Sensor data protection method and system, computer equipment and intelligent terminal
A data protection and sensor technology, applied in the field of information and data security, can solve problems such as application crashes, reduced availability recognition accuracy and accuracy, and realistic data distortion, to eliminate the ability to infer, improve poor real-time performance, and prevent The effect of malicious inference
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment 1
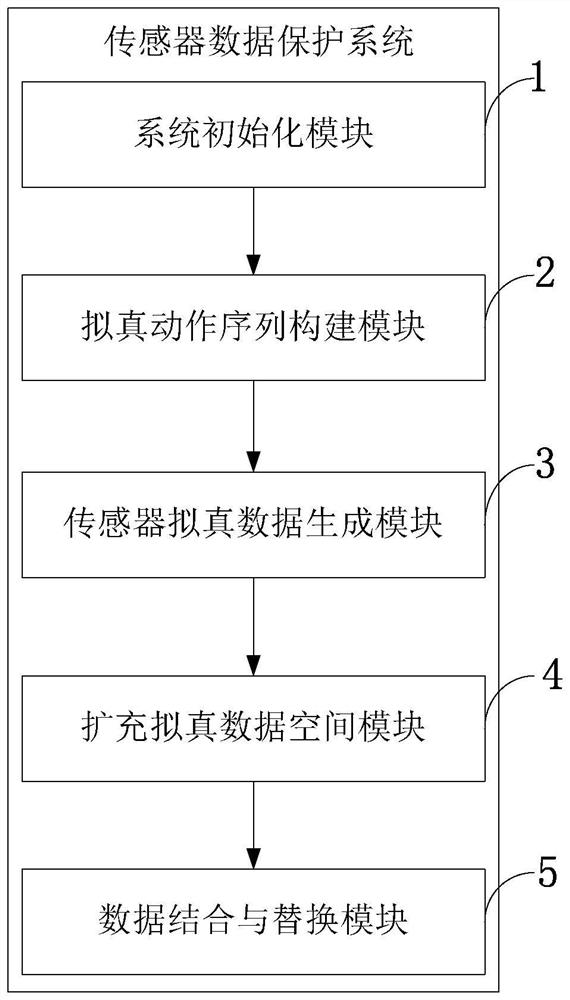
[0098] The sensor data protection method provided by the present invention achieves the privacy protection effect of full life cycle and full anonymity by using the sensor simulation data sequence to replace the sensor data in an all-round way at all times. The sensor data privacy protection method based on multi-sensor immersive data replacement and the multi-sensor immersive data generation method are improved.
[0099] The sensor data privacy protection method of the present invention analyzes the existing differential privacy protection methods for privacy protection, and aims at the limitation of possible user background leakage risks caused by the use of real data processing in the current scheme, and uses highly realistic multi-sensor data for mobile data. Equipment sensors are replaced all the time and in all directions. During the whole process, the server cannot obtain the real data of the user. The server can perform classification tasks such as action classificatio...
