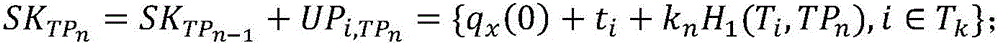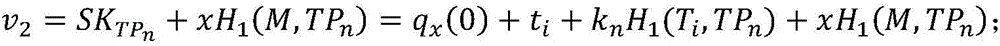Key isolation signing method based on attribute
An attribute and key technology, which is applied to the public key and key distribution of secure communication, can solve the problems of increasing terminal computing overhead and lack of protection measures for key leakage
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
[0034] The specific embodiment of the present invention will be further described in detail in conjunction with the accompanying drawings.
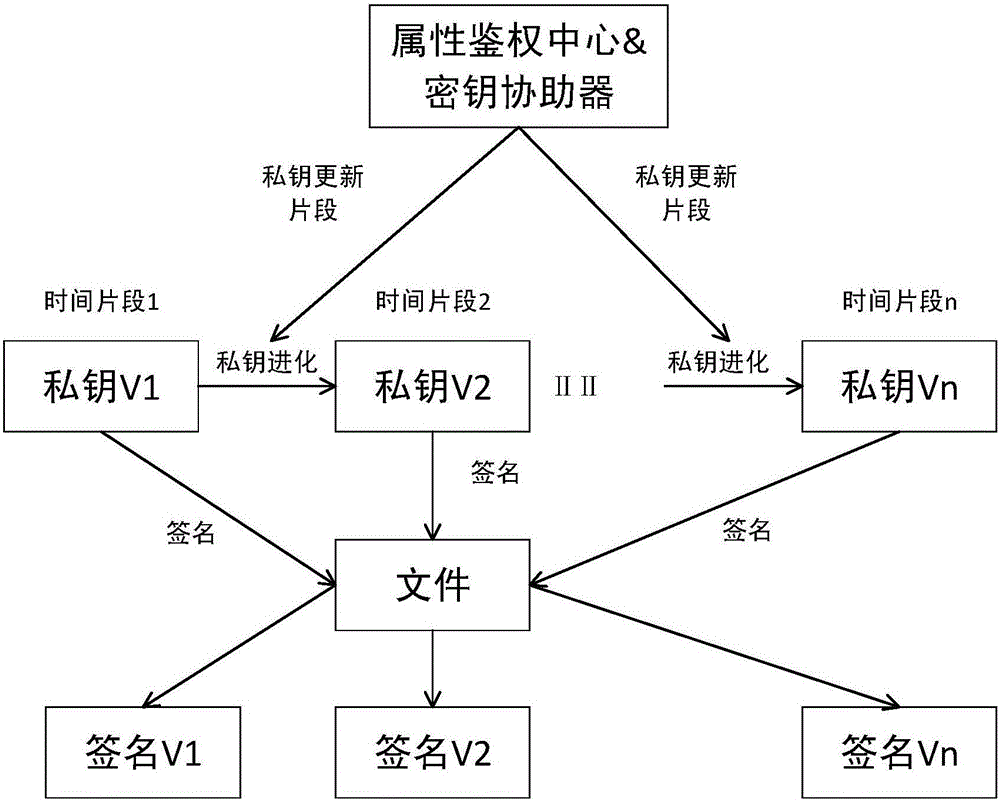
[0035] The present invention discloses an attribute-based key isolation signature method, and the entire signature system is divided into several independent time segments, such as figure 1 shown. Whenever the system enters a new time segment, the key assister generates a private key update segment, and the user updates the private key. For a file, the user signs with the private key corresponding to the current time segment, and the verification result of the signature also corresponds to a certain time segment of the system. If the user's private key is leaked in a certain time segment, the system can still maintain forward security and backward security in other time segments, minimizing the harm of private key leakage.
[0036] In the process of signing, no bilinear pairing operation is required, which reduces the calculation overhe...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com