Blockchain data access authority control method based on proxy re-encryption
A proxy re-encryption and permission control technology, applied in the blockchain field, can solve the problems that hinder the flexibility and security of data access permission control, cannot achieve data-level permission control, and cannot dynamically adjust private data set access members, etc. To achieve the effect of ensuring safety, reliability and traceability
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment 1
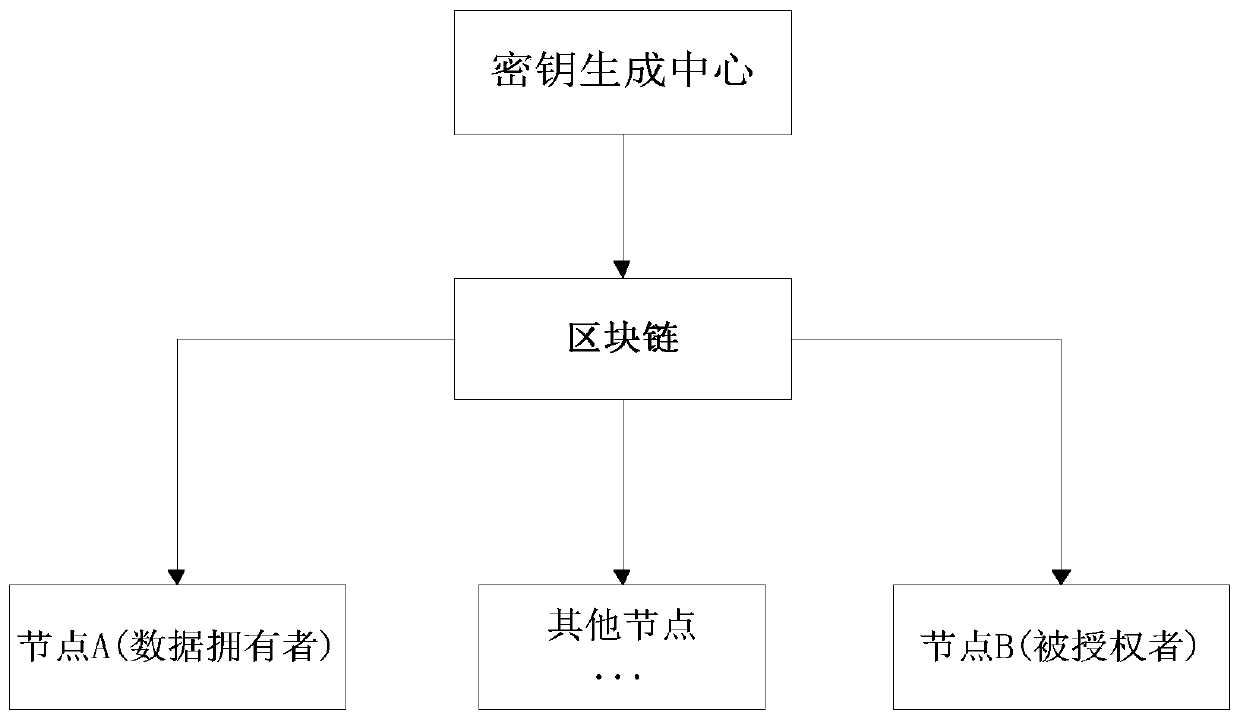
[0087] The objects involved in the method for controlling access rights of blockchain data based on proxy re-encryption in this embodiment are as follows: figure 1 As shown, the participants include: the key generation center, the blockchain and the nodes of the blockchain.