Embodiment 2
[0103] The invention is based on the Android terminal sensor data protection method based on multi-sensor simulation data replacement. o The sensor data replacement of the id platform is combined with the simulation data generation method to protect the privacy and security of sensor data from the data generation process of the mobile terminal, and at the same time prevent the malicious theft and analysis of user privacy by third parties on the application server side; the details include the following step:
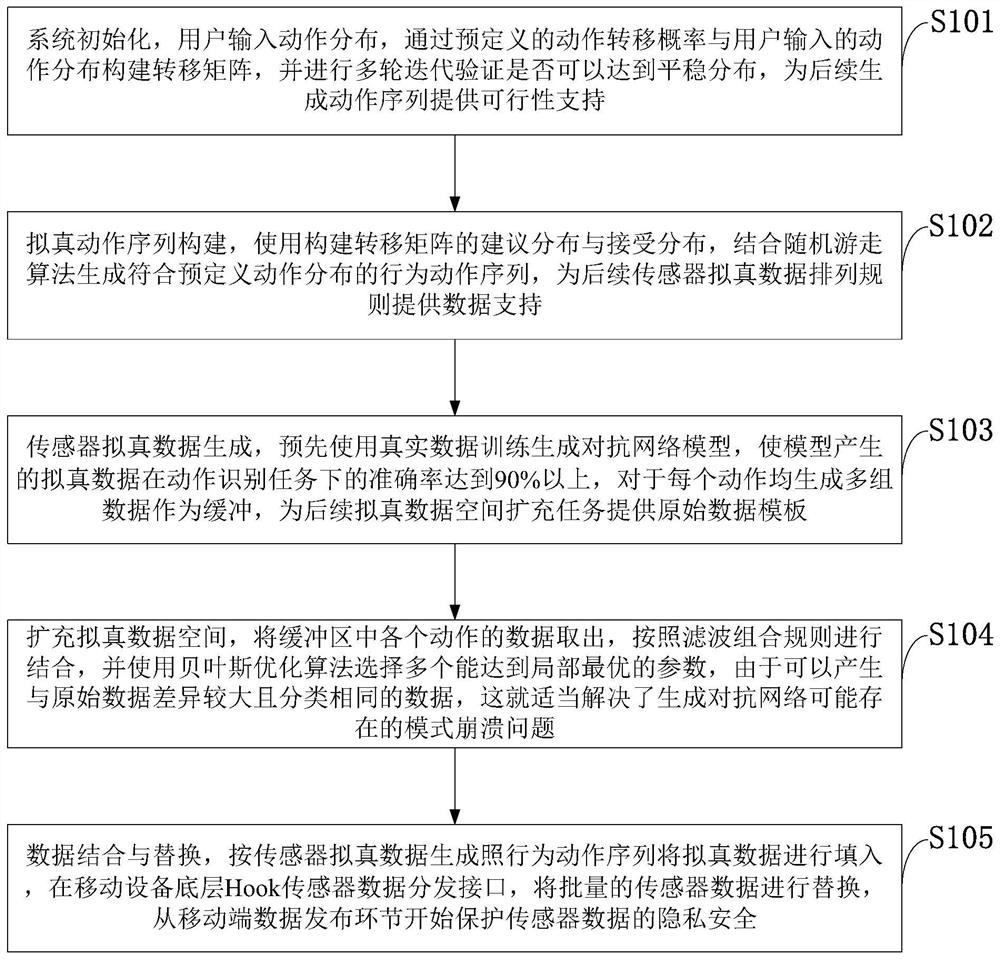
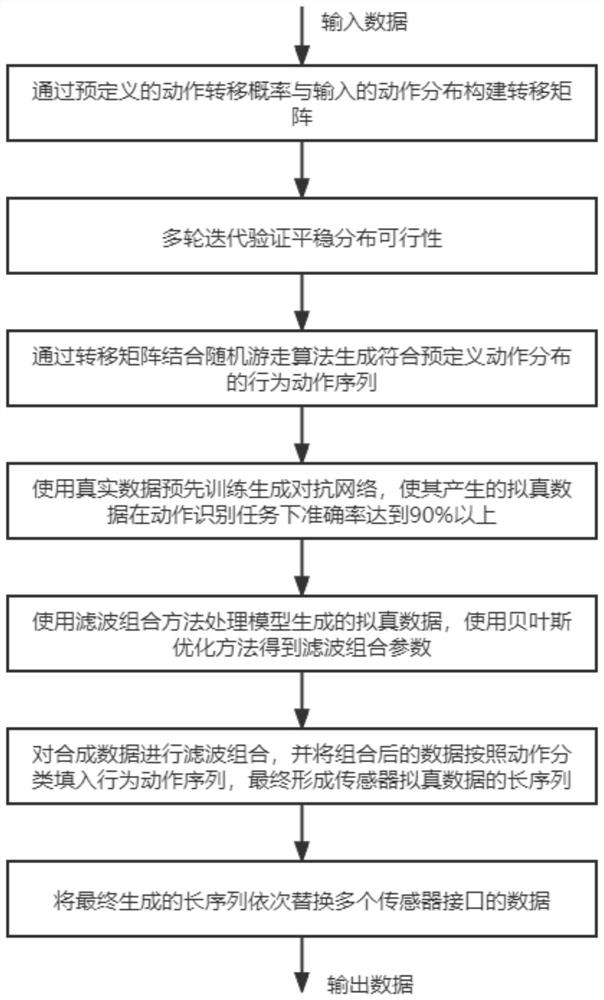
[0104] Step 1, action sequence generation: use the random walk algorithm based on the Markov chain Monte Carlo method to construct a state transition matrix according to the action ratio preset by the user, so as to realize the generation of false action action sequences; use the Monte Carlo method to construct The Markov transition matrix adopts the transition kernel formula as:
[0105] p(x,x')=q(x,x')α(x,x');
[0106] where q(x, x') is called the proposal distributi...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com