A concealed communication method in a block chain network environment
A network environment, covert communication technology, applied in the field of network security
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
[0047] Below in conjunction with accompanying drawing, the present invention will be further described through embodiment.
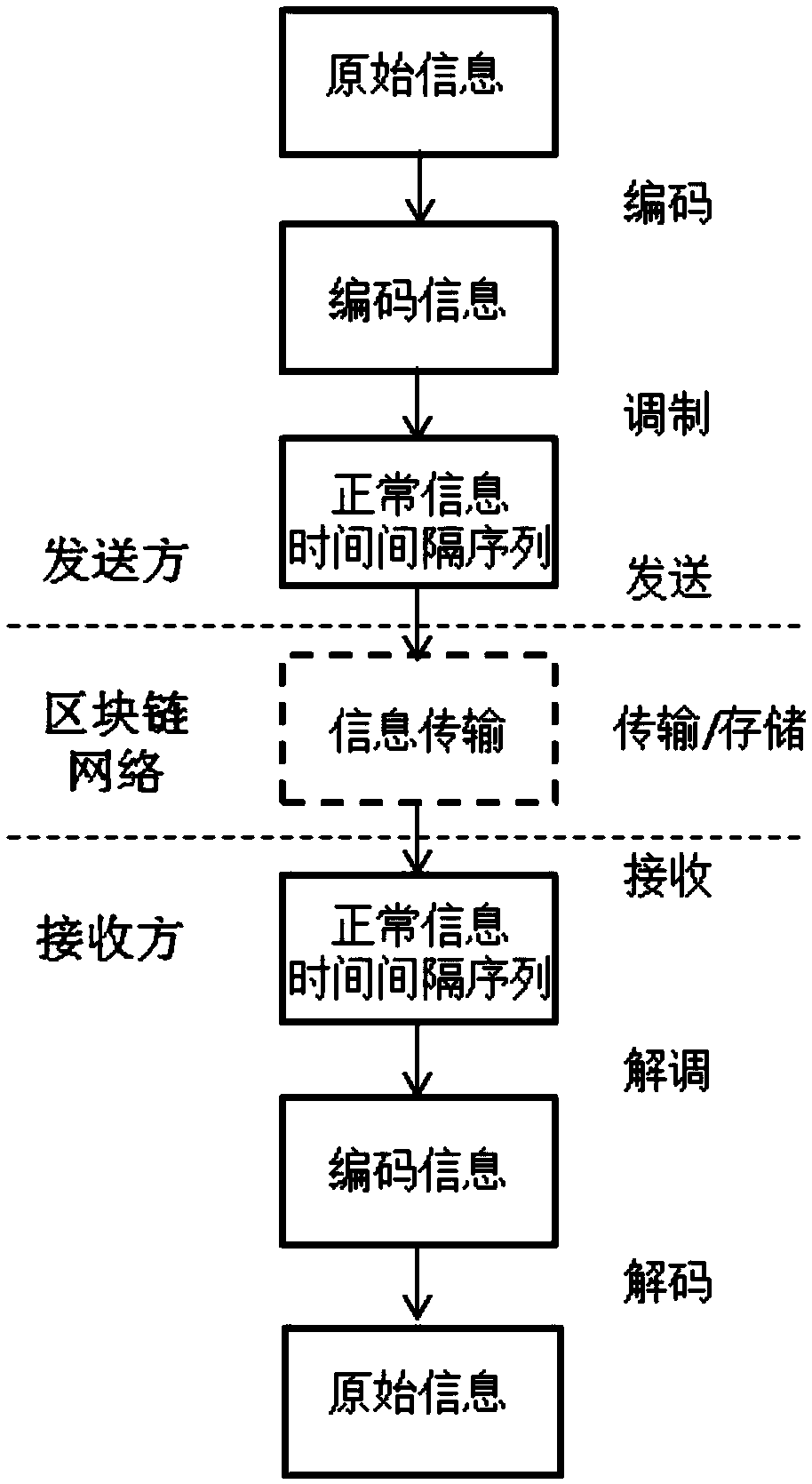
[0048] Such as figure 1 As shown, the concealed communication method under the block chain network of the present invention mainly includes the following steps:
[0049] (1) Information coding. The original concealed information is encoded using a previously agreed source coding or channel coding mechanism.
