Mobile information multi-layer network secure auditing system
A security audit and network security technology, applied in the field of mobile informatization and information security, can solve problems such as security loopholes, no PIN code setting, and weak security awareness of users
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
[0048] The present invention will be described in detail below with reference to the accompanying drawings and an embodiment.
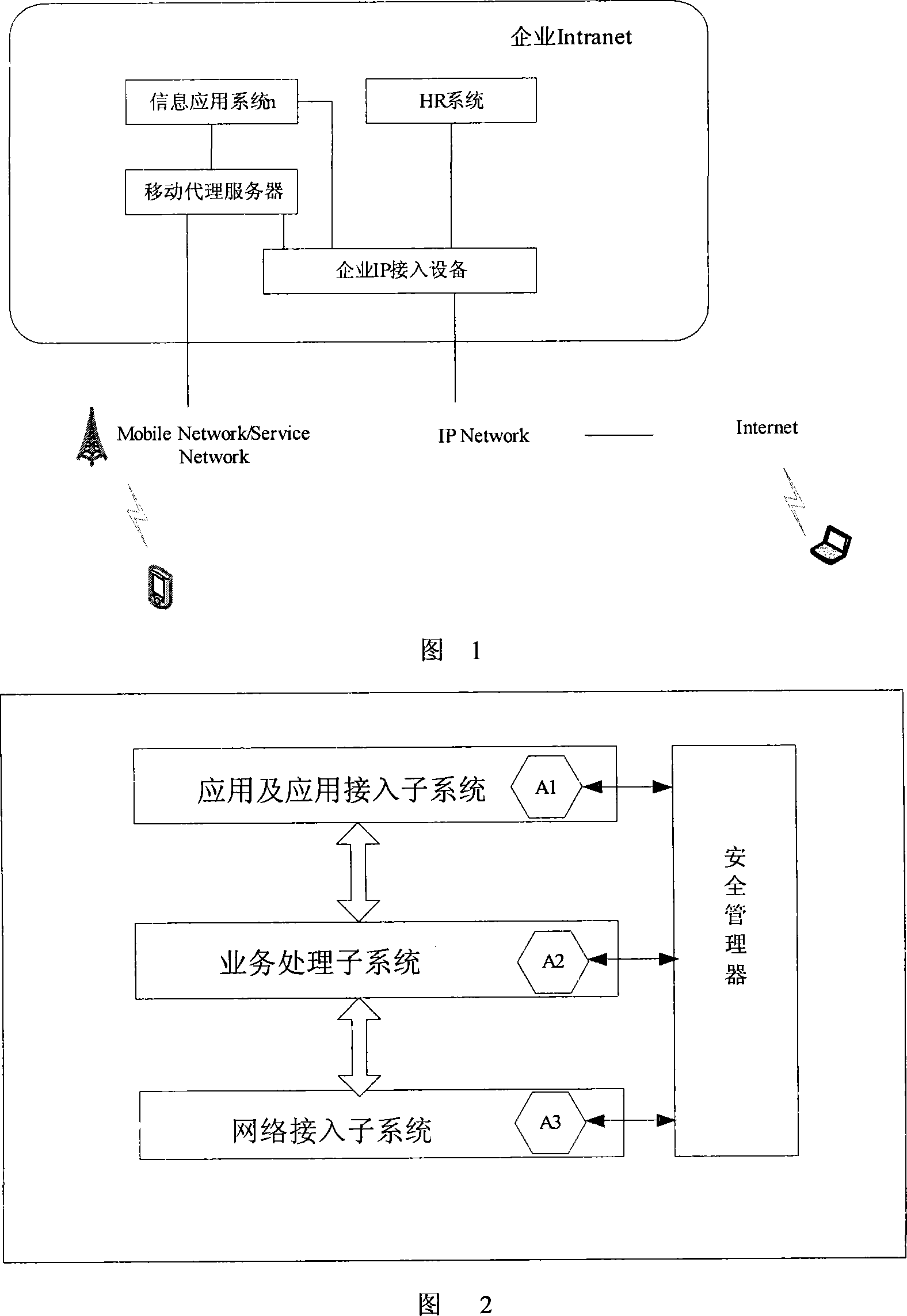
[0049] In this embodiment, the typical position of the mobile proxy server in the network is shown in Figure 1. It is usually located at the junction of the enterprise intranet and the extranet. It is directly connected to the extranet through a firewall or not, and can provide enterprises with mobile information applications. There is business data interaction between internal application systems such as Email, OA, ERP, etc. and the mobile proxy server, and they are routed through the internal LAN of the enterprise.
