Stand-alone security system
A security protection, stand-alone technology, used in transmission systems, user identity/authority verification, digital data authentication, etc., can solve problems such as single protection measures, no protection system, and poor protection performance.
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
[0072] The present invention will be described in further detail below through specific implementation examples and in conjunction with the accompanying drawings.
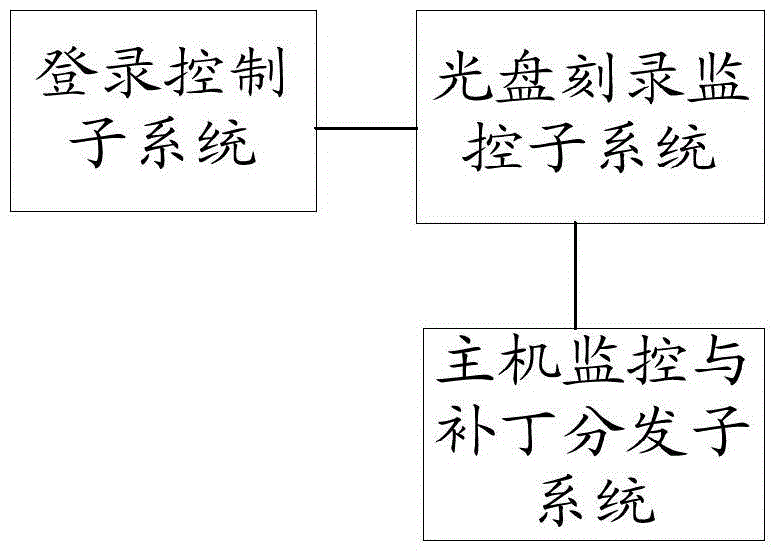
[0073] The embodiment of the present invention provides a stand-alone safety protection system. see figure 1 As shown, it includes the login control subsystem, the host monitoring and patch distribution subsystem, and the CD burning monitoring subsystem.
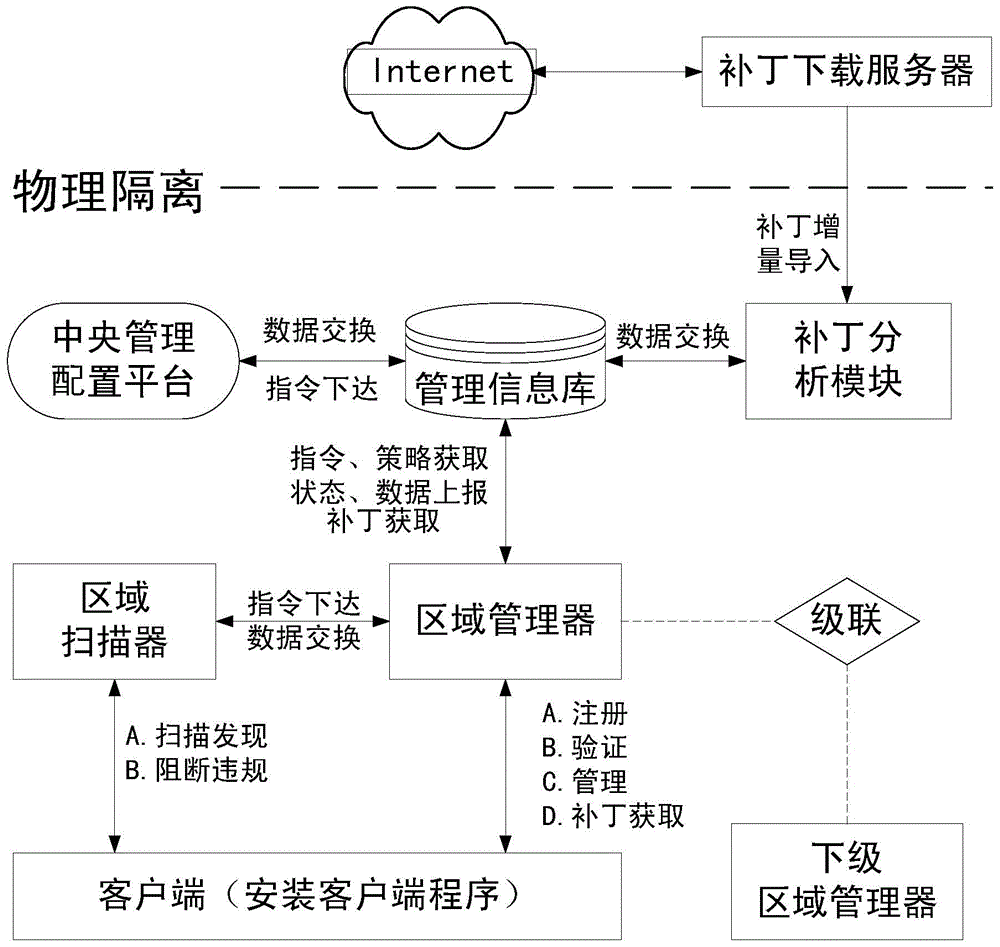
[0074] The login control subsystem is used to control the login process of the user logging into the stand-alone operating system through a USB key; the host monitoring and patch distribution subsystem is used to monitor the security of the running process of the stand-alone computer and manage the patch distribution ; The optical disc recording monitoring subsystem is used for safety monitoring of optical disc recording.
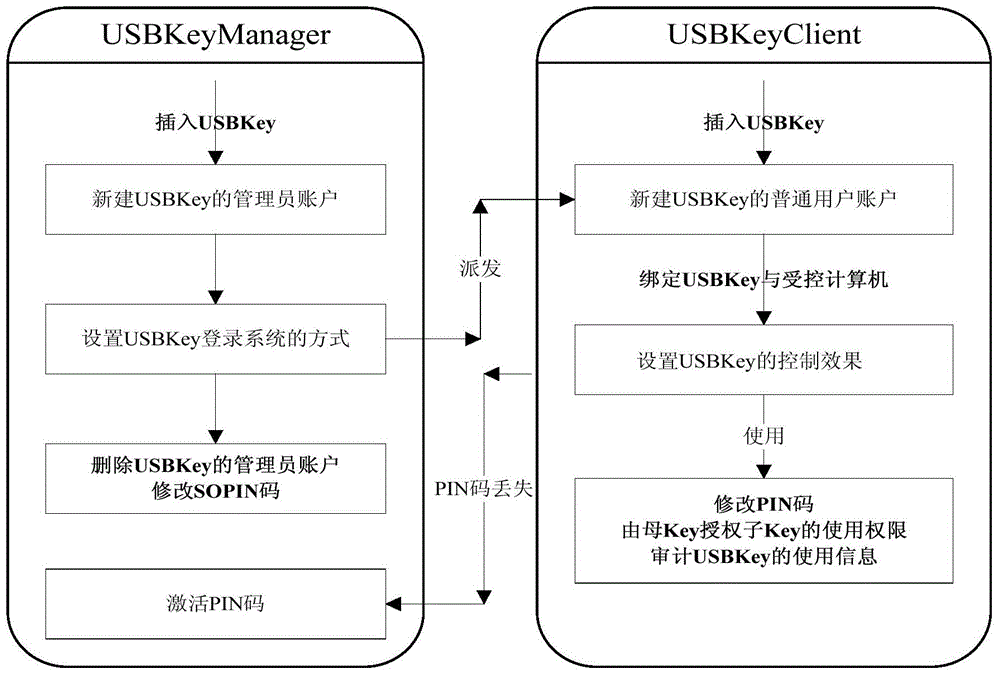
[0075] As a specific implementable manner, the login control subsystem includes a USBKey management module (USBKeyManager), a USBKey client...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com