Privacy protecting method and privacy protecting device
A technology of privacy protection and detection algorithm, which is applied in image data processing, instrument, character and pattern recognition, etc., and can solve problems involving privacy in videos or pictures
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment 1
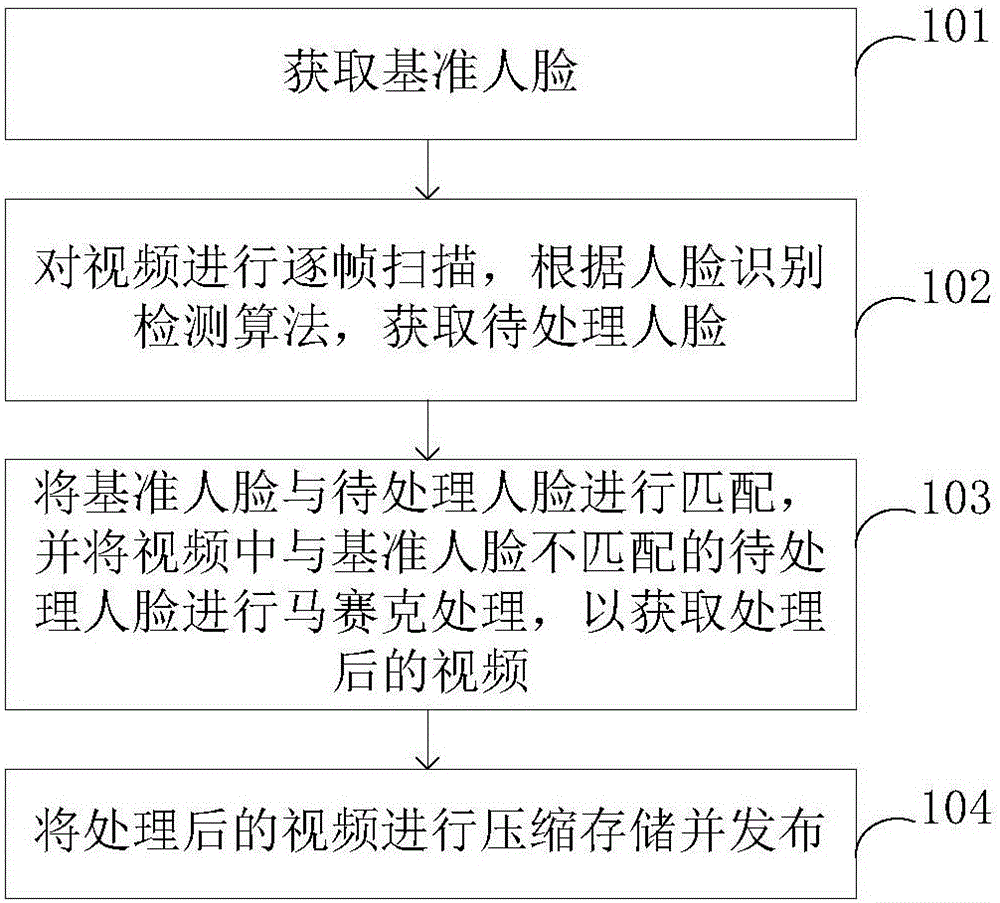
[0048] figure 1 A schematic flow chart of the privacy protection method provided in Embodiment 1 of the present invention; figure 1 As shown, the present embodiment provides a privacy protection method, the method is a video-based privacy protection method, including:
[0049] In step 101, a reference face is obtained, and the reference face is a face used for comparison.
[0050] Specifically, in practical applications, for example, during public security investigation, the face of the criminal suspect needs to be disclosed to the public so that the public can provide clues to the suspect. At this time, the criminal suspect can be regarded as a person of concern, The face of a person is the reference face, and the selection of the reference face is for comparison (matching) processing in the subsequent steps.
[0051] Step 102, scan the video frame by frame, and obtain faces to be processed according to a face recognition detection algorithm, and the faces to be processed a...
Embodiment 2
[0058] This embodiment is a supplementary description based on the above embodiments.
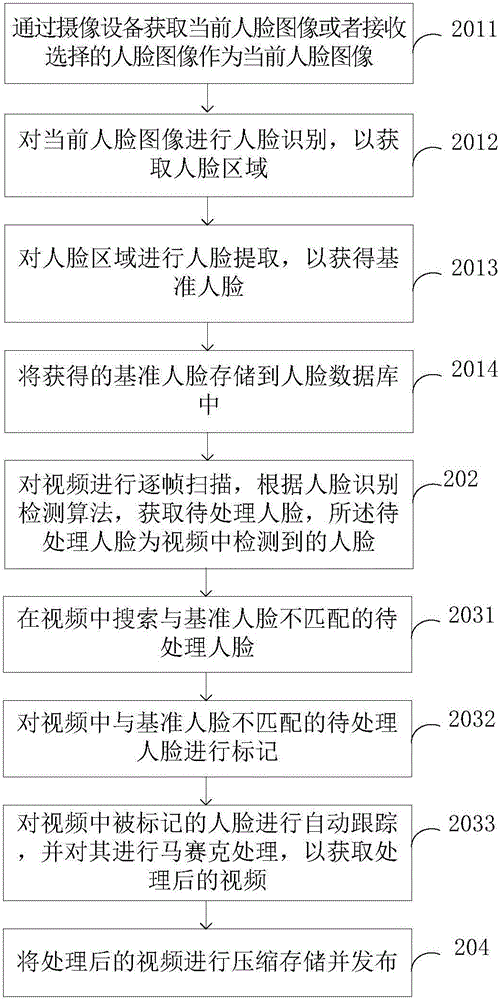
[0059] figure 2 A schematic flow diagram of the privacy protection method provided in Embodiment 2 of the present invention; as figure 2 As shown, the present embodiment provides a privacy protection method, the method is a video-based privacy protection method, including:
[0060] Step 2011, acquire the current face image through the camera device or receive the selected face image as the current face image;
[0061] Specifically, the current face image can be obtained by taking pictures with a mobile terminal or a computer, or can be obtained from a face database.