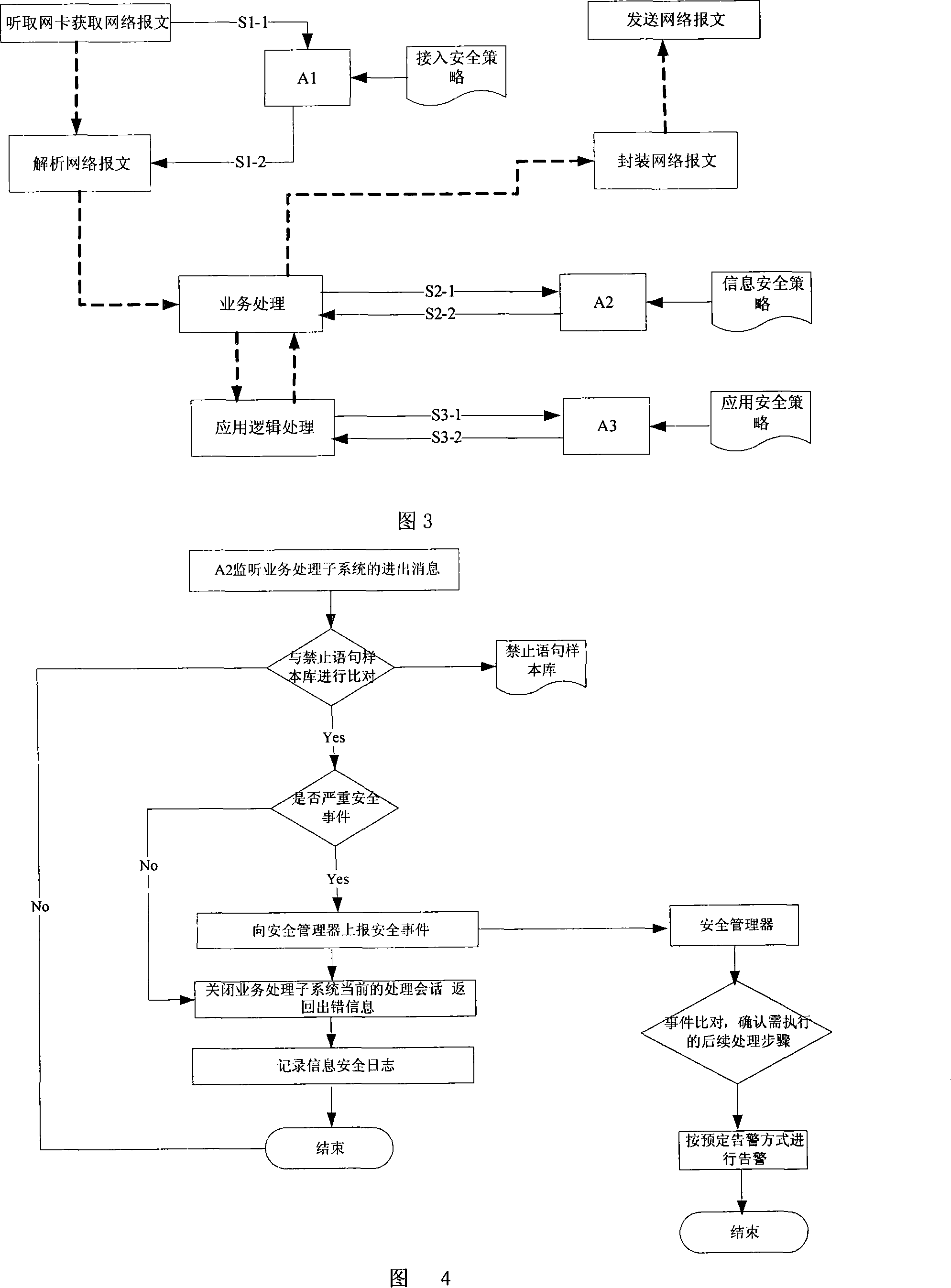
[0050] The internal structure of the mobile proxy server is shown in Figure 2. Like a conventional proxy server, it includes a three-level network access subsystem, business processing subsystem, and application and application access subsystem. In addition, a security subsystem composed of a security manager and security audit agent mo...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com