Data processing method and system
A data processing system and data processing technology, applied in the field of data security, can solve problems such as unavoidable data leakage, failure to meet the principle of minimum authority, etc., and achieve the effect of reducing the risk of key leakage and high security
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment 1
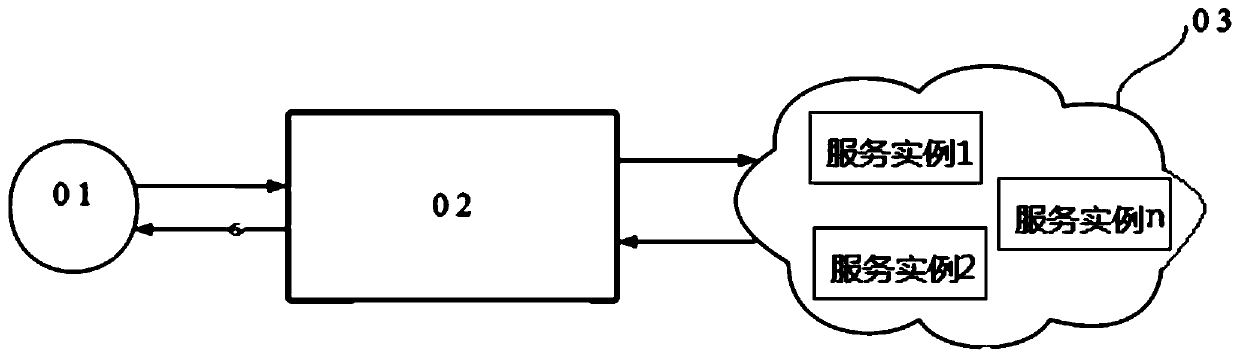
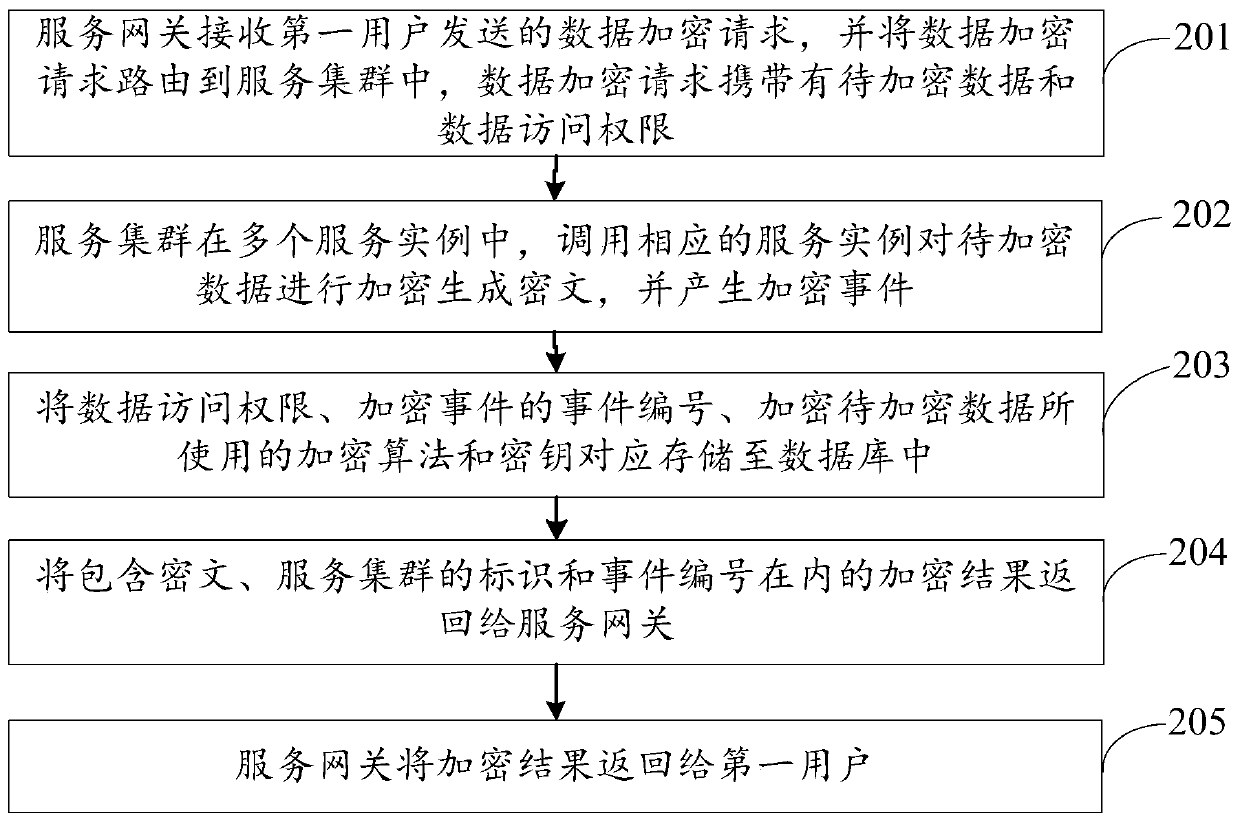
[0067] An embodiment of the present invention provides a data processing method, the data processing method is applied to a data processing system, the data processing system includes a service gateway and a service cluster, the service cluster includes multiple service instances, and a database is deployed in the service cluster, such as figure 2 As shown, the data processing method may include steps:
[0068] 201. The service gateway receives a data encryption request sent by a first user, and routes the data encryption request to the service cluster, where the data encryption request carries data to be encrypted and data access rights.
