Computer security apparatus and method
A computer security and protective device technology, applied in computer security devices, internal/peripheral computer component protection, computing, etc., can solve problems such as low convenience of use, incompatibility of software or driving computer hardware, etc., and achieve complete security protection Effect
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
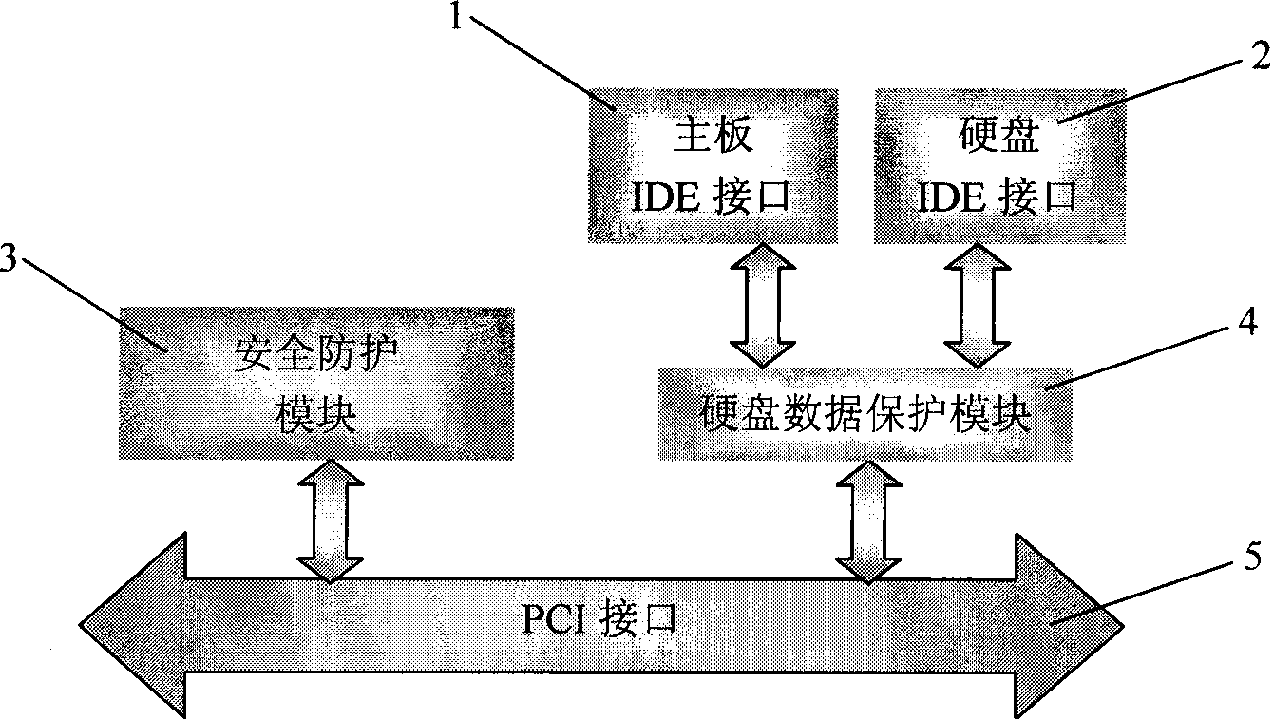
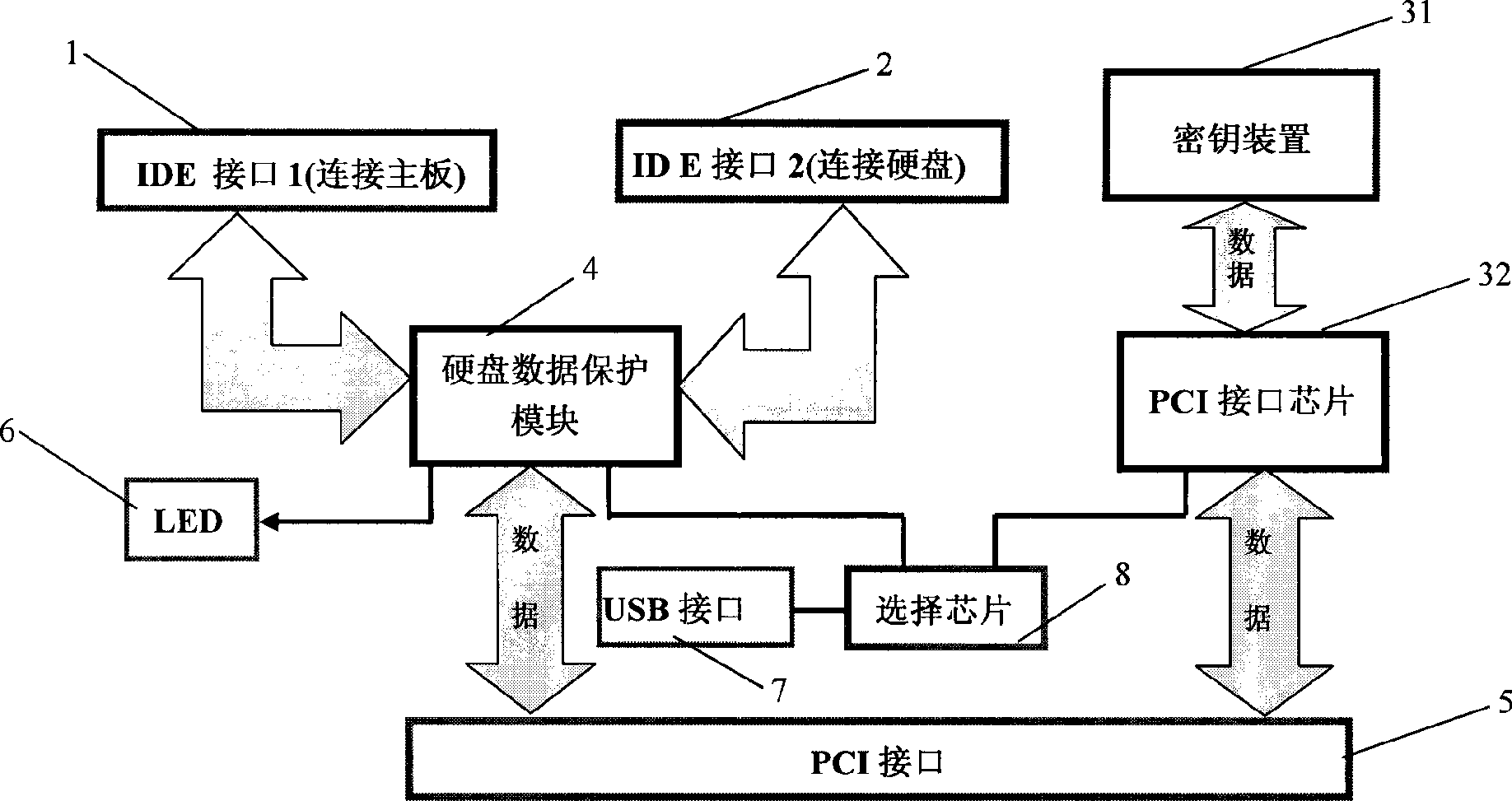
[0030] The computer safety protection device of the present invention is a hardware card with a PCI adapter card as a carrier, and a key device with verification passwords and authorization files attached. The present invention provides the password verification of computer start-up, provides the protection measure of starting computer hardware at the lowest level at the BIOS layer, and provides a double verification mechanism in combination with hard disk full-disk data protection verification, ensuring that only authorized users can use computer hardware equipment and Hard disk data provides computer system confidentiality and integrity testing; the full disk protection of hard disk data realizes real-time protection of hard disk data and is completely transparent to users; the configurable computer startup medium selection function realizes forced hard disk startup or according to The BIOS is set to start sequentially, which avoids the safety hazard caused by CD-ROM booting....
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com