Asset password exporting method used for operation and maintenance audit system
A password and asset technology, applied in the field of information security, to achieve the effect of convenient management, guarantee of security, and resistance to attackers
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment 1
[0057] A method for deriving asset passwords for an operation and maintenance audit system, mainly comprising the following steps:
[0058] Step S102: The password sharing module matches the information of the divided sub-ciphertext and the plaintext part according to the asset, and sends it as a record to the file analysis module, and the file analysis module encapsulates the data, and outputs n different password export files;
[0059] Step S103: Add the user name to the generated file to get a hash value, and digitally sign the key pair generated by each user; according to the preset authority division, assign files to each user, and use the user's files with the user Reversible file encryption using the login password; use encrypted channels to transfer files to the user's host.
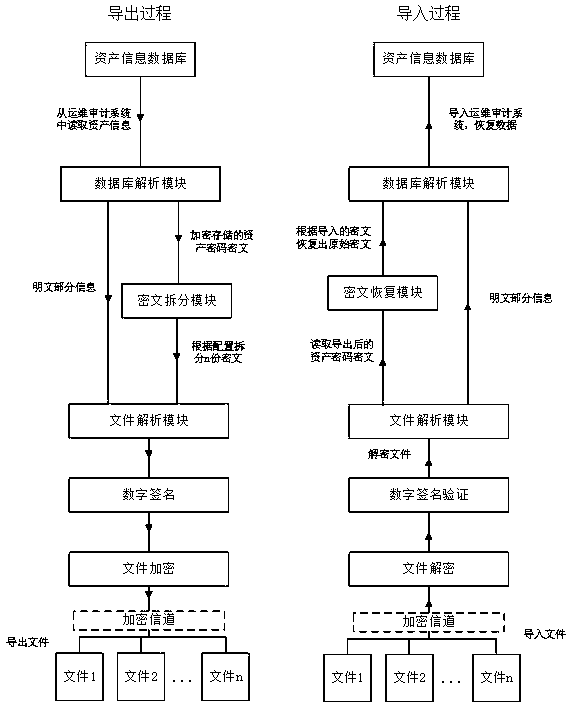
[0060] like figure 2 In the export process, the asset information is read from the asset information database, and then imported into the database analysis module to obtain part of the plaintex...
Embodiment 2
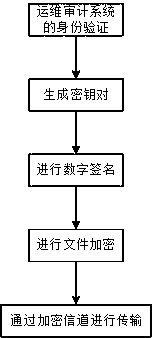
[0063] This embodiment is optimized on the basis of embodiment 1, such as image 3 As shown, in the step S103, the legal identity of the department administrator and the password administrator is first guaranteed through the identity verification system; inside the operation and maintenance audit system, a public key encryption system is used to generate a pair of public key and private keys for each password management user. Key pair, which is stored inside the system and used to digitally sign exported files. In the step S103, the generated file is reversibly encrypted using the password of the password manager to log in to the operation and maintenance audit system; the file is sent to the machine for backup by the password manager using the sftp protocol, and an encrypted channel is used to avoid man-in-the-middle attacks.
[0064] Through the multi-authentication system, it is guaranteed that the user exported using the asset password is a legitimate user. It realizes st...
Embodiment 3
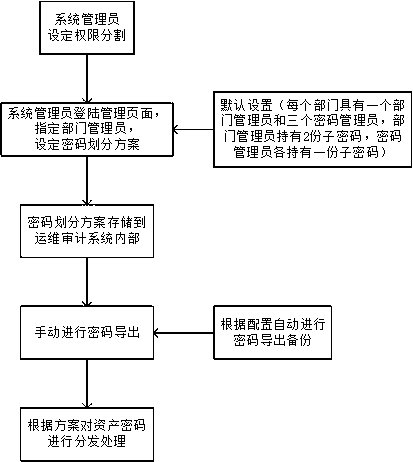
[0067] This embodiment is optimized on the basis of embodiment 1 or 2, as figure 1 As shown, the user in step S103 includes a department administrator and several password administrators, and the password import and recovery can be completed by the total file of the department administrator and one password administrator or the total files of all password administrators. The password export file n is 5, the department administrator is 1, and the password administrator is 3; the department administrator holds 2 sub-passwords, and the password administrators each hold 1 sub-password; when importing passwords, 3 sub-passwords are required.
[0068] like figure 1 As shown, the system administrator sets the division of authority. The default setting is that each department has a department administrator and three password administrators. The department administrator holds two sub-passwords, and each password administrator holds one sub-password. Then the system The administrator...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com