[0069] In this embodiment, the first user may be a data producer or a data provider, and the first user submits a data encryption request to the service gateway through the first client.
[0070] Wherein, the data to be encrypted carried in the data encryption request may be data containing sensitive information, for example, user identity...
Embodiment 2
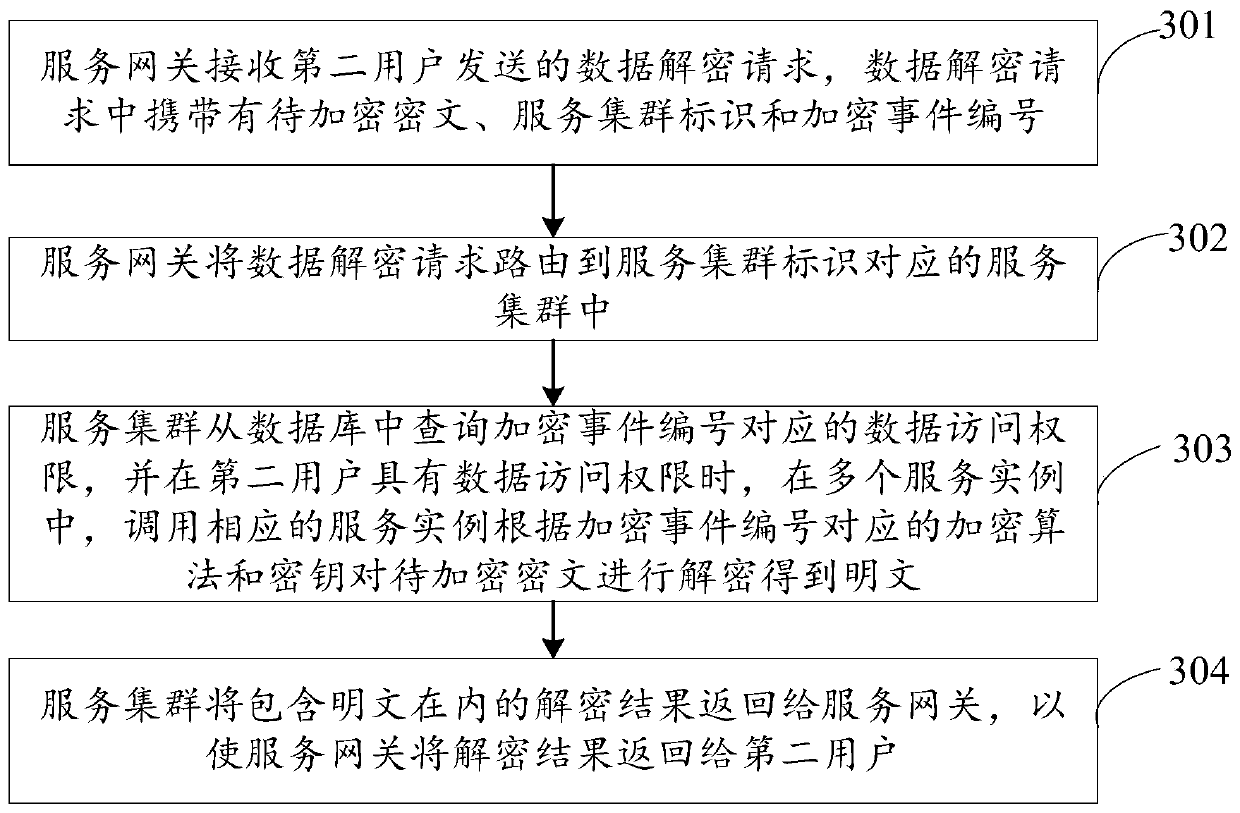
[0110] An embodiment of the present invention provides a data processing method. In this embodiment, the data processing method includes figure 2 In addition to the steps described in , after step 205, it also includes steps 301 to 304, which are omitted for the sake of brevity. figure 2 steps described in . Such as image 3 As shown, the data processing method also includes:
[0111] 301. The service gateway receives a data decryption request sent by a second user, and the data decryption request carries ciphertext to be encrypted, a service cluster identifier, and an encrypted event number.
[0112] In this embodiment, the second user may be a data user, and the second user submits a data encryption request to the service gateway through the second client.
[0113] 302. The service gateway routes the data decryption request to the service cluster corresponding to the service cluster identifier.
[0114] In this embodiment, the service gateway may determine the correspo...
Embodiment 3
[0126] An embodiment of the present invention provides a data processing system, such as Figure 4 As shown, the data processing system may include a service gateway 41 and a service cluster 42, the service cluster 42 includes multiple service instances, and a database is deployed in the service cluster 42, wherein:
[0127] The service gateway 41 is configured to receive the data encryption request sent by the first user, and route the data encryption request to the service cluster, where the data encryption request carries the data to be encrypted and the data access authority;
[0128] The service cluster 42 is used to call corresponding service instances among multiple service instances to encrypt the data to be encrypted to generate ciphertext and generate encryption events;
[0129] The service cluster 42 is also used to correspondingly store the data access authority, the event number of the encrypted event, the encryption algorithm and the key used to encrypt the data ...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com