Database tamper-proofing method and system applied to data security products
A data security and database technology, applied in the field of data processing, can solve the problem that audit information cannot reflect the real historical situation of the database.
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment 1
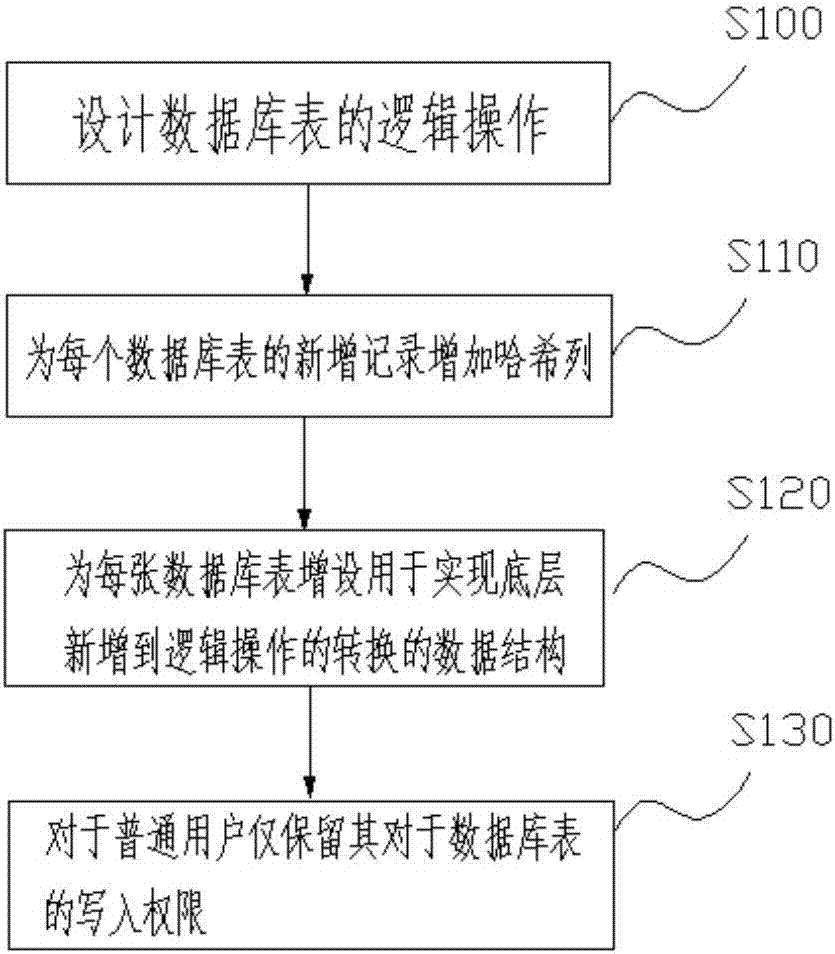
[0016] Embodiment 1 provides a database tamper-proof method applied to data security products, please refer to figure 1 , including the following steps:
[0017] Step S100: Design the logic operation of the database table. Logical operations include logical addition, logical deletion, logical modification, and logical query. Logical addition is to add a valid data record. Tombstone is to add a delete record to indicate that the object data has been deleted. Logical modification is carried out in the manner of deleting first and then adding. Firstly, logical deletion is performed to record that the object data has been deleted, and secondly, logical addition is performed to record the modified object data and the identifier of the object data. Logical query is to query all valid data records except logical deletion.
[0018] Step S110: Add a hash column for each new record in the database table. The field content of the hash column can be customized, and the hash value in ...
Embodiment 2
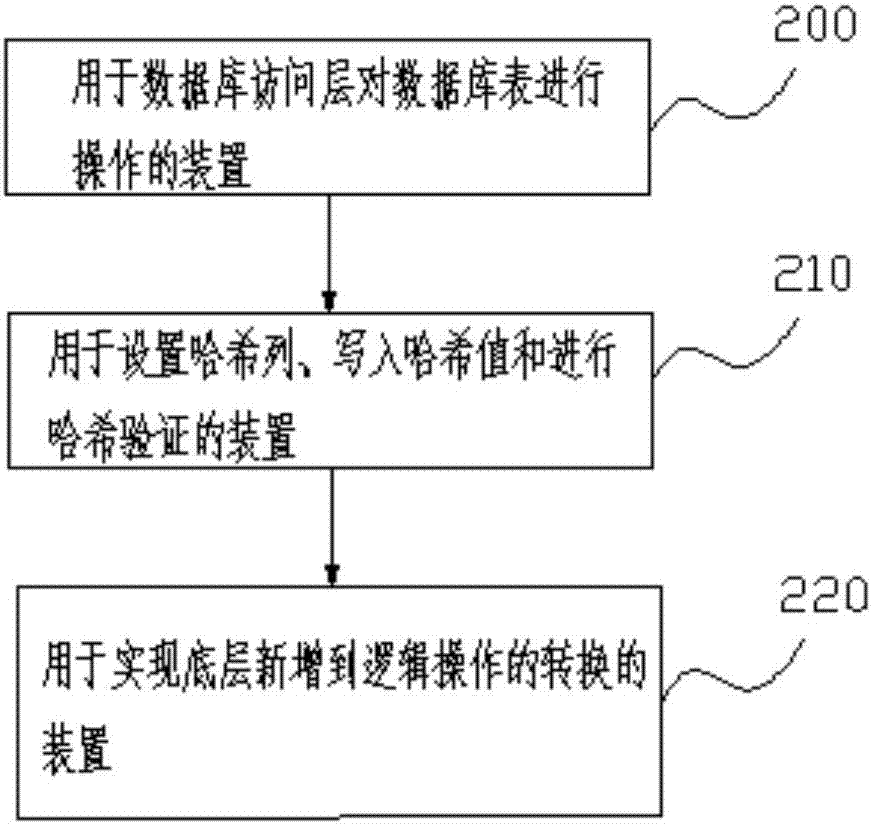
[0023] Embodiment 2 provides a database tamper-proof system applied to data security products, please refer to figure 2 , the system includes a device 200 for the database access layer to operate the database table under the logic operation described in the first embodiment; a device 210 for setting the hash column, writing the hash value and performing hash verification; for Means 220 for implementing conversion of bottom layer additions to logical operations.
Embodiment 3
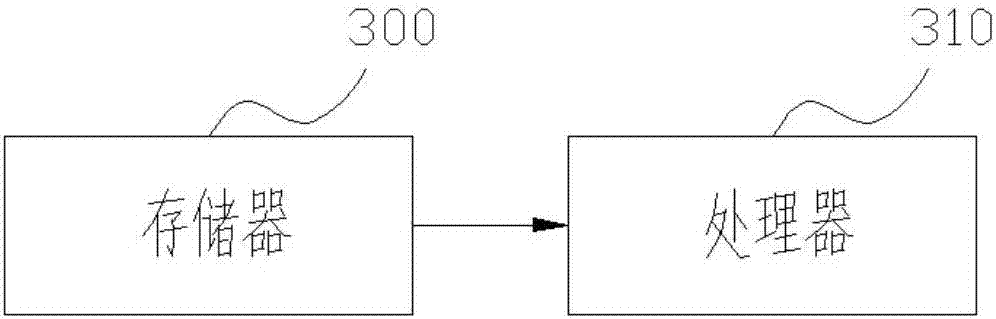
[0025] Embodiment 3 provides a kind of product, please refer to image 3 , the product includes a memory 300 and a processor 310 . The memory 300 is used to store programs, and the processor 310 is used to execute the programs stored in the memory 300 to implement the method described in the first embodiment.
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com