Security authentication method for wireless network
A security authentication, wireless network technology, applied in the field of wireless network security authentication, can solve the problems of weak encryption strength, key cracking, trouble entering the key, etc., to enhance security, ensure security, avoid brute force cracking and key The effect of leakage
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
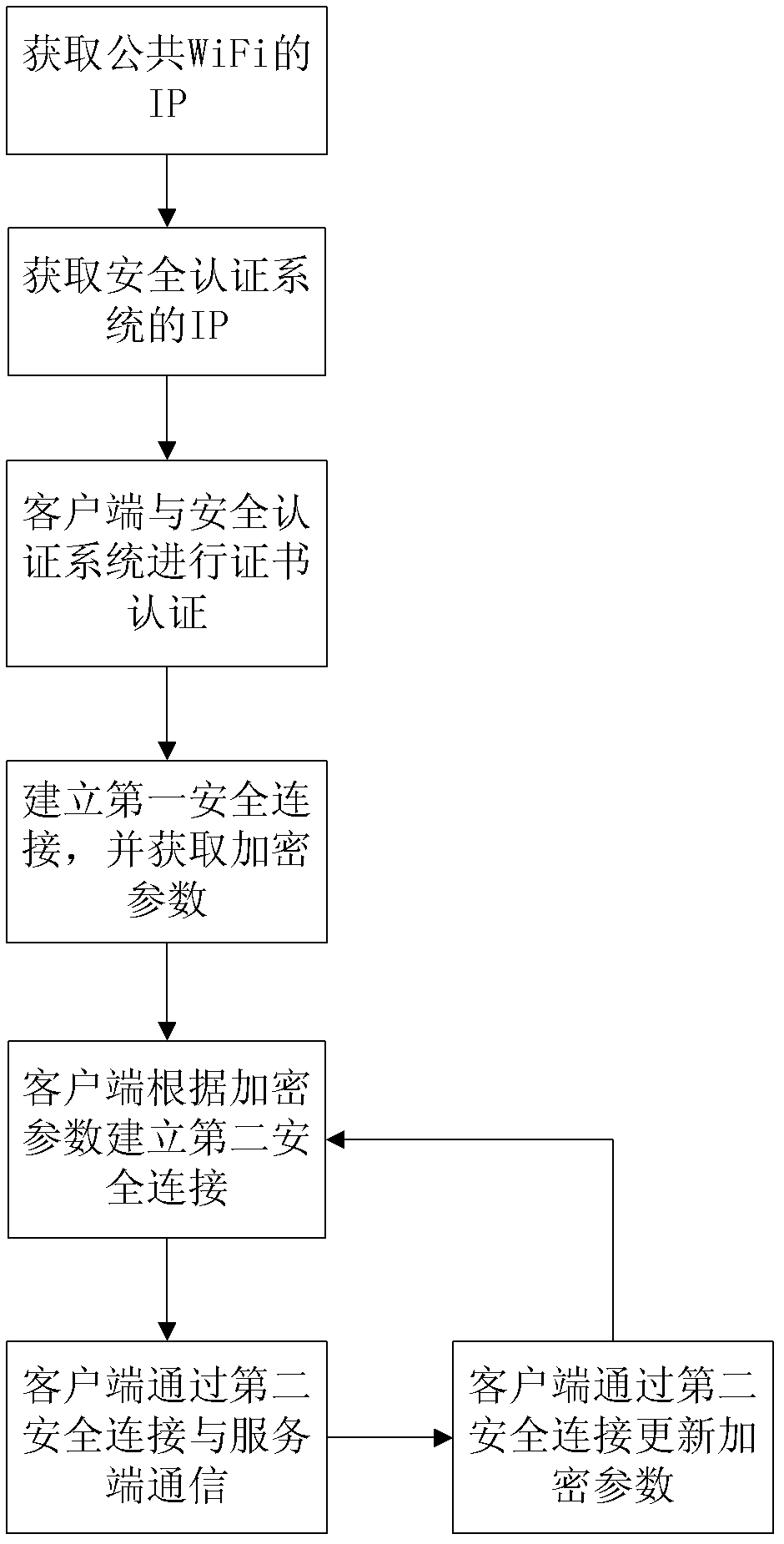
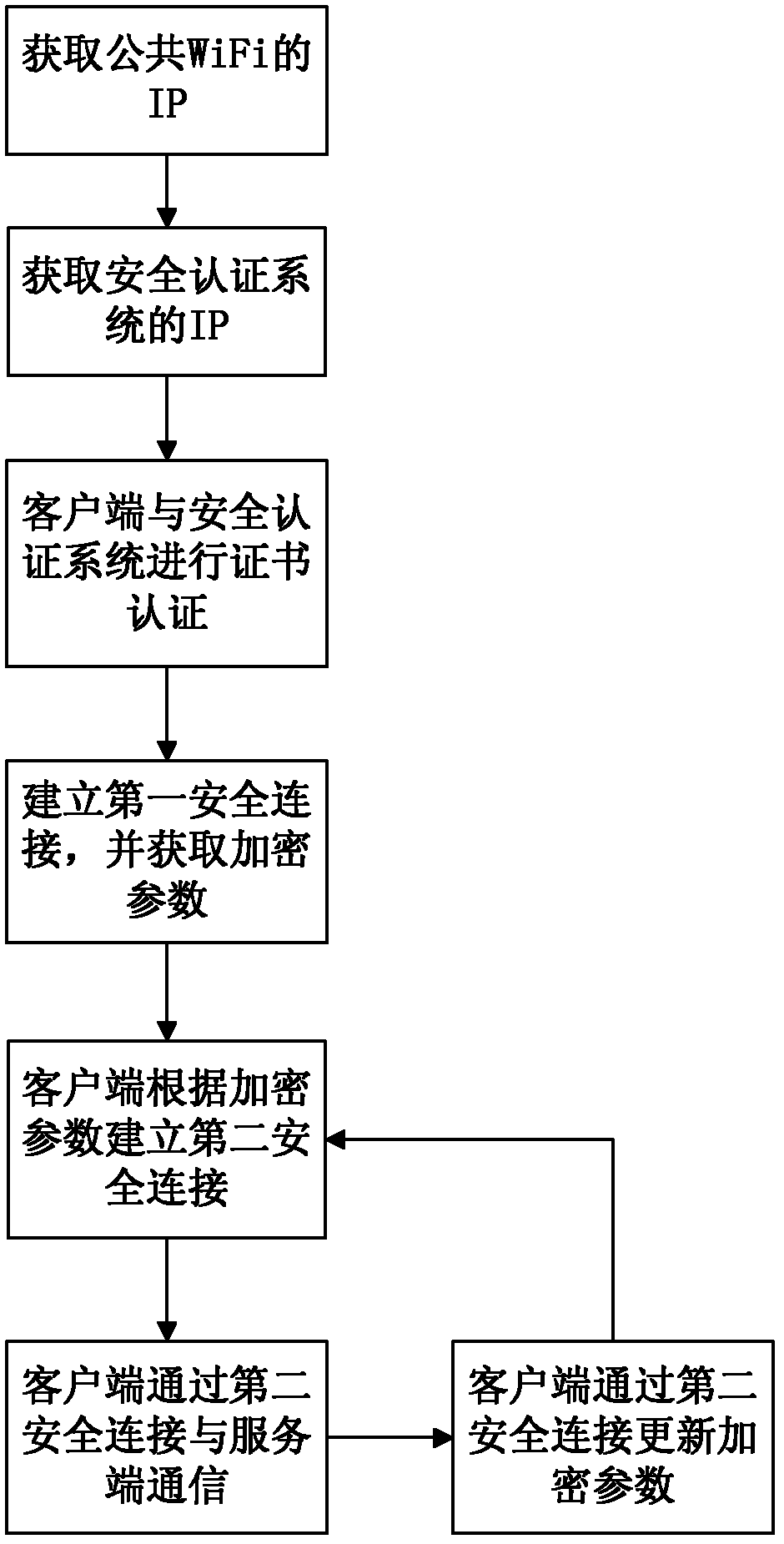
[0025] Such as figure 1 The method for wireless network security authentication of the present invention has a WiFi server and a client. The steps include:
[0026] a. Deploy the authentication service program on the client, the client scans the wireless network, and automatically accesses the public open system of the WiFi server to obtain the corresponding IP address;
[0027] b. The client obtains the IP address of the security authentication system of the WiFi server according to the IP address of the public open system. The IP address may be the gateway address of the public open system IP address. The client accesses the address through the SSH authentication port of the security authentication system to try to connect;
[0028] c. The security authentication system of the WiFi server requires certificate authentication for visiting clients. The client authenticates with the security authentication system by reading a local certificate or a USBkey certificate, wherein the USB...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com