Security enhanced communication positioning terminal
A communication positioning and enhanced technology, applied in secure communication devices and key distribution, to prevent impersonation of legitimate users, efficiently control access rights, and prevent resource intrusion
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
[0030] The present invention will be further described below in conjunction with the accompanying drawings and specific embodiments.
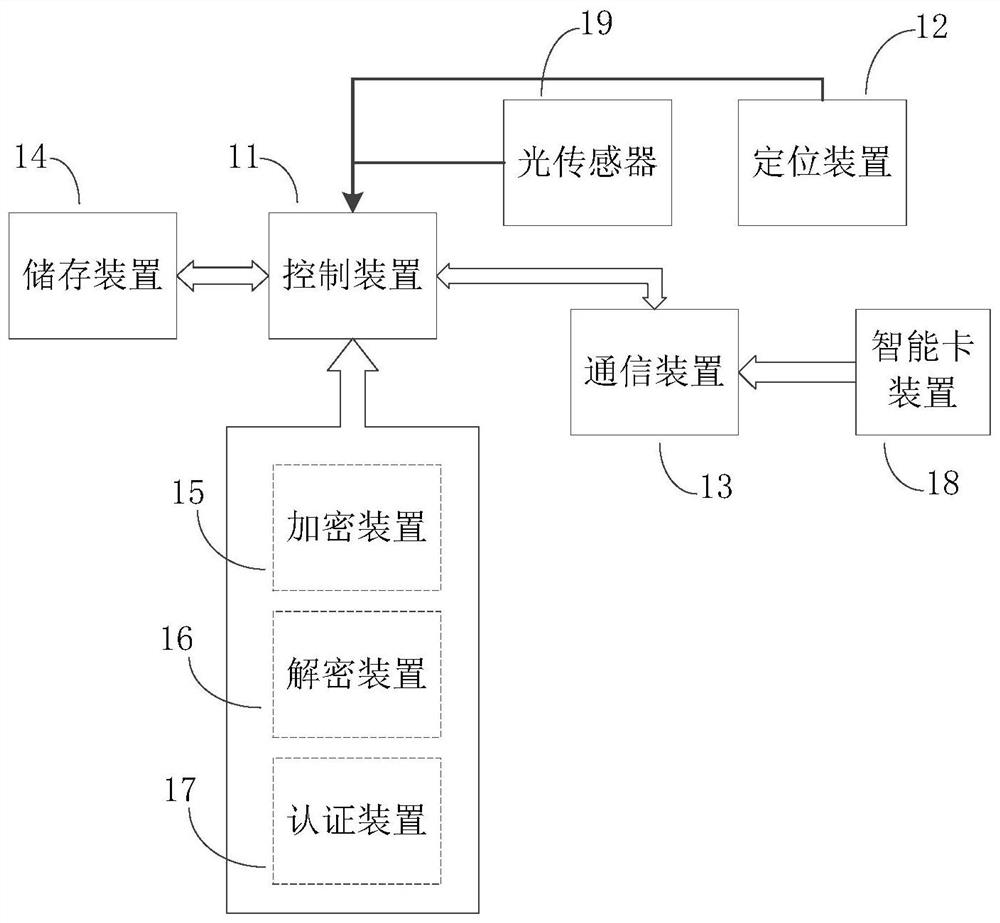
[0031] The security-enhanced communication positioning terminal 10 of this embodiment includes a control device 11 , a positioning device 12 , a communication device 13 , a storage device 14 , an encryption device 15 and a decryption device 16 .
[0032] The control device 11 is connected with the positioning device 12 , the communication device 13 and the storage device 13 through an I / O interface.
[0033] The positioning device 12 is used for acquiring position information.
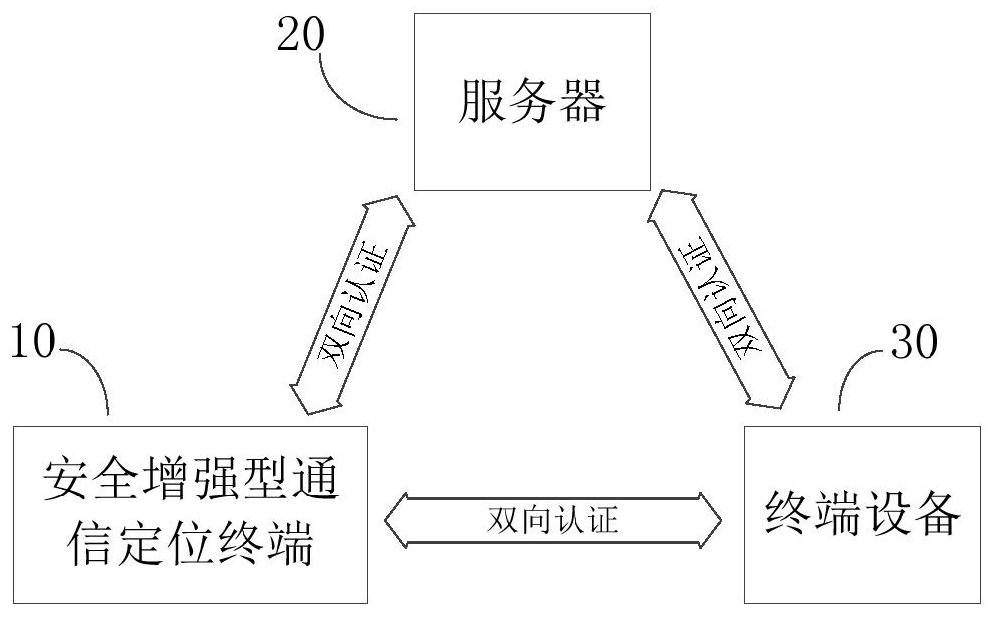
[0034] The communication device 13 is used to establish a communication connection with the terminal device 20 / server 30 to send or receive data. The communication device 13 receives the unique identification key distributed by the server 30 and stores the unique identification key in the storage device 14 . Among them, the unique identification key is used as the pri...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com