[0062] Step 2012, performing face recognition on the current face image to obtain the face area;
[0063] The current face image is processed through the face recognition algorithm to obtain the face area, so that the face area can be processed later.
[0064] Step 2013, perform face extraction on the face area to obtain a...
Embodiment 3
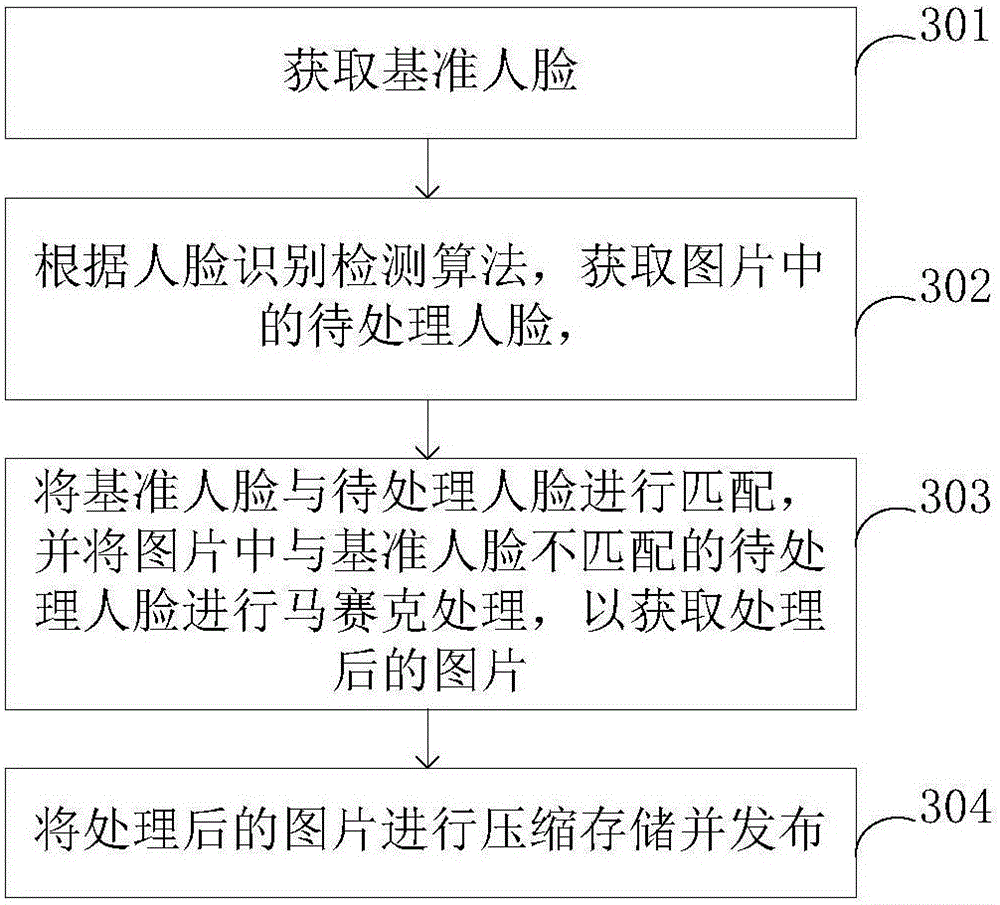
[0076] image 3 A schematic flow chart of the privacy protection method provided in Embodiment 3 of the present invention; image 3 As shown, this embodiment provides a privacy protection method, the method is a picture-based privacy protection method, including:
[0077] Step 301, acquiring a reference face, which is a face used for comparison;
[0078] Further, this step specifically includes:
[0079] Obtaining a picture of a human face to be extracted, wherein the picture of a human face to be extracted contains a reference human face;
[0080] Face extraction is performed on the image to be extracted to obtain a reference face.
[0081] Specifically, the picture of the human face to be extracted can be obtained by taking pictures with a mobile terminal or a computer, or can be obtained from a human face database.
[0082] Further, this step specifically includes: acquiring a reference face from a face database.
[0083] Specifically, the reference face is directly ob...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com