Key-insulated safe car networking V2I authentication system and method
An authentication system, a technology of the Internet of Vehicles, which is applied in the field of security authentication for communication between vehicles and infrastructure, and can solve the problems of time-consuming bilinear mapping and limited resources.
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
specific Embodiment approach
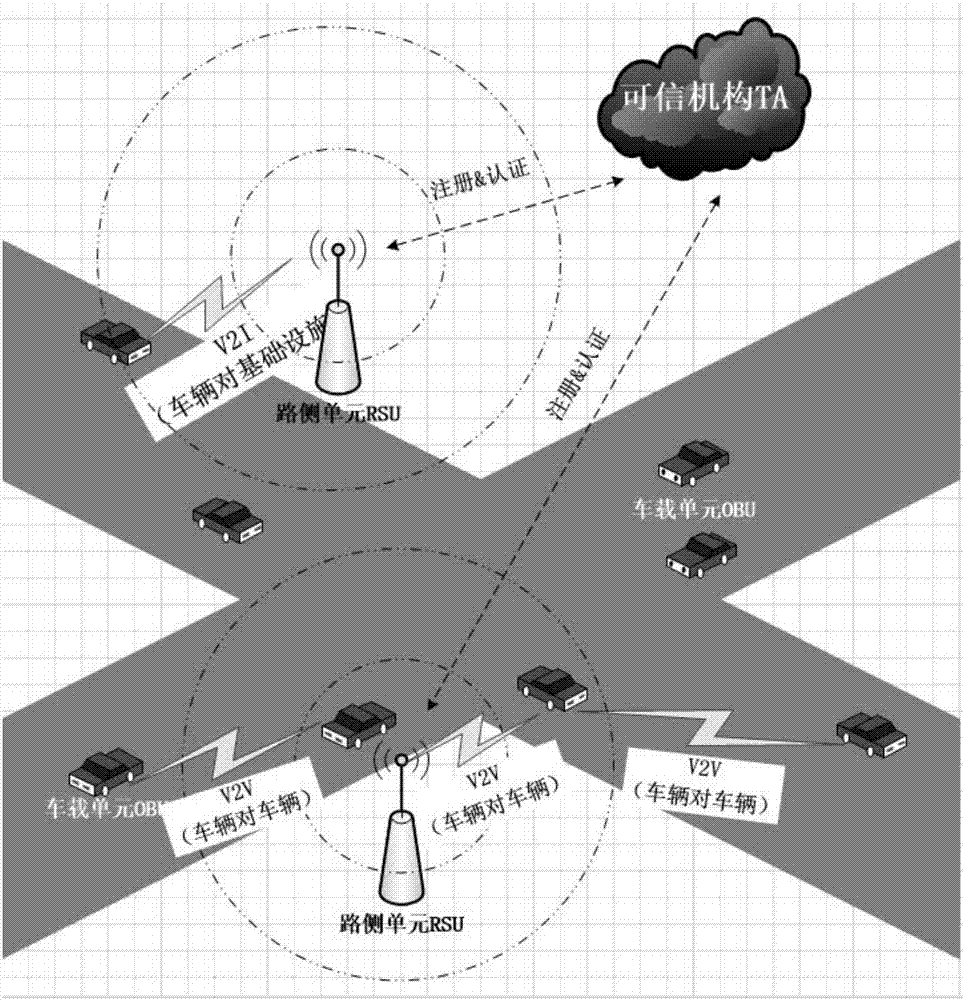
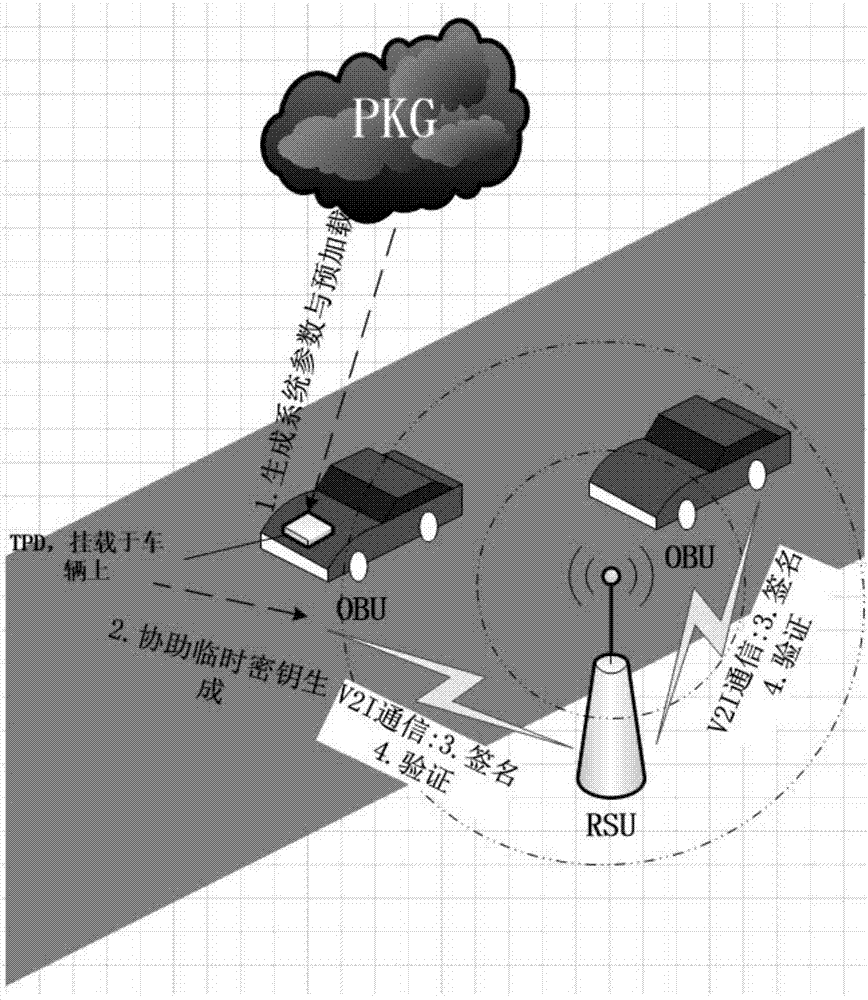
[0036] refer to Figure 1-Figure 3 , the specific embodiments of the present invention are as follows:
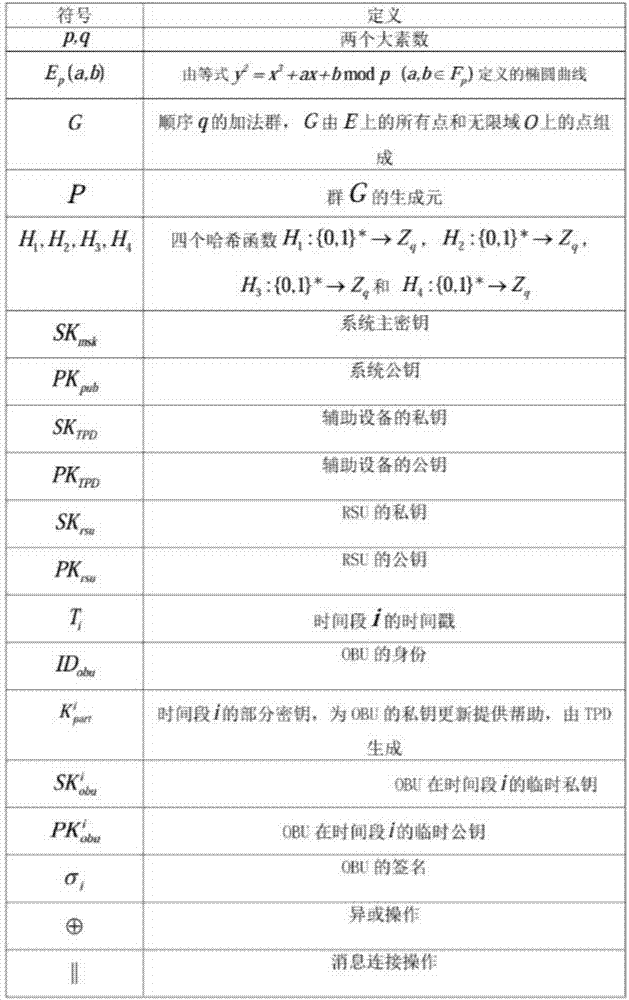
[0037] 1. In the most initial situation, each element under the Internet of Vehicles is initialized. First, the key generation center PKG generates a series of basic system environment parameters and selects random numbers As the system master key, and calculate the system public key PK pub =SK msk P, choose random number As the private key of the helper TPD, and calculate its corresponding public key PK TPD =SK TPD • P; all these four parameters are preloaded into the helper TPD. Road side unit RSU selects random number As your own private key, and calculate the corresponding public key PK rsu =SK rsu ·P. Among them, the public key of the vehicle OBU and its corresponding public key carrying the assistant TPD have been loaded in advance, and finally, the key generation center PKG publishes the public parameter set:
[0038] param={a,b,p,q,P,PK pub , PK TPD ...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com