interaction event sequence of the external environment and the internal system as an observation sequence, calculating the observation sequence according to a preset second model learning algorithm to obtain a probability model, and generating a monitor through the probability model. According to the method, the learning process is combined with the log, so that the learning efficiency is greatly improved.
Owner:NAT UNIV OF DEFENSE TECH
Optic machine automatic fixing device of image scanning device
ActiveCN100481862CFixed in timeProtect from harmPictoral communicationEngineeringMechanical engineering
Owner:北京高德品创科技有限公司
A computer network security protection system
ActiveCN106503524BRealize self-testAchieve self-healingDigital data authenticationPlatform integrity maintainanceRights managementProtection system
The invention discloses a computer network safeguard system in the technical field of computer safety systems. The computer network safeguard system comprises a foreground safeguard system and a background maintenance system, wherein the foreground safeguard system and the background maintenance system are bidirectionally and electrically connected through a computer center system. The foreground safeguard system comprises an identity identification subsystem, an authority management subsystem and a virus defense subsystem. The background maintenance system comprises an establishment maintenance subsystem, an interface locking subsystem and a safety evaluation subsystem. The virus defense subsystem of the computer network safeguard system can check files in a computer and remove viruses after virus behavior analysis, and the interface locking subsystem achieves USB interface outage and power supply closing when the system is not used. The computer network safeguard system prevents computer file leakage, is high in safeguard performance and achieves all-around computer network safeguard.
Owner:EASTERN LIAONING UNIV
Integrated construction technology of anti-collision wall formwork
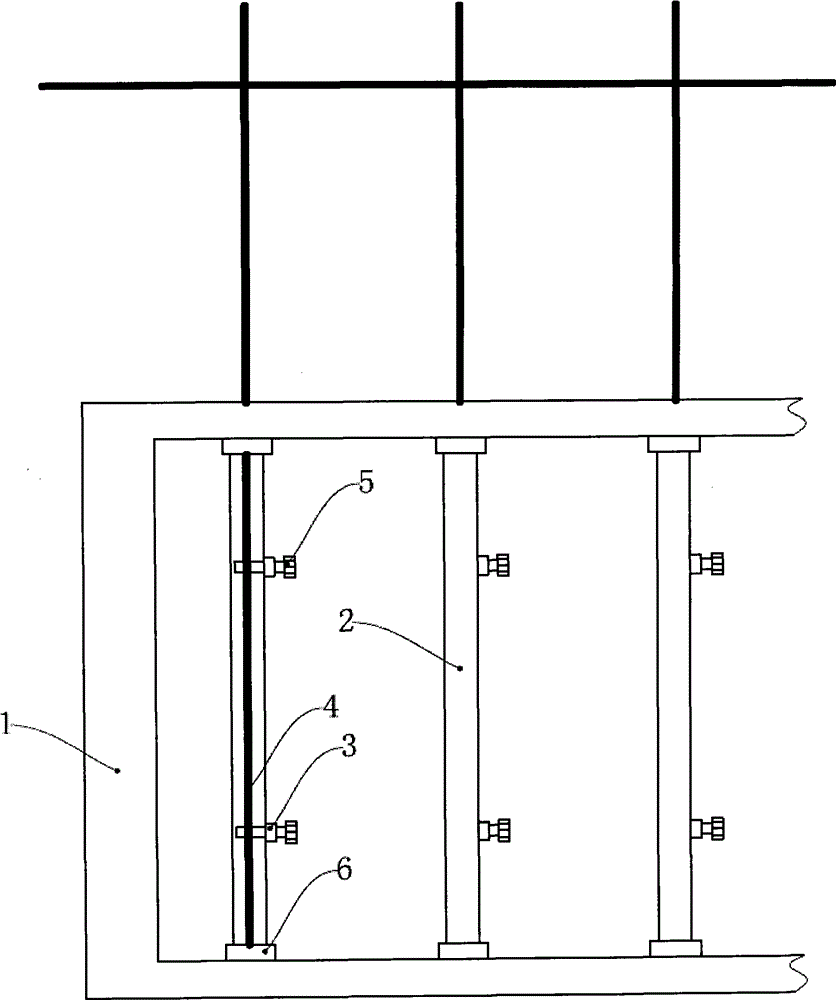
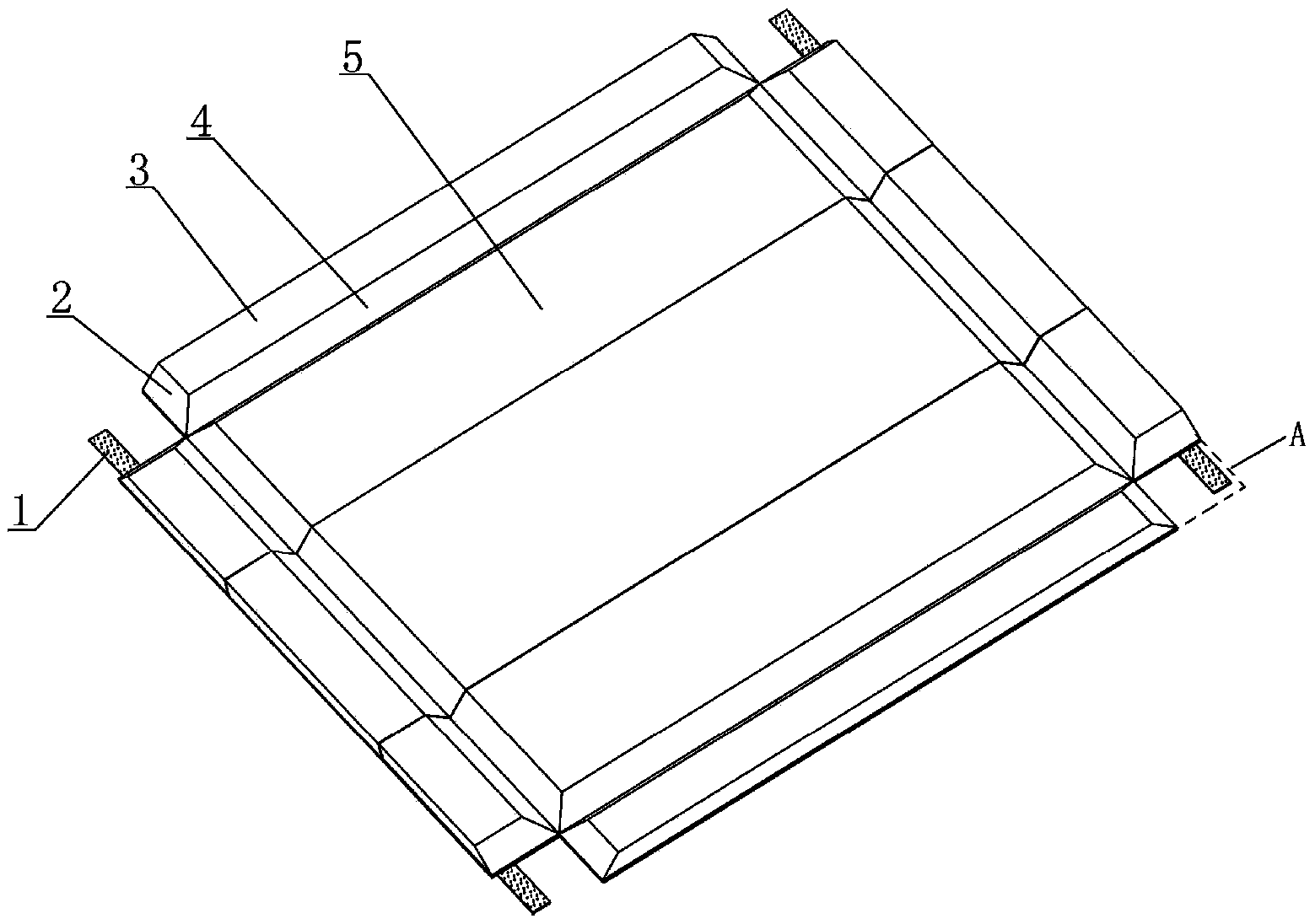
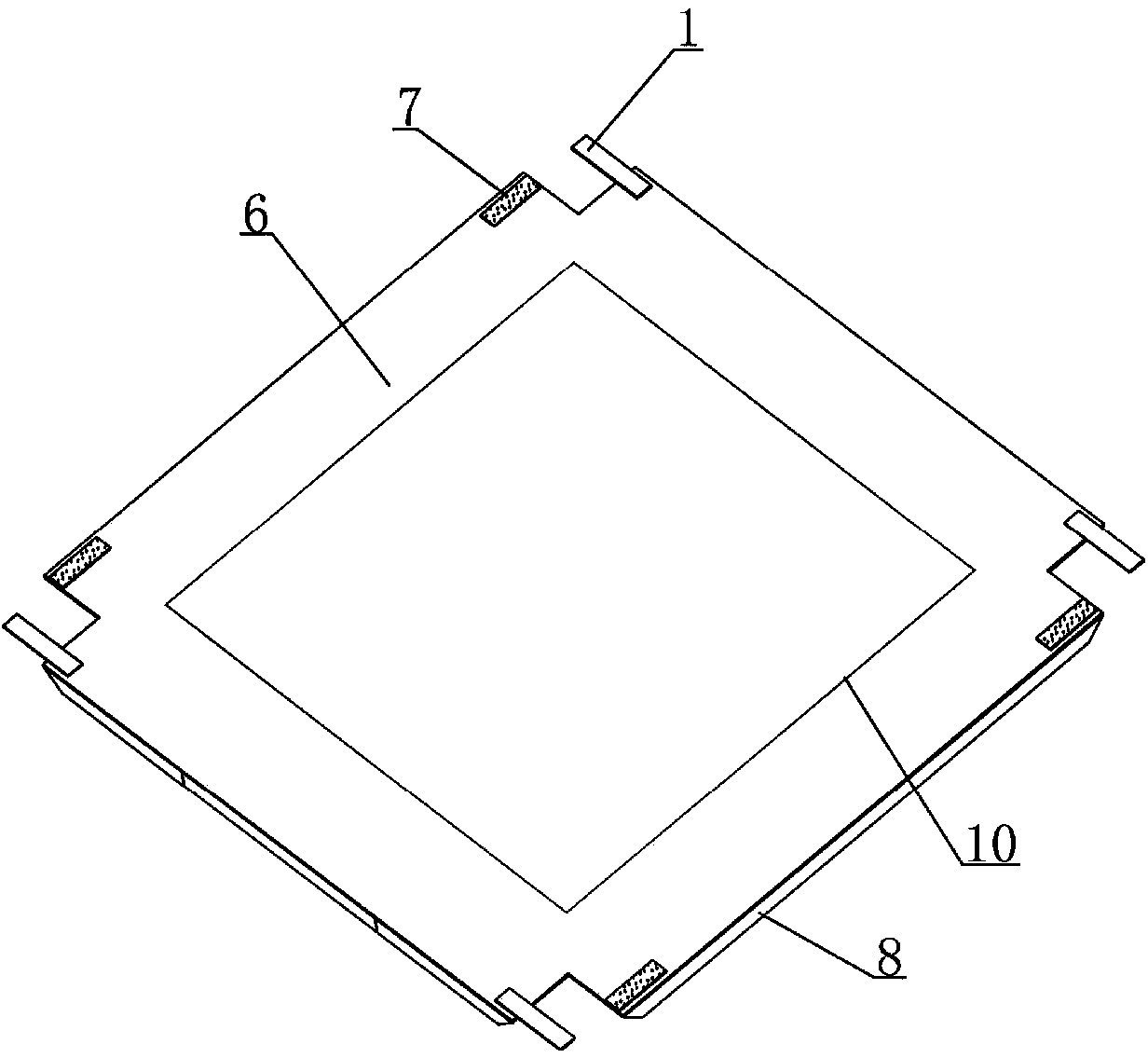
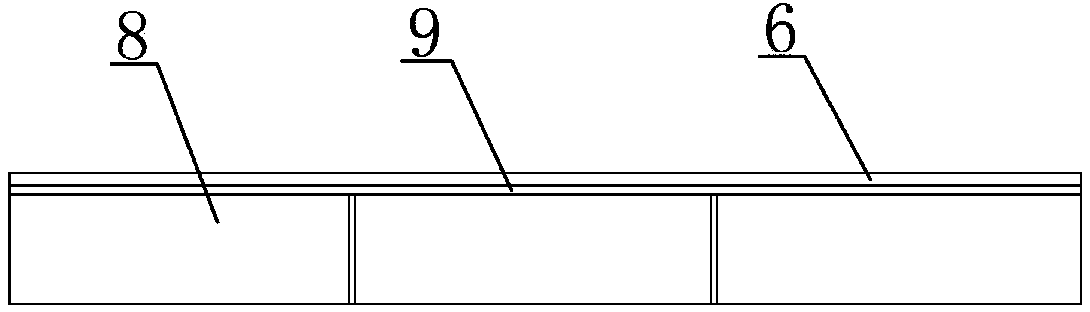
ActiveCN106400691BImprove securityImprove construction efficiencyBridge structural detailsBridge erection/assemblyArchitectural engineeringIntegrated systems
The invention discloses an integrated construction process for an anti-collision wall formwork. A T-shaped operating platform is additionally arranged at a vertical rib of an outer mold of an anti-collision wall and is firmly connected with the vertical rib of the outer mold through a bolt. By using an integrated system of the anti-collision wall formwork, and due to the modification of the process, the safety coefficient for anti-collision wall construction is obviously increased, and the anti-collision wall can adapt to complex construction environments; safety protection at each process stage is enhanced, so that safety measures are relatively perfect; in addition, the modified formwork process is simple in working procedure, convenient to operate and capable of obviously increasing the formwork turnover construction efficiency, improving the effect, shortening the construction period and reducing part of construction cost.
Owner:NO 1 ENG COMPANY CO LTD OF CCCC FIRST HARBOR ENG COMPANY
Features
- R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
Why Patsnap Eureka
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Social media
Patsnap Eureka Blog
Learn More Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com