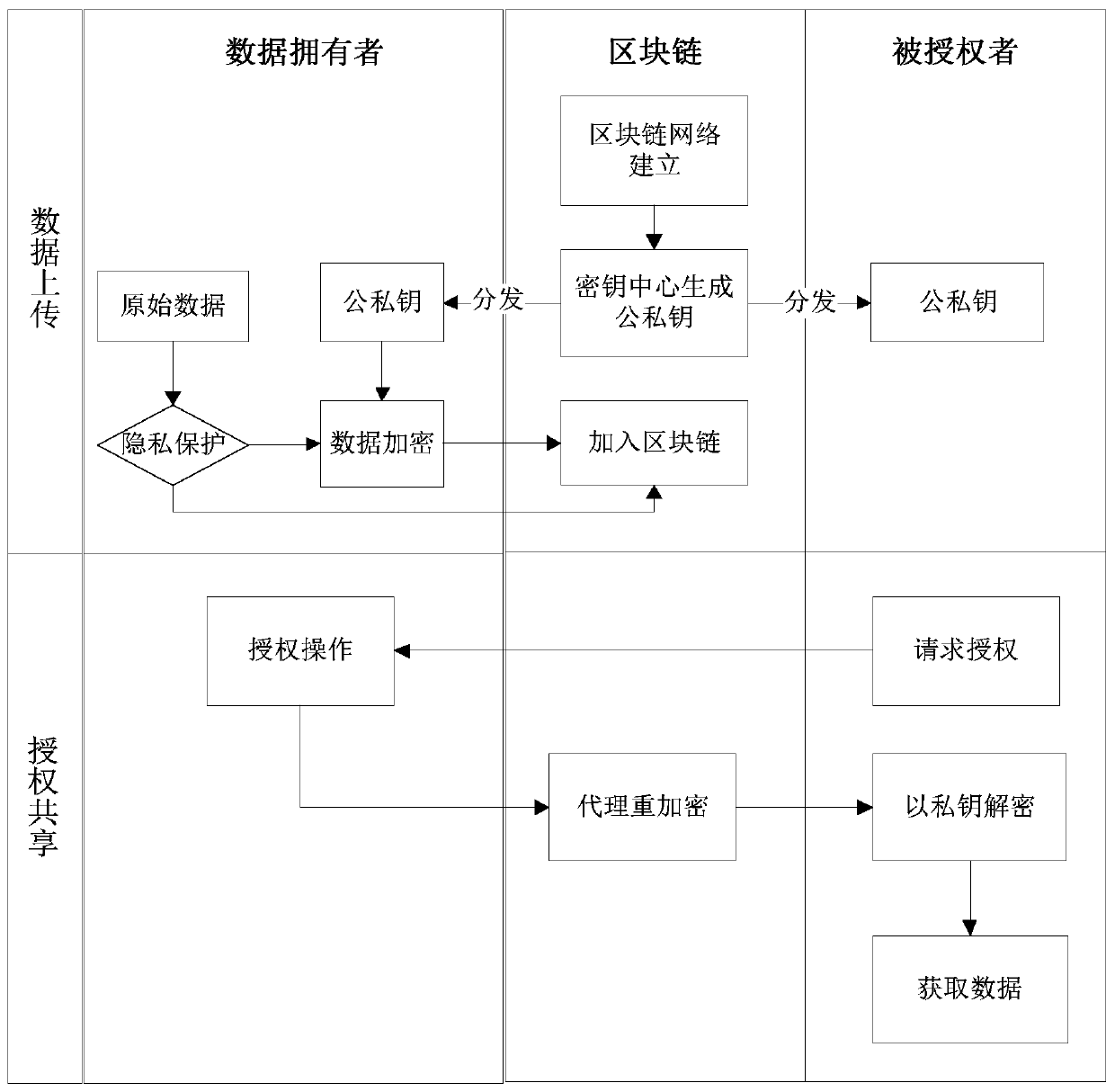
[0088] The overall process of the blockchain data access control method based on proxy re-encryption provided is as follows figure 2 As shown, it specifically includes the following steps:
[0089] (1) Establish a key generation center (KGC) in the blockchain network to generate and distribute public and private keys and symmetric keys.
[0090] Key parameter setting: completed by the key generation center. Algorithm input parameters L, L are security parameters (key length), output system parameters params based on elliptic bilinear mapping, params={type,q,h,r,exp2,exp1,sign1,sign0}, randomly select all Establish G in the system 1 For an element g of the group, calculate the bilinear mapping paring(g,g)=z, ...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com