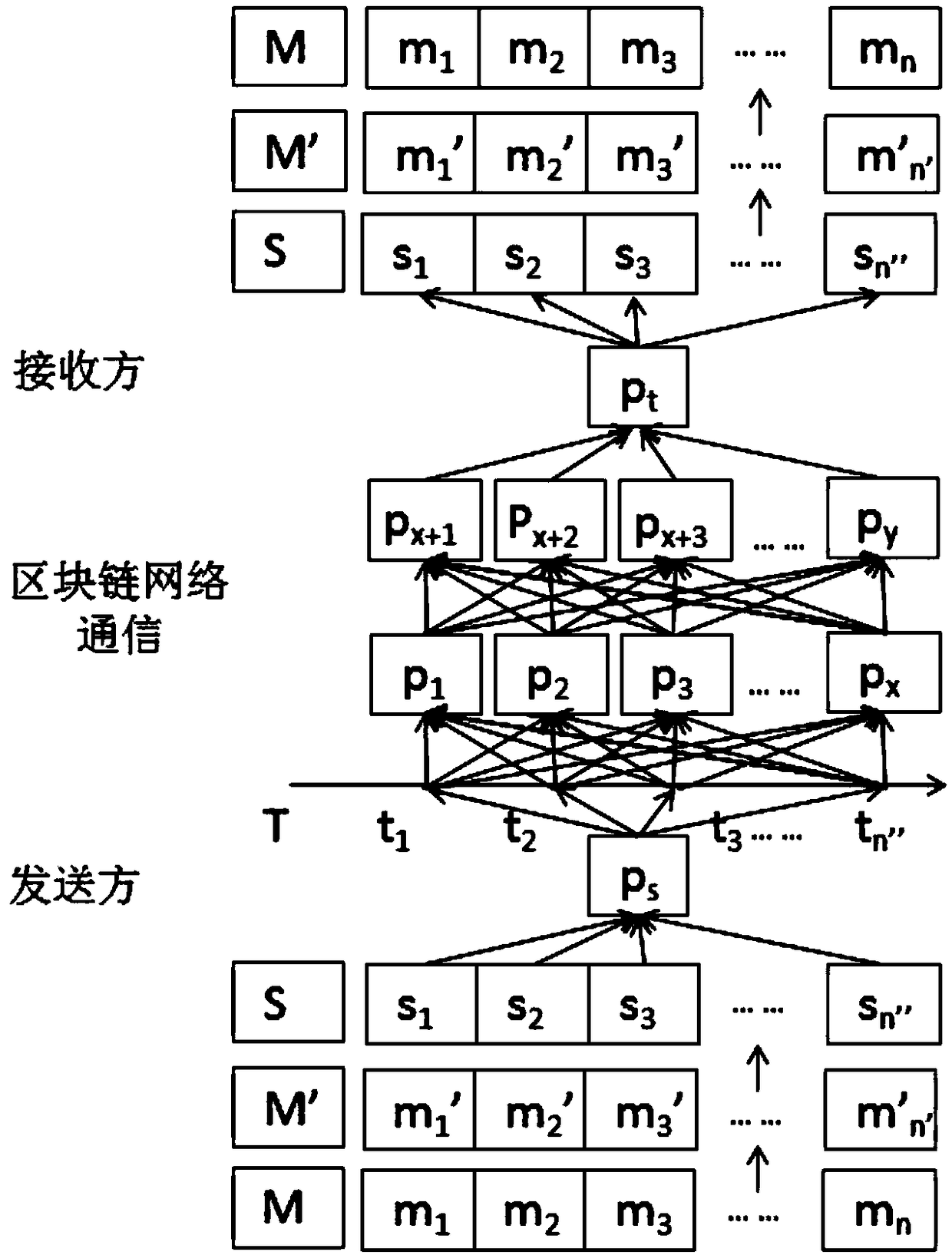
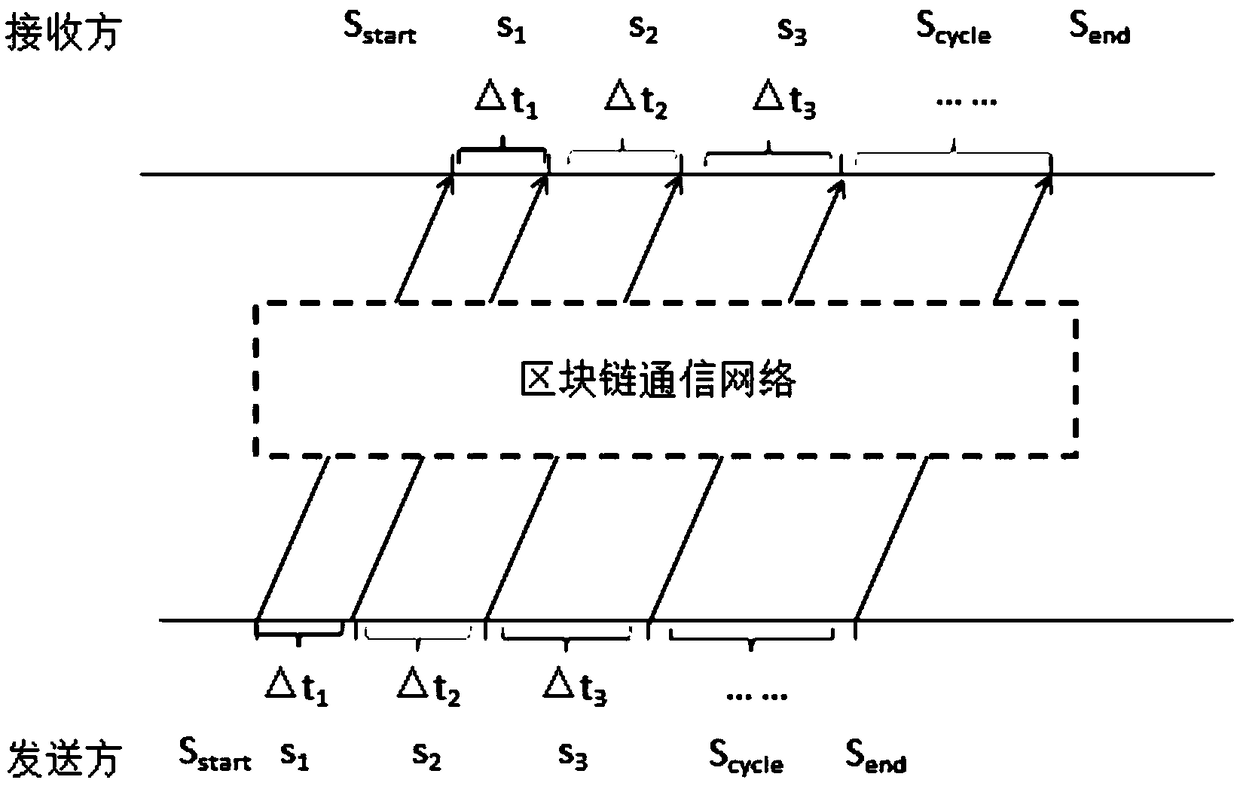
[0050] Specifically, the covert communication flow chart under the blockchain network is as follows: figure 2 As shown, the covert communication information encoding under the blockchain network is detailed as follows:
[0051] (1a) Using the previously agreed source coding or channel coding mechanism, which may include source coding or channel coding (for example: binary coding, Huffman coding, spreading code, etc.), the original hidden information sequence M(m 1 ,m 2 ,m 3 …m n ) to encode and generate the coded information sequence M’(m 1...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com